Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Cybercrooks Leveraging Anti Automation Toolkit for Phishing Campaigns
By Vihar Shah and Rohan Shah · December 18, 2023
Threat actors have a track record of abusing tools hosted on GitHub for malicious purposes. Last year we showed how attackers abused Python’s tarfile module. Trellix Advanced Research Center has tracked abuse of one more such tool used for quite some time now. Predator, a tool designed to combat bots and web crawlers, can distinguish web requests originating from automated systems, bots, or web crawlers.
This blog will show how cybercriminals have abused this GitHub tool, and how this tool has been used in multiple phishing campaigns with frequently changing url patterns in a very short span.
Attack Flow:
The attack starts with a phishing email containing malicious links. All samples we have checked have originated from compromised email accounts. So, this is a staged attack where attackers are using already compromised accounts to conduct subsequent phishing campaigns. Attackers change their email template and the brand they’re impersonating quite often. The emails are designed to create a sense of urgency or mimic a legit notification to trick users to interact with URLs.
Once the victim clicks on a malicious link, evasion code checks for possible bot/crawler/automation. If it detects one, it redirects to legit pages like Wikipedia or Google search; otherwise it will show the actual phishing page.
Analysis of evasion technique used:
In this attack, criminals are using evasion techniques to avoid scanning of URL content. For automation detection, the attackers used a tool created for legitimate red-teaming purposes, and has abused it maliciously.
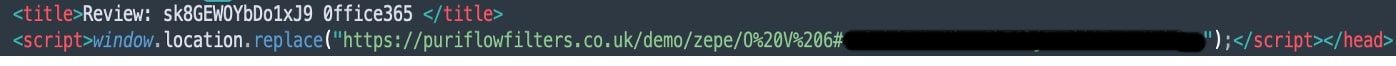
When the user clicks on the link, the first page uses the window.location.replace method to redirect to the next page. But the page still hosts further code to test possible bot/crawler/automation.

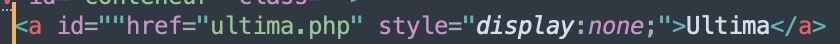
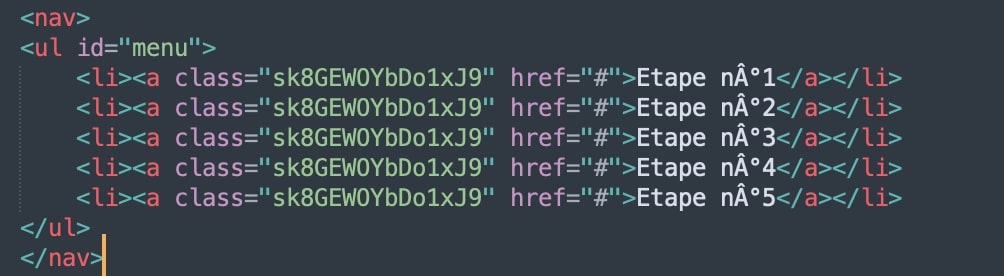
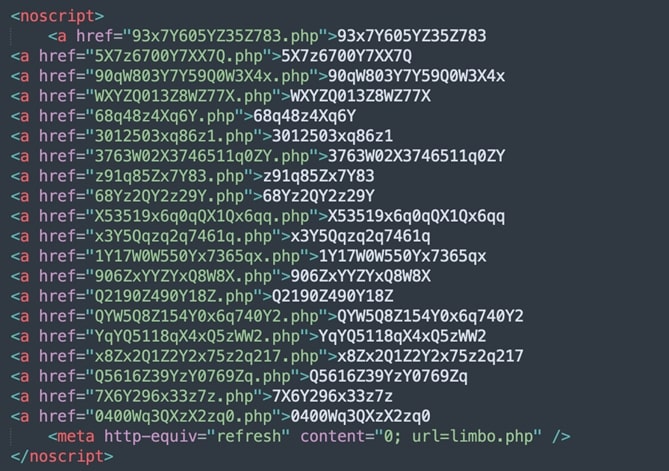
The above images show how hidden/empty links are created to detect automation tools. These invisible links will be not visible when the page is rendered in the browser window, but automated programs can still see them as they check for all links present in code. If any of these URLs are traversed, most visitors will be automated programs only and the attacker can take a desired action such as blocking the IP address or redirecting to legit sites instead of actual phishing pages. Also notice the use of “junk” text in between words to avoid any string-based detection.
