ARCHIVED STORY
Protecting Against HAFNIUM With FireEye Endpoint Security Process Guard Module
By Ryan Delany · March 11, 2021
In March 2021, Microsoft announced an active global campaign named HAFNIUM targeting Microsoft Exchange servers with a chain of four zero-day vulnerabilities. According to Microsoft, a threat group or groups was able to exploit these vulnerabilities, which allowed them to gain initial access to targeted machines and deploy web shells. Once the web shells were established, operators used credential dumping techniques to gather credentials and exfiltrate information that can be used for further privilege escalation and lateral movement within targeted organizations.
For more information about this ongoing campaign, please see our detailed analysis blog post.
Credential Dumping
Credential dumping (MITRE ATT&CK® technique: T1003.001) is a method of collecting user credentials stored in memory and is a popular technique used by many state sponsored APT and financially motivated (FIN) groups today. Once threat actors obtain these credentials, they can be used to facilitate lateral movement and privilege escalation within a compromised network.
Process Guard for FireEye Endpoint Security
Process Guard for FireEye Endpoint Security can help prevent the critical step of credential dumping and deter any forward progress operators hope to make. By preventing the dumping and exfiltration of credentials, even unpatched and compromised organizations would have a level of protection against this type of attack. This video shows Process Guard in action.
Process Guard for FireEye Endpoint Security prevents attackers from obtaining access to credential data or key material stored within the Windows Local Security Authority Subsystem Service (LSASS) process, thus helping to protect endpoints against common credential theft attacks. Process Guard is a lightweight, efficient module that can be deployed to individual hosts, host sets, or all hosts in an environment directly from the FireEye Endpoint Security console.
