Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Scanning Danger: Unmasking the Threats of Quishing
By Shyava Tripathi and Rohan Shah · December 7, 2023
This blog was also written by Raghav Kapoor
Phishing, a prevalent cybercrime worldwide, is responsible for as much as 90 percent of data breaches, making it a significant avenue for the theft of sensitive credentials and information. While phishing itself is not a new threat, the landscape has evolved in recent months.
Interpol made a significant breakthrough in the fight against phishing by successfully shutting down '16shop', a notorious and widely used phishing-as-a-service platform in August 2023. While this takedown was a significant victory, the availability of phishing-as-a-service platforms, which offer subscription-based access and automation tools laden with phishing kits, means that virtually anyone can employ such services with minimal effort. This concerningly simplifies the launch of phishing campaigns to a few simple clicks.
The proliferation of Quick Response (QR) code-based phishing attacks also adds a new layer of risk to the landscape. QR codes, originally designed for convenience and whose usage was exacerbated by contactless transactions during the COVID-19 pandemic, have become a vital tool for attackers seeking credential compromise. QR code-based phishing, or Quishing, is a type of phishing attack that employs QR codes to deceive victims. In this form of phishing, attackers distribute malicious QR codes placed in seemingly legitimate locations such as emails, websites, flyers or posters. Unsuspecting individuals scan these codes with their smartphones, unknowingly granting access to malicious websites, leaking login credentials or downloading malware.
As users have grown more familiar with QR codes in their everyday routines, the opportunities for quishing attacks have expanded. Trellix has detected more than 60,000 email samples in the last quarter alone, responsible for business email compromise, credential leakage & malware infections through quishing.
In this blog, we explore the modus operandi of threat actors who utilize QR code attacks by examining the most recent and widespread quishing campaigns detected by Trellix. These campaigns encompass various tactics, including postal phishing, spear phishing, malware delivery, business impersonation, and file-share phishing payloads delivered and deployed using QR code phishing attacks.
Quishing Kill Chain
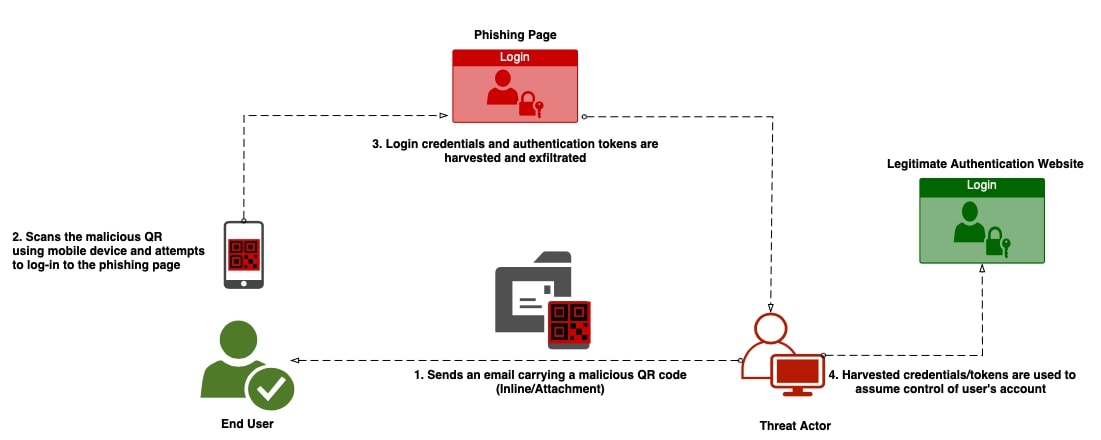
The resurgence of QR codes in our daily lives has paved the way for a fresh wave of sophisticated phishing attacks that have set their sights on numerous organizations across the globe. These threats employ cunning tactics to entice end users into scanning QR codes delivered through email, using the camera on their mobile devices. Once scanned, these QR codes redirect unsuspecting victims to malicious websites with the nefarious intent of pilfering their login credentials, siphoning financial data, or infiltrating their devices with insidious malware (Figure 1).
This evolution in cyberattacks capitalizes on the widespread adoption of QR codes for various purposes, exploiting the trust individuals have developed in this technology. It's crucial for individuals and organizations alike to be vigilant and adopt security measures to guard against the increasingly sophisticated tactics employed by quishing attackers.