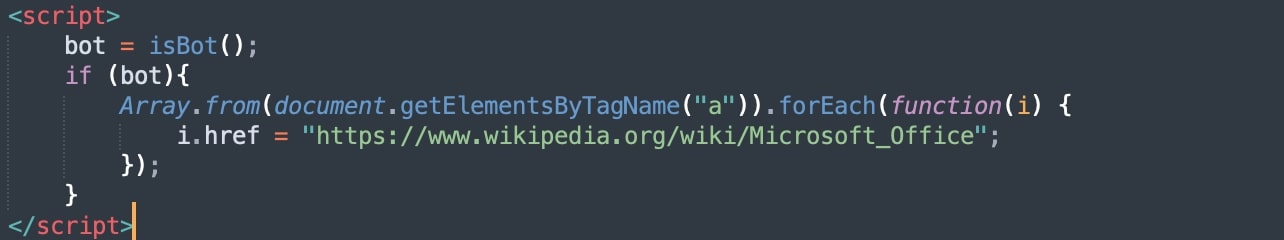
And if the above method does not work, the tool uses further techniques to detect bot/crawler/automation using the isBot() function that performs various tests. As you can see in the above code, if a bot is detected, it changes all <href> links within the page to Wikipedia links.
After this, there are 2-3 further redirects that change path within the same site and are not doing much. In the final redirection we see the below code.
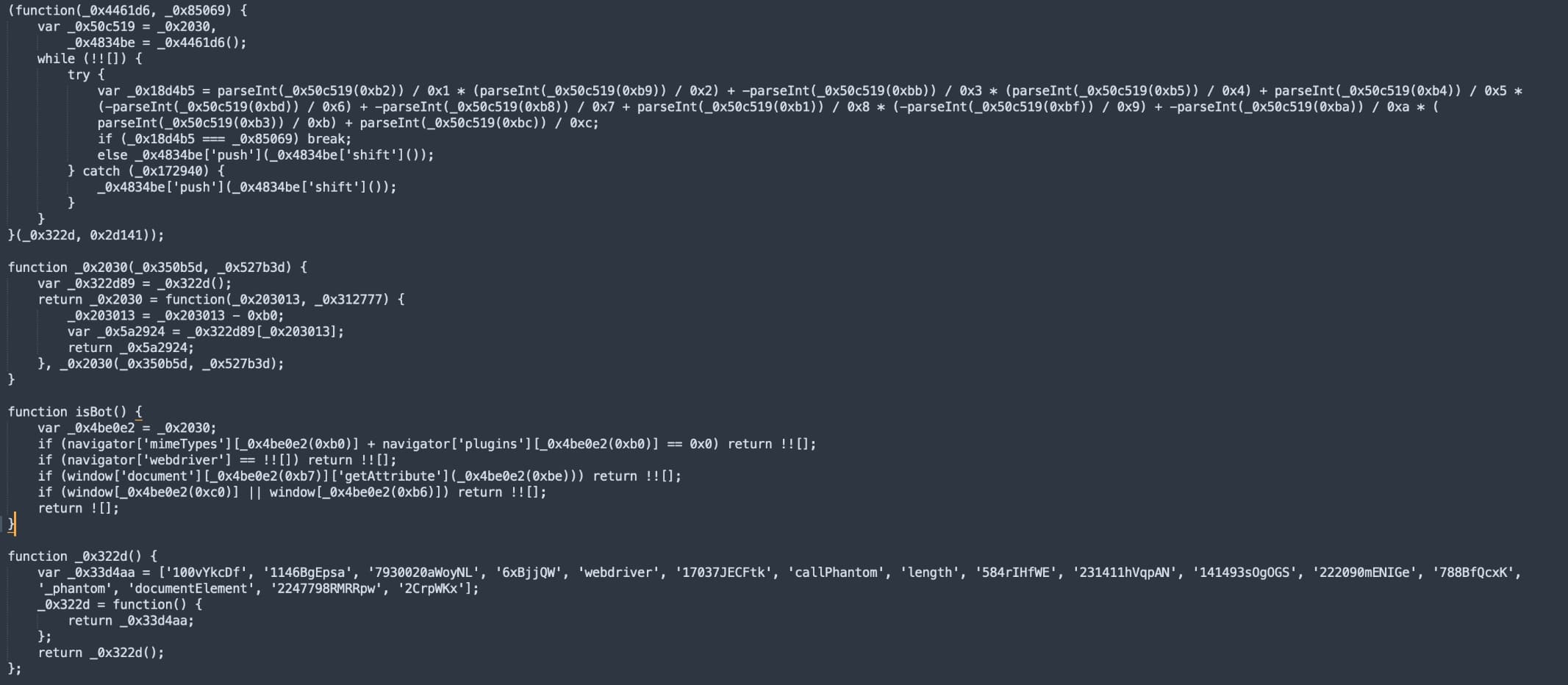
There are four functions which are highly obfuscated with hex strings, seen above. The main function is isBot(). To make things difficult for analysis, instead of using straightforward code used in the original tool, the