Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Cyber Tools and Foreign Policy: A False Flag Chinese “APT” and Nancy Pelosi’s Visit to Taiwan
By Anne An · September 29, 2022
Preface
U.S. House Speaker Nancy Pelosi’s visit to Taiwan led to an aftershock across the Taiwan Strait and through the Asia Pacific region. Immediately after Pelosi’s visit, China’s People’s Liberation Army carried out waves of intensive military drills near Taiwan. This military activity was accompanied by a false flag Chinese “APT27_Attack” hacktivist group claiming to be the well-known nation-state APT27 as it declared a cyberwar against Taiwan’s government and commercial organizations. APT27_Attack’s subsequent distributed denial of service (DDoS) attacks took down a number of Taiwanese government websites. Messages mocking Pelosi were plastered all over the island's popular convenience stores and train terminals. The cyber domain became a focal point of tensions between China and Taiwan alongside kinetic military actions.
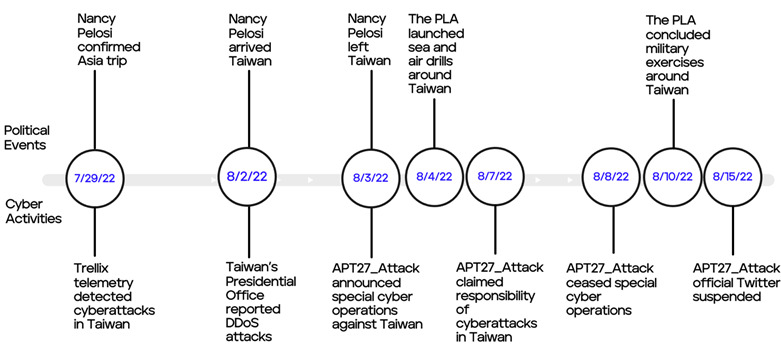
Operational timeline overview
The following graph illustrates a timeline of geopolitical events and corresponding cyber activity between July 29 and August 15, 2022.
New findings based on Trellix detections
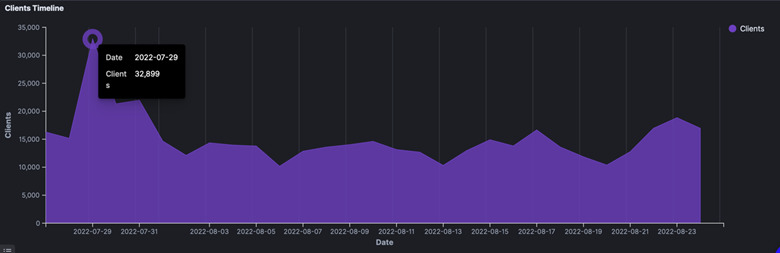
Based on Trellix telemetry detections, threat activities targeting the Taiwan government and commercial organizations are likely to have started days before Pelosi’s arrival on August 3, 2022. On July 29, 2022, Trellix telemetry data showed a spike in detections in Taiwan, with over 32,000 detections of suspicious activity (malware, vulnerability scanning, etc.) hitting the self-governed island in one day, compared to a typically daily range of 9,000 to 17,000 detections (figure 2). The spike caught our attention because a sudden increase in detections frequently indicates the presence of cyberattacks in the detected region.
We assess with moderate confidence that the increase in malicious activity detected in Taiwan may be related to active and passive scanning, as well as pre-operational activities, such as actively compromising IoT devices, testing malware or attack vectors prior increasing attack potency, and so on. It is also possible that cyberattacks were taking place almost a week before Pelosi’s arrival on the island, starting on the exact day Pelosi’s trip was confirmed, which triggered a spike in detections.