Trellix Email Security Detection Telemetry
Trellix has observed a surge in quishing emails utilizing both inline and attachment vectors to deliver malicious QR codes. More than 60,000 quishing samples were detected by Trellix in Q3 alone, with a steady spike observed in September.
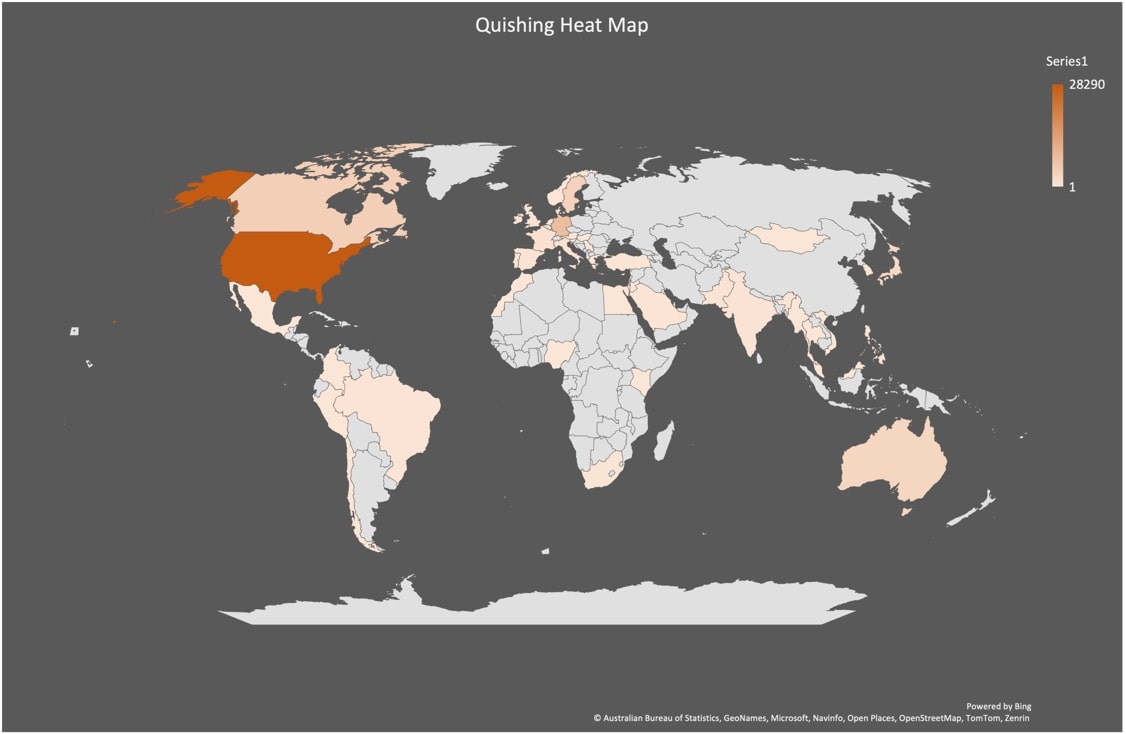
Furthermore, 55 countries were targeted during the quishing surge, with United States, Germany, Canada, Sweden and Australia (Figure 2) being the primary targets in Q3, followed by Japan, Singapore, France, United Kingdom and the Republic of Korea.
The following sections describe the top quishing campaigns in detail, observed email variants, URL/host structure and additional evasion tactics deployed by threat actor groups:
Postal Quishing
1. FedEx
Postal phishing emails impersonating FedEx lure users under the guise of dealing with legitimate FedEx shipment or delivery concerns. Users are prompted to scan the QR code in the interest of updating delivery information, paying levied customs or approving delivery (Figure 3). Users are directed to a FedEx login phishing page (Figure 4), prompting them to enter their email credentials which are exfiltrated to a .PHP page once the user attempts to log-in.
