Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Ongoing Saga of Job-Themed Attacks
By Daksh Kapur and Alfred Alvarado · January 23, 2024

(Attribution at the Bottom)
In late 2023, Trellix Security Researchers identified an ongoing trend where cybercriminals exploit job-themed attack vectors to target both job seekers and employers. Near the start of 2023, we released a comprehensive research report on similar campaigns, which you can explore here.
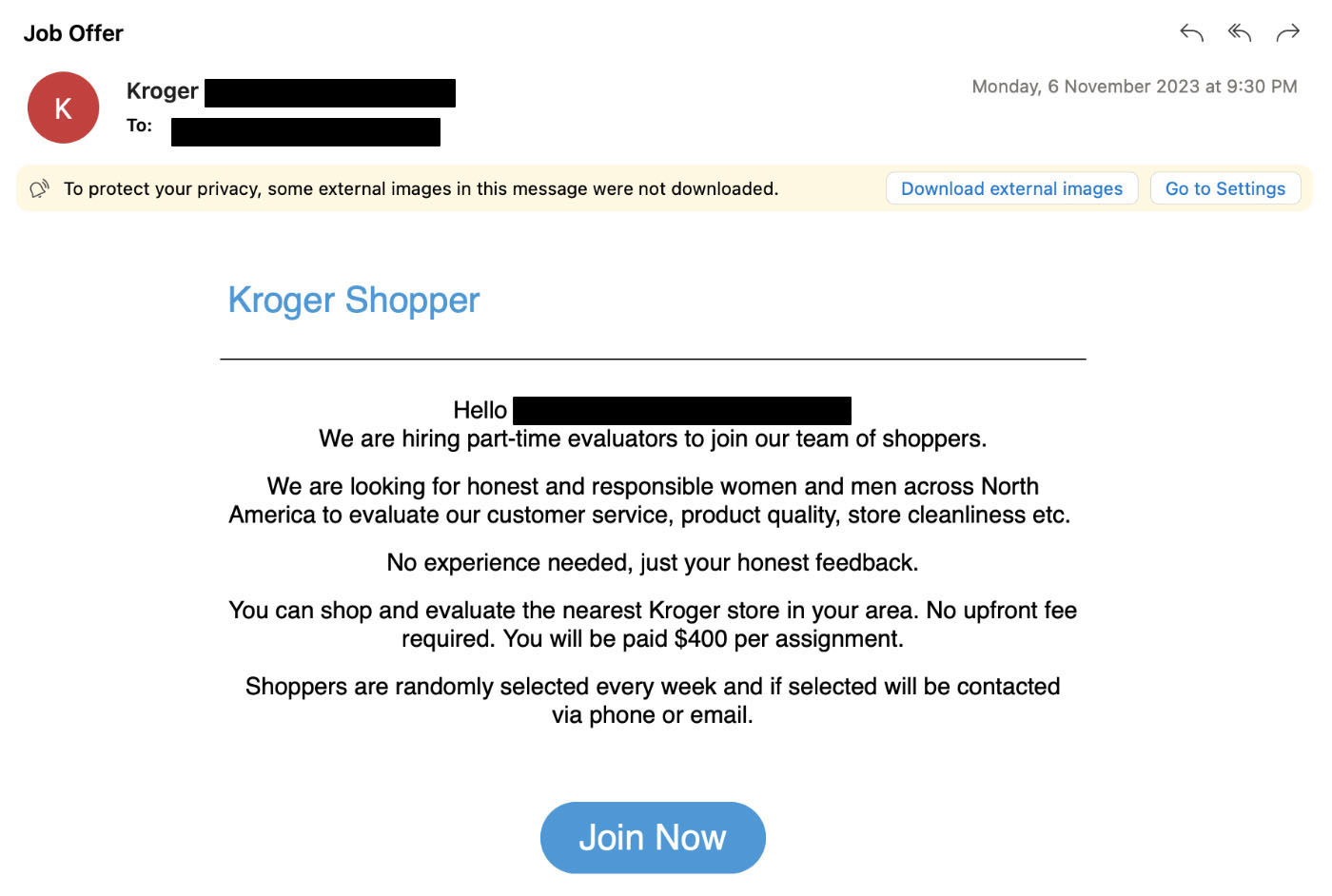
Cyber attackers have been employing tactics to entice job seekers through deceptive job availability emails while simultaneously targeting employers with malicious emails disguised as job applications. In the midst of a persistently challenging job market characterized by widespread layoffs, opportunistic attackers are capitalizing on the situation to launch attacks.
