Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Trellix Global Defenders: Analysis and Protections for Destructive Wipers
By Ayed Al Qartah · November 17, 2022
Modern cyber warfare involves the actions of a nation-state or their proxies (organized crime and hacker groups) to attack and attempt to damage other nations’ computers or information systems through, for example, denial-of-service attacks, web defacement, or wiper malware.
The sole purpose of wipers is to damage target systems by corrupting system components, such as the Master Boot Record (MBR) or the Master File Table (MFT). Moreover, wipers can permanently delete the victim's data by overwriting or encrypting files along with backups found on the system. Both approaches can lead to making the data irrecoverable or the compromised host unbootable after the restart.
This year we’ve seen a high volume of wiper attacks against Ukrainian government organizations and critical infrastructure. In parallel with the military actions on the ground, pro-Russian threat groups launched destructive wiper attacks on hundreds of systems in Ukraine. The most significant strains of wiping malware discovered before or after the invasion are: WhisperKill, WhisperGate, HermeticWiper, IsaacWiper, AcidRain, CaddyWiper, and DoubleZero.
As a companion to the Trellix threat intel blog “Wipermania: an all you can wipe buffet” by Max Kersten, this blog will cover Trellix protections and detections of various wipers, primarily focusing on HermeticWiper.
Gathering threat intelligence on wiper campaigns
The Trellix Advanced Research Center is monitoring the threat actors currently targeting Ukraine and the threat tools being observed in those attacks. Monitoring for the usage of these tools in your environment can be a proactive step in detecting compromise of your infrastructure.
Trellix Insights provides intelligence and actionable insights from a single console. Critical context on threat actors/crime groups behind the campaign is shared, including the tools they’ve used, the common vulnerabilities and exposures (CVEs) they’ve been associated with, the MITRE ATT&CK adversary tactics, techniques and procedures (TTPs), the associated Indicators of Compromise (IoCs), and credible sources on the campaigns. As shown in the below figure, we can see cyber campaigns that have been observed during the Russia-Ukraine war listed in Trellix Insights.

Let’s take HermeticWiper as an example; for customers who have Trellix Insights this process is simple. By filtering the Profiles to HermeticWiper, you will get a complete overview of the HermeticWiper campaign. As an introduction, the tool provides a short description of the group and their current targeted countries / sectors. Trellix Insights will alert to detections and Process Traces that have been observed and systems that require additional attention to prevent widespread infection in your environment. Trellix Insights will also include Hunting Rules for threat hunting and further intelligence gathering of the threat activity and adversary.
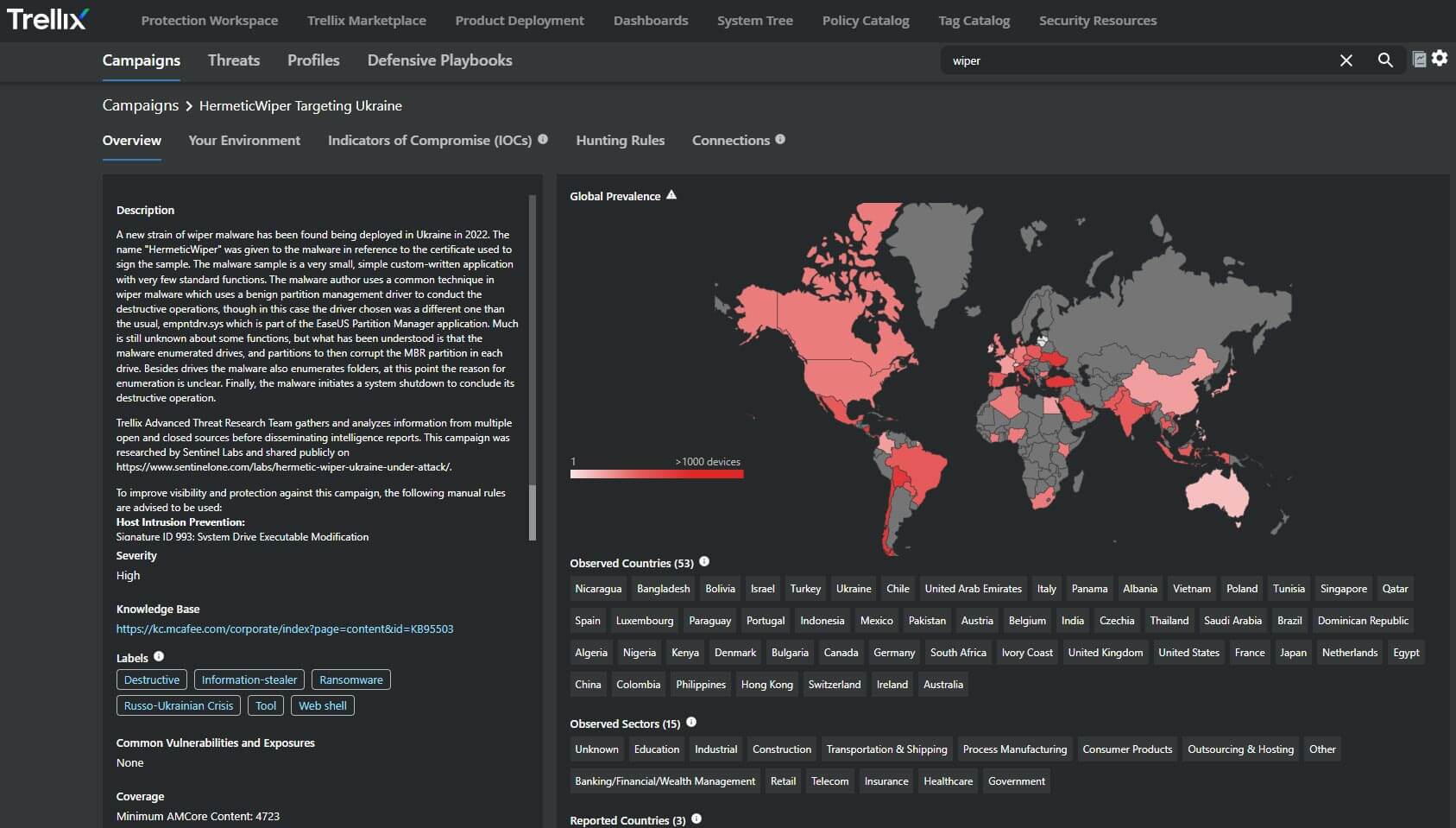
The next section of the interface describes the MITRE ATT&CK Techniques associated with the HermeticWiper campaign.
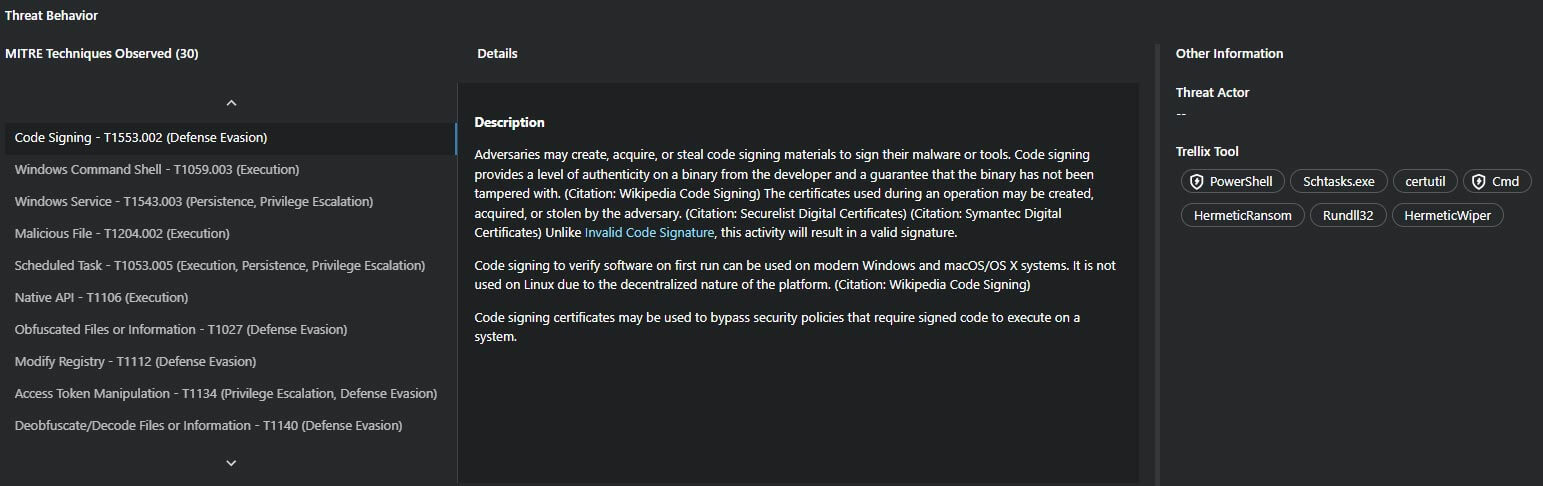
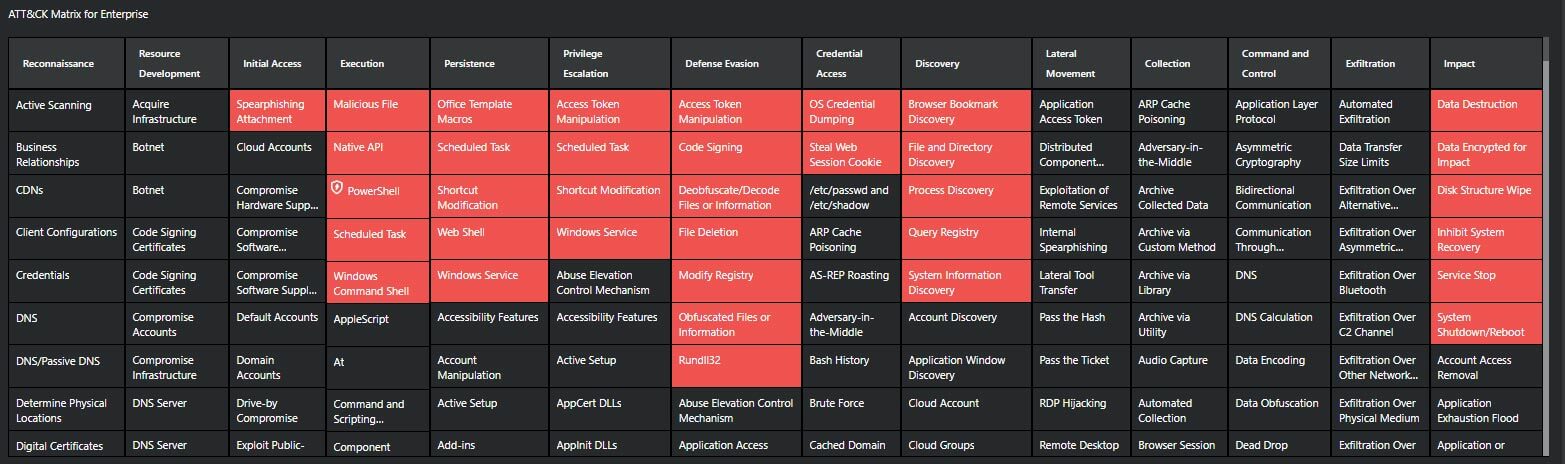
And finally, based on all those information, the interface builds for you the following MITRE ATT&CK Matrix with a clear representation of the observed techniques.