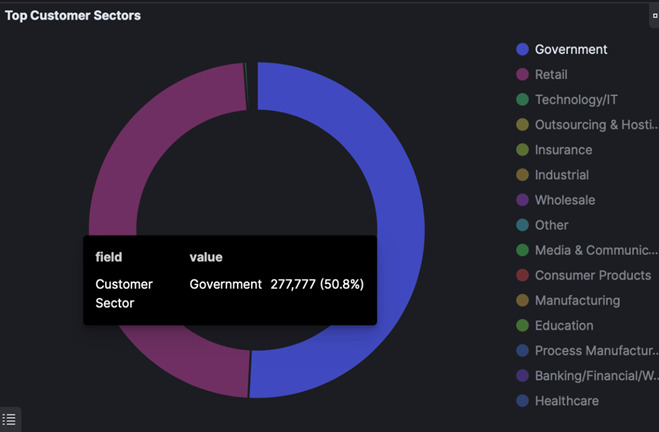
Trellix telemetry data revealed that between July 29 (five days before Pelosi’s arrival) and August 6, 2022 (two days after Pelosi’s departure), a significant portion of detections were directed at Taiwan’s government entities and retail stores (figure 3). A small percentage of malicious traffic also targeted the technology sector in Taiwan. During the same period, Taiwan news reporting confirmed that several government offices, train stations, and branches of convenience stores operated by Uni-President, Taiwan's largest food manufacturing and retail conglomerate, were targeted by hackers.1
APT27_Attack as APT27?
Though “APT27_Attack” claimed to be the nation-state threat actor APT27, we assess with moderate confidence that this APT27_Attack hacktivist group is unlikely the same as the well-known cyber espionage group APT27, also known as Emissary Panda. One reason is that APT27_Attack hackers exhibit different characteristics from APT27 operators. APT27 is a Chinese cyberespionage group targeting organizations across government, telecommunications, and financial services sectors globally. APT27 hackers, similar to other APT groups, have a history of hiding in plain sight to avoid being exposed and thus remain undetected in a target system for an extended period of time. As a result, APT27 members are unlikely to come forward and publicly claim responsibility for the hacking via social media platforms. Social media or public exposure could seriously jeopardize operational security and endanger existing or future cyberespionage activities. In essence, APT groups do not self-declare that they are APT groups.

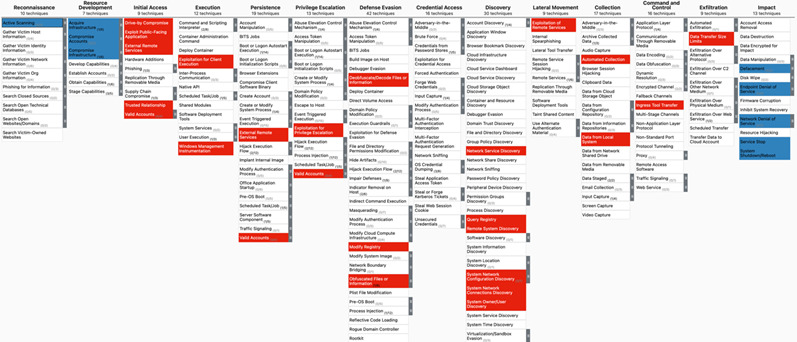
When using the MITRE ATT&CK framework to compare adversarial behavior, tactics, techniques, and procedures (TTPs) between the two threat groups, as indicated in the graph below, APT27_Attack (highlighted in blue) and APT27 (highlighted in red) exhibit significantly different attack patterns. Overlaps in adversarial behaviors and TTPs typically indicate a potential connection between threat actors. It suggests that the groups are likely closely aligned, share resources, and may operate for the same organization. In this case, the adversarial behavior and TTPs of APT27_Attack and APT27 do not intersect in any way. This supports our assessment that APT27_Attack is likely a distinct group separated from APT27.
From a technical standpoint, the top MD5 hashes detected in Trellix’s telemetry during the height of APT27_Attack’s cyberattacks in Taiwan from August 3 to August 8, 2022 do not show significant connections to attack techniques mapped to APT27. Trellix detections indicate that a great portion of malicious traffic detected in Taiwan during the same time period were associated with NBTscans, generic malware and droppers that were not specific to APT27.
The APT27_Attack hacktivist group also operates differently from APT27 and other typical APT groups in that it publicly discloses its targets, missions, and operations. After accomplishing its goals, APT27_Attack formally terminates operations. Under the same circumstances, APT27 operators may stay undetected on victims’ networks for long periods of time to maintain long-term persistence.
For APT27_Attack hackers, claiming to be APT27 may be strategic to intentionally trick the public into thinking that they are APT27. The public is likely more familiar with APT27. It is also an established cyberespionage group capable of deploying a variety of tools and tactics for its cyberespionage missions. By posing as APT27, APT27_Attack’s declaration of cyberattacks appear more real and credible, which would in turn incite more fear and chaos in Taiwan.
APT27_Attack as Honeker Union of China?
