Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Shrinking the Gray with Modern Endpoint Security
By Trellix · October 17, 2024
This blog was written by Joe Malenfant
Can endpoint security really get anymore modern than it is today? The short answer is yes. But first, what is Modern Endpoint Security and how does it help security teams reduce firefighting and implement more effective and efficient strategic security initiatives?
Modern Endpoint Security is essential for today’s organizations that operate in complex, hybrid environments. Very few organizations are fully cloud or on prem, but instead a hybrid thereof. Ultimately a modern endpoint security solution should address all environments, and include prevention, detection, forensics, and remediation in an integrated platform. As IDC puts it in their MarketScape for Modern Endpoint Security where Trellix was named a leader for both Enterprises and Midsize Businesses:
IDC MarketScape: Worldwide Modern Endpoint Security for Enterprises 2024 Vendor Assessment (#US50521223e)
Dealing with nuance and “shrinking the gray”
Threats continue to get more sophisticated with multi-stage and multi-vector attacks. Trellix CTO, Ashok Banerjee observes that detecting suspicious activities is like looking for the proverbial needle in the haystack, but that “needles in the haystack are looking more and more like hay.” IDC notes that endpoints are attractive targets because they are inherently exploitable (ie: exploiting Ivanti Connect Secure VPN Zero-Day Vulnerability), and protecting against adversaries continues to be a challenge because “there will always be a gray zone of uncertainty.”
The gray zone is exemplified by the increasing trend of adversaries using legitimate processes, services, and applications to launch attacks. Researchers from Trellix ARC documented how threat actors had embedded an infostealer into legitimate Cisco Webex’s binaries. In this example, modern endpoint security would alert users to the new threat, identify the scope of the incident, and provide remediation.
So how does a Modern Endpoint Security solution help security teams with this increasing level of nuance? One way according to IDC is that “Multiple layers of security technologies are needed to shrink the gray zone and effectively react when adversaries compromise devices.“
At Trellix, we have been detecting threats for over 25 years, and we’ve built a multi-layered protection stack to address the challenge of shrinking the gray zone. We’ve forgotten about more threats than most have ever seen. Over the last few years we have seen adversaries become more adept at masking their activities such as using living off the land techniques. Whether it’s ransomware that deletes shadow copies, an info stealer that removes registry keys, or a supply chain attack that escalates privileges with legitimate credentials, the gray zone has been steadily growing.
Each layer of the Trellix Endpoint Security stack is tuned to maximize legitimate detections while ensuring that performance for endpoints is optimized. Unlike solutions that have an over reliance on machine learning and struggle with consistent legitimate detections and false positives, Trellix Endpoint Security consistently provides award winning protection while minimizing false positives and performance impact.
In Figure 1 we see a stack of technologies that illustrates the capabilities that deliver high fidelity detections and minimal false positives. These are engineered for efficiency, leveraging attack surface reduction and Trellix’s Global Threat Intelligence reputation network that block threats before more advanced technologies such as machine learning (ML) and behavioral analytics need to be engaged. In the event that a sophisticated attack like multi-stage ransomware or supply chain attacks (such as the WebEx binaries) manages to bypass all the controls, a modern endpoint solution will provide security teams with continuous monitoring and automated responses to remediate or fully roll back from the impact of ransomware.
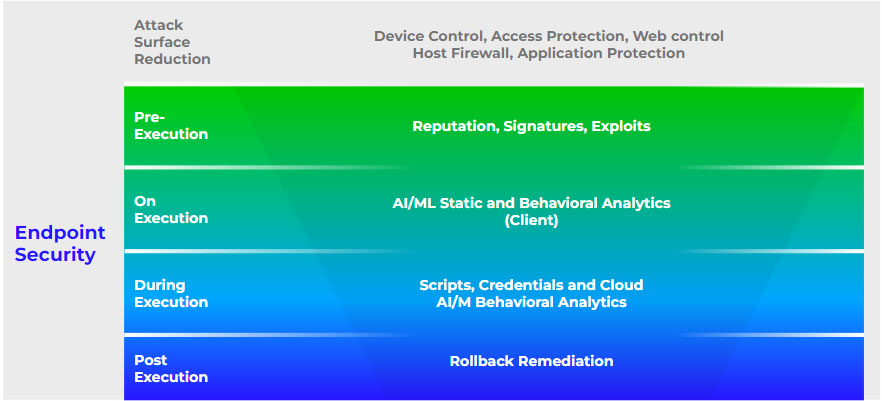
Trellix Endpoint Security has a unique rollback remediation that delivers an intelligent approach to remediating systems impacted, such as by ransomware. Unlike other solutions that require manual intervention to restore volume shadow copies, old backup images, or connecting via remote shell into a machine, Trellix leverages its monitoring capabilities to cache changes made by unknown processes and restores them if the process that made the changes is found to be malicious. (This knowledge base has more technical details).
