Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Phobos: Stealthy Ransomware That Operated Under the Radar - Until Now
By Jambul Tologonov, John Fokker and Duy-Phuc Pham · November 20, 2024
On November 18th, the US Justice Department unsealed criminal charges against a Russian national for allegedly administering the sale, distribution, and operation of Phobos ransomware. Phobos is considered an evolution of Dharma Ransomware (aka CrySIS). Code similarities and ransom notes suggest that the creators are either the same or closely connected.
First seen in October 2017, Phobos emerged as an evolution of Dharma. It resurfaced in 2019, exploiting exposed services like RDP and targeting users in Western Europe and the United States through spam email attachments.
Phobos in the Ransomware Ecosystem
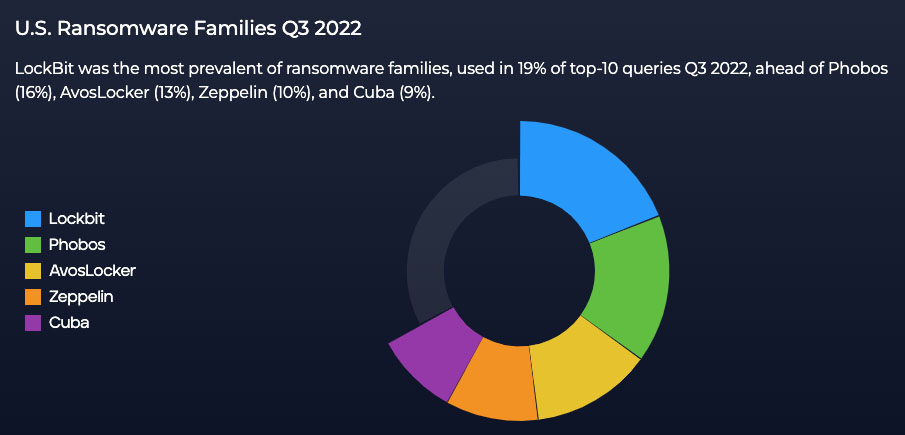
According to the Trellix CyberThreat Report from November 2022, Phobos ransomware was a notable player in the ransomware ecosystem globally and in the United States. At the time, Phobos was responsible for a significant number of attacks worldwide, and its impact was especially prominent in the US. The group's use of straightforward but effective tactics, such as targeting RDP and leveraging spam emails, made it a persistent threat despite lacking the more sophisticated tactics employed by groups like LockBit or Zeppelin.
Underground Dealings of Phobos Ransomware
Phobos has been linked to various monikers, as mentioned in the criminal charges, and identities that facilitate its operations on underground forums. A key moniker associated with Phobos is "phobos777," which has been seen operating through Jabber IDs and maintaining contact with other ransomware groups. For instance, "phobos777[at]exploit.im" is a known contact. Although this username is now banned from certain underground forums, it has likely re-emerged on other platforms, such as xss.is under the alias "Derxan." Other contacts connected to Phobos include "neo777[at]404.city," which is also linked to Dharma, and "cryptxxx[at]xmpp.jp," a name that is believed to be tied to the CryptXXX ransomware strain.
Communication and Coordination
Communication between these actors occurs over Jabber and other encrypted messaging platforms, allowing them to exchange information, coordinate attacks, and maintain anonymity. Another Jabber ID associated with these activities is "zimmermanx[at]xmpp.jp," which has also been linked to ongoing coordination efforts among these ransomware actors. For example, the Jabber ID "Debtrack" appears to have a direct link to multiple ransomware families, including Phobos, Dharma, and CryptXXX. The conversations observed between these actors suggest a Ransomware-as-a-Service (RaaS) model, where various components of the ransomware operation are compartmentalized and sold or rented to other threat actors.
Phobos' Low-Profile Approach
Phobos' approach focused on volume rather than high-profile targets, allowing it to maintain a steady stream of victims while remaining relatively under the radar. The absence of a dedicated leak site helped Phobos avoid drawing the attention of law enforcement and cybersecurity researchers, which was a critical factor in its ability to operate for years without major disruption. This operational model positioned Phobos as a lower-profile but highly impactful threat in the global ransomware landscape, contributing to the wider ransomware-as-a-service market and offering lessons in the importance of maintaining a low profile to evade detection.