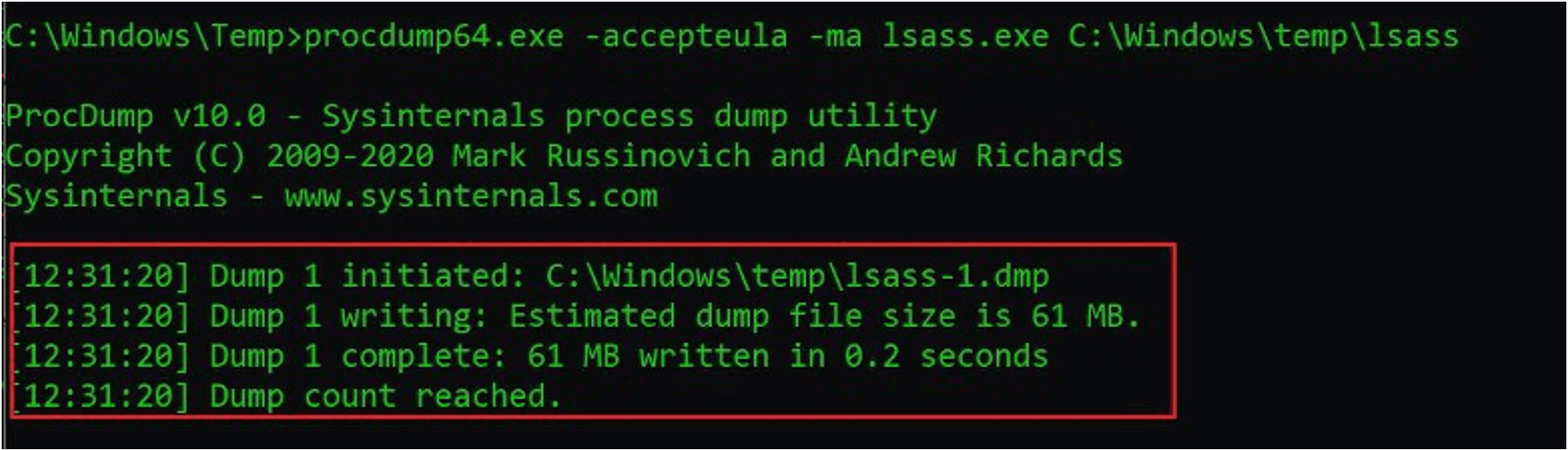
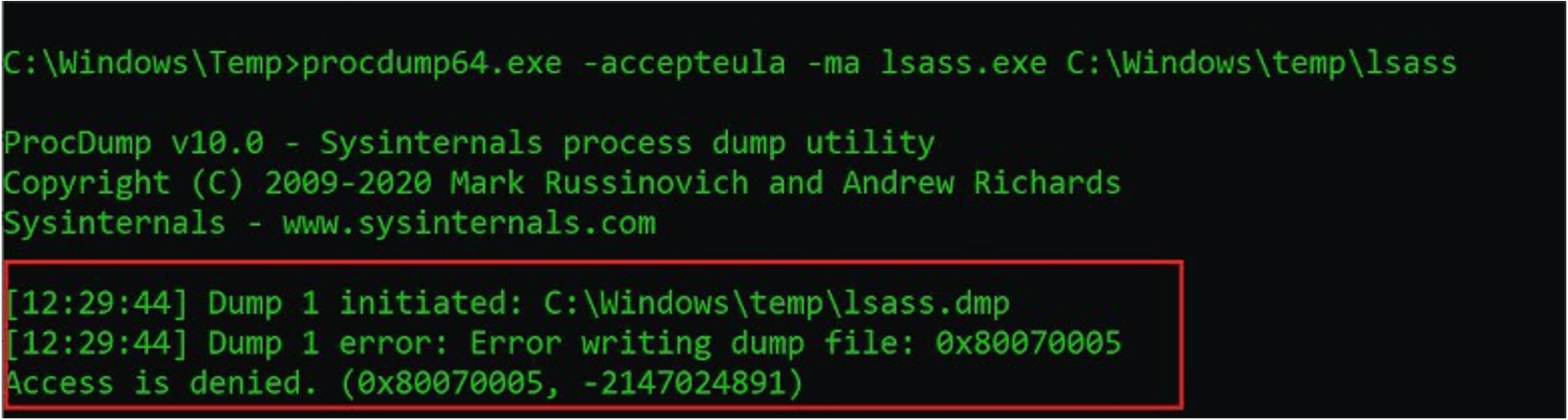
The Process Guard module for FireEye Endpoint Security is an Innovation Architecture (IA) module developed based on FireEye’s extensive front-line experience investigating and responding to the largest, most sophisticated breaches around the world. Our unique modular approach allows customers to rapidly deploy innovative components to address ever changing tactics, techniques, and procedures (TTPs) used by today’s threat actors. Figure 2 shows Process Guard successfully preventing a credential dumping attempt using the procdump tool.
The Process Guard module provides the ability to:
- Enable/Disable LSASS process protection
- Enable/Disable BLOCK on detection capability
- Add Exclusions for allowed applications
- View Process Guard events
- Integrate with the Enricher module
- Generate Alerts
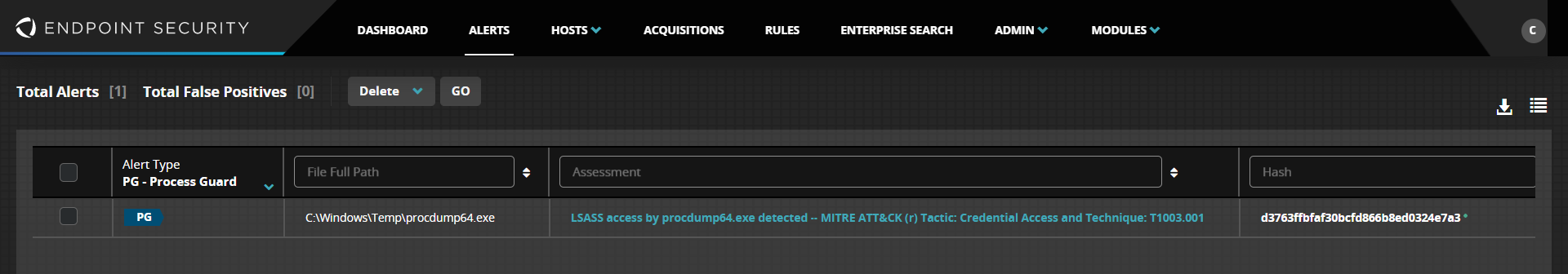
Alerts from Process Guard will show up on the Alerts page on the Endpoint Security console with an Alert Type of PG, as shown in Figure 3. Clicking on an individual alert will bring you to the Hosts page to reveal specific details of the alert.
The Process Guard module provides the ability to:
Summary
Credential dumping is a widely used technique by threat actors today and was even used as part of the recent global attack on unpatched Microsoft Exchange Servers. Deploying and enabling Process Guard for FireEye Endpoint Security can help strengthen your security posture and reduce the attack surface in your organization.
Existing FireEye Endpoint Security customers have access to the Process Guard module at no additional charge and can download and deploy it today from the FireEye Market. Modules, release notes, and user guides are all available now.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.