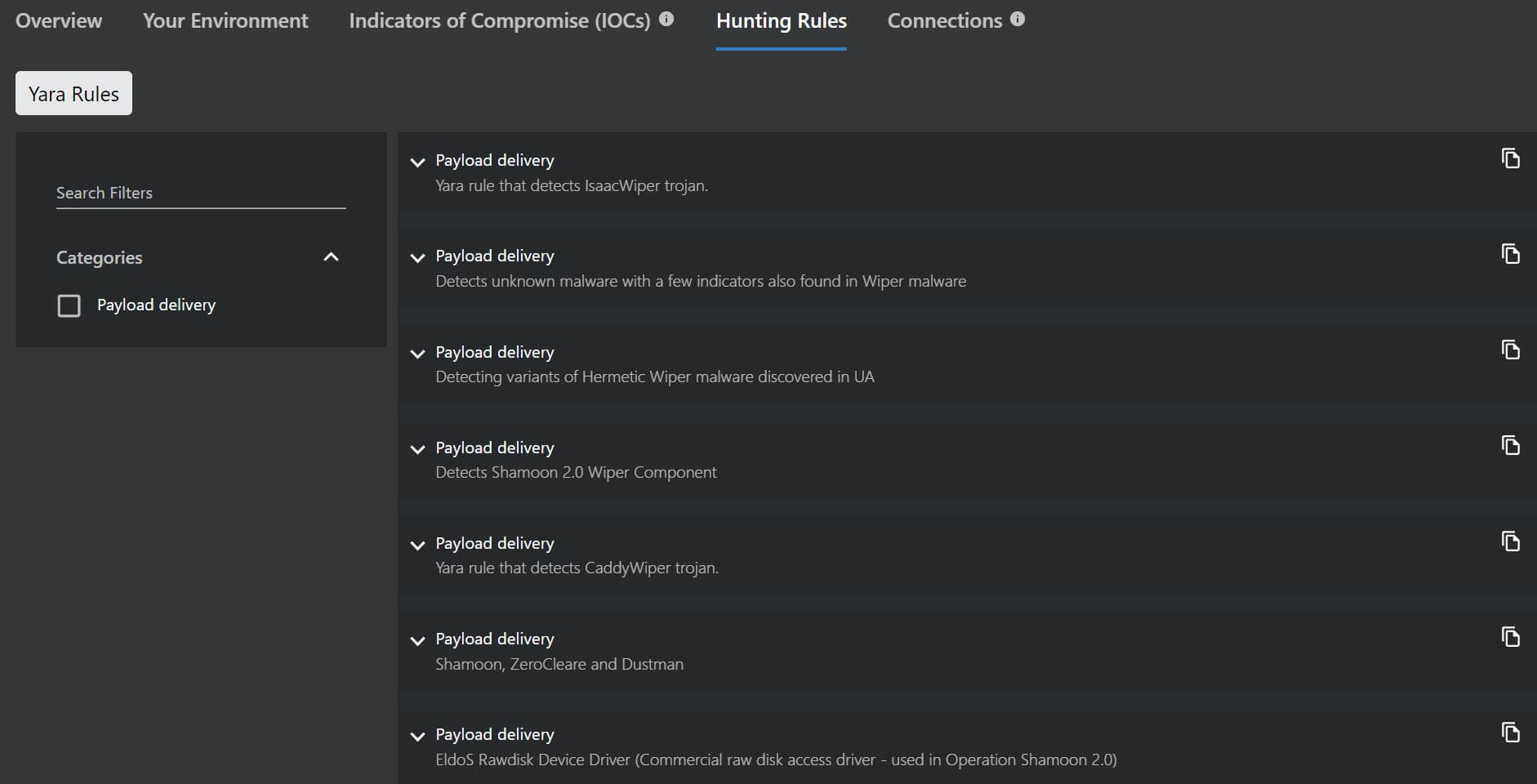
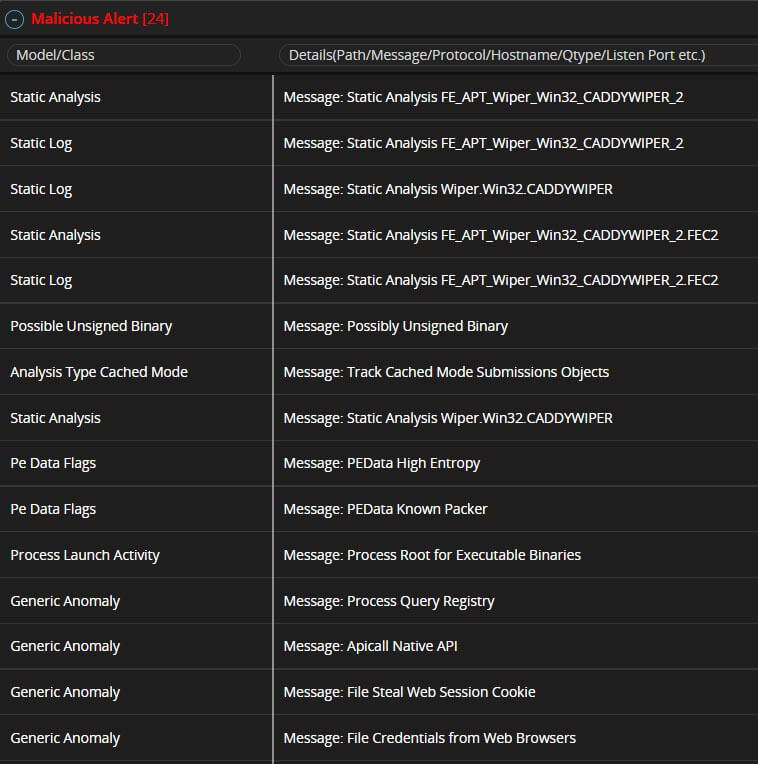
Applying hunting rules and threat intelligence across the security stack is key for the detection and identification of the TTPs associated with different wiper families. As shown in the figure below, threat hunters have access to Yara rules for wiper campaigns, including IsaacWiper, HermeticWiper, CaddyWiper and others.
Blocking wiper attacks with Endpoint Security (ENS)
Trellix ENS is currently detecting wiper IOCs with signature detections and the malware behavior associated with wiping campaigns.
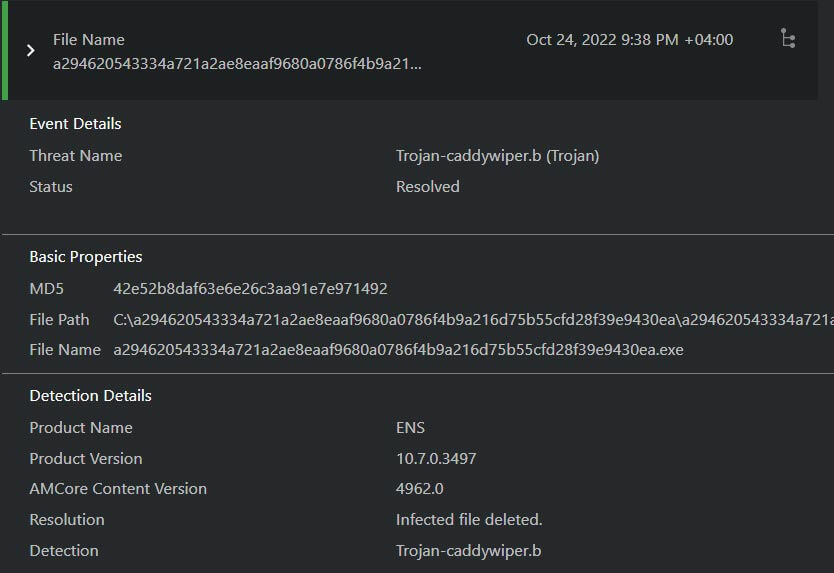
The following rules in Trellix ENS Exploit Prevention and Adaptive Threat Protection (ATP) are recommended to observe or block behavioral activity associated with wiper campaigns. Trellix always recommends testing in Report Only Mode before blocking to confirm that no false positives are being detected by the signature rules.