Vendors that claim Trellix Endpoint Security relies on signatures are either being disingenuous about their over-reliance on cloud-based machine learning, which is prone to inconsistent detection and high false positives when looking at 3rd party testing by AV-Comparatives. They may not be aware of how a broad technology stack helps organizations prevent threats while ensuring operational efficiency for SOC teams across hybrid environments, particularly those in constrained networks without cloud access where updates are not as frequent.
Trellix Endpoint Security minimizes performance impact on endpoints while protecting against modern sophisticated threats. Protection efficacy, false positives, and endpoint performance are important metrics that multiple 3rd parties test against in independent testing of endpoint security solutions. Trellix is recognized for effectiveness in all metrics across AV-Test, AV-Comparatives, and SE Labs. Read our blog about being recognized with Best Protection 2023 by AV-Test and Approved Business Protection for Windows and Mac by AV-Comparatives to learn more.
| AV-Test | AV-Comparatives | |||||
| 2023 Award | Protection/ Performance/ Usability (max 6) |
2023 Business Security Approved Award | False Positives | Malware Protection Rate | Impact Score | |
| Trellix | Best Protection Corporate Users Windows | 6/6/6 | Business Security | Very Low | 99.7% | 14.8 |
| CrowdStrike | - | - | Business Security | Medium/ Average | 99.6% | 20.9 |
| Microsoft | - | 6/6/6 | Business Security | Very Low | 99.5% | 18.5 |
| SentinelOne | - | - | - | - | - | - |
| Trend Micro | - | 5.5/6/5.5 | - | - | - | - |
| Palo Alto Networks | - | - | - | - | - | - |
Faster Investigations with Summarization and Contextualization
When needles in the haystack look more and more like subtle shades of gray, organizations need to improve their investigative processes with actionable insights and contextualization.
