Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
From Click to Compromise: Unveiling the Sophisticated Attack of DoNot APT Group on Southern European Government Entities
By Aniket Choukde, Aparna Aripirala, Alisha Kadam, Akhil Reddy, Pham Duy Phuc and Alex Lanstein · July 8, 2025
Introduction
The DoNot APT group, also identified by various security vendors as APT-C-35, Mint Tempest, Origami Elephant, SECTOR02, and Viceroy Tiger, has been active since at least 2016, and has been attributed by several vendors to have links to India. The global cybersecurity landscape is continually challenged by state-sponsored threat actors conducting espionage operations. The DoNot APT group (also known as APT-C-35), is believed to operate with a focus on South Asian geopolitical interests. This threat group typically targets government entities, foreign ministries, defense organizations, and NGOs especially those in South Asia and Europe. DoNot APT is known for using custom-built Windows malware, including backdoors like YTY and GEdit, often delivered through spear-phishing emails or malicious documents. Their operations are marked by persistent surveillance, data exfiltration, and long-term access, suggesting a strong cyber espionage motive. This report provides an analysis of a recent campaign orchestrated by the DoNot APT group.
Trellix Advanced Research Center's ongoing hunting efforts have uncovered a sophisticated campaign attributed to the DoNot APT group targeting a European foreign affairs ministry highlighting the evolving tactics of the group. The attackers impersonated European defense officials mentioning their visit to Bangladesh and lured their targets to click on a malicious Google Drive link. This delivered a malicious RAR archive, ultimately deploying malware consistent with the group's known toolset. This incident underscores the group's persistent focus on governmental and diplomatic entities and their adaptability in using common cloud services for initial infection.
The Trellix Advanced Research Center discovered this campaign by identifying the initial email chain, which was then blocked from customer inboxes via security signatures. This crucial starting point allowed us to further uncover the Tactics, Techniques, and Procedures (TTPs) and modus operandi (MO) of the campaign through correlation with existing threat intelligence. Other security organizations and threat hunting groups have also reported similar DoNot APT group activities, utilizing different initial infection methods.
Attack summary: A multi-stage intrusion
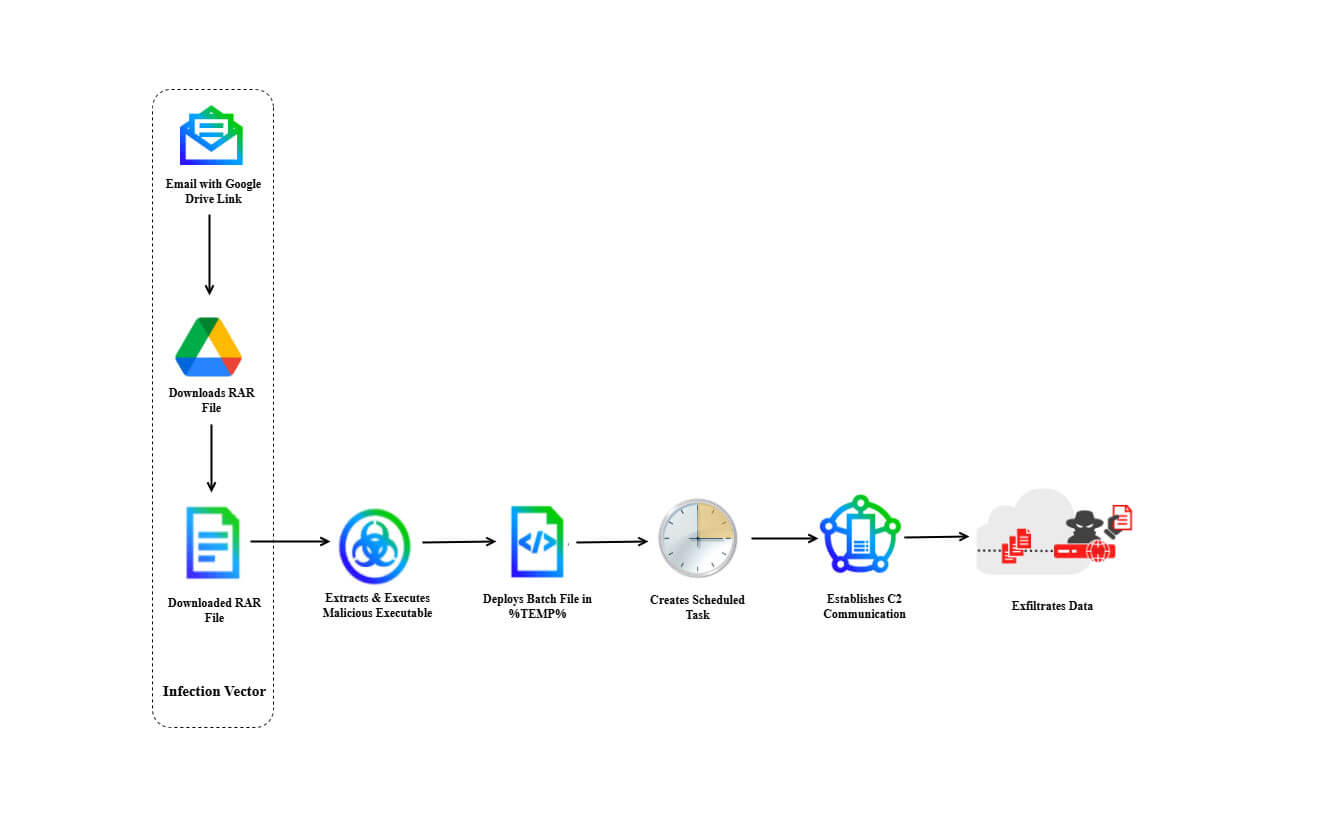
The core of the attack involved a multi-stage infection chain designed to establish a foothold within the target's network and exfiltrate sensitive information. Here’s a breakdown of the incident:
- Attack vector: Spear-phishing email originating from a Gmail address (int.dte.afd.1@gmail[.]com) impersonating official correspondence, with a subject line referencing diplomatic activities.
- Target: A European government entity within the diplomatic sector.
- Delivery method: The email contained a Google Drive link (drive[.]usercontent[.]google[.]com/download?id=1t-fBZBgVtW_S81qYGn9loubWZwIXjI_T) pointing to a malicious RAR archive named SyClrLtr.rar.
- Payload and persistence: The infection chain involved the user execution of notflog.exe from the RAR archive, which then deployed a batch file (djkggosj.bat) in the %TEMP% directory. Persistence was achieved via a scheduled task named "PerformTaskMaintain," configured to run every 10 minutes, ensuring continued communication with the attackers' command and control (C2) server.
- Malware implicated: The telemetry and analysis of the payload associated this attack with "LoptikMod" malware, reportedly used exclusively by DoNot APT since 2018.
Deconstructing the attack chain
The attack unfolded in a series of calculated steps:
-
Initial lure: The victim receives a carefully crafted spear-phishing email, impersonating defense officials and referencing a legitimate-sounding event to build trust.
The email leveraged diplomatic themes related to defense attaché coordination between Italy and Bangladesh. While the exact body content was not gathered in the findings, the subject line “Italian Defence Attaché Visit to Dhaka, Bangladesh” suggests a lure designed to appear as legitimate diplomatic correspondence that would reasonably contain document attachments or links. The email used HTML formatting with UTF-8 encoding to properly display special characters like “é” in “Attaché,” demonstrating attention to detail to increase legitimacy.
Malicious download: Clicking on the embedded Google Drive link (drive[.]usercontent[.]google[.]com/download?id=1t-fBZBgVtW_S81qYGn9loubWZwIXjI_T) downloads the SyClrLtr.rar archive. The archive is protected with a password and the password to extract the archive is provided in the mail itself.
