Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
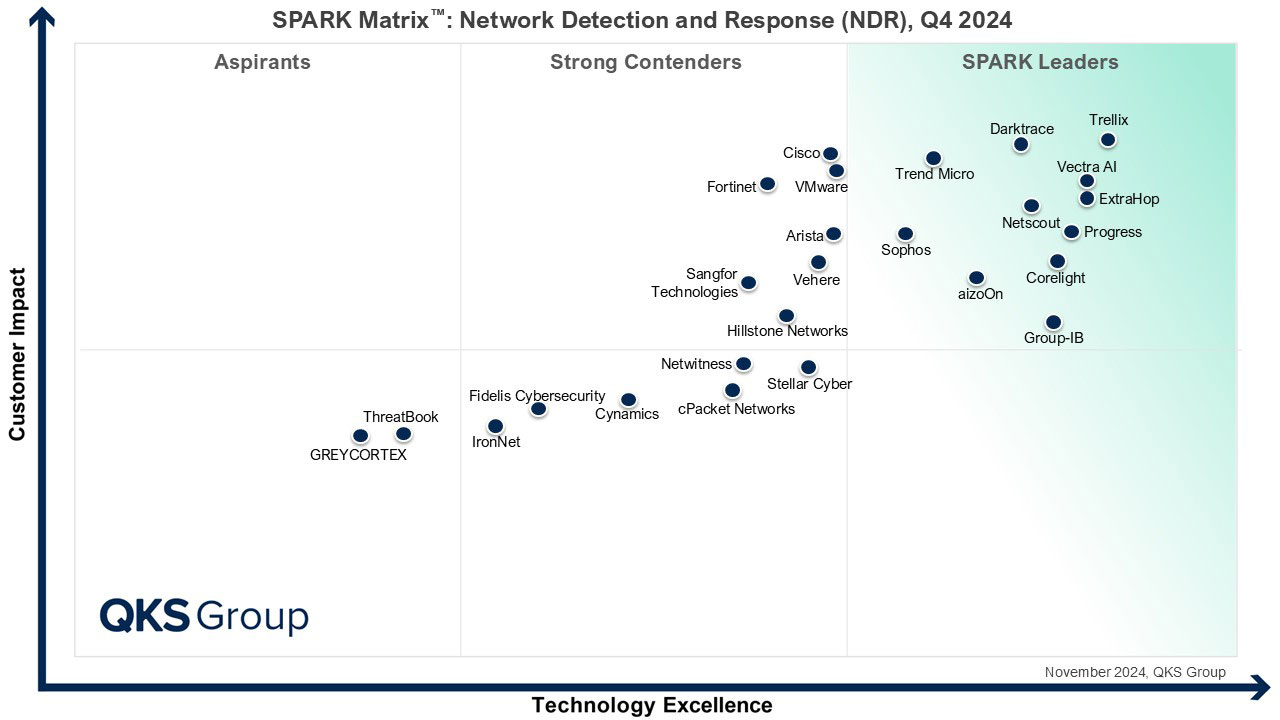
Trellix Named a Leader in Network Detection and Response
By Rohit Unnikrishnan · November 21, 2024
Trellix has been recognized by QKS Group as a Leader in the 2024 SPARK Matrix™ for Network Detection and Response (NDR). This prestigious recognition highlights our commitment to providing advanced threat detection and response capabilities that help organizations defend against today's most sophisticated cyber threats. Based on technology excellence, vision, and customer impact, Trellix is positioned among the top providers in this critical cybersecurity segment.
The Power of Multi-Layered Detection
Our innovative multi-layered detection approach is at the heart of Trellix NDR's leadership position. By combining network sandbox capabilities, signature and signature-less detection, and advanced behavioral analytics powered by machine learning and AI, we provide comprehensive threat coverage across both north-south and east-west traffic.
The integration of these detection layers includes signature-based analysis for known threats, sandbox analysis of over 160 file types for zero-day threats, and advanced analytics with over 180 specialized rules for lateral movement detection. Our advanced behavioral analysis, powered by machine learning, identifies subtle deviations from normal network behavior, while deep packet inspection across 2,000+ applications and protocols ensures comprehensive visibility.
This sophisticated approach, enhanced by our vast threat intelligence network processing 1.5 PB of threat data daily, enables security teams to identify and respond to threats at every stage of the attack lifecycle - from initial reconnaissance to data exfiltration attempts.
