Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
When SPNs Go Rogue: Detection and Remediation with Trellix NDR
By Maulik Maheta and Henry Bernabe · February 10, 2026
Executive summary
Service Principal Names (SPNs) are essential for Kerberos authentication in Active Directory (AD), but misconfigurations, such as assigning SPNs to standard user accounts enable Kerberoasting. After obtaining valid domain credentials, attackers can list SPN-enabled accounts and request Kerberos TGS tickets, which are then extracted and cracked offline using tools such as hashcat to recover service account credentials.
Because this technique exploits legitimate Kerberos functionality and cracks passwords offline, it avoids account lockouts and produces minimal authentication noise, making it difficult to detect by traditional log- or signature-based defenses. Misconfigured SPNs turn ordinary accounts into high-value targets, allowing for stealthy privilege escalation.
To address this detection gap, the blog shows how Trellix Network Detection and Response (NDR) detects Kerberoasting activity by analyzing deviations in identity behavior and comparing network-level telemetry. Detected events are enriched with contextual metadata, mapped to the MITRE ATT&CK framework (T1558.003 - Kerberoasting), and accompanied by actionable remediation guidance via integration with Trellix Wise, an AI-driven investigation assistant. The Trellix Knowledge Graph improves visibility by combining users, assets, techniques, and alerts into a single threat model, enabling faster triage and the identification of related exposure paths.
What is the process of Kerberoasting?
Kerberoasting is a post-exploitation attack method that targets Kerberos-based authentication in AD. It entails exploiting SPNs, which are identifiers that connect service accounts to specific services within the domain. SPNs are typically associated with privileged service accounts, but misconfigurations can occasionally bind them to standard user accounts, resulting in unexpected exposure.
This is how the attack works:
- SPN enumeration: After obtaining valid domain credentials, the attacker scans for accounts with registered SPNs, which are eligible for Kerberos service ticket requests.
- Requesting TGS tickets: After identifying the SPN, the attacker requests a Ticket Granting Service (TGS) ticket. The ticket is issued by the Key Distribution Center (KDC) and encrypted with the NTLM hash of the target account's password.
- Exporting the ticket: The attacker extracts this ticket from memory (e.g., using GetUserSPNs.py) and saves it in a format where password extraction tools like hashcat can be used.
- Offline cracking: Because the encryption is linked to the password hash, the attacker can use offline brute-force or dictionary attacks to recover the plaintext password without informing the domain controller or risking account lockout.
Before going into detail Please refer to our previous blog, where we discussed the 'Crown Jewels' scenario, in which an attacker with Domain Admin privileges extracts the entire directory database. But how does an attacker gain that level of access in the first place?
Kerberoasting is frequently used as an answer. Unlike NTDS dumps, which require high-level administrative rights, Kerberoasting can be performed by any authenticated user with no special privileges, making it an important step in the attack lifecycle.
Attack flow: From misconfiguration to credential theft
End-to-end Kerberoasting attack flow for network detection and response Figure 1 shows the full Kerberoasting attack chain, beginning with user compromise and ending with lateral movement and service access, as well as multiple network detection and response (NDR) visibility points. To extract reusable credentials, this attack exploits misconfigured Service Principal Names (SPNs) in an Active Directory environment, as well as weak Kerberos encryption. The attack begins when a victim user unknowingly visits a malicious website. During this interaction, the attacker's machine downloads a malicious binary. At this point, the binary exists as a network malware object, which Trellix NDR can already detect based on reputation, file transfer patterns, or unusual download behavior.
When the victim runs the binary, it creates a callback connection to the attacker's command-and-control (C2) server. This outbound callback is a critical detection opportunity because it frequently deviates from typical user traffic patterns and can result in network callback alerts.
After gaining execution on the victim's system, the attacker uses a credential dumping tool (such as Mimikatz). Credentials from System A are extracted, including NTLM hashes and Kerberos tickets that are stored in memory. This enables Pass-the-Hash (PTH) and Pass-the-Ticket (PTT) attacks, which allow the attacker to authenticate as the compromised user without knowing the plaintext password. At this point, the attacker has successfully moved from initial access to credential access and privilege abuse, significantly expanding their reach in the environment.
The next step is SPN enumeration and Kerberoasting; for further details, please see the rest of this blog section.
