Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
China-Taiwan Tensions Spark Surge in Cyberattacks on Taiwan
By Daksh Kapur, Leandro Velasco · May 17, 2023

“In the past few years, we noticed that geopolitical conflicts are one of the main drivers for cyber-attacks on a variety of industries and institutions. Monitoring geopolitical events can help organizations to predict cyber-attacks in countries they operate in. Trellix with Atlas and Insights our global monitoring services, together with our mail, network, EDR and XDR solutions can help organizations to preemptively fine tune their systems to detect and mitigate emerging attacks.” – Joseph Tal Senior Vice President of Trellix Advanced Research Center.
Recent tensions between China and Taiwan have been escalating due to China's increasing military presence and provocative actions in the region. China has long claimed Taiwan as a part of its territory and has been putting pressure on the island to reunify with the mainland. China has also (in late 2022) become a top threat actor country and was the most prevalent threat-actor country behind nation-state activity. Taiwan, on the other hand, has maintained its independence and has been strengthening its military capabilities in response to China's aggression.
In the last few months, the rise in tensions between Taiwan and China have contributed to a noticeable increase in cyberattacks towards Taiwan. Our researchers have identified a worrying surge in attacks aimed at various industries in the region, with the goal of delivering malware and stealing sensitive information.
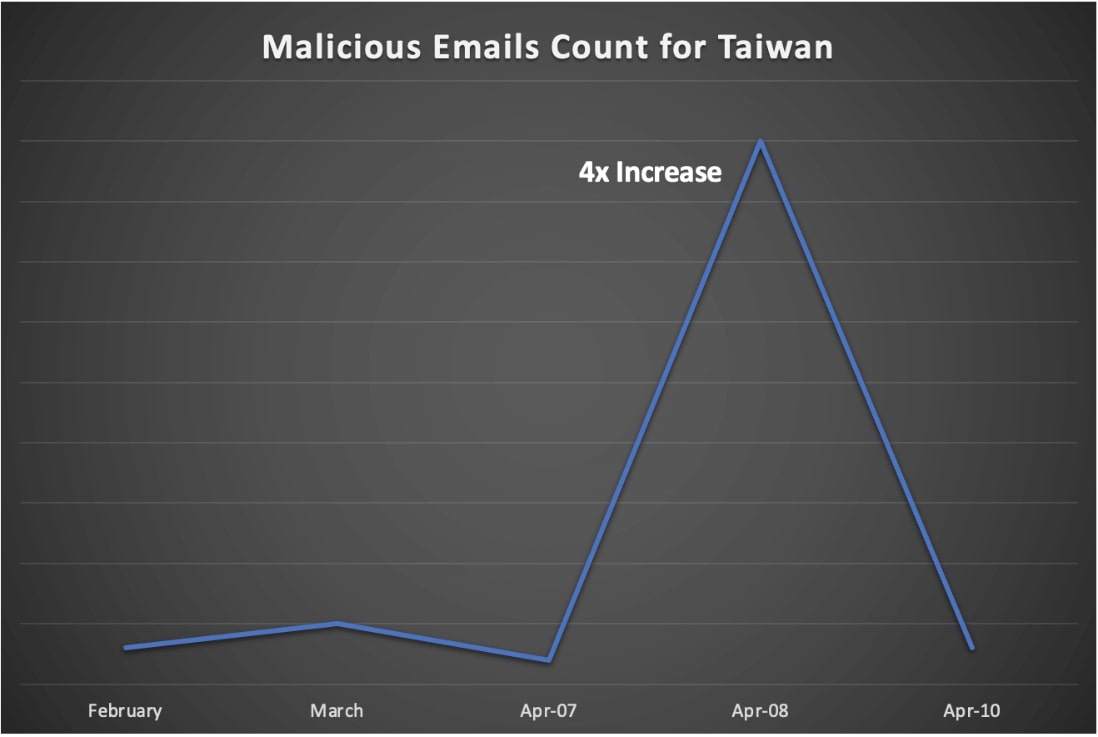
Trellix has observed a surge in malicious emails targeted towards Taiwan, starting April 7 and continuing until April 10. The number of malicious emails during this time increased to over four times the usual amount. Even though various industries were targeted during the surge, the most impacted industries in the respective time frame were -
- Networking/IT
- Manufacturing
- Logistics
Furthermore, during the last week of January 2023, our researchers observed a significant rise in extortion emails aimed at Taiwan Government officials, with a 30-fold increase in malicious email counts. Though it’s unclear if this activity is from China-backed threat actors, it speaks to a continued increase in attacks specifically targeting Taiwan.