Trellix Endpoint Detection and Response (EDR) is designed to uncover advanced techniques being used by threat actors, and provide actionable data to security teams for further investigation. Recently we’ve added generative AI to Trellix Wise to hyper-automate security teams investigative efficiencies even further.
AI-Guided investigations deliver summaries and context that help define “the needle in the haystack” as a needle. For example, the investigation in Figure 3 recorded over 2,000 artifacts from an endpoint. AI distills these into 8 key findings in the form of answers to questions that experienced analysts would ask when triaging an incident. Trellix EDR is also the only solution that connects activities from previously seen threats to ones currently being investigated.
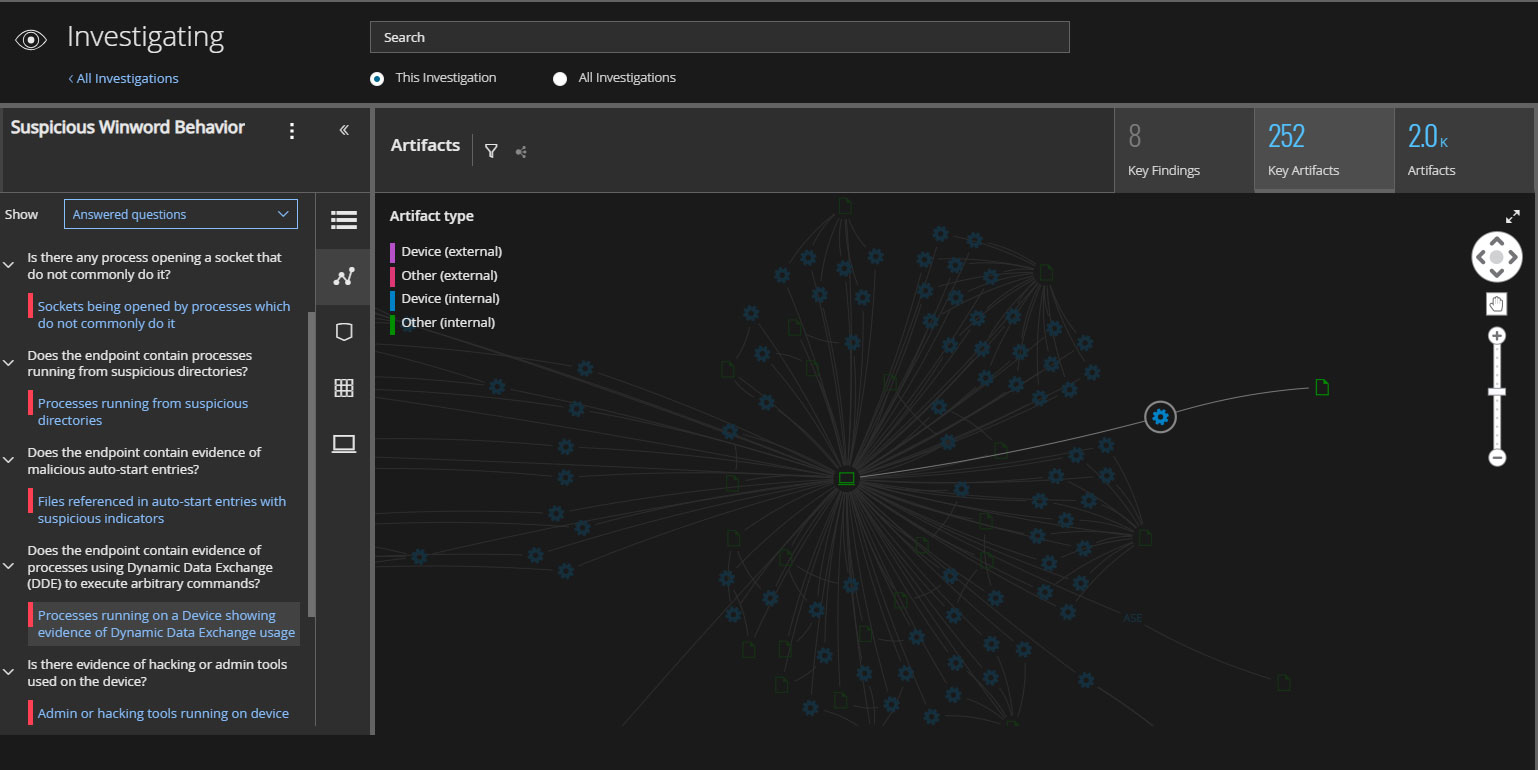
Further guidance is provided when the security analyst selects a key insight, in this example regarding the technique that uses DDE to execute commands. The relevant, proverbial needle in the haystack is highlighted, which immediately provides the investigator relevant details and context to take quick and effective action to drive the investigation to conclusion.
Feedback Mechanisms to Fortify Modern Endpoint Security
Security teams don’t always know if they are using controls available in their tools effectively. Understanding risk exposure based on the threat landscape and whether or not mitigations have been deployed helps organizations be less reactive and better advance more proactive and strategic security initiatives.
With Trellix Insights, integrated with Trellix Endpoint Security, customers get industry and geographically relevant threat intelligence along with security posture visibility for endpoints. As IDC puts it:
IDC MarketScape: Worldwide Modern Endpoint Security for Enterprises 2024 Vendor Assessment (#US50521223e)
Trellix Insights empowers security teams to be more proactive defending against adversaries. The Security Posture Score for endpoints assesses the device for configuration according to corporate requirements, including software inventory and versions, ensuring security teams get more out of their endpoint investment.
