Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Managing Risk During the CrowdStrike Global Tech Outage
By Mo Cashman & Trellix Advanced Research Center · July 19, 2024 (Updated: July 25, 2024)
How it Happened
A defective content update provided by cybersecurity firm CrowdStrike caused Microsoft Windows systems to crash, disrupting airline travel, healthcare, government services and many other critical industries and organizations globally. This blog is focused on what to do now and how Trellix can keep you safe during this crisis.
Need Help to Recover?
CrowdStrike published steps to recover and we recommend you follow those procedures: CrowdStrike Issue Landing Page.
Accessing Safe Mode on Encrypted Systems:
For impacted systems using Trellix Encryption Software please refer to the following knowledge article: Accessing Safe Mode when using Trellix Encryption Software
For customers using Bitlocker:
- BitLocker recovery in Microsoft Azure
- BitLocker recovery in Microsoft environments using SCCM
- BitLocker recovery in Microsoft environments using Active Directory and GPOs
- BitLocker recovery in Microsoft environments using Ivanti Endpoint Manager
Additionally, you can leverage Trellix Endpoint Forensics to search and verify the location of defect files or malicious files. Trellix Forensics provides an enterprise search capability by file hash and verifies the Crowdstrike .sys files are in the proper "C:\WINDOWS\SYSTEM32\DRIVERS\CROWDSTRIKE\" directory.
If you are a Trellix customer, please refer to the Trellix Thrive support portal for more info. If you are not a Trellix customer, Trellix Support is available to assist all impacted companies. Refer to our Customer Support information for contact information by country.
NEW! Threat and Protections Update - Day 7 - July 25, 2024
Note that all indicators of compromise (IoCs) present in the update can be found within Trellix Insights.
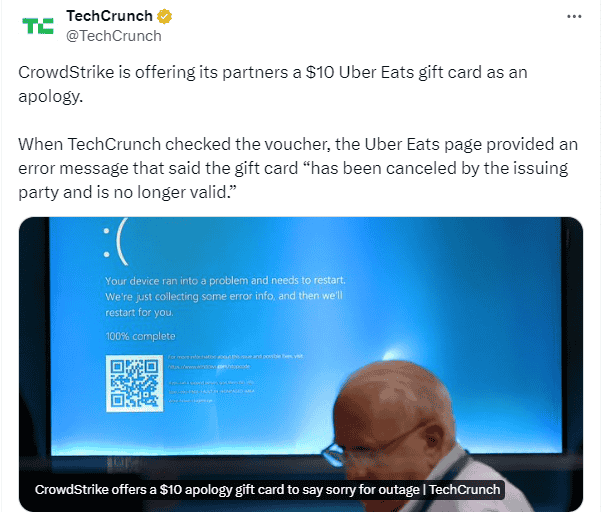
Gift Card Fraud
Since the news broke that CrowdStrike offered apology gift cards to those who are helping out impacted people, actors have been impersonating CrowdStrike to likely scam gift cards and/or personal information. Domains with the keywords “CrowdStrike” and “gift card” have been registered. This shows, once again, that actors are quick to jump on events and adapt their attack plan accordingly. Below is a post on X from TechCrunch that mentioned the gift cards and not long after this, the first domains related to CrowdStrike and gift cards appeared online.
Infostealers Mainly Found in Adapted Campaigns
Since the start of the outage, CrowdStrike themed malware has surfaced. In the past week, information stealers have been the main payloads. Below, the observed stealers are listed in order of discovery by the security community, along with a brief summary.