We assess with medium confidence that the APT27_Attack hacktivist group is likely a loosely connected group of hackers or script kiddies who share patriotic sentiments for China, similar to those who participated in the missions of the Chinese hacktivist group Honker Union of China (HUC) back in 2013. Based on its attack motivations, the APT27_Attack group likely consists of hackers either based in China or with close ties to China. It is not clear whether APT27_Attack group is affiliated with the Chinese government.
APT27_Attack hackers were likely motivated by news reporting by Chinese media that tends to have a strong nationalistic tone. China’s hacking community has a history of perceiving themselves as crusaders on a mission to fight perceived anti-China bias or sentiment in the world. For example, in 2012, HUC declared a cyber war on Japan over a territorial dispute involving islands in The East China Sea. Hackers affiliated with HUC defaced hundreds of Japanese government and commercial websites.2
There has been speculation that APT27_Attack is the reincarnation of HUC, which disbanded and rebranded itself in July 20223. However, on August 4, 2022, the official HUC account refuted accusations and involvement in hacking against Taiwan and subtly denounced recent APT27_Attack cyberattacks in Taiwan.
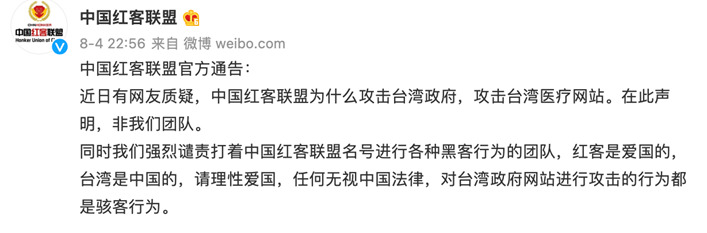
Translation of the screenshot above:
“The Honker Union of China’s official announcement:
Recently some Chinese netizens questioned why the HUC attacked the Taiwan government and healthcare websites. We hereby declare that [they] were not members of the HUC team.
At the same time, we firmly condemn those who carried out the attacks using the name of the HUC for the attacks. HUC hackers are patriots. Taiwan is a province of China. Please act patriotically and rationally. Any behavior that ignores Chinese laws and attacks Taiwan’s government websites is malicious hacking behavior.”
APT27_Attack operation timeline
August 2, 2022: The website of Taiwan’s presidential office reported that it was under cyberattack and was soon temporarily taken offline4. Taiwan news outlets reported that several Taiwanese government websites, including the Ministry of National Defense, the Ministry of Foreign Affairs, and the website of Taiwan Taoyuan International airport where Pelosi’s plane landed, had been attacked prior to Pelosi’s visit on August 3, 2022.5 However, Trellix detections spiked in late July prior to the start of APT27_Attack’s publicly reported operations.
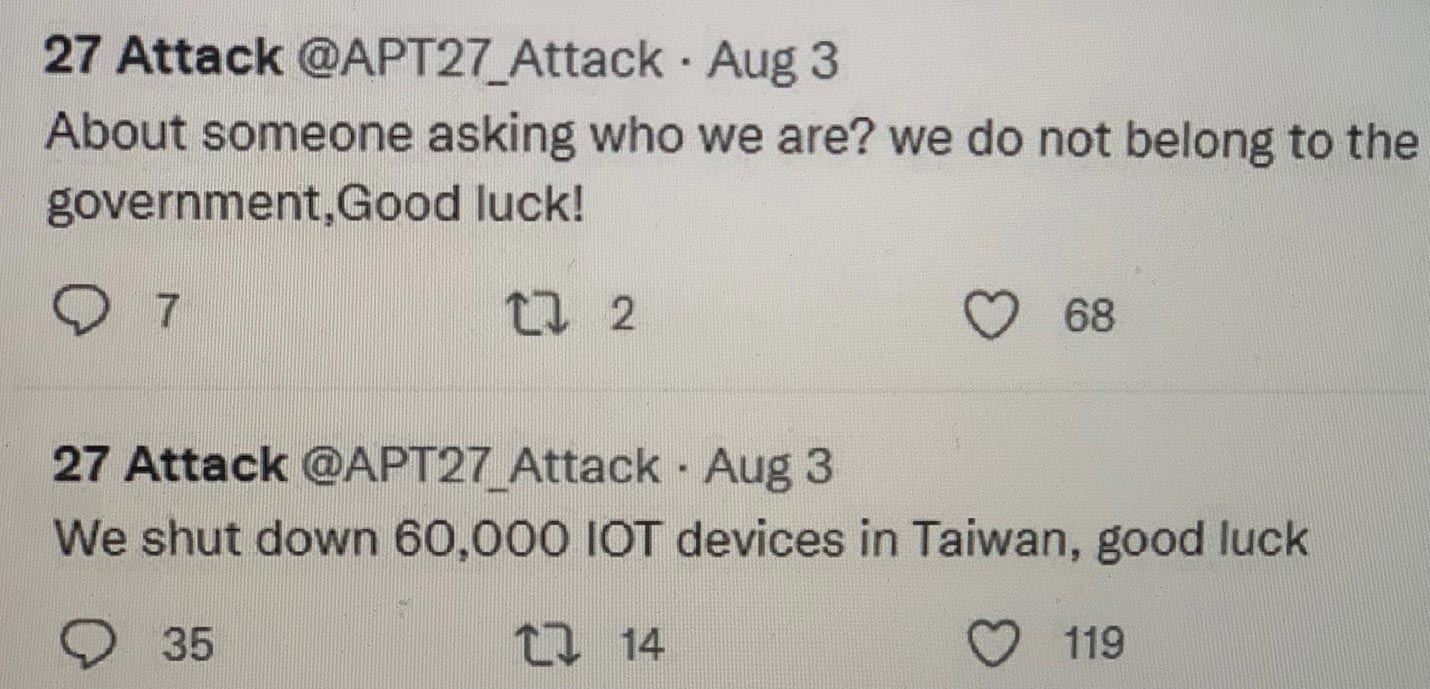
