In The Nation-State Crosshairs: Australia, India & Japan
By Trellix · March 28, 2022
Today Trellix and the Center for Strategic and International Studies (CSIS) released a global report, In the Crosshairs: Organizations and Nation-State Cyber Threats, examining security professionals’ mindsets towards nation-state actors, the extent to which they are being targeted, how these state actors differ from cybercriminals and what the role of government should be in confronting these threats. The report, written by CSIS and based on research conducted by Vanson Bourne, surveyed 800 IT decisions makers in Australia, France, Germany, India, Japan, the United Kingdom and the United States.
This blog highlights the survey findings for the Asia Pacific nations of Australia, India and Japan.
Perceptions of Nation-State Threats
The Vanson Bourne survey asked participants if they suspected having ever been targeted by a cyber-attack by a nation-state or a threat actor group acting on behalf of a nation-state. There are always challenges in cyber-attack attribution, and Trellix has long advised technical evidence of cyber-attacks be complemented with traditional intelligence before attribution can be reliably established. The adversary behind an attack could be a nation-state, a ransomware gang, a hacktivist group, or one of these masquerading as another in an effort to enjoy plausible deniability (or enhance their profile) should the campaign be exposed and investigated.
Globally, 86 percent of respondents believed they have been targeted by a cyber-attack by an organization acting on behalf of a nation-state. Ninety-seven percent of Australian survey participants were somewhat to highly confident they have been targeted by a threat actor working on behalf of a nation-state. Eighty-three percent of Indians and 82 percent of the Japanese respondents believed the same. Sixty percent of the Australians believed it “highly likely” they were targeted—exhibiting more confidence than any other nationality among the seven countries surveyed.
Ninety-one percent of Australian respondents were confident their organization was the target of a nation-state in the last 18 months, compared to 76 percent of Indian and 71 percent of Japanese participants.
Of these respondents, the survey attempted to quantify how many attacks had been detected. Twenty-one percent of Australian respondents reported being the target of three cyber-attacks over the previous 18 months. This is the highest “three attack” count among the three Asia Pacific countries surveyed. Forty-two percent reported two attacks, 31 percent one attack and only 1 percent reported four or more attacks.
Fifty-nine percent of Indians surveyed reported being the target of two attacks the previous 18 months. Twenty-nine percent reported one attack, only 9 percent reported three attacks and only 1 percent reported four or more attacks.
Among the Japanese surveyed, 44 percent reported being the target of two attacks the previous 18 months. Thirty-seven percent reported being the target of one attack, 18 percent reported three attacks and only 1 percent reported four or more attacks.
Know Thy Enemy
Ninety percent of Indian respondents, 86 percent of Australians and 77 percent of Japanese surveyed believed nation-states are working through cybercriminal groups to acquire tools, techniques and even their services to execute their cyber campaigns.
Based on the information assets targeted within their organizations, their industry role and country of origin, survey participants were asked which nation-state actors they suspected were most likely to have targeted them in the past.
Half of Indian respondents suspected China, 29 percent North Korea, 26 percent Russia, 25 percent unknown western governments and 22 percent Iran.
Forty-four percent of Japanese respondents suspected the Russians, 41 percent the Chinese and 37 percent the North Koreans.
Forty-seven percent of Australians suspected the Russians, followed by the Chinese (46 percent), North Koreans (36 percent) and Iran (35 percent).
Among Japanese survey respondents, 70 percent identified Russia as the most likely actors to target them in the future. Sixty-five percent anticipated the Chinese and 55 percent the North Koreans.
Sixty percent of Indian participants foresee China as a future leading threat, compared to 27 percent for unknown western governments and 20 percent for Russia.
Forty-three percent of Australians view China as the most likely adversary, compared to 14 percent for Russia, North Korea, western governments and Iran.
While the Indians were on balance more confident than their peers in their ability to know the difference between state and non-state actors, only 43 percent had “complete confidence” and 37 percent had a “high level of confidence”. Forty-eight percent of the Australians and 50 percent of the Japanese had “very little” confidence.
What Makes A Good Target
Vanson Bourne asked survey participants what they believed the motivations were for the adversaries targeting them.
Fifty-nine percent of Indian survey respondents believed the actors’ objective is access to business or government confidential information. Forty-seven percent believed intellectual property (IP) theft is the lure. The Indians also identified other objectives, including access to consumer or citizen data (45 percent), sabotage or disruption of services (41 percent) and coercion intended to force them to make unwanted business decisions (41 percent).
