Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Cyber Readiness & XDR: Progress, Challenges & Opportunities
By Trellix · May 13, 2022
As an industry leader focused on extended detection and response (XDR) solutions, Trellix pays particularly close attention to how the related technologies categorized as endpoint detection and response (EDR) and XDR are being implemented across the public and private sectors.
The Trellix Cyber Readiness Report released last week gauges the adoption of advanced cyber defense technologies and practices and the role of national government leadership overall among public and private organizations considered as critical infrastructure providers (CIPs). The impetus behind Trellix commissioning the survey behind the report was the U.S. Executive Order on Improving the Nation’s Cybersecurity (EO 14028), which required U.S. federal government agencies to implement EDR and XDR (EDR-XDR), as well as cloud cybersecurity modernization, multifactor authentication (MFA), zero trust architectures (ZTA) and software supply chain risk management policies and processes.
Trellix commissioned independent market research agency Vanson Bourne to survey 900 security professionals from organizations with 500 or more employees from government agencies (national government and armed forces) and critical infrastructure organizations (state and local government, government critical infrastructure, private critical infrastructure) in Australia, France, Germany, India, Japan, the United Kingdom and the United States.
Overall, the report found that EDR and XDR technologies are a priority among government agencies and critical infrastructure providers but they are difficult to implement. A lack of in-house cyber talent, a lack of implementation expertise, and a lack of trusted vendors were key barriers to the deployment of these and other technologies.”
This blog details these findings and suggests areas where Trellix and its partners might be able to better assist organizations in overcoming barriers to implementation.
Difficulty of Implementing EDR & XDR Solutions
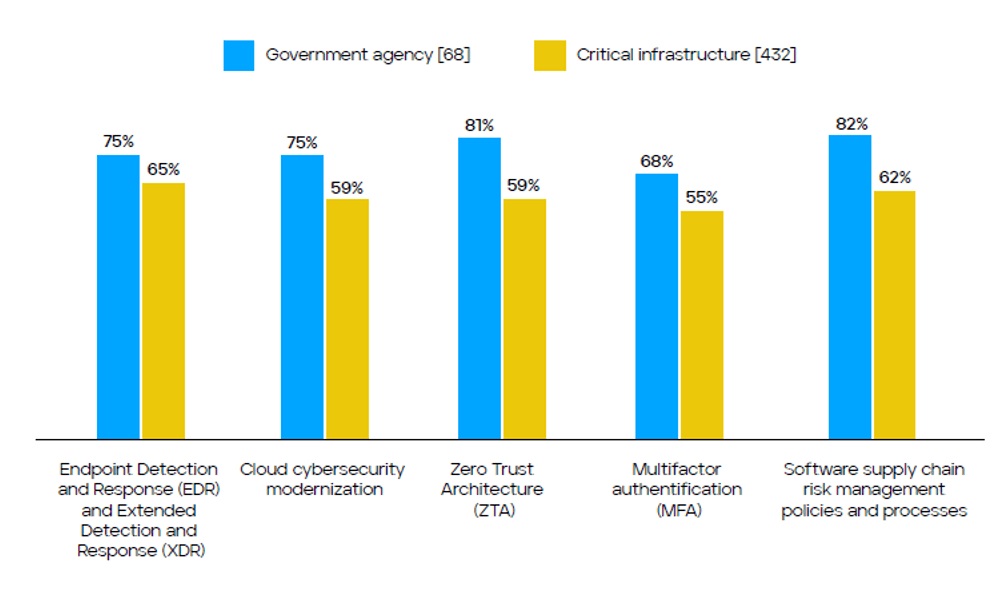
The report’s survey found that EDR and XDR are the most likely to be difficult for U.S. government agencies and CIPs. Seventy-five percent of U.S. government agency and 65 percent of U.S. CIP respondents reported that the EDR-XDR category of solutions involve a “high” to “extreme” level of difficulty to implement. Only zero trust and software supply chain risk management policies are more difficult to implement within the U.S. government, but no other category is more difficult than EDR-XDR among U.S. CIPs. Nearly two-thirds (64 percent) of U.S. state, tribal and local government respondents cite EDR-XDR solutions as difficult to implement.
