Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Automated Moving Target Defense: An XDR Deployment Scenario
By Doug Umoru and Liberty Williams · November 6, 2023
Ever get tired of manually responding to emerging malware and advanced persistent threats? Us too! Take advantage of the Trellix XDR Platform’s automation to ruin the bad guy’s day!
Why does it matter:
At Trellix, we know CISOs face big, constantly shifting challenges. 94% of you say the right technology would save your team significant time, and 81% of you say the right technology would reduce overtime. That’s not surprising, as the volume of cyber threats looks like a hockey stick, and it’s not likely to change direction soon. It’s tempting to dream of hiring our way out of overtime, but it may not be possible even if you have the budget. We must rely on innovation, automation, and AI/ML to get the job done. We need tools that automatically flip the script on our cyber adversaries with minimal real-time human oversight.
Understand the Problem:
Defense in the cybersecurity game has traditionally been the underdog. The overwhelming advantage of having to be right only once favors attackers, while defenders must get it right. Every. Single. Time. This challenge is compounded by the fact that traditional countermeasures are based on patterns, which had to be discovered and defined by humans at a human pace.
Our adversaries, on the other hand, are only limited by the vulnerabilities available to them. Five or six malicious packages might exploit the same vulnerability, each of which could be mutated in hundreds or thousands of ways. Our good friend ChatGPT even got in the game to make our adversaries’ life easier. Static defenses are mandatory but insufficient to meet modern organizations' or CISOs' needs.
Define the Solution:
We can rely on the expertise of the US National Institute of Standards and Technology (NIST) as expressed in their Special Publication 800 series. While these standards were baked up with the goodness of US Civilian Gov requirements inside, they’re nutritionally complete for any growing cybersecurity program! (As part of a balanced cybersecurity governance breakfast.)
Key Publications:
- NIST SP 800-207 Zero Trust Architecture
- NIST SP 800-53 Rev 5 Security and Privacy Controls for Information Systems
Our key control families for this challenge are Access Control (AC) 3: Access Enforcement and Incident Response (IR) 4: Incident Handling. Let’s check in with our friends at CSF.tools for more details on these controls:
- AC-3(13): Attribute-based Access Control - CSF Tools
- AC-3(3): Mandatory Access Control - CSF Tools
- AC-3(4): Discretionary Access Control - CSF Tools
- AC-3(15): Discretionary and Mandatory Access Control - CSF Tools
- AC-16(8): Association Techniques and Technologies - CSF Tools
- IR-4(9): Dynamic Response Capability - CSF Tools
- IR-4(12): Malicious Code and Forensic Analysis - CSF Tools
- IR-4(13): Behavior Analysis - CSF Tools
- Zero Trust Tenets:
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy—including the observable state of client identity, application/service, and the requesting asset—and may include other behavioral and environmental attributes.
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
Attribute-based access control refers to making access enforcement decisions based on a security attribute. This could be a static ID like a SID or a GUID, it could be a dynamically computed security attribute like a content category, or it could even be an externally stored attribute like a threat reputation. There are as many attributes as you can dream up, and as long as we can computationally define and reference them, we can make an attribute-based access enforcement decision. Machine learning and AI can be used to dynamically compute an attribute, at least most of the time.
Mandatory access controls are just that: Mandatory! These access controls must be checked and passed every time a particular access is requested or that access must be denied. Think of this as the no shirt, no shoes, no service sign at your local McDonald’s.
Discretionary access controls add a little bit of flavor to our access control cocktail. Using these controls, we can choose to enforce a more (or less) stringent set of access controls against access requests based on attributes of our choosing. For example, if someone shows up to the job site without proper safety equipment, we can set a policy to only allow sidewalk viewing access.
Putting Theory into Practice:
By now, you’re probably wondering, “What Attributes?”. It’s a fair question, thanks for asking! Files of any type on a computer system have several attributes, including date modified, owner, file size, etc. Executable files have even more attributes, including digital signatures, compilers, dependencies, etc.
Hash values and threat reputations are of particular interest to us. Hash values are a computed attribute created by math algorithms. Hashes allow us to identify a file or really any information you can imagine without keeping a complete copy, dramatically reducing the cost of intelligence sharing. Threat Reputations are a handy credit score for files, which we can use to approve or reject CPU and data loans access in our environment.