The intent behind these attacks is multifaceted: deploying malware, stealing credentials, and extracting sensitive information. Moreover, cybercriminals may utilize generic contact details as part of a social engineering strategy, setting the stage for further scams.
Most Targeted Regions
Our researchers have observed a substantial portion of job-themed attacks, with Australia accounting for 41% of the total attacks, closely followed by the United States at 29%. This highlights a notable trend in job-themed attacks predominantly targeting these two countries.
Malicious emails
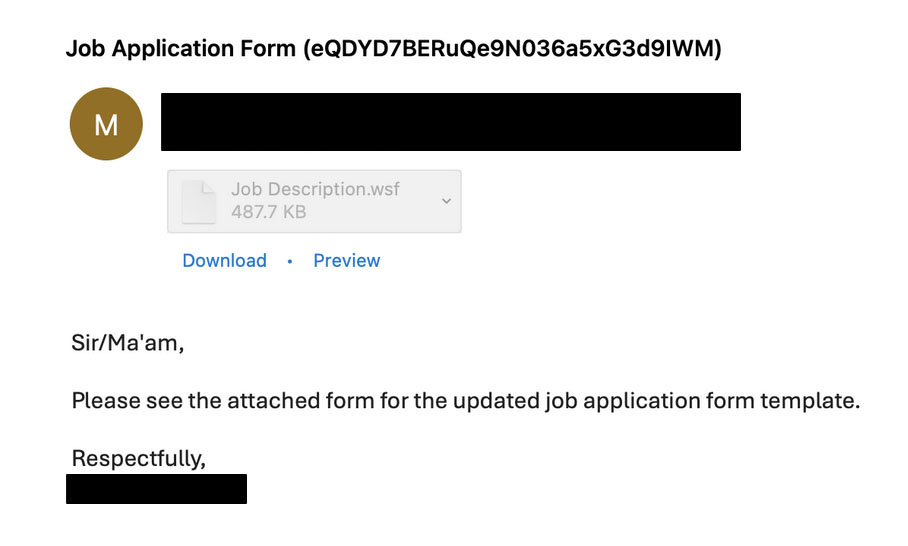
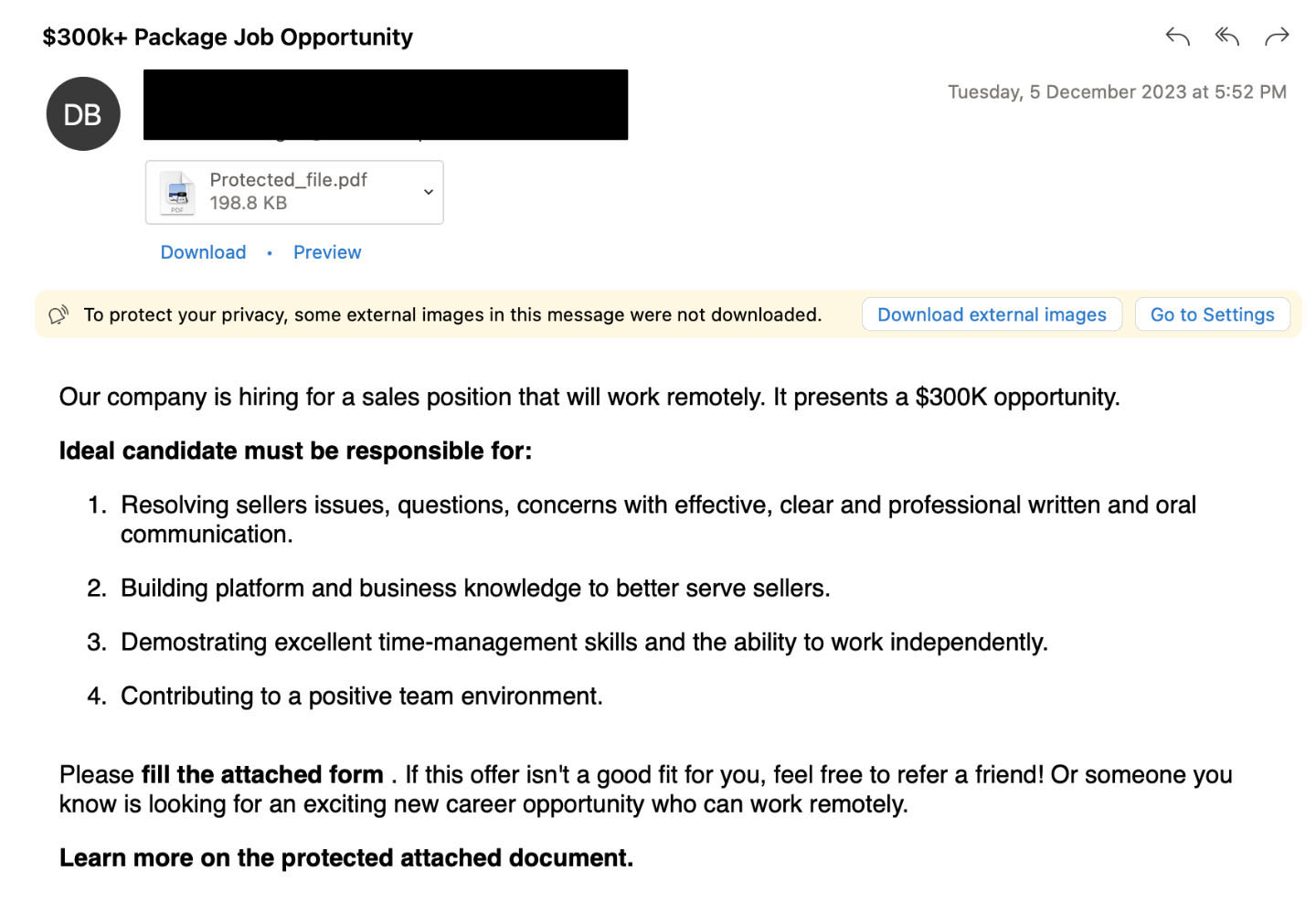
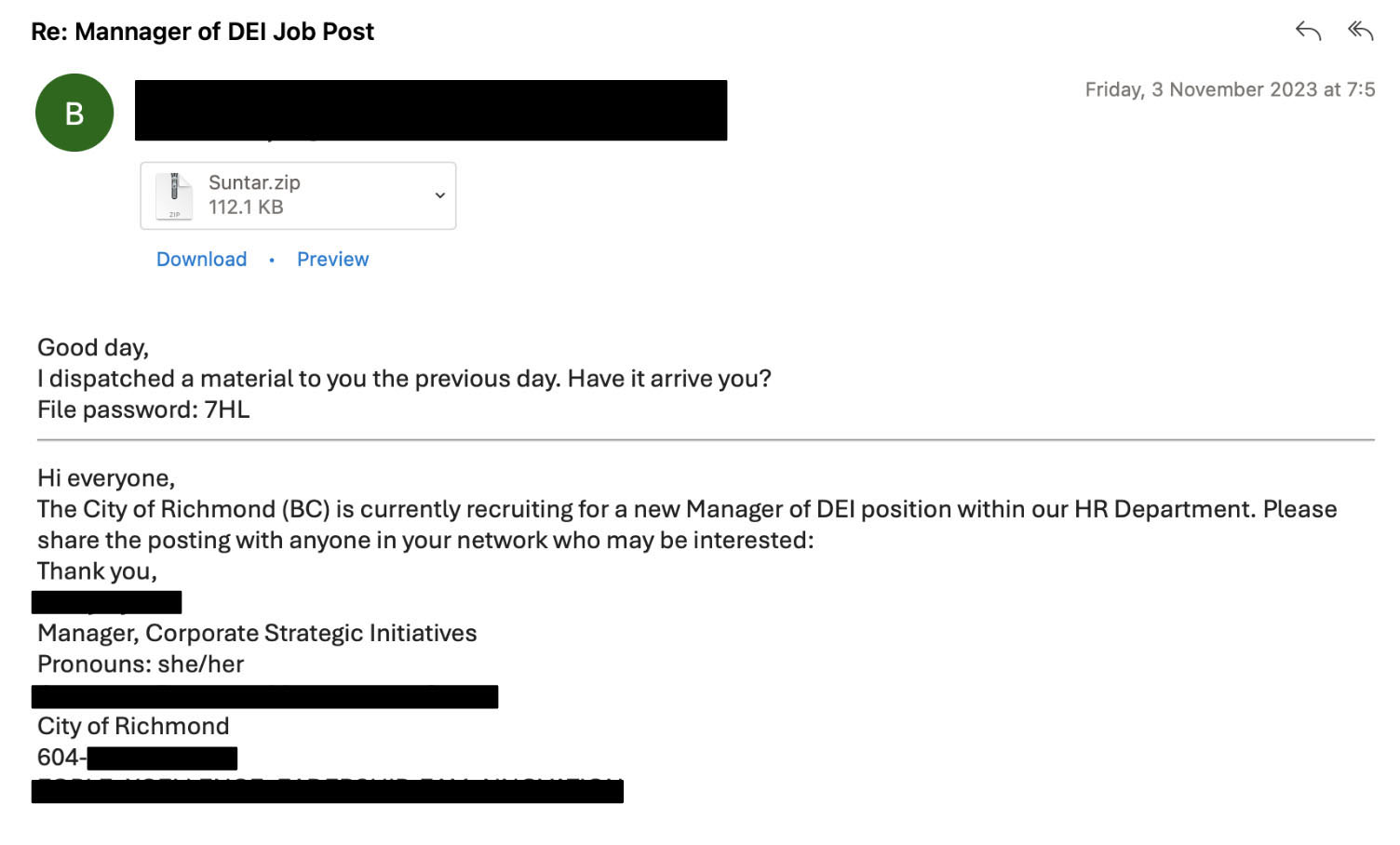
Trellix Email Security researchers have identified various iterations of emails employed in job-themed attacks. Additionally, attackers have been observed using password-protected attachments as a tactic to bypass detection mechanisms.
Malicious URLs
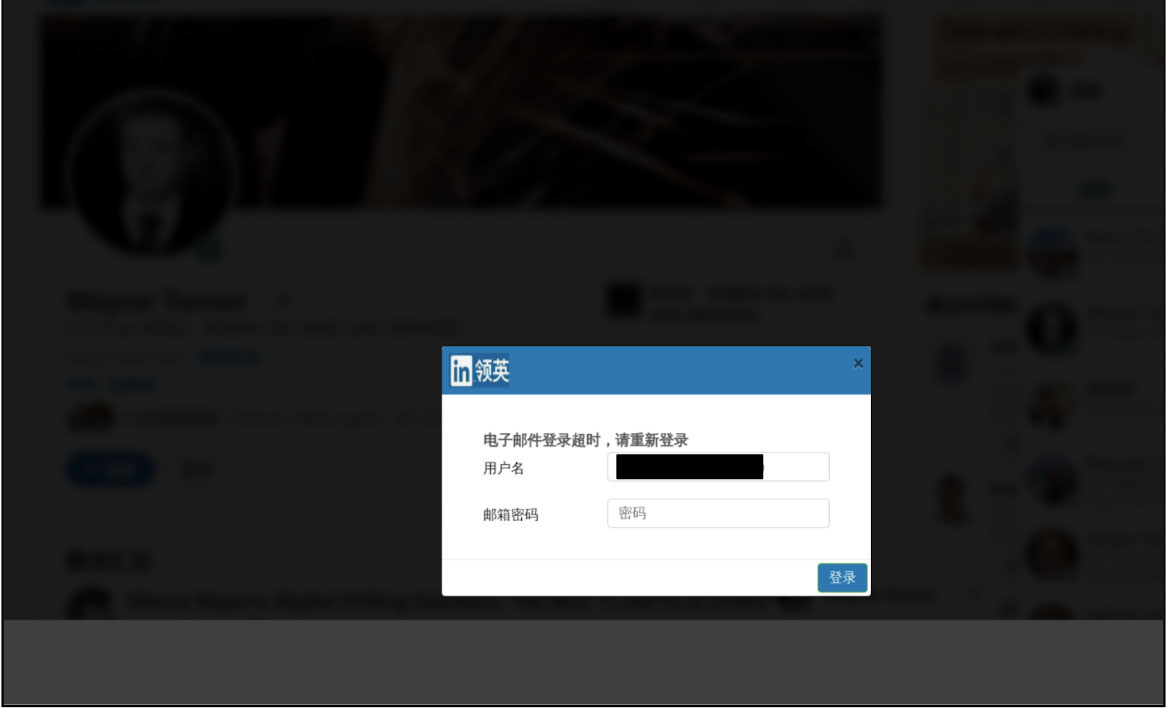
