Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Trellix NDR Innovation: Risk-Based Intelligence for Modern Network Security
By Tom Stitt · May 29, 2025
The modern network security landscape continues to overwhelm security teams with an unprecedented scale and complexity. According to a 2024 report, the average enterprise now manages over 1.5 million cyber assets, a number that has increased by 145% year-over-year.1 Meanwhile, 40% of security alerts are ignored due to analyst overload,2 leaving organizations vulnerable to critical threats. Additionally, organizations face over 3,000 new vulnerabilities monthly,3 yet traditional security tools often fail to provide actionable insights tailored to a business's specific environment.
Trellix Network Detection and Response (NDR) transforms this challenge through intelligent risk prioritization—automatically focusing security teams on threats that matter most to their specific environment. Trellix NDR delivers three core advancements that support risk-based decision-making: streamlined analyst workflows that eliminate low-value activities, advanced detection and investigation capabilities that provide threat context, and comprehensive integrations that enrich risk-based threat assessment with vulnerability and asset intelligence. Additionally, existing Trellix Network Security (NX) customers gain seamless access to these capabilities as NX evolves into the NDR Sensor as part of the Trellix NDR solution.
Enhanced Analyst Experience: Risk-Driven Workflows
The complexity of modern threat investigation often forces analysts to spend more time gathering context than actually analyzing threats. Trellix NDR eliminates this inefficiency through redesigned workflows that automatically surface the most critical information, automatically enrich alerts, and guide analysts to high-impact activities.
Detection Dashboard
The redesigned Detection Dashboard transforms alert triage from a chronological list into a risk-prioritized command center. Rather than overwhelming analysts with every alert, the dashboard presents Top Risky Assets, Top Risky Conversations, and Top Alerts based on our Risk-Based Aggregation Framework. This intelligent prioritization considers MITRE ATT&CK tactics, asset criticality, and vulnerability exposure to ensure analysts focus on threats that pose actual business risk.
