Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Crown Jewels of Active Directory: How Trellix Helix Detects NTDS.dit Theft
By Adithya Chandra and Maulik Maheta · February 2, 2026
Executive summary
Active Directory serves as the central repository for an organization's authentication infrastructure. Malicious actors frequently focus on obtaining the NTDS.dit database file, which holds encrypted password data and essential domain configuration. Successful acquisition of this file can lead to complete organizational compromise.
This blog from the Trellix Advanced Research Center examines a security incident in which adversaries infiltrated a system, extracted the NTDS.dit database, and attempted to remove it from the environment while circumventing standard security measures. This analysis will dissect the adversary's methods for targeting the NTDS.dit file, tracing the full attack flow from initial access to data exfiltration. The blog concludes with robust, multi-stage detection and remediation strategies to contain the breach, and fortify Active Directory.
We'll examine how Trellix Helix identifies and links these activities using integrated threat intelligence and multi-source telemetry analysis. The platform's ability to connect endpoint, network anomalies, unauthorized movement across systems, and credential compromise attempts into a unified alert with comprehensive MITRE ATT&CK mapping proves essential for detection.
This analysis from the Trellix Advanced Research Center provides security professionals, SOC teams, and infrastructure defenders with practical insights into identity-focused attacks and the capabilities of the contemporary Trellix Helix platform for real-time detection.
Understanding the critical nature of NTDS.dit compromise
Within Windows domain infrastructures, Active Directory functions as the authentication and authorization backbone, controlling access rights and trust relationships across the organization. The NTDS.dit file (NT Directory Services Directory Information Tree) sits at the heart of this system.
This database file holds the domain's complete repository, including user credentials, policy configurations, system records, and critically, password hashes for every domain account, including high-privilege Domain Administrator accounts.
For threat actors, obtaining the NTDS.dit file provides complete visibility into the organization's identity infrastructure. Combined with the SYSTEM registry hive needed for decryption, adversaries can recover these hashes, perform offline password cracking, and assume any identity. Direct credential theft eliminates the need for social engineering or login attacks, providing unrestricted access.
The attack methodology proves remarkably covert. After achieving administrative control along with system-level privileges, adversaries typically leverage built-in utilities like vssadmin to generate Volume Shadow Copies, effectively circumventing file locking mechanisms. The NTDS.dit file is then retrieved (T1003.003), repaired using esentutl, and processed with credential extraction tools, including SecretsDump, Mimikatz, or basic file operations, often evading conventional detection systems. More detailed steps of the attack simulation are described in this NDR blog.
The severity stems not from simple data compromise, but from wholesale infrastructure identity theft. Trellix Helix addresses this challenge through cross-platform correlation of endpoint, network, and cloud telemetry, revealing the complete attack sequence that individual security solutions cannot detect.
Active Directory NTDS.dit extraction and exfiltration
Figure 1 illustrates the complete attack progression, spanning initial compromise through NTDS.dit extraction and attempted exfiltration, along with detection and mitigation opportunities. The diagram presents adversary tactics, techniques, and procedures alongside detection mechanisms, emphasizing critical vulnerability points.
