Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Safeguarding Election Integrity: Threat Hunting for the U.S. Elections
By Max Kersten, Ernesto Provecho, and John Fokker · December 20, 2024
With 2024 being a major election year globally, the stakes for election security were and remain high. More than 60 countries, including the United States, Mexico, India, and Indonesia, held elections and engaged nearly 2 billion voters. The U.S. general election on November 5th, 2024, drew significant attention due to concerns over potential interference and cybersecurity threats.
At Trellix, we recognize that election security is crucial to maintaining trust in democratic institutions. Our footprint in the U.S. public sector and our array of sensors around the world uniquely position us to support election integrity through proactive threat hunting. By leveraging our technology, the Trellix Advanced Research Center monitors and identifies malicious activities targeting election infrastructure or systems critical to the voting process.
Our research focuses on understanding and mitigating cyber threats impacting our customers. While we do not address misinformation campaigns, our goal is to detect and analyze malicious cyber activity. We prioritize telemetry data from U.S.-based sensors to identify threats that could compromise election integrity, providing timely insights and actionable intelligence.
By narrowing our focus to key sectors supporting election operations, we aim to deliver impactful insights and help safeguard the democratic process from evolving cyber threats. This targeted approach makes our threat hunting more effective, contributing meaningfully to the security of election infrastructure.
Threat hunting scope
Before looking at the specific data, it is important to define what is within the given scope, and what is not. In our case, the scope includes malicious activity towards or on devices from customers. Both mis- and disinformation are excluded as this is not what our products focus on. When talking about sensors, we refer to any type of Trellix product which sends back telemetry data.
Given that the volume of daily telemetry from all sensors is too much to comb through, two limitations have been imposed. The first is a geographical one, since only telemetry coming from sensors located within the United States are included. Interesting telemetry from other countries have not been ignored during this research, but aren’t included in this blog. The exclusion of non-U.S. telemetry is due to the location of the presidential election.
Second, the focus has been on a subset of U.S. based customers. The decision on who (not) to include in the subset is based on any sector which bears relevance with regards to the election process.
Results
The results are given below, and are split between the good, old fashioned telemetry, as well as telemetry from the Trellix EDR install base, as the two install bases differ in terms of what they report back.
Note that the telemetry consists of detections. A detection does not refer to a unique indicator of compromise, as the same indicator can be detected multiple times. As such, this does not state something about the variety of unique observed indicators, but rather the frequency of indicators which are deemed malicious.
Telemetry
To draw meaningful conclusions from the data at hand, all included telemetry has been manually combed through to see if additional information and/or analysis could contextualize and/or group findings into one or more clusters. This started with a list of U.S. based government customers (ranging from county and state levels all the way to the federal level), combined with a list of customers which are otherwise involved in the election process. The telemetry of these customers which was then looked into. Of the customers which had telemetry available, a subset was taken based on their geographic location. The ones within competitive, tipping point, or swing states were then looked into manually. These three definitions combined lead to the list of the following states: Arizona, Florida, Georgia, Michigan, Nevada, New Hampshire, North Carolina, Ohio, Pennsylvania, Texas, and Wisconsin.
The manual analysis ensured that files and URLs were analyzed, allowing the accurate labeling of the artifacts as relevant or irrelevant to potential U.S. election interference. A few artifacts were unknown, as they could not be found anywhere but at the customer. These unknown cases have been left as-is, as no conclusion can be drawn from them.
Both dis- and misinformation campaigns are out of scope for this research. The gray area between what is campaigning and what isn’t, is not for us to decide. The focus of this research is malicious interference in the elections via malware and/or phishing.
Docusign phishing campaigns
At Trellix we also observed the docusign phishing campaigns, as documented by Wallarm on the 5th of November. The campaigns were observed towards a variety of election related customers, as well as a wide variety of other sectors. As such, are confident in stating this attack wasn’t targeted to a specific sector nor customer. The attack is more likely to be opportunistic, looking for any target out there.
