Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more

Trellix Global Defenders: Unmasking ViperSoftX: In-Depth Defense Strategies Against AutoIt-Powered Threats
By James Murphy · August 29, 2024
There’s a common misconception that threat actors must always write complicated and custom code in every piece of their malware, skilfully evading defenses, infiltrating networks, and exfiltrating data. While this absolutely does occur, the reality is that even advanced and sophisticated threat actors often struggle with the same issues as regular workplaces - resourcing issues, time constraints, and occasionally even skill shortages - and are always looking for efficient ways to evolve their operations. When an opportunity presents itself to make a threat actor’s life easier, why not take it?
It’s no different for the authors of ViperSoftX, a malware that emerged in 2020. My colleagues Mathanraj and Sijo wrote an excellent blog analyzing the mechanics of the malware and how it leverages AutoIt (a legitimate dual-use tool), the Common Language Runtime (CLR), and existing offensive security scripts to accelerate development while improving their evasion tactics.
In this blog, we unpack how you can build a layered defense against ViperSoftX with Trellix’s broad suite of security tools and explore AutoIt’s use by threat actors to obfuscate activities and evade defenses.
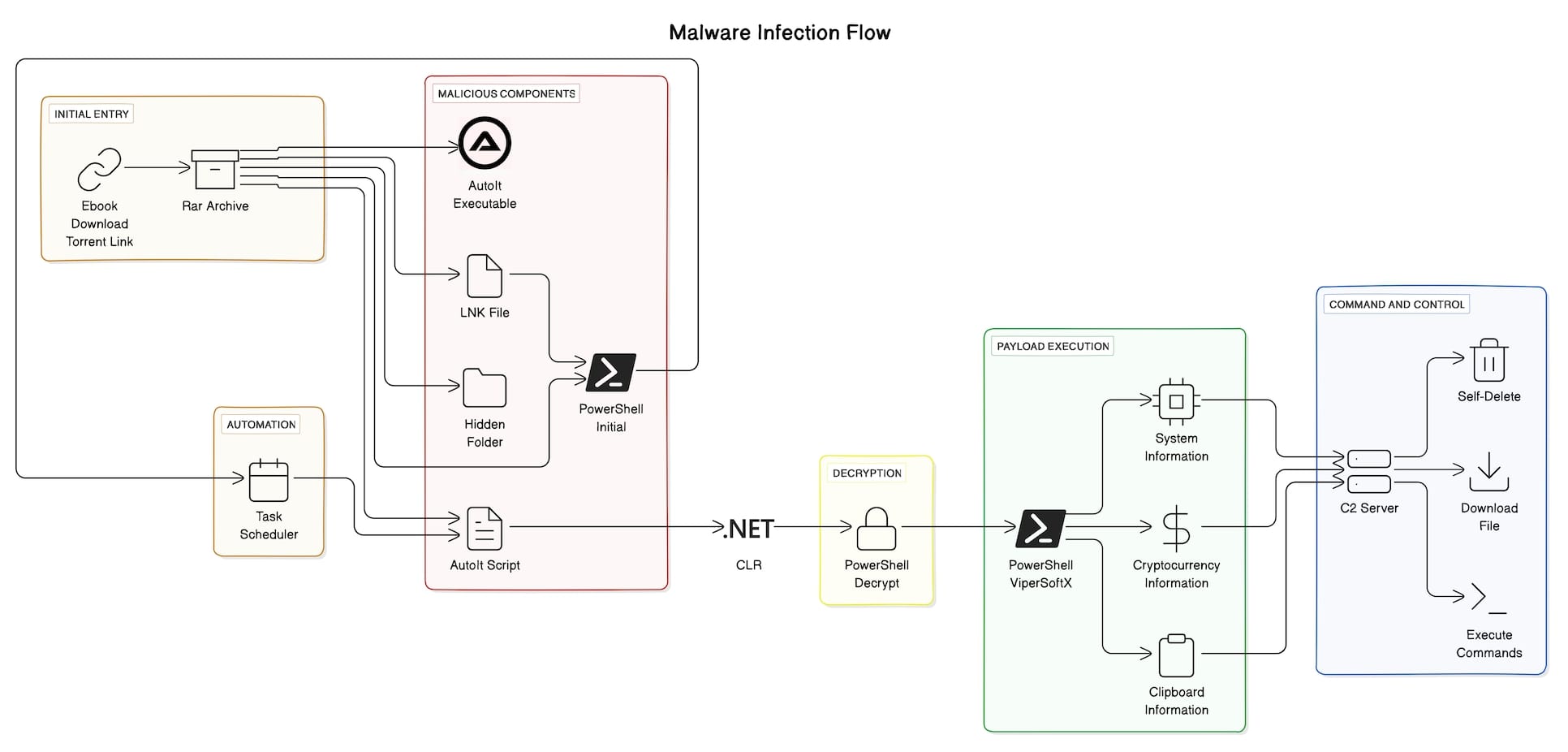
Increased AutoIt usage by threat actors
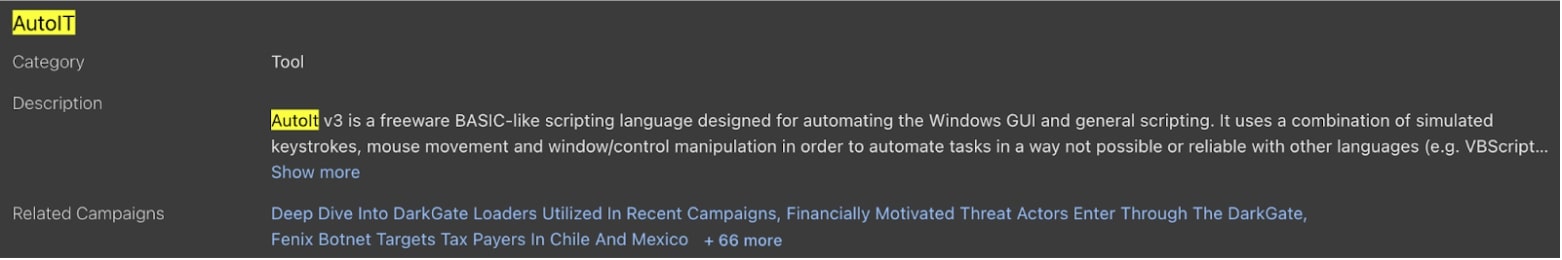
AutoIt is a legitimate freeware scripting tool designed to give scripters a simple and powerful way to automate tasks on Windows operating systems. It leverages a combination of simulated keystrokes, mouse movement, and window/control manipulation to provide automation not possible or reliable with other methods. It’s attractive to system administrators and other IT pros due to its simple syntax and extensive library of functions, and, importantly, the ability to compile scripts into standalone executables.
It’s these same reasons that make it attractive to threat actors, too. Recently Trellix has observed an increase in the use of AutoIt by malware authors to enhance their evasion techniques and reduce the effort required to build and maintain complex code. Other examples include DarkGate, a popular Remote Access Trojan (RAT) that Trellix’s Advanced Research Center wrote about here and here, and even Kimsuky, a North Korean state-sponsored actor, uses AutoIt in their RftRAT and Amadey tools.
