Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Better Security with Trellix XDR & Gen AI
Today’s threat landscape requires Gen AI to surface all your org’s threats.
By Bill Thorn · March 13, 2024
Overview
You have probably heard everyone in security talking about something along the lines of “In today’s era of relentless cyber threats from nation states and other advanced actors, the need for cutting-edge and integrated cybersecurity solutions has never been more critical. Organizations find themselves having increasing difficulty separating meaningful signal from the noise. All are faced with more environmental complexity, expanding third-party risk, ever-increasing volumes of data and events, and increasing costs. Simultaneously, those same groups are braving a scarcity of resources and talent to properly comprehend what is occurring in their environment.” And it’s true. But, did you know, even the best-resourced security shops often can review no more than 10% of the alerts their teams receive? Thus, a better approach is required for all.
Enter Gen AI. Gen AI leverages machine learning, behavioral analysis, natural language processing, and predictive analytics to revolutionize threat detection, response, and remediation. By harnessing Gen AI, organizations are empowered to stay ahead of adversaries, identify emerging threats with unprecedented speed and accuracy, and fortify their defenses against cyberattacks. Even better, with Trellix XDR with Gen AI, your organization can analyze 100% of the alerts observed, giving your organization a ten-fold increase in visibility. As a security executive, exploring the capabilities of Gen AI is essential to enhance your organization's cyber resilience and ensure proactive protection in today's dynamic threat landscape, and Trellix makes it easy
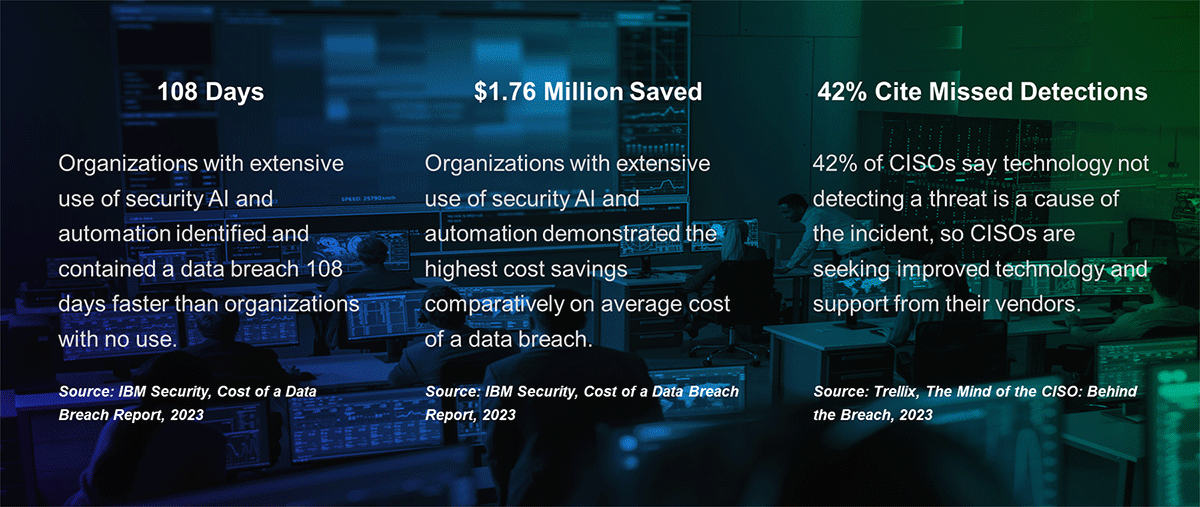
It's a Math Problem, And I Hate Math
I don’t really hate math, just the math that works squarely against me like credit card bills…and security funding. In this case (based on a real scenario), it goes something like this:
I run a SOC at mid-to-large enterprise with 100+ locations around the globe. My SOC is collecting 30-40k events per second, or more than 2.6 billion events per day. The SOC receives more than 150,000 alerts per day – a mere 0.00006% of the event volume. I have five Tier-1 frontline analysts working 24/7, two Tier-2 analysts 24/7 for escalations, and onetwo Tier-3 analysts 24/7 for investigations and hunting, as well as a SOC manager 24/7. All-in-all, it is a well-resourced SOC.
As mentioned, my Tier-1 analysts are the front line and they have a capacity to review just over 1,400 alerts per day under ideal conditions (5 analysts x 24 hours per day x 30 sec review per alert), but conditions are regularly far from ideal. There are many alerts that do not take as long to analyze and many that take much longer. Additionally, analysts often receive side projects, need training, need breaks, and any number of other things that chip away at this capacity, Thus, their real capacity as a whole ends up being somewhere closer to 1,000 alerts per day under good conditions.
So, what do I do about the other 149,000 alerts? Just as the Titanic was tragically unprepared for the hidden dangers of an iceberg by focusing only on the visible threat, SOCs often grapple with the overwhelming volume of unseen cybersecurity threats beneath the surface, struggling to navigate and respond effectively amidst the vast, unseen dangers of the digital sea.
To review all 150,000 alerts, I would need roughly 52 Tier-1 analysts, along with corresponding Tier-2 and Tier-3 analysts 24/7. It is a non-starter for my organization. As a matter of fact, it is a non-starter for all but a precious few. For those few that do see those size teams, they are also seeing much higher event and alert volumes to justify those teams. Thus, we all end up in the same boat with a large percentage of alerts that go unreviewed, slipping beneath the surface due to lower priority, event type, and any number of other factors. The question then becomes, what could be lurking beneath the surface that can really hurt us?