The extracted executable (notflog.exe) mimics a PDF document by displaying a PDF icon, tricking users into believing it’s a safe document and prompting them to open it.
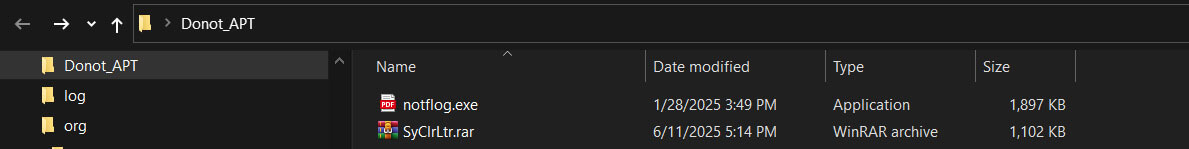
Figure 2: notflog.exe with PDF document icon
The file metadata of the executable contains information associated with a game program and is digitally signed by "Ebo Sky Tech Inc."
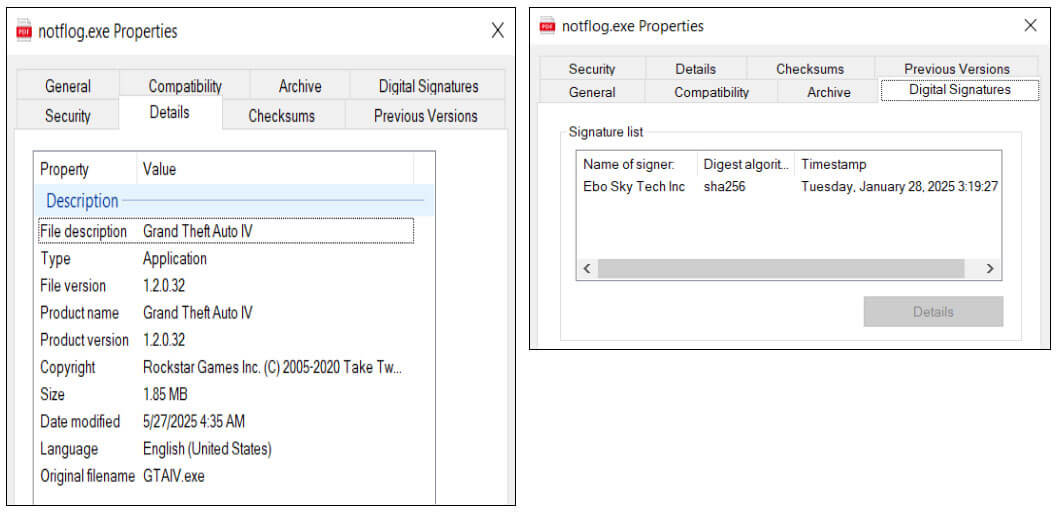
Figure 3: The embedded executable filename corresponds to a legitimate game program digitally signed by "Ebo Sky Tech Inc."
Static analysis of the malware executable also reveals the presence of the string "Loptik" within the strings which is significant because it is identified as being characteristic of the "LoptikMod" malware. This malware is associated exclusively with the DoNot APT group. Other identified string patterns also match previous DoNot APT campaigns, including the use of similar scheduled tasks (sfs.bat and djkffosj.bat) for persistence. Subsequently, based on ThreatRay code-based analysis, out of 653 functions, there were 590 benign, and 30% of the combined malicious and unknown functions (which totals 63) is 19 malicious functions overlapped with other LoptikMod variants.This identification helped us to attribute the malware to this specific threat actor.
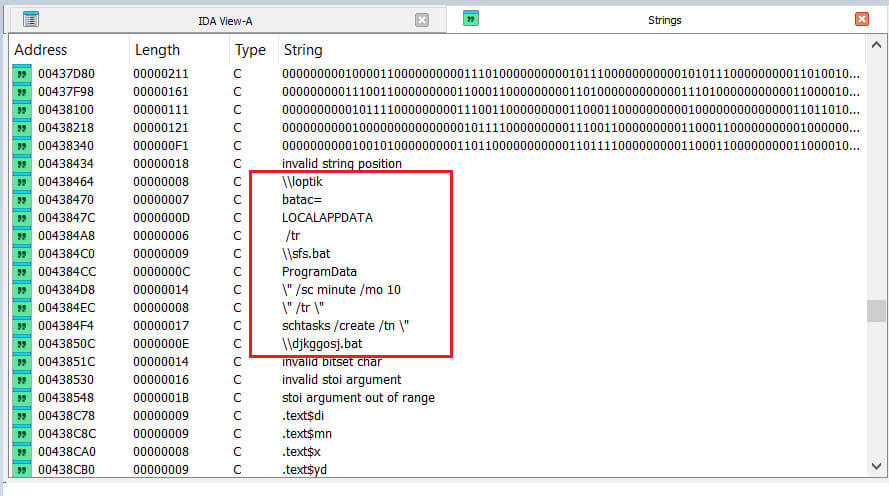
Figure 4: Identifying "Loptik" in Executable Strings Characteristic of DoNot APT's Remote Access Trojan
Further analysis of the binary also illustrates the use of binary strings used by the malware to decode or restore other meaningful strings within the malware. The analysis reveals that the malware uses binary representations of ASCII characters. These strings serve as decryption keys to restore other strings, such as API names. This technique is a form of obfuscation to hinder static analysis and to make it harder to understand the malware's functionality. By encoding strings in binary, the malware hides its true actions until runtime, when these strings are decoded and used.
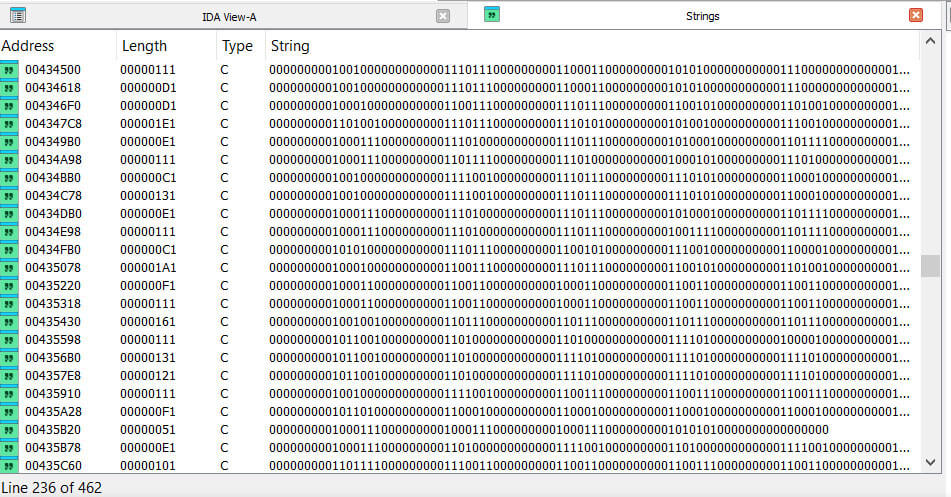
Figure 5: Binary Encoded Strings Used for Decryption in LoptikMod Malware
These binary strings, when decoded into ASCII characters, reveal the actual actions the malware is designed to perform, showcasing the malware's technique of encoding important strings in the binary.
ASCII representation of the binary strings embedded within the malware.
Scheduled Task - PerformTaskMaintain
- MicorsoftVelocity
- schtasks /create /tn
- /sc minute /mo
C2 Server Domain - Totalservices[.]info
HTTPS POST Request - WxporesjaTexopManor/ptomekasresdkolerts
Persistence Directory - %localappdata%
- FROX
Payload DLL - Socker.dll
This approach is a way for malware authors to hide or obfuscate their code, making it harder for security analysts to quickly understand the malware's purpose by simply looking at the raw binary file. By decoding these strings, we can see the specific tasks the malware schedules for persistence and the server it tries to contact, both of which are crucial pieces of information for understanding the malware's operation and impact.