NetSupport RAT
The usage of a remote administrative tool, often shortened to RAT, is frequently used with malicious intent by threat actors. A RAT allows an attacker to completely control the infected machine. In this case, telemetry detections from Michigan between May and August 2024 showed malicious usage of the benign NetSupport Manager. This attack isn’t new, and has been documented in August 2023 by Trellix researchers.
Commodity stealers
Stealers have been, and will continue to be, prevalent. They are used en masse by a variety of threat actors. Their goal is to harvest credentials from unsuspecting victims, which are then re-used and/or sold via third parties. This allows other actors (i.e. ransomware gangs) to get access to a victim, and execute whatever attack they have in mind. Within the telemetry, hits for Snake Keylogger and AgentTesla have been observed between May and August 2024. These hits were found in Illinois and Florida.
Potentially Unwanted Programs and AdWare
Potentially Unwanted Programs (PUPs) are, usually, software to which the user did not (fully) consent to, as (a part of) the intent is hidden. Given that this depends on the information a user has, this is a potentially unwanted program. AdWare is software that pushes advertisements to the user, to which it has not consented.
A PUP campaign across various customers has been observed, along with AdWare at a subset of those customers, has been found in Texas, Florida, and Ohio, between May and August 2024.
EDR Telemetry
Trellix has different endpoint solutions that send telemetry data for further analysis. However, in this section, the scope is limited to the Trellix EDR solution, which provides useful information from processes, network communications, file system manipulations, and other system activity depending on whether the system is a Windows, Linux, or macOS.
At the moment, Trellix EDR has more than 3000 detection rules that are delivered and maintained by the Trellix EDR Research Team within the Trellix Advanced Research Center. These rules are organized not only by operating system and scope, but also by severity, which represents the likelihood of a rule to trigger, along with the impact of such detection. Trellix EDR has four different levels to represent severity, information or contextual, low, medium, and high.
When a rule triggers, an alert is created including information about the process that generated it, like the command line, the file path, or the hash, to mention some. This context will be key to successfully determine whether an alert is a true or false positive.
Analysis process
EDR telemetry can be overwhelming for an analyst due to its size, thousands of records are stored every single day from every host from every organization. In order to properly analyze the data, we followed a process consisting of three steps, detection checking, detection analysis, and post-analysis.
Detection checking
The first step was checking the different alerts that were triggered and could be categorized as uncommon. However, due to the high alert volume that analyzed organizations faced, such detections needed to be sorted in order to prioritize the most critical ones. To do so, we followed the next scheme:
-
High severity rules: start with high severity rules, then medium, low, and, finally, contextual ones.
Uncommon rules: check those detections triggered by rules that are not that frequent. If a rule triggers too often, there is a high probability that the behavior is a controlled one. Also, depending on the case, there are rules more prone to generate false positives, which will be reflected in the number of alerts generated.
Uncommon detections in clients: similar to the previous check, but in this case the detection frequency is filtered by each organization.
Newly discovered techniques: usually, threat actors tend to be updated in terms of capabilities, trying novel techniques as soon as they are available. The main reason is to try to stay under the radar of security software, which might not cover the new technique.
After every single step has been completed, the remaining detections should also be checked, so as to confirm no successful breach has happened.
Detection analysis
When starting analyzing a detection, it is important to have in mind that their complexity can vary depending on the context, and the employed technique. There might be some detections that are easily discarded just by checking the command line, while others may require a deeper analysis.
There are several details we need to check to determine the maliciousness of a detection, these can be organized as follows (the order do not determine the priority in this case):
Command line: usually, among the detection details, a command line is given. This information can be really important to determine whether an alert is legitimate or not. However, it is recommended to continue with the analysis process to completely discard it. The following command line showcases a legitimate execution that can be confused with an attempt by ransomware operators to disable the Volume Shadow Copy Service (VSS).
Execution chain: understanding the execution chain of a process can help to rapidly determine the legitimacy of a suspicious behavior. Nevertheless, sometimes, even if the process has been executed by a legit application or apparently by the user (usually the parent process will be explorer.exe), we need to continue with the analysis, since a process injection or other bypassing techniques might be executed to hide the infection.