Additional dashboard components include geographic alert visualization, MITRE ATT&CK tactic distribution, and asset operating System risk correlation—providing comprehensive situational awareness without information overload.
Alert Workflows
Alert investigation workflows provide comprehensive context within a single interface, eliminating the need to pivot between multiple tools for threat analysis. The enhanced Alert Details page automatically enriches alerts with MITRE ATT&CK mappings, CVE correlations, and threat intelligence context, while the integrated conversation graph visualizes network communications related to the alert.
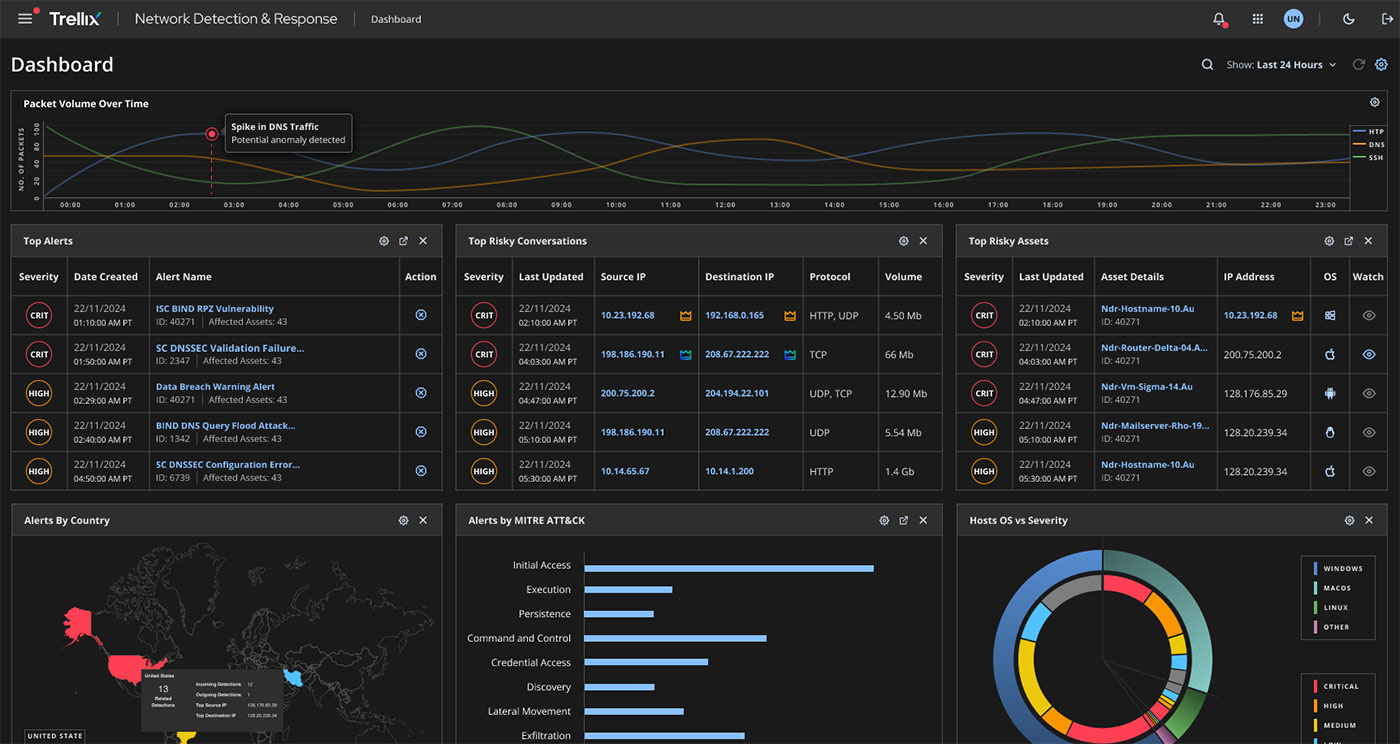
Analysts can validate threats, understand attack scope, and initiate response actions from a unified workspace that aggregates all relevant information.
Asset Workflows
Asset investigation capabilities provide visibility into system risk and activity patterns. The redesigned Asset Details page combines vulnerability assessments, alert history, network communications, and endpoint status into a comprehensive risk profile. The integrated conversation graph reveals both primary and secondary network relationships, enabling analysts to quickly identify potential lateral movement paths.
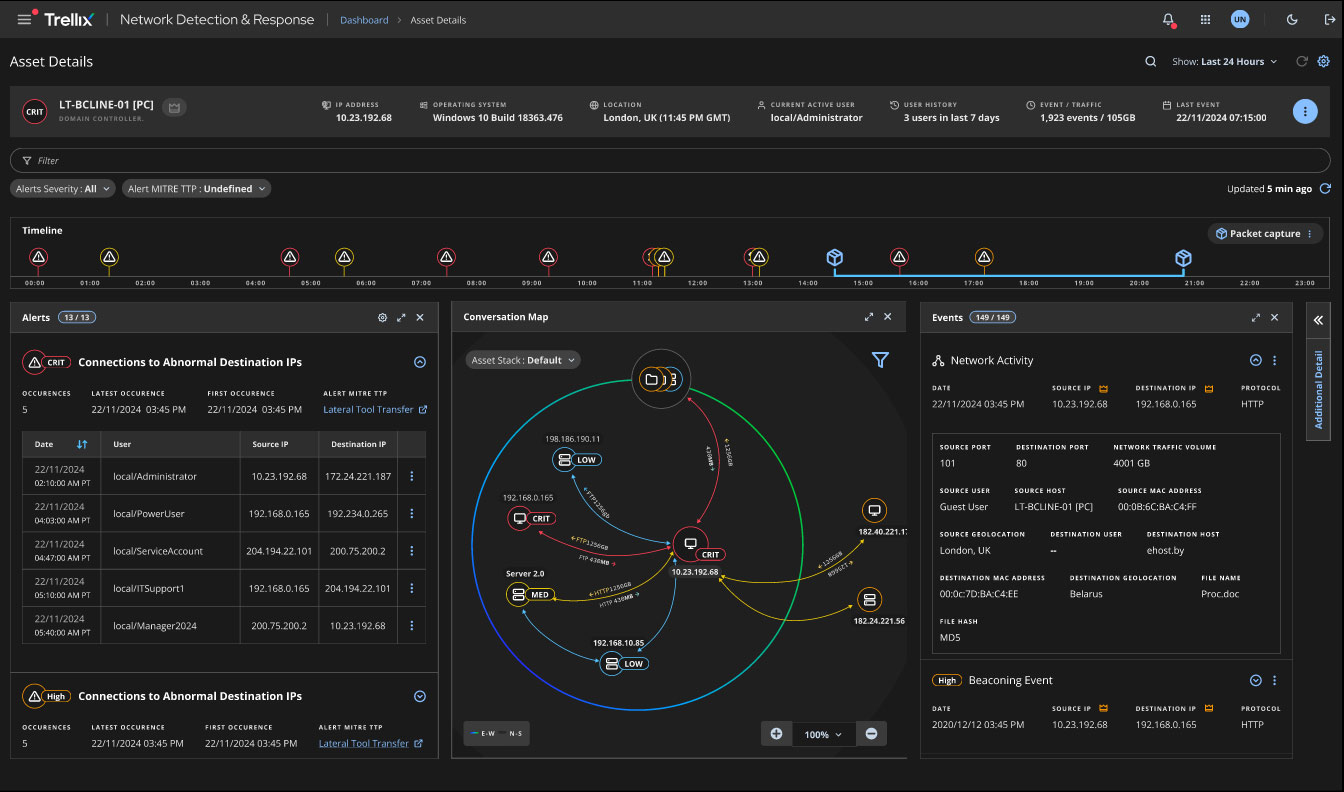
Timeline visualization shows alert progression and network activity changes, providing crucial context for understanding attack evolution and system compromise indicators.
Trellix Wise: AI-Powered Investigation Assistant
Trellix Wise transforms junior analysts into advanced investigators through automated threat analysis and contextual guidance. This AI-powered capability automatically generates alert summaries, identifies top affected entities, provides MITRE ATT&CK context, and recommends specific remediation steps based on threat intelligence and environmental factors.