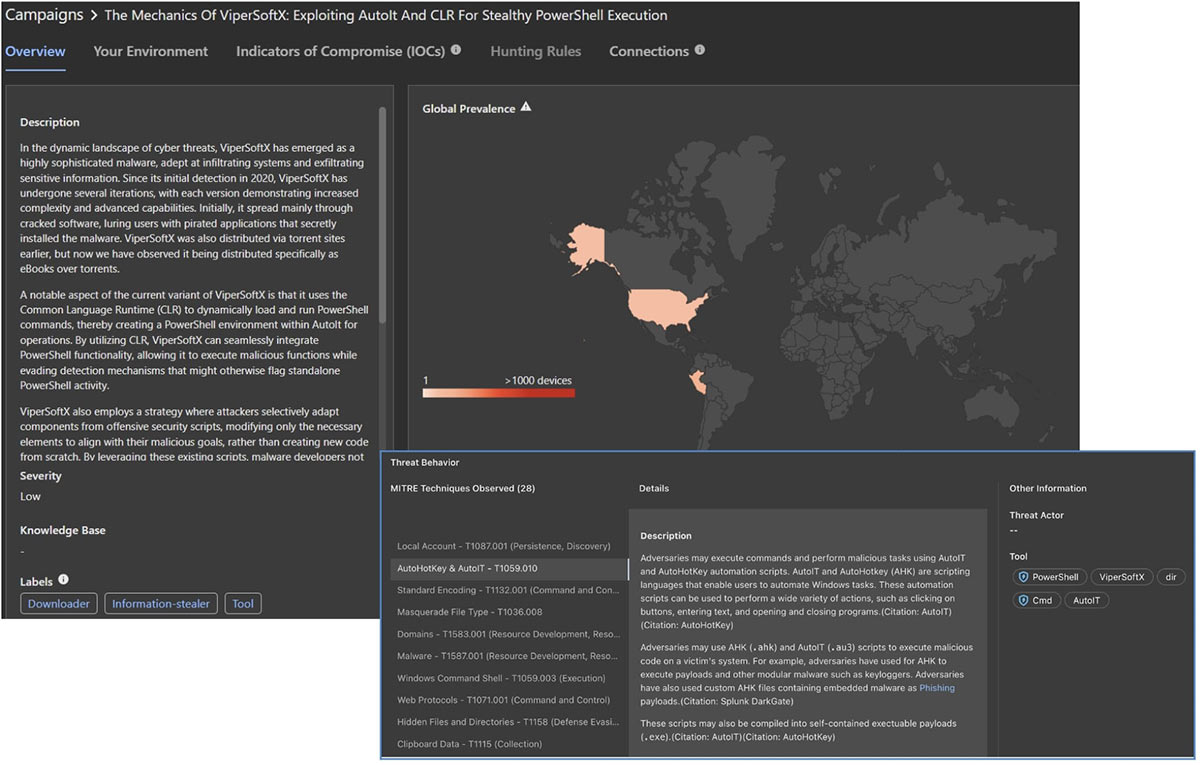
A quick look inside Trellix Insights reveals more context surrounding ViperSoftX, and that AutoIt is a related tool:
In fact, if we look at the AutoIt tool record in Trellix Insights, there are 69 campaigns that are associated with the scripting tool to date, illustrating how popular AutoIt is amongst malware authors:
Three key reasons threat actors favor AutoIt
- 1. Evasion
As in the case of ViperSoftX, attackers can use AutoIt scripts to obfuscate their malicious actions. Initially, this makes it difficult for security teams to identify the specific activity that is occurring within. By leveraging Common Language Runtime inside of the AutoIt script, ViperSoftX is able to orchestrate PowerShell operations within the AutoIt environment to seamlessly execute malicious functions. This integration means the malware’s authors are able to evade detection mechanisms that would typically flag standalone PowerShell activity.
Beyond ViperSoftX, AutoIt also provides the ability to compile custom scripts into standalone executable files. This means it’s even more difficult for defenders to detect this underlying activity, especially if they’re relying on signature-based defenses rather than behavioral-based detection of the malware and the context of the threat within their environment.
- 2. Ease of Use
Not every threat actor has advanced skills or experience in writing each piece of code for their malware. AutoIt provides an intuitive syntax and extensive library of functions for Windows automation, providing accessibility to those with more limited programming skills to achieve the desired outcome. In the same way that AutoIt can provide advanced capabilities for legitimate system admins and programmers, it allows more threat actors to achieve their malicious goals and widens the pool of potential threat actors leveraging malware in this manner.
- 3. Accelerated Development
AutoIt also accelerates the development and maintenance of malware by offering threat actors the ability to streamline the writing and updating of malicious code. Like the developers of ViperSoftX, threat actors can more easily reuse code with AutoIt’s modular structure. Updates to the malware are simplified by AutoIt, allowing attackers to quickly refine their evasion techniques as new security measures are deployed.
What can we do about ViperSoftX?
As we’ve explored, ViperSoftX uses a sophisticated range of tactics to obfuscate code, evade detections, and streamline the malware’s activities on its victims’ systems, making it difficult for cybersecurity teams to detect with traditional measures. In turn, this means a layered and comprehensive defense strategy that encompasses detection, prevention, and response capabilities is required to mitigate the risk posed.
Where do we begin with a strategy to protect key assets and the integrity of our systems? A multi-faceted approach that provides visibility across endpoints, application control, and malware analysis, as well as other vectors such as network and email, is a good place to start. This approach encompasses core areas that we can monitor to gain visibility into malicious activities as they attempt to infiltrate the network. We can then tie these (and many other vectors) together with an enterprise XDR strategy, coupled with threat intelligence, to improve our response times and gain situational awareness and an understanding of trends specific to our organization.
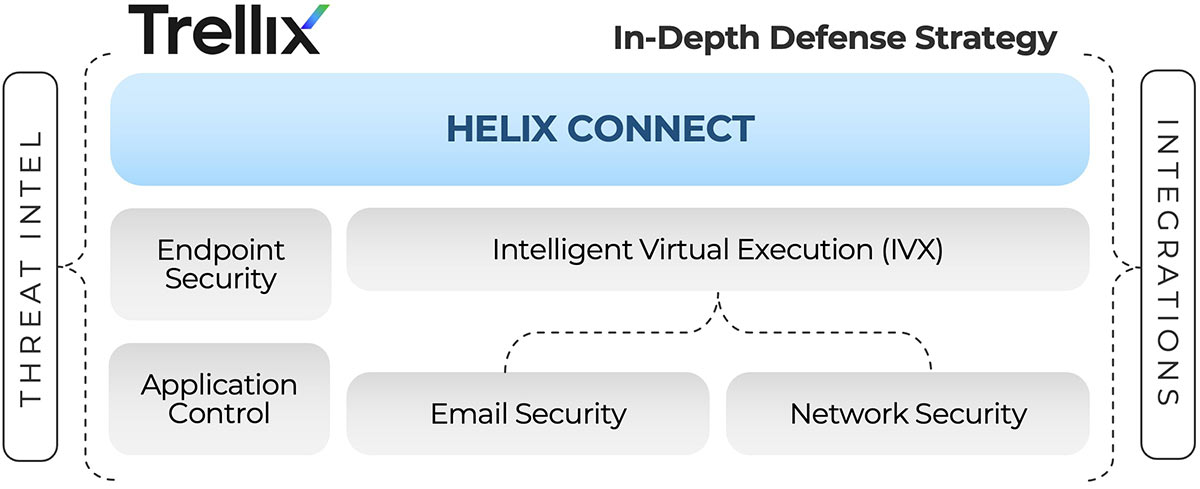
Start at the top: Trellix Helix Connect
Trellix Helix Connect is a powerful XDR platform providing enterprise visibility, detection, and response across all of your threat vectors, including third-party tools, which makes it a great starting point to detect and investigate an instance of ViperSoftX running in our environment.
Helix Connect makes life easier for analysts by automatically correlating alerts and events from multiple detection sources into an overarching threat, with integrated threat intelligence, behavioral analysis, and automated risk scoring. As an analyst, we are immediately presented with prioritized risks in our environment that we need to investigate first, including one generated by the ViperSoftX malware running in our environment.
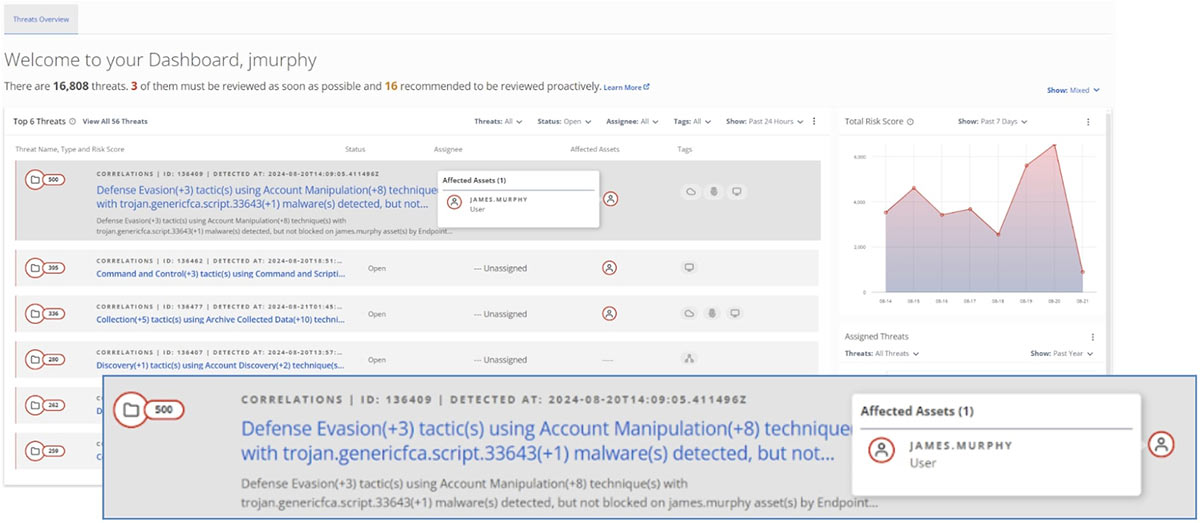
Helix Connect’s analysis engine ties together a number of correlated alerts, events, and related assets (such as my user account, “james.murphy”) to provide analysts with automatic context gathering and intelligence and a starting point to begin investigation and response. An analyst can immediately get a sense of the scope and severity of this threat, rather than having to switch in and out of all the tools in the security stack, manually investigate each alert’s relevance, and put all of the pieces of the puzzle together.
