Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Saints Turned Evil
By Daksh Kapur and Rohan Shah · January 2, 2024
This blog was also written by Sushant Kumar Arya

As technology advances, attackers are constantly developing new evasion mechanisms to bypass security products and stay one step ahead of security vendors and their products. We have seen various types of evasion mechanisms employed by attackers in recent years.
Evasions
- Geofencing, where a URL serves malicious content only when accessed from the target country or region, while remaining legitimate or providing no content to users from other countries.
- Captcha to bypass automated crawling thus restricting analysis of URL payload by security products.
- IP evasion, where attackers blacklist the public IPs of specific services or organizations. By doing so, they ensure that their phishing or malicious payload is not served when requests come from those blacklisted IPs. This approach effectively blocks the analysis of URLs by security products.
- QR codes serve phishing attacks as discussed in our recent blog, since QR code hides the embedded payload, it evades detection from traditional email security products thus bypassing them.
Trellix Email security has recently discovered a novel evasion tactic. In this method, attackers aim to deceive the caching mechanism of security products. Their strategy involves caching a seemingly benign version of the attack vector and subsequently altering it to deliver a malicious payload.
What is caching?
In simple terms, caching involves temporarily storing the result for an input element. When that same input comes in again, the stored result is swiftly retrieved, cutting down on time and processing costs. Security Products frequently use caching to boost speed and efficiency. So, when a URL gets scanned, the result is stored and cached for a set time. If the same URL is checked within the pre-set time frame, the security product doesn't reprocess it — it just serves up the stored result.
Attack flow
Phase 1
The attack begins with the targeted individual receiving an email containing a Call To Action (CTA) URL, guiding them to a website or document containing an additional link or button. Our researchers have noted a recurring pattern where attackers often employ OneDrive Document URLs as CTA URLs. This choice is attributed to the sense of trust added by the reputation of Microsoft owned domain.
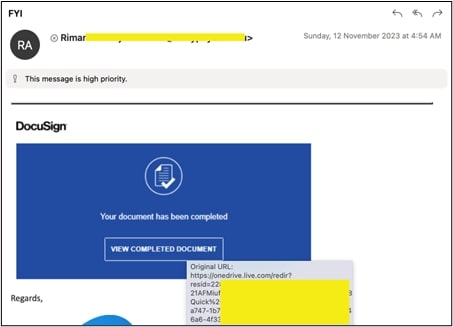
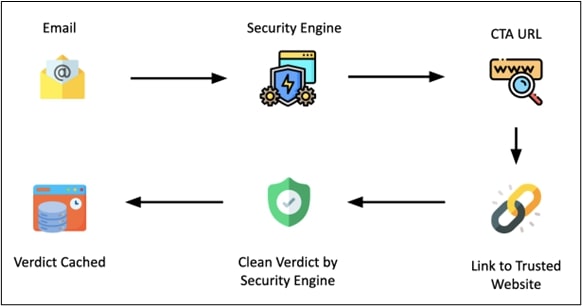
Phase 2
In the second phase, the Security Engine checks the CTA URL. This URL has a link/button that leads to well-known and harmless sites like google.com or microsoft.com. Since there's nothing suspicious about a URL linking to such trusted sites, the security engines label the CTA URL as safe and save this verdict in their cache.
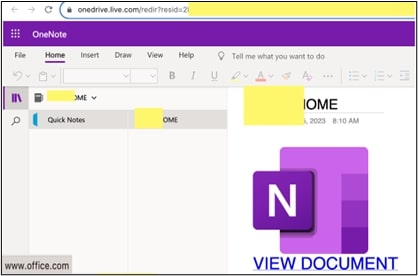
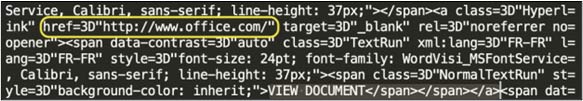
Phase 3
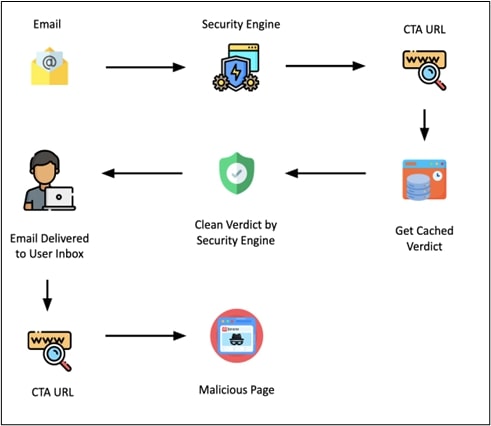
In the third phase, the attackers wait for security vendors to process the CTA URL and cache their verdict. Once this happens, the attackers make their move: they tweak the link/button on the CTA URL. The link which was earlier leading to trusted websites, now redirects to the actual malicious page.

Since the page was initially cached as benign after the first scan by security vendors, until the cache period expires, every encounter with the same CTA URL prompts the security engine to consistently return a benign verdict stored in the cache.