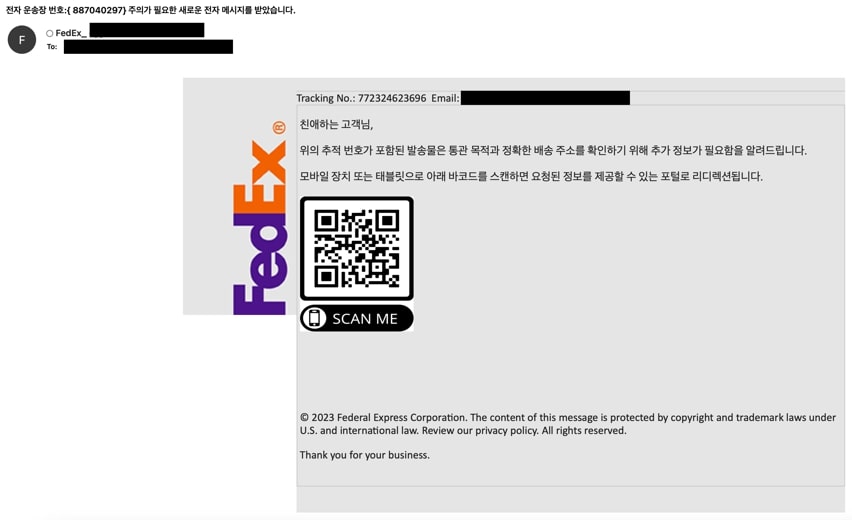

2. DHL
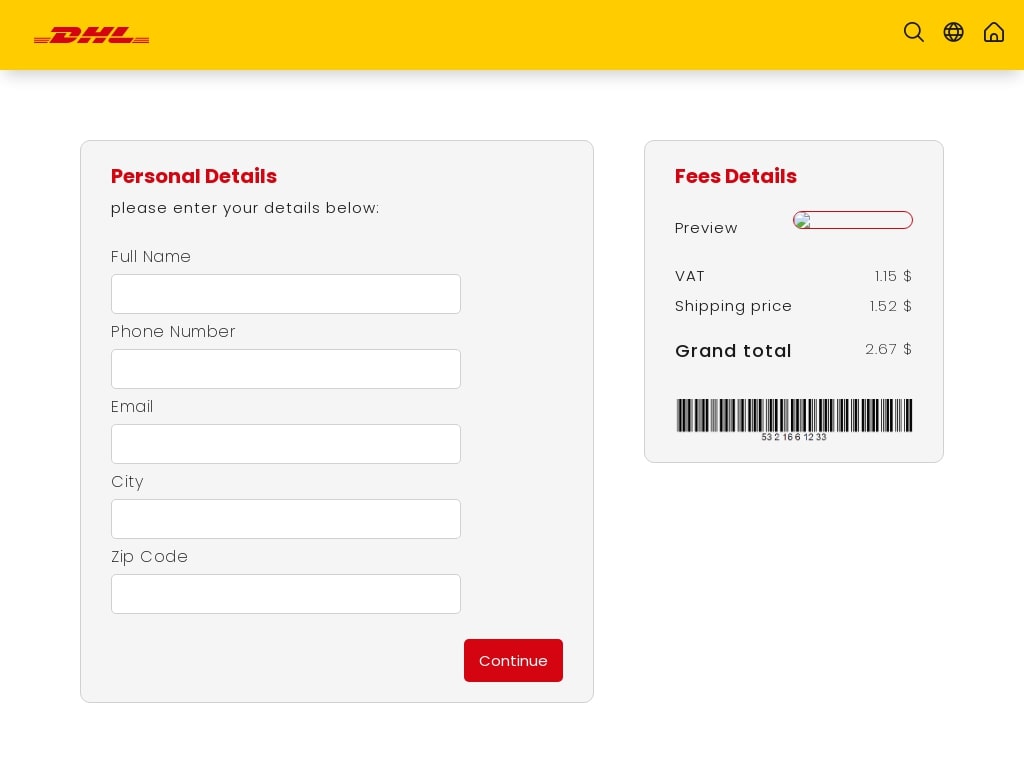
Postal phishing emails impersonating DHL contain waybill numbers, shipment numbers and template subjects such as ‘Waybill:’, ‘Delivery Attempted’ and ‘Package put on hold’ to deceive victims (Figure 5).

Emails contain QR codes, which when scanned, redirect the users to phishing pages, requesting them to enter their email credentials along with updating delivery and payment information (Figure 6). This data is then exfiltrated to threat actors.
