Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Mitigating Security Update Risks Part 2: Product Features ePO, EDR, and ENS
A Professional Services Perspective
By Liberty Williams, Zak Krider, Aaron Yarnal, Brandon West and Eugene Morganti · July 26, 2024
In part 1, we explored best practices for structuring testing and deploying updates in customer environments. Trellix promotes these best practices because they have proven to work consistently to improve customer experience and mitigate risks associated with software and content updates. Let’s explore more deeply how Trellix puts this into practice from a technology perspective.
How Does the Design of Trellix Products Support these Testing Procedures?
Whether customers deploy in SaaS or on-premises, Trellix has designed our ePolicy Orchestrator (ePO) to offer a high degree of control over both software and security content update deployment.
How ePolicy Orchestrator Manages Software and Content Updates
Trellix ePO for both SaaS and on-premises, has a storage area called “The Main Repository,” which stores both software and content updates in “Branches.” In ePO for SaaS, the branches correspond to each software release, for example 2024-06, 2024-05, etc., and one branch for N-0, which is labeled “Current.“
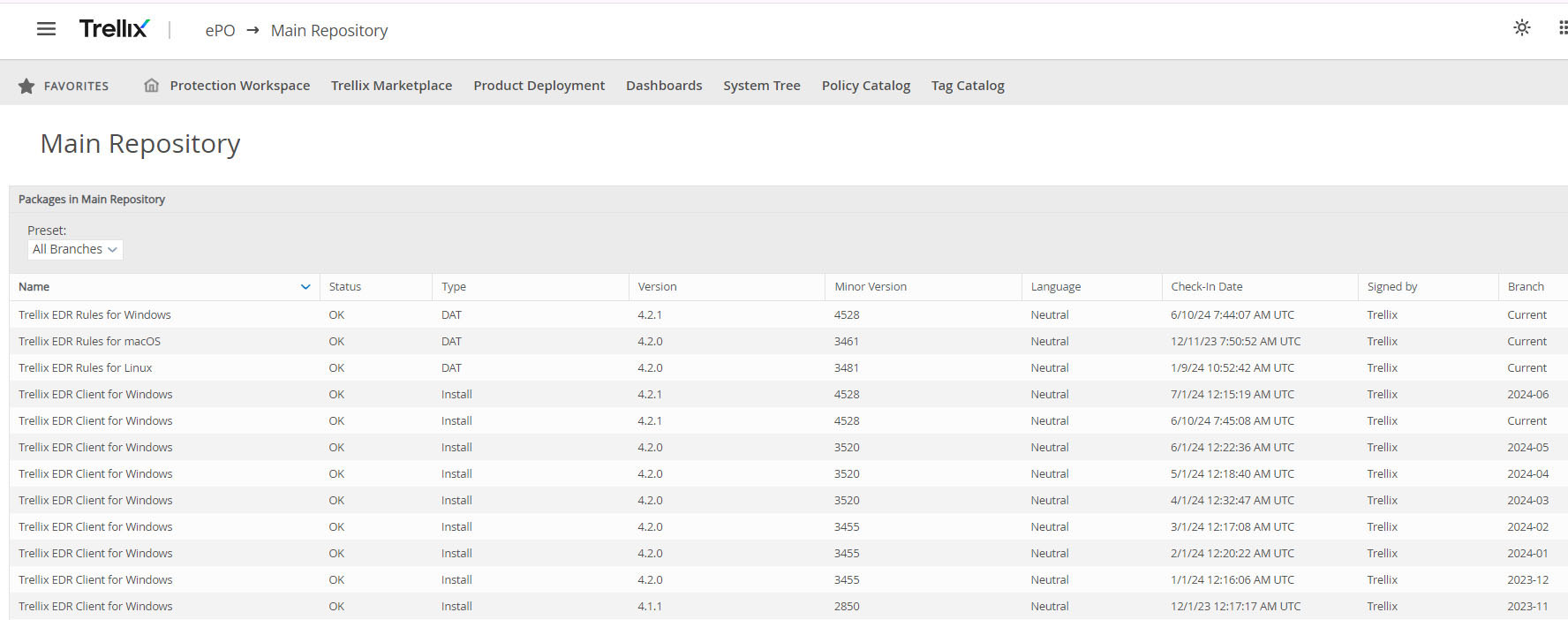
In ePO for on-premises, the three branches are named “Evaluation,” “Current,” and “Previous,” representing N-0, N-1, and N-2 versions. Each software and content package moves through the branches separately, at a pace controlled by the customer ePO administrator.