August 3, 2022: On the day of Pelosi’s visit, the Chinese hacker collective that calls themselves “APT27_Attack” (with Twitter handle @APT27_Attack) announced special cyber operations against Taiwan’s government services, infrastructure, and commercial organizations.6 On their official Twitter account, APT27_Attack self-proclaimed that they are a loosely connected hacktivist group with no ties to the Chinese government. The “APT27_Attack” hacktivists also claimed to be “APT27,” though they are likely a false flag and separate from the well-known nation-state threat group “APT27.” This hacker collective also claimed to have shut down 60,000 IoT devices in Taiwan (figure7).7
August 4, 2022: China’s People’s Liberation Army launched sea and air drills around Taiwan.8
Following APT27_Attack’s announcement, hacking was reported by Taiwan’s various railway systems and Uni-President, the island’s largest operator of convenience stores. Hackers defaced large billboard-type displays in a number of Taiwan railway stations.9 Hackers displayed messages on the billboard displays: “The old witch’s visit to Taiwan is a grave challenge to the sovereignty of the Chinese motherland; those who actively support (her visit) will face reprimand from the people of China;” and “Taiwanese and Chinese people are of the same race/ethnicity and share the same blood, and therefore they cannot be separated. great China will become one” (see figure 8).10 Messages were written in simplified Chinese characters, as opposed to the traditional characters commonly used in Taiwan.

On the same day, displays across Uni-President’s organization, were also defaced with anti-Pelosi messages: “War warmonger Pelosi get out of Taiwan.”11

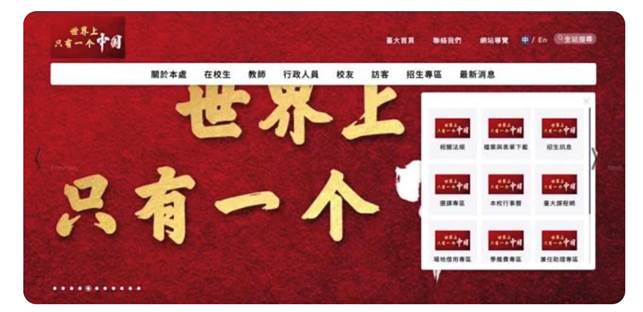
August 7, 2022: APT27_Attack hacktivist group claimed responsibility for a series of cyberattacks against Taiwan’s presidential office, the National Police Agency, Taiwan Power (Taipower) Company, and Taiwan Highway Administration, among others. The website of National Taiwan University was also defaced on the same day with pro-China remarks: “There is only one China in the world.”12
August 8, 2022: APT27_Attack made another claim that they gained control of over 200,000 Internet-connected devices in Taiwan, allowing them to potentially leverage these networks for more destructive or damaging cyberattacks. The group further threatened to leak government information and publicize zero-day vulnerabilities in Taiwan’s network devices/equipment.13 The same day APT27_Attack abruptly announced to temporarily cease their action if there was no further provocation from the Taiwanese government.
