Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Global ESXiArgs Ransomware Attack on the Back of a Two-Year-Old Vulnerability
By John Fokker, Alfred Alvarado, Tim Hux, Jeffrey Sman, Joao Marques · February 09, 2023
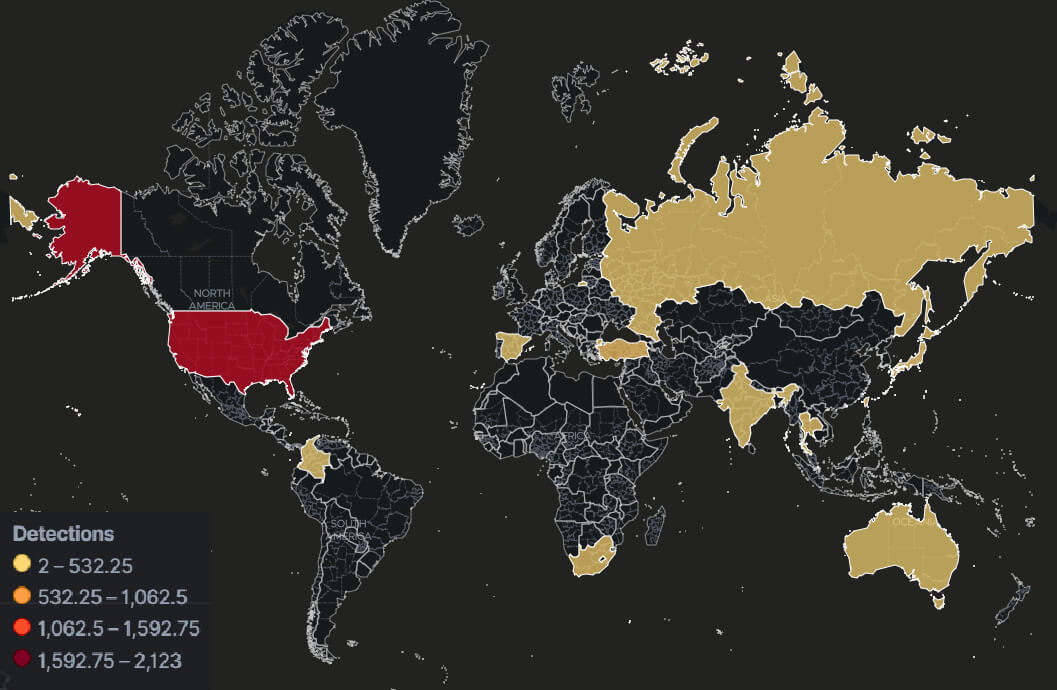
Introduction:
Early this week, VMware issued a publication regarding a massive global ransomware campaign targeting “End of General Support (EOGS) and/or significantly out-of-date ESXi products.” The vulnerability ransomware actors targeted is CVE-2021-21974 and allows an attacker to exploit the OpenSLP protocol if the affected server is exposed to the internet. VMware remediated the vulnerability and released a patch that has been available for general deployment as of February 23, 2021, as a precaution VMware also disabled the OpenSLP protocol by default for future product installations.
What is the OpenSLP protocol?
OpenSLP, the Open Service Location Protocol, was designed to allow machines in a local area network to discover services within the local environment. With that in mind, attackers are actively scanning internet resources for public facing devices to identify server services and or protocols that may be exploitable and have been exposed to the internet.
How it is it exploited?
According to VMware, the proof-of-concept code available and activity that has been observed, threat actors are actively scanning the internet for vulnerable ESXiArgs servers that are susceptible to this remote code execution vulnerability. Once the exploitable machine is identified the attacker attempts to create a heap buffer overflow and execute code remotely to compromise the server.
Often the vulnerable service or protocol has a patch available but not deployed and the threat actors use publicly known, or known to the attacker, code to exploit the vulnerabilities for initial access. As is in the case of the activity surrounding the ESXArgs attacks, the patch was available in early 2021; servers that are not updated or upgraded are targeted for compromise.
Our take
The ESXArgs ransomware activity follows VMware vulnerabilities previously reported on by our Trellix Advanced Research Center in 2022, (ContiESXi, NewGold). Once the vulnerability has been exploited, threat actors deploy a ransomware variant dubbed ESXArgs. This is due to artifacts identified in analyzed samples as well as the fact an “. args” extension is appended to targeted files, which also contain metadata that is suspected to aid in the identification and decryption process. Files targeted by the threat actors include those with the following extensions: “.vmxf”, “.vmx”, “.vmdk”, “.vmsd”, and “.nvram” extensions. Once the targeted data is encrypted, the malware performs clean up tasks to deleting log files, remove the Python based backdoor and delete various lines from several files to hinder recovery and analysis.