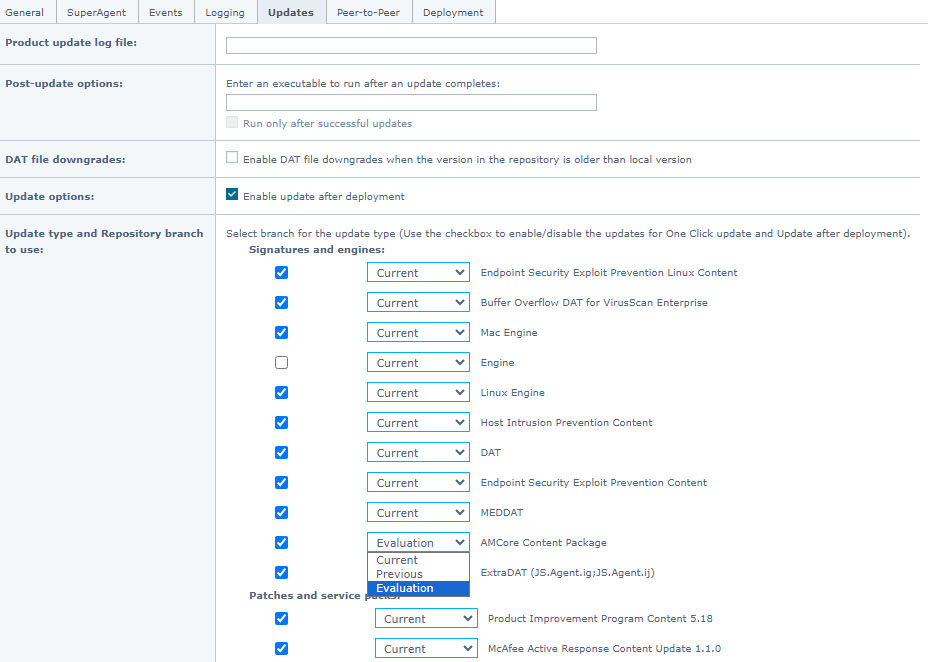
Trellix Agent (TA), the component that communicates between managed endpoints and Trellix ePO, has an administrator configurable policy that selects, per content package, whether it will download updates from the “Evaluation,” “Current,” or “Previous” branches. This allows ePO administrators to create multiple testing groups for each type of security content used in their environment. Customer ePO administrators can also choose to set different update schedules for different subsets of their environment. For example N-0, for a group of testers, N-1 for the majority of end user workstations, and N-2 for critical operational infrastructure.
How Customers Access Content Updates
SaaS ePO administrators automatically receive the latest content files and can choose when to provide those updates to end-user machines by a task schedule defined by the customer administrator. The Trellix Operations Team has created a Canary Deployments waterfall for daily content updates, and customer administrators can configure specific machines to act as canaries in their environment.
With on-premises ePO deployments customers, have control over an automation task that downloads the latest available content, which can be our flagship AMCoreDAT, Intrusion Prevention rules, Endpoint Detection and Response rules, Post-Execution Analysis rules, updated AI/ML Detection Models, etc.
Customer administrators for SaaS and on-premises can choose how often this task checks for updates, which updates are selected each time, and whether the updates are immediately deployed to end user devices or not.
Trellix Endpoint Detection and Response Content Updates
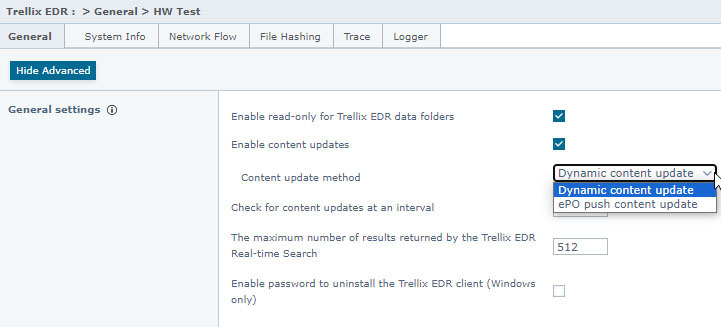
Customer Administrators have the option to dynamically update content for Trellix Endpoint Detection and Response, or to handle these updates via a push from ePO. Customers can select this in policy and it is set differently for multiple groups of machines.