Figure 6: Decoded ASCII Strings Revealing Malware Artifacts - Scheduled Tasks and C2 Communications.
Static analysis of the binary data also indicates that few of its sections are packed, which suggests that the malware employs selective obfuscation. This means the attacker compressed or encrypted only specific, crucial parts of the code, rather than the entire binary. This makes it harder for analysts to immediately understand the malware's full functionality or identify key malicious routines by simply looking at the raw code. They would need to unpack or decrypt those specific sections to gain a clear understanding. This method is a common tactic to evade detection and prolong analysis time. Such targeted packing forces researchers to invest more resources in reverse engineering to fully reveal the malware's true intent and capabilities. Ultimately, this sophisticated approach highlights the evolving efforts of adversaries to complicate security investigations.
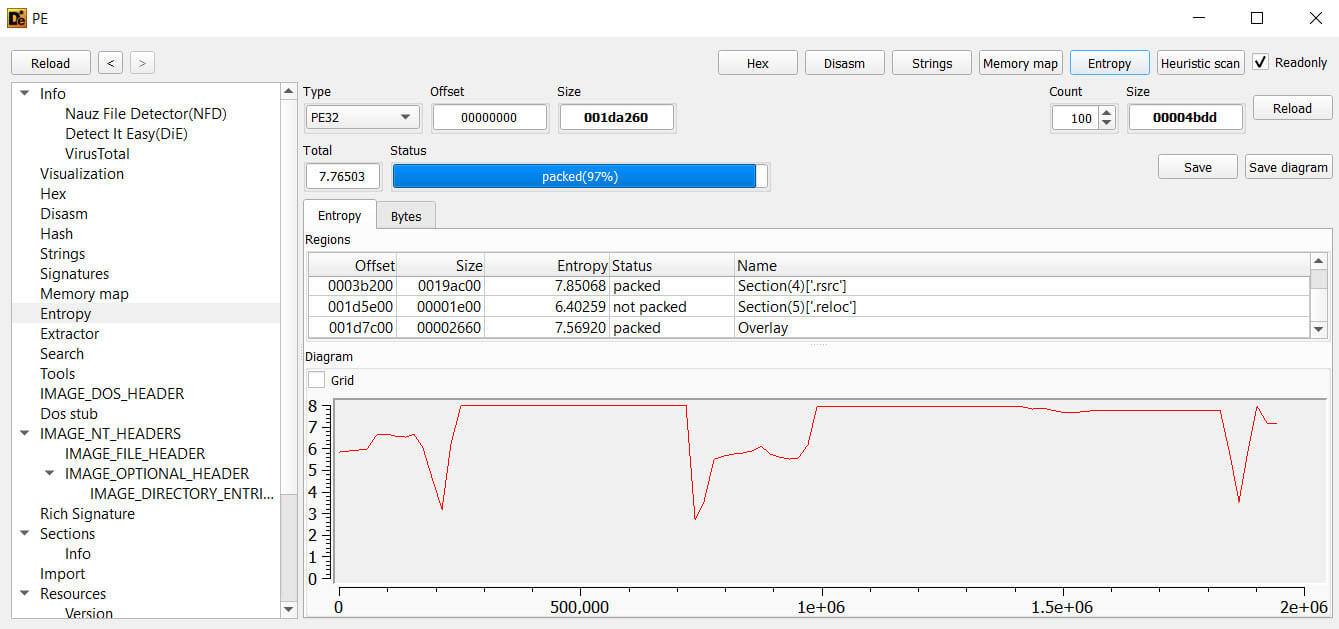
Figure 7: Selective Obfuscation via Section Packing in Malware Binary.
The file has less number of imports and the APIs required for the functionality of malware are loaded at runtime. Malware authors sometimes minimize the number of listed imports. This makes it harder for static analysis tools to quickly understand what the malware does just by looking at its imports. A low number of imports can make the file appear less suspicious at a glance.
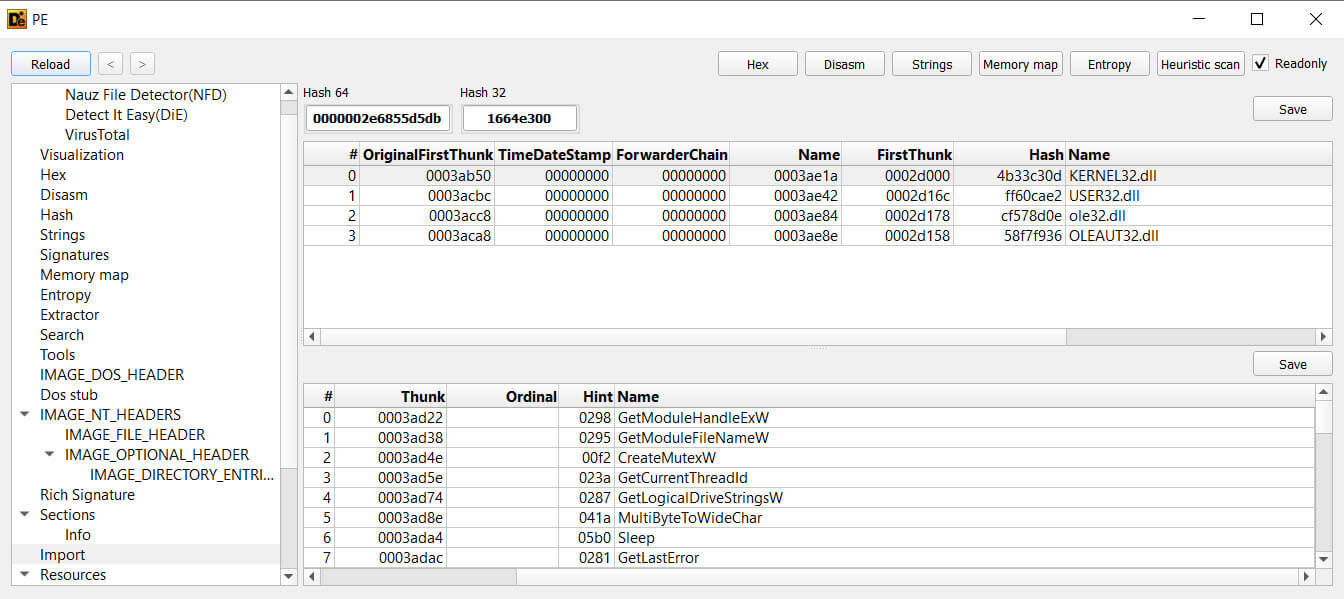
Figure 8: Minimal Import Table - API Obfuscation
Instead of directly importing APIs, malware can load them dynamically at runtime. This is done using functions like `LoadLibrary` (to load a DLL) and `GetProcAddress` (to retrieve the address of a specific function within that DLL).