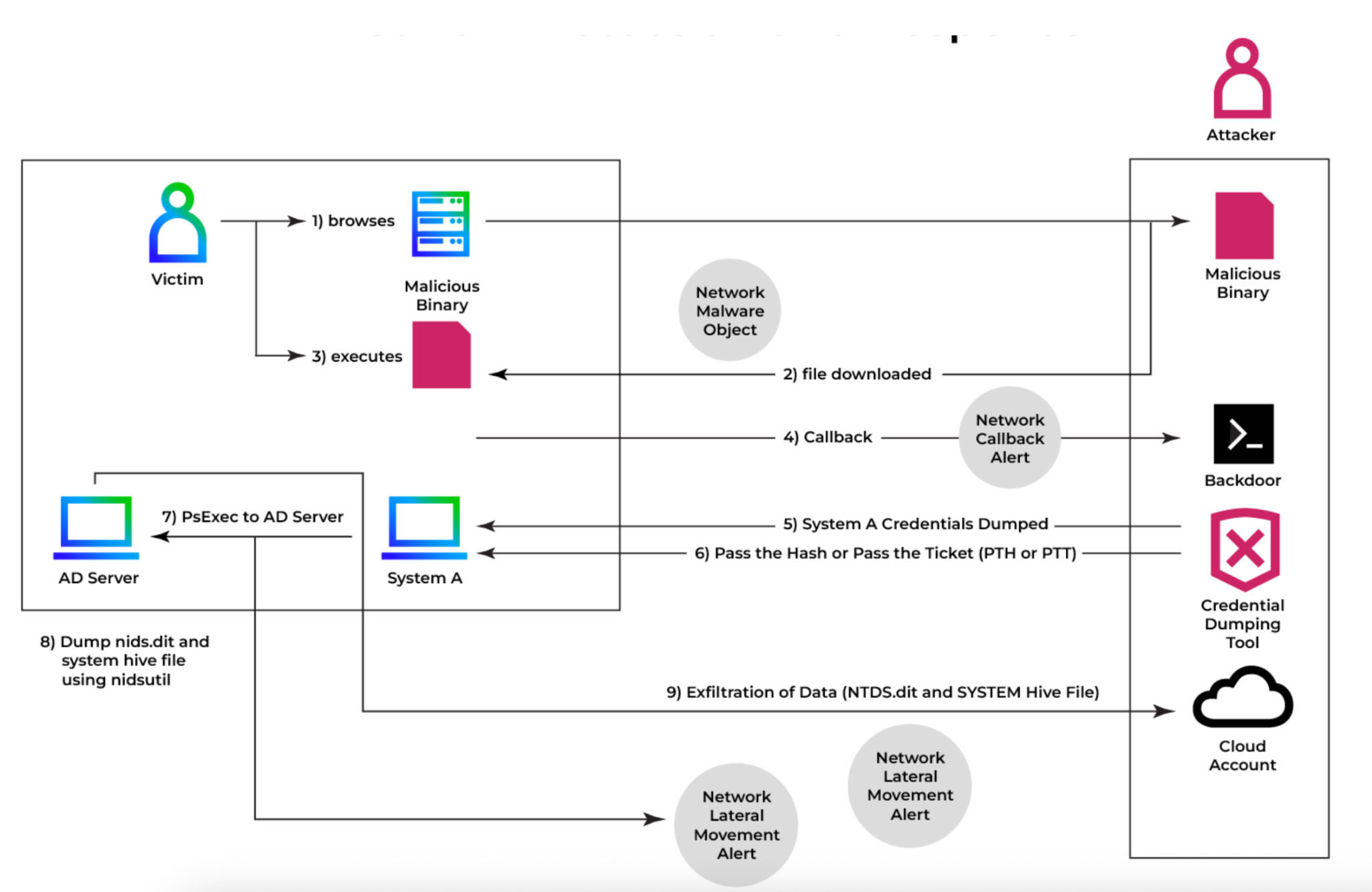
Detection: Trellix Helix
Trellix Helix detected and automatically correlated this multi-stage attack through its unified platform. Unlike traditional security solutions that generate isolated alerts, Helix brings together telemetry from Trellix Endpoint Security, Network Security, and other integrated products to create a single, high-fidelity alert that represents the complete attack story. This correlation dramatically reduces alert fatigue and provides security analysts with immediate context about the threat's scope and progression.
The platform automatically mapped the attacker's activities to the MITRE ATT&CK framework, enabling rapid understanding of tactics and techniques used throughout the attack chain. Please refer to Figure 2, which displays the primary alert generated by Trellix Helix for this incident.