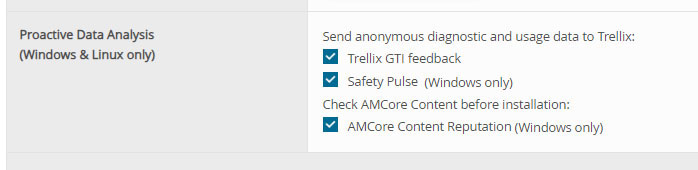
AMCore Content Reputation (DAT Reputation)
AMCore Content Reputation is a feature developed specifically to automatically defend against content updates that include risky and disruptive false-positive detections. When configured, the endpoint checks a reputation database via web API to see if other machines and customers experienced difficulties with that version of the content. If they have, it automatically rejects the update. It’s a simple checkbox in the policy, and Trellix highly recommends all customers use Content Reputation.
How Customers Access Software and Driver Updates
In SaaS ePO, customers automatically have access to several of the most recent versions of software packages included in their subscription. They can choose to deploy the N-0, N-1, and N-2, etc. versions of each product to any subset of their environment by creating a deployment task. This task has a schedule, which can be set to run only once or to recur at any interval chosen by the administrator. Software updates are never deployed to a customer endpoint in SaaS ePO except as specified by a customer administrator using a deployment task or by manually deploying the SmartInstaller to specific systems.
On-premises ePO deployments require extra legwork on the part of the customer administrator. The “Software Catalog” allows for certain packages to be added/updated into the Master Repository with the click of a button, depending on the customer subscription. Customers can also download all the software packages they are entitled to via the Trellix Product Downloads page, and manually check these into the desired main repository branch. Just like SaaS ePO, the software packages are never deployed to a customer endpoint except as specified by a customer administrator using a deployment task or by manually installing the executable on specific systems.
How ePolicy Orchestrator Can Automate Testing in Your Environment, According to Your Wishes
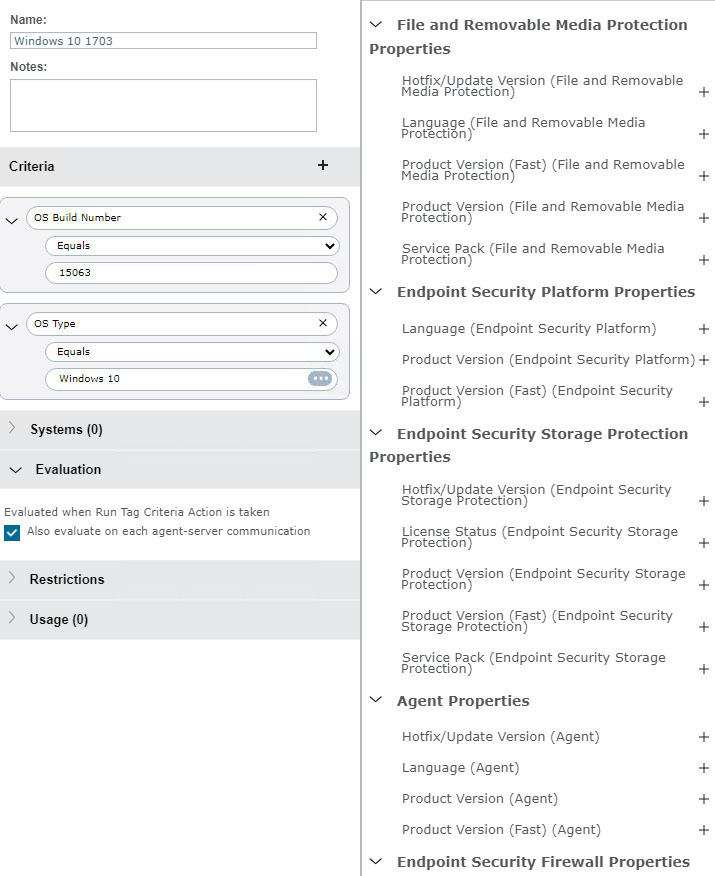
Trellix ePO supports tagging machines using automatic criteria information. This criteria can be hardware, OS, or Trellix installed software-related information. This enables customer administrators to choose groups of representative machines to act as canaries for phased deployments and daily update testing.
