Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more

Trellix Global Defenders: Follina — Microsoft Office Zero-Day (CVE-2022-30190)
By Taylor Mullins, Robin Noyce, Benjamin Marandel · June 3, 2022
Trellix is continuing to monitor the threat activity associated with the Microsoft Office Zero-Day vulnerability that has been dubbed “Follina.” Chinese-linked Threat Actors are actively exploiting this zero-day vulnerability to execute malicious code remotely. At the time of this writing there is no official patch from Microsoft, but steps and protections can be put into place to mitigate against the attacks utilizing this Microsoft vulnerability.
Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability
The method at which these attacks are taking place is using malicious Word documents that execute PowerShell commands via the Microsoft Diagnostic Tool (MSDT). The ‘Follina’ zero-day features a remote code execution that works without elevated privileges, does not require macro enablement to execute binaries or scripts, and can bypass Windows Defender detection. Opening a Microsoft Word document in preview mode in Explorer is another method to detonate the malicious code which provides a vector for the exploitation to take place outside of the Protected View that Microsoft is reporting will prevent the attack. Furthermore, it is a signed binary, which enables the code to bypass windows validation controls. The Follina vulnerability is exploitable with Office 2013, 2016, 2019, 2021, Office ProPlus and Office 365.
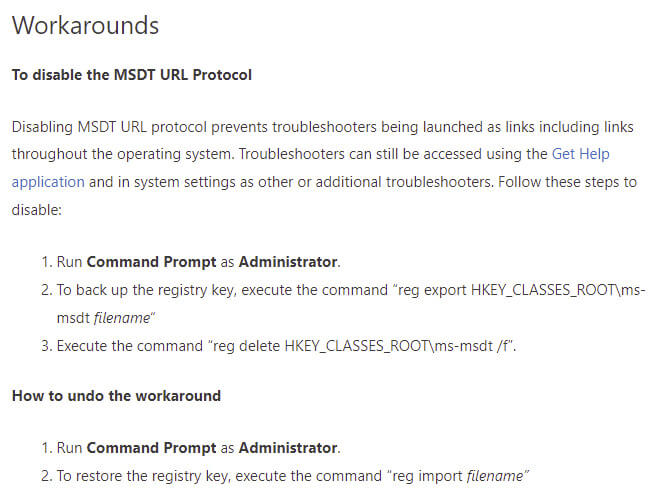
Microsoft recommended workaround for microsoft support diagnostic tool (MSDT)
Microsoft has released guidance on disabling the Microsoft Diagnostic Tool (MSDT) URL protocol. The Microsoft Support Diagnostic Tool (MSDT) is a tool designed to collect information to send to the Microsoft Support.
CISA: Microsoft Releases Workaround Guidance for MSDT "Follina" Vulnerability
Trellix product protections for follina vulnerability
Trellix is continuing to add protections via threat feeds and content updates to the Trellix products as Indicators of Compromises (IOCs) and behavioral techniques are detected in the wild. In addition, there are initiative-taking steps that can further protect your environment against the attacks targeting the Follina zero-day vulnerability.