Network activity: malicious processes tend to communicate with their command and control to request new orders or exfiltrate information, to mention some techniques, this is why it is important to check the network activity of the detected process, something that needs to be done keeping in mind it is also a common behavior for legit processes.
Previous rule alerts: a single rule can be triggered several times by a malicious actor while trying to compromise a system. However, when this rule is triggered during a certain period of time and the number of alerts is relatively big, it is probable that the behavior is legitimate and the rule needs to be fine tuned, a statement that needs to be verified with further checks.
Other related detections in the same system: generally, alerts don’t come alone, something that happens due to the different techniques malicious threats tend to use during a campaign. If a system does not have any related alerts, it is probable that the previous steps of the intrusion were performed in another system or it is a false positive.
Other related detections in the same organization: this case is similar to the previous one, infections tend to propagate to different systems within the organization to obtain more sensitive data or cause greater disruption, so it would be normal to have linked detections in various systems. If an organization does not have any related alerts, it is probable that the previous steps of the intrusion were performed in an unprotected system or it is a false positive.
Rule goal: another aspect to check is what is the goal of the rule, what aims to detect. There will be rules that have been created to detect just some anomalous behavior, while others have been built to catch behavior that can probably be categorized as malicious.
vssadmin resize shadowstorage /For=C: /On=C: /MaxSize=5%
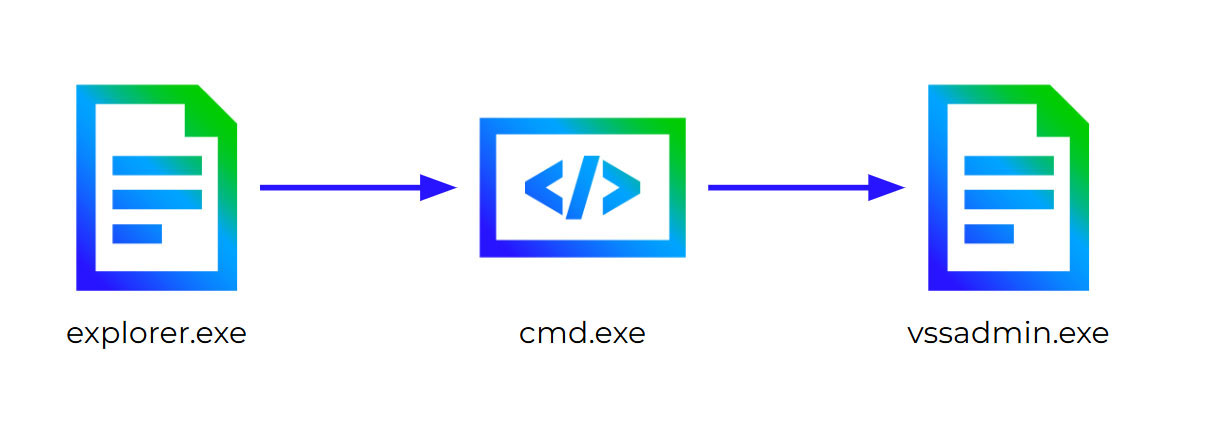
In other cases, there can be further checks in the case the organization has provided some information about their systems and activities, like if a specific remote access tool is allowed or a penetration system is being carried out during the hunting phase.
Post-analysis
The outcome of the analysis of a detection can be one of these possibilities, confirmed attack, confirmed legitimate activity, or suspicious behavior, in this case, we are not sure if the behavior was a real attack or a controlled activity.
In the case of a confirmed attack, there are some steps that need to be performed in order to contain the threat and prevent future attacks.
-
Alert the organization: to successfully contain the infection, the affected organization needs to be informed as soon as possible, including the required information to completely understand what we know about the intrusion. Once notified, the corporate managers will determine the necessary steps to contain, remove, and prevent future incidents. This may include the execution of an Incident Response (IR) assessment to better comprehend the threat and which assets have been compromised or stolen.