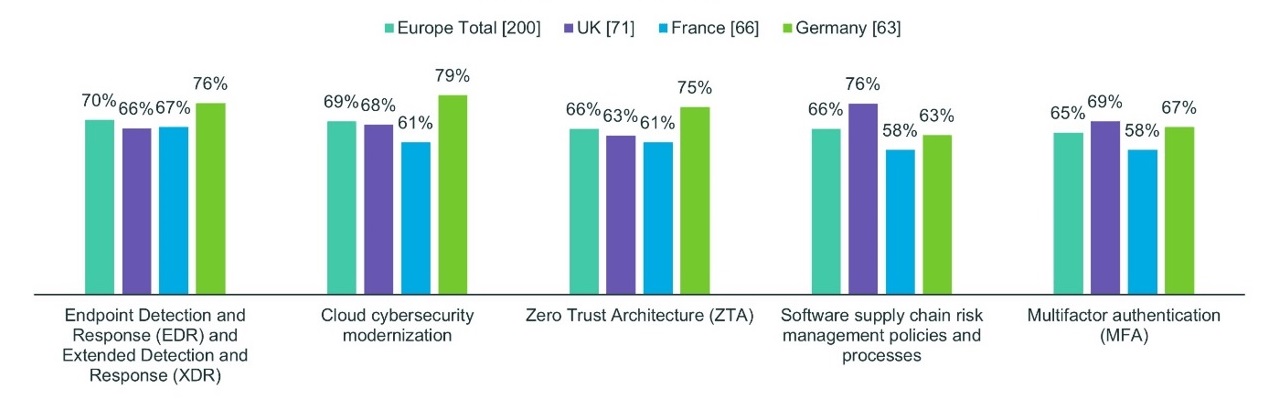
Across the Atlantic, 76 percent of German, 67 percent of French and 66 percent of British respondents found EDR and XDR difficult to implement.
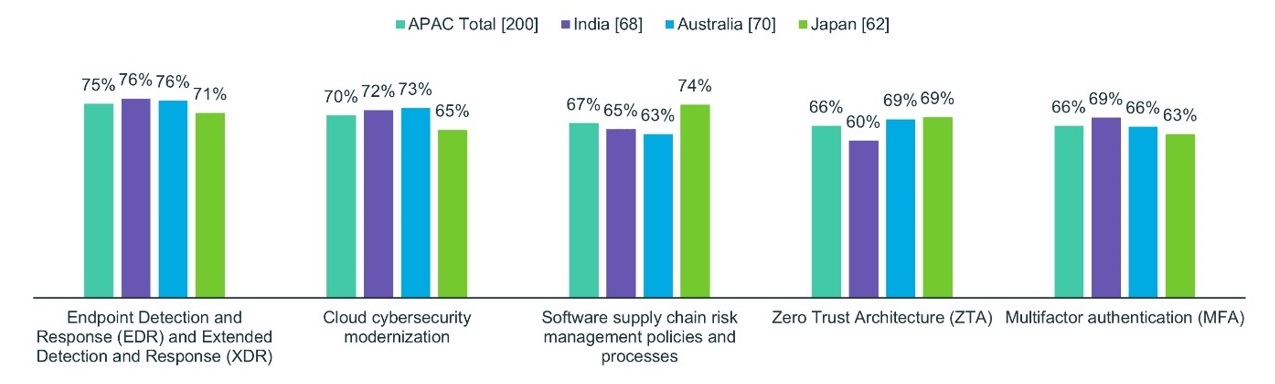
In Asia-Pacific, 76 percent of Indian and Australian respondents and 71 percent of Japanese surveyed identified EDR-XDR solutions as an extremely or highly difficult cybersecurity measure to implement..