Endpoint Security - Advanced Threat Protection:
Rule ID: 4 Use GTI file reputation to identify trusted or malicious files
Rule ID: 259 Detect masqueraded files or process launches
Rule ID: 239 Identify suspicious command parameter execution
Rule ID: 263 Detect processes accessing suspicious URLs
Rule ID: 57 Use GTI file reputation to identify files that Might be Trusted or Might be Malicious
Endpoint Security - Exploit Prevention:
Rule ID: 6081 PowerShell Command Restriction - NoProfile
Rule ID: 6070 Hidden PowerShell Detected
Rule ID: 6135 Unmanaged PowerShell Detected
Rule ID: 6083 PowerShell Command Restriction – NonInteractive
Rule ID: 6086 PowerShell Command Restriction – Command
Blocking wiper attacks with MVISION EDR
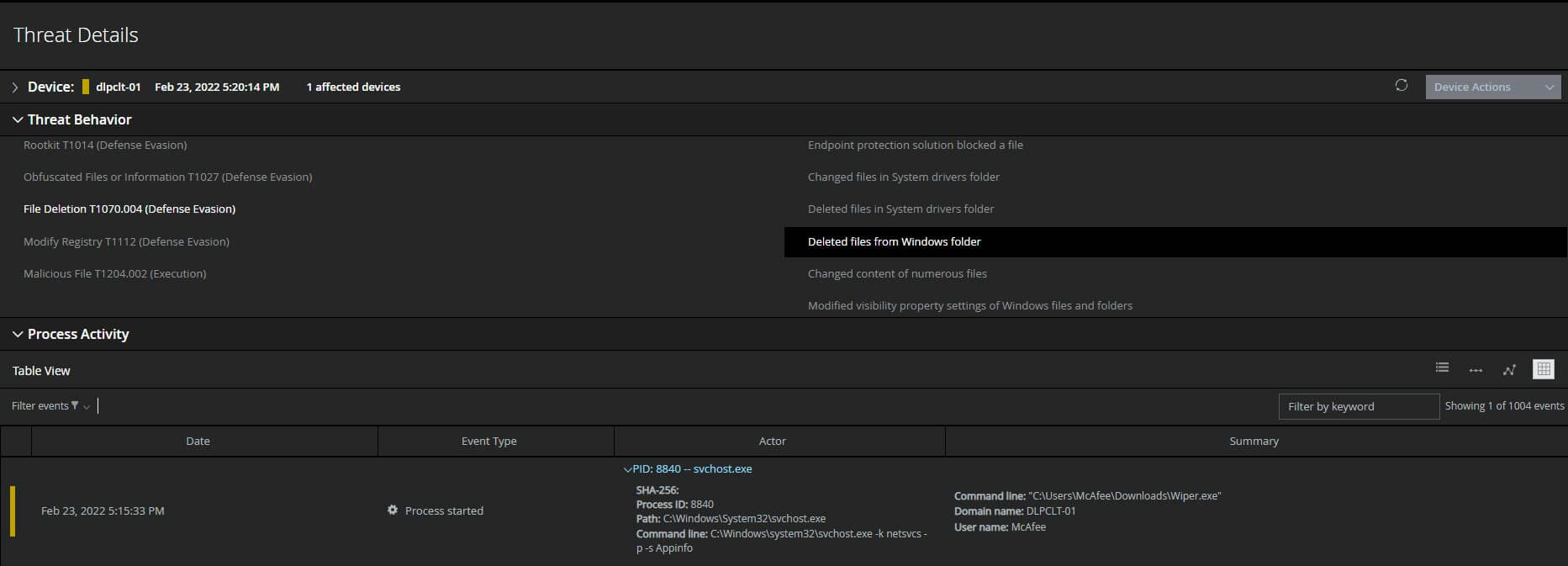
MVISION EDR is currently monitoring for the activity associated with wiper malware and will note the MITRE techniques and any suspicious indicators related to the adversarial activity. As shown in the figure below, detecting and preventing HermeticWiper from spreading throughout your environment is critical due to the destructive nature of the malware. Once the HermeticWiper has infected a system, it will remove the Windows files leaving the system inoperable.
Blocking wiper attacks with Endpoint Security (HX)
Trellix Endpoint Security (HX) uses multiple protection engines and customer deployable modules built from the experience of front-line responders to defend against these types of attacks. The combination of signature-based, machine-learning based, and behavioral-based protection capabilities, the UAC Protect module, and the Process Guard module for Trellix Endpoint Security provide maximum protection for customers. Trellix has protection coverage for different strains of wiper malware in the wild.
To use Trellix Endpoint Security to defeat techniques used by wiper campaigns, Trellix recommends enabling the following settings:
- Malware Protection – Signature-based and Machine-learning based protection
- UAC Protect – Module that protects against User Access Control (UAC) Bypass Attacks
- Process Guard – Module that protects against Credential Dumping
- Real-Time Indicator Detection – Indicator of Compromise detection
- Exploit Guard – Module that delivers behavior-based detection and prevention against exploits and payloads.
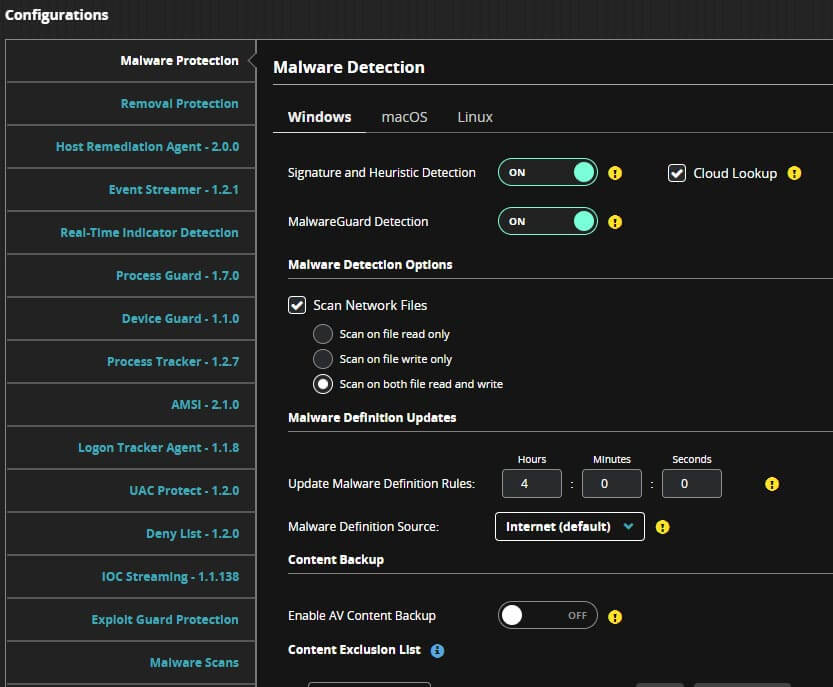
Trellix Endpoint Security (HX) offers ML-based behavioral detection and prevention of known and unknown wipers.
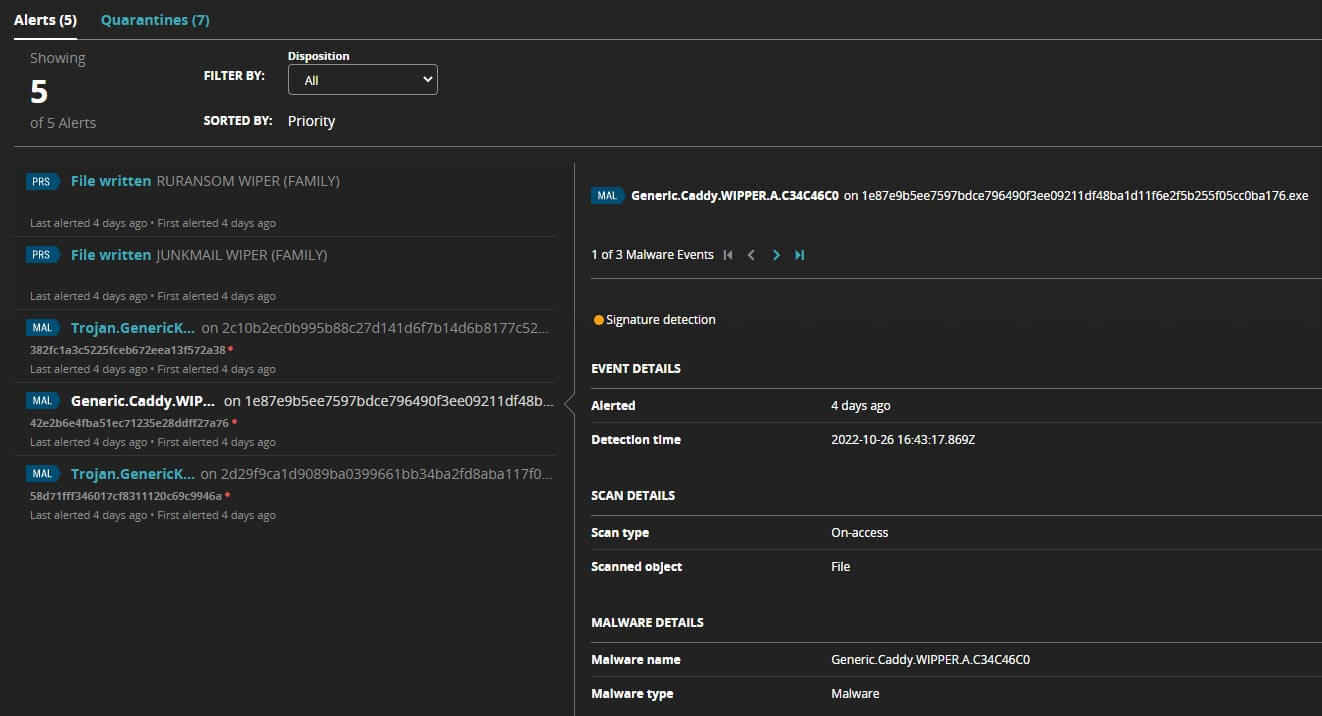
After gaining initial access, adversaries will move within the victim’s network from one compromised host to another, performing reconnaissance, stealing credentials, and elevating privileges. Adversaries have been known to install their own remote access tools (i.e., Cobalt Strike, Mimikatz, Empire) to accomplish lateral movement or use Living-off-the-Land (LotL) tactics in the form of abusing built-in system tools such as PowerShell, PsTools, WMI and command line. In the figure below, Trellix Endpoint Security (HX) reported the presence and execution of Cobalt Strike and malicious PowerShell scripts.