Malicious Emails
Trellix Advanced Research Center researchers found different styles of malicious email campaigns. The following is a brief about the samples presented below -
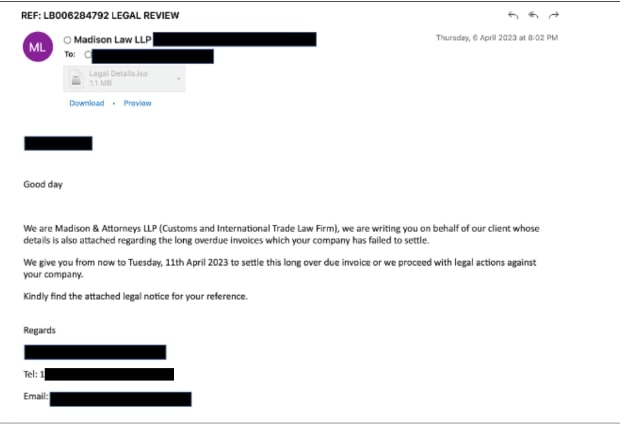
- Sample 1: The email is a fake payment overdue notification spoofing a Law firm and to add a sense of urgency, the email contains a warning of legal action on non-payment of the amount. Along with it, the email contains a malicious attachment.
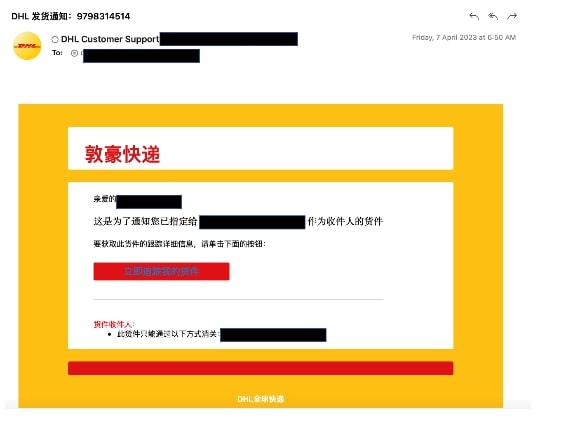
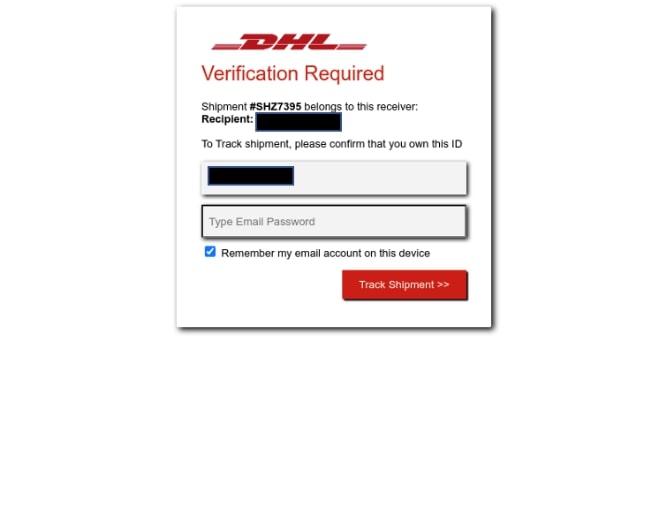
- Sample 2: The email is fake shipment notification spoofing DHL and containing a URL which redirects the user to a phishing page.
