Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Stopping a Low Noise Attack Using Trellix Helix
By Grant McDonald · January 22, 2026
A simple misconfiguration could be all it takes for your passwords to get into the hands of attackers. Worse, the noise this type of attack generates is often low for incident responders making it difficult for teams to be aware that the theft is occurring.
The attack in question is the Authentication Server Response (AS-REP) Roasting. It is a nearly silent, low-tech attack that targets a common misconfiguration, allowing criminals to steal and crack user passwords without ever being seen by traditional security tools.
It works by targeting Microsoft Active Directory (AD) user accounts where a pre-authentication step has been disabled. Although a simple misconfiguration, it allows an attacker to obtain an encrypted password component that can then be cracked offline using other tools in their arsenal. Once cracked, the attacker walks away with your users’ passwords, giving them the keys to your network.
Trellix Helix shines a light on AS-REP Roasting
Traditional security tools often treat each stage of the AS-REP Roasting attack as a single, harmless event. Trellix Helix transforms this fragmented noise into a clear, actionable story.
Step 1:
Helix notices a small, suspicious behavior, like a minor reconnaissance scan or an unusual request to the Domain Controller. These individual events are low-noise and easy for attackers to hide among the daily activity. Helix catches these for the next step.
Step 2:
Helix uses analytics to stitch together these seemingly isolated alerts—a reconnaissance query, plus an unusual ticket request, plus an attempt to extract a hash. Instead of three separate, low-priority warnings, you get one high-priority alert titled "AS-REP Roasting Attack in Progress" providing the full attack narrative.
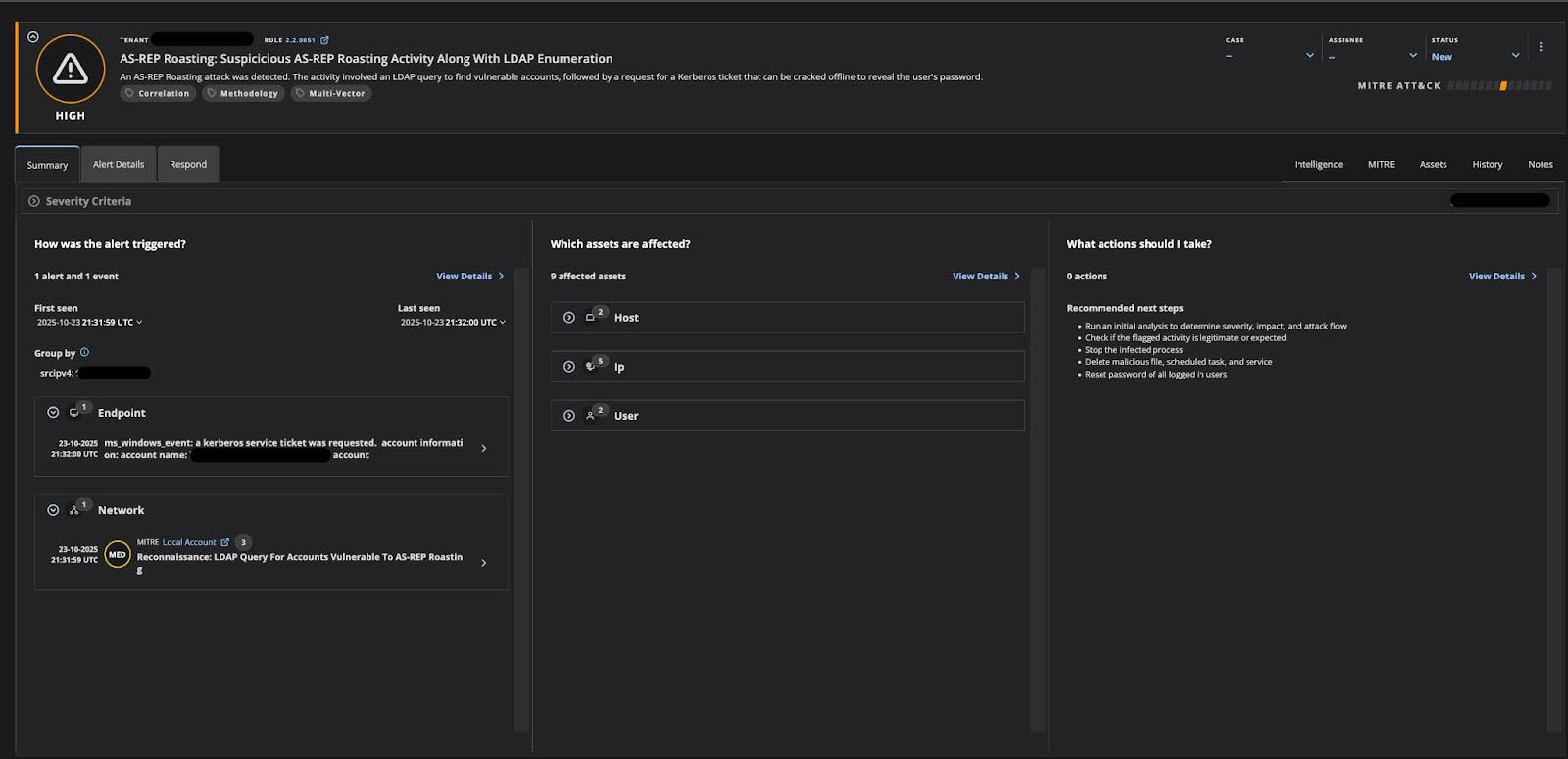
Step 3:
Helix simultaneously monitors network traffic (the request for the ticket), endpoint activity (the tool used to extract the hash), and identity logs (which user accounts are involved). This keeps attackers from hiding regardless if they switch tools or techniques. Helix combines all angles (endpoint, network, identity) to stop attackers from achieving persistence in your environment.