attacker has created 3 extra functions that use hex strings. Hex coded strings in the isBot() function are replaced by some strings found in var _0x33d4aa.
If we compare this code with the original code used in the tool, we can easily see what the code is doing.
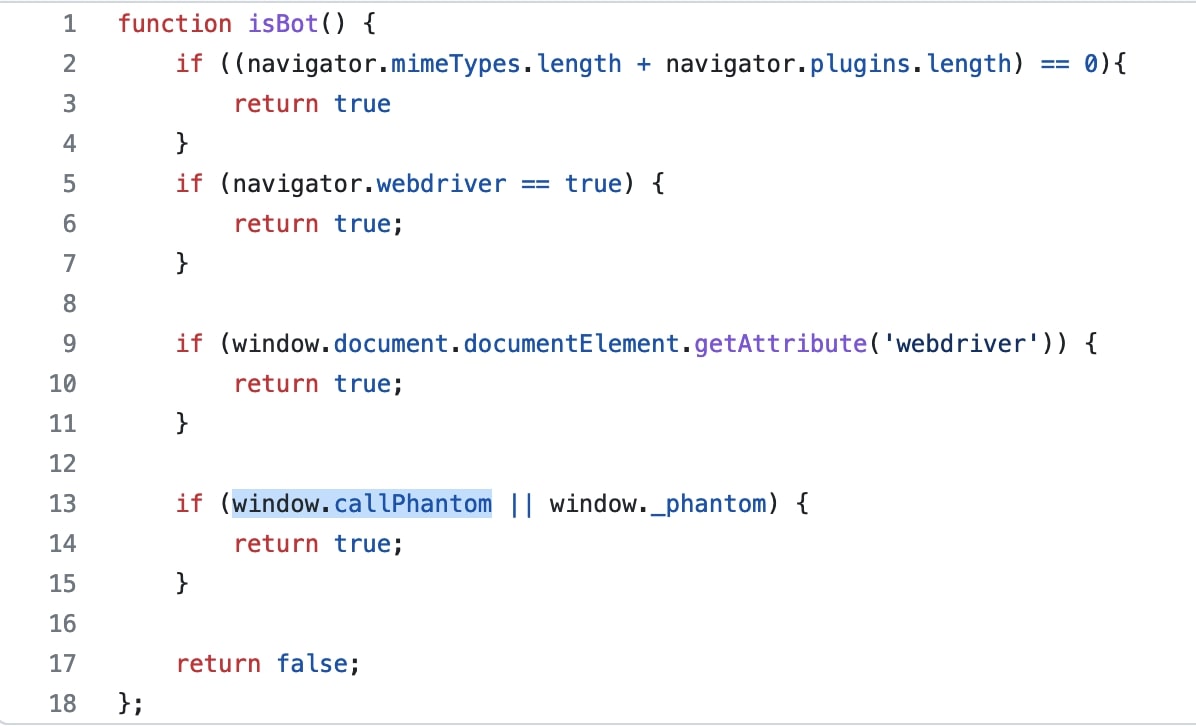
The first condition is checking for “mimeTypes” and the number of plugins in the browser. HTTP headers sent by bots/automation tools are often in different order when compared to a real browser or many just do not send at all. mimeTypes obtains a list of all the MIME types supported by the browser, and navigator.plugins contains a list of plugins installed. If the length of both is 0, then it probably means that the visitor is a bot.