The success of postal phishing scams often hinges on exploiting trust in postal services and the urgency associated with package deliveries. Victims are lured into clicking on fake tracking links, providing personal details, or even downloading malicious attachments, all while pretending to address a legitimate shipment.
Spear Quishing
1. HR Impersonation
Human resource (HR) impersonation phishing is a malicious tactic wherein cybercriminals pose as HR personnel within organizations to manipulate employees into disclosing sensitive information or performing harmful actions. In this type of phishing attack, deceptive emails often mimic legitimate HR communications, such as requests for compliance information, policy updates, or even employee financial information such as payslips and tax statements.
These attacks exploit the trust and authority associated with HR departments, as well as the sensitive nature of HR-related matters, like leaves, benefits, or job-related inquiries (Figure 7). The attackers aim to create a sense of urgency or fear, pressuring employees into quick responses, thereby increasing the likelihood of successful data theft or malware delivery.
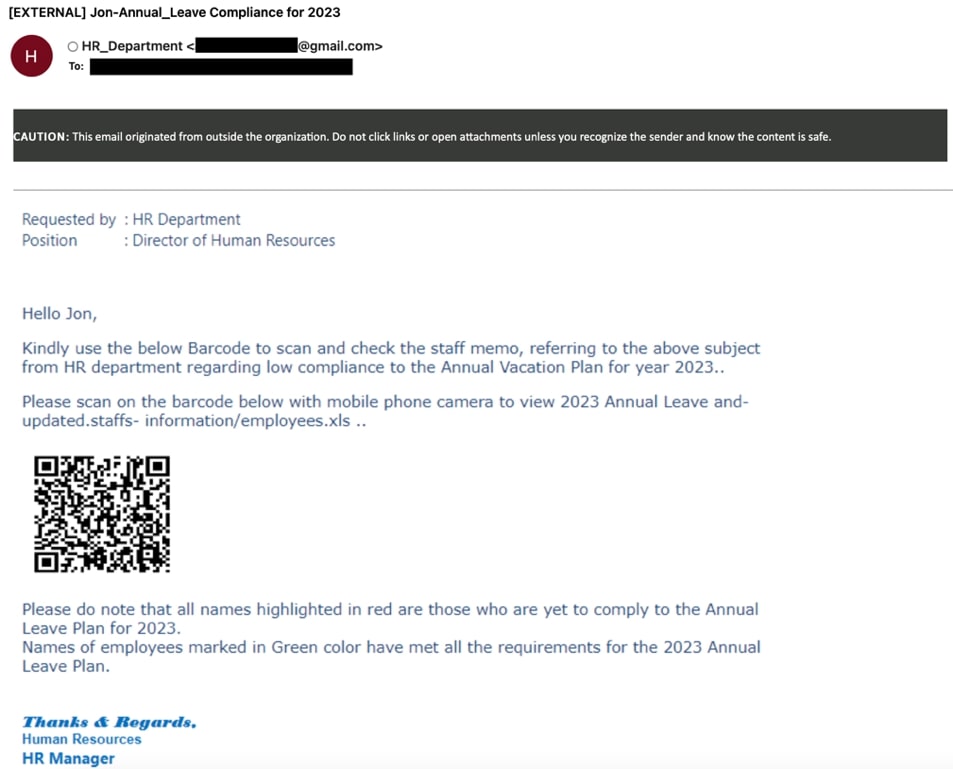
This campaign leverages 'workers.dev' and 'glitch.me' domain URLs, which instantly deploy serverless code to evade detection. These call-to-action URLs redirect through Cloudflare captcha checks followed by serving a Microsoft login phishing page.