Trellix Threat Intelligence Exchange (TIE) allows organizations to track and associate these hash values and threat reputations for files observed in their environment. These attributes can be dynamically queried and/or published to the entire environment via the Data Exchange Layer (DXL) for use in access control decisions.
So where does TIE get these threat reputations? Surely, we’re not going to try to convince you we’ve seen every file there ever was; and aren’t the bad guys coming out with new threats every single day? That’s reasonable skepticism and proof you’re paying attention! There are several sources used to associate files with threat reputations:
- Trellix Global Threat Intelligence (GTI), an intelligence-sharing service available to all Trellix customers
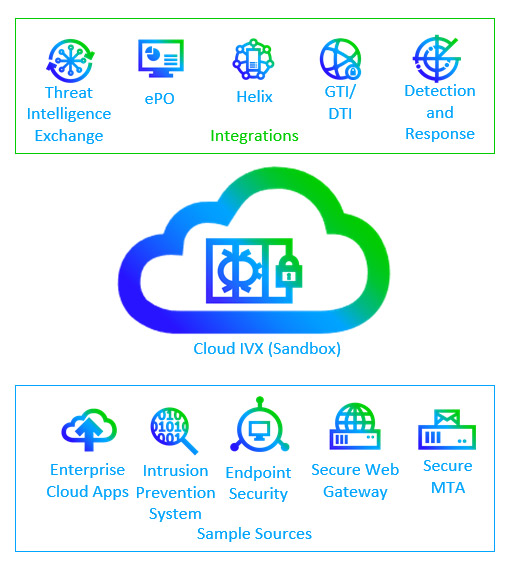
- Trellix Intelligent Sandbox (TIS, Formerly ATD) and Intelligent Virtual Execution (IVX) (More on this shortly, I drew a picture)
- Trellix Endpoint Security 10 (ENS) Adaptive Threat Prevention’s ML Protect (formerly RealProtect ) machine learning/AI malware analysis engine
- Skyhigh Web Gateway’s Gateway Antimalware Engine
- Imported STIX format Indicators of Compromise (IOCs)
- You and your expert opinions
To get a reputation for files we’ve never seen before, Trellix Intelligent Virtual Execution accepts potential malware submissions from endpoints, network detection and response tools, and enterprise collaboration apps such as Teams and SharePoint. These samples are put through a rigorous multi-step analysis, including static, dynamic, and machine learning/AI analysis. During the dynamic analysis phase, IVX attempts to deceive malicious files into executing in a well-monitored environment, enabling forensic and behavioral analysis. The results of this analysis are automatically made available to Threat Intelligence Exchange.
These network capabilities are great for stopping anything from landing on the endpoint, but what if a threat lands on your sales director’s laptop (they clicked on a phishing email attachment labeled Urgent Invoice)?
Endpoint Security 10’s Adaptive Threat Protection (ATP) module offers us continuous behavioral analysis during execution, hybrid local/cloud machine learning/AI analysis, the ability to submit files to IVX, the ability to submit to and receive threat reputations from TIE, and a handy dandy automatic moving target countermeasure called Dynamic Application Containment.
ML/AI and continuous behavioral analysis are automated dynamic response capabilities that allow us to ask the robot, “Hey, does this thing look like/act like malware? Answer in the form of a threat reputation.” Imagine that suddenly, a supply chain attack causes normally benign software to start doing some crazy new shenanigans that likely put it into the malware category. In that case, our AI countermeasure can update the local threat reputation and lock it down while also updating TIE, thereby alerting the entire environment that this file needs more attention. These decisions can be configured to take place automatically without human intervention. Humans can override these reputations, and we can adjust actions and sensitivity as appropriate.
Dynamic Application Control (DAC) is an automated dynamic response capability composed of a set of optional access controls we can apply preferentially based on our threat reputation attribute, including based on unknown threat reputations. This allows us to have one set of exploit prevention rules for processes we have assessed as most likely trustworthy (so far) and a second, additional, much stricter set of rules for processes we have assessed as unknown or possibly malicious. DAC can impose some relatively debilitating controls around potential malware, effectively and automatically moving the target file and operating system assets out of reach.