Additionally, MITRE ATT&CK is integrated into the fabric of Helix Connect, allowing analysts to get the big picture across all TTP detections in their environment:
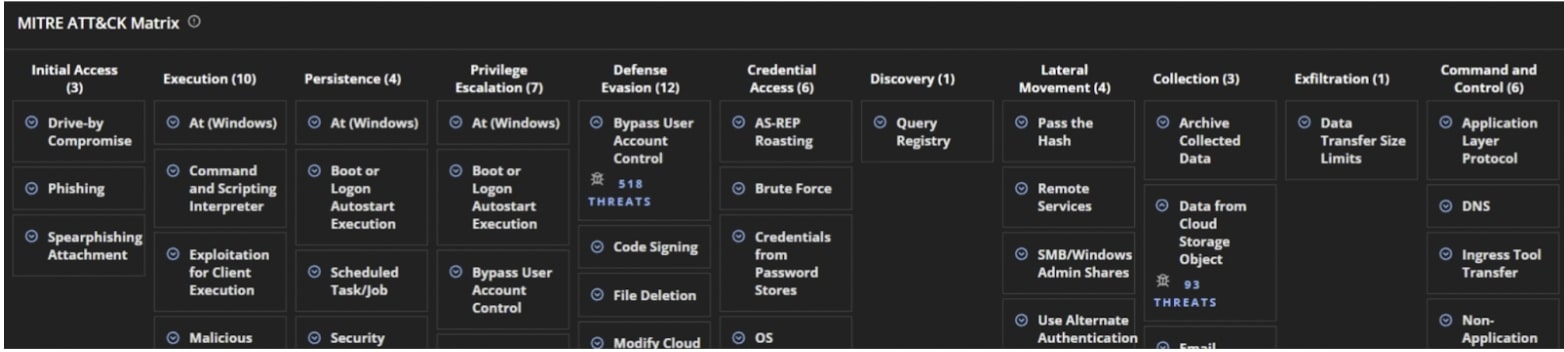
When we dig into the ViperSoftX threat identified by Helix Connect, a mix of Trellix and Windows alerts, along with intel hits from Trellix IVX, appear. The analyst can see exactly which assets were involved, such as the user, hosts, event IDs, and malware analysis outcomes. On the right, we can see how Helix Connect has automatically connected the specific detections within the ViperSoftX threat to the relevant MITRE ATT&CK TTPs.
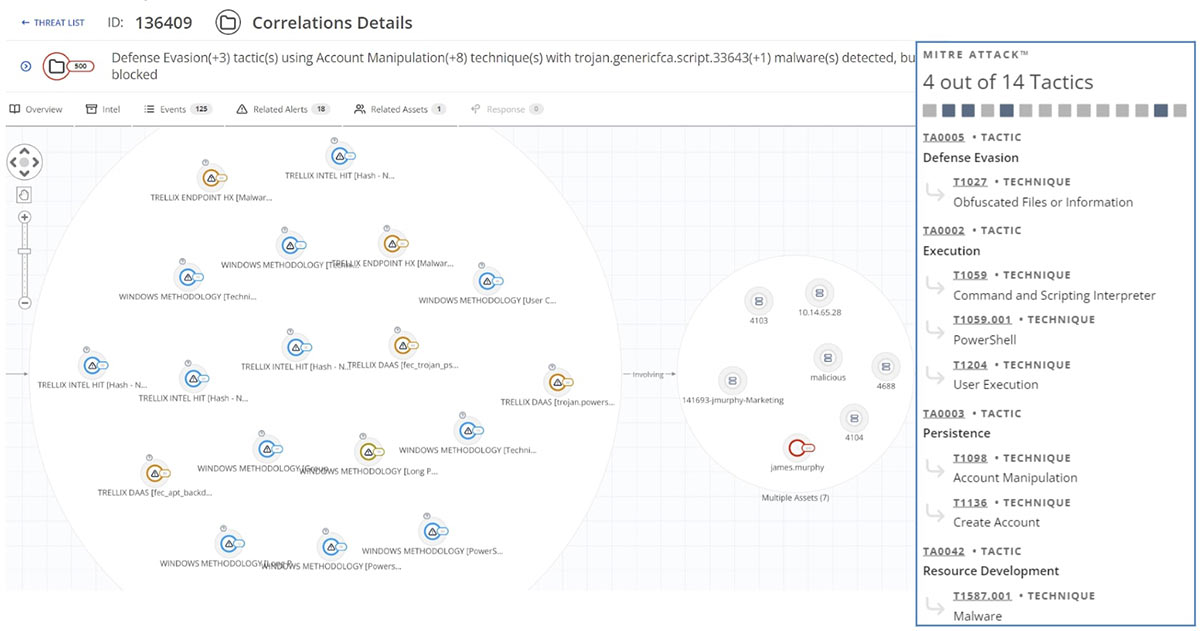
Full artifact information is automatically extracted from a correlated threat, making it simpler for analysts to understand all relevant information, and allows for further forensic analysis across the environment when responding to an incident:
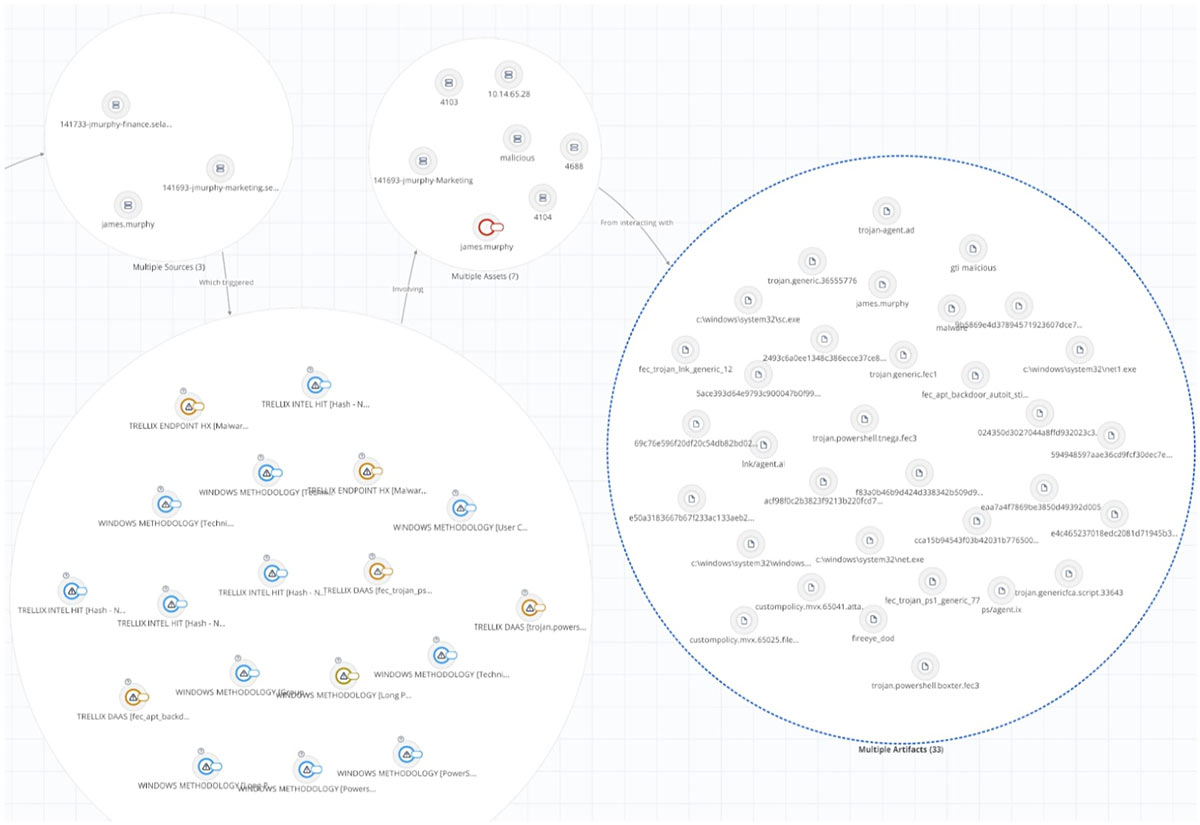
Digging deeper into the specific events, we see the associated Windows events that reveal the presence of the AutoIT scripts triggered by the fake .JPG image files:
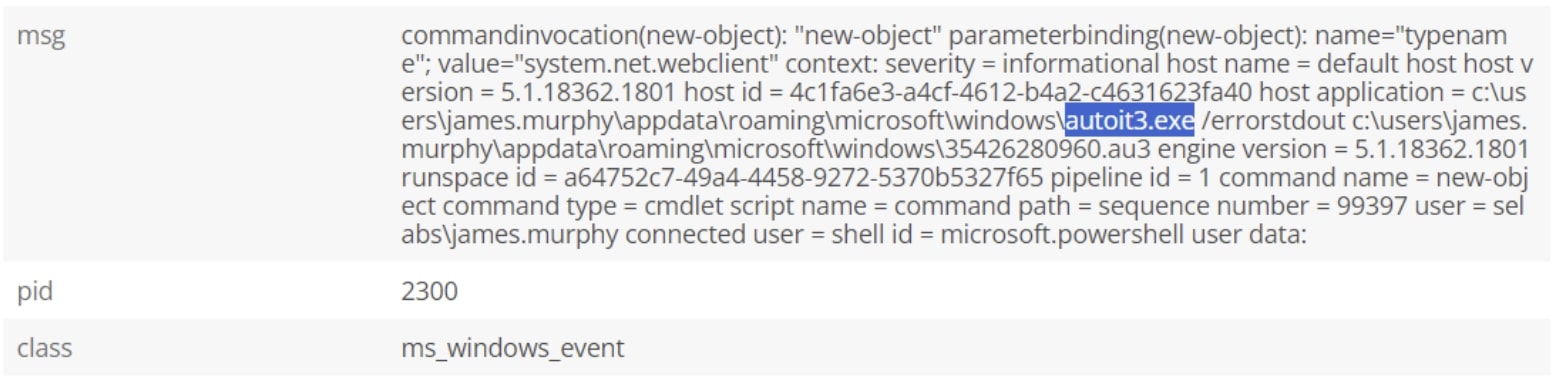
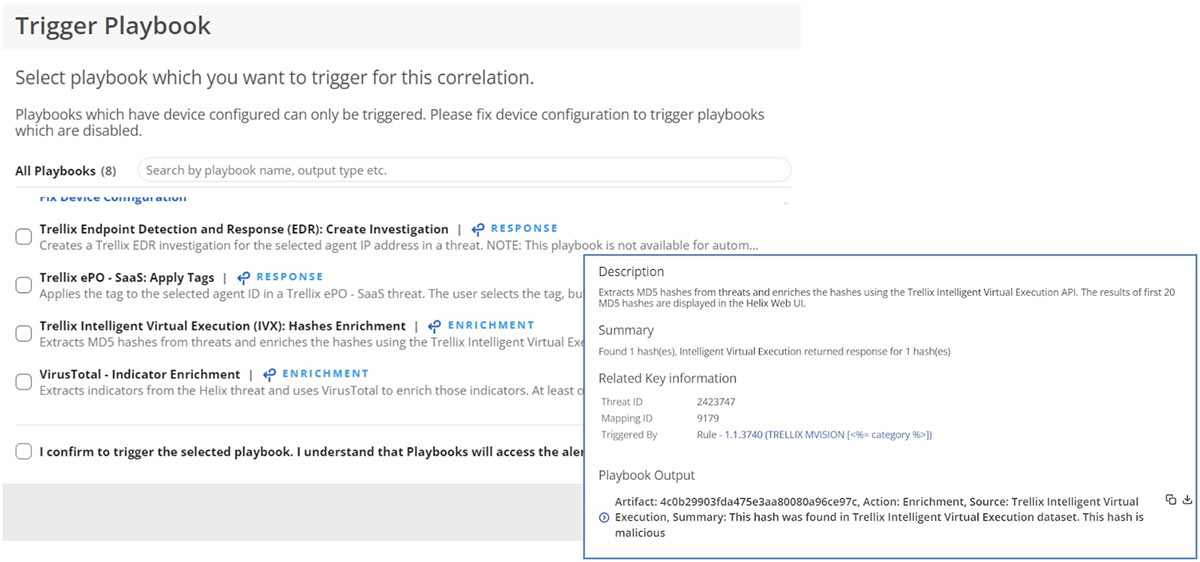
Now that we’ve detected and investigated the threat, we can take action against it by using the Actions feature within Helix Connect. This allows us to choose to contain the endpoint, to cut off any C2 or exfiltration activity and prevent ViperSoftX from spreading, or to run playbooks to automate further information gathering and response tasks.