The knowledge graph feature visualizes relationships between threats, assets, and vulnerabilities, while sequence diagrams reconstruct attack timelines—capabilities that previously required extensive manual analysis and specialized expertise.
Advanced Detections and Analytics: Comprehensive Threat Coverage
Modern attackers leverage sophisticated evasion techniques that bypass traditional signature-based detection systems. Trellix NDR delivers multi-layered detection capabilities that identify threats across all attack phases, with particular strength in analyzing encrypted communications and identifying subtle behavioral anomalies.
Attack Path Discovery
Understanding potential attack vectors before exploitation occurs represents a fundamental shift toward proactive security operations. Attack Path Discovery visualizes how attackers could escalate privileges and move laterally through network infrastructure, combining real-time vulnerability data with network topology analysis to identify the most critical and risky assets.
This capability integrates seamlessly with Tenable Security Center to provide risk-informed vulnerability prioritization, transforming generic CVSS scores into contextual risk assessments based on actual attack feasibility. Security teams can now focus remediation efforts on vulnerabilities that pose genuine threats to critical business systems rather than addressing every identified weakness.
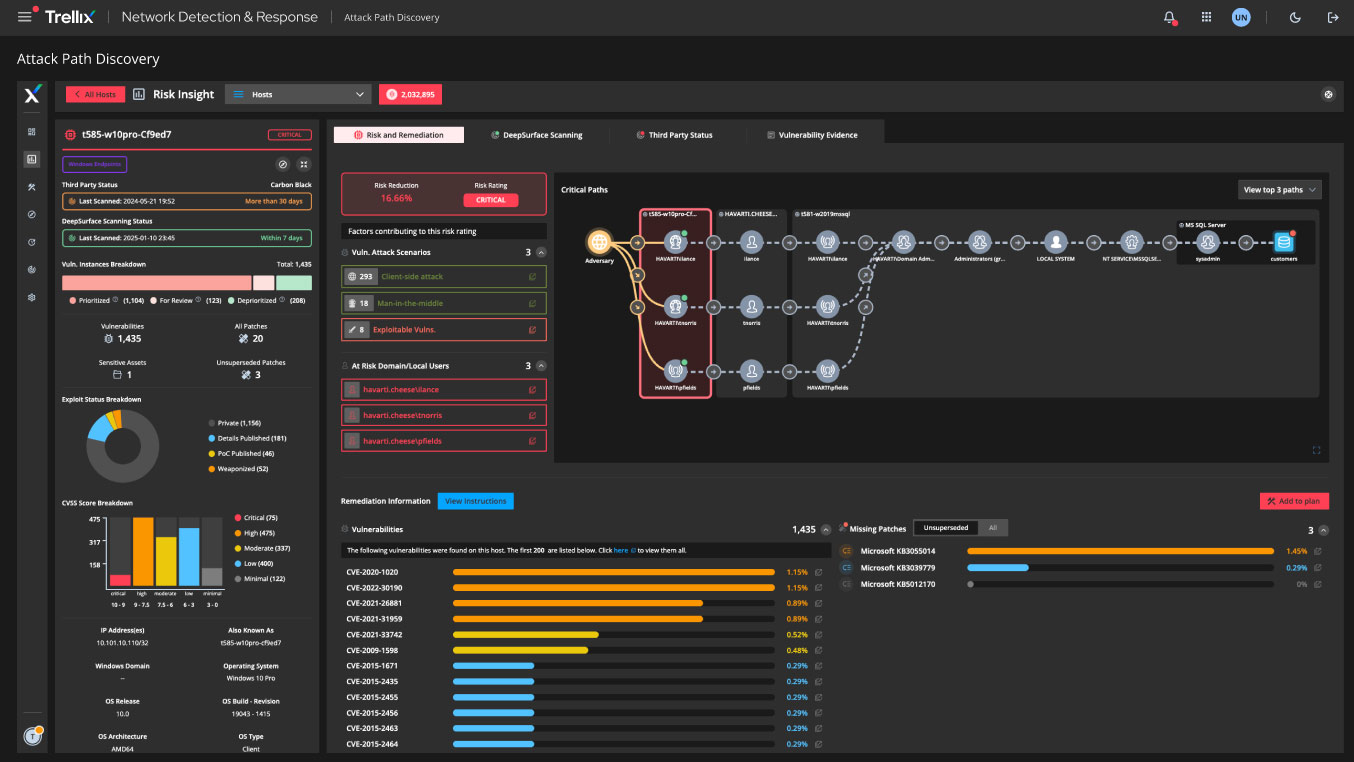
The proactive identification of attack vectors enables preventive security measures and strategic risk reduction aligned with actual threat landscapes.
Machine Learning-Based Detections
Trellix NDR employs advanced behavioral analytics that establish environment-specific baselines and identify subtle anomalies indicating compromise. These machine learning models adapt continuously to network communication patterns, enabling detection of previously unknown threats and attack techniques that evade signature-based systems.
Key capabilities include lateral movement detection, which correlates weak indicators across network segments to identify sophisticated privilege escalation attempts, and beaconing detection that identifies command-and-control communications through statistical analysis of traffic patterns.
