
Trellix Global Defenders: How to Defend Against Genesis Cookie Attacks
By Carlo Bolzonello, Filippo Sitzia · June 15, 2023
On the 4th and the 5th of April 2023, a law enforcement taskforce spanning agencies across 13 countries – including the FBI, Europol and the Dutch Police – disrupted the infamous browser cookie market known as Genesis Market and approached about 700 of its top users. Based on the information gathered, criminal users were either arrested or approached for serious knock-and-talk conversations. Genesis Market has been around since 2018 and is the largest underground marketplace that sells credentials, browser fingerprints, and browser cookies.
Browser fingerprints are unique digital footprints that are generated by your web browser based on various factors such as your browser type and version, installed plugins, screen resolution, and other settings. These fingerprints can be used to track your online activity and may also be stolen by malicious actors for identity theft or other malicious purposes.
In this blog we focus on how security analysts can gather relevant intelligence on credential stealing attacks and specifically detect stolen cookies and browsers that are being used to compromise users’ machines with Trellix XDR. The basis for this in-depth blog was Trellix's assistance in this global law enforcement operation.
Gathering intelligence with Trellix Insights
Trellix Insights is designed to provide our customers with visibility around threats and mitigations. Trellix Insights also shows you where your weakest links are against attacks, and provides recommendations on how to strengthen your defenses. Below we provide visibility in terms of prevalence to date of this campaign globally and the MITRE ATT&CK techniques mapped to this campaign.
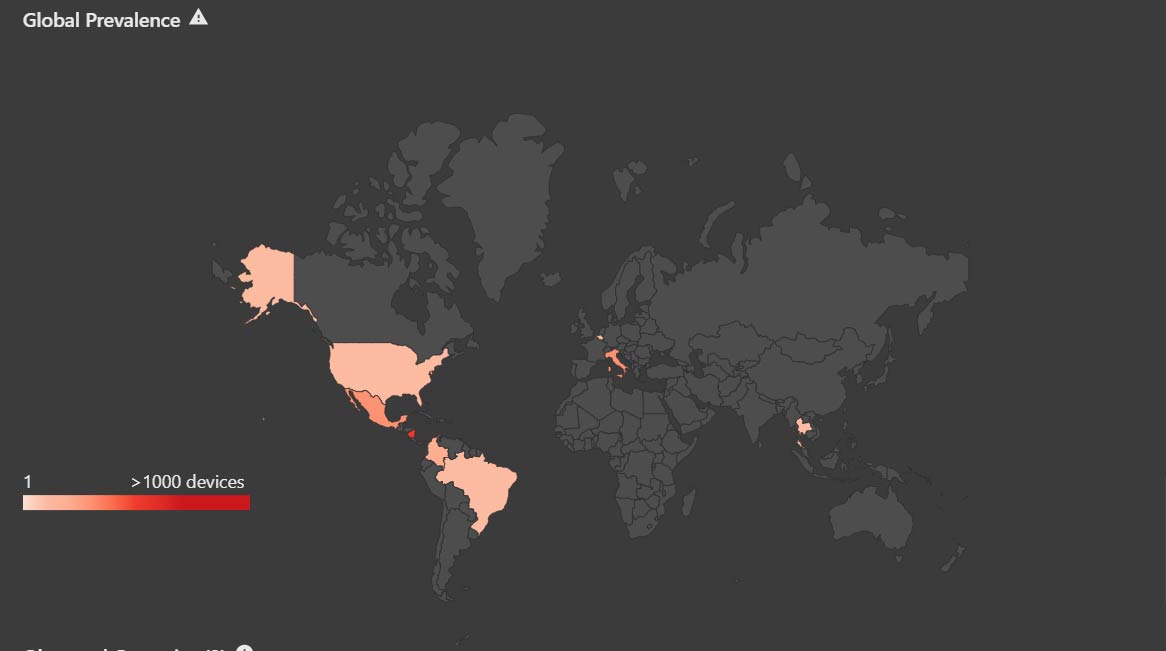
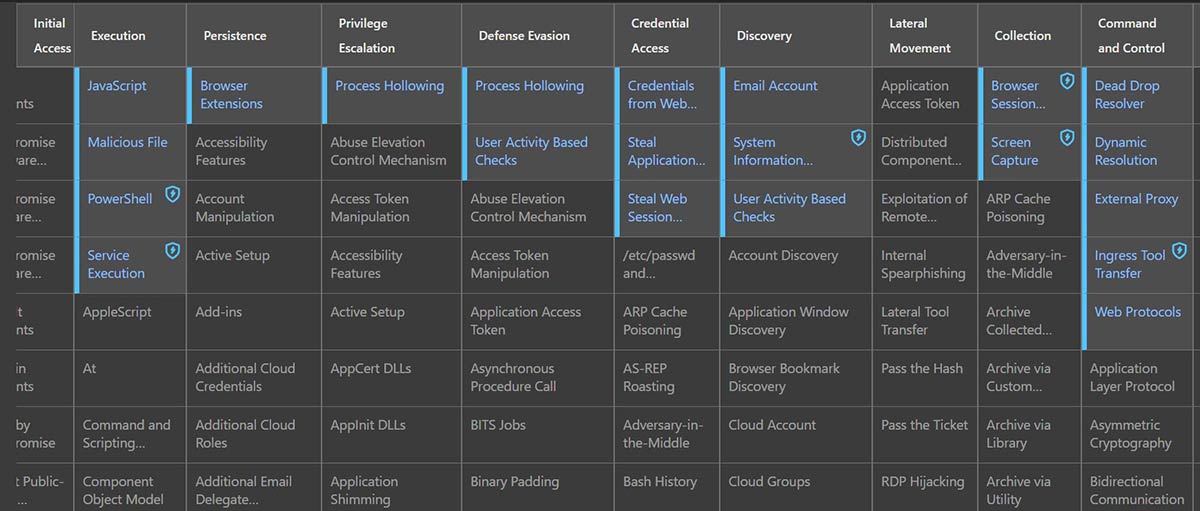
Irrespective of the specific malware used by Genesis Market that we have incorporated in our threat intelligence, the danger and impact of online fingerprint theft and abuse is something every organization should be aware of.
