Ransomware Detection and Response
Put ransomware nightmares to sleep. Minimize the time to detect, investigate, and respond to ransomware threats.
The ransomware challenge
Ransomware is not an if but a when. The Trellix Advanced Research Center analyzed more than 9,000 real-world attacks to develop a ransomware kill chain model that helps you combat ransomware while reducing time to value, cost, complexity, and overall risk.
Addressing all stages of the ransomware kill chain
Trellix provides critical coverage for all stages of a sophisticated ransomware campaign—from reconnaissance to recovery.


![]()
Reconnaissance
Prepare for an attack with insights, services, and threat intelligence.

![]()
Initial access
Prevent attackers from gaining access and detect suspicious activity on email and endpoints.

![]()
Escalation and lateral movement
Detect attacker activity with visibility into lateral movement, use of remote management tools, and more.

![]()
Data collection and exfiltration
Mitigate potential impact by preventing data loss and providing visibility into data archiving and other activities.

![]()
Degradation of recovery and system security services
Mitigate malicious tampering of files, services, and security settings and detect any destruction of data.

![]()
Ransomware deployment, execution, and encryption
Recover with rollback actions, guided playbooks, and enhanced visibility.

![]()
Recovery and retrospective
Perform root cause analysis, so that you avoid reinfection and emerge stronger and more resilient.
The Trellix Security Platform advantage
Related products
Trellix Endpoint Security
Protect against modern and novel threats with a multilayered protection stack delivered in a single agent. Identify and contain the blast radius with embedded forensics.
Trellix Network Detection and Response
Get extended visibility, multilayered threat detection, and accelerated investigation and response into network traffic across each stage of the MITRE ATT&CK framework.
Trellix Data Security
Protect sensitive and proprietary information shared on endpoints, networks, email, the web, and within databases.
Trellix Email Security
Identify, isolate, and protect against advanced URL and attachment-based attacks.
Trellix ePolicy Orchestrator
Automate daily tasks with a single, centralized, and extensible platform for endpoint security policy management.
Trellix Threat Intelligence
Gain actionable insights into cyberthreats and the entities behind them based on data from hundreds of millions of sensors globally.
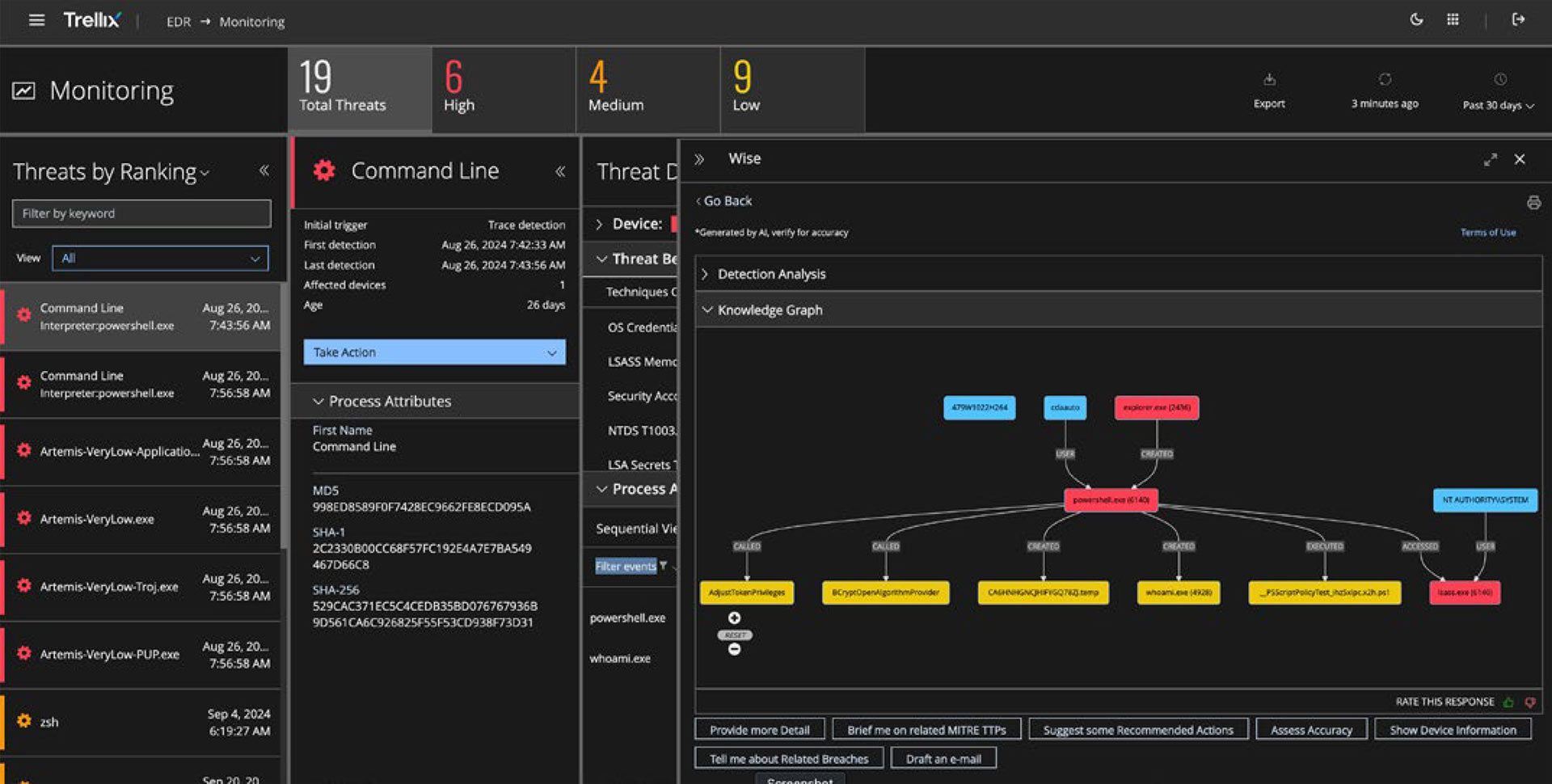
Trellix Wise
Accelerate investigations with Trellix WiseTM AI
Amplify detections, alert correlation and prioritization, and investigative workflows with Trellix Wise AI.
Investigate
all alerts
Make better,
faster decisions
Automate
findings reports
Optimize security operations with Trellix MDR offerings
Extend your security teams and achieve peace of mind with continuous AI-powered detection and response, managed 24/7 by elite Trellix experts.
E-book
The CISO's Guide to Ransomware
How to prepare your organization to take action when every minute counts. Communicate with your board more effectively, evolve your maturity, and learn 10 best practices to become ransomware ready.
Related resources

Get a comprehensive framework for integrating threat intelligence, proactive hunting methodologies, and advanced detection engineering into modern security operations.

Insights gleaned from a global network of experts, sensors, telemetry, and intelligence.

Stay ahead of cyber risks with our analysis of cybersecurity threats, emerging vulnerabilities, and defense strategies.

Effective threat hunters need AI-driven tools to counter adversaries. Learn how to combat threats using the highest-quality intelligence.