Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Approaches to Defending Endpoints Before, During, and After Ransomware Attacks
By Trellix · August 17, 2023
This blog was written by Marcus Brownell
Endpoint Security and Ransomware
Comprehensive endpoint security is essential to ransomware detection and response: Stopping attacks at the endpoint ensures ransomware campaigns are thwarted before business disruption. This means optimizing endpoint controls before an attack, identifying and disrupting an attack that is underway, and critically, leveraging advanced forensics for root cause analysis after an attack to improve security posture and prevent attacks from reoccurring.Endpoints are under constant attack and security teams must work tirelessly to minimize impact by attackers. Highly impactful attacks, such as sophisticated multi-stage ransomware campaigns, continue to disrupt organizations of all sizes in all industries. Endpoints are key targets for attackers, allowing them to further access high-value assets that can cause significant damage to organizations. Stopping attacks at the endpoint ensures ransomware campaigns are thwarted before extortion and business disruption.
Security teams need visibility and control over their complex endpoint attack surface to keep their organizations resilient. Comprehensive endpoint security means having visibility and control of endpoints before, during, and after attacks occur.
Endpoint security has come a long way since the days of antivirus and prevention-only approaches. Endpoint Detection and Response (EDR) technologies filled a gap by increasing visibility of attacker activity in progress on endpoints during sophisticated and stealthy attacks.
Despite continuous improvements in advanced prevention and EDR technologies, security teams still struggle with managing the complexity of their endpoint attack surface, dealing with inefficient alert triage, and perhaps most troubling, reoccurring endpoint incidents.
Visibility and control before, during, and after an attack
What does it mean to have endpoint capabilities before, during, and after attacks and how does it feed into a lifecycle?
The following diagram shows phases common to security lifecycle frameworks (e.g., manage, protect, detect, investigate, respond) with respect to when an attack occurs: before, during, and after.
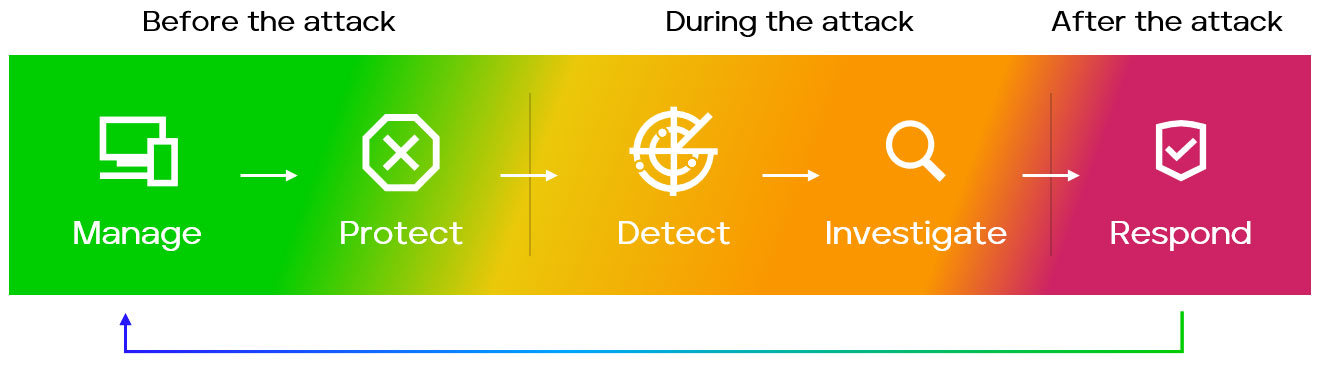
Recognizing the importance of each phase can help security teams identify where they may have gaps in their security strategy and where they should focus additional counter measures to reduce risk and cost posed by attacks on endpoints.
Before the attack – Manage and Protect
The least expensive time to address an attack is before it happens. It’s critical to be prepared before attacks occur. Reliable management and optimizing available protection capabilities on endpoints are essential to minimizing the risk and cost associated with investigating and recovering from attacks. Since every organization’s requirements and environments are unique, there is not a one-size-fits-all configuration that is appropriate everywhere. Optimizing protection before an attack occurs is a key way to minimize unnecessary alerts that can end up overwhelming security teams.