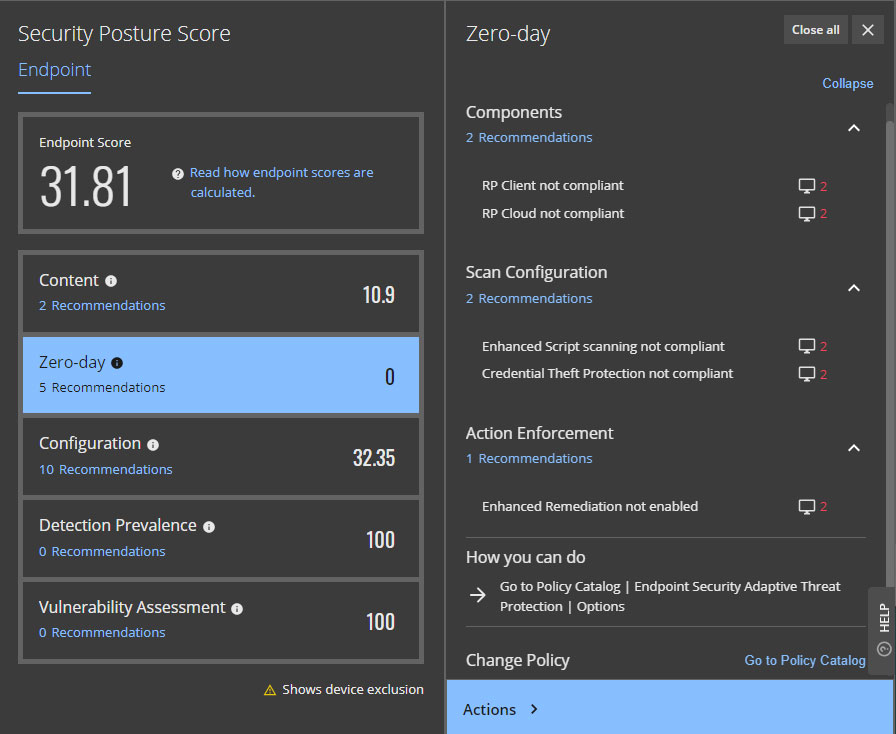
Security teams get visibility on capabilities in the protection stack that optimize defenses against modern threats. Since it is integrated with Trellix ePolicy Orchestrator (ePO), addressing misconfigurations that expose an organization to risk can be quickly and easily remediated.
Modern Endpoint Security is a Platform
A Modern Endpoint Security solution must extend visibility and control across the complex and diverse environments in a way where the broad capabilities work together to simplify the management of capabilities across protection, detection, investigation, response and forensics. While digital transformation and cloud migrations have been underway for years, organizations require coverage for heterogeneous environments at scale more than ever. This is why Trellix continues to support and innovate for multi-device and multi-OS support as well as providing security controls across cloud, on prem, hybrid, and even air-gapped networks with a single platform.
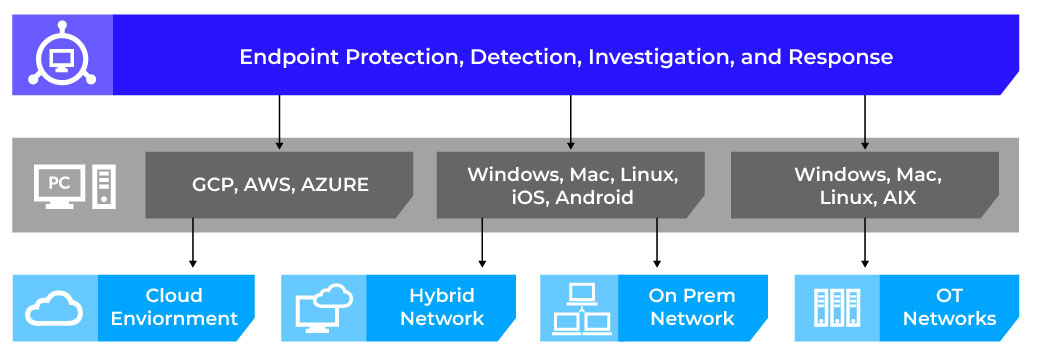
Tying it Together
The shift to Modern Endpoint Security is underway and Trellix Endpoint Security delivers on the key outcomes organizations need to be more proactive in addressing the complex and nuanced challenges of sophisticated threats and heterogenous endpoint environments. Today’s hybrid organizations are solving broad and complex problems and subsequently require an equally broad and capable solution that is integrated to provide fortifying feedback mechanisms across the endpoint security life cycle.
Investigating increasingly nuanced threats with increasing shades of gray while ensuring that optimized controls are deployed in complex and diverse environments are not separate siloed security initiatives, but at the core of what a Modern Endpoint Security solution is built to deliver.
Contact your account team or ask our experts on the website for more information about additional use cases that a Modern Endpoint Security solution is designed to address.
Further reading:
IDC MarketScape Vendor Assessment
https://www.trellix.com/platform/wise/
Modern Endpoint Security Demystified (10 minutes)
https://www.youtube.com/watch?v=MxFZuPIWlzg&t=8s
Trellix Wise
https://www.trellix.com/platform/wise/
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
