Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Nation State Actors got you down? A CISO's guide to protecting data from Keyboard to Cloud
By Liberty Williams and Laurie Robb · March 21, 2024
It’s nearly impossible to provide quality business-to-business or business-to-government services without encountering sensitive, regulated, or secret customer data. That’s a lot of risk to take on. Trellix can help keep data safe from the moment you collect it until the moment you securely dispose of it.
The Problem:
The news has been full of breach notifications lately, and the loss and exploitation of customer data is getting to be more and more common. From the smallest mom and pop shops, to the biggest name brands in business software and services, it seems like Nation State Actors are coming for everyone these days. These state-affiliated hacking groups attempt to breach organizations they believe can provide actionable intelligence for warfare or diplomatic advantage, to gain cyberwarfare capability (think, shutting off the water supply, internet, or power to a metro area), or simply to do crime to fund their regime. As supply chain attacks become more popular, it’s worth remembering that most of our organizations are part of someone else’s supply chain.
It can be tempting to solve the problem by simply never collecting any customer data. This is unfortunately unrealistic for many organizations, especially those who provide products and services to government organizations. Responsible business partners, vendors, suppliers, and OEMs have a duty to secure their information systems, and properly manage IT operations and data handling practices. Don’t worry, you’re not alone in defending your patch. Trellix actively tracks Nation State Actors, including global activity, infrastructure, and TTPs. We use the intel we gather to provide detection, protection, and response content