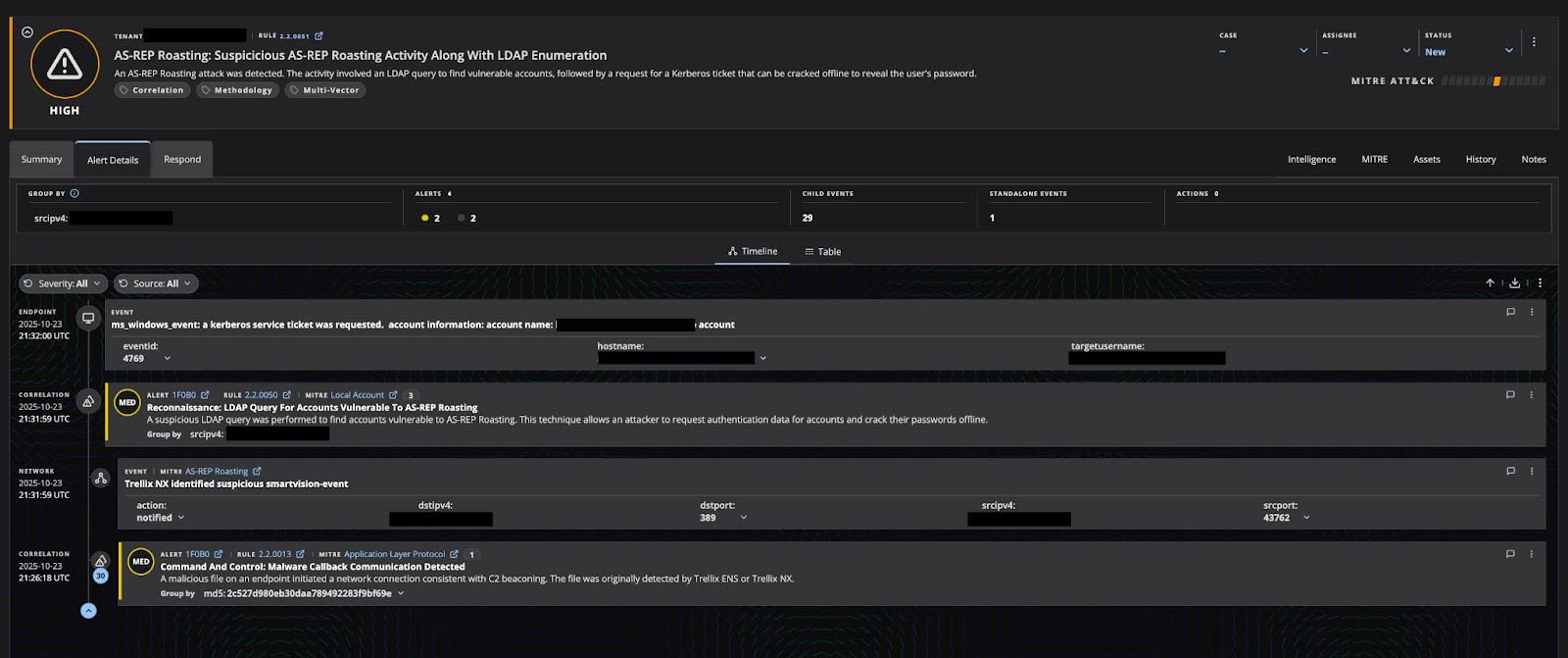
Better protection through context
Trellix Helix doesn't just tell you something is happening; it tells you exactly what, where, why, and what to do about it.
Helix applies risk-based scoring, meaning that if an attack targets a critical financial server or a senior executive's account, the alert is automatically flagged as higher severity, ensuring your SOC team focuses on the most dangerous threats first.
You also get a clear narrative thanks to the consolidated alert Helix provides to your team. MITRE ATT&CK mappings ( industry-standard for attacks), affected assets (which systems and users are compromised), and recommended remediation steps. By understanding the full attack chain—from initial discovery of the vulnerable account to credential extraction—your security team can stop the attack, reset the vulnerable passwords, and enable preauthentication faster, minimizing the time the attacker has inside your network.
Conclusion
AS-REP Roasting can be a quiet threat with loud consequences. By leveraging Trellix Helix’s ability to draw from multiple security tools and link fragmented events into a clear, unified threat narrative, your business can detect these stealthy attacks early. Additionally, Trellix Hyperautomation can act as a force multiplier with automated responses to the early signs of these attacks. Automatic password resets, AI alert investigations, and threat intelligence enrichment can help you respond even more decisively, and keep your critical systems and user data secure.
For more detailed information on how Trellix Helix works to thwart AS-REP attacks, check out this blog from the Trellix Advanced Research Center.
To learn more about Trellix Helix, take our product tour to see it in action or visit this page.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