In the second condition, “navigator.webdriver” indicates whether the user agent is controlled by automation. So, if it is true then it is a bot. The third condition checks for the same.
The last condition “if (window.callPhantom || window._phantom)” checks for usage of the PhantomJS browser. PhantomJS is a discontinued headless browser used for automating web page interaction.
And lastly, when the tool suspects that the visitor is a bot, it generates random links which direct to a page limbo.php containing more random links, and this process keeps repeating. Again, attackers slightly changed tactics from the original tool: instead of generating random links dynamically, they hardcoded random links as can be seen in the below screenshot.
Phishing samples from the wild
The Trellix Advanced Research Center has tracked various campaigns using this evasion technique since December 2022. The following are a handful of samples found in the wild:
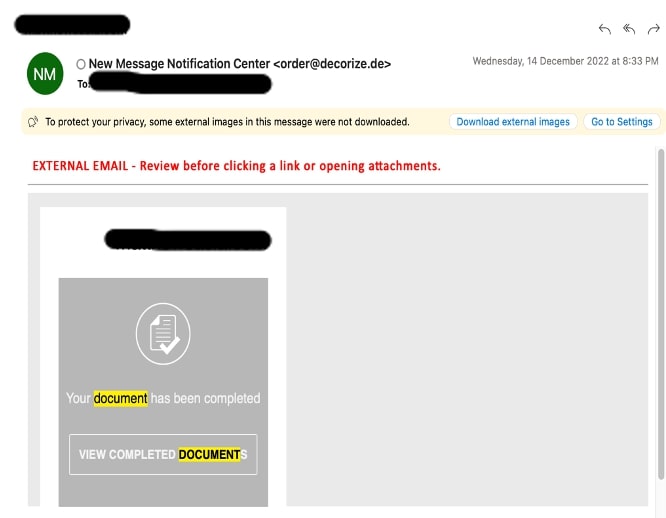
Sample 1
The email is a fake notification asking to review a document sent by a user and the recipient has completed that document.
There is a URL which leads to a phishing page once clicked.
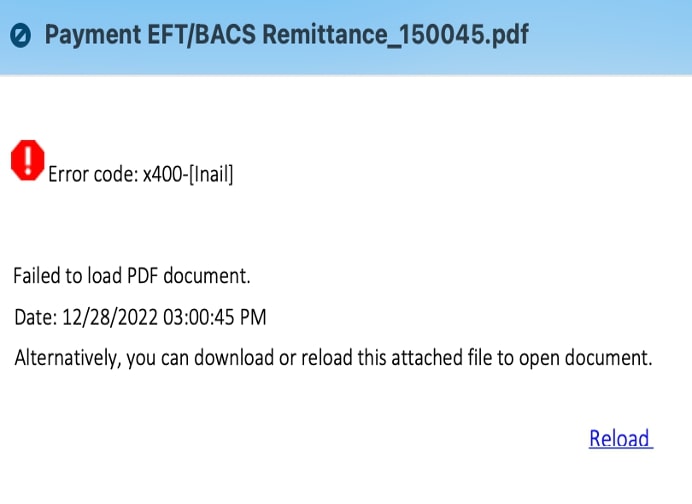
Sample 2
The email includes a fake remittance, and has a malicious link in the attached pdf.