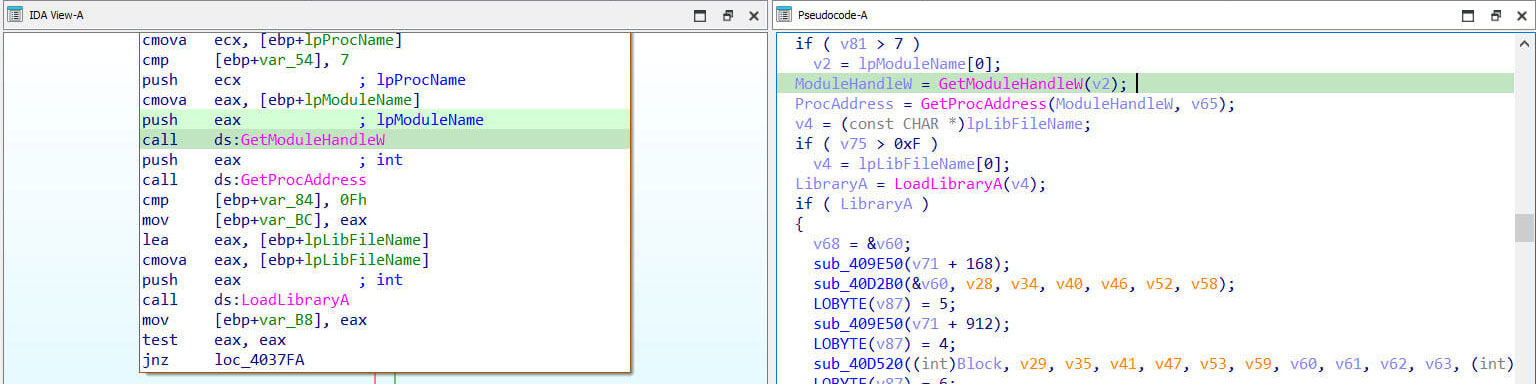
Figure 9: Import Address Table Evasion via Runtime API Lookup
Loading APIs at runtime means that these function calls are not visible in the static import table of the executable. This further hinders static analysis. Dynamic API loading adds an extra layer of obfuscation.
Key modules that have been loaded by malware are described below.
DLL name Description wininet.dll Provides high-level functions for accessing the internet (HTTP, FTP) used by browsers and applications. advapi32.dll Provides access to advanced Windows functions like the Windows Registry, service control manager, and security APIs. winhttp.dll Provides low-level access to HTTP protocols for sending/receiving HTTP requests. urlmon.dll Handles URLs and protocols for downloading and linking content, used by Internet Explorer and other apps. ws2_32.dll Provides the core WinSock (TCP/IP) networking API used by nearly all network-enabled applications.
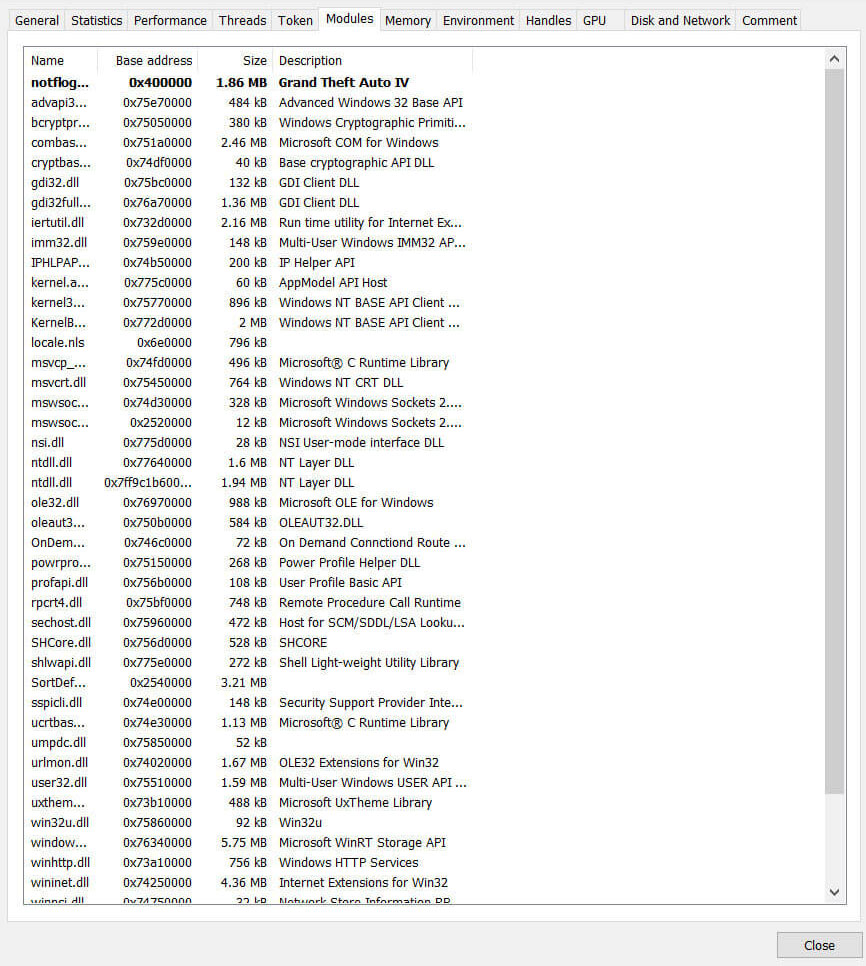
Figure 10: Modules loaded by the executable at runtime
Execution and deployment: Upon extraction and execution of notflog.exe, the payload creates a mutex with name “08808” to ensure that only one instance of the malware is active on the compromised system, preventing conflicts or interference with its operations.
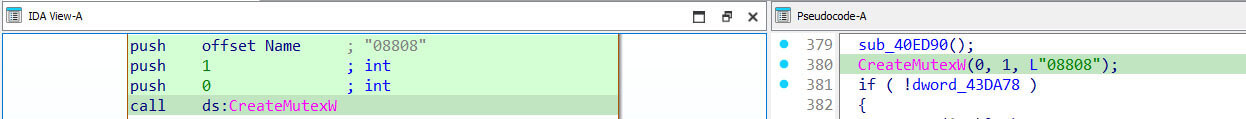
Figure 11: Mutex Creation for Single Instance Control.
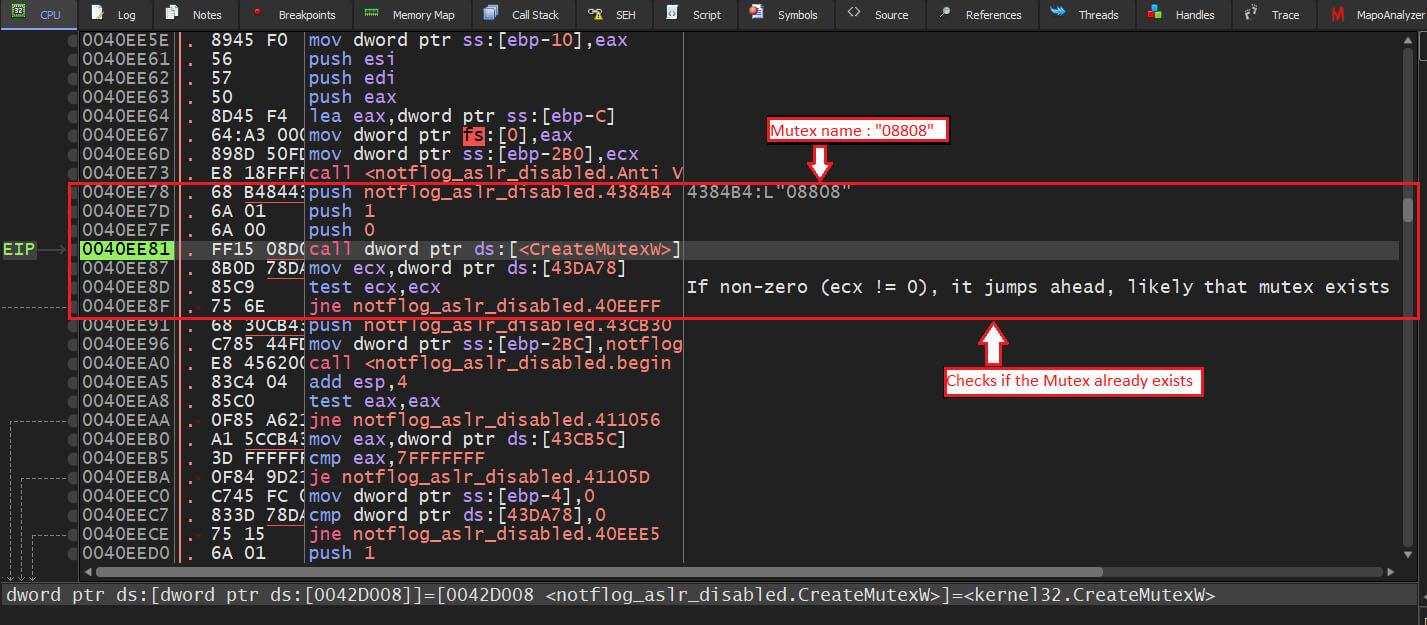
Figure 12: Malware Mutex Check for Instance and Infection Status.