Rule check: to better detect malicious activity in the future, an analysis to verify which behaviors are covered by the current rule set and which are not needs to be done. Also, maybe the rules that detected the activity can be improved, something that needs to be done the threat behavior could be detected by a rule. In both cases, the outcome should be the same, rules update or the creation of new ones.
Intelligence: after the analysis, the obtained information, including Tactics, Techniques, and Procedures (TTPs) and Indicators of Compromise (IoCs), can be useful to understand the threat and prevent future attacks.
On the other hand, if the activity was legitimate, the rule that triggered the alert should be checked and updated, if necessary, to minimize future false positives.
Finally, it might be the case that the analysis of a detection does not yield any specific result. In such cases, the approach would be alerting the organization and, once they have confirmed whether the activity was malicious or legitimate, take the appropriate steps to address it.
Observed detections
During the election period, we monitored the EDR telemetry from different organizations from the U.S. that primarily belonged to the government sector. The analysis did not yield any positive results or infections, however, we have included the analysis of three suspicious behaviors to showcase the work done by Trellix.
Suspicious RClone execution
Different executions of the RClone utility were detected in one of the monitored organizations during the first days of November, before the elections took place. RClone is a legitimate tool, but it has been abused by malicious actors in the past, specially ransomware operators, to exfiltrate sensitive information.
The RClone executions had the following command line.
"C:\Program Files\IDM Computer Solutions\Common\UltraCloudStorage\rclone.exe" rcd --rc-web-gui-no-open-browser --rc-no-auth
The command simply starts the RClone utility so that it only listens to remote control commands, so apparently, it did not indicate any malicious behavior. Further inspection in the organization telemetry showed that this utility was actively used in different systems. Moreover, no other related detections were triggered, indicating that the behavior was completely legitimate and controlled.
Suspicious remote access applications
During November 5th, the U.S. presidential election day, different alerts were triggered by a suspicious execution of a remote access application in one of the organizations, the Bomgart Remote Support Tool application.
This kind of tool is usually installed by systems administrators to manage the different systems within an organization, however, it is also a way for attackers to fully control a system, something that ransomware operators have done in the past.
One of the alerts was triggered due to the remote control tool being configured to run at system 1startup using the following command line.
C:\Users\[REDACTED]\AppData\Local\BeyondTrust\bomgar-scc\[REDACTED]\bomgar-scc.exe --uninstall
The command line was intended to uninstall the current installation of Bomgar Remote Support Tool, probably due to some update, but no malicious behaviour was observed.
A deeper look at previous Bomgar Remote Support Tool executions showed consistent activity during the last weeks in different systems, suggesting the tool was installed by system administrators.
While checking other alerts, another remote access tool was discovered in the same organization, in this case TeamViewer. However, it also had different executions during the previous weeks.
The analysis of other potentially related alerts did not yield any positive result, which suggested that the presence of such applications seemed to be legitimate.
Suspicious BCDEdit execution
During the days after the U.S. election several alerts were triggered regarding a suspicious execution of the Boot Configuration Data (BCD) Windows tool, also known as BCDEdit, in one of the organizations.
bcdedit /set recoveryenabled No
"C:\WINDOWS\system32\bcdedit.exe" /set -encodedCommand YwB1AHIAcgBlAG4AdAA= recoveryenabled No -inputFormat xml -outputFormat text
bcdedit /set {current} recoveryenabled No
The execution of these commands are usually seen in ransomware incidents to prevent data recovery. However, in this case, no other related rules were triggered, so it was unlikely that a ransomware was deployed.