With the verdict being benign, the email smoothly lands in the victim's inbox. Now, should the unsuspecting recipient decide to open the email and click on the link/button within the CTA URL, they would be redirected to the malicious page.
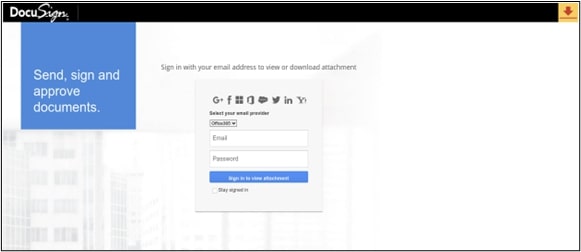
(Attribution at the Bottom)
(Attribution at the Bottom)
Trellix email security
Trellix Email Security performs force analysis of CTA URL at the time of user interaction, hence it sees the phishing URL embedded into the CTA URL, thus detecting the phishing URL. Consequently, any detected phishing URLs are instantaneously blocked, preventing the user from accessing potentially harmful content. Moreover, a protective block page is presented to the user, ensuring the safety of both the individual and the organization.
Trellix email security telemetry
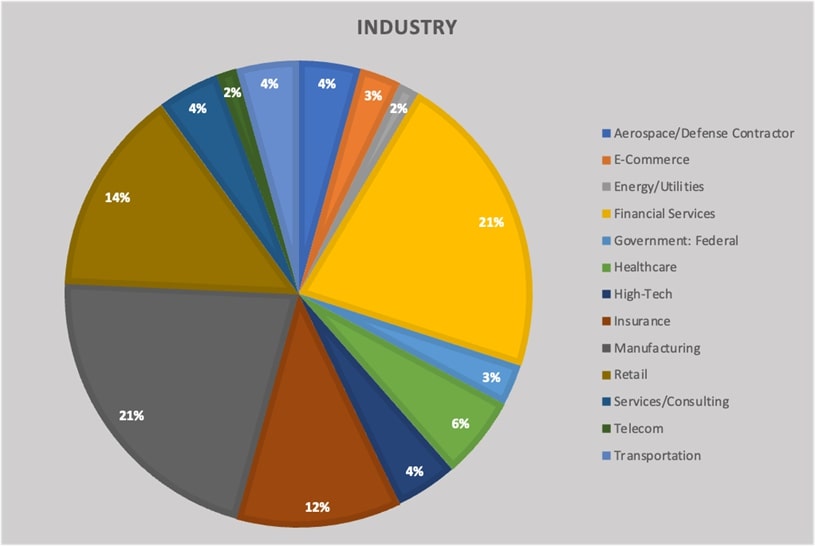
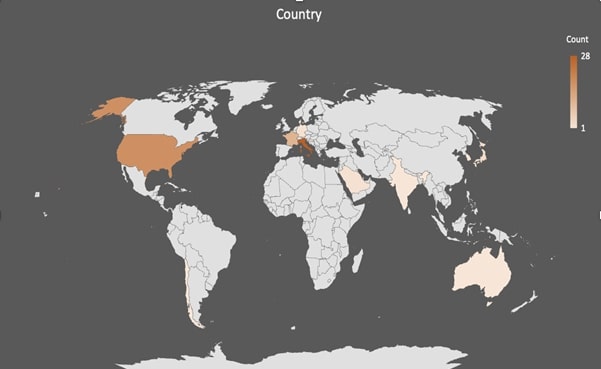
We have witnessed these attacks occurring on a large scale rather than being aimed at specific customers, regions, or industries. Instead, they have encompassed various regions and industries. The following diagrams depict the impact of this attack on various industries and countries.
Indicators of Compromise (IOC)
URL
Subjects
Trellix product protections
The following is a subset of the Trellix Security detections that have been observed for the ongoing campaigns:
Phishing_OneNote_Abuse_SS_1
Phish.Live.DTI.URL
Conclusion
In summary, we have observed that attackers have devised an innovative method of evading security products by targeting their architecture and design to carry out successful attacks. However, thanks to Trellix email security's force scanning of URLs during user interaction, altered phishing links are swiftly identified and detected. As a result, this novel evasion technique is effectively mitigated, ensuring the protection of our valued customers.
Attributions
We would like to give proper credit and recognition to the various elements that have contributed to the content of this blog. The following list outlines the attributions for these elements:
Images
Icons
- Email icons created by Freepik - Flaticon
- Search icons created by Freepik - Flaticon
- Link icons created by Freepik - Flaticon
- Shield icons created by Freepik - Flaticon
- Cache icons created by Freepik - Flaticon
- Anti virus software icons created by phatplus - Flaticon
- Security icons created by Freepik - Flaticon
- User icons created by Freepik - Flaticon
- Click icons created by Freepik - Flaticon
We sincerely appreciate the contributions of these elements to our blog and acknowledge the importance of giving credit where it's due. Should there be any concerns regarding attributions or if corrections are needed, please don't hesitate to contact us. Your understanding and support are greatly valued.
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.
