Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Harnessing the Power of AI in SOAR: Enhancing Incident Response and Automation
By Trellix · June 08, 2023
This story was also written by Tyler Horschig.
In today's complex cybersecurity landscape, organizations face an overwhelming number of security alerts and incidents that require swift and effective response. Security Orchestration, Automation, and Response (SOAR) platforms have emerged as valuable tools to streamline security operations by automating repetitive tasks and enabling seamless collaboration between security teams. Integrating artificial intelligence (AI) capabilities into SOAR playbooks takes efficiency and effectiveness to new heights, revolutionizing incident response and mitigating potential threats. In this post, we cover a few of the many possibilities of AI in SOAR playbooks, highlighting the transformative potential it brings to security operations.
Summarization of an incident
Harnessing the power of machine learning and advanced analytics, AI systems can analyze security data and swiftly generate concise incident narratives. Leveraging natural language processing and intelligent contextualization, AI can sift through diverse data sources, including logs, alerts, and threat intelligence, to extract meaningful insights. This allows security analysts and incident responders to quickly grasp the nature of an incident, its potential impact, and the necessary steps for mitigation. By providing easily understandable incident descriptions, AI in SOAR empowers organizations to make informed decisions and take swift actions, fortifying their defenses and minimizing the impact of security breaches.
Recommendations for remediation
AI can learn from historical incident data and past remediation actions to provide recommendations for effective remediation strategies. By analyzing the characteristics and similarities between current and previously resolved incidents, AI can suggest appropriate remediation steps based on proven best practices. These recommendations can include specific actions such as isolating compromised systems, applying patches, updating security configurations, or deploying additional security controls. By leveraging AI's ability to process large volumes of data and derive actionable insights, security teams can respond swiftly and efficiently to mitigate the incident's impact and prevent similar future occurrences.
Recommendations for protections
In addition to remediation recommendations, AI can also provide guidance on improving security postures to prevent future incidents. By analyzing incident data, AI can identify vulnerabilities, misconfigurations, or gaps in security controls. Based on this analysis, AI can offer recommendations for enhancing defenses, such as implementing intrusion detection and prevention systems, tightening access controls, updating security policies, or conducting security awareness training. These proactive recommendations enable organizations to strengthen their overall security posture and mitigate the risk of future incidents.
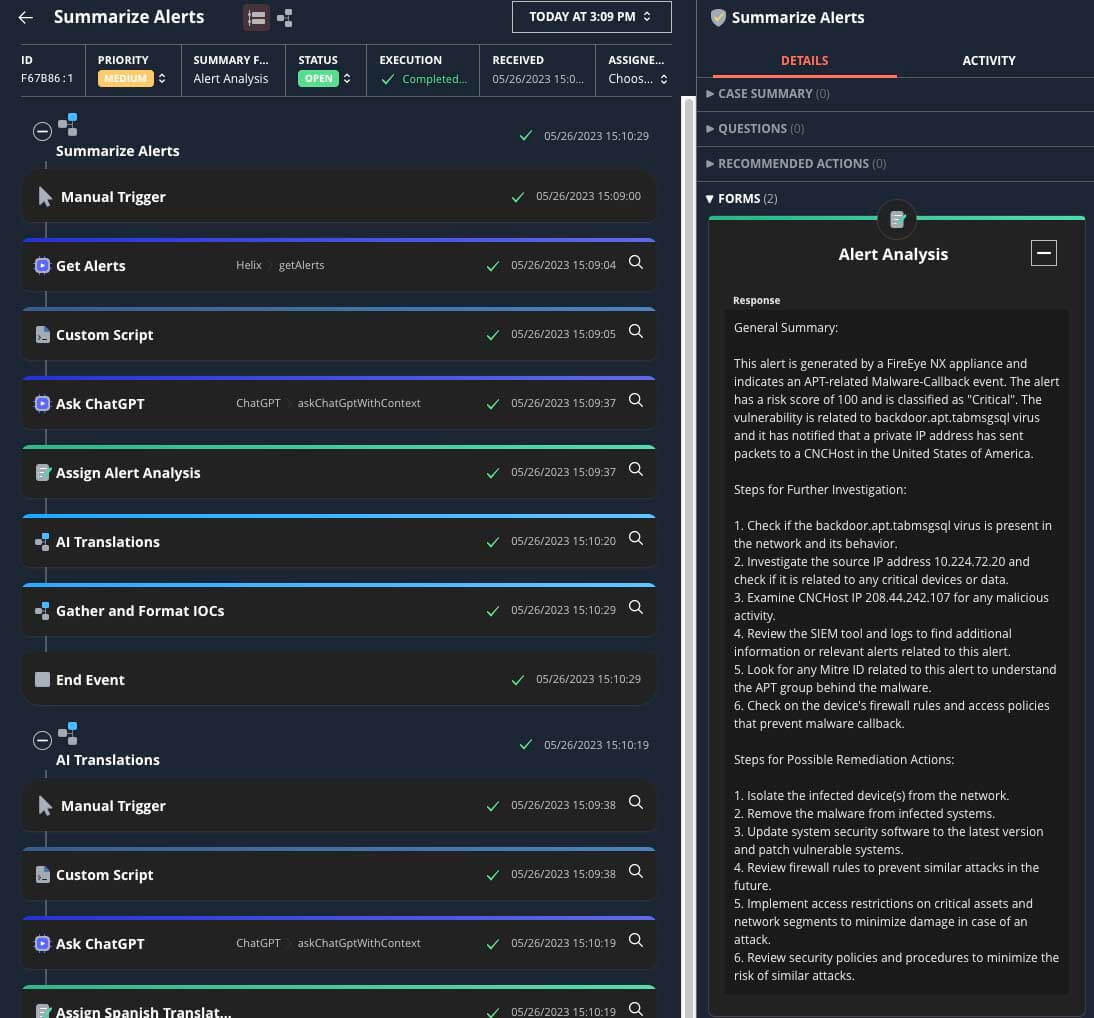
Multilingual support