Maturity of EDR-XDR Implementation
While as many as 84 percent of U.S. CIPs have “developed, implemented and deployed” some degree of EDR-XDR capabilities within their enterprises, only 35 percent of respondents report having full capabilities deployed. By comparison, 38 percent of U.S. government agency respondents report having fully implemented these capabilities. Among U.S. federal agencies, this places the category behind MFA and zero trust, at par with software supply chain processes, but ahead of only cloud modernization. Among U.S. CIPs, it appears to be lagging in maturity versus all categories save zero trust.
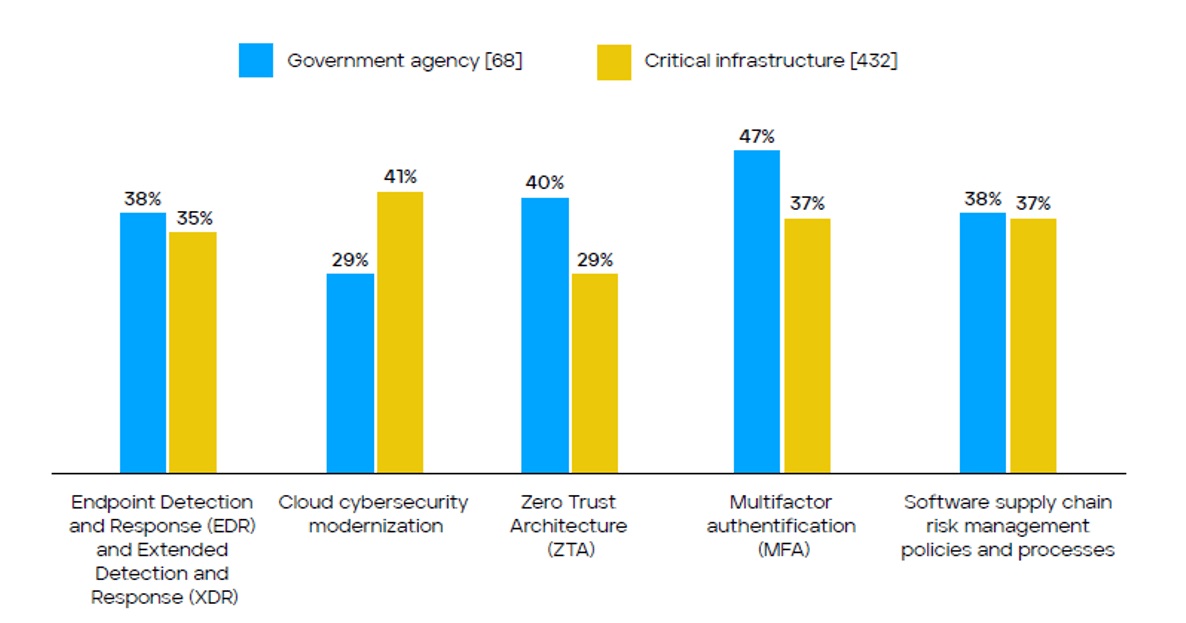
While the U.S. telecommunications sector respondents appear to slightly lead the overall U.S. CIP category in implementation with 41 percent reporting full capabilities, the overall U.S. CIP percentage of 35 percent is likely dragged down by segments such as U.S. state, tribal and local government services and healthcare services, where only 23 percent and 21 percent respectively claim to have achieved full implementation.
Among the British, EDR and XDR were the most mature new cyber defense solutions along with cloud cybersecurity modernization, with 37 percent of respondents claiming full deployment in each area. Thirty-five percent of French and 27 percent of German respondents reported full deployment of the technologies.