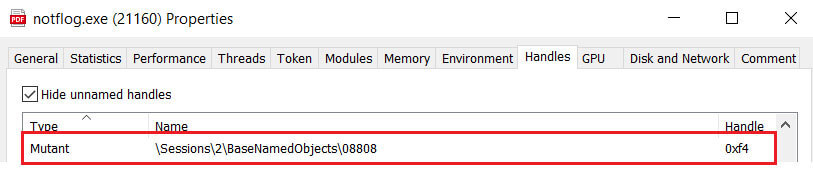
Figure 13: Malware Mutex Object Creation.
The malware employs anti-VM techniques, specifically the "IN" assembly instruction, to hinder execution in virtual environments and evade analysis.
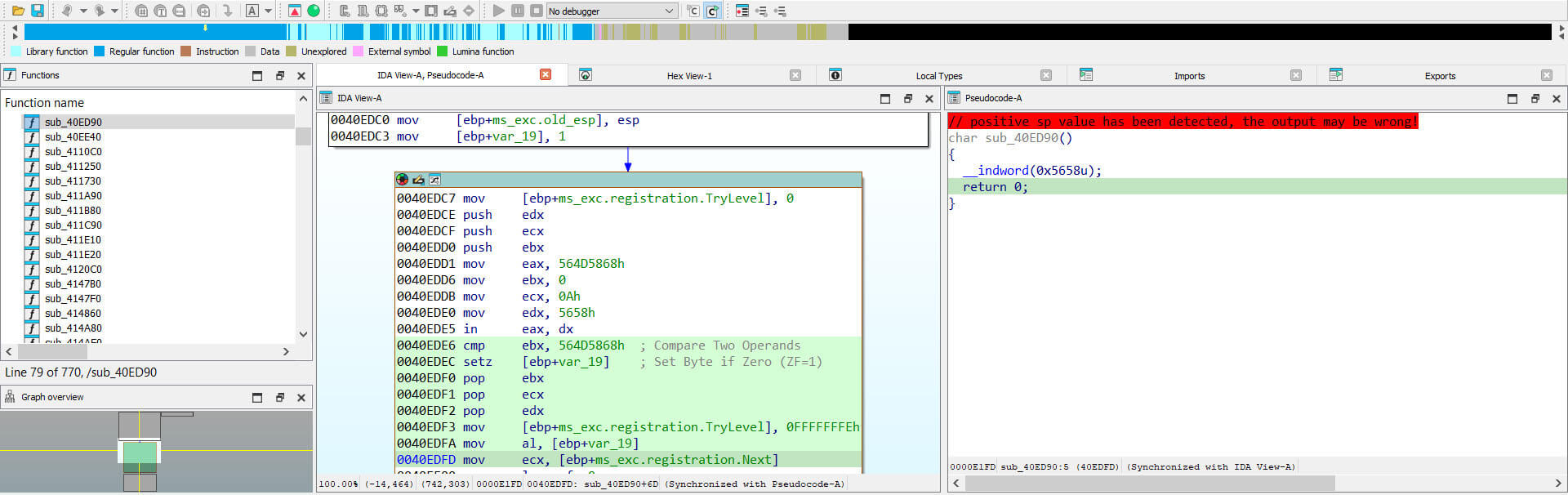
Figure 14: Anti-VM Check (Virtualization/Sandbox Evasion)
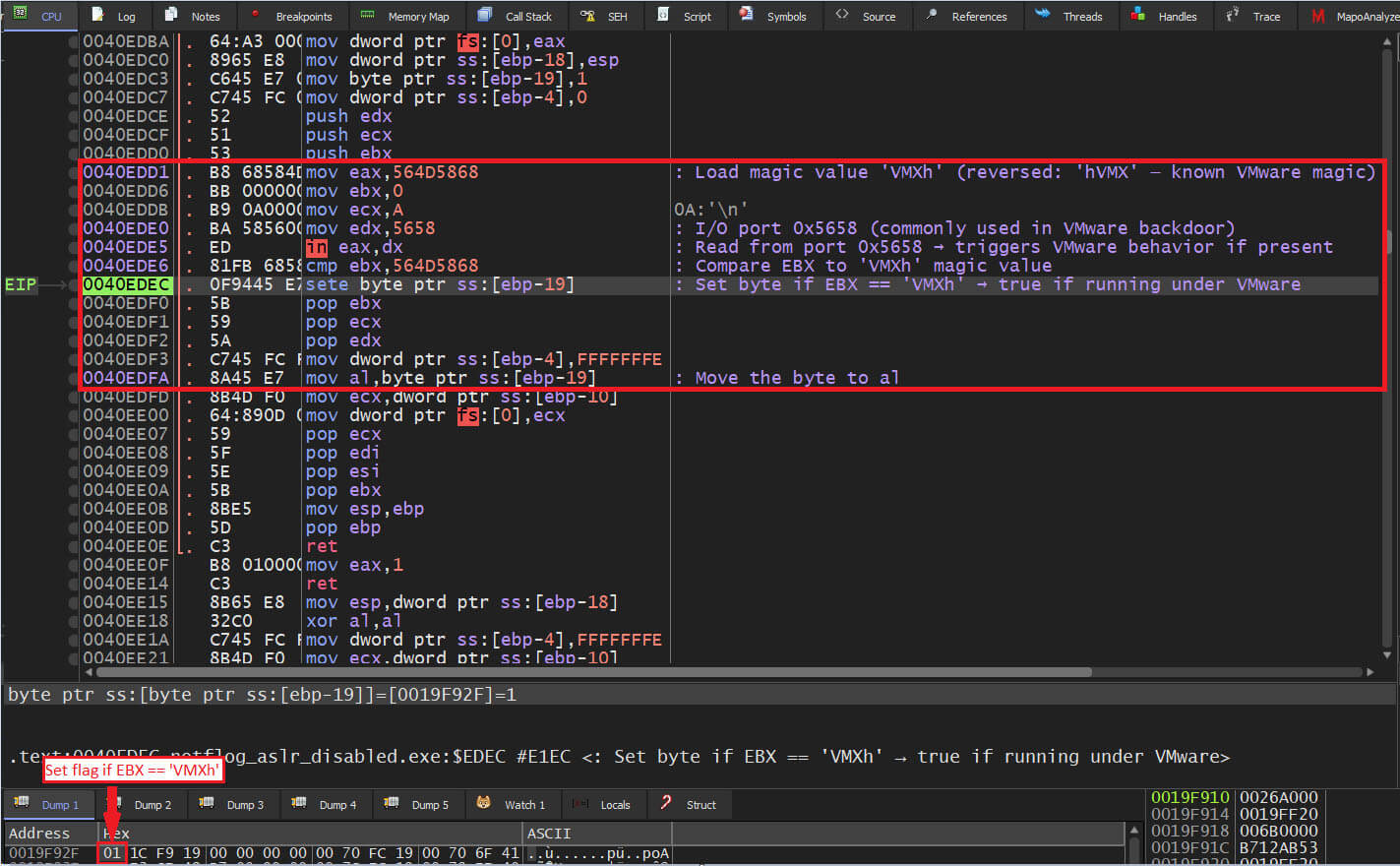
Figure 15: VM/Sandbox evasion capabilities using x86 “IN” instruction
Initially, the sample generates the "%LocalAppdata%\\TEMP\\FROX\\" folder and drops "djkggosj.bat" into that location. This script likely handles the next stage of the infection.