for our products, as well as to inform continuous product enhancement to counter dynamic threats. We also provide strategic, operational, and tactical level threat intelligence to customers through our threat intelligence services. Trellix XDR can provide automated moving target defense to ruin the bad guy’s day. We have tools to protect against Insider Threats too.
The Solution:
Data Security is about more than just preventing and healing the breach quickly, we also need to make sure we are following the organization’s Data Strategy, and utilizing Data Governance processes to exert affirmative control over how the organization interacts with data. Organizations need countermeasures for every data vector, which Trellix can provide, but they also need to know what data matters to them, what it looks like, and how they intend to protect and manage it.
If you aren’t sure what a high-quality Data Governance program looks like, here’s a high-level view. As you can see, we have to carefully consider both internal and external stakeholders, and our desired outcomes, across the entire data lifecycle. Trellix Professional Services is able to help you get started with this process if you’re unfamiliar, and provide advanced guidance to those already on the journey. It’s a great way to spend your Trellix Thrive credits.
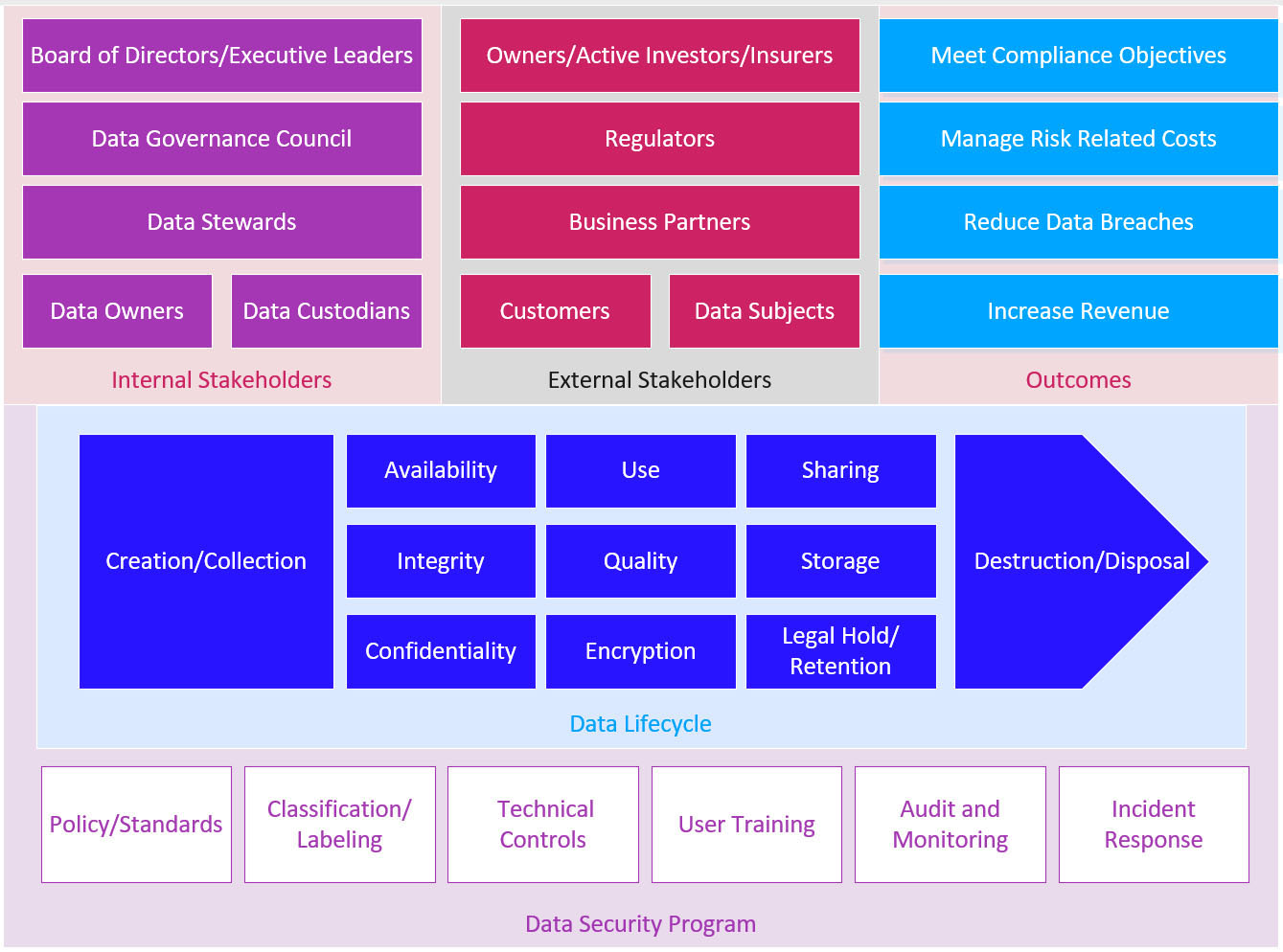
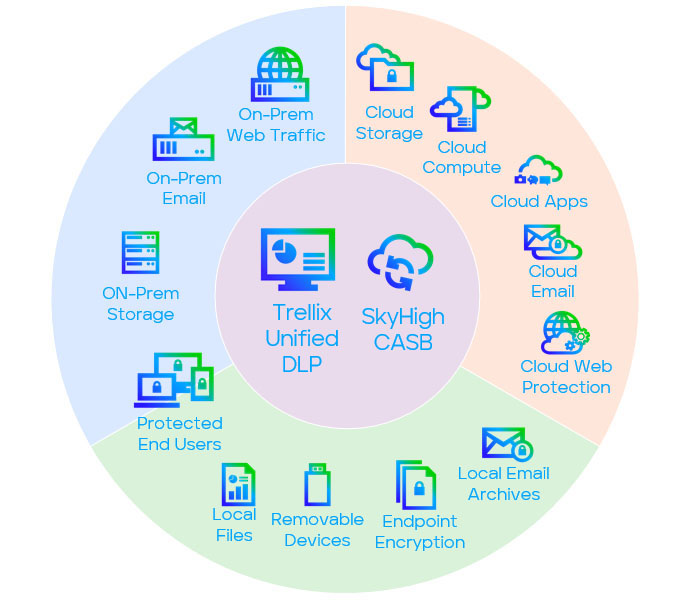
Once the organization has developed the Data Governance muscle, we will be able to exert control across the many data exfiltration vectors. Knowing what data needs to be restricted and what data can be allowed through each vector, and to/from for each destination, is critical to the success of your data security program. Trellix has a variety of countermeasures to cover data whether the user is entering it for the first time with their keyboard or storing and manipulating it in the cloud.