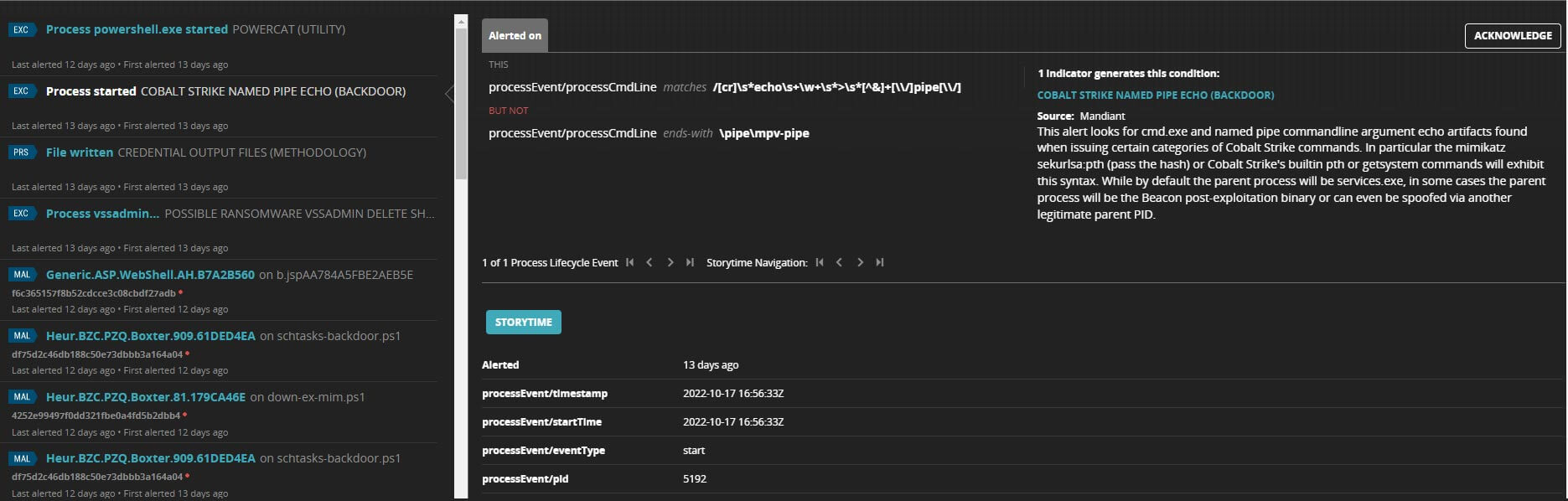
During an investigation, cyber defenders would leverage the digital “bread crumbs” in an alert triage audit or manually run audits to then go out and hunt for attacker artifacts at scale via Enterprise search.
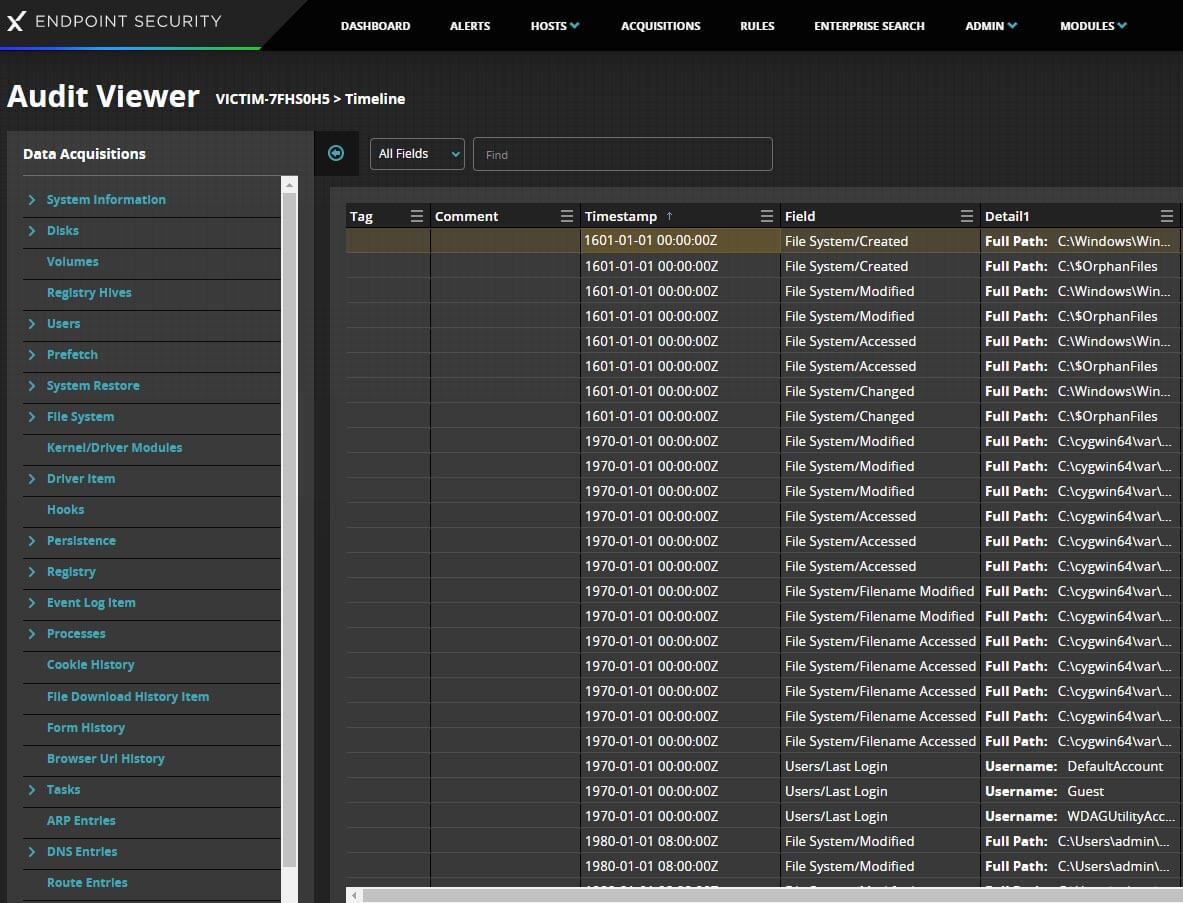
Blocking spear-phishing and malware with email security
Trellix research team tracks and monitors phishing lures related to the Russia-Ukraine war. Several threat groups use phishing to gain access, gather information and credentials, and establish and maintain access to the victim’s networks. Their targets are mostly national institutes and government entities, based on Trellix Labs’ observations. On April 18, 2022, a malicious email, presumably from a compromised ukr[.]net account, with the subject “ua_report”, was observed on one of our email gateways. This email attempted to lure the victim to open the attached compressed file with the following line “Operation ‘The Eye of Sauron’ results” followed by the password needed to open the attachment.