Moreover, checking the execution chain of these commands revealed that they were executed by gpscript, the Group Policy script orchestrator process. Something that suggested it was handled by the system administrators of the client
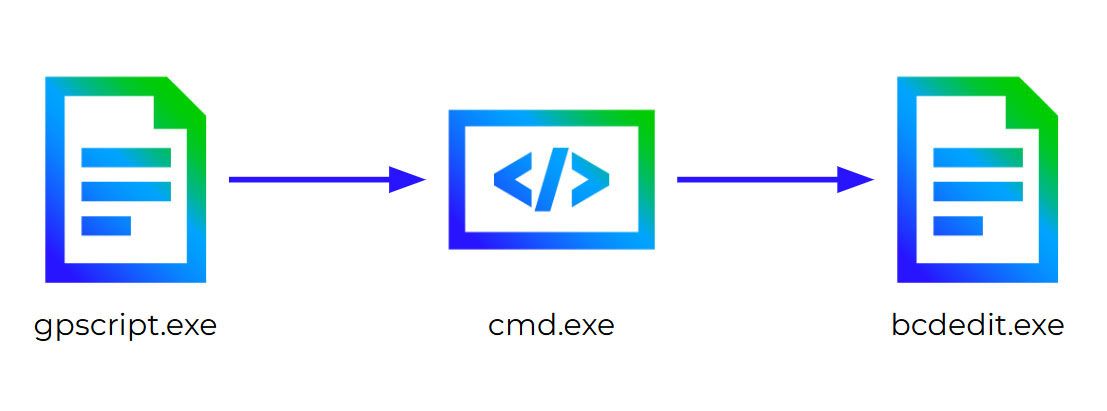
The full analysis made us believe this behavior was legitimate, discarding the execution of any malicious program.
Typosquatting
Trellix telemetry can also be used to search for external threats. The observed domain names within the telemetry were used to obtain a list of domains which matched one or more keywords from a given list.
This keyword list was compiled to narrow the vast amount of telemetry down to a chunk which contains useful information. The next step in the process required manual verification of the observed domain names, as partial matches of domains aren’t necessarily a true positive. To illustrate, the word “election” is present in the word “selection”. Boutique shops aren’t in scope for the election, and are thus excluded from this research.
The filtered list of domains with domains related to the election contained the official party websites, voter guides from the federal, state, and local levels, as well as campaign merchandise and donation websites. Using dnstwist, permutations for all given domains were generated. Opting to only store existing permutations, a DNS request per permutation was required. Several million permutations later, a few thousand existing seemingly typosquatted domains remained.