- RemcosRAT (July 19, 2024)
- Named “CrowdStrike-hotfix.zip”, which contains the HijackLoader that subsequently loads RecmosRAT
- The Spanish notes within the ZIP archive potentially indicate a target demographic of Spanish speaking victims in Latin America
- Daolpu (July 22, 2024)
- A macro within a Word document, named “New_Recovery_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.docm” was sent to victims. Once executed, the malware collects credentials such as login data and cookies stored in Chrome, Edge, and Mozilla browsers
- Daolpu stealer also targets Cốc Cốc, a web browser primarily used in Vietnam, possibly indicating the malware's origin
- The name is “Upload” in reverse
- Connecio (July 23, 2024)
- Connecio Stealer is a Python-based information stealer delivered via a malicious ZIP file
- The ZIP file uses the filename CrowdStrike Falcon.zipin an attempt to masquerade as a Falcon update. The file CrowdStrike Falcon.exe with the ZIP file is a self-extracting RAR that contains and executes a Python-compiled executable, containing the Connecio infostealer
- Lumma (July 23,2024)
- Lumma Stealer was observed in a phishing campaign impersonating CrowdStrike
- The domain “crowdstrike-office365[.]com” (registered on July 23, 2024) was used to deliver malicious ZIP and RAR files containing a Microsoft Installer (MSI), which ultimately executes the (packed with CypherIt) Lumma Stealer
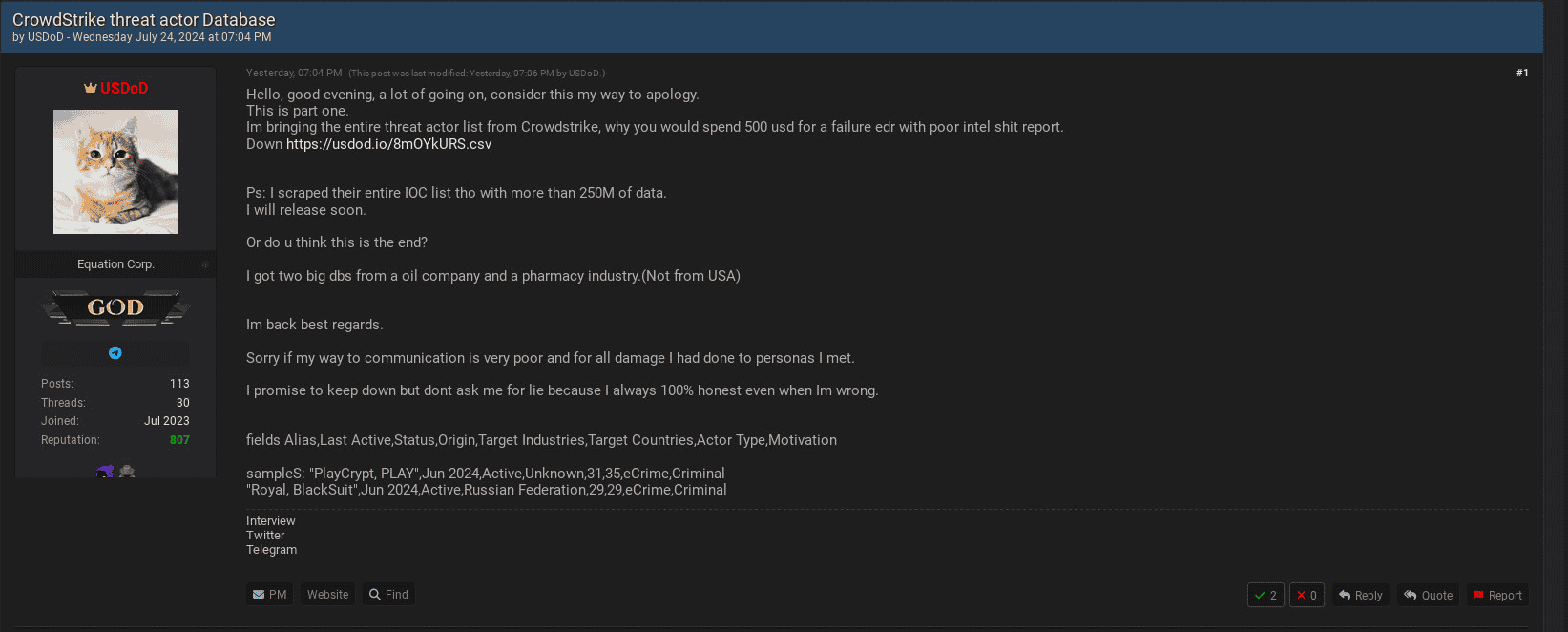
Crowdstrike Threat Actor Information Allegedly Being Leaked and Offered in the Underground
A well-known underground threat actor, USDoD, published a post on Breachforums offering the entire CrowdStrike threat actor library. USDoD provided a preview of the data, which Trellix ARC reviewed for authenticity. We can confirm that the data is structured as a threat actor library, including industry synonyms, activities, and countries of origin. The reviewed snippet did not contain any sensitive or customer data. USDoD also claimed to have additional data on indicators of compromise (IoC) and databases from an oil company and a pharmaceutical company. However, Trellix was unable to verify the authenticity of the IoCs or the databases.