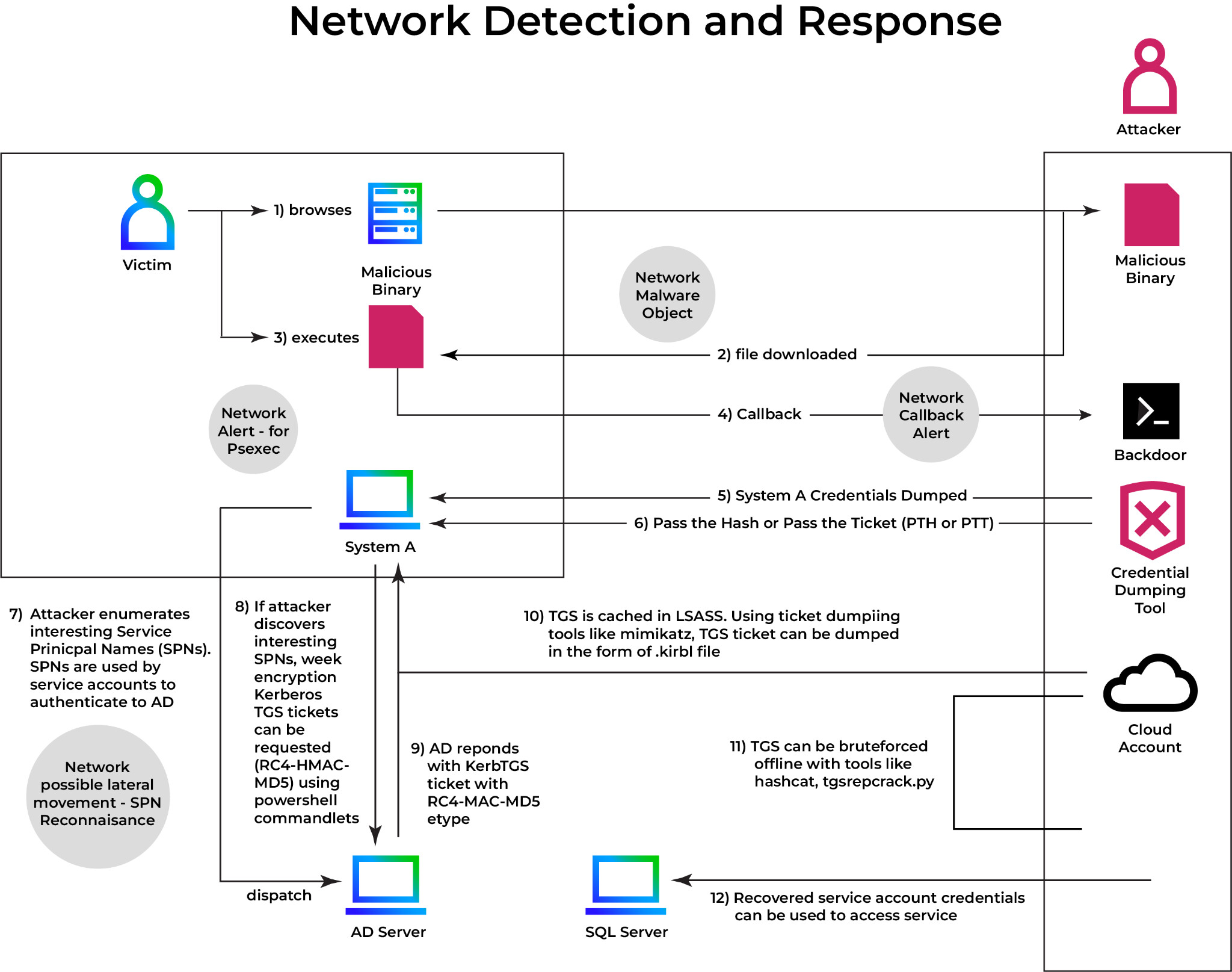
Figure 2 shows a critical oversight: an SPN (e.g., MSSQLSvc/...) is assigned to a standard user account rather than a service account. When SPNs are assigned to ordinary users, they expose the user's password hash to offline cracking, which is important because SPNs are meant to represent services in Kerberos authentication. In this example, the user account "Trellix" is associated with a service SPN, making it a valuable target for Kerberoasting despite the fact that it does not run a service.
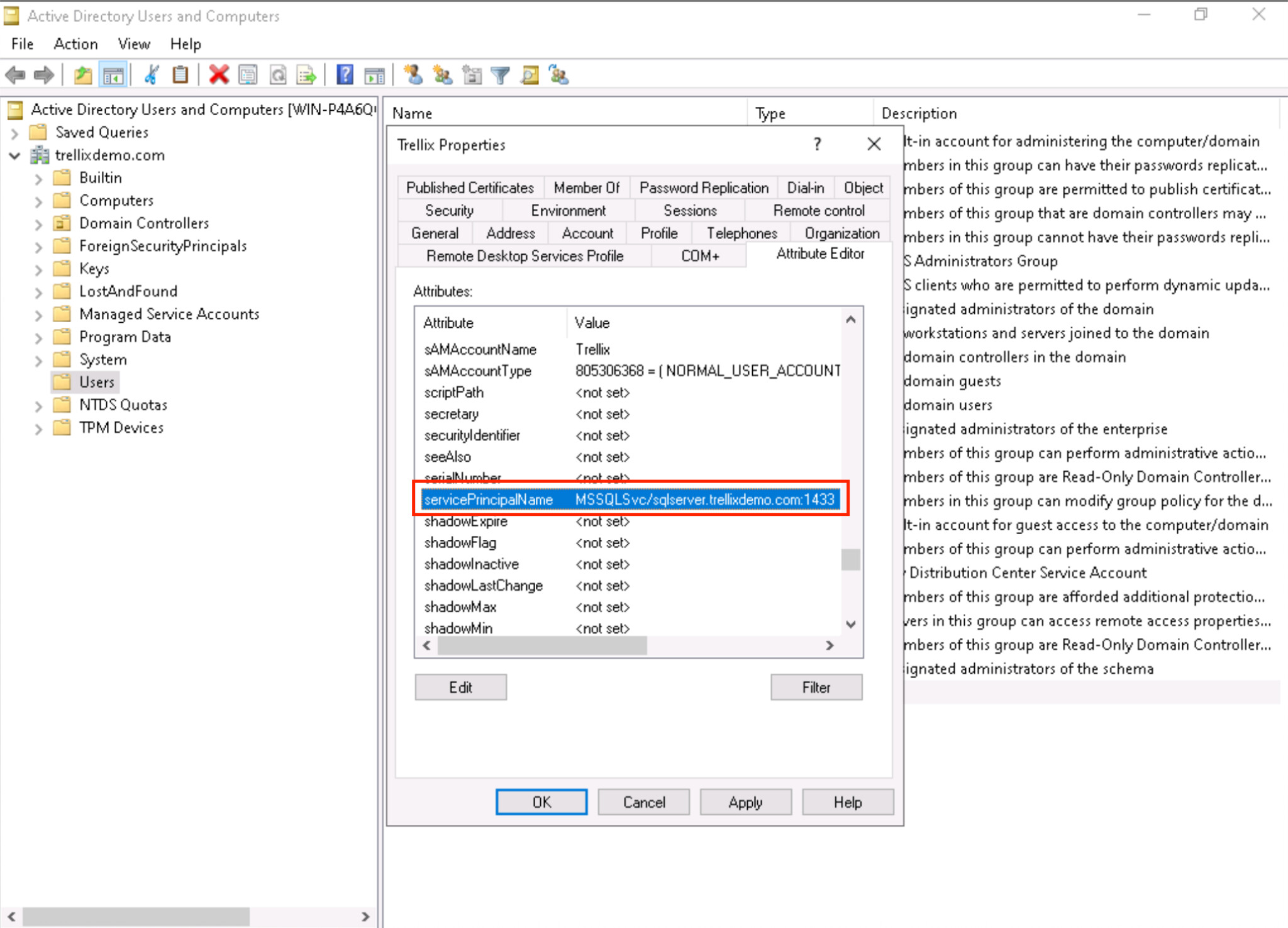
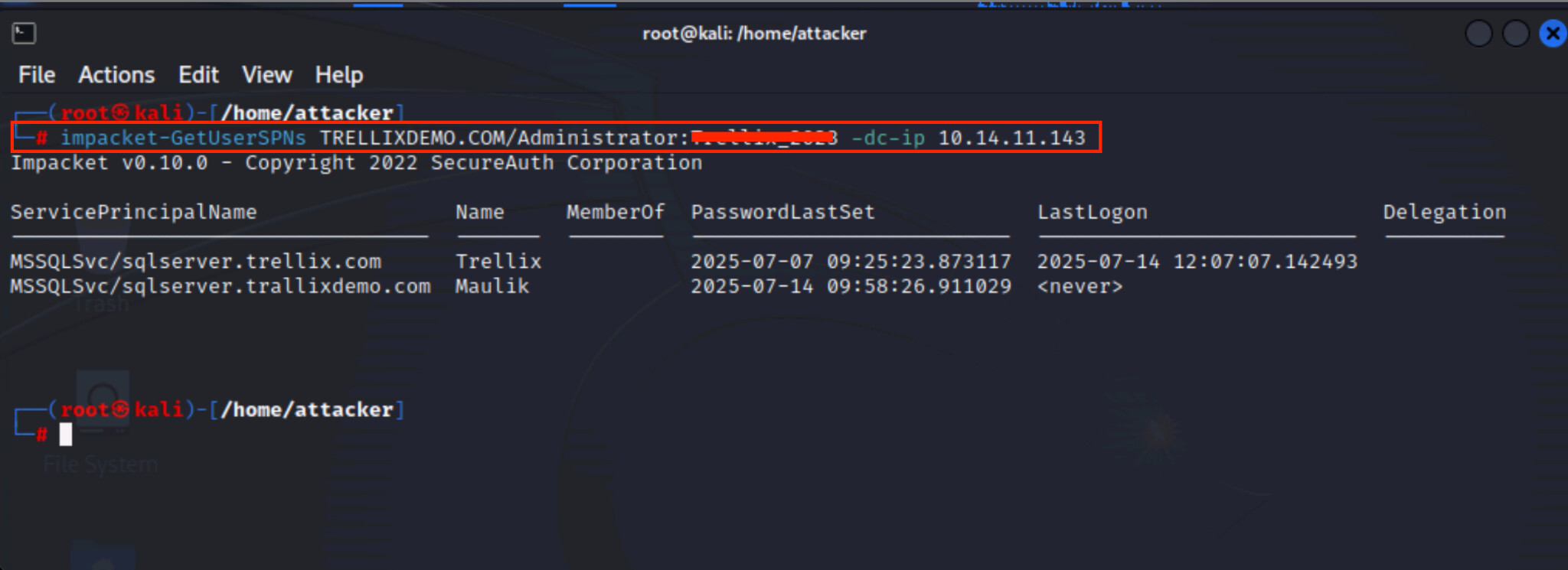