August 10, 2022: The PLA concluded military exercises around Taiwan.14
August 15, 2022: Twitter suspended APT27_Attack’s official Twitter for violating its terms of use by exposing private information.
Implications
The successful cyberattacks carried out by APT27_Attack against government websites, as well as convenience stores and train station displays have several implications. APT27_Attack demonstrated how cyberweapons can accompany kinetic military action as a useful instrument to protest against and influence foreign policy. One result of their effectiveness is South Korean president Yoon Suk-yeol declining to meet with Pelosi in the aftermath of cyberattack threats and China’s missile strike in six zones surrounding Taiwan.
Additionally, these successful cyberattacks carried out by APT27_Attack, despite their limited scale, may lead to more hacktivist cyberattacks in support of military action in future China-Taiwan crises. APT27_Attack’s cyber threat efforts effectively complemented China’s official military activity to stoke fear in Taiwan and other nations throughout the region. Furthermore, Chinese netizens praised APT27_Attack as national heroes, which could invite future copycats.
Conclusion
Hacktivists and other cyber-enabled threats have brought new twists to geopolitical tensions ranging from Russia’s invasion of Ukraine to the most recent political tensions in the Taiwan Strait. U.S. House Speaker Nancy Pelosi’s recent visit to Taiwan drew global attention and regional cyber threat activity to Taiwan. Trellix data suggests threat activities targeting the Taiwanese government and Taiwan’s commercial organizations likely began when Pelosi confirmed her trip to Asia, even several days before the publicly reported DDoS attacks against Taiwan’s presidential office and other government agencies.
While the hacktivist group APT27_Attack claimed responsibility for these DDoS attacks, this hacktivist group is unlikely the same group as the APT27 espionage group known as Emissary Panda. The group’s Twitter post claiming to be “APT27” is therefore a false flag, which successfully misled most major news agencies in their news reports. This incident involving Taiwan and Pelosi reveals how cyberattacks have turned into an effective tool for instilling national sentiment, retaliation, and intimidation.
1 https[:]//www.reuters.com/technology/7-11s-train-stations-cyber-attacks-plague-taiwan-over-pelosi-visit-2022-08-04/
2 https[:]//thenextweb.com/news/japanese-government-sites-allegedly-hacked-chinese-island-dispute-extends-online
3 https[:]//weibo.com/chinesehongker
4 https[:]//tw.news.yahoo.com/總統府官網遭境外d-do-s攻擊-流量暴增-200-倍-122259329.html
5 https[:]//tw.news.yahoo.com/裴洛西訪台前總統府等網站遇襲-專家-中駭客所為-012736529.html;
6 https[:]//www.nytimes.com/2022/08/02/world/asia/taiwan-cyberattack-pelosi-visit.html
7 https[:]//www.ctwant.com/article/199251
8 https[:]//www.reuters.com/world/asia-pacific/chinese-military-begins-drills-around-taiwan-state-media-2022-08-04/
9 https[:]//tw.news.yahoo.com/裴洛西訪台-總統府-超商-台鐵看板全遭駭-揭台灣2大弱點-104722493.html
10 https[:]//tw.news.yahoo.com/裴洛西訪台-總統府-超商-台鐵看板全遭駭-揭台灣2大弱點-104722493.html
11 https[:]//tw.news.yahoo.com/裴洛西訪台-總統府-超商-台鐵看板全遭駭-揭台灣2大弱點-104722493.html
12 https[:]//tw.news.yahoo.com/台大教務處網站也被駭-世界上只有-個中國-狂蓋版-131440326.html
13 https[:]//tw.news.yahoo.com/apt27再現身-恐嚇-握有台20萬聯網設備-062910654.html
14 https[:]//www.reuters.com/world/asia-pacific/china-extends-military-drills-around-taiwan-after-pelosi-visit-2022-08-10/
This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers. Trellix conducts research in accordance with its Vulnerability Reasonable Disclosure Policy. Any attempt to recreate part or all of the activities described is solely at the user’s risk, and neither Trellix nor its affiliates will bear any responsibility or liability.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
