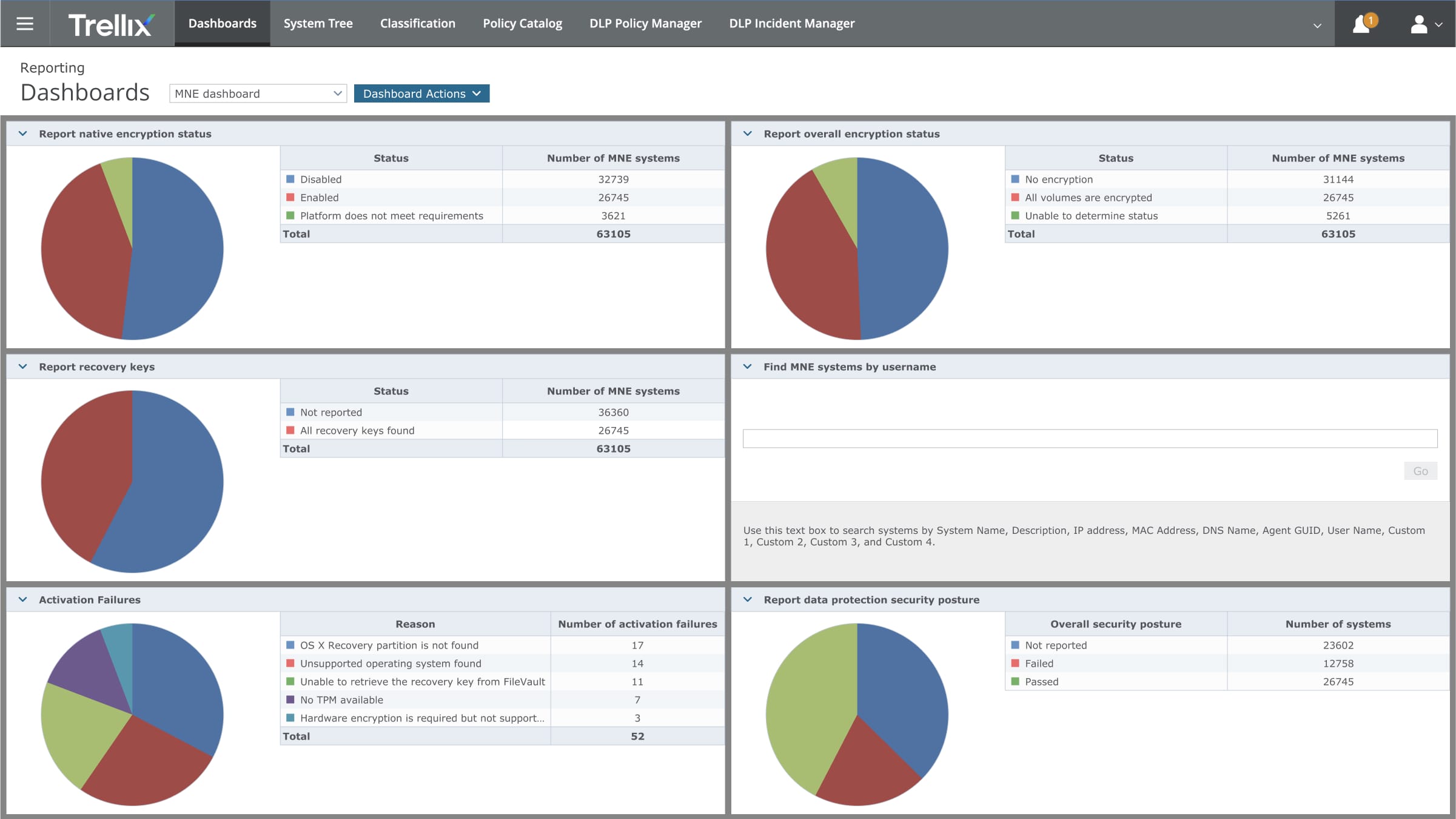
Protect Data and Devices from Unauthorized Access
Trellix Data Encryption products secure devices and removable media to ensure that only authorized users can access the information they contain. Deploy encryption policies through a single management console, while monitoring encryption status and generating compliance reports.
Did you know ...
Trellix Data Security statistics
00M+
Drives protected worldwide by Trellix Data Encryption
000+
File formats supported by Trellix Data Loss Prevention
000+
Patch protections delivered by Trellix Database Security
Why Trellix Data Encryption?
Protect Devices Anywhere
Data on devices and removable media is protected if lost or stolen.
Quickly Demonstrate Compliance
Pre-boot authentication options for multi-user environments and device status reports.
Save Time and Resources
Administer policies from a single console and offer user self-service options.
Product features
Trellix Data Encryption products
Trellix Drive Encryption
Protect data and devices from unauthorized access.
- Control user and device access through smart card authentication
- Authenticate multiple users and maintain compliance
- Use a single management platform integrated with Active Directory
Trellix Native Drive Encryption
Manage Microsoft BitLocker and Apple FileVault.
- Protect data on devices that are lost or stolen
- Deploy through a single console available on-premises or via Saas
- Manage encryption keys and pin features on devices
Trellix File & Removable Media Protection
Enforce encryption and authentication on removable media.
- Protect files, folders, network shares, and removable media devices
- Choose from a variety of authentication methods
- Compatible with Windows and macOS
Complementary services to accelerate your success
Installation and Configuration
Integration and Training
Monitoring and Optimization
Frequently asked questions
Related resources

What problems does Data Security solve, and what capabilities should your solution include? Take a look at the future of Data Security.

Follow along as our Data Security hero embarks on an epic journey to protect sensitive information at an organization of superheroes.

Understand insider threats and how Trellix technologies like File & Removable Media Protection (FRP) can help protect against them.

Understand insider threats and how Trellix technologies like File & Removable Media Protection (FRP) can help protect against them.