Among the Japanese surveyed, 54 percent believed the prize within their enterprises is access to government and business confidential information, compared to 41 percent for damage to organizational reputation, 38 percent for IP theft and 30 percent for sabotage or disruption of services.
Among Australians, 47 percent viewed access to consumer or citizen data as a lure, followed by access to confidential government and business information (42 percent), coercion to influence business decisions (41 percent), financial gain (37 percent), IP theft (37 percent) and sabotage or disruption of services (33 percent).
When asked whether they thought the cyber-attacks targeting their organizations were unique attacks or part of a larger campaign targeting multiple organizations, 57 percent of Indian, 56 percent of Australian and 55 percent of Japanese respondents believe they were targeted by unique attacks.
When asked which factors make them particularly vulnerable to nation-state actors, respondents interestingly did not identify lack of cybersecurity budget or low awareness of the problem.
The Japanese identified the lack of cyber hygiene across their organizations (47 percent), followed by cyber skills deficits (43 percent), and legacy cyber tools (35 percent).
The Indian respondents identified cyber outdated tools (48 percent), then cyber skills (44 percent), lack of sector collaboration (42 percent), lack of collaboration with government (39 percent), and lack of cyber hygiene (36 percent).
The Australians identified the cyber skills shortage and lack of sector cooperation (both at 40 percent), and then outdated cyber tools and poor hygiene (both at 35 percent).
Perceived Impact of Attacks
The survey also gauged the perceived impact of suspected nation-state attacks. Sixty percent of Indian respondents experienced data exposure, 55 percent of Japanese experienced data loss, and 52 percent of Australians experienced both data loss and data exposure.
Half of Japanese survey participants acknowledged attacks on business operations data, as well as attacks on consumer and citizen data (48 percent), IP (33 percent) and business strategy information (31 percent).
Fifty-three percent of Indian participants reported attacks on consumer and citizen data, as well as attacks on IP (47 percent), operational data (40 percent), business strategy information (38 percent) and financial data (36 percent).
Forty-two percent of Australian respondents reported attacks on business process data, as well as business strategy documents (35 percent), consumer and citizen data (33 percent) and IP (31 percent).
When asked to estimate the total financial impact sustained as a result of a successful nation-state cyber-attack, overall impact across all seven countries’ respondents was $1.6 million. U.S. respondents reported $1.8 million. Indian respondents estimated the highest cost at $2.3 million, compared to $1.6 million among the Australians and $1.2 million among the Japanese.
What is significant about the survey’s findings on financial impact is that the numbers are specific to suspected nation-state attacks (versus that of general or cybercrime attacks).
To Disclose, or Not Disclose
Vanson Bourne also asked survey participants what details they did not disclose publicly. Among the Japanese, 40 percent said they did not identify the data affected or the enterprise weaknesses that made the incident possible, the financial cost to the organization (35 percent) or mistakes by the staff that made it possible (26 percent).
As many as 59 percent of the Indians admitted withholding details on the weaknesses in their enterprise infrastructure that made the incidents possible. Forty-four percent did not share their suspicions on which nation-state actors was involved, 41 percent did not disclose the financial costs of the incident, and 37 percent chose not to share information on the data affected of the mistakes the staff made.
Australian respondents were most resistant to disclosing the financial costs to the organization (45 percent), followed by the data affected (42 percent), weaknesses in the network (39 percent) and the length of time the organization was exposed to the threat (33 percent).
But, from the perspective of preparing industries for future attacks, the lack of corporate transparency in reporting the details of attacks makes it difficult for organizations to learn from their collective experiences with nation-state attacks.
National governments can play a constructive role in this area with incident reporting liability protection policies and public-private partnerships that anonymize the sharing of cyber-attack data. In this way, governments can foster greater understanding of these sophisticated attacks, the actors behind them, and the development of not only best practices in cyber defense and risk management, but also in the key area of critical incident response.
Working with National Governments
The report reveals a sentiment that private organizations feel outmatched by highly resourced, highly sophisticated nation-state actors or proxies working on their behalf. They are not entirely sure how to go about fending off this daunting threat and they look to government for guidance and support.