The problem with using DNS to check if a domain exists lies with the sales websites for said domain. Often, a domain is parked, with a registrar or provider stating the domain is for sale. Manually visiting all sites is a tedious and slow process, and is not the favorable route. Instead, with the help of some Python and Selenium, a screenshot from each website can be taken. Saving each screenshot with the domain name as file name allows one to correlate the image and domain. Viewing all images using a file explorer with extra large thumbnail icons set allows a quick check for non-parked and valid-looking typosquatted domains.
The minor cryptoscam
Barring a few redirects, the search resulted in two typosquatted domains. The first domain, trrump[.]com, loaded a single image. Note the double ‘r’, where only one is present in the actual The image, shown below, shows a website with a Bitcoin QR code on it, to which no funds were transferred. The image (which displays the fake donation site) had an on-click event connected to it, where it would prompt the user to share it on Twitter. Note that the QR code at the top right corner of the image has been blurred.
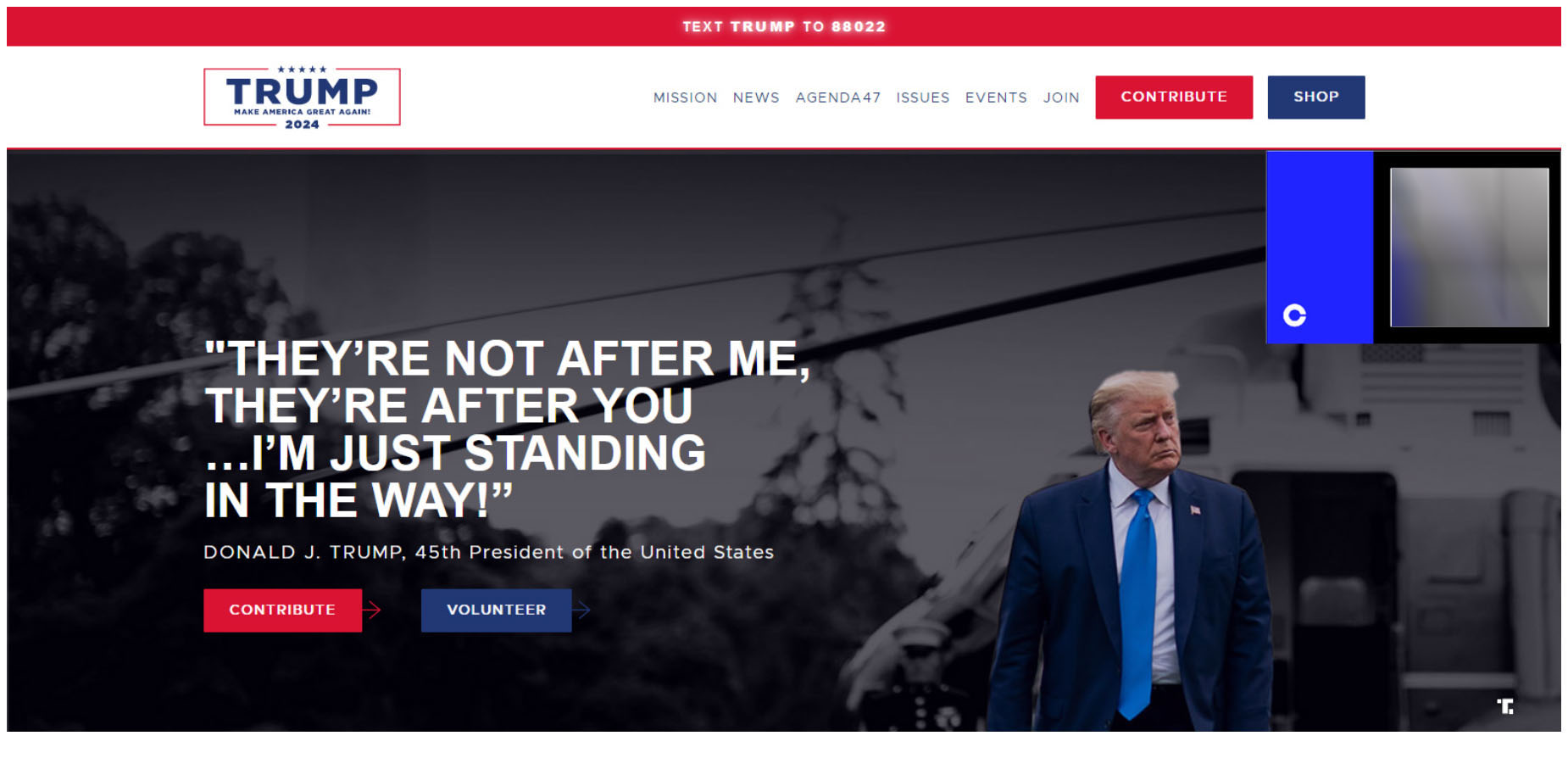
With the help of Mandiant, additional insight was gained into this campaign, as it was spread via multiple social media platforms, including YouTube.
The major cryptoscam
Much like the minor cryptoscam website, the goal of this scam is to obtain cryptocurrency under the guise of donating to the 2024 Republican presidential candidate. The website (doonaldjtrump[.]com, note the “oo” in the beginning) is HTML- and JavaScript-based, compared to the image in the previous example. The website’s functionality is limited, only the “happy flow” in which a visitor wants to donate money, is implemented. Other links are simply not referencing anything.