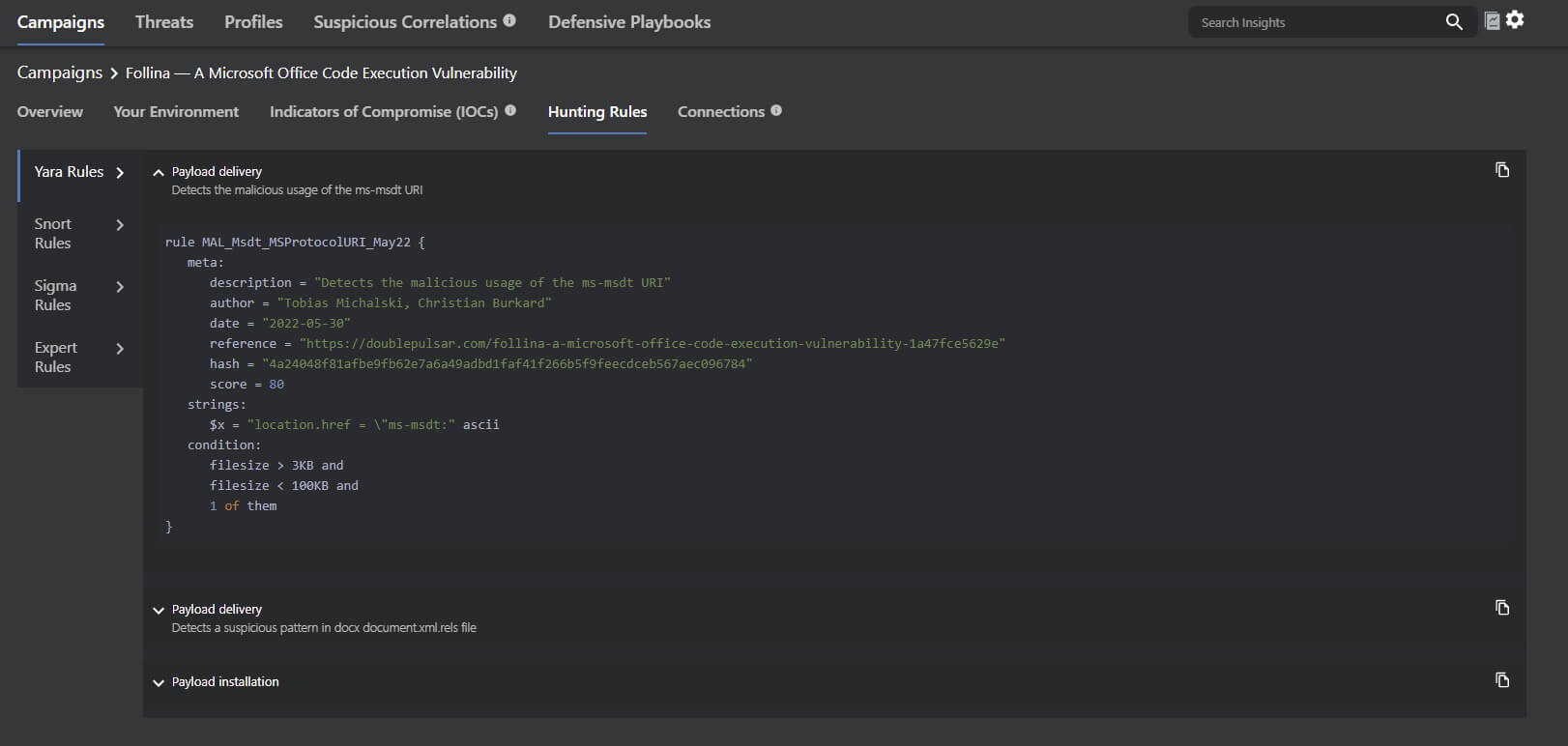
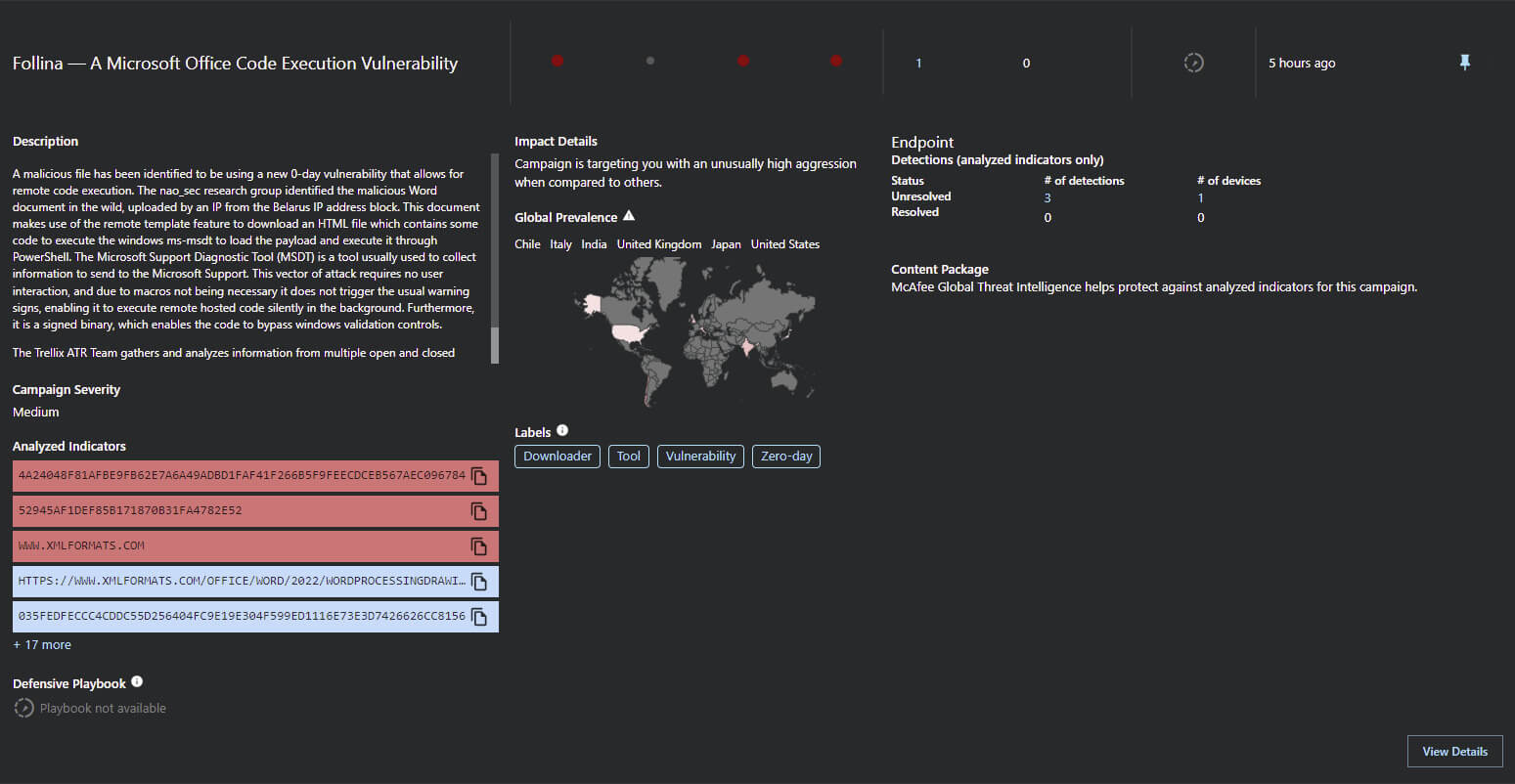
Follina zero-day threat intelligence and hunting rules
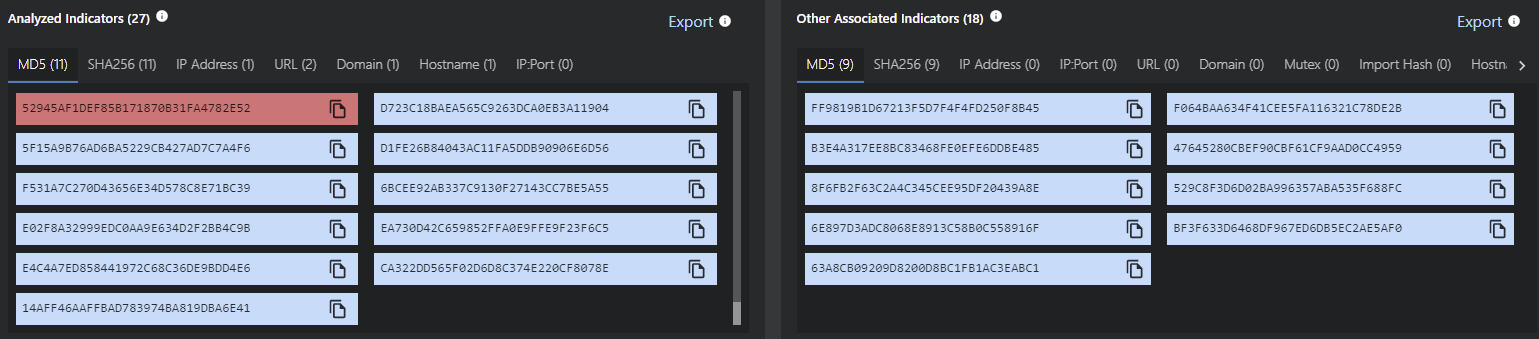
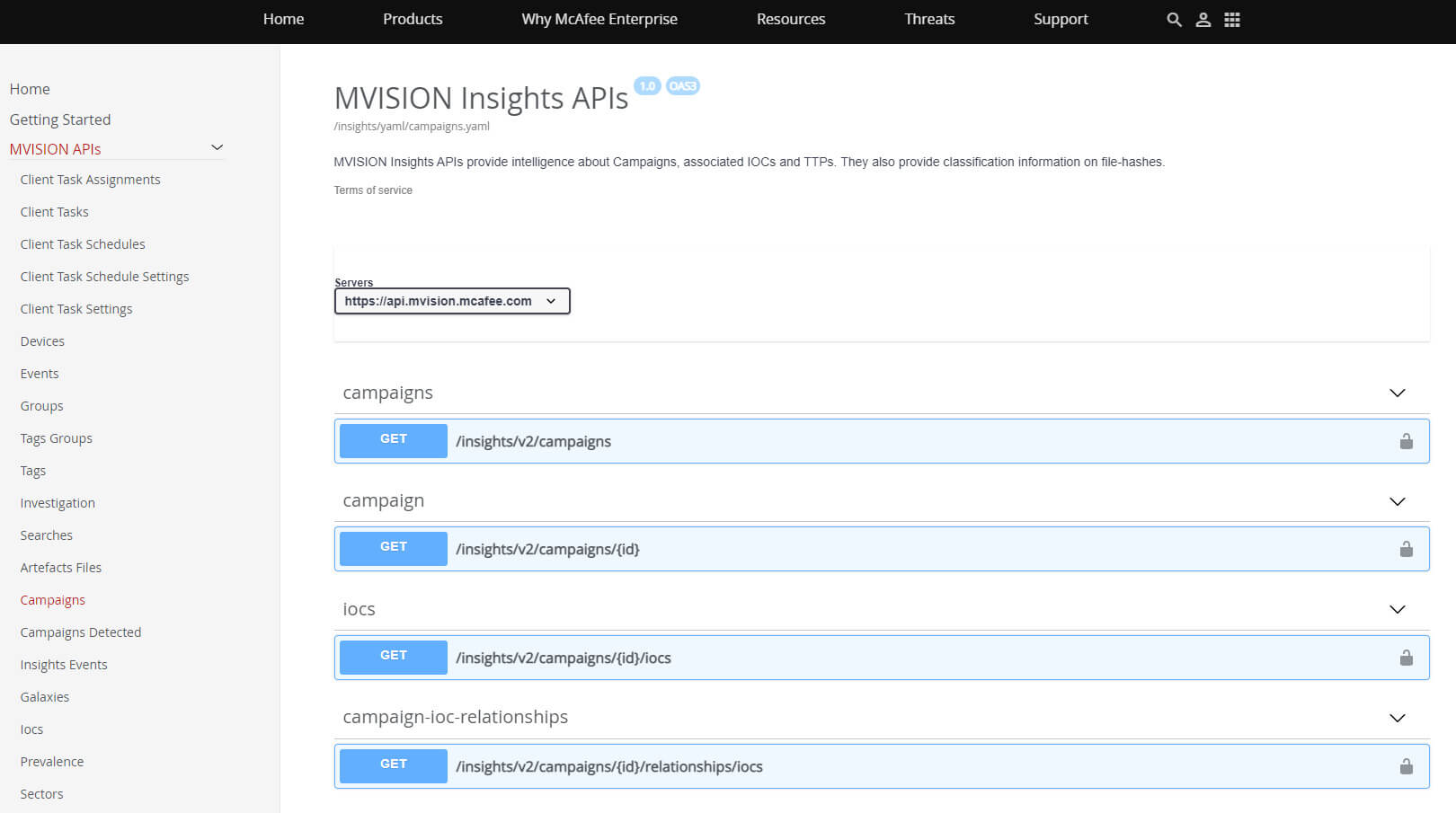
MVISION Insights is continually updated with the latest threat intelligence and known indicators that are being discovered related to the Microsoft zero-day vulnerability. Additionally, applying hunting rules and threat intelligence across the security stack is key for early detection and identification of the Tactics, Techniques, and Procedures (TTPs) associated with Follina.