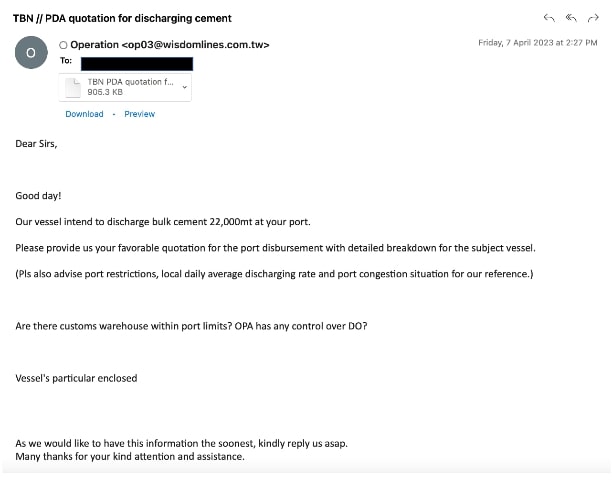
- Sample 3: The email is a fake quotation request email for a bulk cement order containing an archive as an attachment which contains malware.
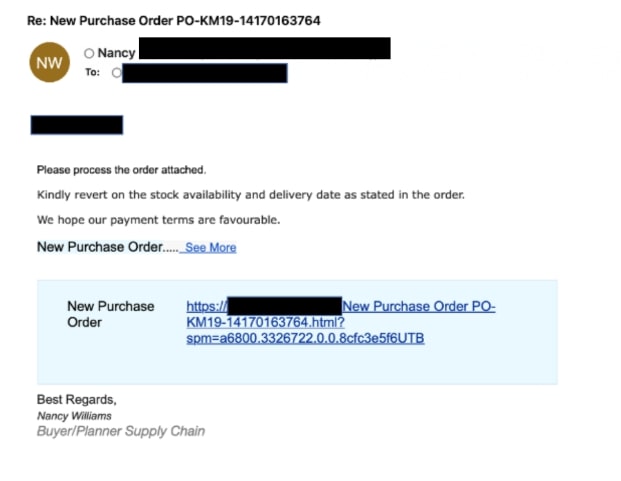
- Sample 4: The email is a fake notification email for purchase order containing a URL which redirects the user to a phishing page.
Malicious URLs
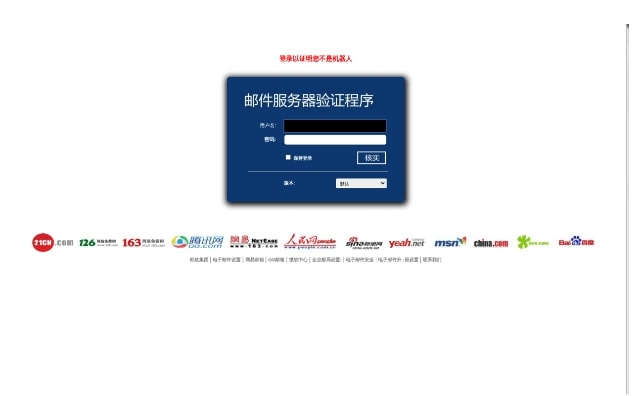
The following are some of the malicious web pages being utilized to target Taiwanese organizations. Our researchers noticed many different themes like generic login pages, targeted company specific pages, multi-brand login pages, etc. being used to target users with an aim to harvest credentials.