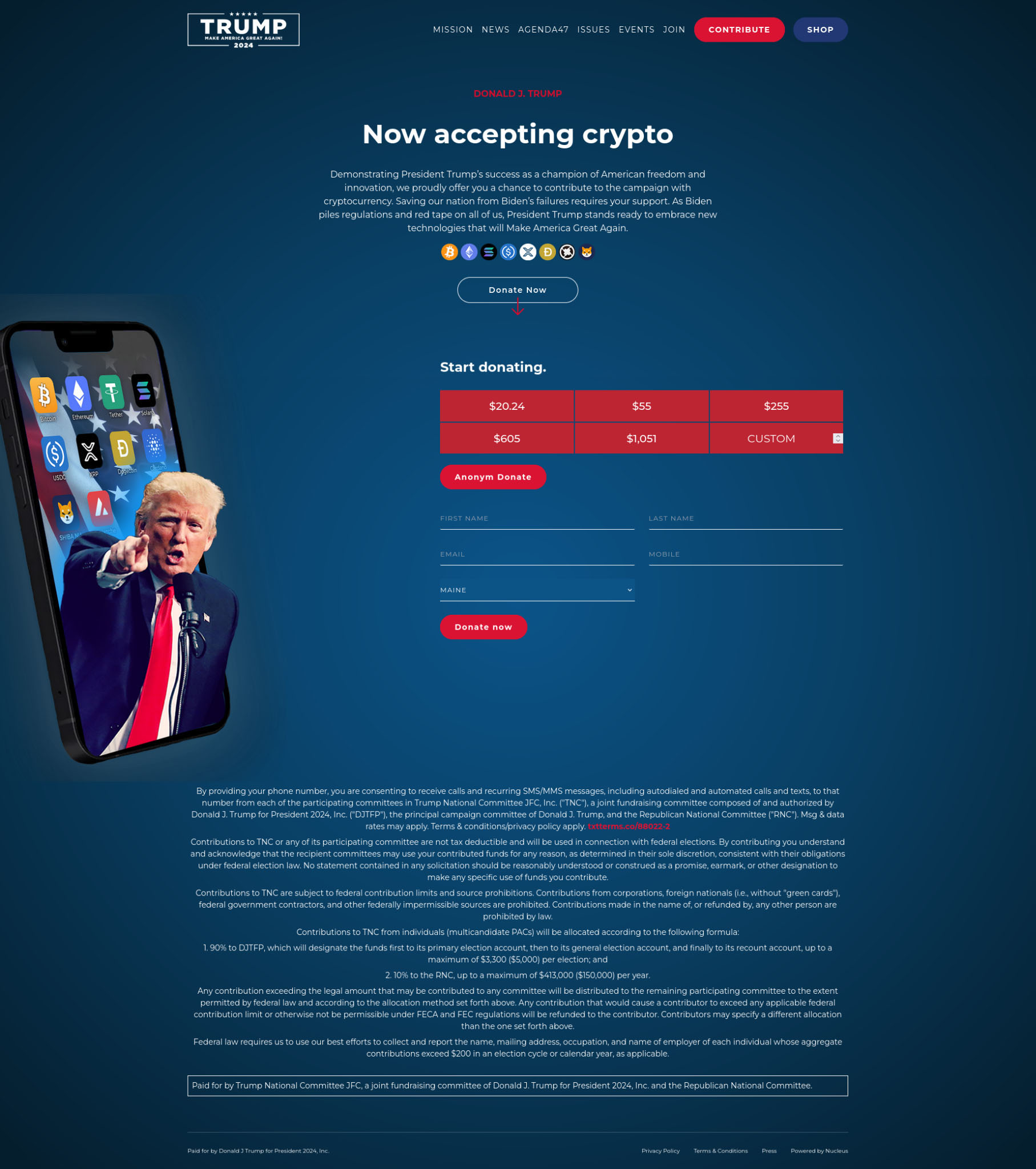
Upon following said “happy flow”, it is possible to move on to the donation page. The donation page is another typosquatted domain with the reference to CoinGate, but spelled as “coingaete[.]com” with an extra “e” after the “a”. The image below shows the typosquatted donation page.