Threat and Protections Update - Day 5 - July 23, 2024
Global Telemetry Overview of Malicious Detections Linked to Crowdstrike Outage
Today, we have included a Trellix Insights malicious detection overview of the threats related to the CrowdStrike outage that the Advanced Research Center has discovered. All of the indicators are processed through Trellix Insights 24/7, making them easily consumable for our customers. However, everyone can access the same IOCs from our Insights Preview page that is updated daily.
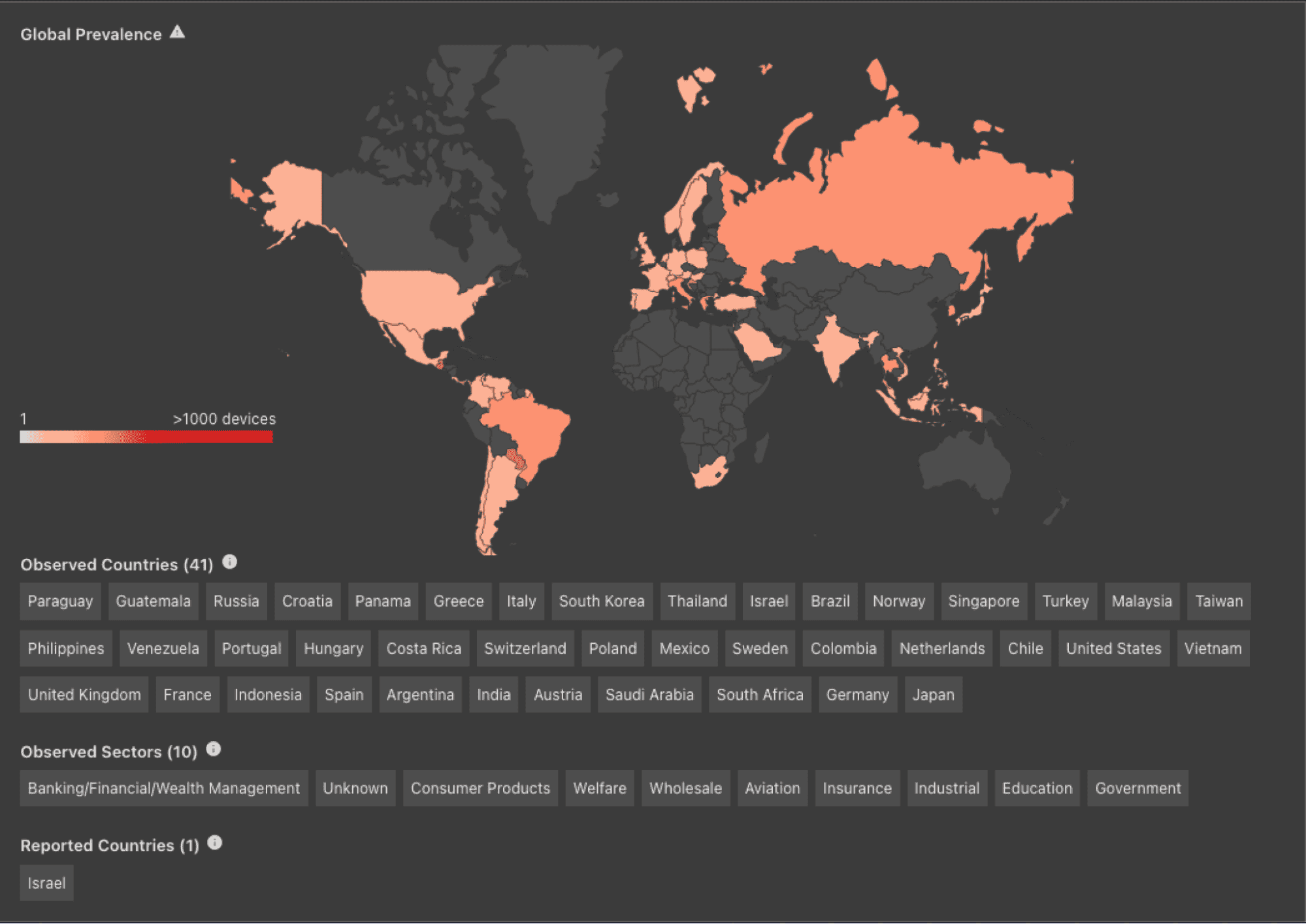
Trellix Insights malicious detection overview
Stopping Wipers
This telemetry overview includes detections from the Handala group wiper, as outlined in the day three threat update. This wiper targeted organizations in Israel. The Trellix email appliance detected and subsequently blocked the attempted attacks, helping to ensure the safety of these organizations.