MVISION Insights Campaign Name - Follina — A Microsoft Office Code Execution Vulnerability
Utilizing expert and behavioral rules in trellix endpoint security
Trellix ENS Threat Prevention and Adaptive Threat Protection (ATP) monitor Microsoft Word process activity and the start of a child Command line processes is detected and blocked (if configured to) by ENS ATP. Trellix ENS can also block common processes like cmd.exe from being spawned by Microsoft Office applications in a suspicious manner. The following rules in Trellix ENS Exploit Prevention and Adaptive Threat Protection (ATP) are recommended to observe or block behavioral activity associated with exploitation techniques.
Exploit Prevention Signature 6113: T1055 - Fileless Threat: Reflective Self Injection
Exploit Prevention Signature 6127: Suspicious LSASS Access from PowerShell
Exploit Prevention Signature 6143: T1003 - Attempt to Dump Password Hash from SAM Database
Exploit Prevention Signature 8004: Fileless Threat: Malicious PowerShell Behavior Detected
ATP Rule 239: Identify suspicious command parameter execution
ATP Rule 263: Detect processes accessing suspicious URLs
ATP Rule 301: Blocks cmd.exe from being spawned by office applications
ATP Rule 332: Prevent certutil.exe from downloading or decoding files with suspect extensions
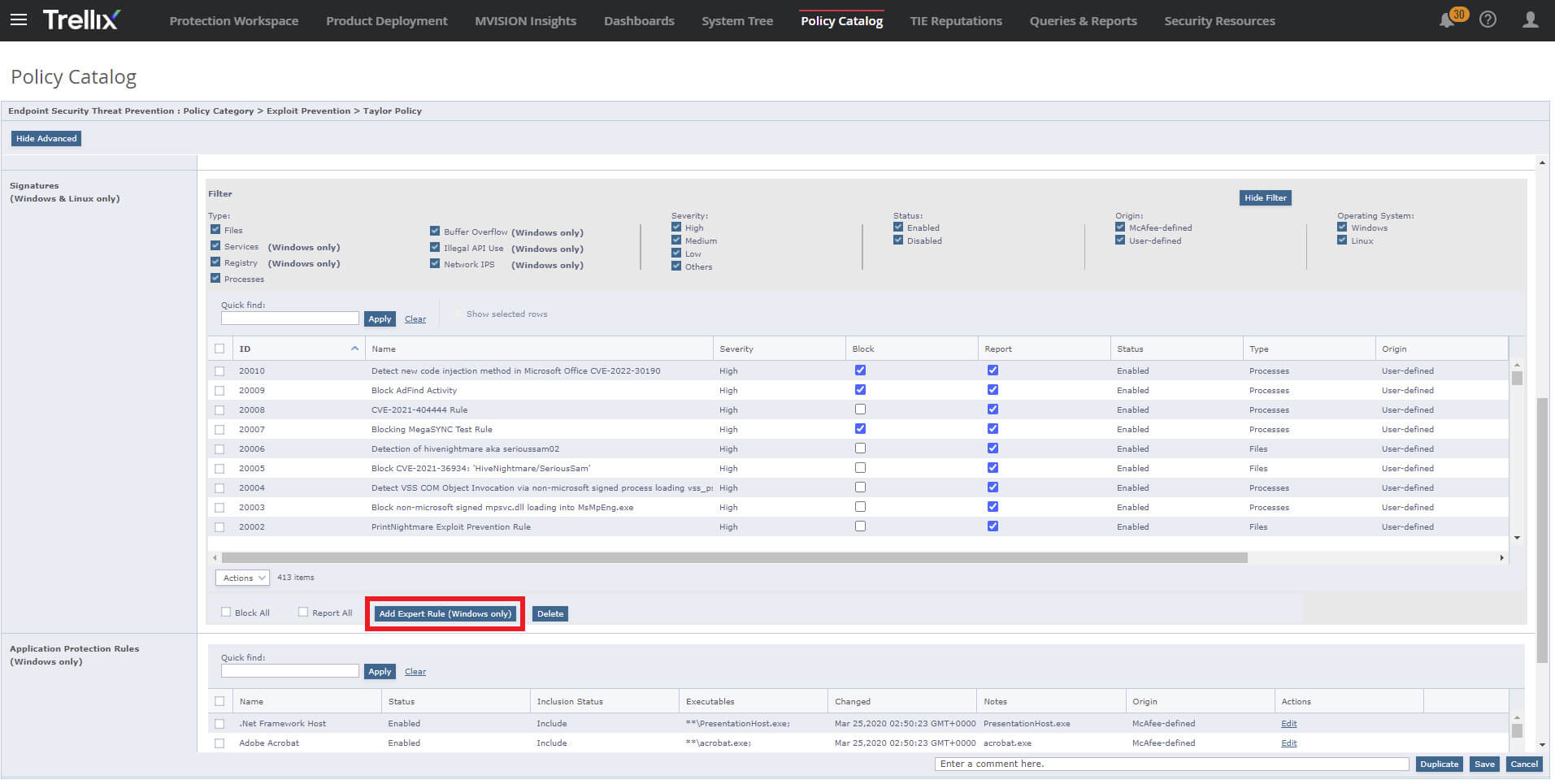
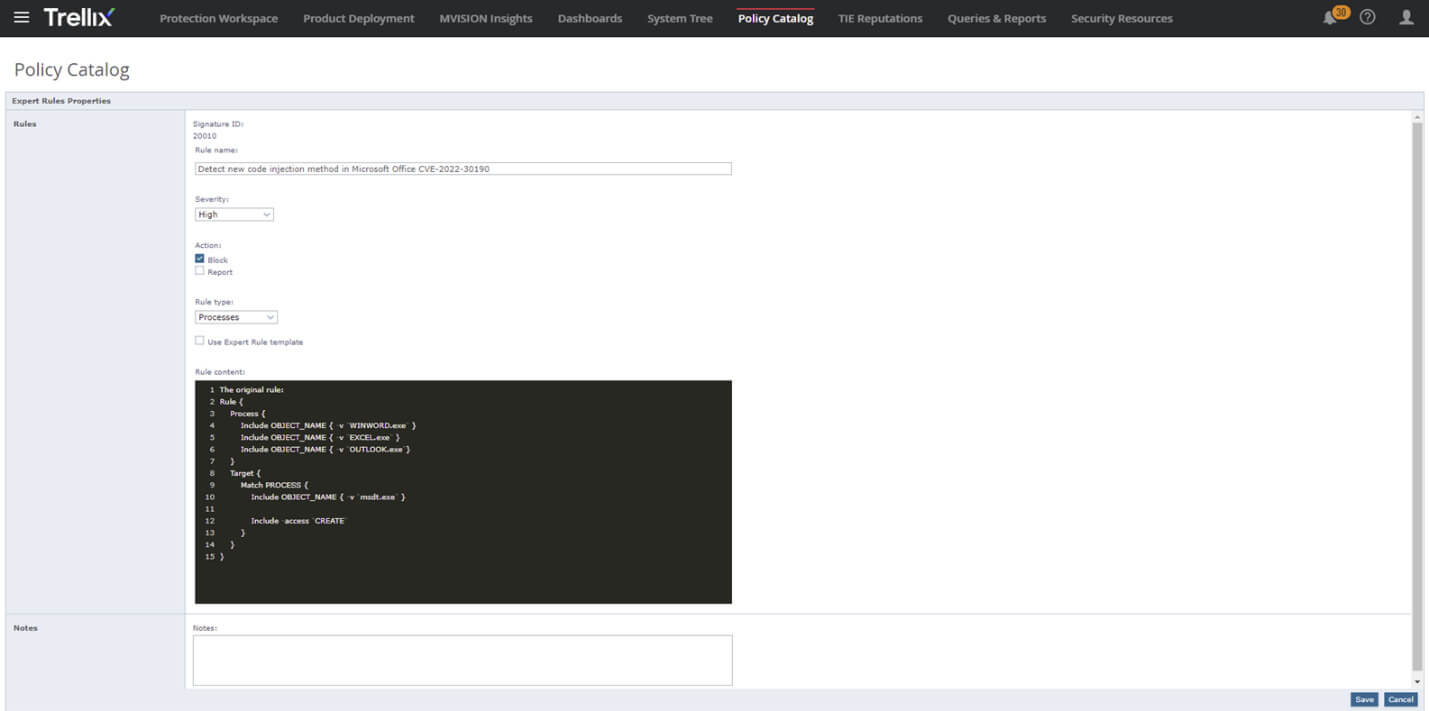
The Trellix Advanced Threat Research (ATR) team has also created the following ENS Expert Rule to prevent techniques associated with exploitation. Outlined below are several screenshots on how to create this specific Expert Rule in Trellix ENS. Per standard practice, we recommend that customers test this rule in Report Only before moving to Block mode.