Malware
PlugX
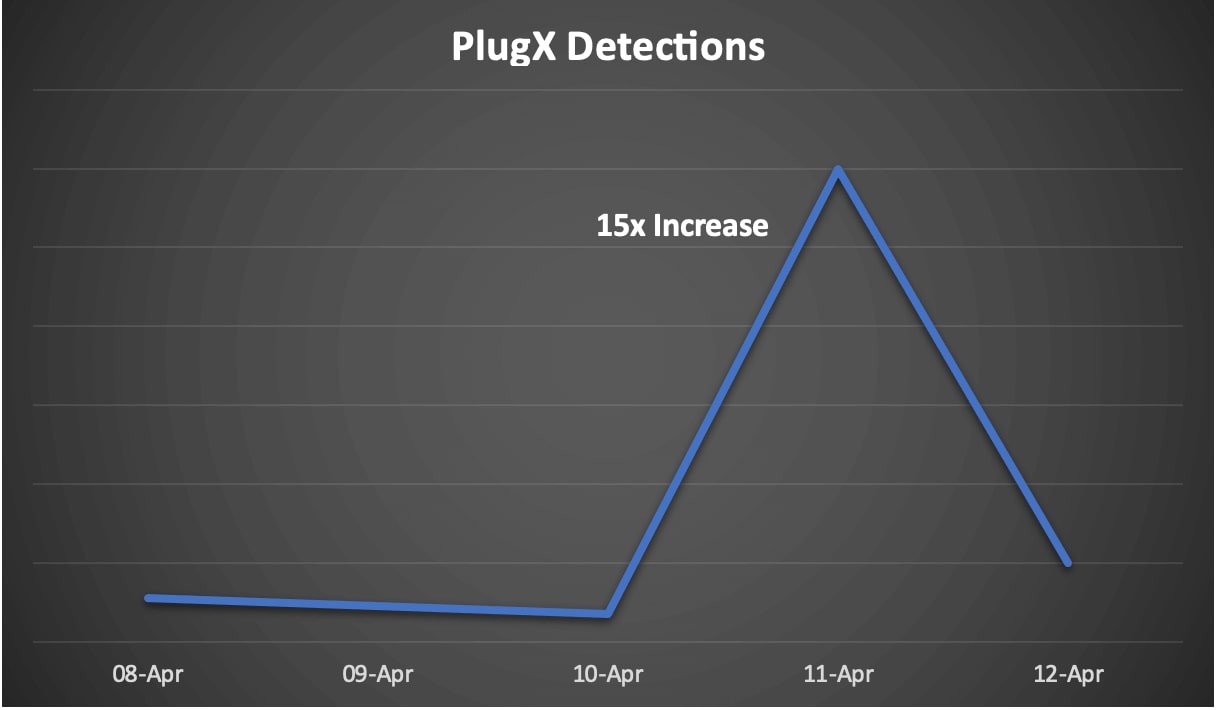
Following the spike in malicious emails targeting Taiwan, Trellix has identified a surge in PlugX detections as shown in the following screenshot. PlugX is a known Remote Access Tool in use since at least 2012, PlugX is most commonly Linked to Chinese linked Threat groups.
The surge was observed via the Trellix Advanced Threat Landscape Analysis System (ATLAS) that shows an aggregated view of various sources of telemetry enriched with campaign data containing research from Trellix’s Advanced Research Center (ARC).
This follows the TTPs of many threat actors that use phishing emails as an initial point of infection and then deploy more powerful tooling to take control of the systems and then move laterally.
PlugX is a Remote Access Trojan (RAT) which is commonly used by several Chinese APT groups for cyber espionage activities. It is known for its stealthy capabilities and ability to evade detection by anti-virus software. PlugX attempts to evade detection during installation by using DLL sideloading on target systems.
This technique consists of a legitimate program loading a malicious dynamic-link library (DLL) file that masquerades as a legitimate DLL file. This allows the execution of arbitrary malicious code bypassing security measures that look for malicious code running directly from an executable file.
PlugX has a wide range of capabilities, including capturing keystrokes, taking screenshots, and accessing and stealing files. Some of the PlugX plugins include disk enumeration, keylogging, network resource enumeration, port mapping, process termination, registry editing, service control, and remote shell access. Some of the known threat actors that use PlugX include Apt10, APT27, APT41, MustangPanda, and RedFoxtrot. These groups are believed to be state-sponsored and have been linked to various cyber espionage activities.