Encrypted Traffic Analysis
With 95% of network traffic now encrypted,4 traditional deep packet inspection provides limited visibility into encrypted threat activity. Trellix NDR addresses this challenge through sophisticated encrypted traffic analysis that identifies threats without requiring decryption.
Certificate and SSL Analysis
- GTI Certificate Reputation automatically identifies malicious certificates in encrypted communications
- SSL Anomaly Detection flags suspicious behaviors including self-signed certificates, expired certificates, and weak cipher implementations
- Advanced fingerprinting techniques (JA3/JA3S/JARM) provide comprehensive visibility into encrypted communications
Communication Pattern Analysis
- Communication to Newly Registered Domains identifies connections to infrastructure created within configurable timeframes
- DNS Tunneling Detection employs machine learning to identify covert command-and-control channels
- ToR Activity Detection automatically identifies anonymized network communications
These capabilities operate through behavioral analysis rather than content inspection, maintaining privacy compliance while providing comprehensive threat visibility.
Advanced Threat Detection Capabilities
Beyond encrypted traffic analysis, Trellix NDR includes specialized detection capabilities for emerging attack techniques:
- Phishing Credential Theft Detection identifies successful phishing attacks
- ICMP Tunneling Detection identifies covert data exfiltration through seemingly legitimate network protocols
- Similar URL Detection uses machine learning to identify domain variations that bypass traditional blocklists
- Communication with Known Malicious Hosts provides threat intelligence correlation for infrastructure with established malicious reputation
These detection mechanisms add to Trellix NDR’s comprehensive coverage across the cyber kill chain, from initial compromise through data exfiltration, ensuring sophisticated multi-stage attacks cannot evade detection.