2. Payroll Impersonation
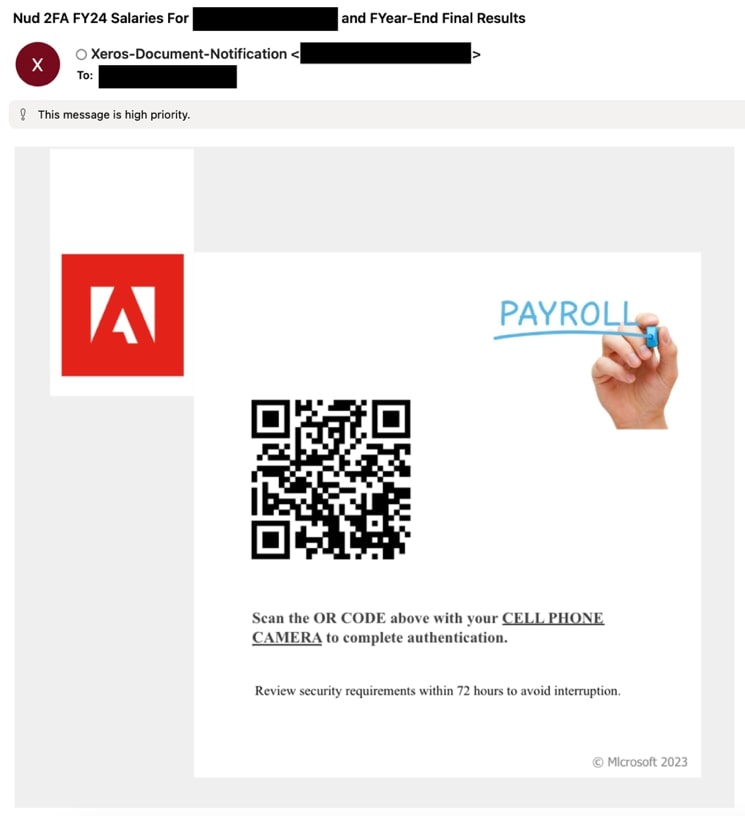
Payroll phishing scams have become a prevalent threat, targeting both individuals and organizations. Cybercriminals employ sophisticated tactics to impersonate payroll services in an attempt to steal sensitive financial information, such as Social Security Numbers, bank account details, or login credentials. These emails are guised as critical information such as salary updates, fiscal year results, and bonus promises, compelling recipients to act quickly without thinking critically.
These emails may include logos, branding, and language commonly used by the actual payroll department, further deceiving recipients (Figure 8). The spoofed emails closely mimic official communications, making it challenging for recipients to distinguish between real and fake messages. Once scanned, the QR code directs the user to a Microsoft phishing page where the user credentials are harvested.
3. IT Impersonation
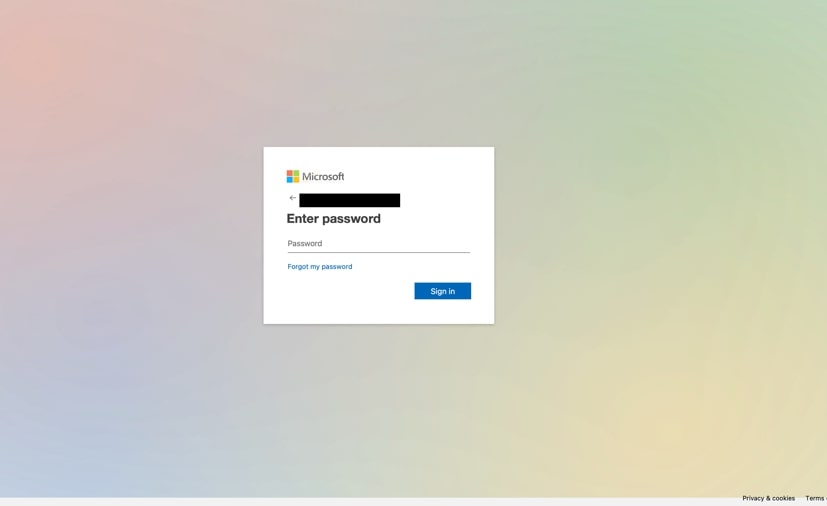
IT service credential phishing emails target employees by impersonating help/resolution desks, prompting users to login in lieu of resetting an expired password or enabling security updates.
The email is disguised as a support or system administrator message and conveys a sense of urgency by utilizing keywords such as ‘Action Required' and 'Notice:' in the body (Figure 9). The QR code when scanned redirects the user to a fake Outlook login phishing page in pursuance of harvesting official credentials.

QR codes in the emails, when scanned, redirect the victims to Microsoft or Outlook login phishing pages (Figure 10). The credentials entered by users are harvested and exfiltrated to threat actor servers.
To safeguard against spear phishing, individuals should exercise caution when receiving unexpected personnel or department related messages, and always verify the authenticity of such communications.