Manage: The endpoint attack surface is increasingly complex. Security teams need management platforms that provide visibility of managed and unmanaged endpoints as well as reliable policy management across cloud, on-prem, and hybrid environments. Heterogeneous operating environments with legacy systems or limited cloud access increase the challenge of deploying available protections to prevent attacks. Gaps in coverage can become entry points for attackers and lead to increased dwell time.
Protect: Given the sophistication of today’s threats, endpoint protection must leverage a broad range of protection technologies to detect and disrupt attacks. Signatures can be effective at stopping most malware before it executes (including malicious document files) but signatures are not enough. A broad protection stack including machine learning, exploit prevention, dynamic containment, automated remediation, for example are needed. Additionally, highly customizable prevention technologies can be critical for customers to have the visibility and control they need to block as many attacks as possible before they require attention from SOC analysts.
Optimizing protection: Too often following an incident, security teams learn that the incident would have been prevented if they would have enabled an available critical protection technology. Since security teams must constantly balance productivity with protection they often need guidance regarding relevant counter measures to address an organization’s risk profile. They also need visibility regarding which endpoints are not compliant with an organizations security baseline.
During the attack - Detect and Investigate
This is the phase that generally gets the most focus by security teams and EDR tools. If an attacker manages to bypass prevention technologies, it is essential for security teams to discover and disrupt it before it causes impact. Recognizing that an attack is underway and understanding the action to take can make the difference between a non-event and a catastrophic incident. EDR solutions provide key capabilities to help detect and investigate during an attack.
Detect: In addition to vendors leveraging threat intelligence for their analytic detections, security teams can act on threat intelligence when information about campaigns, indicators, techniques, tools, etc. are relevant to their organization. Filtering threat intelligence on campaigns that target countries or industries can help teams prioritize threat hunting activities and be more likely to uncover attacks that might be underway.
Investigate: Due to the deluge of endpoint alerts that analysts face every day, it can be impossible to properly triage and prioritize all of them. As a result, some alerts may be ignored. False positives, weak signals, and irrelevant telemetry all contribute to this challenge. EDR solutions should provide deep and granular visibility of endpoint activity but also be able to distill actionable information into key findings that answer questions a security analyst will have during an investigation.
After the attack - Respond
Once an attack is discovered, it is clearly critical to contain the attack and return to normal business operations as quickly as possible. However, returning to normal business operations without understanding the root cause can leave organizations exposed to being hit by ransomware again and again. Simply containing an endpoint, stopping suspicious processes, or restoring from backup, although important, are not enough.
Respond: Following an initial response that disrupts and attack, organizations can still be susceptible to repeated incidents if the root cause (like a gap in coverage or a misconfiguration) is not addressed. Security teams require advanced visibility and control to understand the scope of an incident and ensure proper remediation to avoid being victim to costly reoccurring attacks. Incident responders need to be able to collect targeted forensic data like suspicious files, browser history, command shell history, deleted file history, raw disk, and more to paint a more complete picture of the scope and root cause of an attack.
Trellix Endpoint Security is your foundation
Trellix Endpoint Security is foundational to organizations’ security because it provides security teams broad visibility and control before, during, and after attacks on endpoints. This helps minimize the cost and risk involved with protecting their systems and data that are foundational to their business.
Furthermore, as much value as the endpoint security platform provides on its own, it is also a critical pillar for strategic security initiatives like XDR. Trellix Endpoint Security is natively integrated in Trellix XDR and supports an easier XDR implementation and enhanced endpoint visibility and control into Security Operations.
Stay tuned for follow-up blogs where we examine ways that Trellix Endpoint Security can help organizations implement more comprehensive endpoint security.
Learn More
Learn more about how Trellix solutions can reduce their risk and cost through increasing visibility and control before, during, and after attacks.
Trellix Endpoint Security (ENS) – Prevention Sensors
Trellix EDR – Advanced Detection Sensors
Trellix Endpoint Forensics (HX) – Forensics Sensors
Trellix Application Control – Attack Surface Reduction Sensors
Trellix Threat Intelligence Exchange – Collaborative Threat Intelligence Ecosystem
Trellix Insights – Threat Intelligence Feed
Trellix Advanced Research Center – Threat Research Team
Trellix XDR – Correlate across all your vectors and tools, detect threats in minutes, and respond lightning-fast with AI-guided intelligence
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