Detecting suspicious activity with Trellix XDR
Trellix XDR aggregates and analyzes log data from various sources, including endpoint, endpoint detection and response (EDR), identity and access management systems, web application logs and network traffic logs.
Trellix XDR can detect patterns of suspicious activity that may indicate an attacker is using stolen cookies or a forged browser fingerprint. You can then take appropriate measures to mitigate the risk of attacks. It's important to regularly monitor and analyze web application traffic and logs to stay ahead of potential threats.
Trellix XDR can detect processes with arguments pointing to known browser files that store passwords and cookies and abnormal logon activities, through the following steps:
- Collect data: Configure Trellix XDR to collect logs and data from all endpoints in your network, including web servers, workstations, and identity and access management systems. The data should include information about the user, their browser, and their interactions with web applications.
- Monitor and analyze: Trellix XDR monitors the collected data in real-time and analyzes it for any suspicious activity. When an event occurs that matches one of the rules, Trellix XDR will trigger an alert so that your security team can investigate the issue.
- Respond and remediate: When an alert is triggered, your security team should respond and remediate the issue. For example, if an abnormal logon activity is detected, your team may need to reset the user's browser settings, issue a password renewal, and revoke or restrict their access to the network.
- Update rules: Finally, you should update your rules and playbooks regularly based on new threats and changes in your environment. This will help you stay ahead of attackers and improve Trellix XDR’s ability to detect stolen browser fingerprints and cookies and other attacks.
Example rule to detect stolen browser fingerprint for Trellix XDR
Rule name: Stolen Browser Fingerprint
Description: This rule detects changes in the user's browser fingerprint that may indicate it has been stolen or manipulated.