Adaptability and Continuity
The movement of actors between different monikers, forums, and messaging services reflects an adaptive approach to evading detection and continuing their illicit activities. Despite these changes, the connections between Phobos, Dharma, and CryptXXX indicate a level of continuity, as many of the same actors and networks are involved across these ransomware operations.
The complex relationships between these monikers and the persistent use of encrypted communication channels demonstrate the resilience and coordination among ransomware groups. Understanding these connections provides valuable insights into the broader ransomware ecosystem and helps in predicting and preempting future threats posed by Phobos and its affiliates.
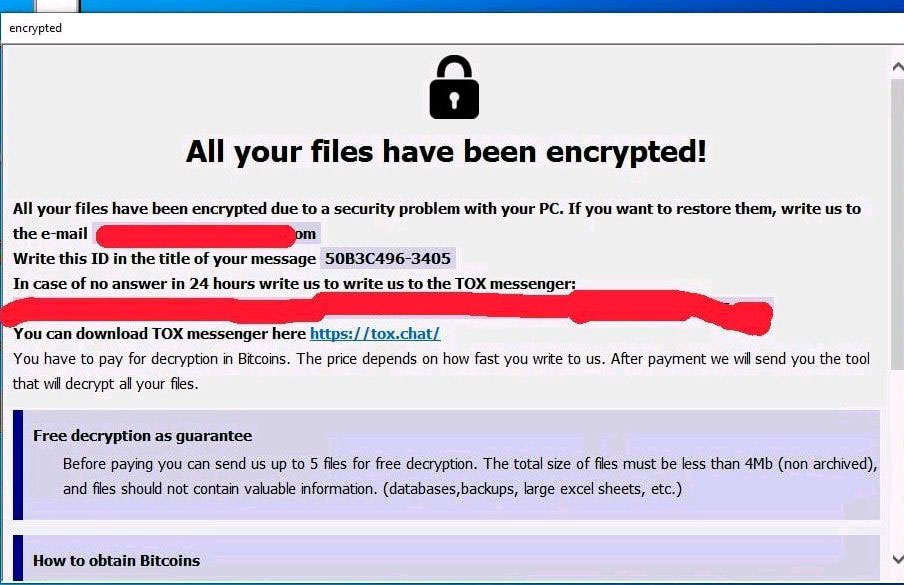
Although Phobos did not maintain a dedicated extortion leak page, it did drop a distinctive ransom note for each victim. This ransom note was a crucial part of their strategy, providing payment instructions and establishing communication with the victims.
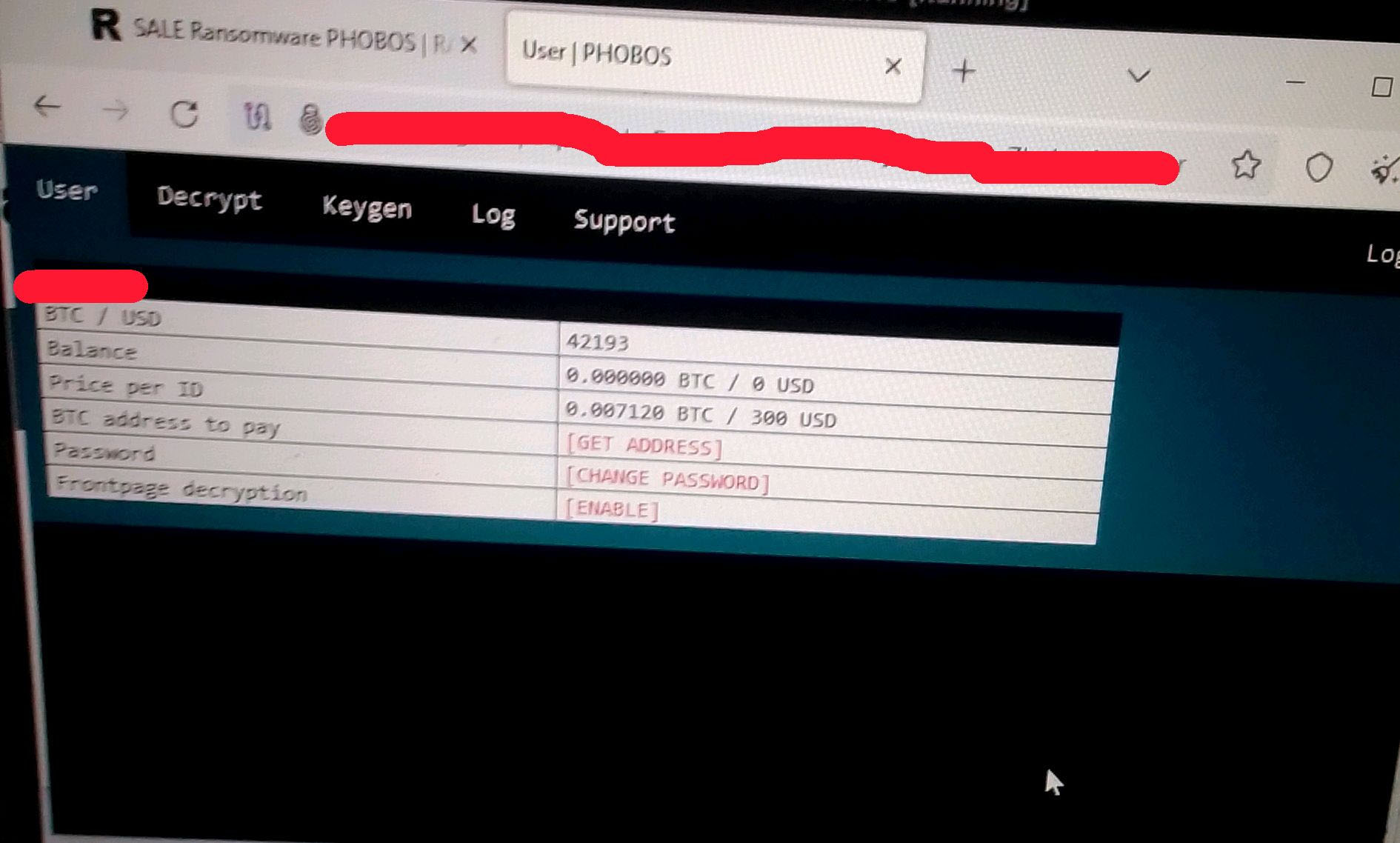
8Base: A Phobos Variant in the Ransomware Landscape
8Base is a ransomware group that emerged in March 2022 and gained significant attention in mid-2023 due to a surge in its activities. They are known to leverage a customized version of Phobos ransomware in their attack campaigns. This group differed from the original Phobos Ransomware group in that they employed double extortion tactics, encrypting victims' data and threatening to publicly release it if ransoms are not paid. They have targeted various industries, including finance, manufacturing, information technology, and healthcare, with a notable focus on small and medium-sized businesses.
Notable Incidents
In May 2023, 8Base was responsible for over 15% of all ransomware attacks reported that month, marking a significant increase in their activity. They have targeted organizations across multiple countries, including the United States, Brazil, and the United Kingdom.