For example, OS Build Number (15063) is used in combination with a specific OS Type (Windows 10). When the endpoint agent connects to the ePO, it is interrogated and if it matches the criteria, the tag is assigned. If the criteria on the endpoint agent changes, the tag will be automatically removed. By using this method, you can automatically deploy or remove software from these systems.
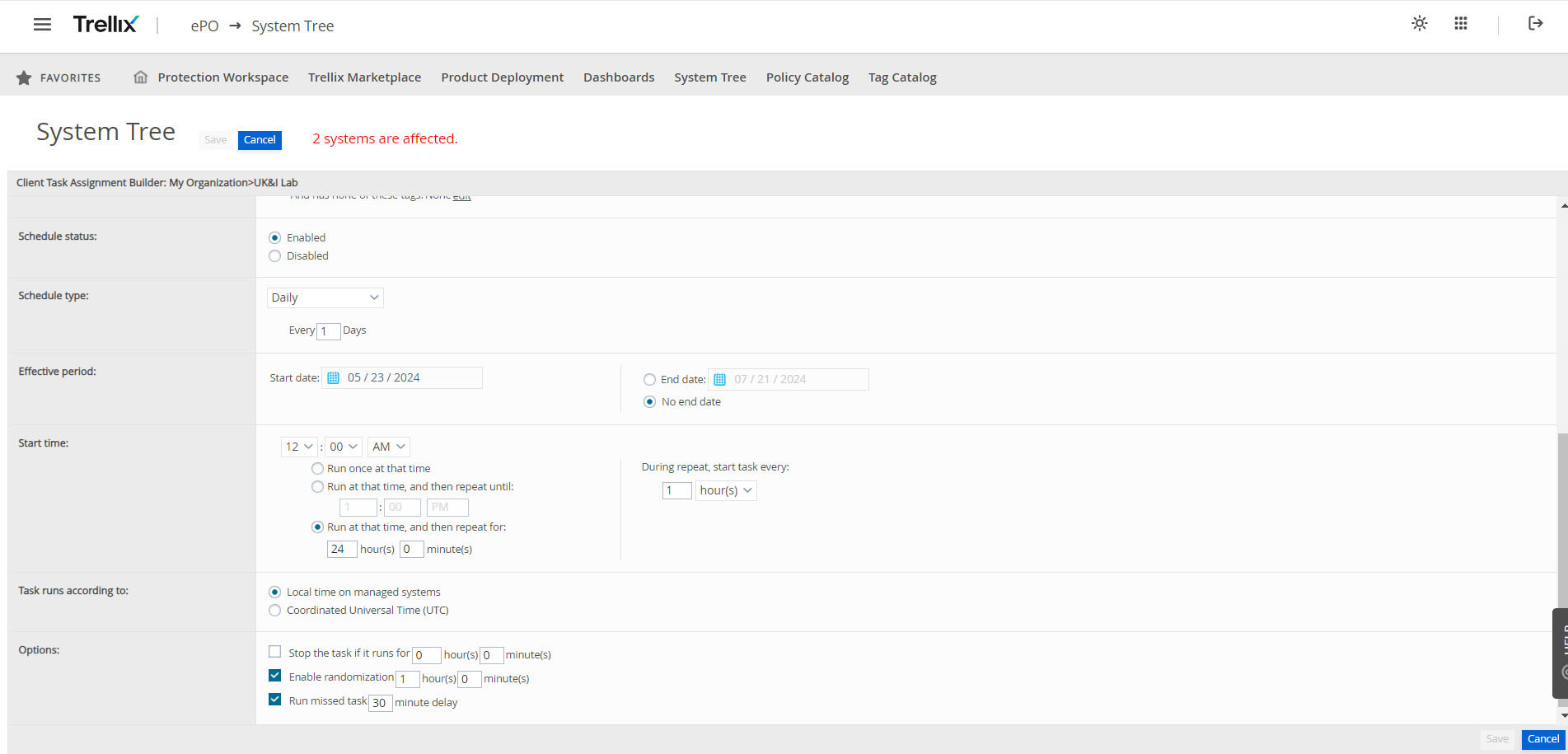
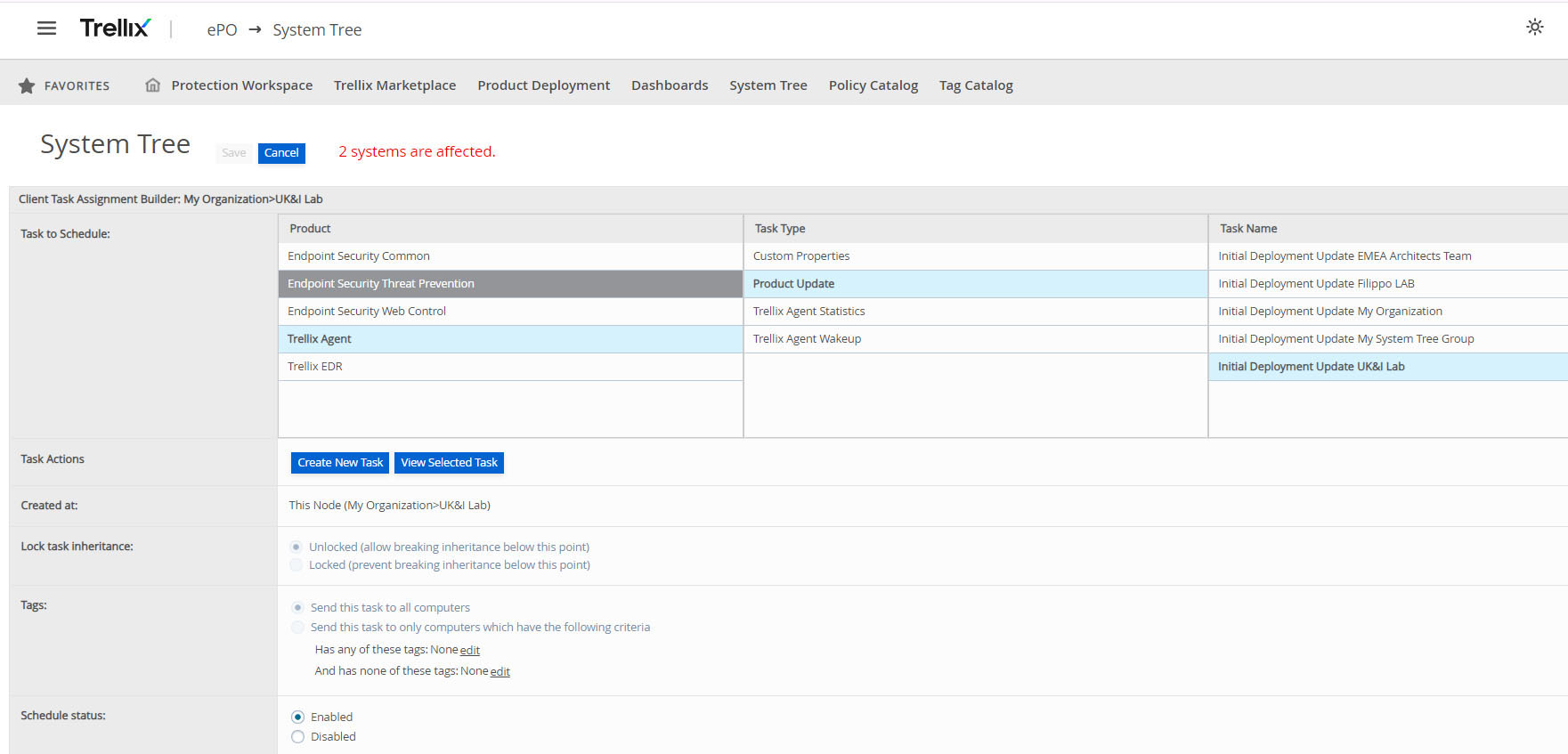
Rolling Back the AMCore Content
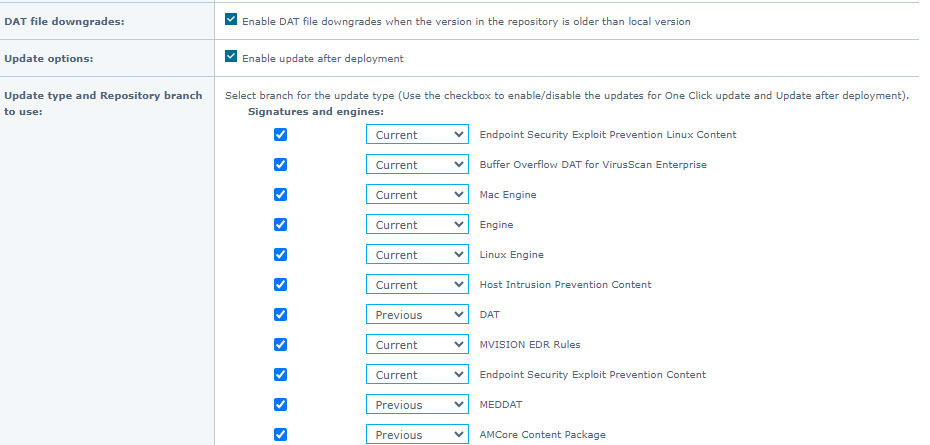
If a DAT file is deployed, that causes unforeseen issues with endpoints, the Trellix Agent has a configuration that will force endpoint agents to downgrade their DAT to a previous version.