Examples of actions (but are not limited to!) include sending samples to Trellix IVX, creating an investigation in Trellix EDR, plus third-party use cases like enrichment from VirusTotal, disabling users in Azure or creating cases in ServiceNow. Helix Connect is designed to match your environment’s requirements to simplify and accelerate your incident response.
Robust protection and advanced forensics with Trellix Endpoint Security
Trellix Endpoint provides comprehensive endpoint protection, detection, and response. With ViperSoftX’s goal of running malicious code on endpoints and simultaneously attempting to evade detection, it’s critical to analyze the behaviors of the malware itself rather than only relying on signatures for detection. As ViperSoftX leverages AutoIt to obfuscate the underlying activity, Trellix Endpoint can monitor for suspicious activity on the endpoint and leverage Trellix’s extensive history with machine learning models to analyze behaviors and identify malicious patterns, regardless of the original source.
Trellix EDR against ViperSoftX
Trellix EDR detects multiple TTPs observed in this campaign. Trellix EDR combines process genealogy, command-line and file system events analysis to deliver high confidence indicators against this threat. Please find below a partial list of high confidence Trellix EDR indicators against this threat (along its mapping to ATT&CK):
- Autoit3.exe binary file created or modified by suspicious process. Ingress Tool Transfer, T1105.
- Registered Scheduled Task using COM Objects. Persistence via Scheduled Tasks, T1053.005.
- Suspicious process loaded task scheduler COM library (taskschd.dll). Persistence via Scheduled Tasks, T1053.005.
- Copied a file to a remote location via PowerShell. Lateral Tool Transfer, T1570