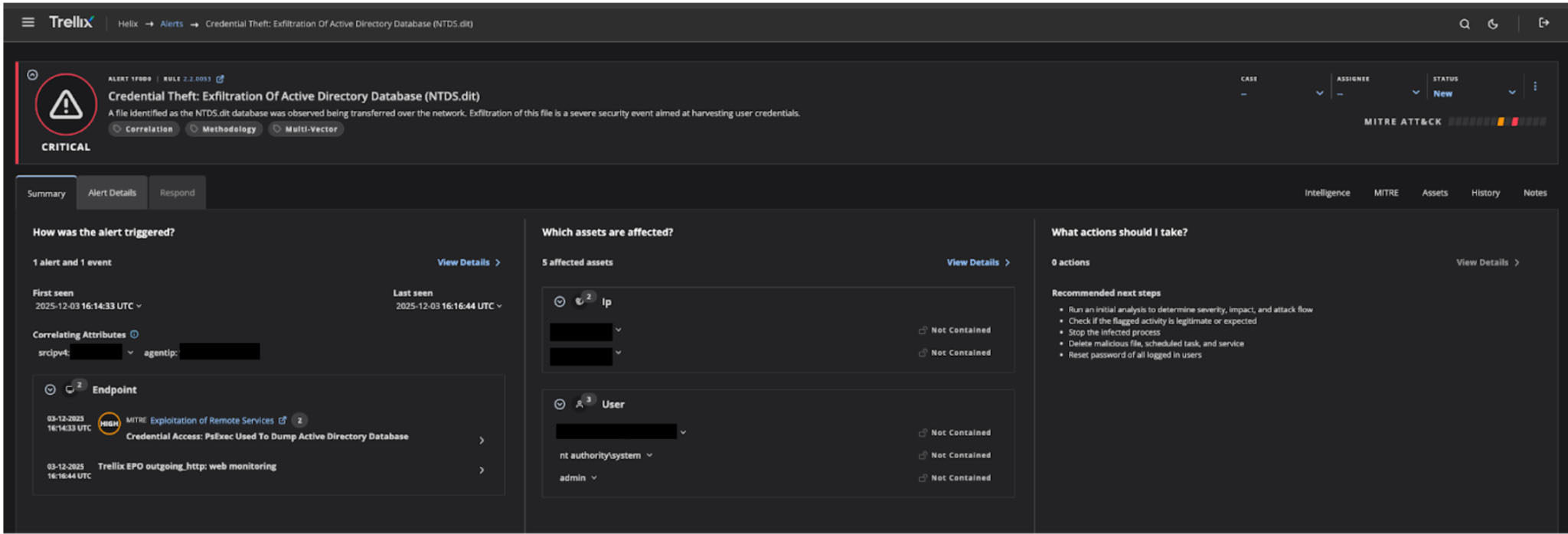
When Trellix Helix detects the exfiltration of an NTDS.dit file, it generates a CRITICAL severity alert that immediately draws attention to one of the most dangerous scenarios in enterprise security. The alert "Credential Theft: Exfiltration Of Active Directory Database (NTDS.dit)" signals that the Active Directory database file has been observed in transit across the network, a severe security event indicating an attacker's attempt to harvest domain credentials at scale.
Understanding the alert trigger
The detection mechanism correlates Endpoint telemetry with Network behavior and EPO events to identify this threat. In this instance, Trellix Helix identified an endpoint alert from Trellix Endpoint Security that mapped to the credential dumping activity [T1003.003]. The platform observed a remote PsExec session being leveraged to extract the Active Directory database file, a technique attackers commonly use to obtain password hashes for every account in the domain. The correlation engine links these related events through matching attributes, timestamps, and behavioral patterns to eliminate false positives and surface the complete attack narrative.
One of Helix's most valuable capabilities is its automatic asset inventory during an active incident. The platform immediately identifies which resources are involved in the attack across two critical categories: compromised IP addresses spanning multiple internal systems, and affected user accounts, including domain administrators, system-level credentials, and administrative users. The "Not Contained" status on these assets provides instant visibility into the scope of the breach, enabling security teams to prioritize containment efforts and understand the potential blast radius of the compromise.
Alert details and correlation timeline
Trellix Helix's Alert Details view (Figure 3) reveals the platform’s full investigative power. The interface displays comprehensive correlation across multiple detection sources, showing multiple alerts and events stitched together as the attack unfolded.