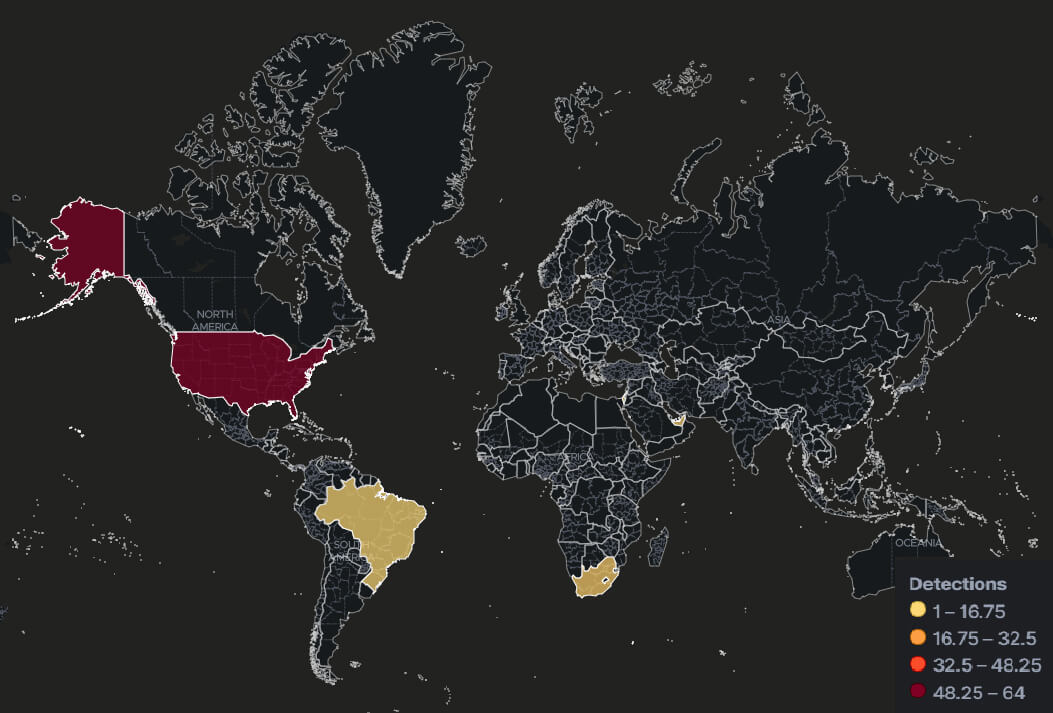
Remediation and mitigation
VMware has acknowledged the vulnerability exists and published a patch to fix the vulnerability in February of 2021. They have also provided documentation on the vulnerable versions currently being targeted as of their public release on Monday, January 6, 2023. Upgrading and/or patching is the recommended course of action where and as soon as possible, as well as the disablement of the OpenSLP protocol.
Furthermore, the Cybersecurity & Infrastructure Security Agency (CISA) has published a recovery script for those who have been victimized by the ESXiArgs campaign.
Conclusion
Conflicting information as to whether the malware has successfully exfiltrated data exists, and the variant of ransomware is speculated to be redeveloped source code form the leaked and now defunct Babuk Ransomware family. Regardless of speculation or fact, it is important server administrators follow recommendations for remediation by VMware to patch vulnerable servers and disable the OpenSLP service wherever possible.
The Trellix Advanced Research Center continues to monitor the ESXiArgs activity and will provide updates to telemetry, detections and indicators vetted by our research teams.
Indicators of compromise:
| 948e6d82d625ec2ebec2b2e5ee21ada8 | encrypt.sh |
| c358fe0e8837cc577315fc38892b937d | python.py |
| d0d36f169f1458806053aae482af5010 | encrypt.sh |
| df1921871117dc84e9d1faf361656a83 | encrypt.sh |
| 87b010bc90cd7dd776fb42ea5b3f85d3 | encrypt |
| 561f5507e28a8822e463b0bd274b71d2 | CVE-2021-21974.py |
| 03b318795ef7926d25f9ec3cb6b00cd5 | hostd-probe.sh |
| 566bc3ae2de680a524e2ec3fc2247826 | local.sh |
MITRE IDs:
| T1059 - Command and Scripting Interpreter |
| T1064 - Scripting |
| T1543.002 - Systemd Service |
| T1522 - File and Directory Permission Modification |
| T1027 - Obfuscated Files or Information |
| T1082 - System Information Discovery |
| T1083 - File and Directory Discovery |
| T1518.001 - Security Software Discovery |
| T1071 - Application Layer Protocol |
| T1573 - Encrypted Channel |
| T1070 - Indicator Removal |
| T1070.004 - File Deletion |
| T1574.002 - DLL Side-Loading |
| T1497 - Virtualization/Sandbox Evasion |
| T1070.006 - Timestomp |
| T1057 - Process Discovery |
| T1095 - Non-Application Layer Protocol |
| T1059.004 - Unix Shell |
| T1190 - Exploit Public-Facing Application |
| T1522 - Cloud Instance Metadata API |
| T1489 - Service Stop |
| T1486 - Data Encrypted for Impact |
Trellix Product Coverage:
| Product | Signature |
| Endpoint Security (ENS) | Ransom-ESXiArgs.a Backdoor-ESXi.a Backdoor-ESXi.b Backdoor-ESXi.c CVE-2021-21974 Linux/Encryptor Linux/Ransom!2902E12F00A1 |
| Endpoint Security (HX) | ESXIARGS RANSOMWARE LINUX (FAMILY) Trojan.Linux.Generic.293309 Trojan.GenericKD.65332757 |
| Network Security(NX) Detection as a Service Email Security Malware Analysis File Protect |
Ransomware.Linux.Generic.MVX Trojan.Linux.Generic.MVX FE_Trojan_Linux64_Generic_10 FE_Trojan_Linux_Generic_31 FEC_Exploit_PY_CVE202121974_1 FEC_Ransomware_SH_Generic_2 FEC_Backdoor_PY_Generic_4 FEC_Trojan_SH_Generic_14 |
| Helix | rule ID-1.1.3987 (ESXIARGS RANSOMWARE [Linux arguments]) rule ID-1.1.3989 (EXPLOIT - VMWARE [CVE-2021-21972 Success]) |
RECENT NEWS
-
Jun 27, 2024
Trellix Named an XDR Market Leader
-
Jun 11, 2024
Trellix Uncovers Spike in Cyber Activity from China and Russia
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.