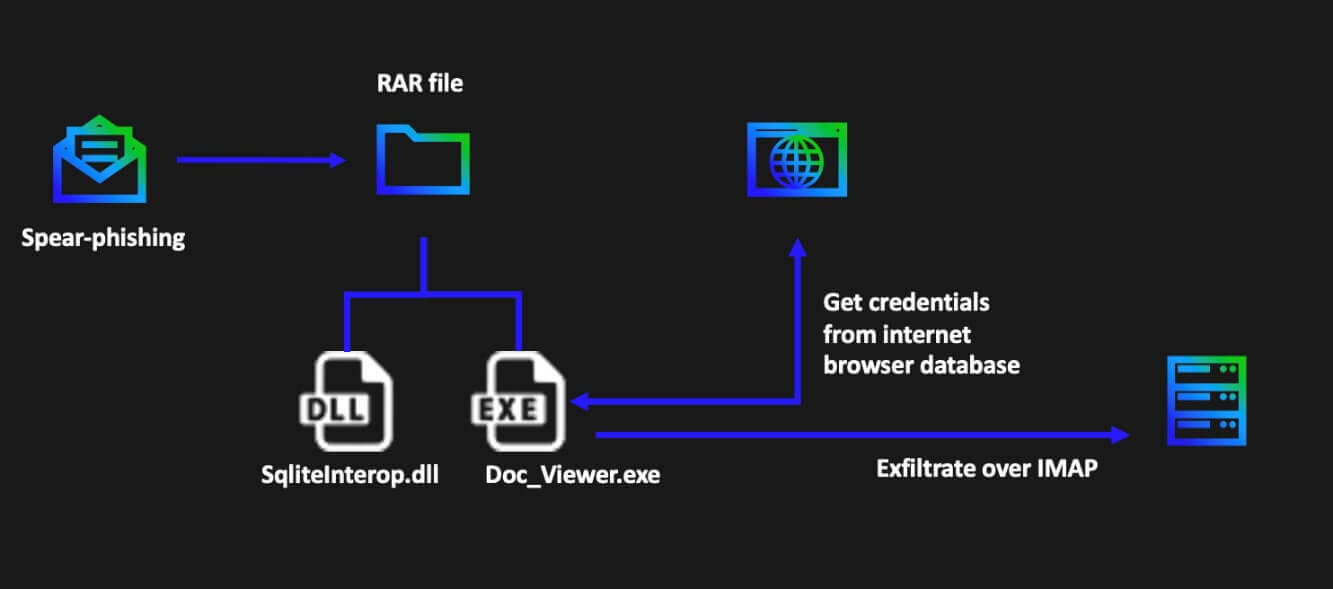
Once executed, the password-protected self-extracting RAR will drop on the system an executable called “Doc_Viewer.exe” or “DocumentSaver.exe”, and a DLL called “SQLite.Interop.dll”. The executable is a .NET infostealer which uses the bundled DLL to interact with various browser’s SQLite databases and extract the stored credentials and cookies. This activity was reported by Google’s TAG and attributed to the infamous APT28 aka Fancy Bear threat actor, known for its ties with the Russian GRU.
In the figure below, we show that Trellix Email Security detected and quarantined the email based on a combination of technologies including real-time threat intelligence from the Trellix reputation cloud, Multi-Vector Virtual Execution™ (MVX) engine analysis, and MalwareGuard (ML-based analytics). Trellix Email Security helps organizations minimize the risk of costly breaches caused by advanced email attacks. It offers comprehensive email security against malicious attachments, credential-phishing URLs, spoofing, zeroday and multi-stage attacks.
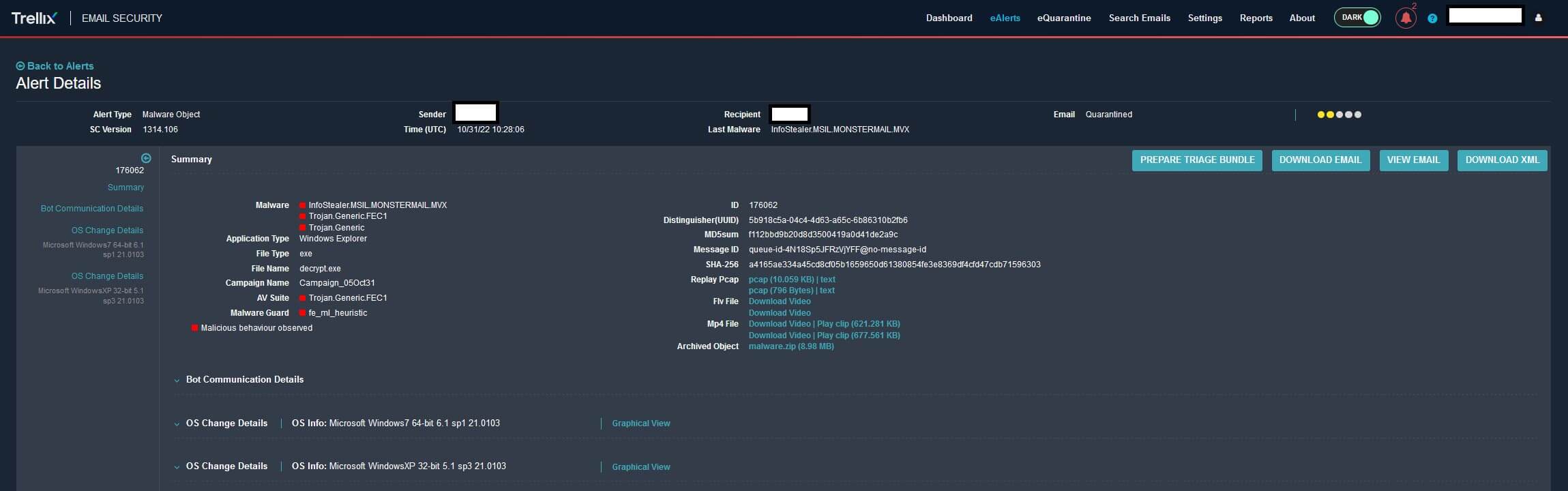
After the MVX analysis is completed, an OS change report is then returned. The report provides an in-depth forensics data of all behaviors discovered during analysis. The OS change report includes:
- File and folder actions
- Windows Registry events
- Processes and Network activity
- Windows API function calls
- Artifacts of exploit activity
- Code injection
- DLL loading
- Mutexes
- User Account Access (UAC)
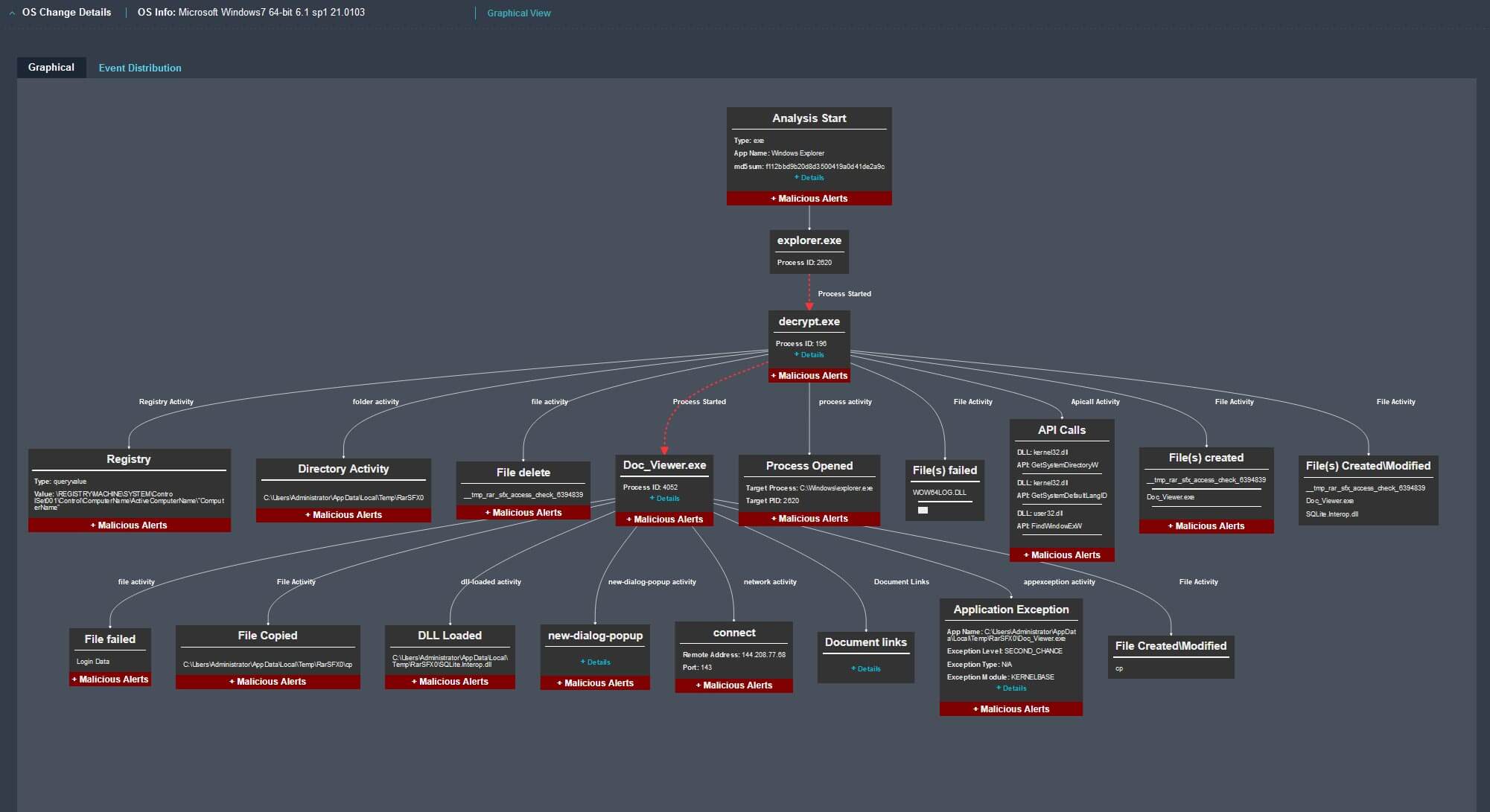
As one can see from the analysis above, the Trellix Email Security product can protect organizations against targeted spear-phishing and malware attacks. It analyzes and quarantines malicious emails if it finds unknown or advanced threats found hidden in attachments or URLs.