- Executed active content by PowerShell. Execution, T1059.001
- Discovered user information using .Net functions in PowerShell. Discovery, T1033
- Unmanaged PowerShell execution (PowerShell automation library loaded). Defense Evasion, T1059.001
- Captured clipboard data via PowerShell. Collection, T1115
These indicators, along with others not included in the list, would be available in the Trellix EDR Monitoring UI as part of High Severity Threats.
Trellix Endpoint Security and Forensics (HX) detects and blocks the ViperSoftX malicious activity and sends this information back to Helix Connect:
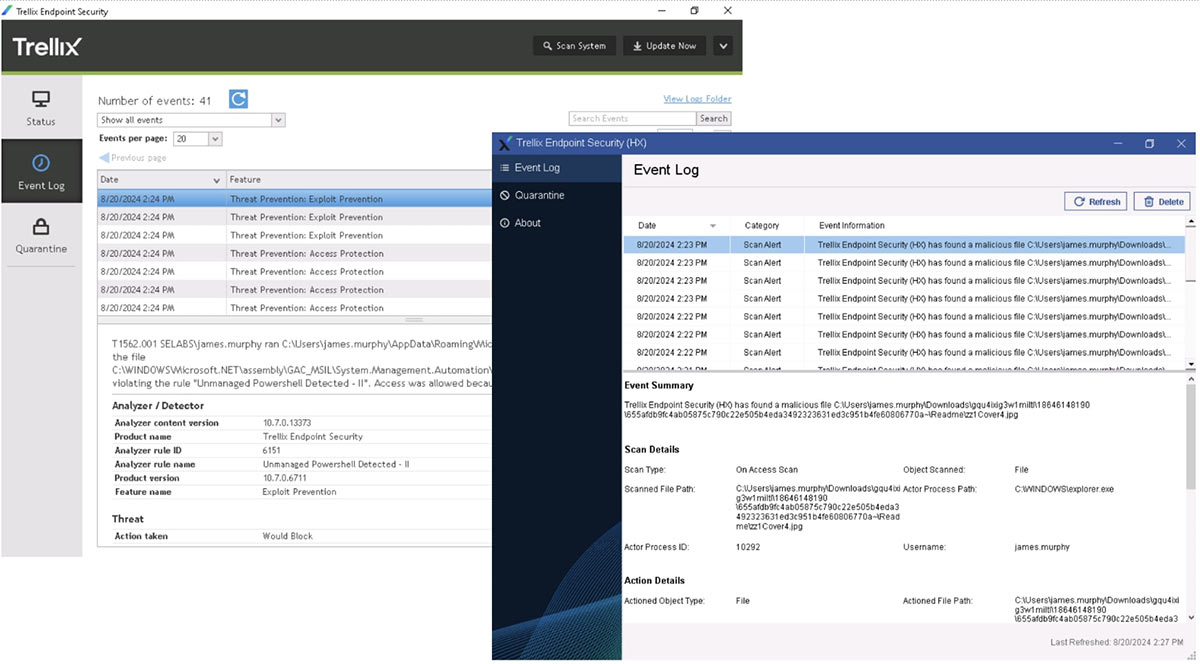
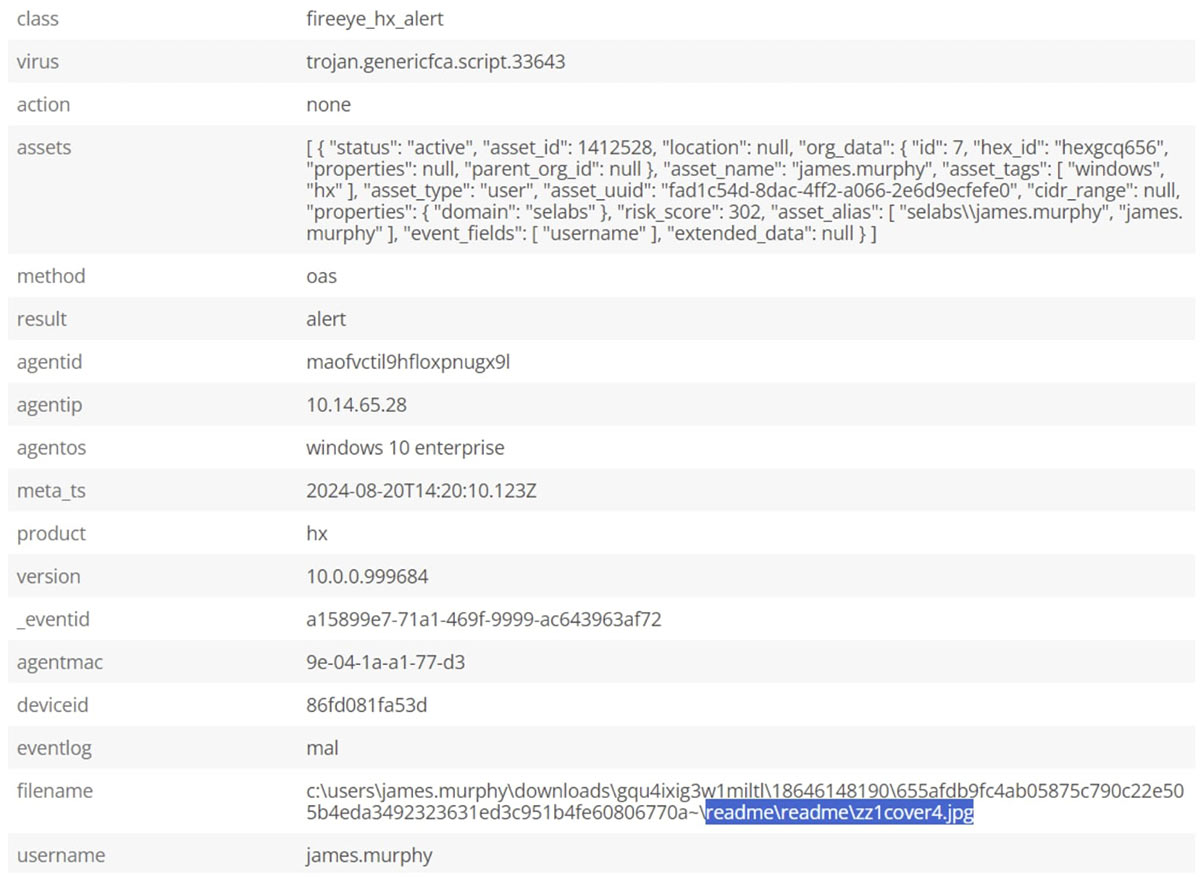
Trellix Forensics (HX) can also collect full forensics information, simplifying the collection process for analysts. Below we can see some information from a HX event sent to Helix Connect surrounding the “zz1cover4.jpg” file, and the full forensics can be accessed using HX and its enterprise search capabilities:
Trellix IVX: Detection efficacy across your entire environment
Trellix IVX is the backbone of Trellix’s malware detection and dynamic analysis capability. Detection is one of Trellix’s core competencies, and IVX provides a thorough sandboxing engine that is well-suited to simulating the behavior of malware like ViperSoftX. IVX is a signature-less, dynamic analysis engine that confirms zero-day attacks and APT attacks as well as known malicious content through the Global Threat Intelligence (GTI) capability.