Conditions:
- Source: Endpoint logs
- Event type: Browser fingerprint changed
- Change type: Significant change
- Time frame: Within the last 24 hours
- Browser fingerprint: Not matching previous values
Actions:
- Generate a high priority alert
- Send an email notification to the security team
Recommended response:
- Investigate the endpoint where the change was detected
- Check for any signs of malware or suspicious activity
- Reset the user's browser settings if necessary
- Review the access control policies and revoke access if necessary
There are several event IDs in the Windows Event Viewer that may indicate a stolen browser fingerprint. Here are a few examples:
- Event ID 4656: This event indicates that specific access was requested for an object. The object could be a file system, kernel, or registry object, or a file system object on removable storage or a device. If access was declined, a Failure event is generated.
- Event ID 4663: This event is generated only if object’s SACL has required ACE to handle specific access right use..
It's important to note that not all instances of these events necessarily indicate a stolen browser fingerprint, as legitimate usage patterns can also trigger them. Therefore, it's important to investigate each event in context and look for other signs of suspicious activity before drawing any conclusions.
Monitoring
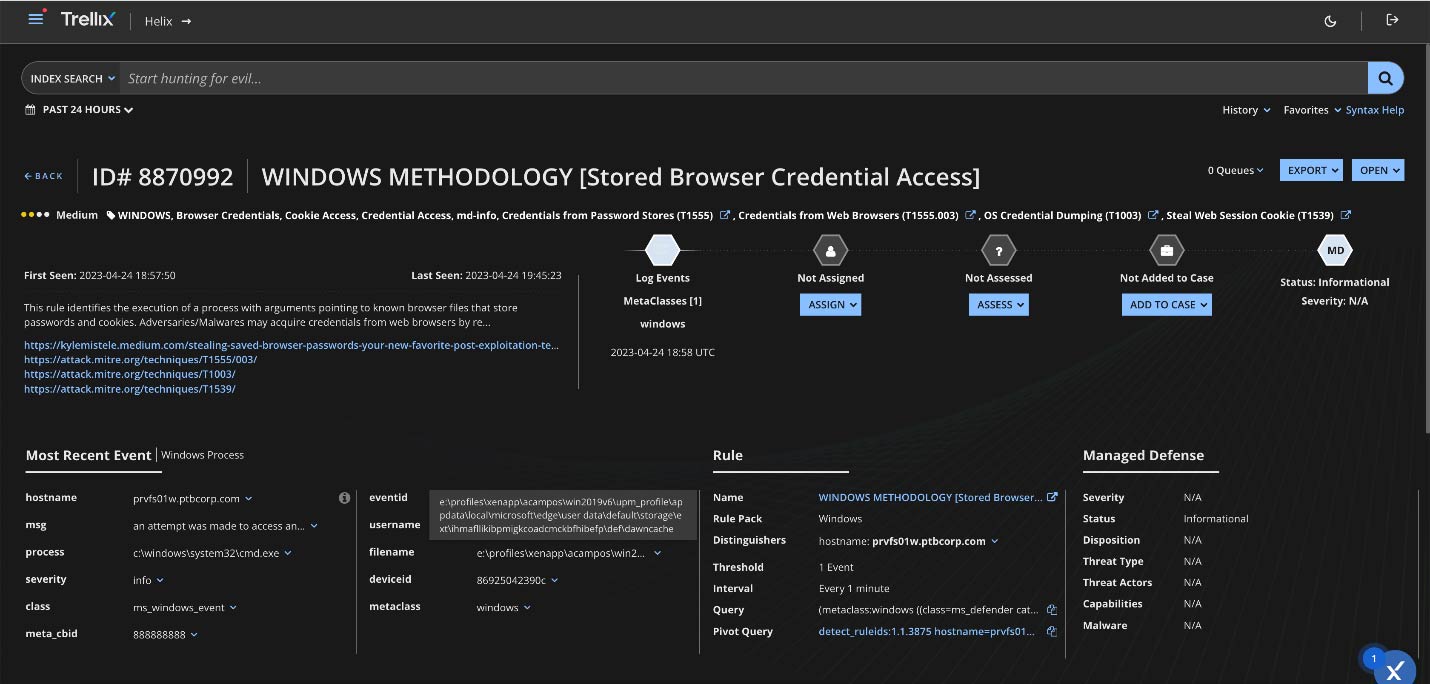
Identity platform Integration to Trellix XDR
Below we demonstrate a key integration with Okta into our Trellix XDR platform that helps customers link to credential tools like Okta to help detect unauthorized access to customer networks working together to unlock the full potential of your existing investments.