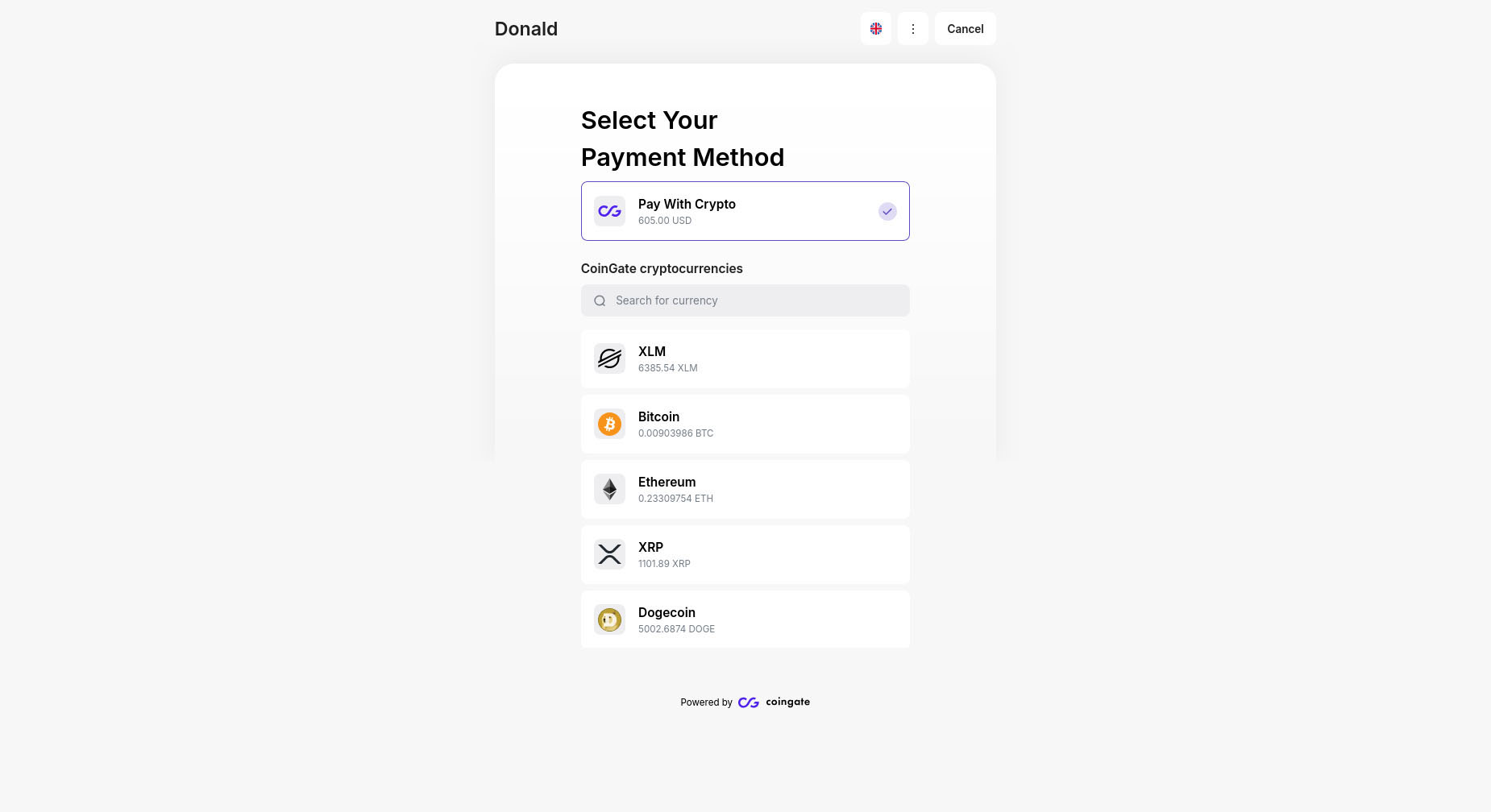
Paying with crypto is the only option, although there are multiple cryptocurrencies available to “donate” with. The wallet for each different currency is generated for each visit to the CoinGaete scam site, which resulted in a lack of findings and insights related to scammed funds. Each visit to CoinGaete via the original scam site creates a different GUID. Revisiting the site with the GUID as part of the URL will show the same wallet addresses.
Much like the previous case, Mandiant also investigated this finding and found overlap with other scam sites. Additionally, an overlap with gift card scam campaigns has been observed, indicating a broader approach from the same actor(s).
Conclusion
During our research with the Trellix telemetry, we found no traces of election interference. The election did garner the attention of opportunity-based grifters and scammers, as showcased in the typosquatting section. These scams aren’t unique to the election, they are merely the same scam with a different cover story for the time being.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