Additional Malware
During the analyzed period Trellix has also identified several other malware families targeting Taiwan. The following are some of the malware families observed by our researchers:
- Kryptik - Malware of this family consists of Trojans that use anti-emulation, anti-debugging, and code obfuscation to prevent their analysis.
- Zmutzy - A spyware and information stealer Trojan written in Microsoft's .NET language. It is used to spy on the victims by collecting credentials and other information from the infected system.
Formbook: An info stealer malware used to steal several types of data from infected systems, including credentials cached in web browsers, screenshots, and keystrokes. It can also act as a downloader, enabling it to download and execute additional malicious files.
Trellix Product Protections
Our security product provides comprehensive protection from attacks such as spoofing, phishing and malware-laced job emails. Our multi-layered approach includes checks on the URL, email, network, and attachment levels to ensure that any potential threat is detected and prevented from causing harm. Our product continuously monitors and updates its threat intelligence database to stay ahead of new and evolving threats.
The following is some a subset of the Trellix Security detections that have been observed for the ongoing campaigns:
Trellix VX
Trellix Cloud MVX
Trellix File Protect
Trellix Malware Analysis
Trellix SmartVision
Trellix Email Security
Trellix Detection As A Service
FEC_Phish_HTML_Generic_257
FE_Trojan_HTML_Phish_336
FEC_Phish_HTML_Generic_141
Trojan.MSIL.ZmutzyPong.FEC3
Trojan.MSIL.AgentTesla.FEC3
Suspicious File (Data) Theft Activity
Suspicious Codeinjection on Known Benign File Location
Suspicious Codeinjection Memory Read Activity
Suspicious Process Memory Read Activity
Suspicious Data theft activity
Suspicious Buckets Reconnaissance Activity
Suspicious Process Infostealer detected
Suspicious Codeinjection Activity
Suspicious File Recon for AMSI
Trojan.Win32.Tnega.FEC3
Trojan.AutoIt.Leonem.FEC3
fe_ml_heuristic
InfoStealer.MSIL.AGENTTESLA.MVX
Suspicious File Dropped
Suspicious Process PowerShell Param
Suspicious Registry on File Dropped
Suspicious File Activity
Suspicious Codeinjection Activity
Suspicious File Persistence Activity
Suspicious Folder Credential Access
Suspicious Process Installation Activity
Malicious AGENTTESLA Indicator
Suspicious File Stealing Activity
Trojan.MSIL.AgentTesla.FEC3
Suspicious Codeinjection Activity
Suspicious Process and CodeInjection Activity
Suspicious Codeinjection Activity
Suspicious File Recon for AMSI
Trojan.Korplug.FEC3
FE_Methodology_Win_StackStrings_1_FEBetaTrojan.Win32.Korplug.FEC3
FE_Hunting_Win_ExportEngine_hex_CEFProcessForkHandlerEx_1_FEBeta
8F068700762CCE061A07AD62B66F57EE - GenericRXVT-IR!8F068700762C
E7C6FD4833C57249A6AB4480AC7DB0BA - GenericRXVT-IR!B74A162EFE4F
BackDoor-PlugX!EAFABA7898E1
Trojan:Win32/Korplug"
Conclusion
In conclusion, the rising tensions between China and Taiwan, coupled with the increasing number of cybersecurity attacks, is a cause for concern for individuals, businesses, and governments worldwide. It is crucial for everyone to remain vigilant and take necessary precautions to protect themselves from potential breaches. This includes adopting best practices for cybersecurity and staying informed about the latest threats. "... To navigate this complex landscape, Trellix' Advanced Research Center (ARC) utilizes our unique offerings, ATLAS and Insights, to provide advanced threat analysis and projection. Leveraging these insights and technology, we deliver preemptive, real-time defenses, ensuring the security of our customers' operations, regardless of industry or location."
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.