Trellix XDR can ingest identity telemetry from Okta and has the capability to analyze identity audit events to find anomalies and correlate them with a wide range of information, such as application behavior and user roles within the organization.
From a Defender’s perspective, context is critical to understanding threats. The XDR integration with Okta is the foundation for identity-based risk scoring in Trellix XDR.
What does defense look like with more verification?
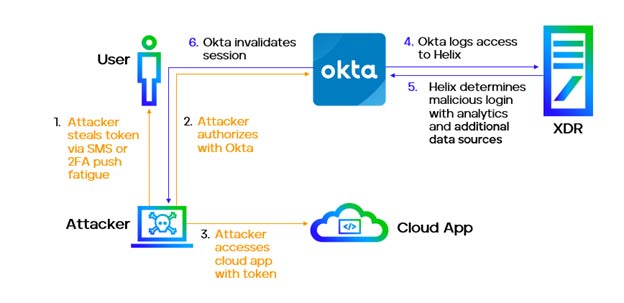
- Understand authorization levels of apps for a given user
- Tracking login patterns provides basis for threat hunting
Below are some visuals of what Trellix XDR would show with the integration we have today with Okta.
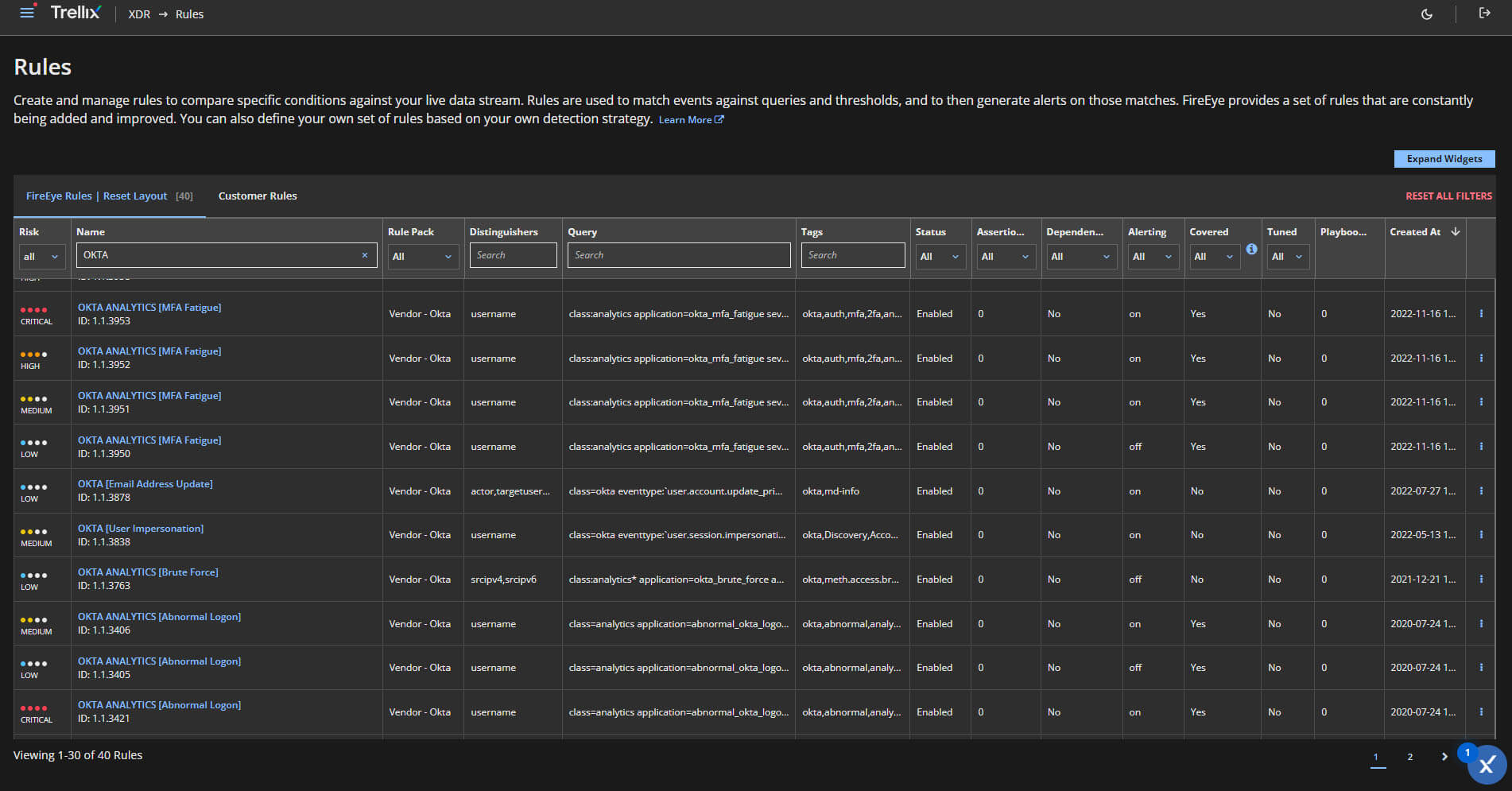
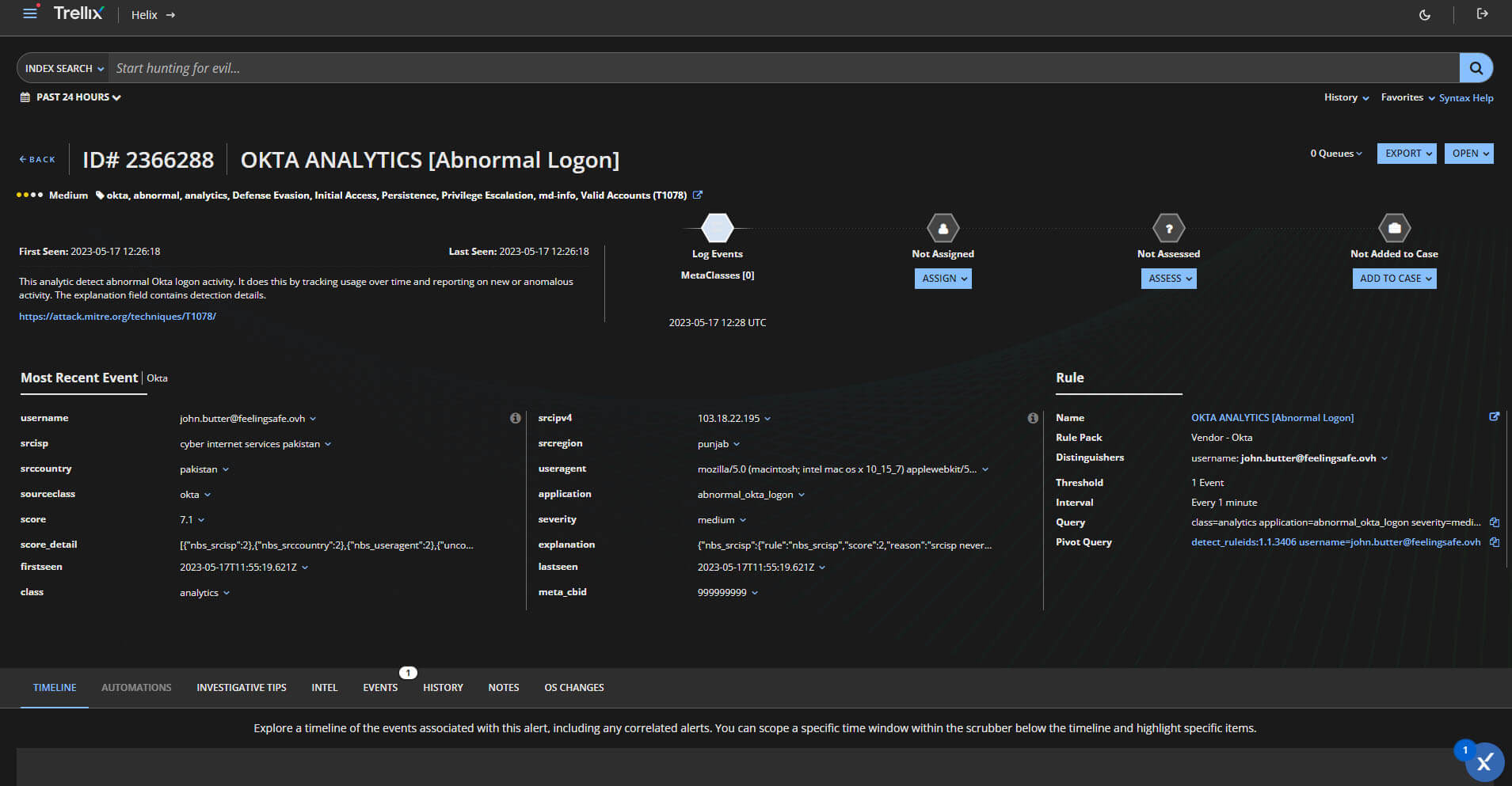
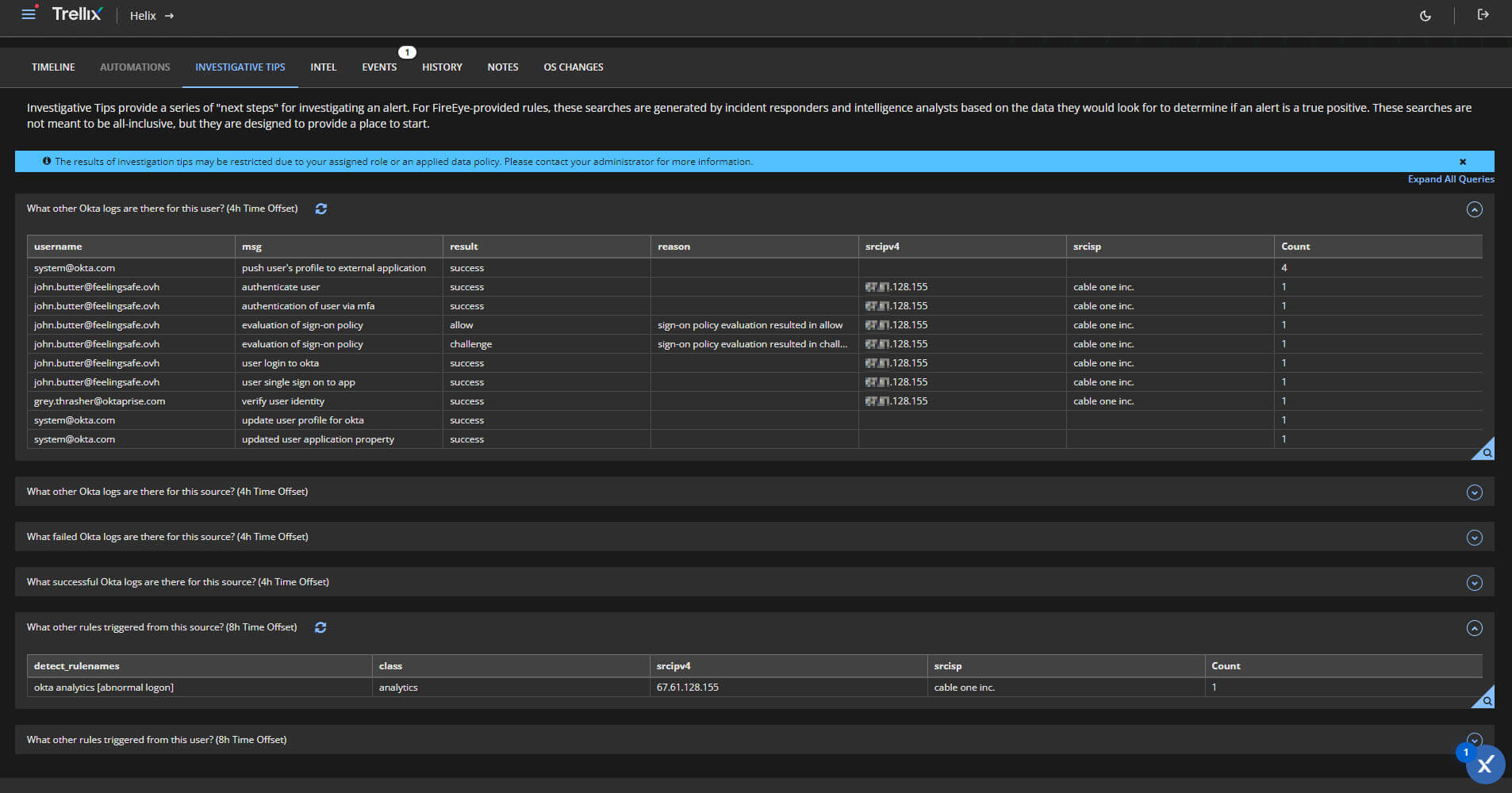
Attack surface reduction