AI's language processing capabilities enable SOAR platforms to support multiple languages, overcoming language barriers in incident response. Whether analyzing incident reports, extracting information from non-English sources, or communicating with global teams, AI can understand and process text in various languages. This multilingual support ensures that security teams can effectively handle incidents and collaborate seamlessly in diverse international environments, enhancing the overall effectiveness and reach of SOAR platforms.
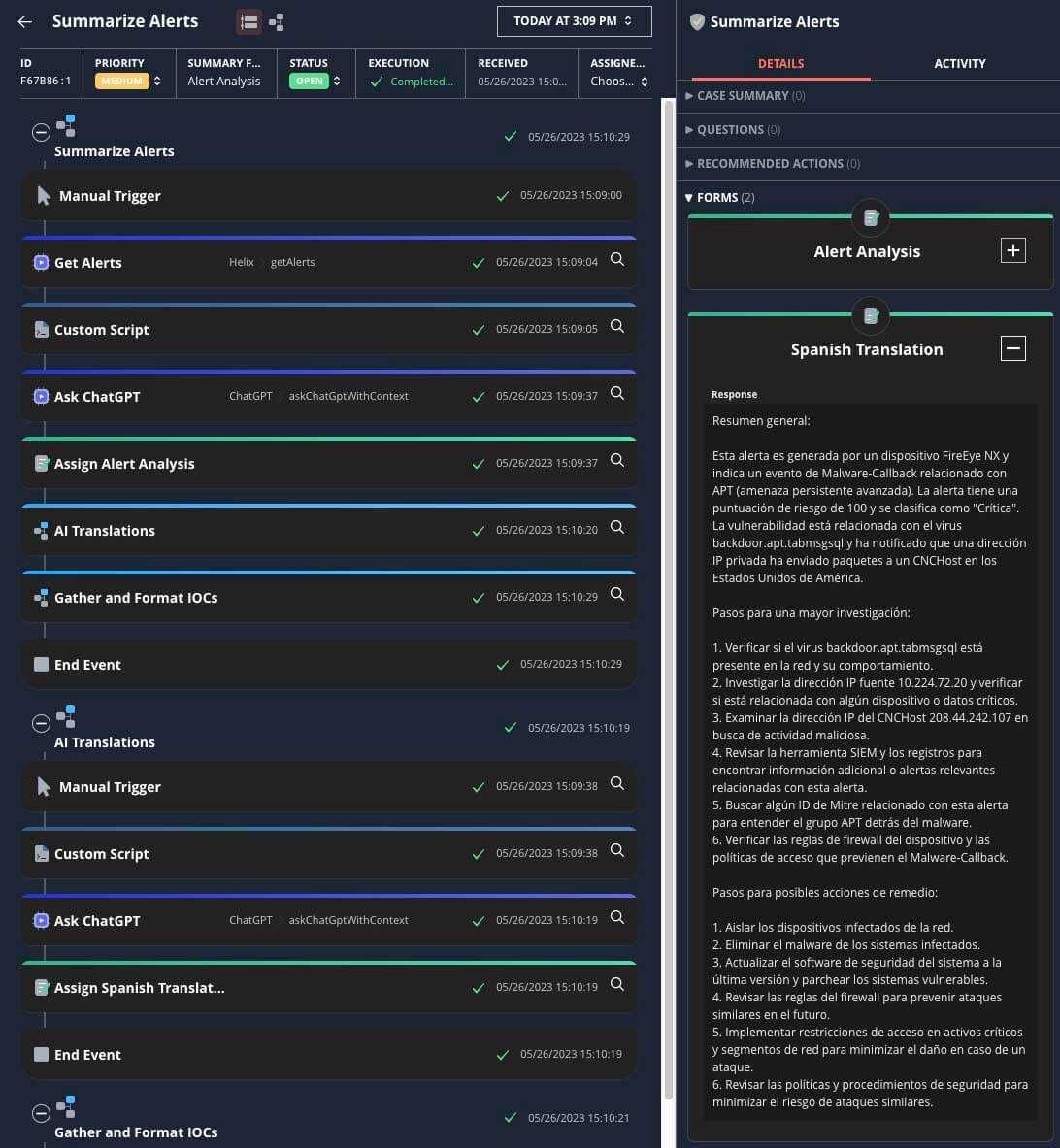
Automatic Data Manipulation
Gathering IOCs instead of using faulty regex
Traditional methods of extracting Indicators of Compromise (IOCs) using regular expressions (regex) can be error-prone and time-consuming. AI-powered algorithms can overcome these limitations by employing advanced techniques like natural language processing and machine learning to accurately gather IOCs. By analyzing textual data, network traffic, and behavior patterns, AI can identify and extract IOCs more reliably, reducing false positives and false negatives. This automated IOC extraction enhances the efficiency and accuracy of automations.
Data transformation
AI enables automatic data transformation, which is essential for normalizing and enriching security data within SOAR platforms. With varying data formats and structures from different sources, data transformation tasks can be complex and time-consuming for security teams. AI can automate these processes by identifying and mapping data attributes, performing data cleansing, and applying normalization techniques. This transformation simplifies data integration, enabling seamless correlation and analysis across different datasets. The enriched and standardized data ensures consistency in incident response, improving the effectiveness of automated workflows and decision making within the SOAR platform.