Our researchers have identified various malicious pages, including but not limited to credential phishing. These pages impersonate job applications, coercing victims to provide personal information like name, phone number, address, etc. Attackers are suspected of using this data to conduct financial scams, utilizing job opportunities as bait.
Malware
Trellix identified several malware families targeting job seekers and employers. The following are some of the malware families observed by our researchers:
Recent Player Taking The Field:
- Tracked as TA4577 (ProofPoint)
- TA4557 is a financially motivated threat group that was first identified in late 2023. Primarily targeting recruiters through sophisticated social engineering tactics. Initially focusing on responding to job listings on job boards, the threat actors later shifted to targeting recruiters directly. Setting their play in motion by sending benign-looking emails, expressing interest in an open position, once the recipient responded the next phase was activated.
- TA4557 is known for distributing the More_Eggs backdoor, a malware that establishes persistence, gathers intel from the respective environment, and awaits commands to deploy additional payloads. This highlights the strategic blend of direct human targeting, advanced malware deployment and the evolving nature of cyber threats from financially driven actors.
- TA4557 Overview: A financially motivated group active since at least October 2023.
- Target Audience: Specifically targets recruiters through direct email campaigns.
- Initial Contact: Benign emails expressing interest in open positions to build trust.
- Malware Distribution: Known for deploying More_Eggs backdoor.
- Attack Chain: The attack chain starts when the recruiter responds to the initial email.
- Tactics Shift 2022-2023: Initially replied to job listings on third-party boards, then shifted to directly targeting recruiters.
- Method of Attack: Fake resume websites and email attachments that lead targets to download malicious files.
- Key Strategy: Combine human targeting with malware deployment.
Other Malware:
- Agent Tesla – A .NET-based Remote Access Trojan (RAT) and data stealer for gaining initial access that is often used for Malware-as-a-Service (MaaS).
- Formbook - An info stealer malware used to steal several types of data from infected systems, including credentials cached in web browsers, screenshots, and keystrokes. It can also act as a downloader, enabling it to download and execute additional malicious files.
- TerraLoader - A backdoor malware, infiltrates systems via malicious files or downloads, enabling attacks like credential theft and file encryption. In another case mentioned in this article by itbrew.com, TerraLoader posed as job application resumes, showcasing its deceptive delivery tactics.
- Pikabot - A malware with advanced evasion techniques, anti-debugging inspired by Al-Khaser, and steganography for payload concealment. It operates on a proprietary C2 framework, supporting commands like host enumeration and secondary payload injection.
- More_Eggs Backdoor - developed in JavaScript, offers covert access to compromised hosts. Other capabilities include downloading additional payloads, evading detection by imitating legitimate software, and its modular architecture that is customizable to specific targets.