We can take the sample from the ViperSoftX analysis blog and analyze it with the Trellix IVX engine to uncover key information about how the malware behaves and its effects on the operating system. The use cases for IVX stretch across the entire organization via automation, but here we can manually upload this sample in Cloud IVX and can choose exactly how much detail we want, such as screenshots, dropped files, PCAP - we can even use VNC Connect to have a live, interactive view of the malware being detonated. Additionally, we can submit directly via a URL or search to see if the sample has already been seen by IVX.
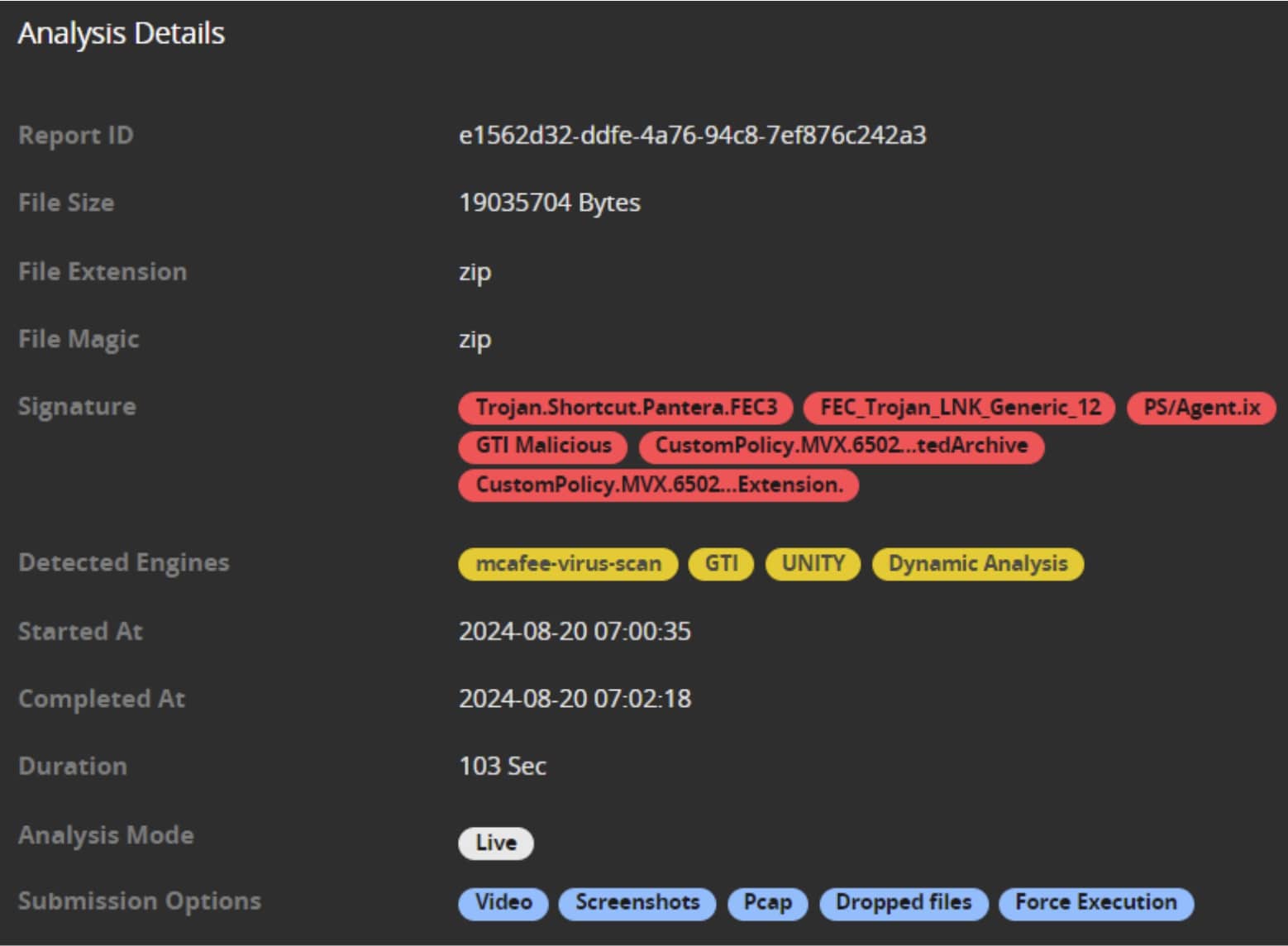
Once the analysis is complete, IVX gives us an overview of the outcome, including its malicious status and the variety of engines used to detect the malware:
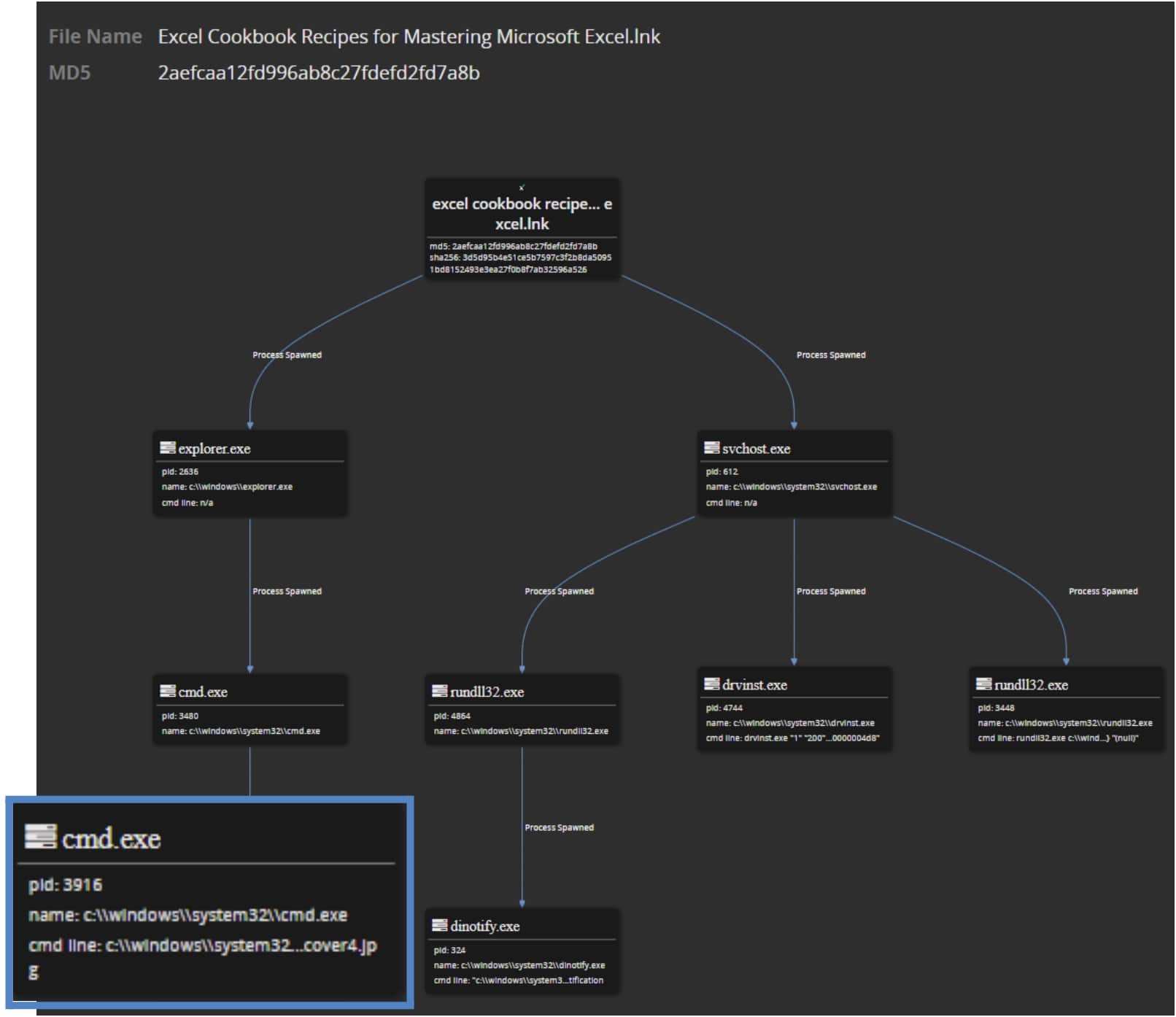
One of the most powerful features of IVX is the ability to simulate OS changes - that is, the actions and behaviors of the malware that would occur if it was allowed to run on a victim endpoint. Visually laying out how the fake ebook carries out its attack allows cyber teams to quickly understand how processes are spawned and the high-level activity involved, and below the simulation reveals the reference to the “zz1Cover4.jpg” file which conceals the PowerShell code.
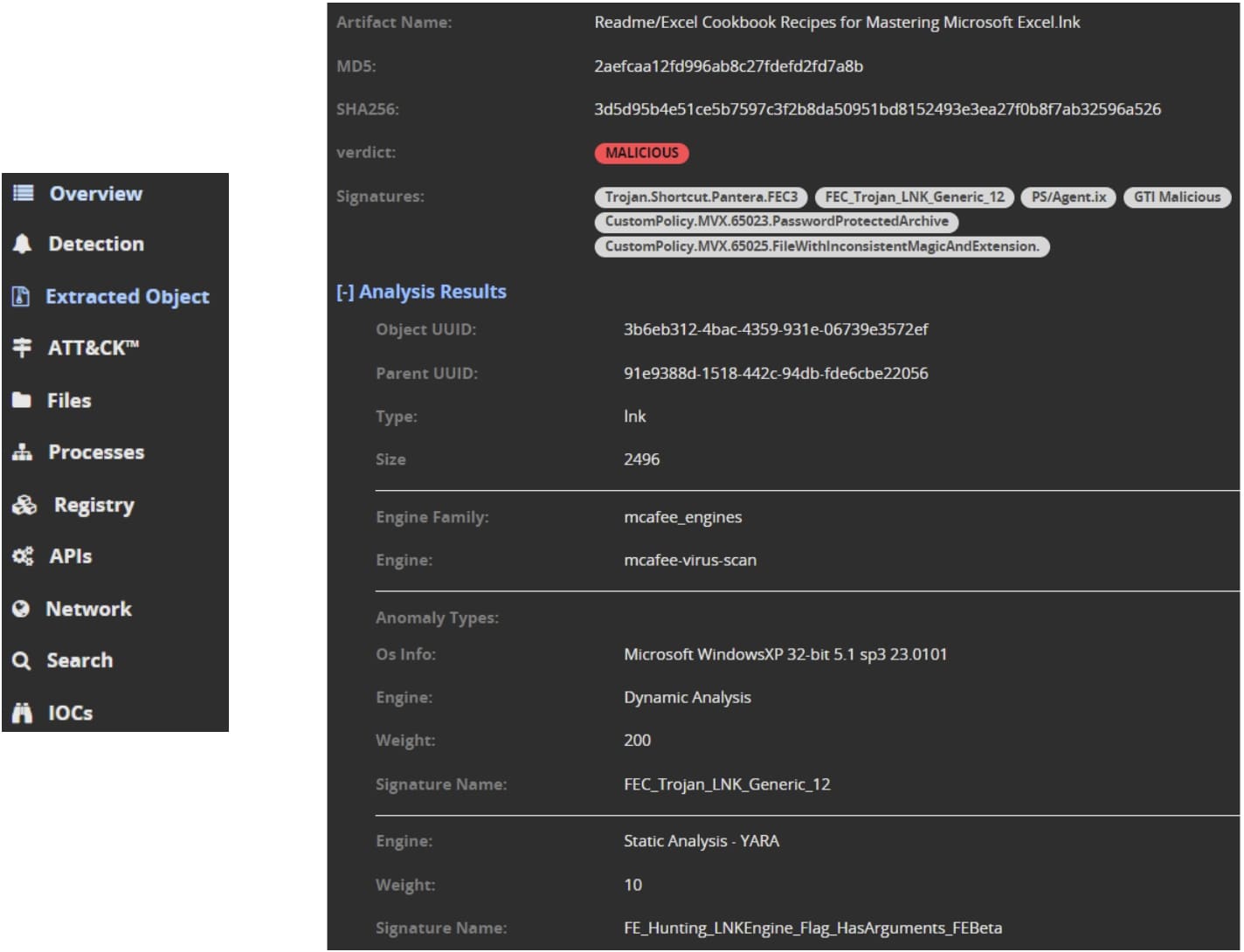
There’s so much more IVX allows us to unpack - more than we can write about in this blog - such as full analysis of each extracted object, MITRE ATT&CK mappings, and all of the artifacts and IOCs. This is critical to understanding the behavior of the malware, and it also provides cyber teams with the key information required to speed up decision-making if this malware has caused a real incident.