Seamless Transition for Trellix NX
From Trellix NX to the enhanced Trellix NDR Sensor, customers retain all current detection capabilities while gaining access to these advanced analytics and machine learning models. The transition preserves operational continuity while significantly expanding threat detection coverage and reducing false positive rates through intelligent correlation and risk-based scoring.
Integrations Hub: Unified Security Operations
Effective network detection and response requires seamless integration with existing security infrastructure to provide enriched context and coordinated response capabilities. Trellix NDR’s Integration Hub transforms isolated security tools into a unified defense ecosystem through intelligent data correlation and automated response orchestration.
Tenable Security Center Integration
Security teams struggle to prioritize vulnerabilities effectively, often managing massive backlogs without clear guidance on which exposures pose actual risk.
Trellix NDR's Tenable Security Center integration enriches alerts and asset details with vulnerability scan findings, while Tenable vulnerability scores integrate with NDR's network activity analysis for holistic asset risk assessment. Assets with high network risk and significant vulnerabilities are automatically identified for prioritized investigation.
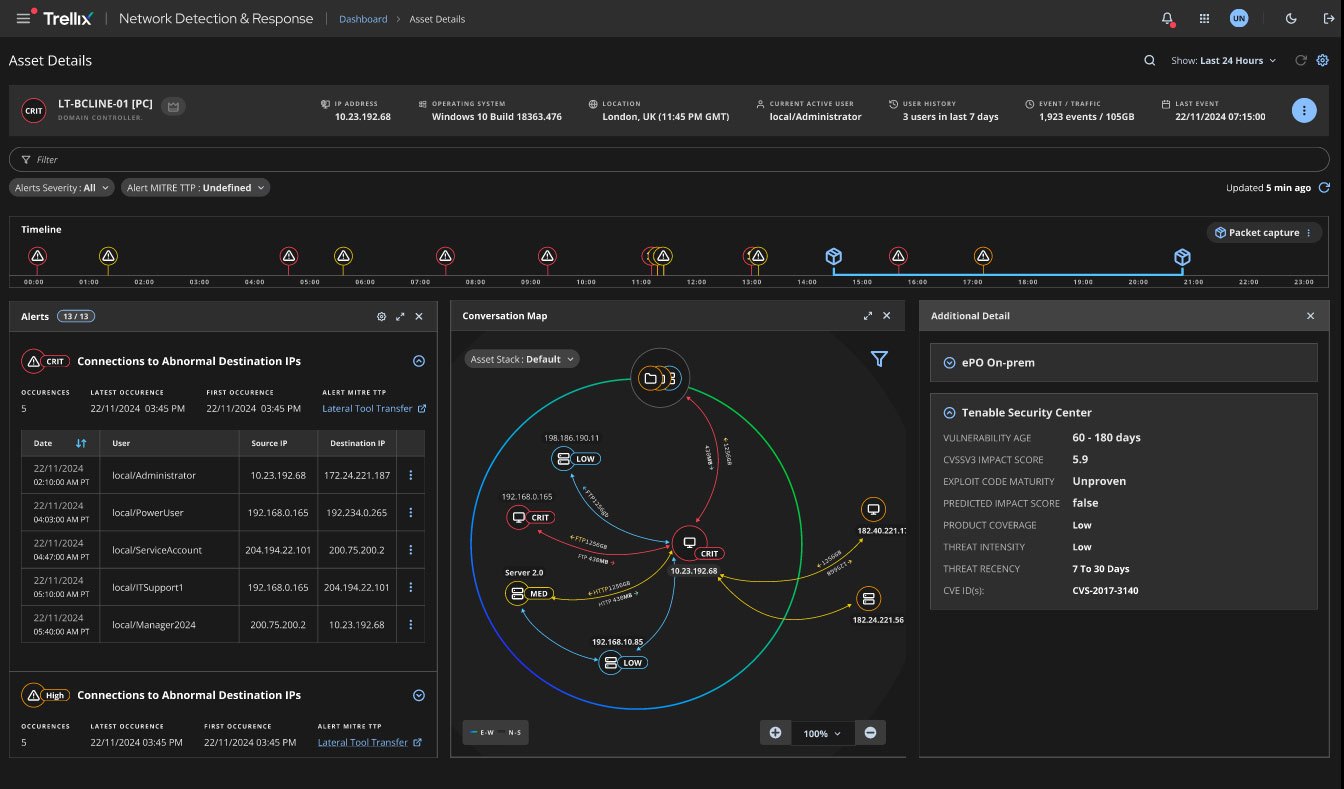
Alert severity calculations now factor in vulnerability ratings from Tenable, reducing low-priority alerts while ensuring critical threats receive appropriate attention. This enhanced risk visibility enables more effective remediation prioritization, helping security teams focus efforts on vulnerabilities that pose genuine threats to their specific environment.