In addition to utilizing malicious QR codes, the campaign utilizes trusted domains like bing[.]com, krxd[.]com and cf-ipfs[.]com to redirect users to phishing sites. Base-64 encoded phishing links present within Bing and IPFA redirect URLs to allow threat actors to mask phishing domains and bypass security solutions (Cofense). Along with Bing redirection, these campaigns utilize typo-squatted domains, anti-bot checks and captcha-based evasion (Peeling off QR Code Phishing Onion), to evade detection.
File-share Quishing
1. SharePoint
SharePoint phishing trends have significantly evolved in recent times. Cybercriminals are increasingly leveraging the popularity of SharePoint, a widely used collaboration platform, to launch sophisticated phishing attacks. Phishers exploit SharePoint's file-sharing capabilities to trick users into clicking on links to supposed shared documents or folders. Victims unknowingly download malicious files or provide login credentials, thinking they are accessing legitimate resources.
SharePoint is used in conjunction with BEC attacks, where attackers impersonate executives or colleagues and request sensitive data through SharePoint documents, masquerading as legitimate business transactions.
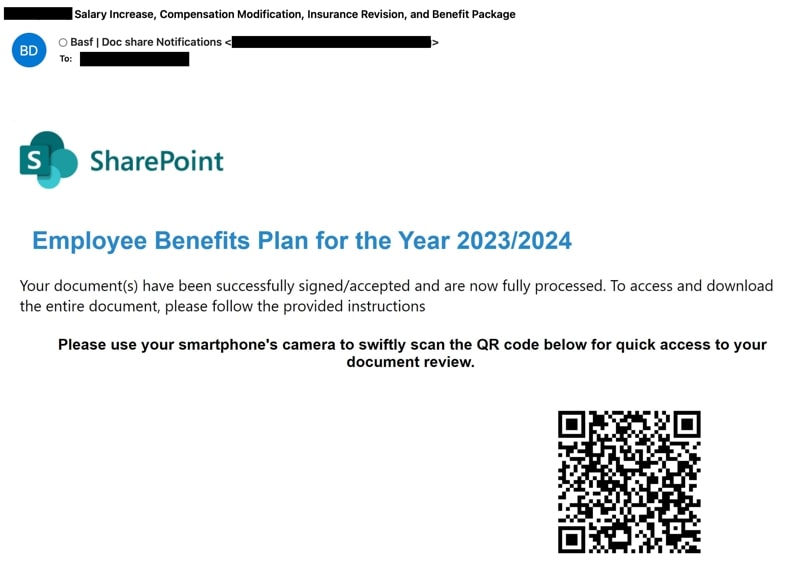
In this widespread campaign, attackers exploit critical operation notifications such as compensation emendations, insurance revisions, bonus allocations and dividends to lure victims (Figure 11).
The QR code, when scanned, redirects users to convincing replicas of Microsoft login pages, tricking users into entering their credentials. These spoofed pages are hosted on malicious domains, making it challenging to differentiate them from the genuine SharePoint portal.
2. DocuSign
DocuSign-themed phishing emails purport to come from DocuSign, and coax recipients by using a structured template of legitimate DocuSign emails (Figure 12).