Trellix Network Security (NX)
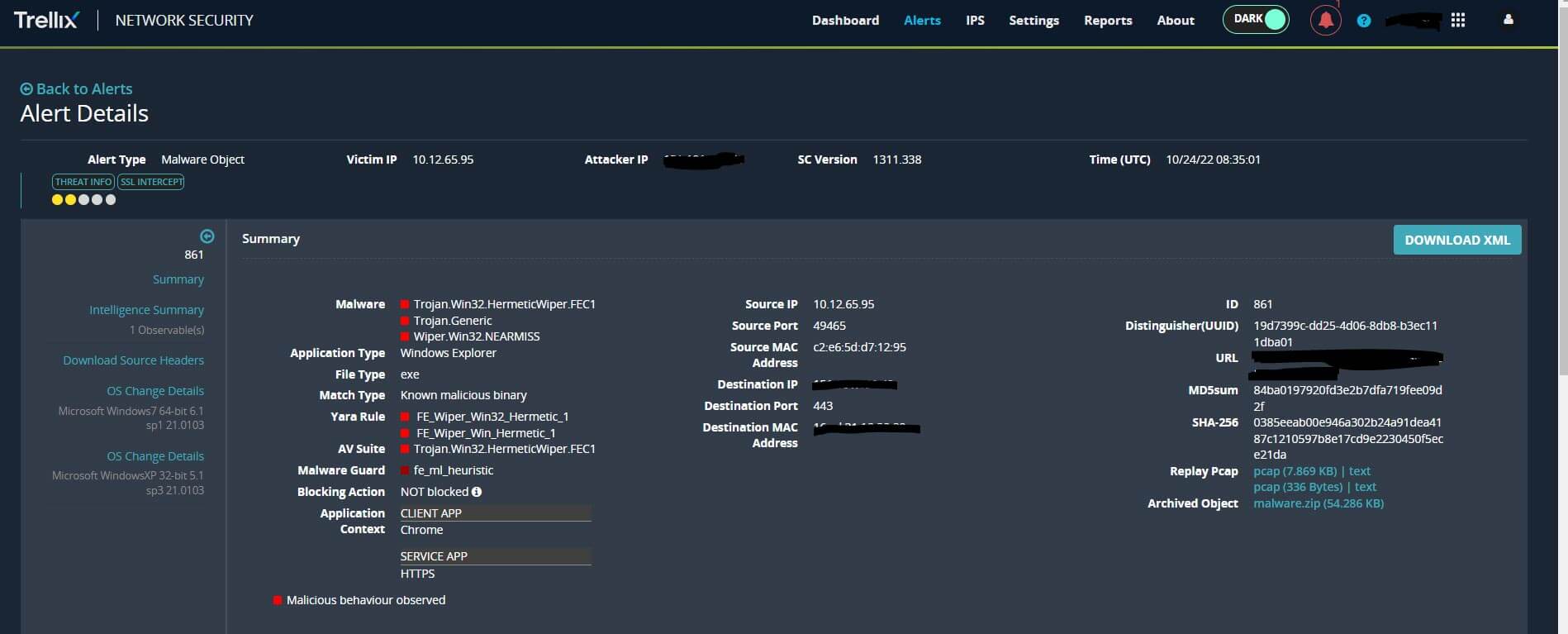
Trellix Network Security (NX) uses multiple analysis techniques to detect different wiper families that have been observed in the wild. The Multi-Vector Virtual Execution (MVX) engine detects zero-day, multi-flow, and other evasive attacks with dynamic, signature-less analysis in a safe, virtual environment. It stops infection and compromise phases of the cyber-attack kill chain by identifying never-before-seen exploits and malware. In the event of a wiper attack, Trellix NX will detonate the malware, extract and submits suspicious network traffic to the MVX engine for a definitive verdict analysis. Response actions include automatically blocking inbound exploits and outbound multi-protocol call backs.
Alerts detected by Trellix Email Security (EX or ETP Cloud)/Network Security (NX) are shared to Trellix Endpoint Security (HX) for additional detection on endpoints.
Detecting lateral movements with Trellix NX “SmartVision”
As the threat landscape continues to change and preventive measures become less reliable, breach detection is becoming more critical—especially as threat actors improve their ability to stealthily move through networks. The anatomy of the lateral attack lifecycle presents many challenges that existing security solutions can’t completely address. But Trellix has identified unique indicators and actions that denote inside efforts to steal data. Trellix used this intelligence to develop SmartVision to detect what used to be undetectable—lateral attack movements. And included with Network Security, SmartVision can be deployed in a variety of network architectures, giving your enterprise visibility into lateral threat actions and helping your business stay secure when threats go sideways.
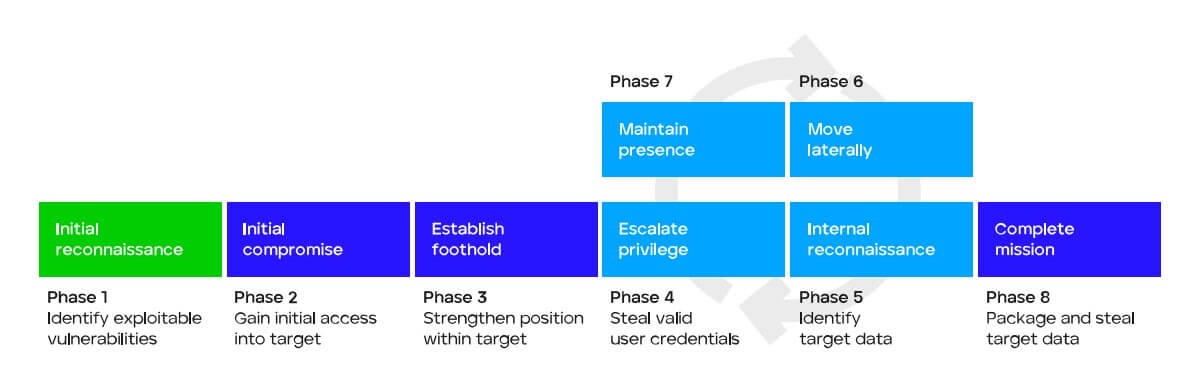
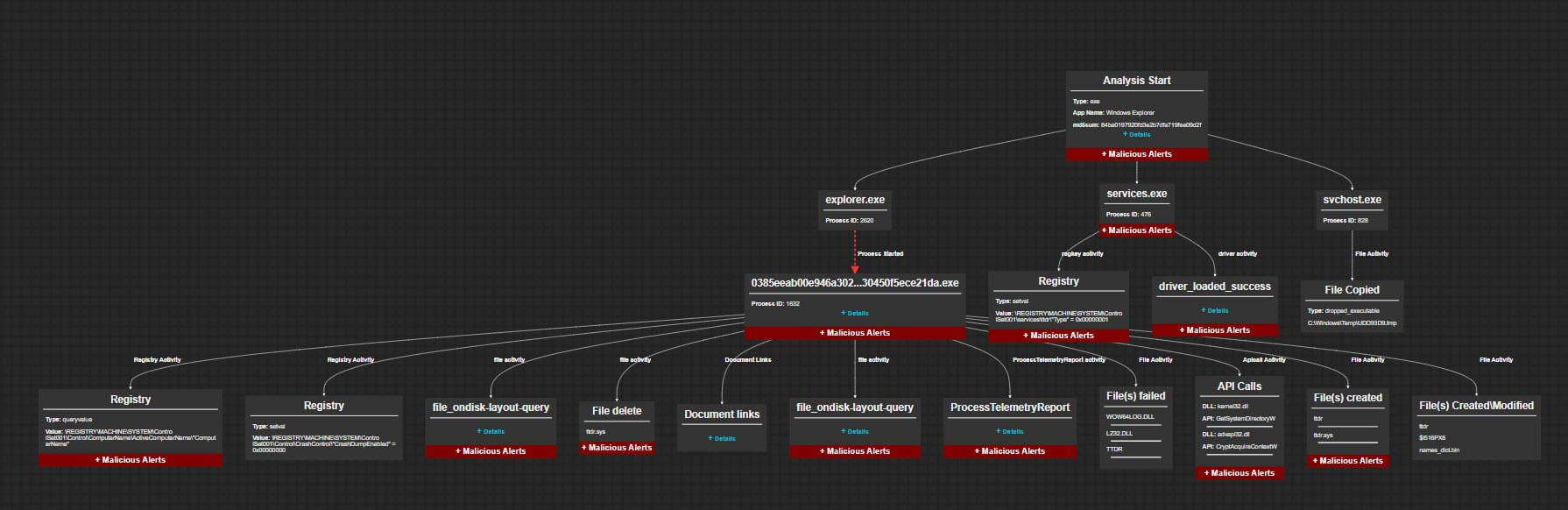
SmartVision detects many malicious activities including the spread of ransomware and wipers within your enterprise network. Because of the unique characteristics exhibited by attackers’ movements during the lateral attack lifecycle, SmartVision can key in on specific activities to trigger an alert. Let’s take the HermeticWiper destructive malware which was targeting several organizations in Ukraine as an example. HermeticWiper is the destructive payload, while HermeticWizard is the tool that leverages WMI and SMB in order to spread to additional hosts. The malware was used to spread to other computers via WMI and SMB, making systems inoperable by corrupting data and encrypting files. The network was also infected with the legitimate RemCom and Impacket tools.