Sample 3
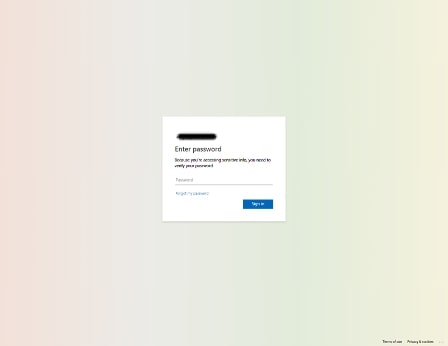
The email is a fake missed voice call notification having a malicious link which leads to a fake Microsoft phishing page.
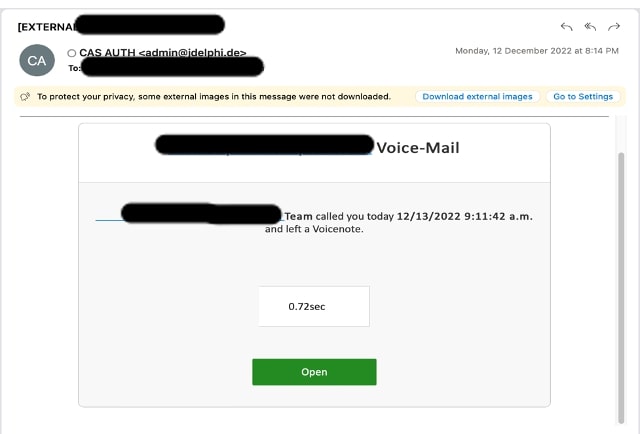
Sample 4
The email is a mailbox storage notification asking for immediate action to prevent mailboxes from malfunctioning.
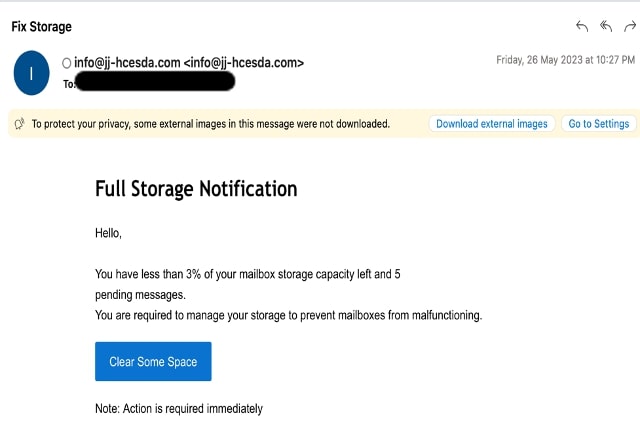
Sample 5
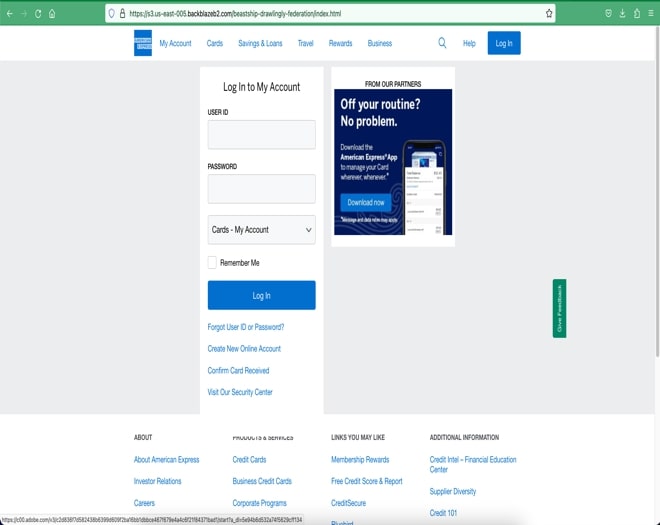
The email is a fake American Express notification to revalidate American Express credentials. To avoid any word/sentence-based detection of the email, the attacker used only inline images having text instead of directly using text in the message body.