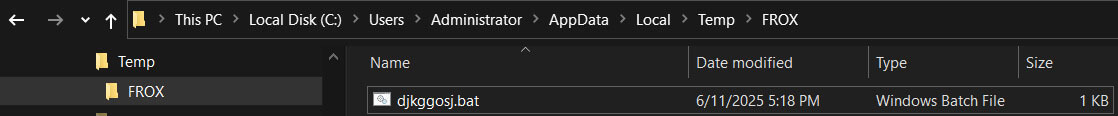
Figure 16: Temporary folder and .bat file creation for next stage infection.
Establishing persistence: The batch script or the initial executable creates a scheduled task named "PerformTaskMaintain." This task is set to run every 10 minutes, ensuring the malware remains active and can re-establish connections even if interrupted.
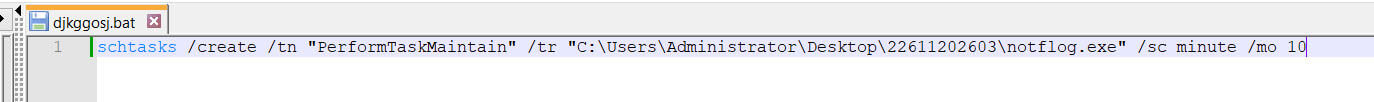
Figure 17: To ensure its continued operation on the compromised system even after reboots, the malware establishes persistence using schtasks.
The bat file is launched via the WinExec API and subsequently erased. This is a common tactic used by malware authors to evade forensic analysis and detection. Removing the file makes it more difficult for investigators to reconstruct the infection chain and understand the malware's actions.
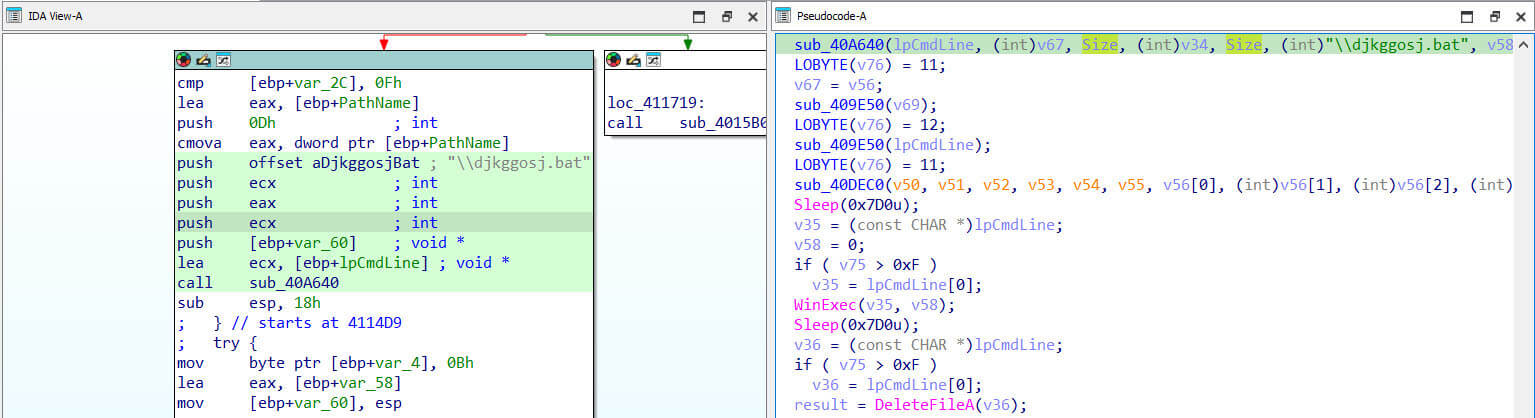
Figure 18: Batch File Execution and Deletion - Evasion of Forensic Analysis
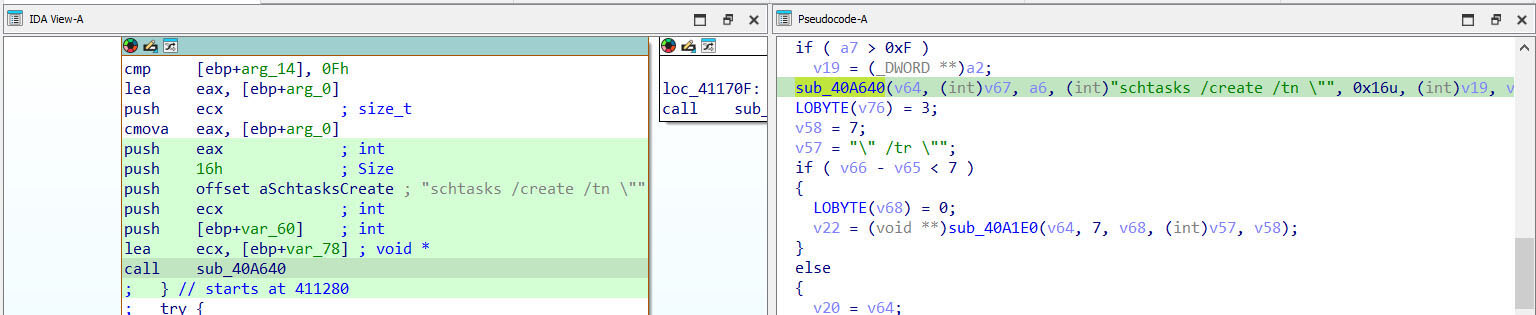
Figure 19: Creating Persistence via Scheduled Task
Command and control (C2) communication: The malware gathers system details, including the CPU model, operating system name and build, username, hostname, CPU ProcessorID, and a list of installed software.
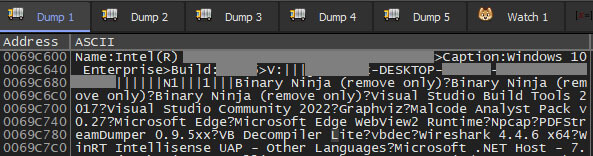
Figure 20: System Information Discovery - Data Collection by Malware.
The malware encrypts the gathered data using AES and then encodes it with Base64. This encoded data is appended to the 'batac=' parameter and sent via an HTTP POST request to 'hxxps://totalservices[.]info/WxporesjaTexopManor/ptomekasresdkolerts'
The malware then attempts to establish communication with the command and control (C2) server located at totalservices[.]info, which resolves to the IP address 64[.]52[.]80[.]252. This communication uses HTTPS, and the malware sends POST requests to the C2 server.
![Figure 21: C2 Communication - HTTPS POST to totalservices[.]info (64[.]52[.]80[.]252) - Mimicking Legitimate Services](/en-us/img/newsroom/stories/from-click-to-compromise-unveiling-the-sophisticated-attack-21.jpg)
Figure 21: C2 Communication - HTTPS POST to totalservices[.]info (64[.]52[.]80[.]252) - Mimicking Legitimate Services
The command and control domain (totalservices[.]info) follows the actor’s typical pattern of using legitimate-sounding service domains.