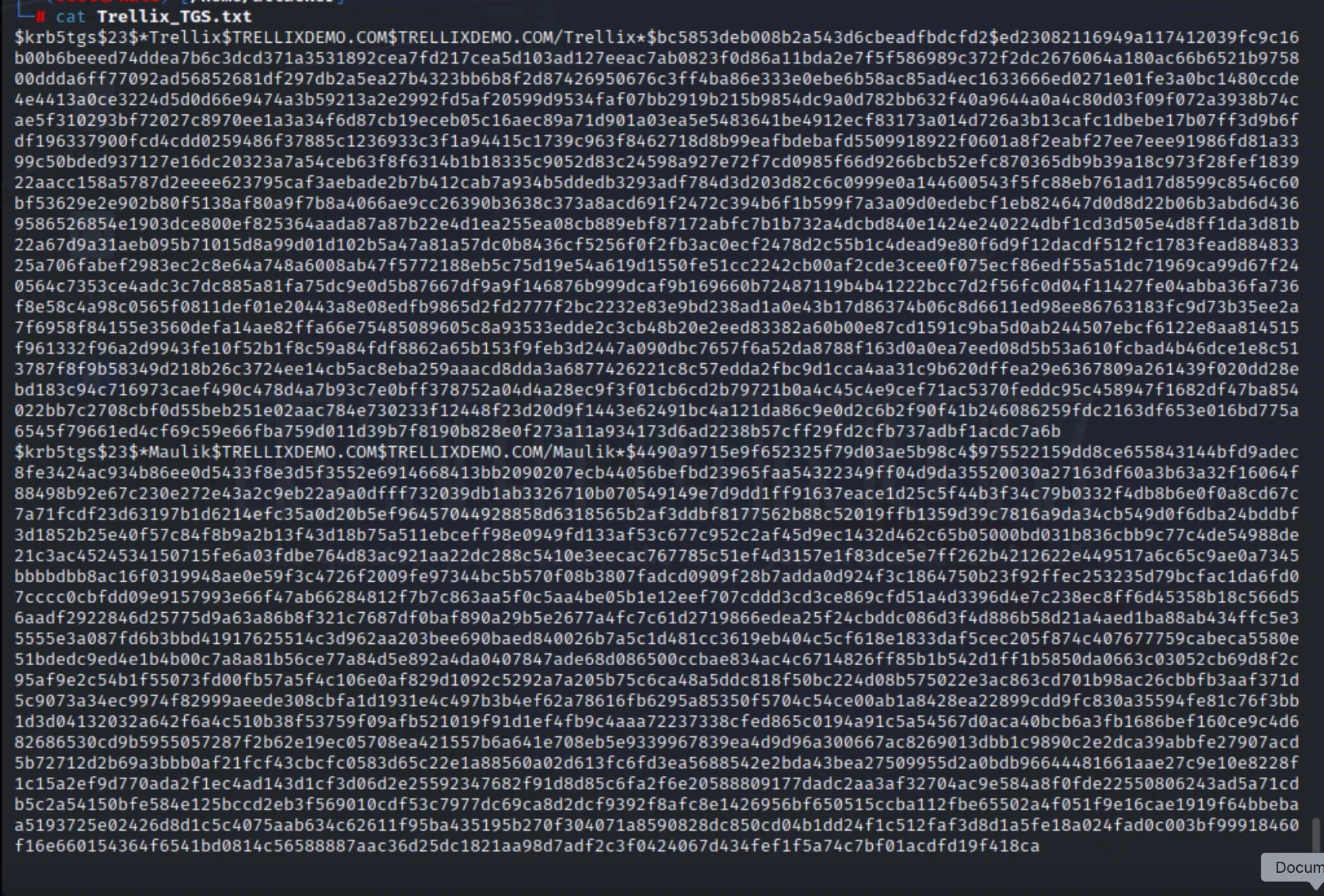
Figure 3 shows the attacker using Impacket's GetUserSPNs.py script to list all accounts in the domain that have SPNs. This post-compromise reconnaissance technique looks for exploitable accounts like "Maulik," “Trellix” by retrieving service ticket metadata such as encryption type and associated user. This enumeration is stealthy, only requires valid domain credentials, and is commonly used in Kerberoasting attacks to set up the next phase.
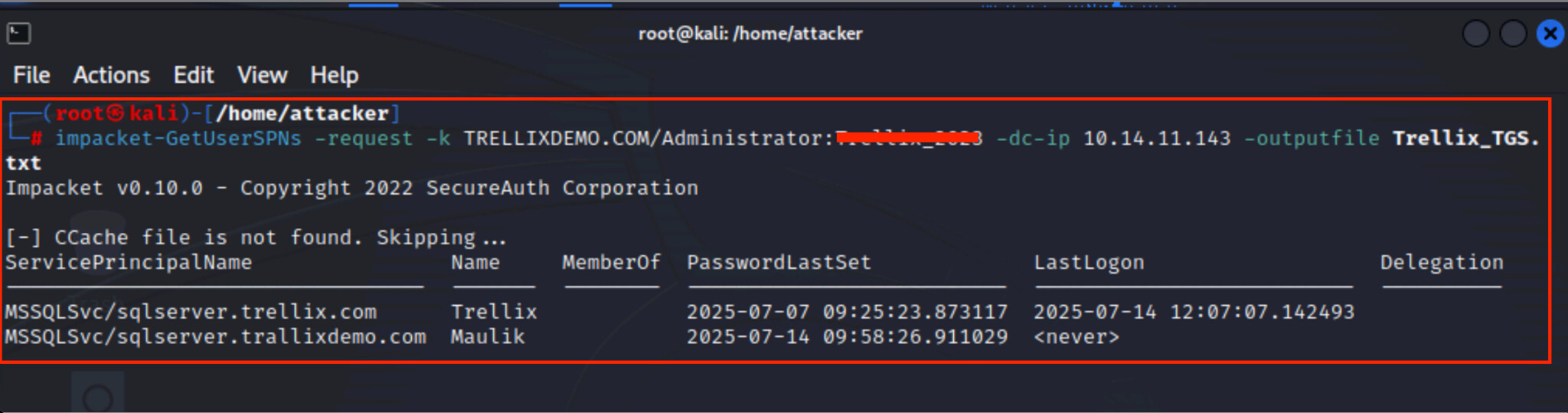
As shown in Figures 4 and 5, the attacker requests a TGS ticket for an SPN-bound service account discovered during enumeration. While attackers typically prioritize accounts that support legacy encryption, such as RC4-HMAC (Type 23), because they are easier to crack, Kerberoasting is not limited to weak encryption. Even with more powerful algorithms, such as AES, tickets can still be compromised if the underlying service account password is weak. The issued TGS ticket is extracted and converted to a hashcat-compatible format, allowing for an offline brute-force or dictionary attack on the service account credentials without requiring further interaction with the domain controller.