The Agent Policy can be configured by customer administrators with "Enable DAT file downgrades" when the version in the repository is older than the local version and the Trellix Agents are configured to use the N-1 or N-2 branch of the repository. When configured this way, their next scheduled or manual DAT update will force them to download the older DAT and replace the newer one with the older one.
Customer administrators who need things to go a little more quickly can issue a client task assignment to roll back both AMCore DAT and EDR Rules content updates, as shown in the figures below.
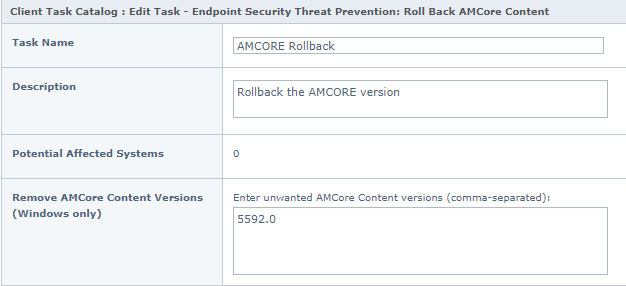
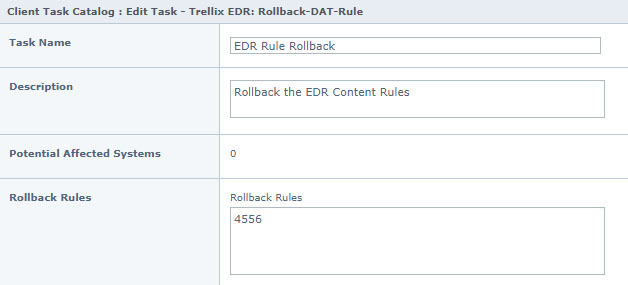
Conclusion
While incidents like the July 19, 2024 CrowdStrike outage are disruptive, Trellix offers customers Transparency, Choice, and Responsibility in our software and content update processes. We give our customers the power to exercise due diligence and consistent testing in their environments, which can dramatically limit impacts and reduce the risks to your organization. If your organization needs help putting in that effort, consider Trellix Professional Services. We offer various strategic and technical services that can help your team test, automate, operate, and govern your cyber defenses. Contact your Trellix account manager, or if you haven’t got one yet, let us know you’re interested. Tell them you want fully tested software and security content updates to get the ball rolling!
Continue reading the series: Part 1 (Intro), Part 2 (Product Features ePO, EDR, and ENS), Part 3 (Product Features Endpoint Forensics), and Part 4 (Testing Procedures for ePO, EDR, ENS, and HX).
Make sure you read this disclaimer after all that recommendations goodness:
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