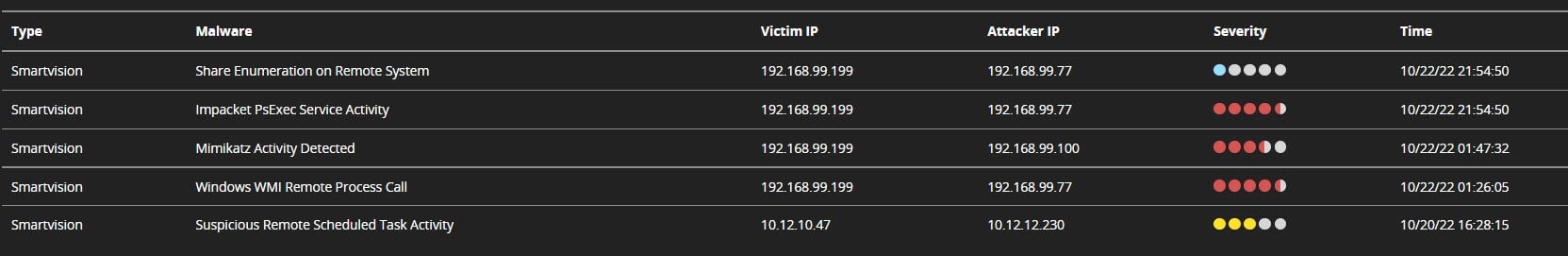
Let’s look at the “Impacket PsExec Service Activity” alert. Impacket’s PsExec offers PsExec like functionality. In this case, Impacket uses the RemComSvc utility. Threat actors commonly leverage Impacket tools to move laterally and execute commands on remote systems. SmartVision can track and detect lateral threats propagating within the network. In this example, we can see the Server Message Block (“SMB”) protocol communication between two endpoints within the network.
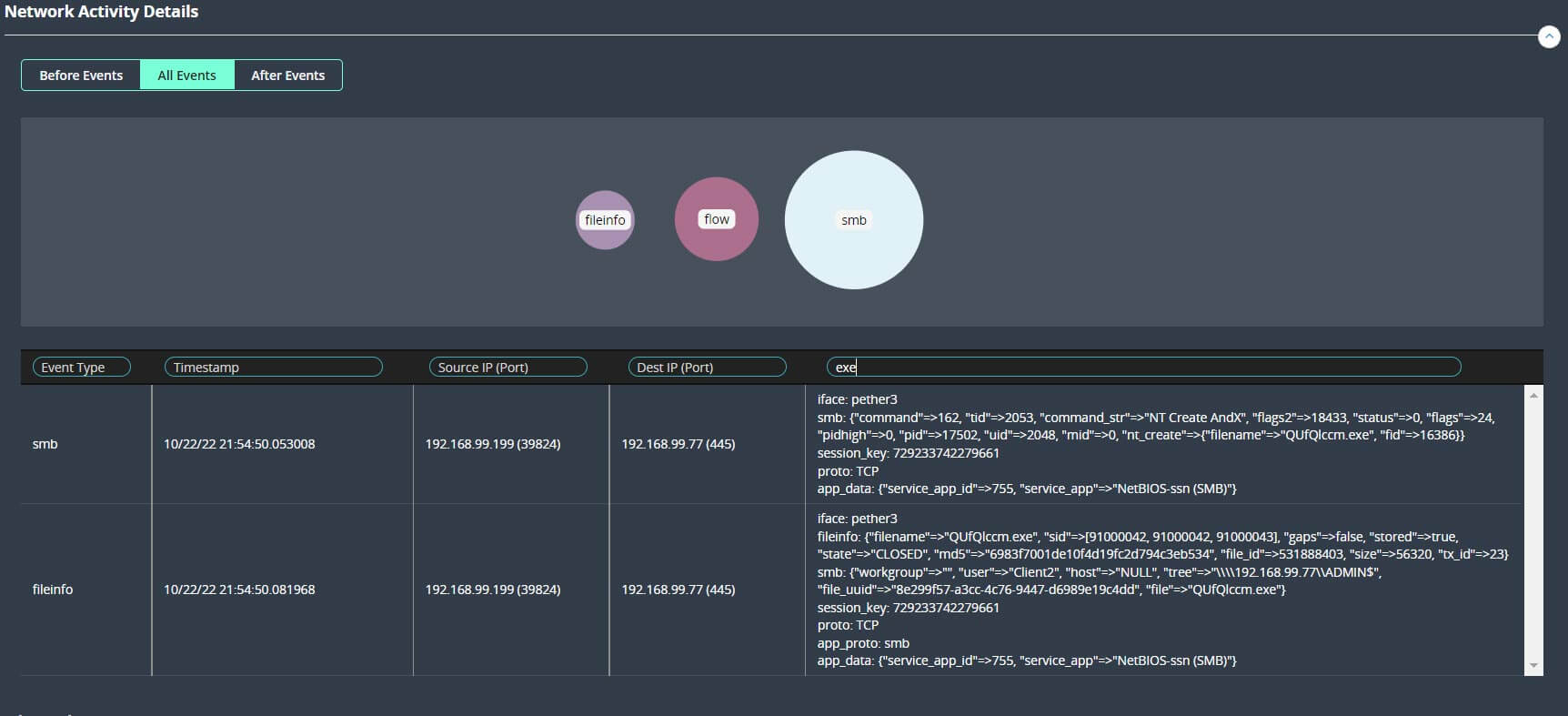
During the lateral movement phase, SmartVision identifies traffic over SMB protocols where threat actors use the SMB v1 and SMB v2 protocols to transfer malware and tools. In our example it extracted and identified the uploaded RemComSvc binary “QUfQlccm.exe “(MD5: 6983f7001de10f4d19fc2d794c3eb534) as Malware.Binary.
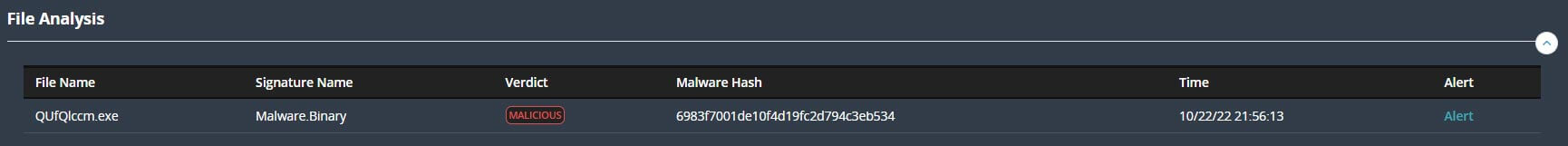
The attack uses SMB version 1 and TCP port 445 to propagate. Threat hunters can identify the network base events which contributed to the SmartVision correlated alert.
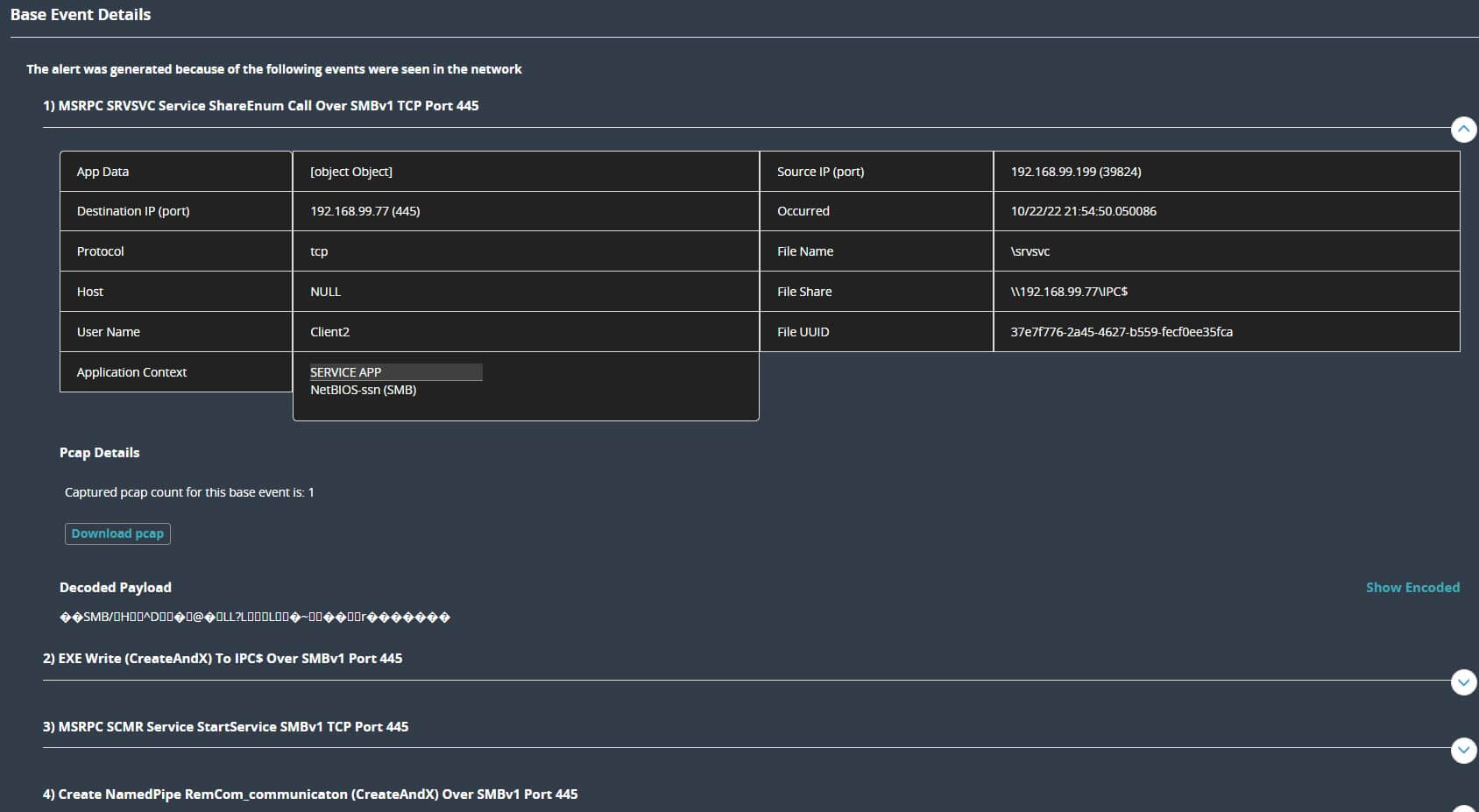
Trellix Sec Ops Platform
It is imperative that security teams have visibility into what's happening across the business so they can respond to and investigate security incidents including destructive wiper attacks. Trellix Helix can analyze events in over 650 security and business tools and is enriched with Trellix expertise to identify the threats happening in an organization. Trellix Helix augments endpoint, email, network, cloud and third-party alerts with intelligence, correlation to the endpoint, automation, and investigative tips.