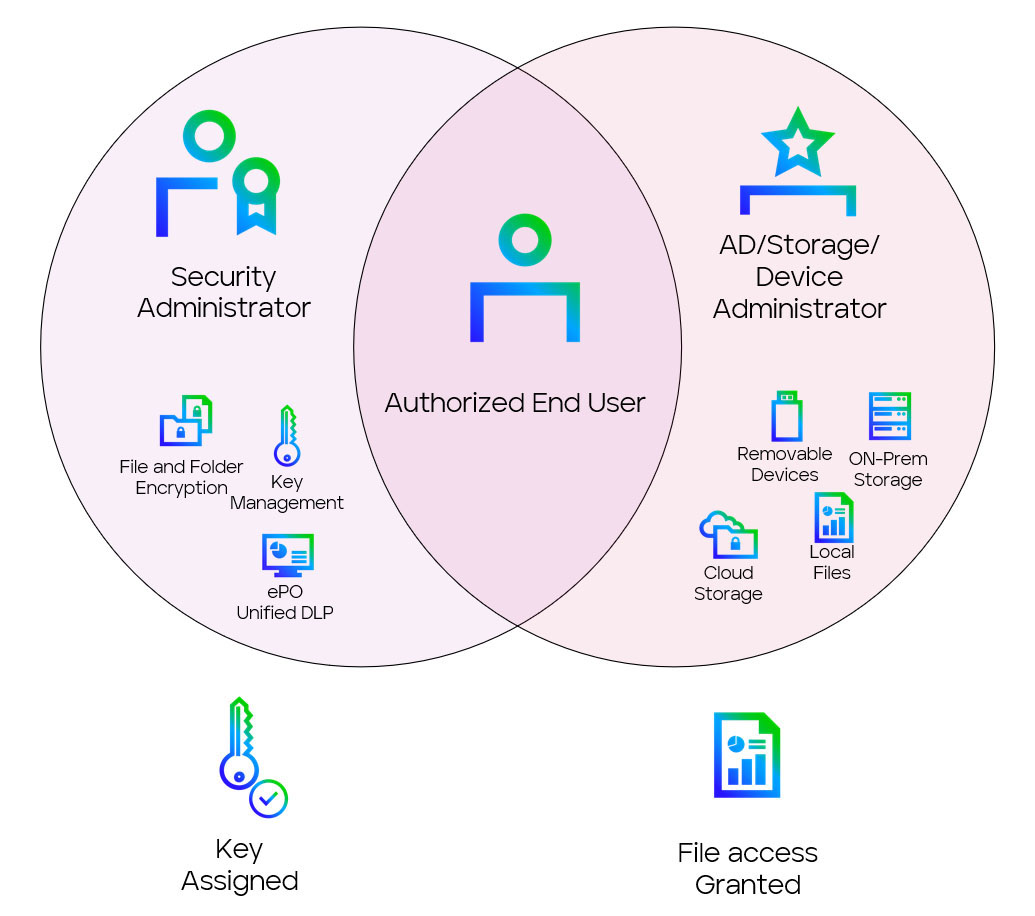
Lastly, we’d love to leave you with a key process control you can implement quickly. Using Encryption for Separation of Duties use-cases can dramatically increase the amount of work that Nation State Actors have to do in order to successfully exfiltrate data. Password Spraying attacks, such as those used to great success early this year, can often be successful in compromising one or two accounts. If the account compromised happens to have administrative privileges, this can open the floodgates to data theft.
We can increase the level of effort required by encrypting the data that’s worth taking, and ensuring that the administrator of our encryption program is not the same as our device or storage administrator. As shown in the graphic below, no single compromised account can grant themselves access they shouldn’t otherwise have. Ensuring that all authorized users have controls like strong Multi-Factor Authentication in place (No did you log in here yes/no? Push notifications please) as a condition of access can further harden your org in these situations. Even something as simple as “Encrypt all locally stored outlook archives” can significantly reduce data exfiltration risk. Trellix File and Removable Media protection can achieve this quickly and easily with a little help from Trellix Data Loss Prevention Endpoint.
The Summary:
- Strengthen or build your organization’s Data Governance Program so you can affirmatively control the data your organization holds
- Map your Data Governance requirements to your technical controls/countermeasures to ensure there are no gaps
- Use Encryption to enforce separation of duties, making successful exfiltration more difficult
- Call Trellix Professional Services if you need help with anything discussed today
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