Detection: Trellix NDR
Trellix NDR utilizes Trellix Wise, an AI-powered investigation assistant, to enhance threat detection and response capabilities. Trellix Wise automates many aspects of alert investigation, reducing false positives and accelerating the time-to-resolution for security teams. This integration enables organizations to achieve greater threat-detection accuracy, automate complex tasks, and focus on strategic defense.
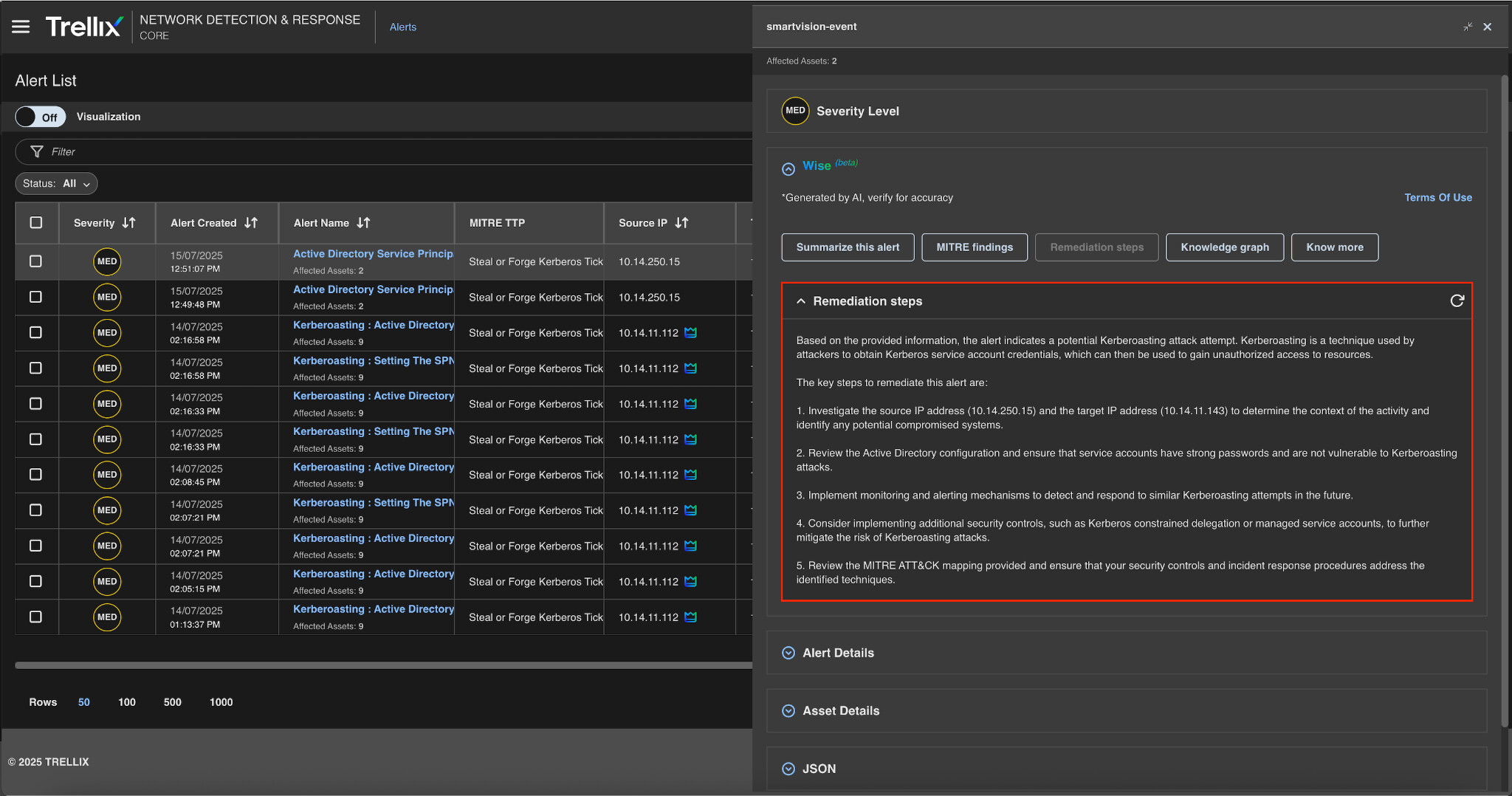
Trellix Wise can provide a user with comprehensive details, such as additional information on the alert, remediation steps, MITRE information, etc.