We’re Getting Better and So Are They
As industry, we have slowly been getting better over time. The introduction of SOAR technologies to add prescribed automation activities to our SIEMs helped extend some of those resources and allow them to handle even more capacity. Even with pre-built automation, however, we were relying too heavily on our analysts to create the right SIEM correlation rules to alert the SOC and build the right SOAR playbooks to carry out automation activities, often at high cost. And, in the end, we still have most alerts beneath the surface.
With the advent of Gen AI and large language models (LLMs) like ChatGPT and Bard (stop me if you’ve heard this one), the cybersecurity world is quickly evolving. These technologies have opened exciting new possibilities for cyber defenders, and the world as a whole. If you are betting person, there is even a possibility that some of these images were generated by such a solution. Yet, at the same time, these same solutions have created new opportunities for threat actors as well. Regrettably, gone are the days of the poorly worded emails from a Nigerian Prince that routinely duped my mother-in-law, entertaining as they were. Now actors can create convincing emails in languages they don’t even speak. I can get help with errors in my Python code, and they can get help with errors in JavaScript for their callback functionality. In that sense, we remain even.
Fortunately for us, when properly applied, Gen AI can be a major difference maker for the entire industry, taking you and your team from just even to leaps and bounds ahead. AI can be looked to for help solving any number of challenges from scrutinizing access and authentication, to dynamically creating and enforcing data protection rules, to assessing and responding to alerts received in our SOCs. In the end this takes risk off the table and simultaneously creates value for the organization, two critical outcomes.
Gain Instant Value and Improved Visibility
So, how do you take advantage of Gen AI’s added value with minimal friction? Gaining value does not require ripping and replacing your existing investments. Simply sending your events into Trellix XDR immediately overlays our vast intelligence providing critical context to the events you already collect. From there our Gen AI and machine learning models in Trellix XDR go to work analyzing the data, asking the tough questions, and pulling together relevant observables to make better decisions around event and incident correlations, priorities, and contextual relevance. Next, our AI-Guided Investigations gather the related events, evidence, and recommended next steps analysts should take, as well as kick off any automated actions or responses you have authorized.
With Trellix XDR, subtle alerts that previously laid beneath the surface unreviewed and relegated to low priority are now analyzed and scrutinized. When XDR identifies an event that needs to be raised to analysts, the priority is adjusted, and the incident is surfaced to ensure analysts both see it and are provided the knowledge and automation needed to respond. This significantly reduces the chances of lurking predators going undetected beneath the surface and AI-Guided Investigations dramatically accelerates your time to respond. Lastly, our analytics will show you and your team the time savings they are receiving from our integrated AI.
Business Outcomes and Metrics from Trellix XDR with Gen AI
Trellix XDR with Gen AI significantly enhances an organization's cybersecurity posture to achieve a more proactive and intelligent security strategy and ensure robust defense mechanisms against the evolving cyber threat landscape. Security leaders can look forward to numerous important outcomes including:
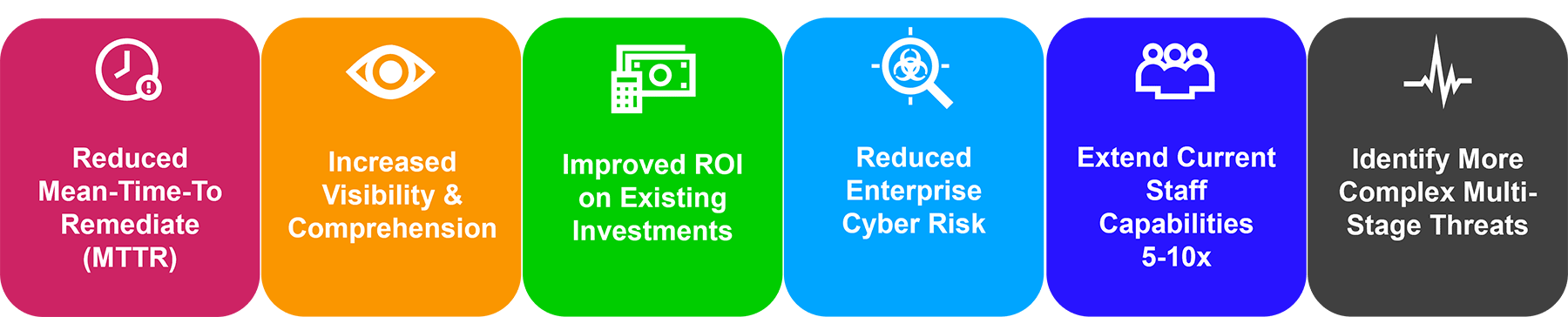
With more than 1,000 technology integrations into the Trellix platform, and an open API framework, Trellix can help you get better value from your security stack today. Elimination of blind spots, better analysis of your telemetry, and automation are the keys to keeping you ahead of today’s high-velocity threats.
Take Action Now
Learn how Trellix can help you and your team optimize your program and maximize value for your organization. Contact your account team or visit https://www.trellix.com/platform/ for more information
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