And again, Trellix has automatically mapped the analysis and detected behavior to MITRE ATT&CK TTPs:
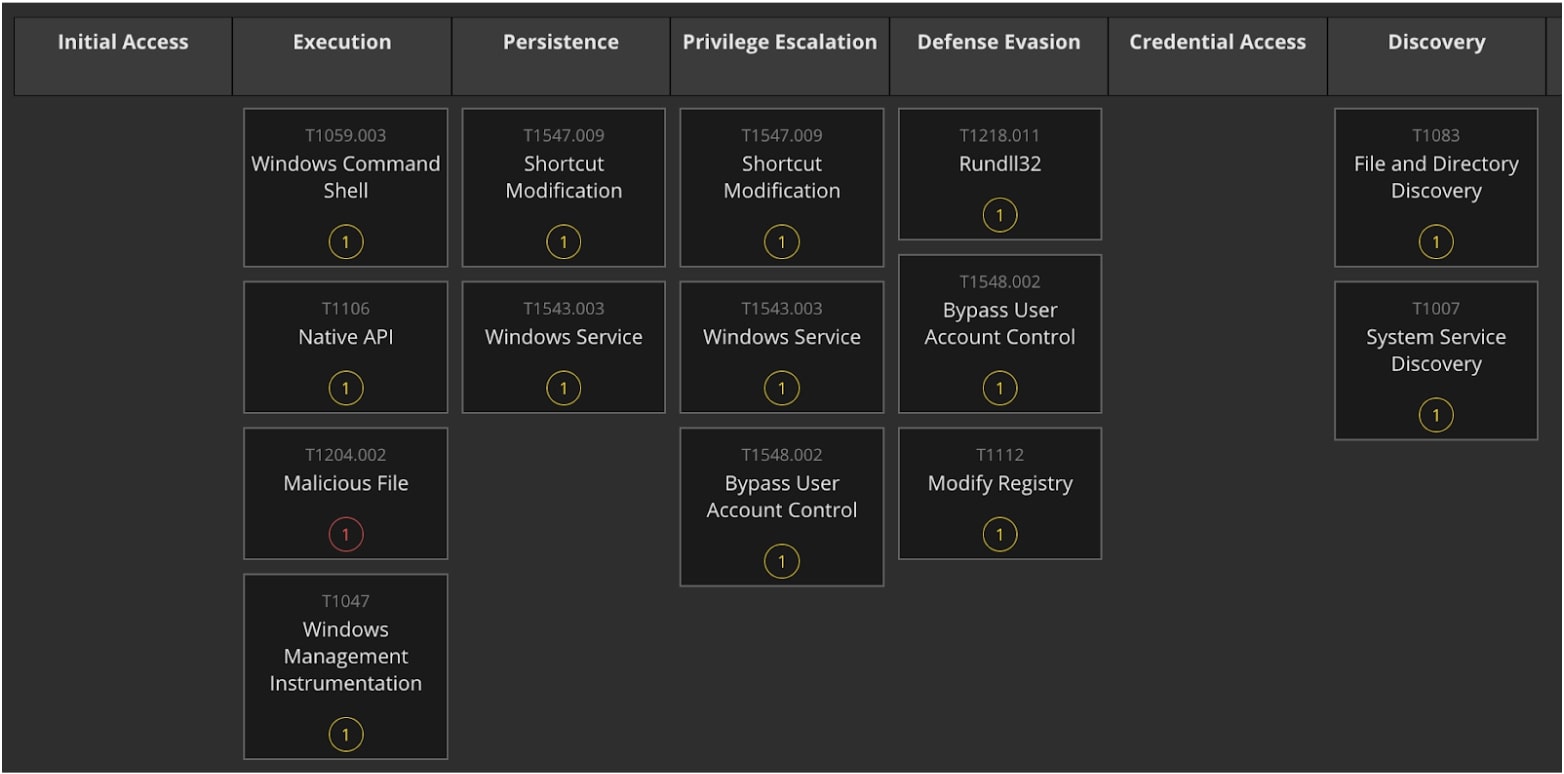
Extending IVX across the enterprise
Trellix IVX is integrated seamlessly into Trellix Email Security and Trellix Network Security and also provides an API for easy integration into your security operations workflows.
Trellix Email Security so often acts as the first line of defense for organizations detecting and preventing malware from infiltrating their networks. While ViperSoftX has evolved its distribution methods, such as via torrents and ebooks, it’s a common tactic for malware to be deployed via phishing campaigns. Trellix Network Security also leverages the IVX engine, providing detection and response on the malware as it traverses through network points, with additional detection of advanced threats at the network layer, both in north-south traffic and east-west, picking up malicious lateral movements.
Stopping AutoIt in its tracks with Trellix Application Control
As we’ve discussed, AutoIt is a legitimate tool that can be misappropriated by malicious actors, and ViperSoftX isn’t the only piece of malware that takes advantage of its toolset. If our organization doesn’t use AutoIt across the environment or in development workflows, then it’s safe to assume any unexpected AutoIt process is unwanted, and we can block it. If our organization is utilizing AutoIt in a legitimate way, then we can still track it and control its usage with Trellix Application Control.
Trellix Application Control provides robust protection by leveraging a dynamic whitelist model, which categorizes applications as trusted, malicious, or unknown. This approach means that instead of manually managing lists of approved applications, inventories of installed software are collected in a streamlined manner and provide a comprehensive view of what’s running across your environment.
This drastically reduces the workload for security administrators by simplifying the process of maintaining enterprise application control. It also means that an untrusted executable like AutoIt.exe (or any other variations of the AutoIt executable) will not run in your environment unless you approve its use. Integrations with Trellix Threat Intelligence Exchange and Trellix Global Threat Intelligence enable real-time reputation tracking, providing assistance to security administrators in asserting the trust level of an executable based on up-to-date intelligence.
Situational awareness with Trellix Threat Intelligence
Trellix’s Threat Intelligence offering gives organizations additional situational awareness of the threats encountering the organization from a strategic high level, all the way down to the operational and tactical levels. Trellix products integrate with Trellix Global Threat Intelligence (GTI) to understand the latest in analysis and reputation information from the Trellix Advanced Research Center (ARC), providing rapid identification of already known threats and attribution for APT attacks, as well as context for zero-day attacks identified by IVX.