Advanced Visibility across On-prem & Cloud Network Infrastructure
In addition to multi-layered detection Trellix NDR was recognized as a leader for our proactive approach to network security through comprehensive visibility and risk assessment. Our attack path discovery capabilities enable organizations to identify high-risk network paths across their infrastructure before attackers can exploit them. This insight allows security teams to implement preventive measures through inline mitigations using NDR sensors or virtual patching via our NDR-ready IPS stack. The integration with Cloud Security Posture Management (CSPM) solutions like Wiz further extends this visibility into cloud environments, providing a unified view of potential attack vectors across hybrid infrastructures, while being able to respond inline to threats as well as virtually patch any vulnerabilities including newly discovered 0-days.
The platform's integration with Trellix EDR also demonstrates our vision and technology excellence for unified security operations. Security analysts can view correlated endpoint and network data in a single, consolidated interface. This includes detailed process information, endpoint events, and synchronized detection data across both network and endpoint vectors. This is further enhanced using our unique Attack Path Discovery (APD) functionality which now enables users to take a proactive approach, as opposed to a purely reactive approach. APD proactively identifies the most likely paths that would be taken by a threat actor within the environment to get to the crown jewels. This view allows for proactive patching and mitigation steps to avoid the identified scenarios. By providing this holistic view within a single console, we significantly reduce the time and effort required for investigation and response, enabling security teams to focus on addressing threats rather than switching between multiple tools.
Integrated Response Workflows
Trellix NDR's integrated response capabilities provide security teams with flexible and powerful options for threat mitigation. Through our multi-tiered approach to threat response, organizations can implement immediate inline blocking using NDR sensors while leveraging our NDR-ready IPS stack for both on-premises and cloud environments. This comprehensive coverage ensures that threats can be contained and mitigated regardless of where they appear in the network infrastructure.
One of our platform's most powerful features is its ability to bridge the gap between network visibility and endpoint protection. When NDR's passive discovery identifies unmanaged assets on the network, our integration with Trellix ePO and EDR enables automated deployment of endpoint agents to these systems. This seamless workflow transforms visibility into action, ensuring that newly discovered assets can be quickly brought under management and protected with our full suite of endpoint security capabilities.
High Performance Architecture & Deployment Flexibility
Trellix NDR is a high-performance architecture designed to meet the demands of modern enterprise networks. Our solution delivers industry-leading throughput of up to 100 Gbps, with a roadmap to scale to 200 Gbps, ensuring that security never becomes a bottleneck for business operations. The platform's flexible deployment architecture accommodates on-premises, cloud, and hybrid environments, providing consistent security capabilities and unified management across all environments.
AI-Driven Innovation with Trellix Wise™
The evaluation highlighted our integration of Trellix Wise, our GenAI-powered investigation tool. This groundbreaking technology automates MITRE ATT&CK mapping, provides detailed event timelines, complete investigations, and delivers actionable remediation guidance. By emulating expert analyst decision-making at scale, Trellix Wise helps security teams accelerate their response to emerging threats while reducing the cognitive load on analysts.
The platform's ability to provide rich contextual insights has proven especially valuable for organizations developing their security teams. It offers a trustworthy path to automation that enhances rather than replaces human expertise. Trellix Wise can be used leveraging cloud infrastructure as well as completely siloed Wise deployment on-prem running on the appliances.
Advanced Forensics for Complex Environments
Visibility is crucial in today's hybrid and multi-cloud environments. Trellix NDR's advanced forensic capabilities enable security teams to conduct detailed investigations across their network infrastructure. From full packet capture and session reconstruction to sophisticated behavioral analytics, inline-file analysis with integrated sandbox on-board the NDR sensor, our platform provides the deep insights needed to understand and respond to complex security incidents.
Our solution particularly excels in detecting and responding to multi-stage ransomware attacks, identifying early indicators such as lateral movement or privilege escalation before ransomware can fully execute. This proactive approach, combined with detailed forensic analysis capabilities, helps organizations maintain compliance with regulatory requirements while effectively protecting their critical assets.
Looking Ahead
As cyber threats continue to evolve, so does our commitment to innovation. Our technology roadmap focuses on enhancing cloud-native capabilities, improving analyst experience through advanced automation, and expanding our AI-driven detection and response capabilities. We're also investing in advanced capabilities for IoT/OT environments and enhanced predictive analytics to help organizations anticipate and prevent emerging threats.
The QKS Group SPARK Matrix™ evaluation validates our strategy of providing comprehensive, intelligent, and integrated network security solutions. As organizations face increasingly sophisticated threats, Trellix remains committed to delivering innovative security solutions that help them detect, analyze, and respond to threats across their entire network infrastructure.
To learn more about Trellix NDR visit:
https://www.trellix.com/platform/network-detection-and-response/
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
