ARCHIVED STORY
Real-Time Threat Protection With Enhanced Traffic Visibility
By Christopher Unick · July 15, 2019
New and expanding cyber attacks target a range of valuable assets from sensitive personal information and intellectual property, to authentication credentials and insider information. These multi-stage attacks breach systems, spread laterally through networks, call back to attackers, and extract high-value data.
Firewalls and intrusion prevention systems cannot stop these attacks, as advanced persistent threats (APTs) easily evade common security approaches. Multi-stage attacks that move laterally through the data center require a pervasive, flexible and scalable architecture. In trying to deal with these advanced attacks, data center security managers often have multiple security products that work in isolation from one another, with limited deployment flexibility. Achieving integration among deployed security products poses a significant challenge.
An ideal solution needs comprehensive visibility across network traffic with the ability to go from alert to fix in minutes and scale service up or down as threats and needs evolve. The right solution should be deployed as needed. With increased vigilance and early detection, security teams can reduce breach impacts, which include costly fixes, disrupted business, stolen information and damaged reputations.
The Integrated Solution
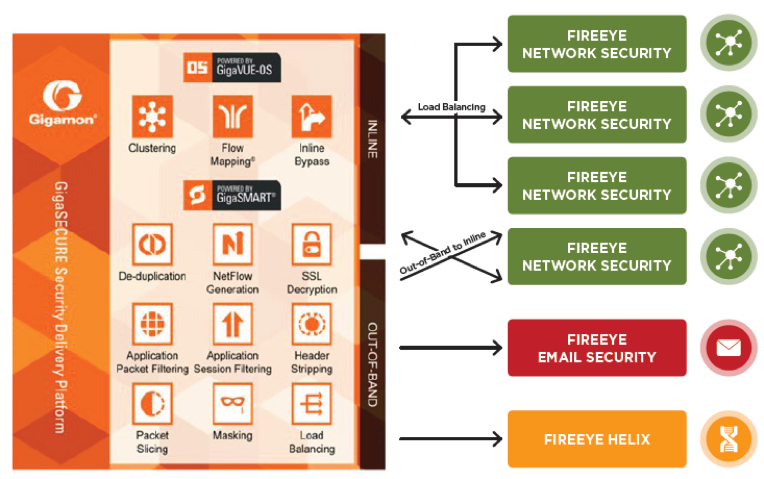
FireEye Network Security and Forensics combined with the Gigamon GigaSECURE Security Delivery Platform offers customers flexible deployment options and scalability (up to 100 GB of traffic) for optimal threat protection. With network-side visibility and options for both inline and out-of-band deployments, APTs can be contained quickly and efficiently.
The combination of the FireEye platform and the Gigamon Visibility Fabric™ architecture ensures that traffic is efficiently analyzed and threats are detected in real time, allowing administrators to quarantine or delete harmful data before it gets inside the network.
How FireEye and Gigamon Solutions Work Together
The joint solution supports two models of deployment for flexibility and adaptability:
- Out-of-band deployment
- Inline deployment
Added Value
- Lower total cost of ownership: Ensures optimal performance and longevity of devices through load balancing across multiple FireEye devices, link consolidation, and filtering.
- Reduced noise: Filters out traffic that doesn’t need inspection and provides greater efficiency from your FireEye appliances.
- Avoided SPAN port contention: Replicates a feed from the SPAN port or a tap to multiple tools while also filtering feeds to just relevant traffic for that tool.
To learn more about the benefits of this joint solution, check out this in-depth solution brief.
RECENT NEWS
-
Jun 27, 2024
Trellix Named an XDR Market Leader
-
Jun 11, 2024
Trellix Uncovers Spike in Cyber Activity from China and Russia
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
RECENT STORIES
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.