Trellix Endpoint Forensics
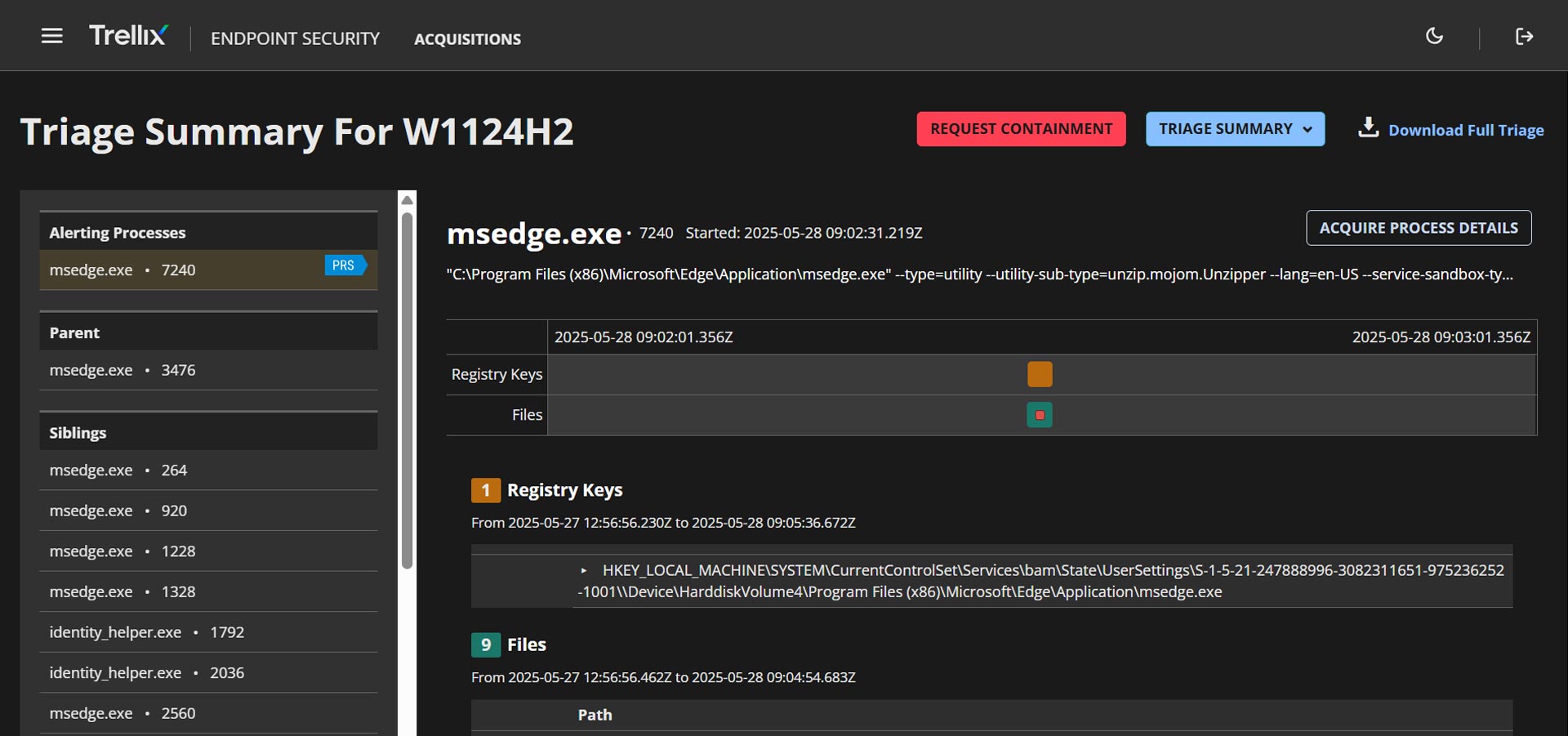
Trellix Endpoint Forensics (HX) performs fast, targeted forensic investigations across thousands of endpoints.
Industry leading endpoint forensics solution
Trellix Endpoint Forensics is chosen by leading incident response teams around the globe. It can collect forensics data from thousands of endpoints in seconds.
Why Trellix Endpoint Forensics?
Protect
Stop threats before they happen. Identify configuration issues including potential exposure to zero days.
Collect
Endpoint telemetry collection, analysis, and indicator searching. Can be deployed post-breach.
Respond
Stop malicious processes, disconnect users, and quarantine hosts to prevent data exfiltration.
Product features
Related Endpoint Security products
Trellix Endpoint Security
Protect against modern and novel threats with multi-layered protection stack delivered in a single agent
Trellix Endpoint Detection and Response
Comprehensive EDR solution that reduces time to detection and time to remediation, reducing alert fatigue.
Trellix Network Detection and Response
Detect and block advanced threats and lateral movement in real time. Resolve incidents faster using concrete evidence and actionable intelligence.
Complementary services to accelerate your success
Installation and Configuration
Integration and Training
Monitoring and Optimization
Industry recognition
Trellix is recognized as an industry leader by key analyst firms
Related resources

Trellix's EDR with Forensics helps find the initial infection point of attacks, capturing forensic artifacts to reduce the time an attacker is present in an organization.

IDC identifies the shift to modern endpoint security, emphasizing the need for AI-guided solutions, as well as remediation and policy management.
Trellix named a Leader in the IDC MarketScape for Modern Endpoint Security offering EPP, EDR, forensics, and AI-guided investigations in a single agent.