NEW! Threat and Protections Update - Day 4 - July 22, 2024
Social Media Misinformation
Posts on social media talk about the “planned complete stop of the globe” by the World Economic Forum. This is misinformation and is spread to gather clicks on the embedded image in the post, as seen in the screenshot below.
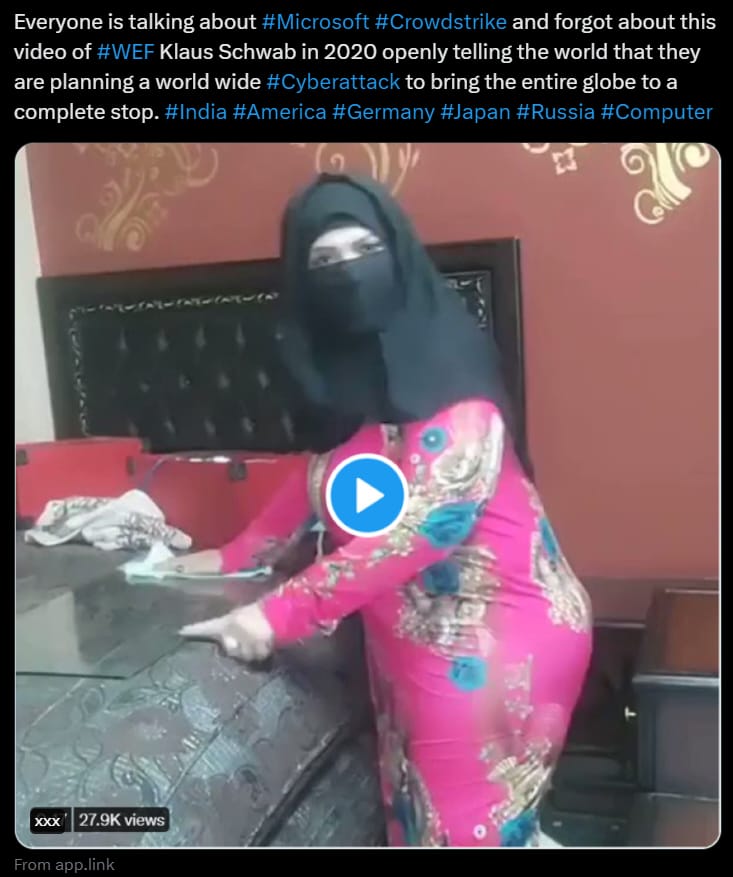
Note that the image looks like a video, meaning that anyone trying to play the “video” will instead open the link.
The images used in the post link, via a couple of redirections and depending on one’s geolocation, to sites with explicit or betting content. The images used contain varying levels of explicit content themselves.
Malicious Domain Update
The following domains are blocked as they aren’t official CrowdStrike links. Some of them are not (yet) hosting (malicious) content, but based on our telemetry, we have indications that they are used maliciously.
CROWDSTRIKE[.]COM[.]VC
FIXCROWDSTRIKEBUG[.]COM
CROWDSTRIKE-BSOD[.]CO
CROWDSTRIKEFIX[.]CO
FIXMYCROWDSTRIKE[.]COM
CROWDSTRIKEMEDADDY[.]COM
SECURE-CROWDSTRIKE[.]COM
The “crowdstrike[.]com[.]vc” domain is actively used by the Handala hacktivist group which targets Israel.
Additionally, malicious files have been observed by Trellix analysts and other researchers alike. File names which reference CrowdStrike and promise a fix are used to trick victims into executing malware. The case linked above is an information stealer, which extracts personal data from installed browsers and programs, which are then sent to the malware operator. CrowdStrike has an official blog about this stealer as well. The official fixes from CrowdStrike are to be used to resolve the recently introduced error.