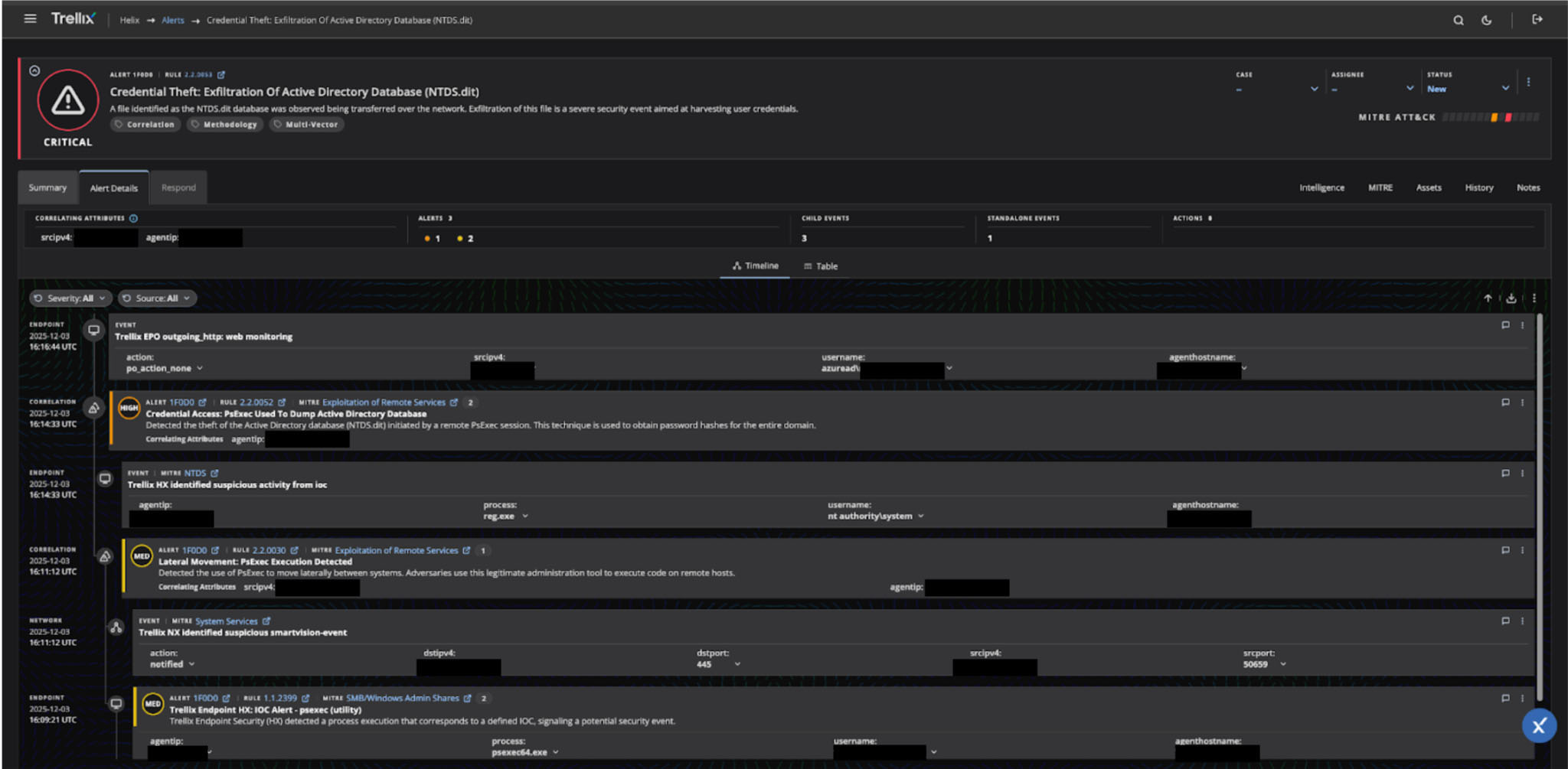
Trellix Helix's correlation engine pieced together a concerning story from multiple security signals across the network. It all started when the system noticed suspicious outgoing HTTP traffic from a workstation using a Domain Admin account, a potential sign that an attacker was preparing to send stolen data out of the network. Around the same time, the platform detected something far more serious: someone was using PsExec, a legitimate remote administration tool, to extract the Active Directory database file containing every user's password hash in the domain. The network intrusion system flagged unusual activity involving the registry tool on a Domain Controller, while lateral movement alerts showed the attacker hopping between systems using PsExec.
The pieces continued to fall into place as the correlation engine linked these events together through matching IP addresses and timestamps. Suspicious SMB file-sharing traffic appeared on port 445, and endpoint sensors caught the PsExec service spinning up on the target system under an admin account. What could have been six separate, confusing alerts suddenly became a clear picture: an attacker with stolen credentials was moving laterally across the network, dumping the crown jewels of Active Directory, and preparing to smuggle the data out. Trellix Helix automatically mapped each step to the MITRE ATT&CK framework, showing defenders exactly where they were in the attack chain and what needed to be stopped immediately.
The power of correlation
What makes Trellix Helix's detection so powerful is its ability to automatically correlate these distinct security events, spanning endpoint, network, and policy management layers into a single, coherent alert. Without this correlation, a SOC analyst would need to manually investigate six separate alerts, determine their relationships, and piece together the attack narrative. This process could take hours and risk missing the connection entirely.