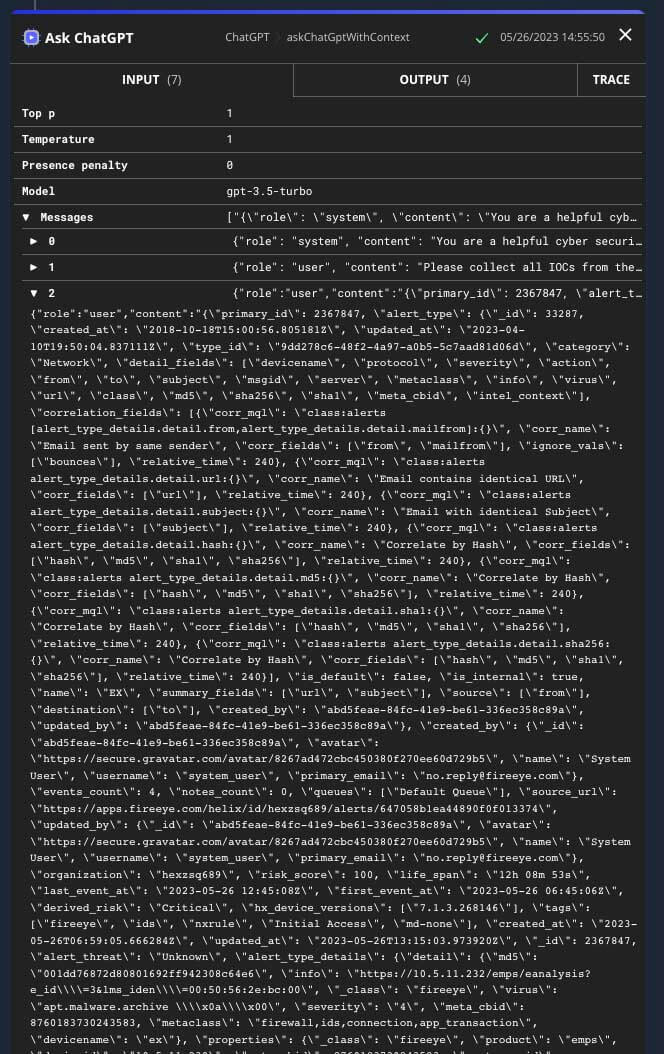
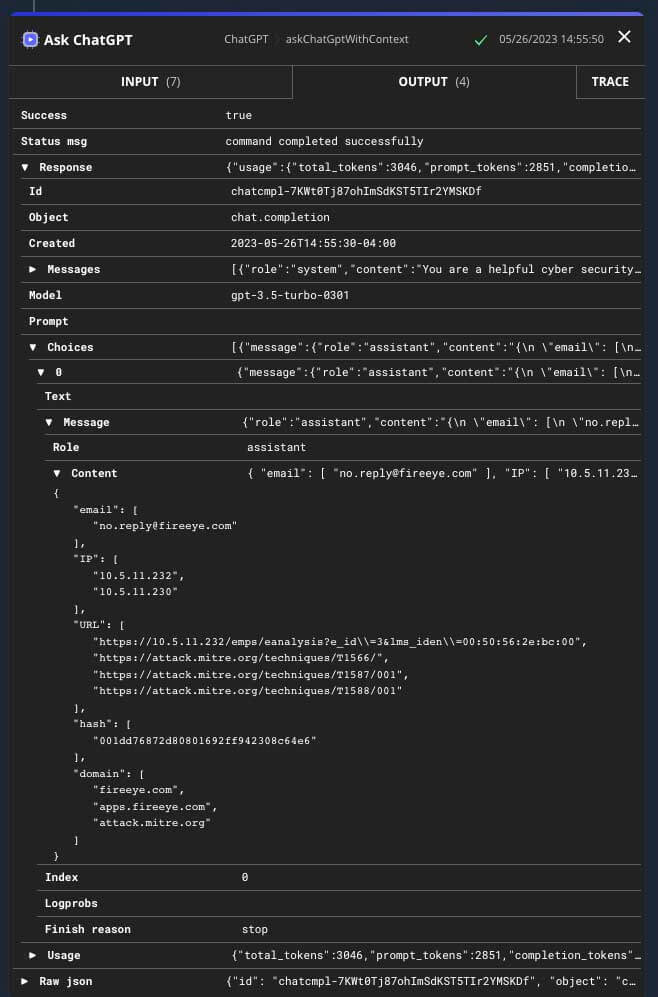
Automated Decision Making
AI-driven automated decision making plays a vital role in optimizing incident response processes by considering the available response actions and their potential outcomes. When faced with an incident, security teams often have multiple response actions at their disposal, such as blocking an IP address, quarantining a device, or launching a forensic investigation. AI can leverage historical incident data, threat intelligence feeds, and machine learning models to make informed decisions about the most appropriate response action. By analyzing the characteristics of the incident, its severity, the assets involved, and the organization's security policies, AI can determine the optimal course of action. This automated decision-making process helps security teams save valuable time and reduce the risk of human error that could arise from manual decision making.
