Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Data Security - A Hero's Journey
By Robert Foster, Liberty Williams · October 27, 2023
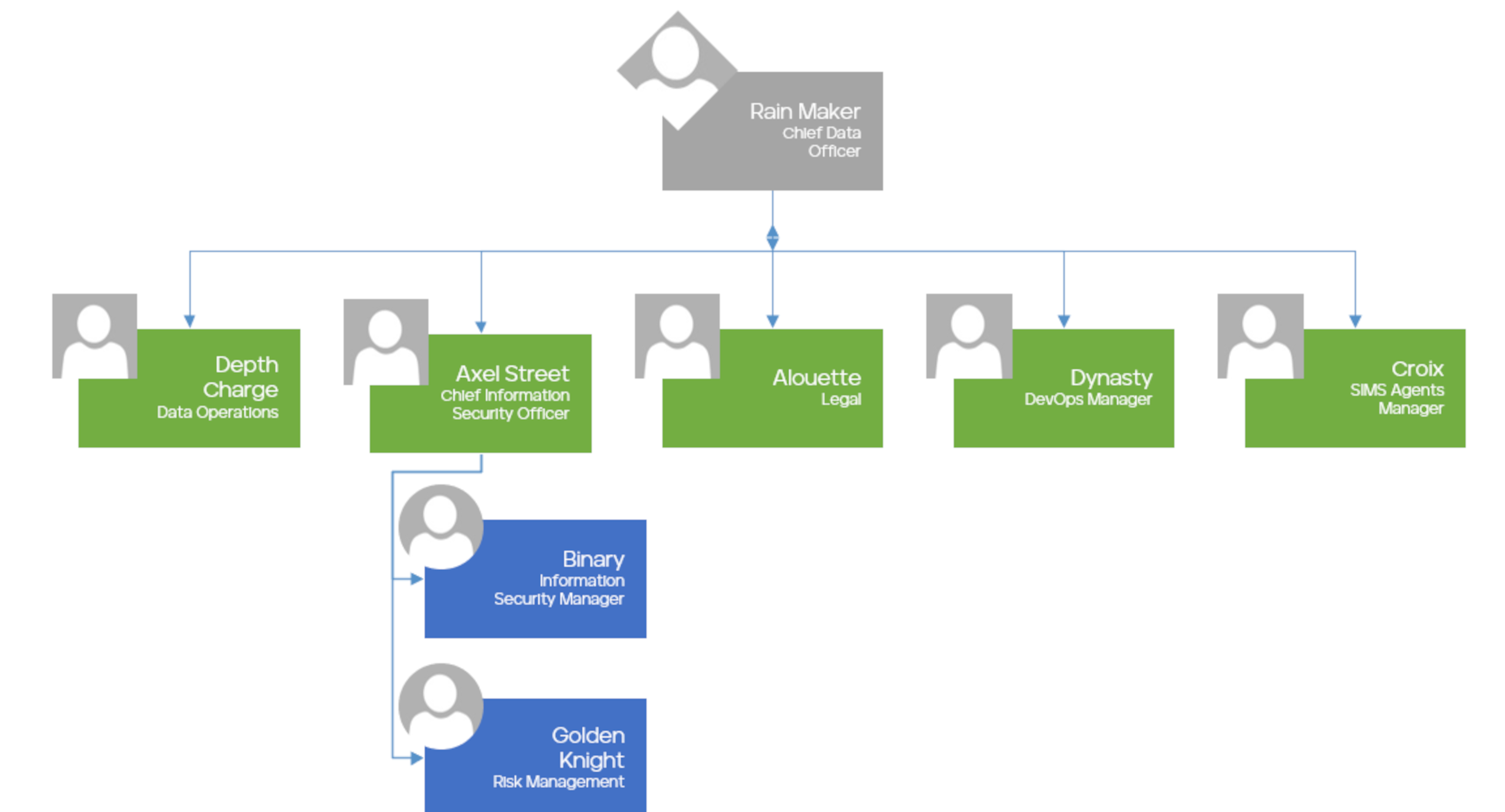
Axel reached out to his Information Security Manager, Binary, to get the back story on DLP. Binary explained that they had no idea what data they were supposed to protect. He also mentioned that out-of-the-box rules from DLP Vendors threw such a massive number of false positives that they couldn’t research any incident.
Axel and Ice Storm meet with the NSKA CDO, Rain Maker.
They discuss the NSKA’s:
- Data Strategy,
- Identifying Trade Secrets,
- The maturity of their Data Governance initiatives, and if they have assigned any roles and responsibilities.
- Building a Data-Driven Culture
Rain Maker mentions that their Data Strategy aims to enhance customer experiences by utilizing a segmentation strategy focused on their Superhero Identity Management System for SIMS Agents.
Working off the Data Governance Org Chart, Ice Storm wants to meet with the Legal/Chief of Compliance/Risk Management Team to review:
- Legal Regulatory Compliance
- Critical Data Elements (CDE)
- Data Risk Assessments
- Data Sharing Agreements
Alouette determined that Secret Superhero Information (SSI) was the highest risk and that we should start with Data Domains that deal with SSI.
Since the SIMS Agents are our most critical Business Unit in our Data Strategy, Ice Storm and Axel Street start with Croix the head of the SIMS Agents department.
They ask how they use sensitive data in their daily operations with a key focus on:
- Where they consume the data
- Where they store the data
- Who they share the data with
Our heroes then interview Depth Charge, the Data Operations Manager, to gain a better understanding of the data in SIMS.To improve policy development, our heroes should clearly understand several data operation processes.
- Data Flow Maps
- Data Storage Types
- Data Operations and Quality Processes
- Metadata Management
- Data Consumers
In Joseph Campbell's original concept of the hero's journey, he outlined several stages that a hero typically goes through, and encountering helpers and mentors is a key part of this process.
Trellix Professional Services is here to assist you in your pursuit of your Data Security initiatives, ensuring optimal results. Throughout this series, we will delve into Axel's journey by exploring components in greater detail through individual episodes.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.