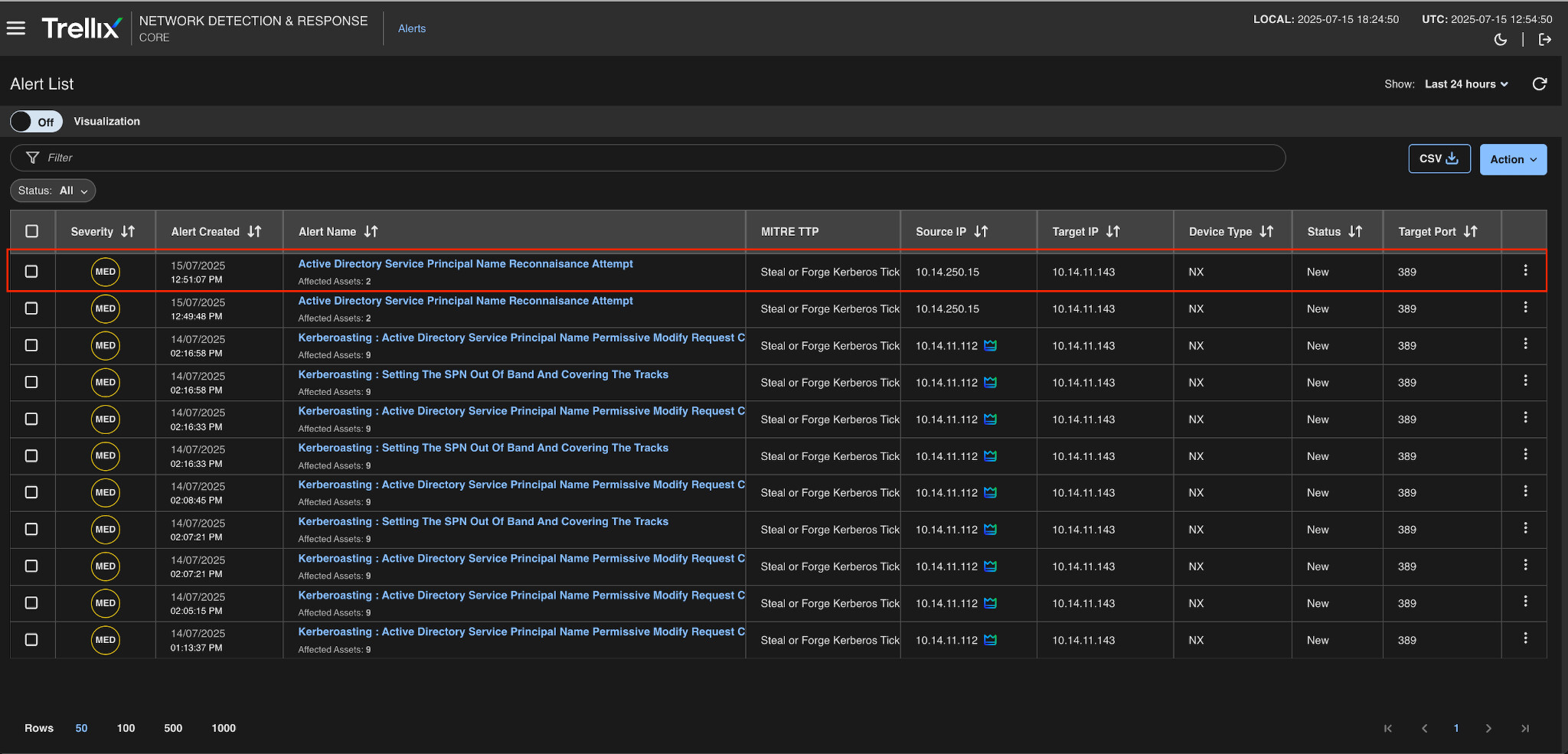
Figure 6 shows a near real-time alert from Trellix Network Detection and Response (NDR) that was triggered by suspicious SPN activity.
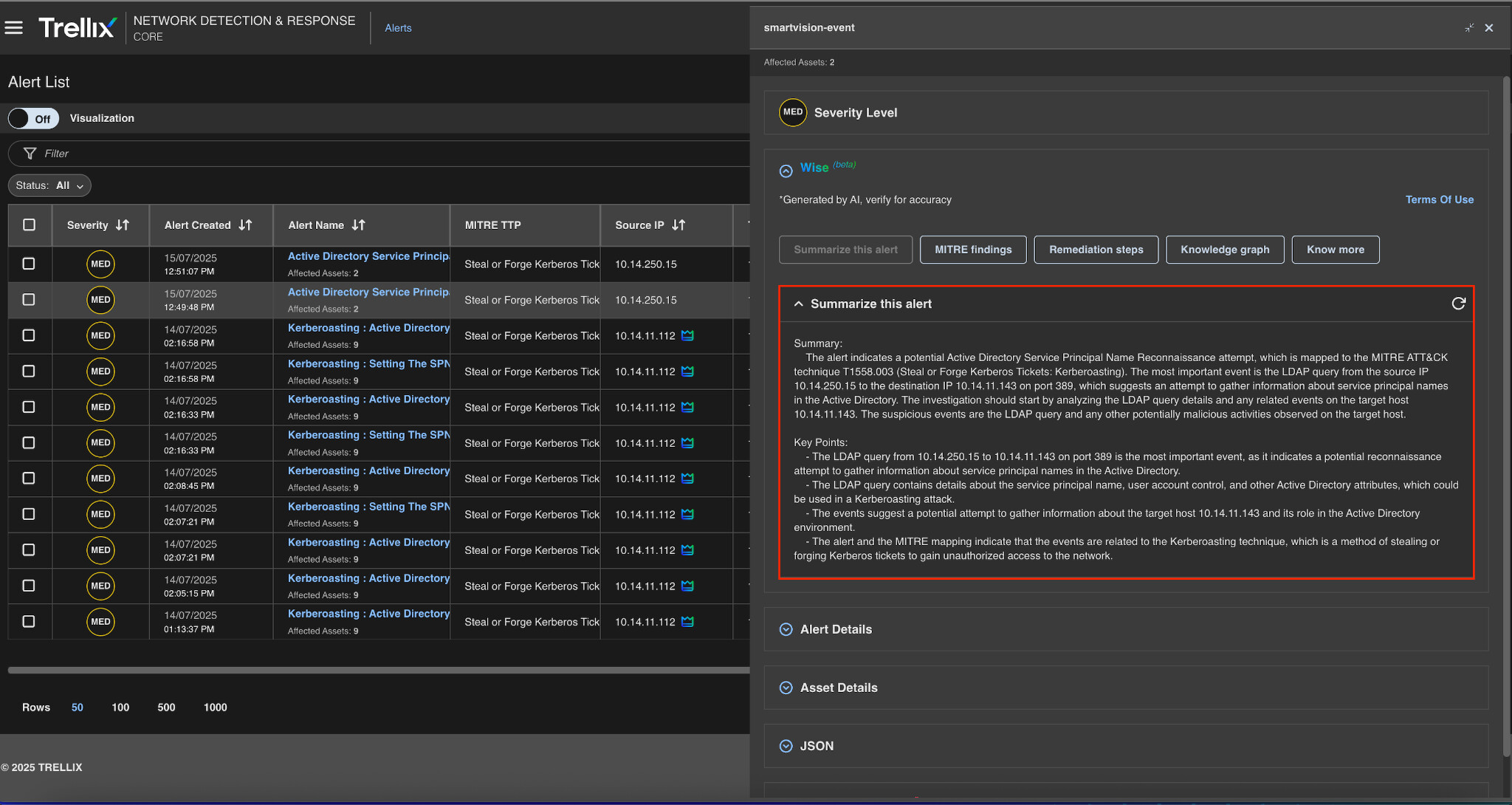
Alert summary
Figure 7 shows an in-depth description of the Trellix NDR alert. The IP address, activity type, and modified object (user account with related SPN) are all included in the metadata.