Trellix Insights can also help you research specific threat actors, campaigns, malware, tools, and TTPs. With over 4000 campaigns tracked and counting, Trellix Insights serves as a central hub for threat intelligence and provides your security team with analysis, research, threat hunt rules, defensive countermeasures, IOCs, and more, providing quick wins when operationalizing threat intelligence in your environment.
Using Trellix Insights already?
Search for ViperSoftX or AutoIT to see all related threat campaigns, as well as the specific IOCs related to this campaign and tool. IOCs can be exported directly from the portal, along with the ability to view MITRE ATT&CK TTPs, tool information, and global prevalence activity specific to countries and industries. Plus, if you’re using Trellix Endpoint (ENS/EDR), you’ll even be able to see any detections of ViperSoftX that exist within your environment directly from Trellix Insights.
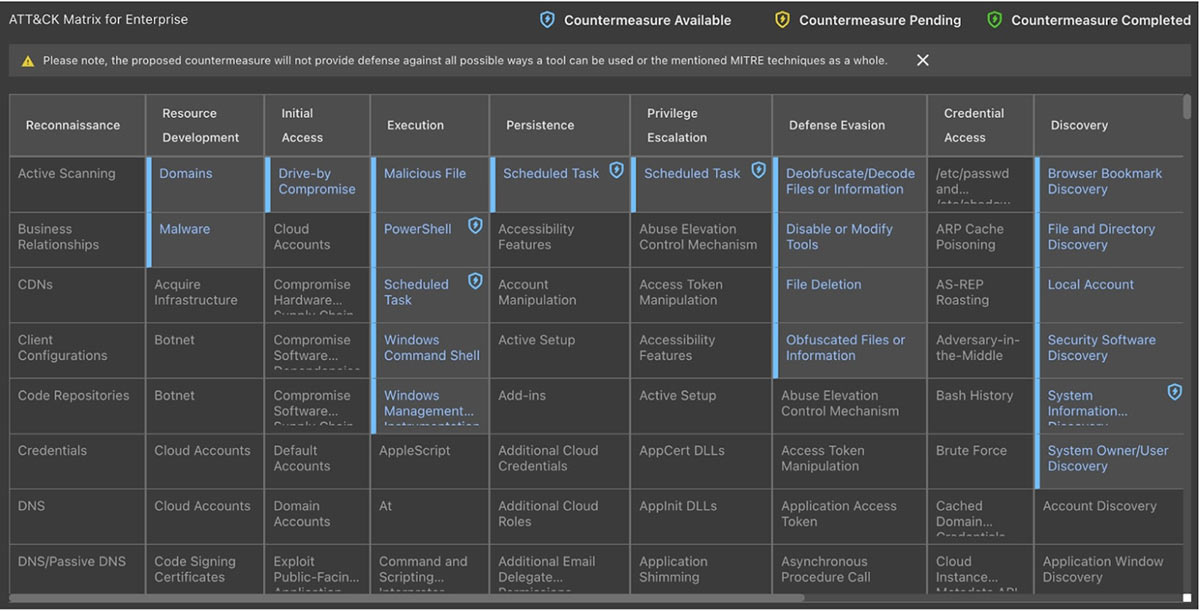
MITRE ATT&CK is natively integrated, allowing analysts to easily understand the characteristics of ViperSoftX:
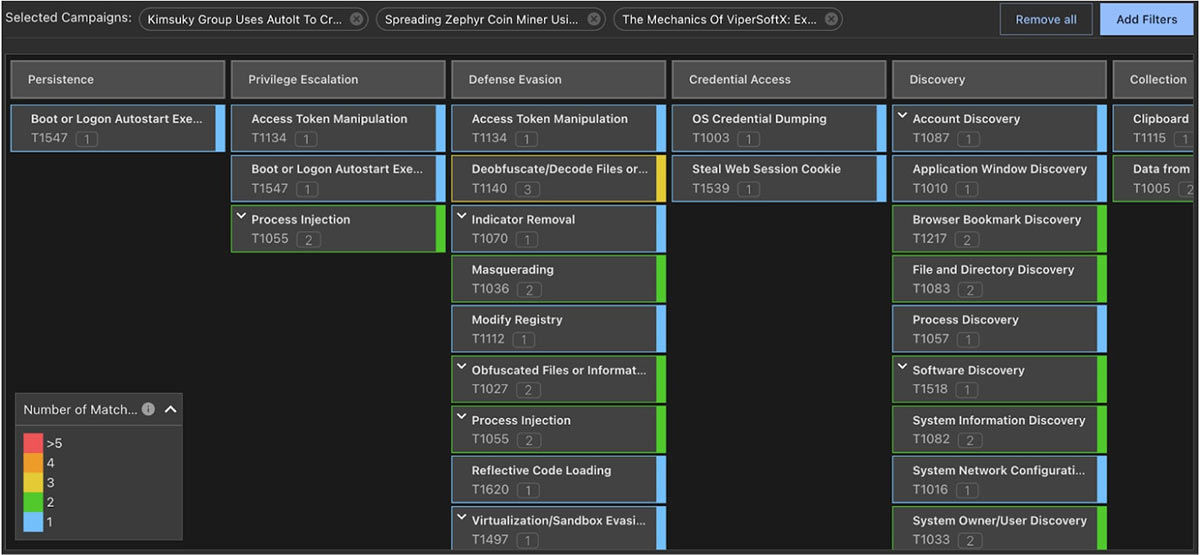
MITRE ATT&CK is tightly woven throughout Trellix Insights, with an included MITRE Explorer providing the ability to build a broader picture of TTPs associated with any campaigns of interest:
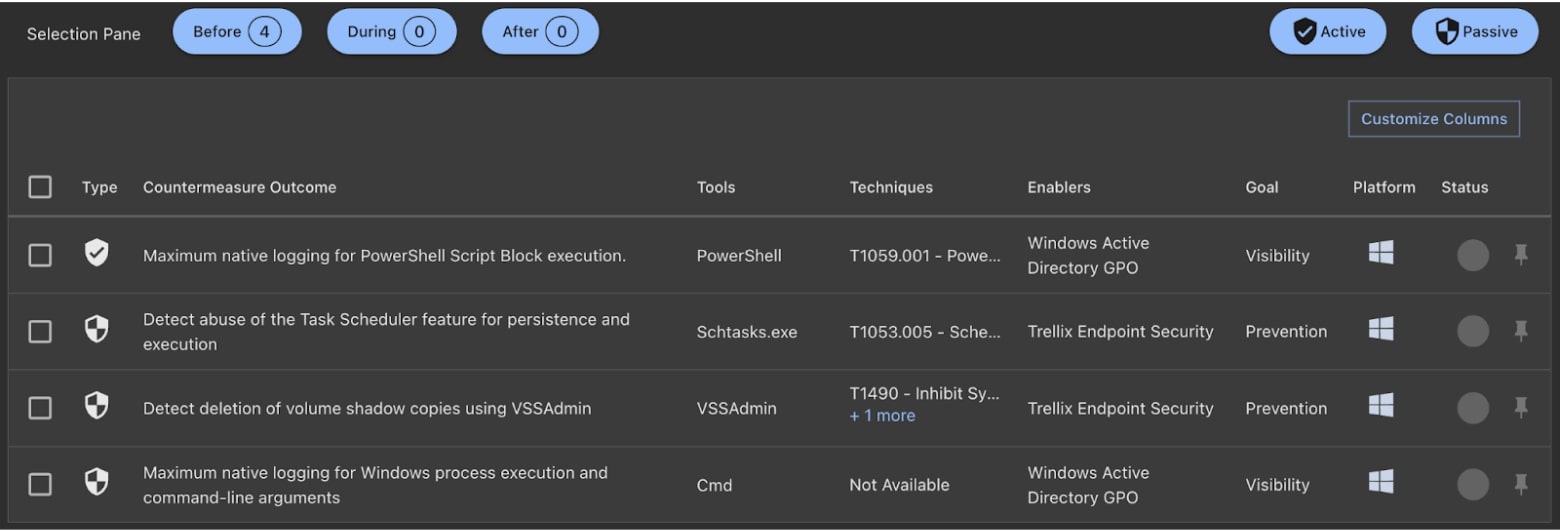
Countermeasures are provided for ViperSoftX, allowing analysts to easily track their implementation progress:
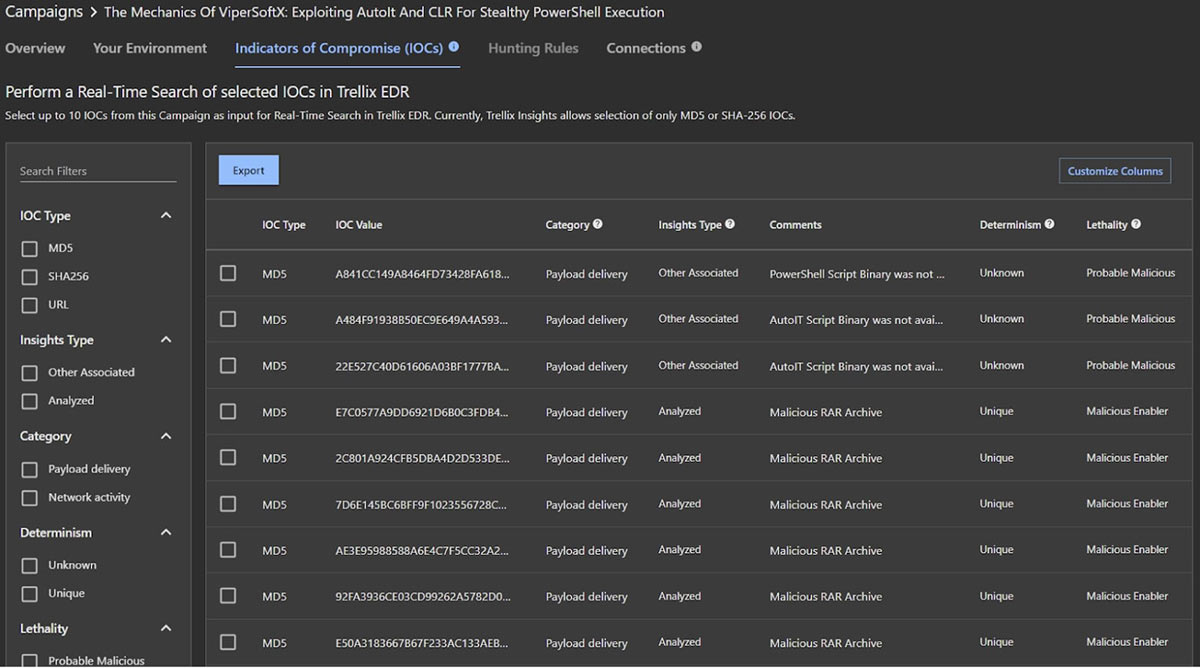
IOCs related to ViperSoftX are provided for analysts, with additional API integration available:
Conclusion: Tackling ViperSoftX head-on with Trellix
The case of ViperSoftX is yet another example of malware authors streamlining and simplifying their development processes in order to stay ahead of cyber defenses and consistently evade detection. It highlights the resourcefulness of threat actors in achieving their goals, even as they navigate the same challenges that genuine IT, cybersecurity, and development teams face, such as skill shortages and time constraints. The ability to repurpose legitimate tools like AutoIt not only resolves those issues for threat actors but also extends their capabilities with the creative use of the Common Language Runtime (CLR) to obfuscate the underlying PowerShell activity.
Malicious creativity like this requires defensive innovation in return, with cybersecurity teams deploying a modern, layered defense strategy to detect and respond across every threat vector. Trellix meets the challenge posed by ViperSoftX through an extensive portfolio of detection and response capabilities, spanning Trellix Endpoint, IVX, Application Control, Email Security, and Network Security. Trellix Helix Connect ties these solutions together, alongside seamless integration with Trellix Threat Intelligence and third-party tools to provide holistic detection, investigation and response for the whole enterprise.
The Trellix Advanced Research Center (ARC) plays a pivotal role in allowing cybersecurity teams to stay ahead of adversaries and their evolving tactics, techniques and procedures. By continuously uncovering new threats and understanding actor behaviour, this research directly enhances the detection efficacy that Trellix prides itself on.
Want to explore how Trellix products can help you? Request a demo now, or if you just want to see the products for yourself, take a tour!
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