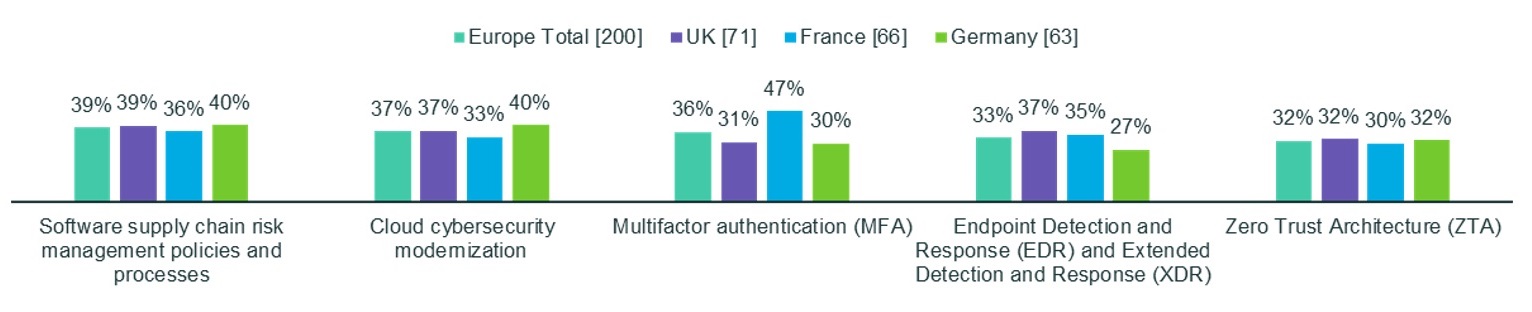
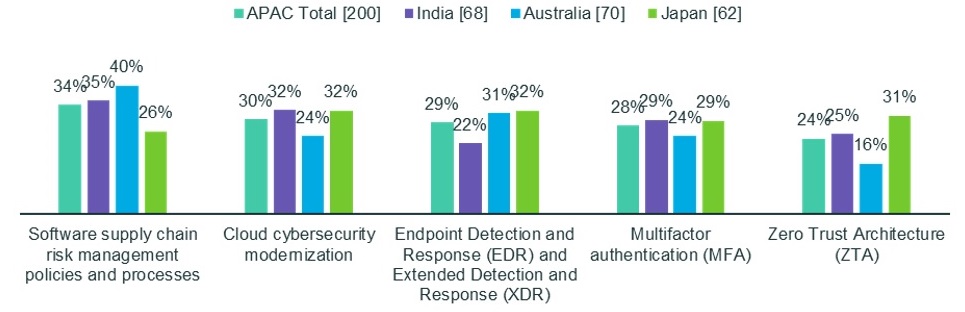
Only 32 percent of Japanese, 31 percent of Australian and 22 percent of Indian respondents report having fully implemented the technologies.
Barriers to EDR-XDR Implementation
While the global survey behind the Cyber Readiness Report did not assess the difficulties specifically associated with EDR-XDR, some notable themes emerged across solution categories.
While U.S. federal agencies identified implementation barriers such as a difficult tender and bidding processes and budget constraints, 75 percent of federal respondents anticipate using the Cyber EO as justification to obtain the necessary funding to overcome these challenges and meet their objectives.