Instead, Helix presents the complete story:
- Initial lateral movement using PsExec (Lateral Movement alert)
- Execution of credential dumping tools (Credential Access alert)
- Network-level detection of suspicious SMB and IOC activity (Network alerts)
- Endpoint detection of PsExec utility execution (Endpoint IOC alert)
- Outgoing communication potentially for exfiltration (EPO monitoring event)
Each detection point is enriched with MITRE ATT&CK context, showing which tactics and techniques align with known adversary behaviors. This enables analysts to quickly understand not just what happened, but how it fits into the broader landscape of threat intelligence.
Recommended next steps
Based on the Trellix Helix alert analysis, organizations should immediately take the following actions when this type of credential theft is detected:
- Immediate containment:
- Isolate affected systems identified in the alert from the network to prevent further lateral movement.
- Disable compromised user accounts, particularly domain administrator and privileged accounts.
- Block outbound connections from affected hosts to prevent exfiltration.
- Credential reset and rotation:
- Immediately reset passwords for all privileged accounts, especially Domain Admins.
- Reset the KRBTGT account password twice (with appropriate waiting period) to invalidate all Kerberos tickets.
- Enable multi-factor authentication (MFA) for all administrative accounts.
- Investigation and forensics:
- Review authentication logs for use of stolen credentials.
- Examine network logs for successful data exfiltration attempts.
- Analyze PsExec execution logs to identify all compromised systems.
- Review scheduled tasks and services for persistence mechanisms.
- System hardening:
- Restrict admin shares and disable unnecessary SMB access.
- Implement application whitelisting to prevent unauthorized tool execution.
- Deploy Credential Guard and remote Credential Guard on Windows systems.
- Monitor and restrict Volume Shadow Copy operations.
- Detection enhancement:
- Ensure Trellix Endpoint Security and Network Security are deployed across all critical assets.
- Enable advanced threat hunting rules in Trellix Helix.
- Configure automated response playbooks for credential theft scenarios.
- Establish baseline behavior profiles for administrative tools like PsExec.
- Long-term security improvements:
- Implement tiered administrative model to limit credential exposure.
- Deploy Privileged Access Workstations (PAWs) for domain administration.
- Enable Windows Defender Credential Guard.
- Regular security awareness training focusing on phishing and credential protection.
Conclusion
The theft of the NTDS.dit file is more than just a data breach; it is a complete loss of identity, trust, and control within a Windows domain. What makes this threat particularly dangerous is its stealth: attackers frequently use native tools, low-noise techniques, and encrypted exfiltration to avoid detection.
Traditional defenses, as demonstrated in this real-world attack chain, are prone to missing warning signs when security tools operate in isolation. However, Trellix Helix provides a cutting-edge approach that fundamentally changes the game. By automatically correlating detections from endpoint, network, and other security layers, Trellix Helix transforms dozens of low-fidelity alerts into a single, high-fidelity incident with full context.
The platform's integration of behavioral detection, MITRE ATT&CK mapping, automated correlation, and actionable response guidance enables security teams to solve the puzzle before it is too late. With Trellix Wise's AI-powered investigation capabilities, analysts can focus on strategic response rather than manual alert triage.
Product coverage
| Product | Signature / Suspicious Indicators |
| Trellix Helix | Credential Theft: Exfiltration Of Active Directory Database (NTDS.dit) Credential Access: PsExec Used To Dump Active Directory Database Lateral Movement: PsExec Execution Detected |
| Trellix NDR | Microsoft Windows NTDS.dit File Exfiltration Attempt Copy ntds.dit From The Volume Shadow Copy To Target Host Dump NTDS.dit and SYSTEM Hive File |
| Trellix EDR | Potential credential access attempt (NTDSUtil.exe executed via PsExec) Discovered unsecured credentials for AD exploitation Retrieve ntds.dit file from Domain Controller to extract password hashes Attempt to dump OS credentials via NTDSUtil.exe Created Volume Shadow Copy via vssadmin Dumped Domain Controller Hashes from Volume Shadow Copy Retrieved the Active Directory database from the Directory Service running on the Domain Controller Suspicious process accessed Active Directory database storage file (Ntds.dit) |
To learn more about the Trellix Helix platform, take our product tour to see it in action or visit this page.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