The detection signature or behavioral rule has been triggered. This level of detail aids analysts during triage by providing them with an immediate understanding of the event's context and scope.
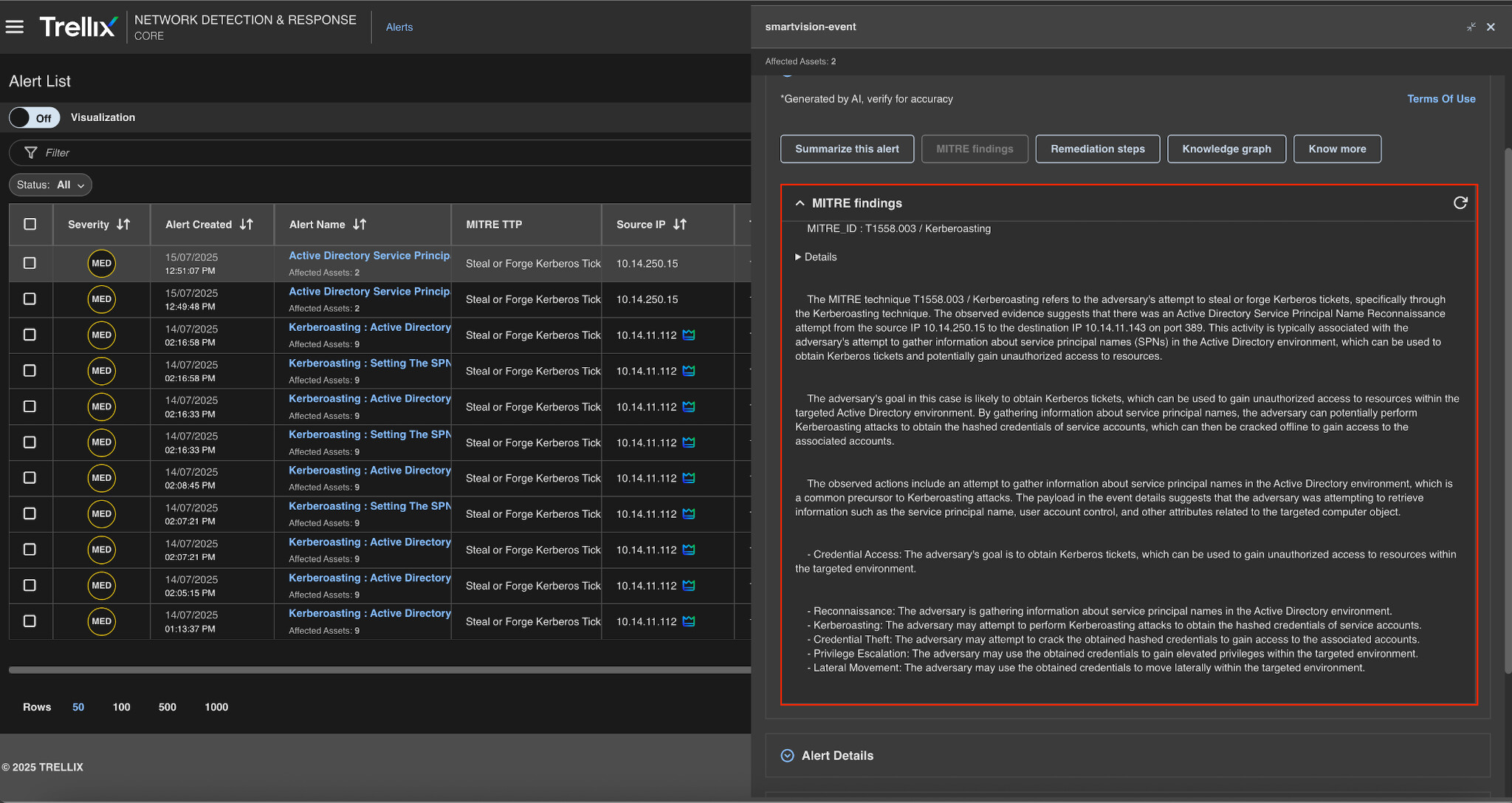
MITRE findings
Figure 8 shows how the observed attacker behavior corresponds to the MITRE ATT&CK framework, specifically technique T1558.003: Kerberoasting. Defenders can gain structured visibility into adversary tradecraft by combining near real-time telemetry with ATT&CK techniques. This alignment also allows for more consistent reporting, supports purple teaming exercises, and promotes proactive detection tuning based on common attacker patterns.