8Base Ransomware Decline in 2024
The 8Base Ransomware-as-a-Service (RaaS) operation demonstrated significant activity during early 2024, averaging approximately seven victim postings monthly on their leak site. The group achieved notable prominence during spring 2024, maintaining a position among the top five ransomware groups based on victim disclosures. However, their operations experienced an abrupt decline beginning in mid-June 2024.
A prolonged period of inactivity followed from June through September 2024, with no new victim posts observed. The group made a brief resurgence in late September, establishing their data leak site on new hosting services and publishing data from several compromised victims. This revival was short-lived, as 8base ceased activities again in October 2024.
There are speculations that 8base's periods of inactivity might be connected to the Phobos ransomware operations decline, suggesting possible shared affiliates or operators between the two groups. The simultaneous quiet periods could potentially be attributed to law enforcement actions affecting both ransomware gangs’ operations.
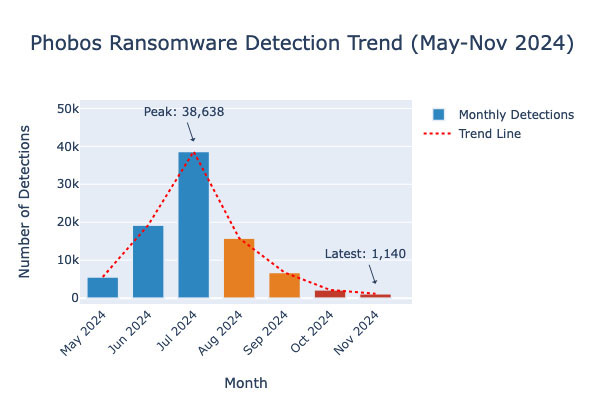
Decline in Phobos Ransomware Activity in 2024
Recent data shows a dramatic decline in Phobos detections, with a 97% drop from July 2024 to November 2024. At its peak in July, there were 38,638 detections, which fell sharply to 1,140 in November (partial month). The month-by-month trend highlights this decline:
- July 2024 (Peak): 38,638 detections
- August 2024: 15,809 detections
- September 2024: 6,754 detections
- October 2024: 2,175 detections
- November 2024: 1,140 detections
Interestingly, Phobos activity was heavily US-focused, accounting for 87.98% of detections, and primarily targeted the telecom sector (80.31%), with secondary impacts in transportation and shipping (14.59%).