Detect new code injection method in Microsoft Office CVE-2022-30190
How to Use Expert Rules in ENS to Prevent Malicious Exploits
Hunting for suspicious behavior with MVISION EDR
MVISION EDR has the capability to search across historical and real-time data on endpoints to identify specific activity associated with exploitation and the MSDT process. Several examples and queries are noted below for using Historical and Real-time searches to analyze the Microsoft Diagnostic Tool (MSDT) process activity and interaction with CMD and PowerShell.
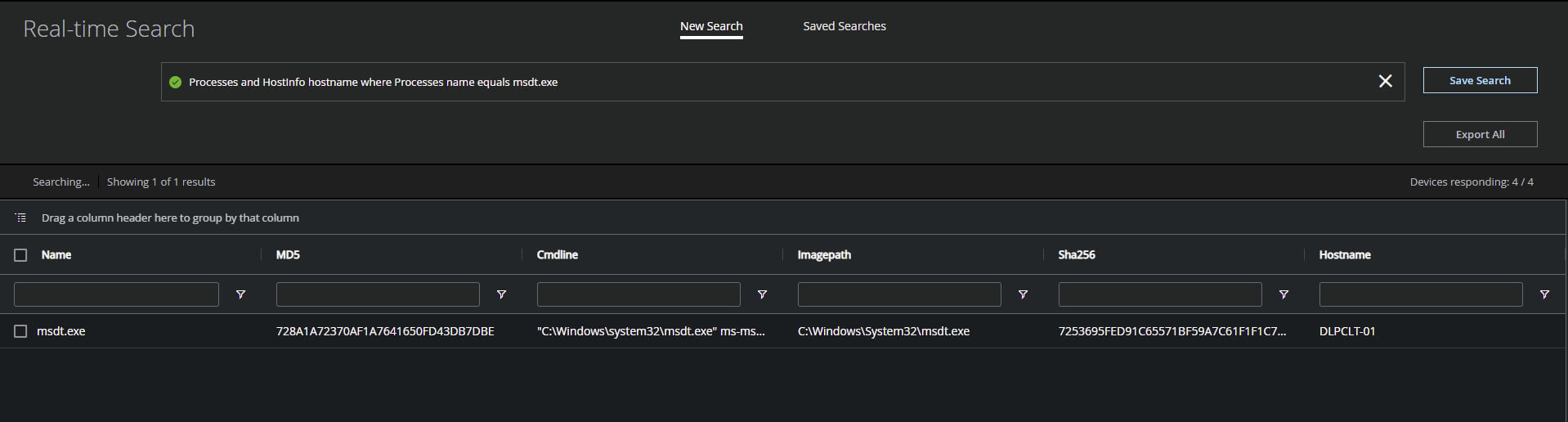
Processes and HostInfo hostname where Processes name equals msdt.exe – Real-time search query to locate activity specific to the Microsoft Diagnostic Tool (MSDT) process