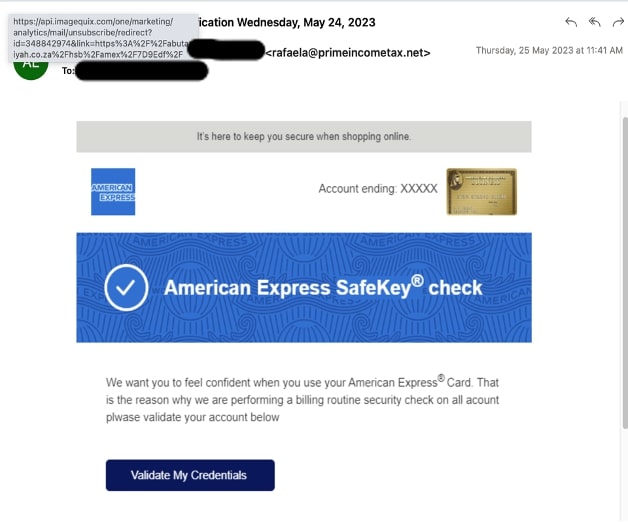
Sample 6
The email is a file share notification by First American Title to open a shared secure Doc. Again, the attacker used only inline images having text instead of directly using text in the message body.
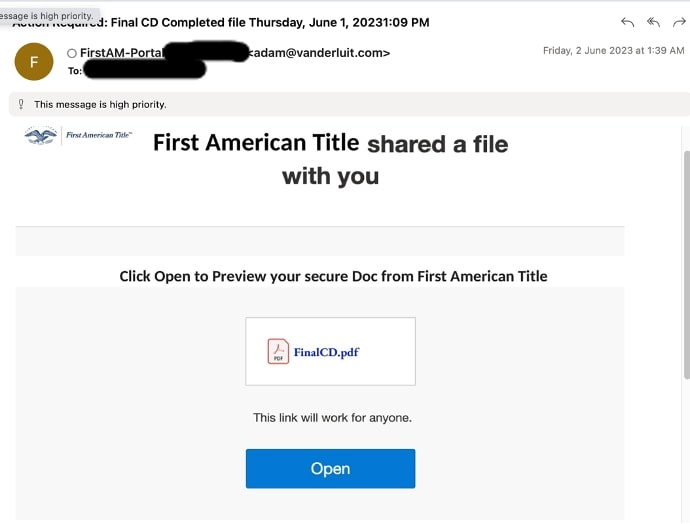
One Tool, many usages:
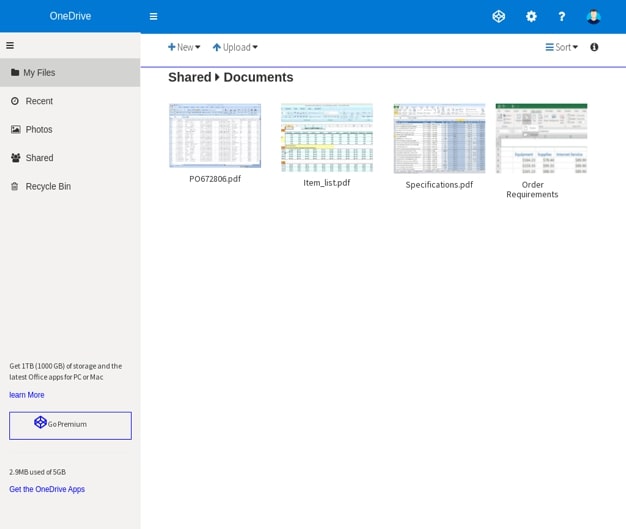
As we can see in the above samples, this tool is not limited to a single phishing campaign. We have seen American Express phishing as well as Microsoft 365 and OneDrive phishing.