NEW! Threat and Protections Update - Day 3 - July 21, 2024
Handala Hacktivist Group Targets Israel
We are aware of a targeted phishing campaign by Iranian threat actor group Handala using a seemingly legitimate Crowdstrike software installation package to deliver destructive malware to Israeli customers and organizations. Trellix Insights maintains the profile of Handala with indicators of compromise.
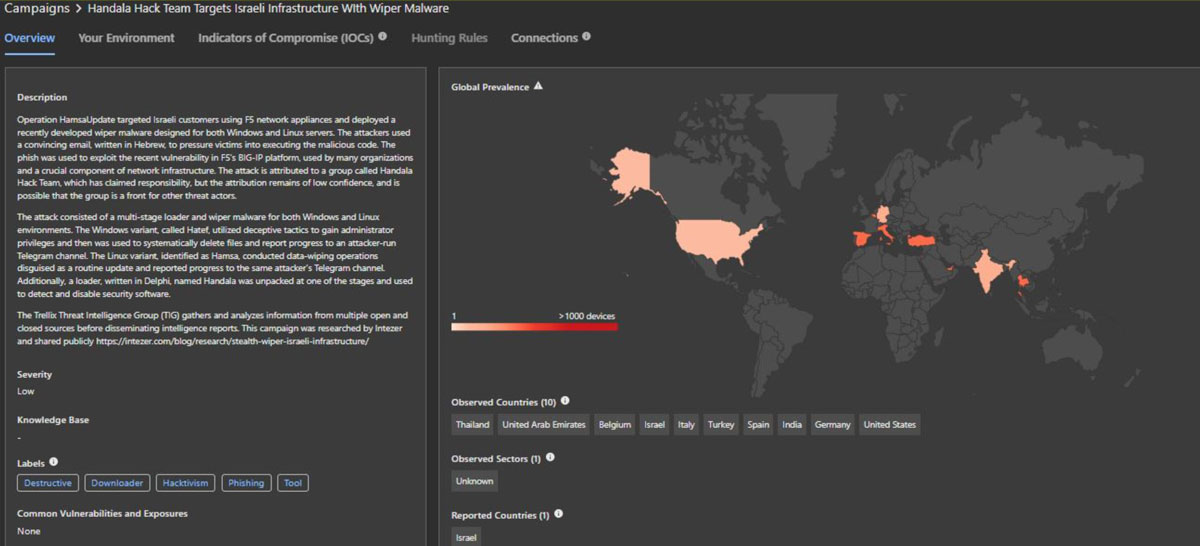
Trellix Insights Handala Profile
You can leverage Trellix EDR’s direct integration with Insights to automatically search for the new and historical indicators.
We observed these 2 new indicators as part of the recent targeted phishing campaign:
Email -> PDF -> URL -> Zip -> CrowdStrike.exe -> AutoIt Execution -> telegram
PDF : 22e9135a650cd674eb330cbb4a7329c3
Zip : d32f89a8a3dd360db3fa9b838163ffa0
CrowdStrike.exe 755c0350038daefb29b888b6f8739e81
These indicators are already blocked by Trellix ENS, Network and Email Security platforms. However the attack is under further analysis and new indicators may be published. In addition to updated endpoint security, it’s important to educate users to be very cautious opening any email related to Crowdstrike and the global tech outage.
New Scams Using Possible Lawsuits as the Lure…
We've also seen the fake domain crowdstrikeclaim[.]com hosting a page which mimics Parker Waichman LLP. It asks users to fill out the form and a team would contact them for compensation for the outage to their IT infrastructure.
Attackers Are Taking Advantage … Using Fake Domains to Deliver Malware
It’s Day 2 of the global tech outage and attackers are leveraging the chaos to deliver ransomware. Emails from fake domains claiming to provide a fix are being used to distribute a malicious ZIP archive named crowdstrike-hotfix.zip. The ZIP archive contains a HijackLoader payload that, when executed, loads RemCos.
MD5: 1e84736efce206dc973acbc16540d3e5
Trellix Insights shows this file with a high prevalence but not yet linked to any specific ransomware campaign.