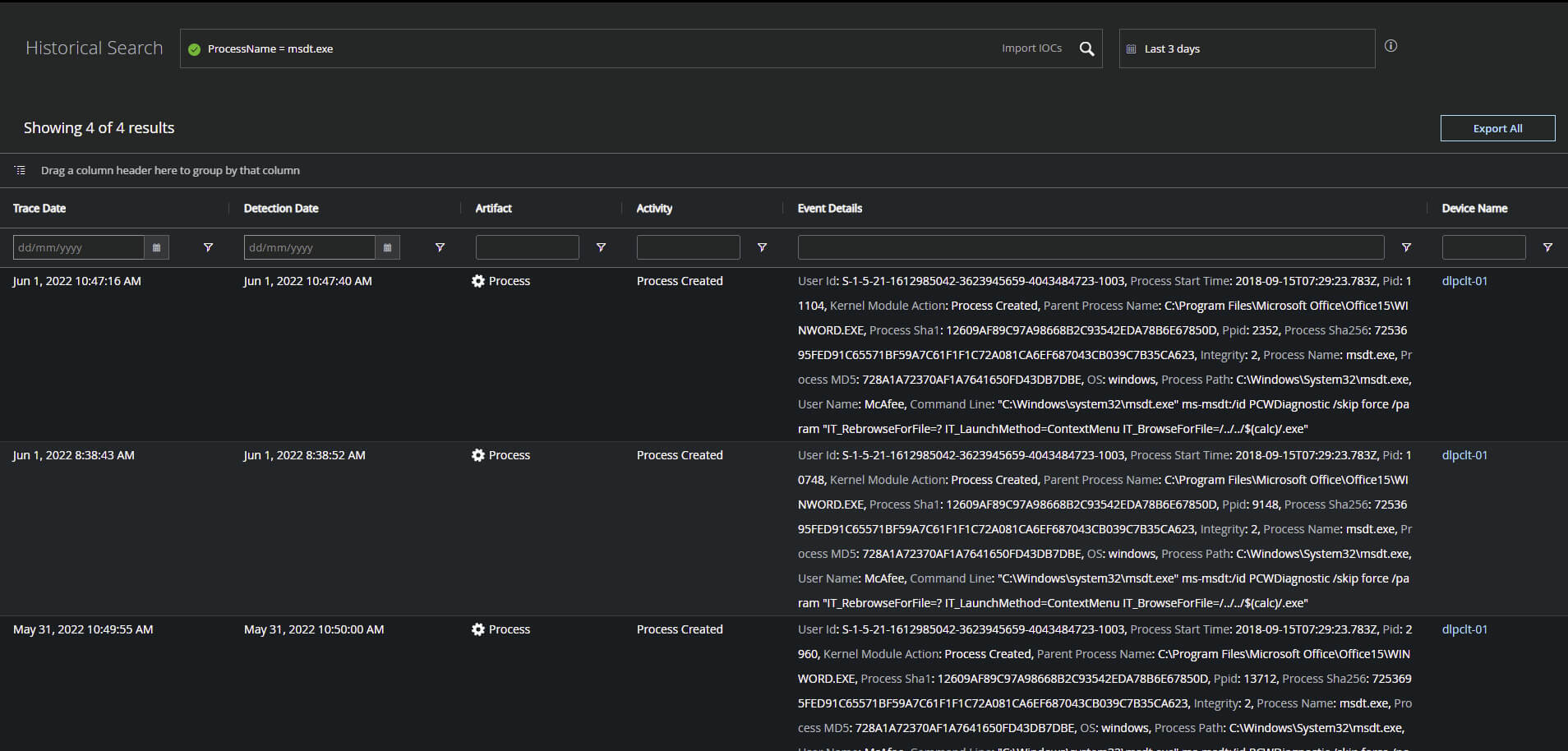
ProcessName = msdt.exe – Historical search string to locate prior activity from MSDT.exe across your endpoints even if they are currently offline.
Trellix network security platform signature release
Trellix has released a User-Defined Signature (UDS) for the Network Security Platform (NSP) to provide an immediate solution to this security advisory. Trellix writes and tests these signatures with the objective of a quick turnaround.
Additional resources
Microsoft: Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability
Huntress: Rapid Response: Microsoft Office RCE - “Follina” MSDT Attack
Bleeping Computer: Windows MSDT zero-day now exploited by Chinese APT hackers
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.