Once the connection is established, the malware can receive further commands, download additional modules, and exfiltrate sensitive data from the compromised system to likely target MFA credentials and diplomatic communications.
However, during our analysis of this malware, the C2 server appeared to be inactive. This made it challenging to observe the full range of commands the malware might receive or the extent of data it intended to exfiltrate. The inactive state of the C2 server at the time of analysis could mean that the attackers have temporarily disabled it, switched to a different server, or the infrastructure is no longer functional.
Based on the C2 server's response, the malware determines whether to download a follow-on payload, 'socker.dll'. Prior to this determination, the malware collects and exfiltrates system information such as username, hostname, and ProcessorID.
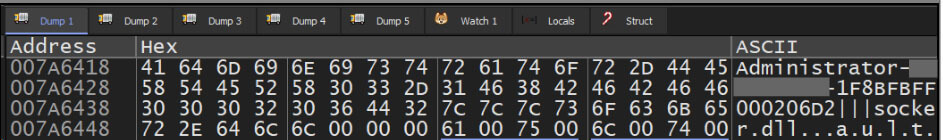
Figure 22: Victim Identification Data Collection (Username, Hostname, ProcessorID).
This payload is encrypted, combined with a victim ID (derived from username, hostname, and ProcessorID), and sent in the 'data' field of a POST request to : 'hxxps://totalservices[.]info/WxporesjaTexopManor/vrptpvabkokamekastra/N1/SA'.
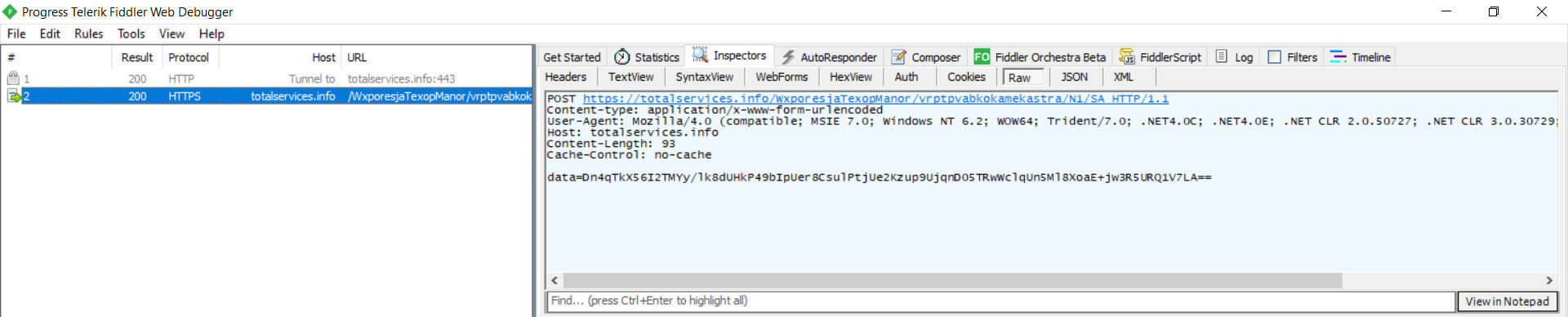
Figure 23: Data Exfiltration via Encrypted POST Request to C2 Server
Following the download of the payload, the malicious actor saves the dynamic link library, "socker.dll," to the location "%LocalAppdata%\\moshtmlclip\\socker.dll."
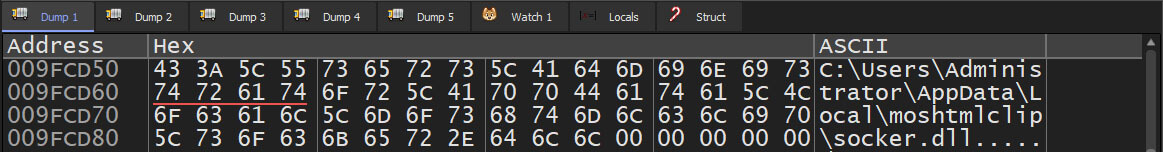
Figure 24: Destination Path for 'socker.dll' Delivery
Subsequently, another batch file, named "sfs.bat," is dropped into the "%LocalAppdata%\\Temp\\FROX\\" directory.
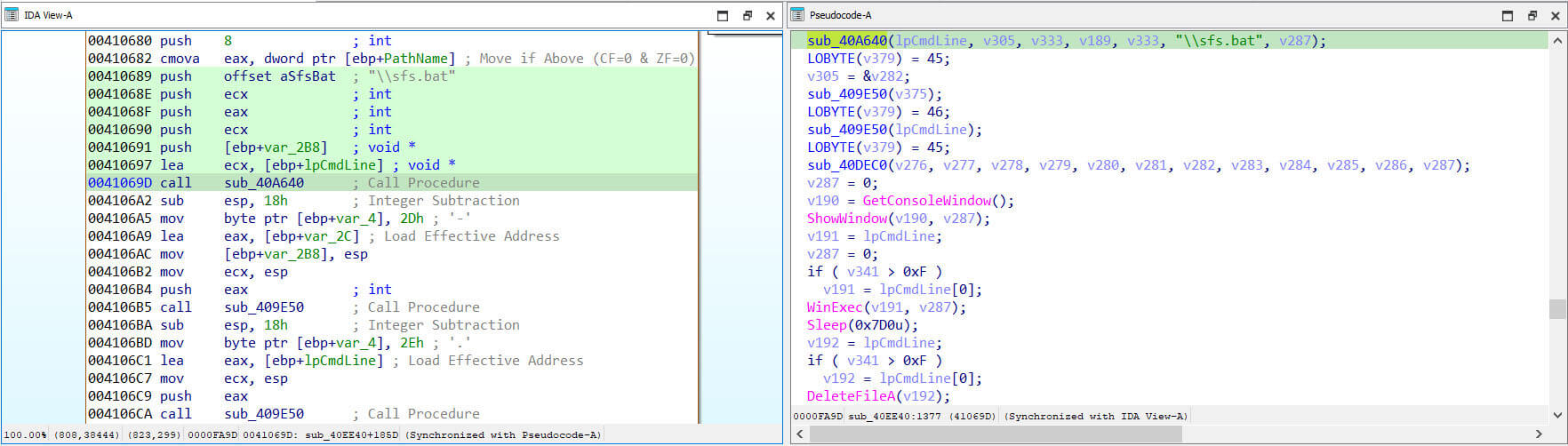
Figure 25: Staging of "sfs.bat" for Scheduled Task Setup
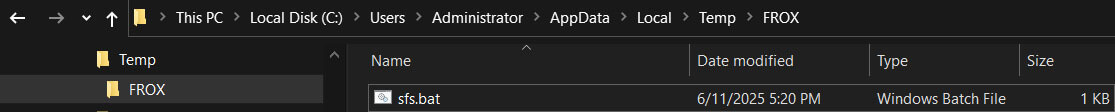
Figure 26: "sfs.bat" Batch File Drop Location
This batch file is designed to create a scheduled task named "MicorsoftVelocity." The purpose of this scheduled task is to ensure the execution of "socker.dll," specifically triggering the export function "?ejjwed@@YAHXZ." This sequence of actions ensures the persistence and subsequent activation of the downloaded payload on the compromised system.
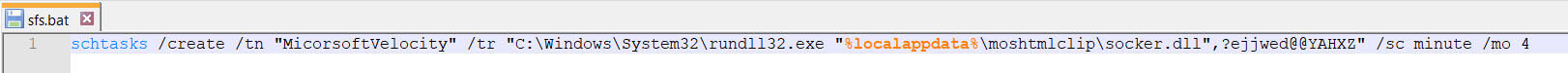
Figure 27: 'MicorsoftVelocity' scheduled task - Execution of 'socker.dll' export function '?ejjwed@@YAHXZ'.