Here's all that on a kill chain because we just love drawing them:
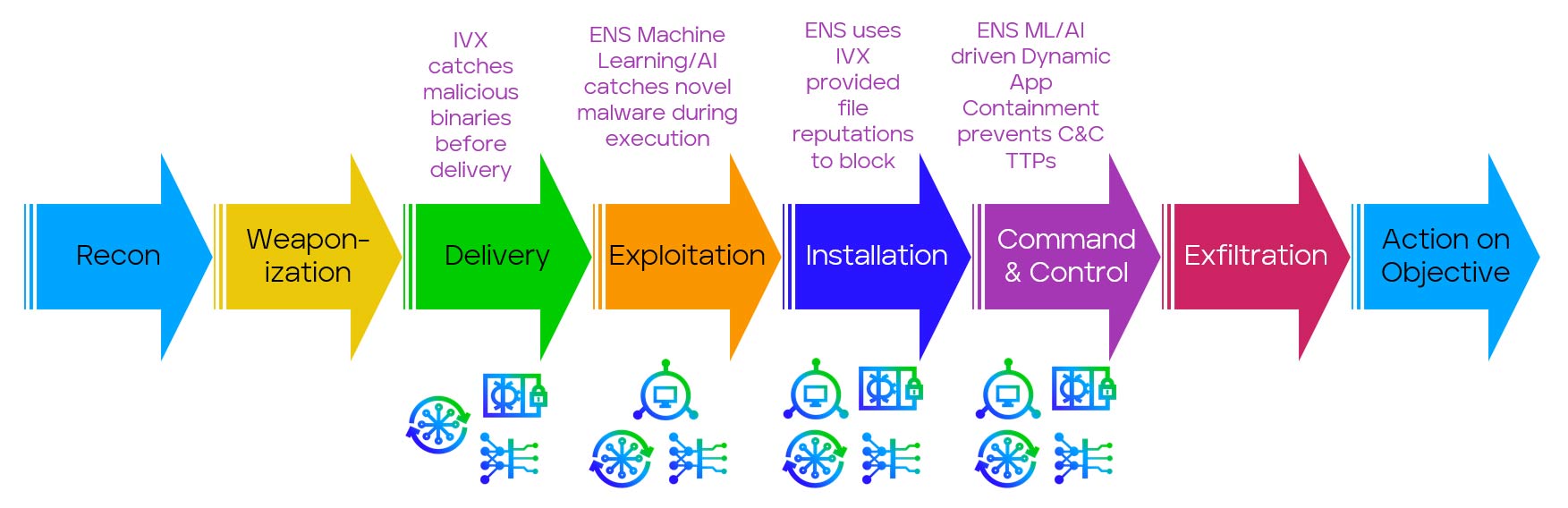
Automated Moving Target Defense:
With these components and configurations in place, the machines do the work for us! We’ve successfully flipped the script on our cyber-adversaries, making our own lives easier while we make theirs much harder. While we’ve shown in this deployment scenario how an automated moving target defense strategy can be enabled by using only a few of the Trellix XDR Platform’s controls, the full XDR Platform enables far more and far spicier techniques to be employed. In particular, Trellix HX can add endpoint forensics to the mix, Trellix’s NDR portfolio can catch and stop threats on the wire, and Helix can provide machine learning/AI and automate across your entire security operations practice.
If everything we’ve discussed here seems like a lot of work to get set up and configured properly, consider Trellix Professional Services. We offer various strategic and technical services that can help your team automate and operate your cyber defenses. Contact your Trellix account manager, or if you haven’t got one yet, let us know you’re interested. Mention you read this blog post to let the sales team know nerds rule.
Make sure you read this disclaimer after all that information:
This document and the information contained herein describe computer security research for educational purposes only and for the convenience of Trellix customers. This document contains information on Trellix products, services, and/or processes in development. All information provided here is subject to change without notice at Trellix’s sole discretion. Contact your Trellix representative for the latest forecast, schedule, specifications, and roadmaps.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