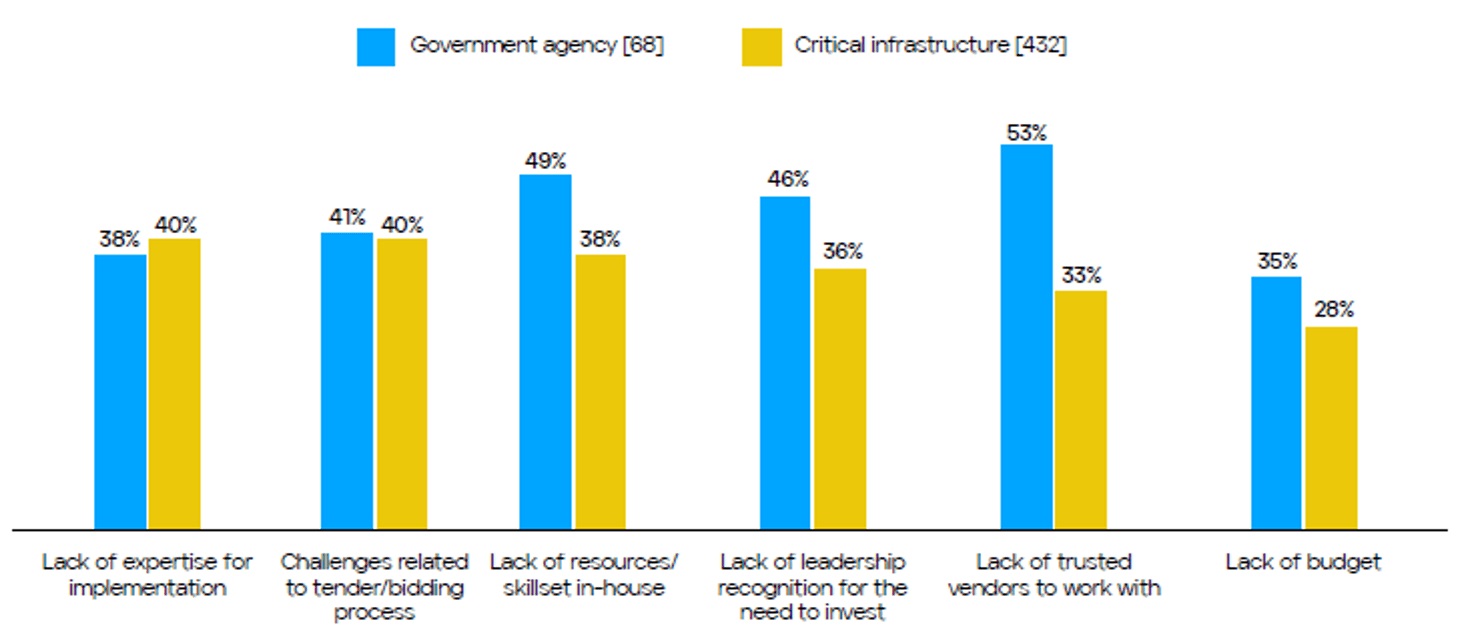
Another challenge reported is the lack of trusted solution vendor entities available to work with them, noted by 53 percent of U.S. federal and 33 percent of U.S. CIP respondents.
Even more concerning are the challenges related to the all too familiar cyber workforce gap, specifically the lack of in-house staffing resources, skill sets and solutions implementation expertise. These in-house cyber skills issues were not only reported by 49 percent of U.S. government agencies, but in sectors such as the U.S. oil and gas sector (55 percent) and U.S. state, tribal and local governments (51 percent).
Beyond just skilled headcount shortages in-house, 35 percent of U.S. federal respondents and 40 percent of U.S. CIP respondents reported a lack of expertise or experience in implementing and managing advanced solutions such as EDR and XDR.
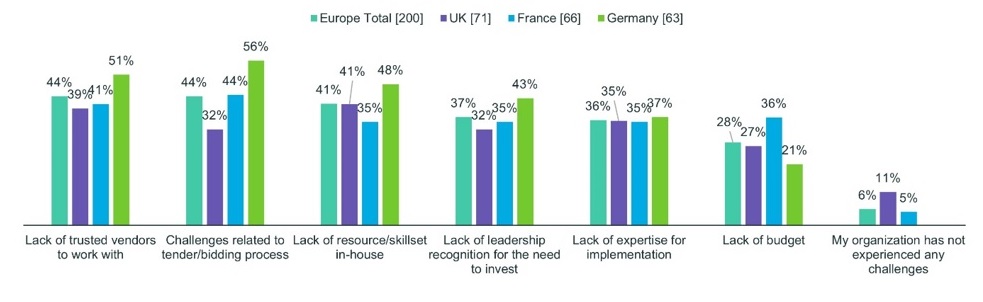
In Europe, 48 percent of German, 41 percent of British and 35 percent of French respondents reported a lack of skilled staff resources in-house. Thirty-seven percent of German, 35 percent of British and 35 percent of French respondents reported shortages in implementation expertise. Fifty-one percent of German, 41 percent of French and 39 percent of British respondents reported a lack of trusted vendor partners to implement the solutions.