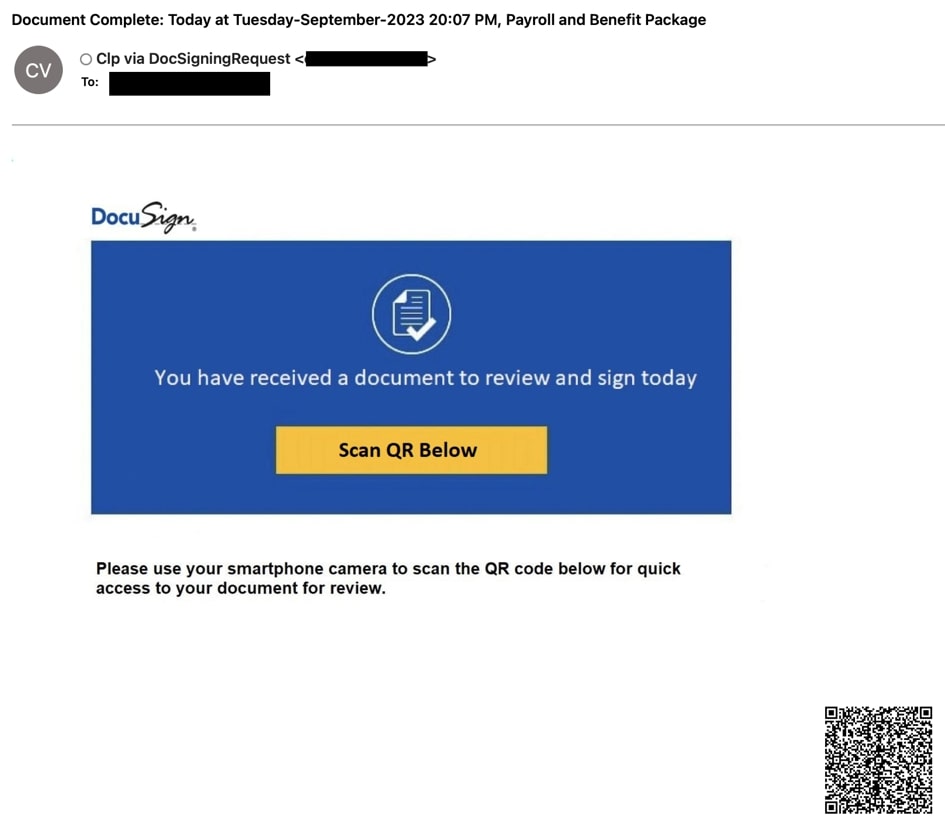
The campaign targets Microsoft Office 365 email credentials and cues users to review their completed documents.
The call-to-action URLs direct the users to a Microsoft login phishing page. The credentials are harvested once the user attempts to login.
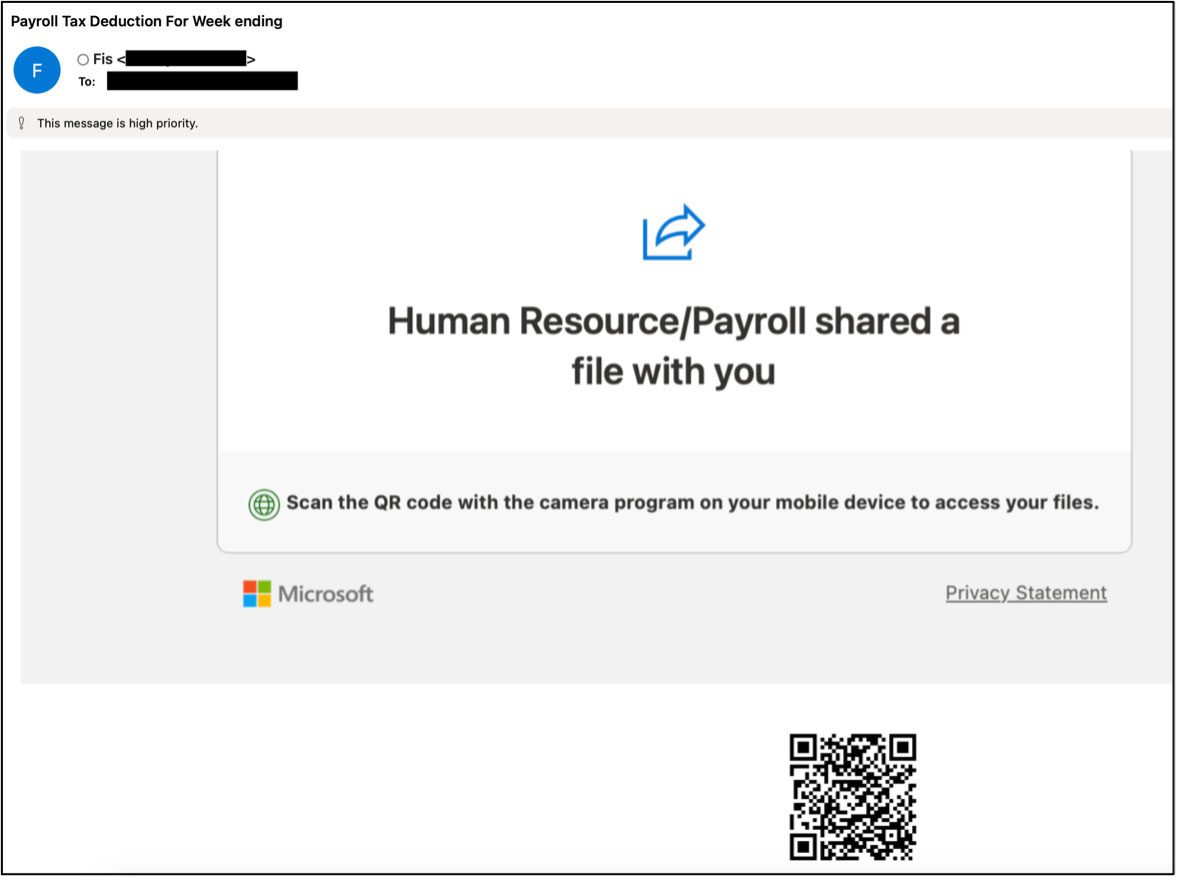
3. OneDrive
In this spear phishing attack, the attacker pretends to be from a HR/payroll support team and impersonates a OneDrive tax deduction file share request (Figure 13). The campaign uses an image-based email body to evade content-based detection filters. OneDrive is leveraged to deliver the phishing URL with the body of the email identical to a standard OneDrive file invitation. The QR code within the email redirects the user to a spoofed Microsoft login page. The credentials are harvested once the user attempts to login.
The above mentioned file-share quishing campaigns also employ Bing redirection, typo-squatting, anti-bot checks and captcha-based evasion checks to bypass detection by security solutions.
Crypto Wallet Quishing
1. Coinbase Wallet
Emails impersonating Coinbase (Figure 14) and Binance (Figure 15) support, popular cryptocurrency wallets, surged this quarter. These samples lure victims to update their wallet in lieu of securing their funds, prompting users to scan the QR code and complete the process.
Once scanned, victims are taken to a fake landing page crafted to look like the actual Coinbase or Binance website, prompting the user to enter their wallet passphrase, private key or Phrase Keystore JSON file (Figure 16). Phishing for crypto recovery phrases, which are a sequence of 12 words, or private wallet keys, allows adversaries to import an existing crypto wallet, thus enabling them to steal the victim's available funds and NFTs. Once harvested, user data is exfiltrated to a .PHP URL using ‘POST’.
Trellix Email Security Prevention