When asked whether national governments should do more to support organizations in defending them against nation-state cyber-attacks, 96 percent of Japanese, 94 percent of Indian, and 90 percent of Australian respondents agreed.
The survey also asked if they have partnered or would partner with their national government’s law enforcement authorities as a result of being targeted by a nation-state attack.
Sixty-nine percent of Indians, 68 percent of Australians and 65 percent of Japanese respondents said they have or would contact these authorities due to government requirements. This suggests that some aspects of public-private collaboration may have to be mandated for the defense of the nation.
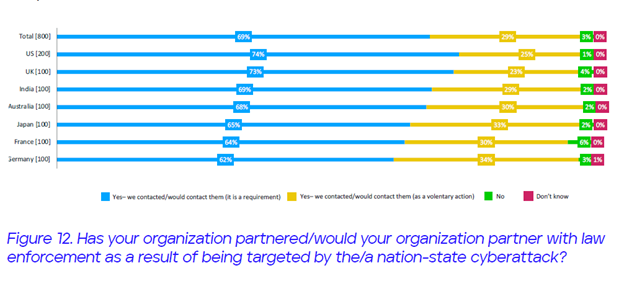
Sixty-two percent of Indians and 48 percent of Australians surveyed would like their national government to provide provision of real-time, machine-based threat intelligence. Fifty-nine percent of Indians and 51 percent of Japanese surveyed favor government support their efforts to acquire additional cyber-skilled staff.
As these nation-state attacks continue to grow in number and severity, we believe it quite likely that organizations will be more likely to work more closely with their national government law enforcement community. The question that remains open is how well they will work together moving forward absent a national cyber catastrophe that forces greater cooperation.
Countering Nation-State Threats
The CSIS report proposes six areas of focus for private sector organizations seeking to better protect themselves from nation-state actors:
Cyber hygiene is critical
Incidents like SolarWinds showed that the absence of basic measures will greatly increase risk. These measures include routine patching and updating (even though there is a degree of “patch fatigue”), maintaining logs, using encryption for sensitive data and requiring multifactor authentication for all users. Easily implemented actions like these would go far in reducing an attacker’s chance of success.
Update defense capabilities
The success of nation-state cyber-attacks is often linked to lack of cybersecurity skills and the use of outdated IT infrastructure or cybersecurity tools. With threat actors’ tools and techniques growing more sophisticated, there is a real need for organizations to modernize and improve their defenses at a similar (or faster) rate.
Identify what needs to be protected
Data is one of the most valuable assets that nation-states usually want. If the intent behind most state-backed attacks is to acquire information on customers or staff, organizations need to take extra steps to ensure the security of this data and build resilience in their use of it. In an ever-expansive threat environment, identifying high- and low-priority data targets should guide internal cybersecurity planning and processes.
Assess actual capacity
An interesting insight from the survey data is the dissonance, in some cases, between a respondent’s assessment of their capacity and the actual implementation of that capability. For instance, while many expressed high confidence in their ability to conduct successful attribution without assistance, other results reveal most organizations rely on external assistance to identify a perpetrator. An overestimation or misunderstanding of actual technical capacity could lead to increased vulnerabilities and inefficient processes or solutions.
Review third-party service providers
Incidents such as the SolarWinds and Microsoft Hafnium illustrate that the targeting of IT service providers is a trend for nation-state actors. This allows state actors to gain access to multiple victims by only targeting one provider. Unfortunately, the exploitation of third-party service providers is not a new threat — all of which makes it more concerning and suggests that as a reliance on things like software-as-a-service (SaaS) and similar services implies a necessity for an additional level of effort in defense.
Increase communication to address threats
Communication between the public and private sectors is crucial to face state-backed threats. Governments can provide advice and information that identify both specific threats and vulnerabilities as well as broader trends, and notify companies of developments, but this can only be improved if there is sufficient information sharing from the private sector to ensure the government is up to speed on the threat environment.
For Historical Perspective on Cyber Activity in Asia Pacific
In closing, the Center for Strategic and International Studies (CSIS) maintains a timeline of cyber incidents thought to be instigated directly or indirectly by nation-state actors. This includes attacks on targets in Australia, India, Japan and the rest of the Asia Pacific region.
The 67-page list noting incidents going back to the early 2000s dramatically illustrates that nation-state activity is by no means a new development and should by no means be downplayed or minimized as a threat.
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.