For customers, it is recommended that you manage the extensions that users are trying to install into the browsers.
For Microsoft Edge or Firefox, follow the below guidance.
Follow the link below for guidance with Group policies and Google Chrome browsers.
Logon Restrictions policy - Within Windows you can enable logon restrictions for users, which reduces the amount of time an attacker can be active on the network. This also reduces the attack surface for many customers.
For organizations, the below best practices should be followed for prevention and identity and access management. Note, some guidance is Trellix-specific.
- Train users in phishing and how to spot phishing – recurrent training with test phishing emails for all users. Users must be alert when it comes to links and attachments.
- Be very careful with password-protected archives, as they will bypass most email scanning and web proxies.
- Check file extensions: a JPG, PDF or Document might not be what it looks like from the icon! It can be an executable which disguises itself with its icon.
- Implement web control and block access to any unknown/uncategorized websites.
- Block or report any unknown application from communicating to/from the Internet with firewall solutions (Trellix Endpoint Security (ENS))
- Implement Adaptive Threat Protection (ATP) and configure Dynamic Application Containment (DAC) for unknown processes, limiting what they can do.
- Enable Exploit Prevention and enable signature for “Suspicious Double File Extension Execution” (Signature 413).
- Protect session cookies with Exploit Prevention Expert rule.
- Implement Expert rules, which trigger on any PowerShell or unknown / contained process accessing your session cookie:
- C:\Users\**\AppData\Local\Google\Chrome\User Data\Default\Network\**\*.*
- C:\Users\**\AppData\Roaming\Mozilla\Firefox\Profiles\**\*.*
- C:\Users\**\AppData\Local\Microsoft\Edge\User Data\Default\Network\**\*.*
- Implement Endpoint Detection and Response (Trellix EDR). It could detect some of the techniques identified, such as malicious use of web protocols, process injection and tool transfers.
- Implement strong and deep email scanning.
- Implement strong and deep web gateway and blocking of uncategorized web-sites, and have a quick and trusted procedure to add more websites if needed.
- Please apply the Identity and Access Management (IAM) best practices as outlined by CISA.
- Review your current visibility and detection capability on credential theft and privilege abuse.
Read more about this in our latest blog: Genesis Market No Longer Feeds The Evil Cookie Monster.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.