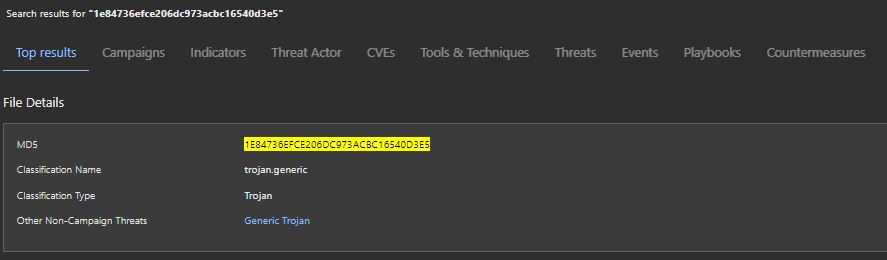
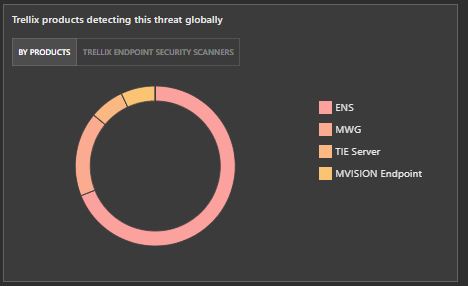
Customers using Trellix products have detections for this payload. Customers with our endpoint solution are protected in multiple ways from this particular threat.
Additionally, you can leverage Trellix Endpoint Forensics to search and verify the location of defect files or malicious files. Trellix Forensics provides an enterprise search capability by file hash.
Malicious Domain Update
In general, the tactics that hackers use to trick the public into clicking malicious links are the same tactics we expected to see in this situation. Trellix Advanced Research Center has already identified several hundred typosquat links for fake updates and support. We have characterized these domains as High Risk and Trellix Global Threat Intelligence has been updated so if you are using Trellix or SkyHigh products, you are already protected.
CROWDSTRIKE0DAY[.]COM
CROWDSTRIKEBLUESCREEN[.]COM
CROWDSTRIKEBSOD[.]COM
CROWDSTRIKE-BSOD[.]COM
CROWDSTRIKEDOOMSDAY[.]COM
CROWDSTRIKEDOWN[.]SITE
CROWDSTRIKE-HELPDESK[.]COM
CROWDSTRIKE0DAYL[.]COM
CROWDSTRIKEFIX[.]COM
CROWDSTRIKETOKEN[.]COM
CROWDSTRIKEOUTAGE[.]COM
CROWDSTRIKE-HELPDESK[.]COM
FIX-CROWDSTRIKE-APOCALYPSE[.]COM
MICROSOFTCROWDSTRIKE[.]COM
WHATISCROWDSTRIKE[.]COM
SUPPORTFALCONCROWDSTRIKE[.]COM
ACCOUNT-LOGIN-CROWDSTRIKE[.]COM
HOWTOFIXCROWDSTRIKEISSUE[.]COM
MISROSOFTCROWDSTRIKE[.]COM
FIX-CROWDSTRIKEBSOD[.]COM
CROWDSTRIKEODAY1[.]COM
CROWDSTRIKEFAIL[.]COM
CROWDSTRIKE0DAY[.]CO
CROWDSTRIKE[.]FUN
FALCON[.]CLOUD
If you are not using Trellix products, it’s critical to update your email, network, or web security solutions to block those domains.
Restore Trust in the Security Supply Chain
This type of incident highlights the need for trust and validation of your critical updates coming from IT and security providers. In the short term, we recommend reviewing and validating that only legitimate sources are used for critical software updates. Many of our customers have asked what Trellix does to ensure the reliability of our software updates. Trellix has a set of robust procedures in place, honed over 30 years of providing security updates for millions of users. For one, Trellix separates content and product updates, allowing our customers the ability to verify and plan updates. We will publish more on this topic in a detailed blog on security supply chain best practices.
Summary
The recent CrowdStrike outage underscores the need to rally as a security industry to protect organizations in crisis. Trellix has mobilized our support and professional services teams to help businesses worldwide recover and stay protected. Trellix is continually monitoring the threat landscape related to this incident. If you are using Trellix products, we will update our Global Threat Intel and Insights product with all malicious domains identified by our research. We will also publish any intel via the Trellix website so it is readily available to all organizations and their IT teams working through this global incident.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.