Most of the detections came from Trellix endpoint security products, with AMCore-ENS and supported by multiple Trellix security products confirming the trend, providing clear quantitative evidence and showing a consistent pattern across different detection products and geographical regions. This data strongly supports Alexander Leslie's observation of a significant drop in Phobos activity. The timing and pattern of this decline could indeed be linked to Ptitsyn's arrest, as the numbers show a clear downward trend.
Despite the significant drop in detection data, Phobos is not currently visible in our ransomware victim sensors. According to CISA, Phobos actors primarily engage in extortion via various email providers, but some affiliate groups also use voice calls to pressure victims.
Threat Actors try to Capitalize on Phobos Legacy
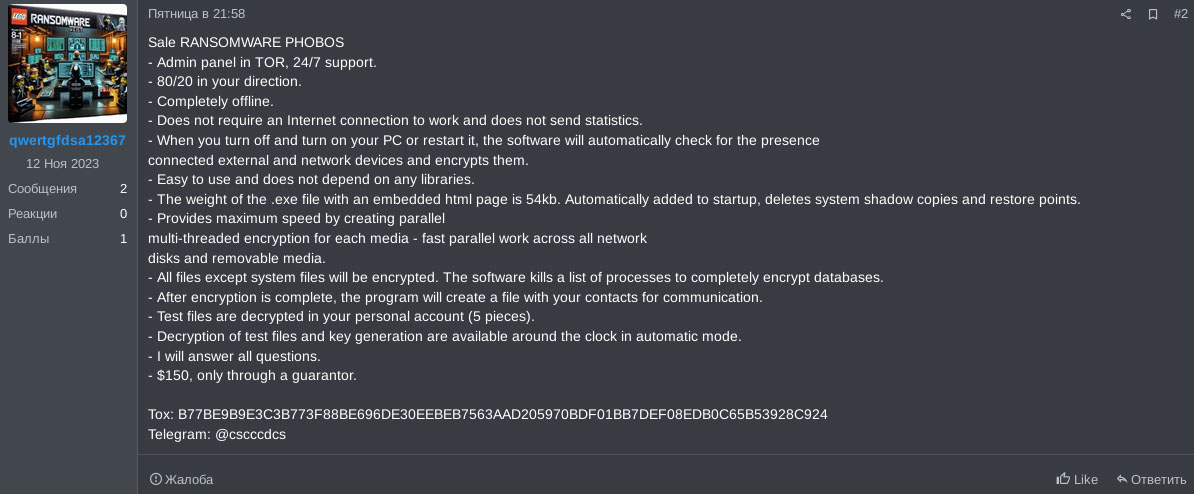
Other threat actors had already begun exploiting the demand for Phobos by offering their own versions of the ransomware builder a year before Derxan's arrest. Two RAMP actors, "qwertgfdsa12367" and "eloncrypto," were observed selling Phobos ransomware builders. Eloncrypto claimed to be an independent reverse engineer not associated with the original Phobos team, selling the builder for $1,000. The builder is a command-line tool written in C, designed for integration with a web panel, and includes features like keygen and RSA encryption.