Trellix ePO On-Premises Integration
Coordinated network and endpoint response eliminates the visibility gap between network detection and endpoint protection. The integration with Trellix ePolicy Orchestrator provides asset context including endpoint security status, installed products, and agent connectivity, while enabling direct containment actions from network investigation workflows.
When network analysis identifies compromised systems, analysts can immediately initiate endpoint containment without tool switching or separate authentication processes. The integration distinguishes between managed and unmanaged endpoints, automatically elevating risk scores for systems lacking endpoint protection.
This unified approach ensures network threats receive immediate endpoint-level response while providing complete asset visibility across both network and endpoint security domains.
Splunk and SIEM Integration
Trellix NDR enhances existing SIEM investments through enriched metadata forwarding and flexible integration options. Rather than basic alert forwarding, the solution provides comprehensive context, MITRE ATT&CK mappings, and correlation intelligence that enriches centralized security operations.
The Splunk integration enables correlation of Trellix NDR insights with other security data sources within existing analytics workflows, while generic SIEM integration supports multiple formats (CEF, LEEF, JSON, XML) and delivery methods (HTTP, syslog) for seamless integration with diverse security ecosystems.
Configurable severity thresholds and extended parameter selection ensure security teams receive relevant intelligence without overwhelming existing SIEM infrastructure with low-value alerts.
Ecosystem Integration Architecture
The Integration Hub provides unified management for all security tool connections through role-based access controls and comprehensive monitoring capabilities. Administrators can track integration health, data volumes, and response action success rates through centralized dashboards that ensure optimal security ecosystem performance.
API-driven architecture supports custom integrations and automation workflows, enabling organizations to leverage Trellix NDR intelligence within existing security orchestration platforms and incident response procedures.
These integration capabilities ensure Trellix NDR enhances rather than replaces existing security investments, providing the contextual intelligence and coordinated response capabilities required for effective modern security operations.
Deployment and Availability
Trellix NDR is available across Essentials, Core, and Enterprise packages, with capabilities scaled appropriately for different organizational requirements and threat environments. The platform supports flexible deployment models including on-premises hardware and virtual appliances implementations to accommodate diverse infrastructure architectures.
For organizations currently operating Trellix NX deployments, the transition to Trellix NDR Sensor capabilities occurs seamlessly through licensing updates that preserve all existing functionality while unlocking advanced NDR detection and analytics capabilities. This evolutionary approach ensures operational continuity while providing immediate access to risk-based prioritization and enhanced investigation workflows.
The enhanced detection capabilities, risk-based prioritization, and operational efficiency improvements in Trellix NDR provide measurable security posture improvements while reducing analyst workload and investigation complexity. As threat landscapes continue evolving toward more sophisticated evasion techniques and targeted attacks, these capabilities enable security teams to maintain effective network protection while managing the operational challenges of modern enterprise environments.
Organizations evaluating network security capability gaps or planning infrastructure modernization can leverage Trellix NDR comprehensive detection coverage, intelligent risk prioritization, and unified security operations to build more resilient network security architectures that stay ahead of sophisticated adversaries.
Take the next step to learn more about Trellix NDR or contact your account manager to request a demo or contact us to speak to an expert.
1Cybersecurity Asset Management Report, JupiterOne, 2024
2Ponemon Institute, "State of Security Operations," 2024
3NIST Vulnerability Database, 2024
4Google Transparency Report, HTTPS Encryption on the Web, 2024
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