Trellix Email Security employs a comprehensive, multi-tiered detection approach for identifying quishing. This approach encompasses evaluations at the URL, email content and attachment levels to ensure the timely detection and prevention of potential threats, safeguarding our customers from harm.
Trellix's QR code detection module is capable of recognizing the presence of QR codes in emails, both inline and as attachments, extracting the embedded data from these QR codes and processing the extracted data through anti-phishing static, dynamic and machine learning modules.
The following is a subset of the Trellix Security detections that have been observed for these campaigns:
Phishing_Microsoft_Creds_37
Phishing_Loading_Wait_Page
Phishing_Generic_Mail_9
Phishing_B64_Pattern_Hunting_01
FE_EMAIL_PATTERN_MICROSOFT_QR_CAMPAIGN2
FE_EMAIL_PATTERN_MICROSOFT_QR_CAMPAIGN3
FE_EMAIL_PATTERN_MICROSOFT_QR_CAMPAIGN4
FE_EMAIL_PATTERN _DHL_CAMPAIGN1
FE_EMAIL_PATTERN_MICROSOFT_SHAREPOINT_CAMPAIGN1
Conclusion
As QR codes become increasingly integrated into our daily lives for various purposes, from contactless payments to accessing websites, it's crucial to recognize the growing threat of QR code phishing attacks. These attacks leverage the unsuspecting nature of QR codes to deceive individuals and gain unauthorized access to personal and financial information. To top this off, more often than not, QR codes are scanned using mobile devices which may not have the same level of security and protection as desktop computers. This makes mobile users particularly vulnerable to QR code phishing.
The trust factor associated with QR codes, reliance on mobile devices for scanning, evasion tactics deployed by threat actors and lack of awareness amongst individuals will inescapably expand the potential attack surface for QR codes, establishing them as a prevalent avenue for phishing and malicious activities. Security solutions must adapt to identify these seemingly simple yet highly effective phishing methods.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.