Remediation action
Figure 9 depicts Trellix's recommended remedial actions after detecting SPN misuse. These consist of: Removing SPNs from inappropriate accounts, changing the passwords of the impacted users, auditing and reducing excessively permissive access rights.
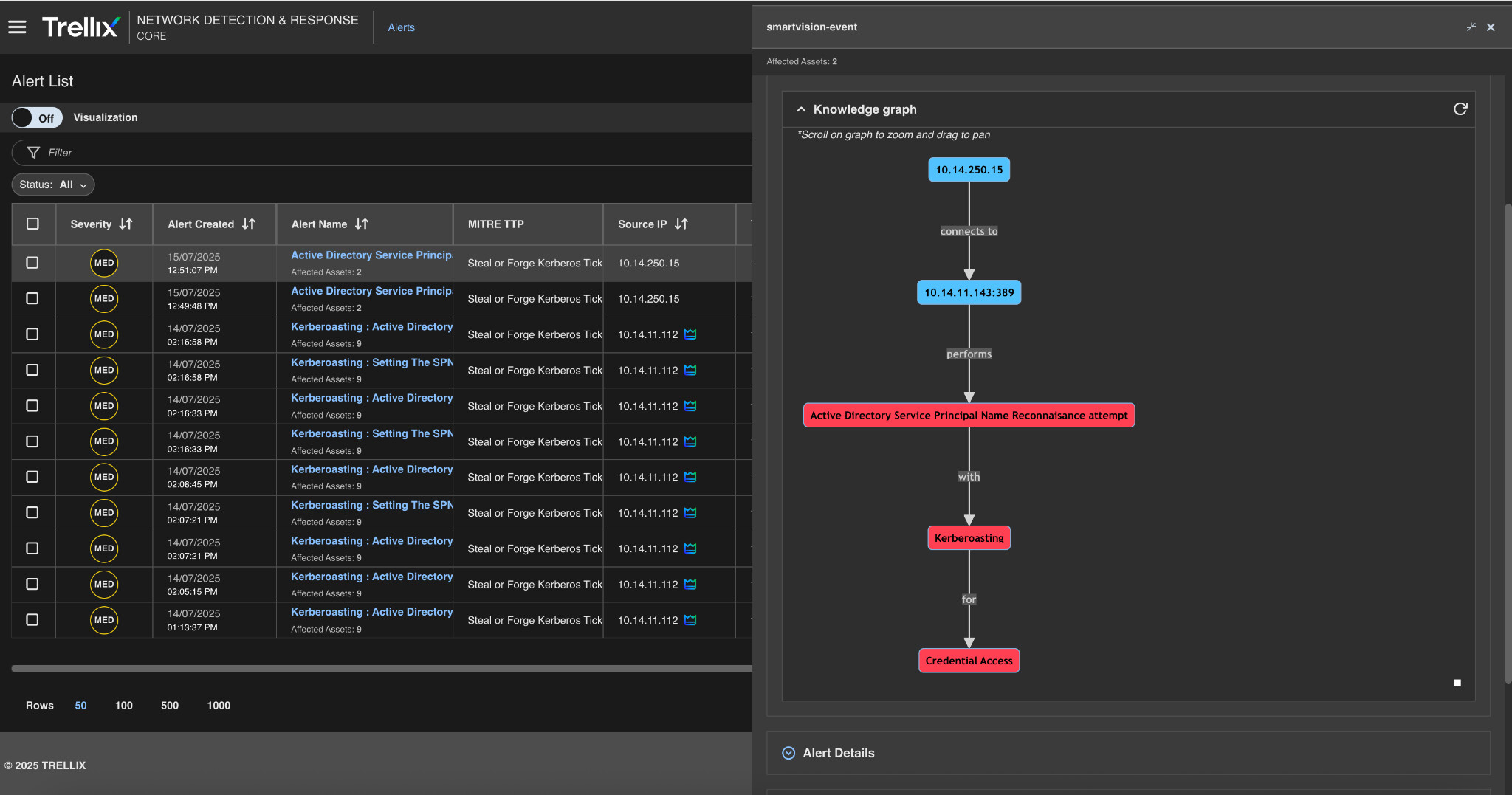
Knowledge graph
Figure 10 shows the Trellix knowledge graph, which links users, assets, techniques, and alerts into a single threat storyline. In this case, the graph shows the relationships between the misconfigured SPN, the requesting account, and the resulting network activity. This view enables analysts to not only investigate the incident more quickly but also to identify additional exposure paths, allowing for a more proactive defense.
Conclusion
Misconfigured SPNs, particularly those assigned to standard user accounts, are a subtle but highly exploitable vulnerability in AD environments. As demonstrated in this blog, attackers can exploit these flaws after a compromise to carry out Kerberoasting attacks, allowing them to extract and brute-force Kerberos service tickets offline without triggering obvious alerts.
Adversaries can use tools like Impacket's GetUserSPNs.py and hashcat to go from simple SPN enumeration to full credential recovery in minutes. These actions, while silent in logs, leave behavioral traces that can be identified using advanced detection mechanisms.
Trellix NDR is critical in detecting this type of abuse by analyzing deviations in identity behavior, correlating them with MITRE ATT&CK techniques such as T1558.003 (Kerberoasting), and guiding responders through effective remediation steps. When combined with contextual insights from the Trellix Knowledge Graph, defenders gain a comprehensive picture of the threat, from initial reconnaissance to credential exposure.
To learn more about the Trellix NDR solution, take our product tour to see it in action or read more by visiting this page.
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