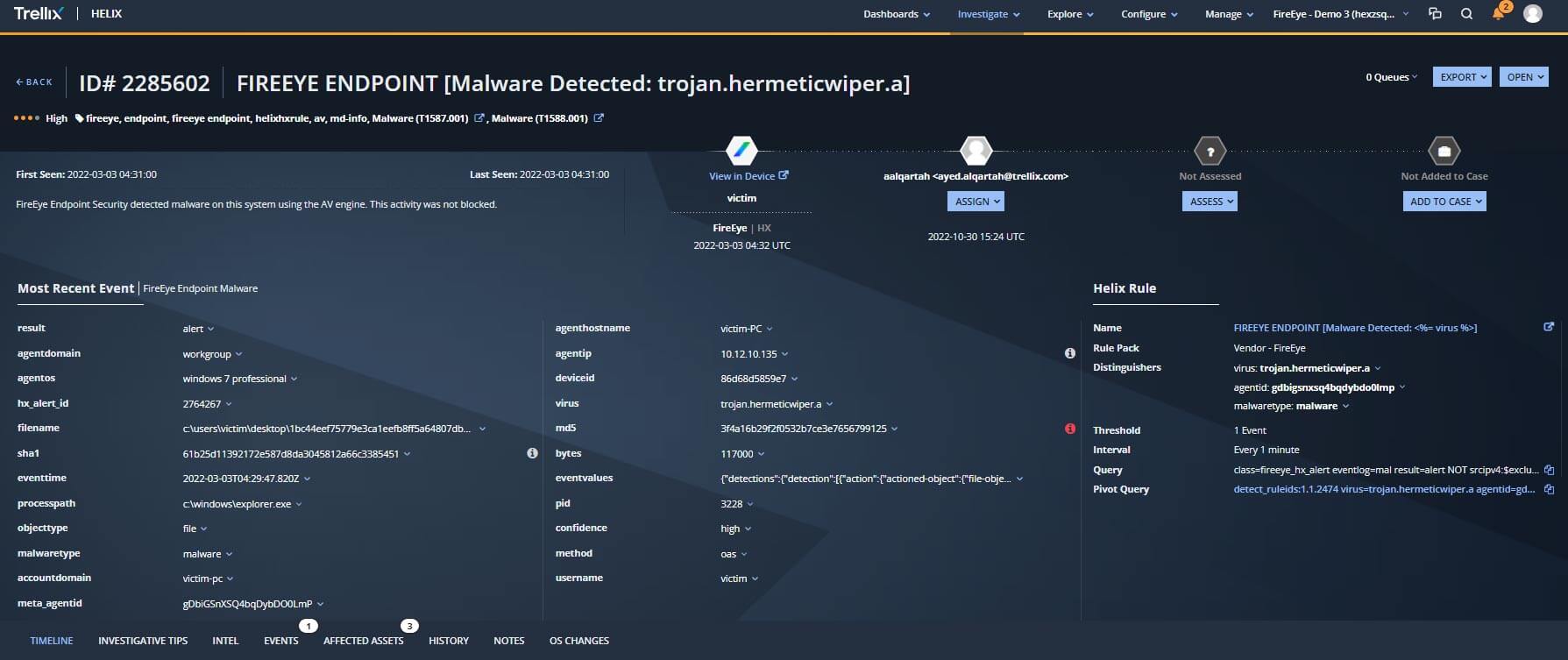
Detecting advanced multi-vector, multi-stage attacks requires context and correlation across multiple data sources so that the right alerts and telemetry is presented to the SOC analyst for effective triage, scoping of the threat, and effective incident response.
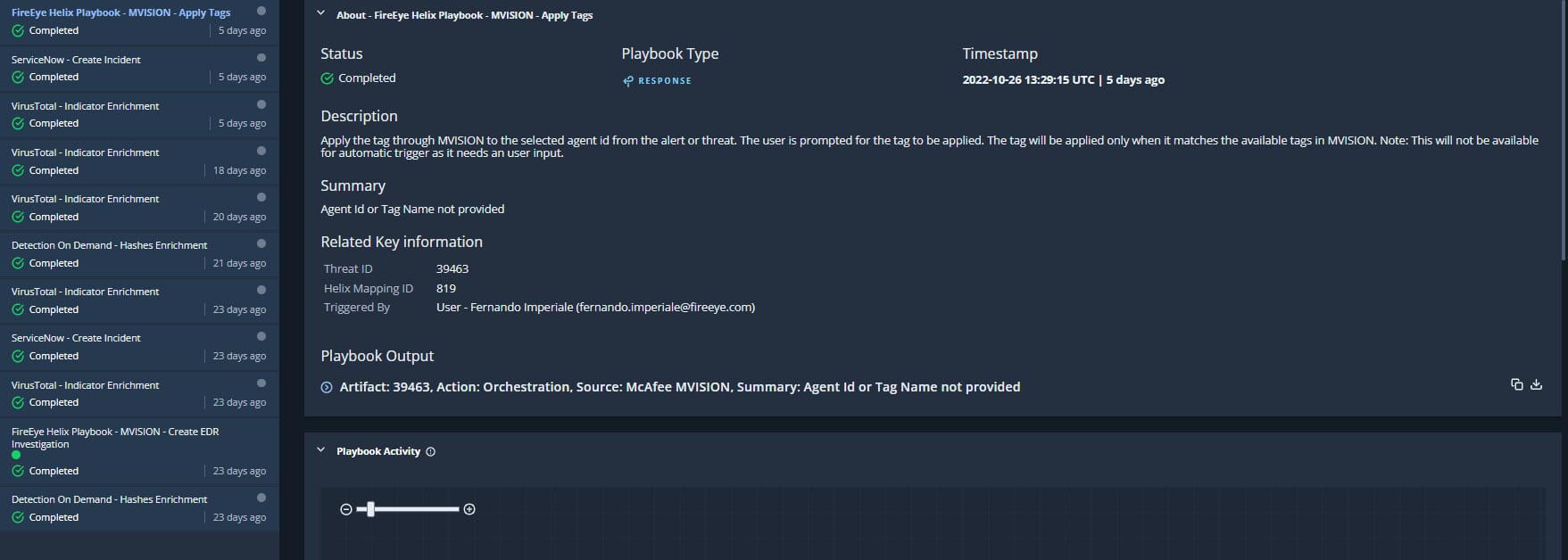
Conclusion
Cyber warfare weapons (including destructive wipers) will be part of every geopolitical conflict. Hence, governments and critical infrastructure organizations must improve their cyber defenses and implement cybersecurity best practices if they don’t want their mission-critical systems or valuable data to be wiped out.
Threat actors will continue the abuse of OS binaries and third-party tools to accomplish many of their objectives. The Trellix Fall 2022 threat report analyzes cybersecurity trends and attack methods from the third quarter of 2022. Living off the Land continues to grow with Windows Command Shell/CMD leveraged in 38% of LotL attacks, followed by PowerShell (37%), Schtasks (21%), WMI/WMIC (18%), and Rundll34 (13%). Furthermore, third-party tools continue to be of interest to threat actors when performing tasks such as remote access, infrastructure discovery, lateral movement, stealing credentials, bypassing defenses, data collection, exfiltration, etc. The report also states that “Red Teams” tools such as (but not limited to): Cobalt Strike, BruteRatel, and Silver Implant are increasingly being used by threat actors for executing tasks from initial access to data exfiltration.
Targeted and destructive attacks are becoming increasingly multivector, and linear security solutions that identify just one vector are no longer sufficient. This is where Trellix Extended Detection and Response (XDR) platform can make a difference. It provides cross-product visibility, automated threat detection and response, and prioritization with advanced analytics.
Trellix is continuing to add protections to our products via reputation and content updates as new malware variants and behavior indicators are discovered. Insights will continue to be updated with the latest threat campaigns.
RECENT NEWS
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
-
Oct 23, 2025
Trellix CyberThreat Report Reveals Blurring Lines Between Nation-State Espionage and Financially Motivated AI Attacks
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