As "socker.dll" was not obtained during analysis, a detailed examination of its loading behavior and subsequent loading functions are currently not possible. Due to this unavailability and lack of a captured sample, the investigation into how it loads and operates is presently limited.
Unmasking the culprit: DoNot APT (APT-C-35)
The DoNot APT group is a persistent cyber-espionage threat, active since at least 2016, targeting government, military, and diplomatic entities primarily in South Asia, but with increasing reach to other regions.
They employ sophisticated malware frameworks like "YTY" and use various infection methods, including spear-phishing and malicious archives, demonstrating adaptability in their tactics.
The recent targeting of a European foreign affairs ministry highlights their expanding scope and persistent interest in gathering sensitive information, underscoring the need for heightened vigilance and robust cybersecurity measures.
European diplomatic interests in the crosshairs
Trellix Advanced Research Center's proactive threat hunting efforts highlighted a significant development which has been observed with the targeting of a European foreign affairs ministry by the DoNot APT group. While historically focused on South Asia, this incident targeting South Asian embassies in Europe, indicates a clear expansion of their interests towards European diplomatic communications and intelligence. These operations underscore DoNot APT's persistent and broadening efforts to gather sensitive political, military, and economic information, a threat that Trellix is actively tracking and analyzing through its advanced intelligence initiatives.
MITRE ATT&CK TTPs and Indicators of Compromise:
This campaign showcases several Tactics, Techniques, and Procedures (TTPs) commonly associated with APT operations, mapped to the MITRE ATT&CK® framework:
| Tactic | Technique | ATT&CK ID | Evidence |
| Initial Access | Phishing: Spearphishing Link | T1566.002 | Email URL: drive[.]usercontent.google[.]com/download?id=1t-fBZBgVtW_S81qYGn9loubWZwIXjI_T |
| Execution | User Execution: Malicious File | T1204.002 | Victim opens SyClrLtr.rar → runs notflog.exe |
| Execution | Command and Scripting Interpreter: Windows Command Shell | T1059.003 | Executes Djkggosj.bat, sfs.bat |
| Persistence | Scheduled Task/Job: Scheduled Task | T1053.005 | Creates scheduled tasks: “PerformTaskMaintain” “MicorsoftVelocity” |
| Defense Evasion | Virtualization/Sandbox Evasion: System Checks | T1497.001 | “IN” x86 assembly instruction used for evading virtual environment |
| Defense Evasion | Obfuscated Files or Information: Encrypted/Encoded File | T1027.013 | Encoded ASCII strings in file Notflog.exe |
| Command and Control | Application Layer Protocol: Web Protocols | T1071.001 | C2 communication: totalservices[.]info |
| Discovery | System Information Discovery | T1082 | Collecting username, hostname, and ProcessorID etc. |
| Discovery | File and Directory Discovery | T1083 | Search for %localappdata% in user environment |
| Exfiltration | Exfiltration Over C2 Channel | T1041 | HTTPS POST request: hxxps://totalservices[.]info/WxporesjaTexopManor/vrptpvabkokamekastra/N1/SA'. |
Key Indicators of Compromise (IoCs) from this campaign include:
| Indicator Type | Value |
| Email Sender Address | int[.]dte[.]afd[.]1@gmail[.]com |
| Email Subject | Italian Defence Attaché Visit to Dhaka, Bangladesh |
| URL – stage‑0 | drive.usercontent.google[.]com/download?id=1t-fBZBgVtW_S81qYGn9loubWZwIXjI_T |
| URL – RAR file | SyClrLtr.rar |
| SyClrLtr.rar (SHA256) | 5317f22c60a4e08c4caa28bc84f653b1902fa082d2d1d7fcf2cd0ce1d29798d6 |
| Initial Executable | notflog.exe |
| notflog.exe (SHA256) | 4d036e0a517774ba8bd31df522a8d9e327202548a5753e5de068190582758680 |
| C2 Domain | totalservices[.]info |
| C2 IP Address | 64[.]52[.]80[.]252 |
| Scheduled Task Name | PerformTaskMaintain, MicorsoftVelocity |
Note: While these IoCs were reported in this specific campaign, public corroboration for the hashes on platforms like VirusTotal or the C2 domain in widely indexed threat feeds was not available at the time of this analysis. The malware name "LoptikMod" and specific file names like notflog.exe and djkggosj.bat are also not broadly documented in public threat intelligence regarding DoNot APT.
Strategic implications
Attacks targeting foreign ministries and diplomatic entities are classic espionage operations. The goal is to gain illicit access to sensitive state communications, policy documents, negotiation strategies, and intelligence reports. For an actor like DoNot APT, such information can provide significant strategic advantages to their sponsors. The use of a trusted platform like Google Drive for initial malware delivery also highlights the attackers' efforts to bypass initial security filters.
Defending against DoNot APT: Detection and mitigation
Organizations, especially government and diplomatic entities, should consider the following measures:
- Enhanced email security: Implement robust email filtering solutions to detect and block spear-phishing attempts. Train employees to identify suspicious emails, especially those containing links or attachments, even if they appear to come from known or official sources.
- Network traffic analysis: Monitor network traffic for unusual outbound connections, especially to known malicious domains/IPs or those not typically associated with your organization's activities. Look for beaconing patterns consistent with C2 communication.
- Endpoint detection and response (EDR): Deploy EDR solutions to monitor endpoint activity for suspicious processes, file modifications (especially in %TEMP%), and the creation of scheduled tasks.
- Specifically, hunt for scheduled tasks with unusual names or frequent execution intervals (e.g., "PerformTaskMaintain" running every 10 minutes).
- Application whitelisting and script control: Restrict the execution of unauthorized applications and scripts (e.g., PowerShell, batch files) where possible.
- Cloud service monitoring: While challenging, monitor or restrict downloads from personal or untrusted cloud storage links if feasible within your organization's policy.
- IoC blocking: Block the known IoCs (domains, IPs) associated with this and other DoNot APT campaigns at your firewall and proxy levels.
- Regular patching: Keep operating systems and applications, particularly Microsoft Office, updated to prevent exploitation of known vulnerabilities.
- Threat intelligence sharing: Participate in threat intelligence sharing communities to stay informed about the latest TTPs and IoCs from groups like DoNot APT.
Trellix product detection:
| Product | Coverage |
| Trellix Endpoint Security (HX) |
|
| Trellix ENS |
|
| Trellix EDR |
|
| Trellix Network Security Trellix VX Trellix Cloud MVX Trellix Malware Analysis Trellix Email Security Trellix Detection As A Service Trellix NX |
|
Conclusion:
The DoNot APT group remains an active and evolving threat, particularly to governmental and diplomatic organizations in South Asia and, increasingly, their interests in other regions like Europe. Their use of common platforms like Google Drive for malware delivery, combined with their established multi-stage infection tactics and custom malware, underscores the need for a defense-in-depth security posture. Vigilance, robust security controls, and employee awareness are crucial in mitigating the risk posed by such sophisticated state-sponsored actors.
Trellix offers a robust and integrated security solution designed to protect various aspects of an organization's digital environment. It covers endpoints, networks, data, email, cloud, and security operations with different security technologies and features. By integrating AI, real-time intelligence, behavioral analysis, and cloud-based detection, Trellix ensures that its security platform remains adaptable and resilient in the face of evolving cyber threats. The continuous learning and dynamic threat response capabilities make Trellix a proactive solution, helping organizations stay ahead of emerging challenges in the ever-changing cybersecurity landscape.
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