Indicators of Compromise (IOC)
Check out the list of indicators of compromise from the recent Job Themed campaigns observed by the Trellix Advanced Research Center: Job Themed Campaigns IOCs.
Trellix Product Protections
Trellix’s XDR solution offers thorough defense against threats like typo-squatting domains and malicious job application emails. Employing a multi-layered strategy, it examines URLs, emails, networks, and attachments to identify and block risks effectively. Trellix’s portfolio of products maintains vigilance through ongoing monitoring and an updated threat intelligence database to stay proactive against emerging and evolving threats.
The following is a subset of the Trellix Security detections that have been observed for the ongoing campaigns:
Trellix Network Security
Trellix VX
Trellix Cloud MVX
Trellix File Protect
Trellix Malware Analysis
Trellix SmartVision
Trellix Email Security
Trellix Detection As A Service
Trojan.MSIL.AgentTesla.FEC3
InfoStealer.MSIL.AGENTTESLA.MVX
Malware.Artemis.FEC4
Trojan.Win32.Guloader.FEC3
FEC_Trojan_NSIS_Generic_8
Trojan.MSIL.FormBook.FEC3
Trojan.Win32.Generic.FEC3
Trojan.MSIL.Injuke.FEC3
Trojan.Win32.Remcos.FEC3
Trojan.Artemis.FEC4
Trojan.Win64.AgentTesla.FEC3
Trojan.MSIL.Lazy.FEC3
Trojan.Formbook
Trojan.MSIL.LokiBot.FEC3
Trojan.Win64.GenSteal.FEC3
Trojan.Win32.TerraLoader.FEC2
Trojan.Win32.Swotter.FEC3
Suspicious Process PowerShell Param
Suspicious Codeinjection Activity
Suspicious Process and CodeInjection Activity
Malicious AGENTTESLA Indicator
Suspicious Process Powershell Activity
Suspicious File Stealing Activity
Suspicious File Dropper Activity
Suspicious Folder Credential Access
Suspicious Process Self-Start Activity
Suspicious File Recon for AMSI
Suspicious File Persistence Activity
Suspicious Codeinjection on Known Benign File Location
Suspicious Process Activity (Email Anomaly)
Suspicious Codeinjection Activity
Trellix Endpoint Security (HX):
AGENT TESLA (FAMILY)
OFFICE SPAWNING CMD (METHODOLOGY)
POWERSHELL CARET OBFUSCATION (METHODOLOGY)
Suspicious File Download using Equation editor Process
Exploit Shellcode downloading a file
Suspicious use of Start-Sleep by PowerShell
Suspicious Powershell Command
Suspicious use of Escape Character in PowerShell
Powershell bypassing execution policies
Executable created by PowerShell Executable file moved
Gen:Variant.Lazy.417492
Generic.mg.daf9b948ed287fd0
Generic.mg.970000496728cf8c
Generic.mg.559aba26ccb31464
Trojan.GenericKD.70138337
Trojan.GenericKD.70716716
Trojan.GenericKD.40044901
Trojan.Generic.34203135
Trojan.GenericKDZ.103119
Trojan.GenericKD.70270517
Trojan.GenericFCA.Script.23256
Generic.Dacic.ACCC3515.A.365028EB
Gen:Variant.Nemesis.29547
Conclusion
To conclude, our research highlights the ways cybercriminals take advantage of the current job market uncertainties to exploit both job seekers and employers. The key takeaway is the importance of maintaining vigilance. For employers and job seekers, implementing proactive security measures becomes essential in protecting against these targeted attacks. Stay informed, stay secure, and navigate the job market landscape with a proactive cybersecurity mindset.
Attributions
We would like to give proper credit and recognition to the various elements that have contributed to the content of this blog. The following list outlines the attributions for these elements:
IMAGES
ICONS
We sincerely appreciate the contributions of these elements to our blog and acknowledge the importance of giving credit where it's due. Should there be any concerns regarding attributions or if corrections are needed, please don't hesitate to contact us. Your understanding and support are greatly valued.
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.