Also, the attacker has changed URL patterns very frequently to avoid any URL based pattern.
Conclusion
Cyber criminals are always looking for new ways to evade detection from organizations’ security products. Open-source tools such as these make their task easier, as they can readily use these tools to avoid detection and more easily achieve their malicious goals.
Also, these threat actors have become more sophisticated, using different URL patterns and targeting multiple brands to achieve better success rate for their phishing campaigns. Since such attacks often originate from compromised accounts, educating employees to be more careful while opening attachments or clicking links in email is absolutely vital today.
Trellix product coverage
Trellix Email Security provides reliable detection from such campaigns by preventing malicious emails from ever reaching your system. Trellix Email Security detects this campaign with the following rule:
- Phishing_Bot_Evasion
Indicators of compromise (IoCs):
Below are just a few examples of ever-changing URL patterns used by attackers.- u29421114.ct.sendgrid.net/ls/click?upn=e94YjHb22mXQExZeqifeFl1jcmssiC-2Bt12dCq-2FC-2B0vGfntvJQRpI0UhFwvn-2BptFK1nJKJNYWovH2Fn0kFMZ7LW9HeSvBsycWiCS2e4DyCGMi4mqRJj-2FnDOJddSOGYimMbNWt_RTDQb-2BhtsIfNiUEWbcIZ3tj5ZqpiJX1igf-2BE5jeDjF6qRwcWCkJ1V-2BbcTddk4l-2FfyH-2BJ5n4wDxapd8wiOWZU3UlLzJoagpMNtk4SEC4-2BM6zaVaqlYbamNRfL4iCCoxaNPhpxj-2FzLhNkNEaBzdOz-2FfYspPyhzQQXWkNKyMwQBTWa0i9dwVZWZWmW4wV6f4p4xxc3-2FMj1KA-2B1VSERCmQ-2Bl3ESVU8CmonAO7pn-2F-2BIbU0QE-3D
- ipfs.io/ipfs/QmWjcYbGL1ek5djYTCe6VU52T7Xd6MSjrrra8zqr88U2Yp
- hxxps://25675.nafay.org/jtuhfhb/vgryujbfhb/gfyujfg/LwBkTy/<victim email id>
- hxxps://698619018.cprecnepal.org/yitixoxufdrv/doicililios/fpZnDg//<victim email id>
- https://1612579504.universalimage.org/zilbanitewed/yitukiniki/QgkcbB/<victim email id>
- hxxp://xx2rpl.inetlte.kpmark.slaughterjbu.alzeraf.com/////rat/////ret/IEYly1////<base 64 encoded victim email id>
- hxxp://47962.adistu.ro/#<base 64 encoded victim email id>
- hxxp://oneconnect.memberdoc.com/v2/EmailTracker/Click?data=247822_120633631_1~https://gagnon-construction.com/own#<victim email id>
- hxxps://www.bing.com/ck/a?!&&p=cfdcca34c3e54300JmltdHM9MTY4NDEwODgwMCZpZ3VpZ
D0xNDdmYWI3MS02M2FiLTZhZjItMDM3OS1iOTlkNjIxYzZiMWYmaW5zaWQ9NTMwNw&ptn=3&hsh=3&fclid=147fab71-63ab-6af2-0379-b99d621c6b1f&u=a1aHR0cHM6Ly9wcm9hdWRpb2xpZ2h0aW5nLmNvbS83ODcvNzI5OTkyLmh0bWw#<base 64 encoded victim email id> - hxxps://api.imagequix.com/one/marketing/analytics/mail/unsubscribe/redirect?id=348842974&link=https://abutazkiyah.co.za/hsb/amex/7D9Edf/
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.