Sixty percent of Indian, 45 percent of Japanese and 36 percent of Australian respondents identified implementation expertise as a challenge. Forty-nine percent of Australian, 42 percent of Japanese and 37 percent of Indian respondents reported a lack of cyber-skilled staff in-house. While not as prominent an issue as in the U.S. and Europe, 49 percent of Indian, 39 percent of Australians and 26 percent of Japanese reported a lack of sufficient vendor partners.
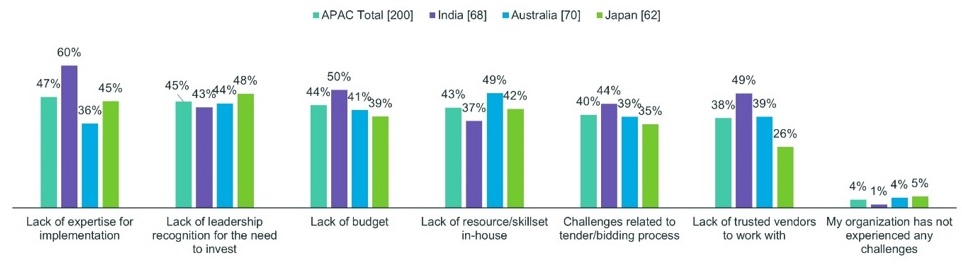
The cyber skills and experience gap findings imply that even if governments and corporations are willing and able to spend whatever it takes to acquire and implement the latest cyber defenses, there simply are not enough cybersecurity professionals with the skills and required expertise in-house to implement and run them.
Similarly, there is a lack of trusted vendors capable of sufficiently meeting organizations’ needs to not only provide, implement and support these technologies effectively.
What Is Needed to Progress
The issue of addressing the cyber talent shortage—shortages of skilled staff and the shallow expertise of the staff we have—are issues on which both government and the private sector will have to team to address in a serious way, and over time.
But it is also clear organizations need EDR-XDR platforms possessing the capabilities to overcome skills and expertise shortages, the flexibility and openness to ease their integrations and the solution vendor and channel integration partnerships that can help them implement these cyber defenses. These realities are particularly relevant as organizations increasingly realize that they must move their current and planned implementations beyond EDR to the XDR paradigm, which combines a wider variety of solutions.
Trellix’s native and open XDR platform supports organizations’ desires for ease of implementation as complicated integrations are helped along by open standards, interoperability and the deep integrations they enable. This is particularly important in the area of XDR where multiple information sources must be streamlined together to inform security operations.
With over 650 third-party solution integrations and hundreds of partners, Trellix provides an open platform that evolves and supports whatever technical integrations customers require within their implementations. When you combine XDR and an open security ecosystem for XDR capabilities, agencies and businesses will have a solid foundation to advance their visibility and detection capabilities across their entire cyber infrastructure.
Trellix provides native integrations and open API partners for telemetry data exchanges, plus native connections for security policy orchestration across a broad portfolio of owned security products, providing maximum visibility, control and vendor choice across all attack surfaces. This includes security information and event management (SIEM) integrations with more than 36 partners and security orchestration automation and response (SOAR) integrations with more than 150 third-party tools and data sources for seamless management.
Please visit our partners page to learn more about Trellix’s extensive third-party partner ecosystem.
For more information on the Trellix Cyber Readiness Report:
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.