AI Integration into Trellix Automated Response
Trellix’s integration with OpenAI for Automated Response allows you to utilize many of these ideas and more. You can follow the steps below to integrate OpenAI in your instance today.
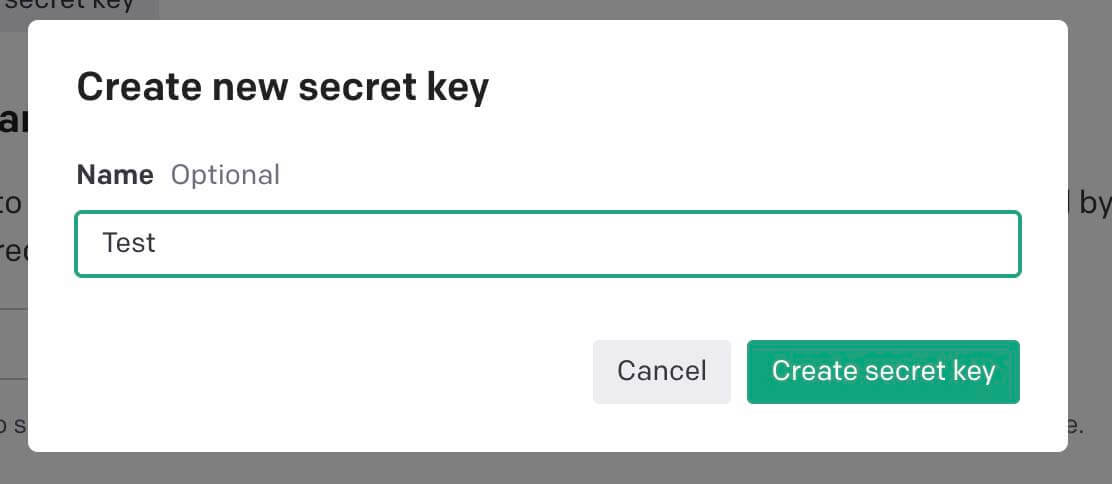
Obtain an OpenAI API key
- Login into https://platform.openai.com/login?launch
- Select API
- Select your profile icon
- Select view API keys.
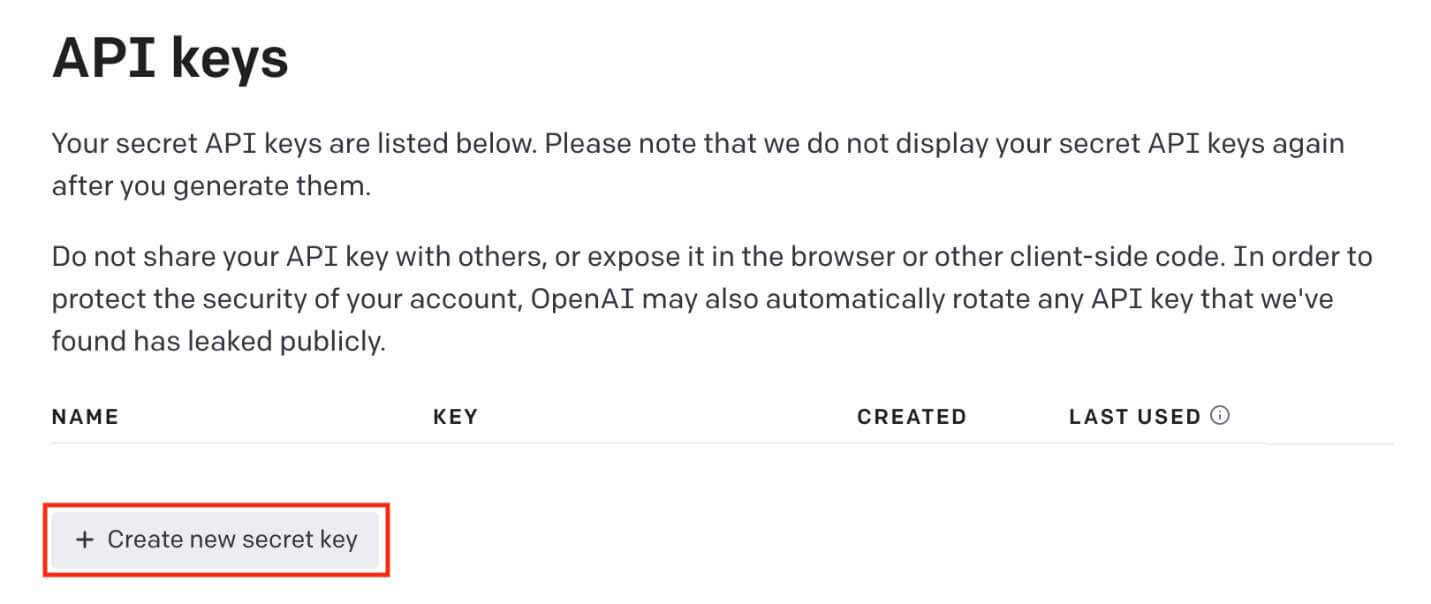
- Select create new secret key.
- Fill in a name for your API key.
- Save your newly created key for the integration.
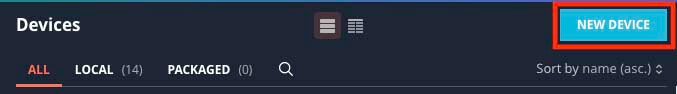
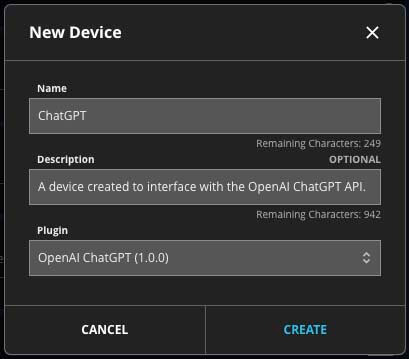
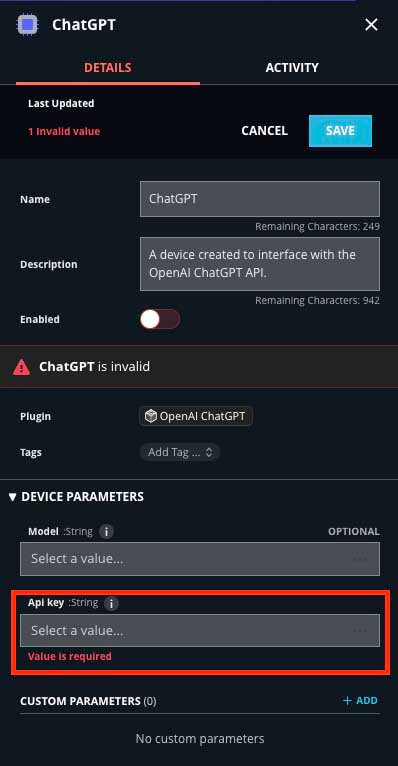
Configure the Integration in Automated Response
- Install the integration on your instance.
- Add a new device for the integration.
- Fill in the details for your device.
- Fill in your API key
- Save your configuration
-
a. For those who need to manually download the plugin, you can do this at the following URL: https://fireeye.market/apps/wBmqIEc2
-
b. For those with instances connected directly to the marketplace, you can one click install the integration directly from your plugin menu.
You are now ready to utilize the integration in your Trellix Automated Response playbooks! Do you want to discuss playbook use cases like these for your organization? Do you want help implementing playbooks in your organization to help automate time consuming tasks? If you answered yes to either of these questions, please reach out to your Trellix sales representative to schedule time to discuss options on how Trellix Professional Services can help!
NOTE: Be aware of what data is being sent to ChatGPT. All data sent to the AI is shared between all users of the API as the model use this data to learn and become more effective.
Want to see it all in action? Check out the video below.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.