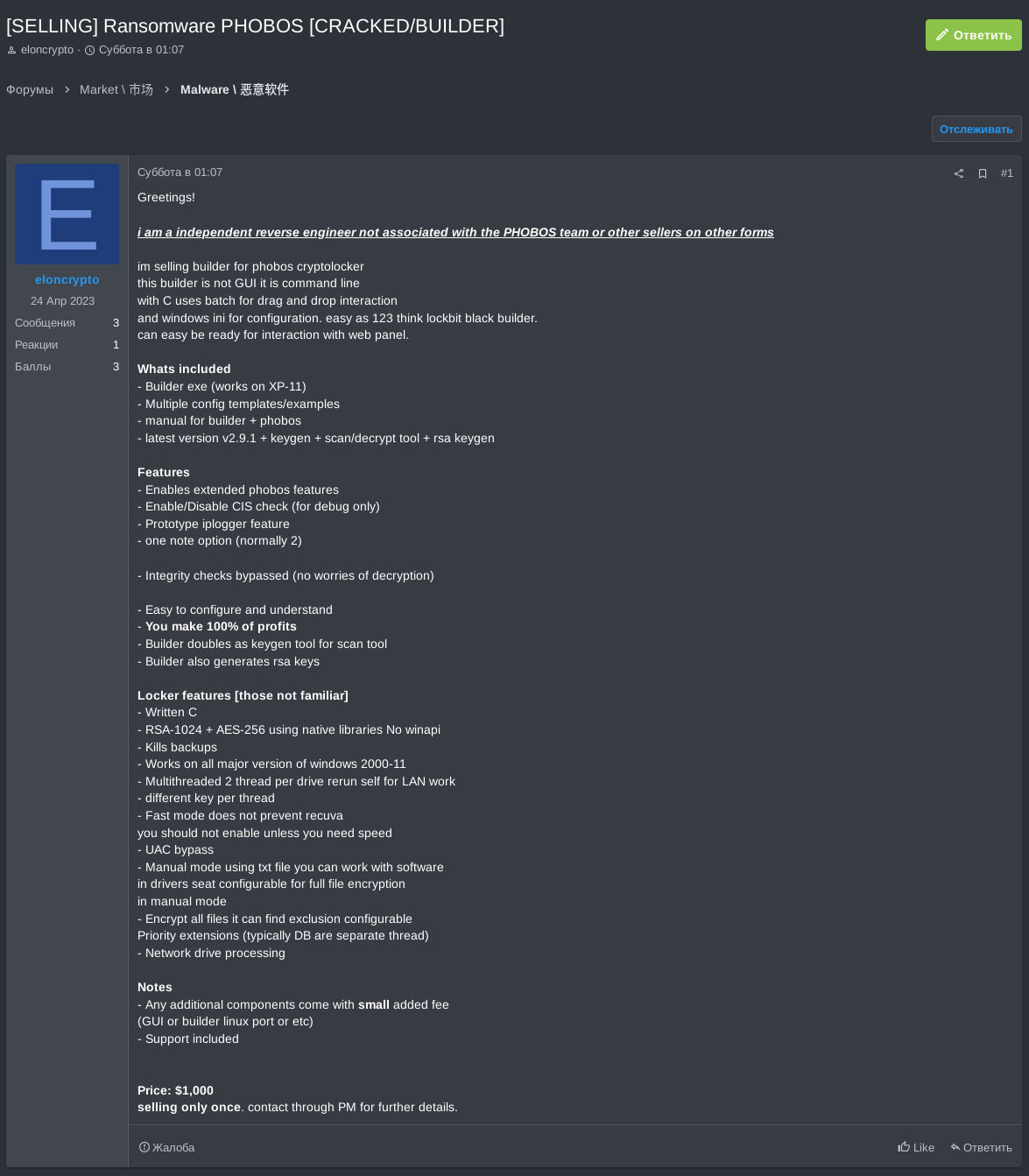
Eloncrypto's version includes various features such as an extended builder with multiple configuration options, an integrated keygen, support for drag-and-drop interaction, and a manual for operation. The builder is designed to be easy to configure, promises buyers 100% of the profits, and claims to include integrity bypass features to avoid decryption.
Meanwhile, "qwertgfdsa12367" is offering a similar product for a lower price of $150. The disparity in pricing suggests different levels of confidence or quality in their offerings. Nonetheless, these listings illustrate how quickly opportunistic actors adapt to fill the void left by a weakened ransomware group, ensuring the ecosystem remains active and profitable for those involved.
Conclusion
Trellix is pleased that global law enforcement efforts have put silver bracelets on Derxan, significantly reducing Phobos' activity. Despite seeing other cybercriminals trying to profit from the Phobos legacy, we remain optimistic. The coordinated efforts of law enforcement agencies and cybersecurity teams have been crucial in disrupting Phobos' operations. The decline in detections proves the effectiveness of these actions. While Phobos operated under the radar for years, its activities have finally been halted, marking a significant win for global cyber defense.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
