Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Eradicate Deeply Embedded Threats with AI-powered Endpoint Forensics
By Sanjay Raja · July 22, 2025
Almost four in five (78%) of organizations who pay a ransom demand are hit by a second ransomware attack, often by the same threat actor, according to Infosecurity Magazine. These occurrences can be fueled by both a lack of proper root-cause analysis and a failure to impose stronger security measures based on lessons learned post-ransomware attack.
Major gaps in current EDR approaches
While endpoint detection and response (EDR) and endpoint protection platform (EPP) solutions have become essential for detecting and investigating advanced threats, current solutions have not kept up with threat actors’ ability to deeply entrench malware beyond the scope of detection offered. Such threats are often missed by solutions that collect only surface level data and send it off to a centralized analytics engine (on-premises or cloud-based).
By not consistently performing detailed information gathering and analysis, such as forensics, these solutions fail to fully identify deeply rooted malware. Coupled with a lack of root-cause analysis, this can leave systems vulnerable to reinfection.
In addition, the complexity of filtering out false positives and manually investigating endpoint security events often poses a steep learning curve—especially for junior analysts early in their cybersecurity career. This means more-experienced security analysts must bear the burden of manually collecting, analyzing, and further investigating data to determine root cause. If remnants from the initial compromise remain, they could be reactivated at a later date and even modified easily as a new variant of the existing attack.
To patch and harden systems to prevent any recurrence, it’s critical to figure out the root cause and all components of an attack. To do so, current approaches need to be replaced by deep AI-powered endpoint forensics that can simplify and automate complex investigations and provide richer, context-aware insights.
What endpoint telemetry is essential?
Trellix is focused on accuracy above all else. Accuracy actually fosters speed, especially when it comes to investigation and response. Speed of detection without accuracy means you are chasing false positives and building responses that do little to prevent damage from a breach. This approach can fail to prevent a re-emergence of an attack or a new variant that works off an existing beachhead into your environment.
The marriage between Trellix Endpoint Detection and Response (EDR) and forensic capabilities fosters better accuracy that enables even junior analysts to work faster, transforming reactive incident response into a proactive and deeply analytical process that has been simplified. Trellix EDR with Forensics (EDRF) continuously monitors endpoint activity, collecting rich telemetry data such as process execution, file changes, network connections, and user behavior in real-time.
This constant stream of high-fidelity data forms the foundational evidence for forensic investigations. When a suspicious event or alert is triggered, Trellix EDRF's integrated forensic features allow security analysts to immediately pivot from detection to deep-dive analysis. This includes:
- Reconstructing attack timelines
- Visualizing attacker movement across the environment
- Identifying the root cause of an incident
- Understanding the full scope of a breach without needing to manually collect artifacts or take devices offline
By providing this granular, historical context and enabling remote investigation and data retrieval, Trellix EDRF significantly accelerates the forensic process, allowing organizations to not only contain and remediate threats faster but also to gain critical insights for strengthening future defenses and ensuring compliance.
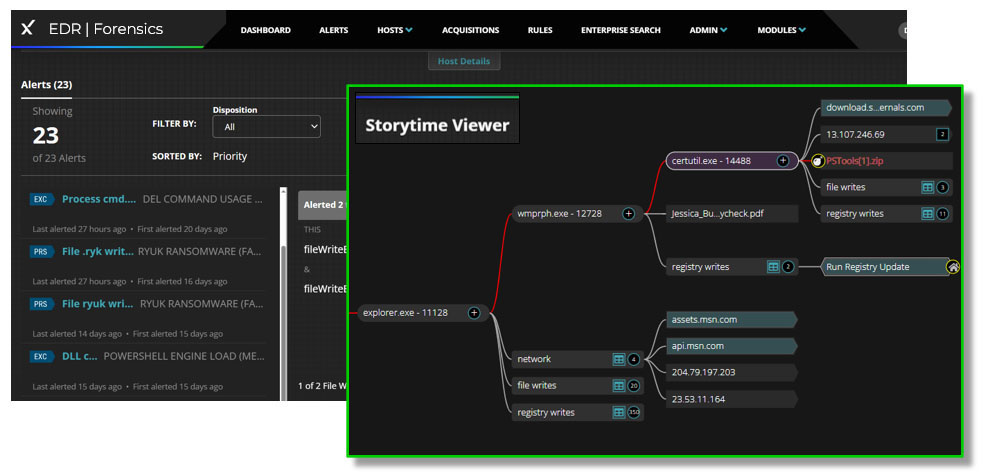
Closing the loop: Protection to detection to prevention
When you integrate Trellix EDRF with Trellix Endpoint Protection Platform (EPP), which can also harden endpoints, you achieve a truly holistic and proactive security posture. Trellix EPP acts as the first line of defense, proactively preventing known and emerging threats through technologies like next-generation antivirus (NGAV), behavioral analysis, and application control. This hardening significantly reduces the attack surface, making it more difficult for malicious actors to gain initial access.
Should a threat manage to bypass these preventative measures, the forensic capabilities of Trellix EDRF immediately kick in, providing real-time visibility into endpoint activity, detecting suspicious behaviors, and correlating events to identify potential attacks. Trellix EDRF's rich telemetry data feeds directly into the forensic analysis, allowing security teams to reconstruct the entire attack chain, understand the root cause, determine the scope of compromise, and identify affected systems.
Crucially, the insights gained from these forensic investigations are then fed back into Trellix EPP's hardening mechanisms. For example, if a specific attack variant exploited a particular misconfiguration or vulnerability, Trellix EPP can be automatically updated or configured to close that gap across all endpoints, preventing the same or similar variants from succeeding in the future.
This continuous feedback loop of prevention, detection, response, forensic analysis, and re-hardening creates a self-improving security system, enabling organizations to adapt to evolving threats and build truly resilient endpoints.
How do AI and intelligence accelerate the process?
To completely eradicate the full scope of an attack and understand all facets of a complex threat or campaign and its associated risk, security analysts must go beyond what a typical EDR solution provides and manually gather additional data during investigations.
However, organizations often struggle with limited resources and to retain experienced analysts. Higher-level analysts lack time for numerous alerts, while inexperienced analysts may escalate prematurely, overburdening Tier 3 analysts and hindering proactive threat hunting.
By combining the expertise of Trellix incident responders and the Trellix Advanced Research Center with AI, investigation guides in Trellix EDRF force multiply the investigation process. Unlike playbooks that automate scripted tasks for known threats, investigation guides dynamically adjust to each case, combining different investigation strategies and data. Trellix EDRF automatically gathers, summarizes, and visualizes evidence from multiple sources and iterates as the investigation evolves.
In addition to guided investigation, analysts and threat hunters can use Trellix EDRF with Trellix Wise™ GenAI capabilities to reduce the expertise and effort needed to perform investigations, This increases the speed with which analysts can determine the risk of an incident and its root cause by enabling automated investigation, alert correlation, and report generation.
Trellix EDRF with Wise automatically collects and correlates related breaches, artifacts, network connections, and more into a visual graph to accelerate investigations. In addition, Trellix Wise provides detailed recommendations of next steps to take based on the nature and severity of the threat identified, cutting down response time. It also provides one-click report generation so analysts can focus on security instead of paperwork.
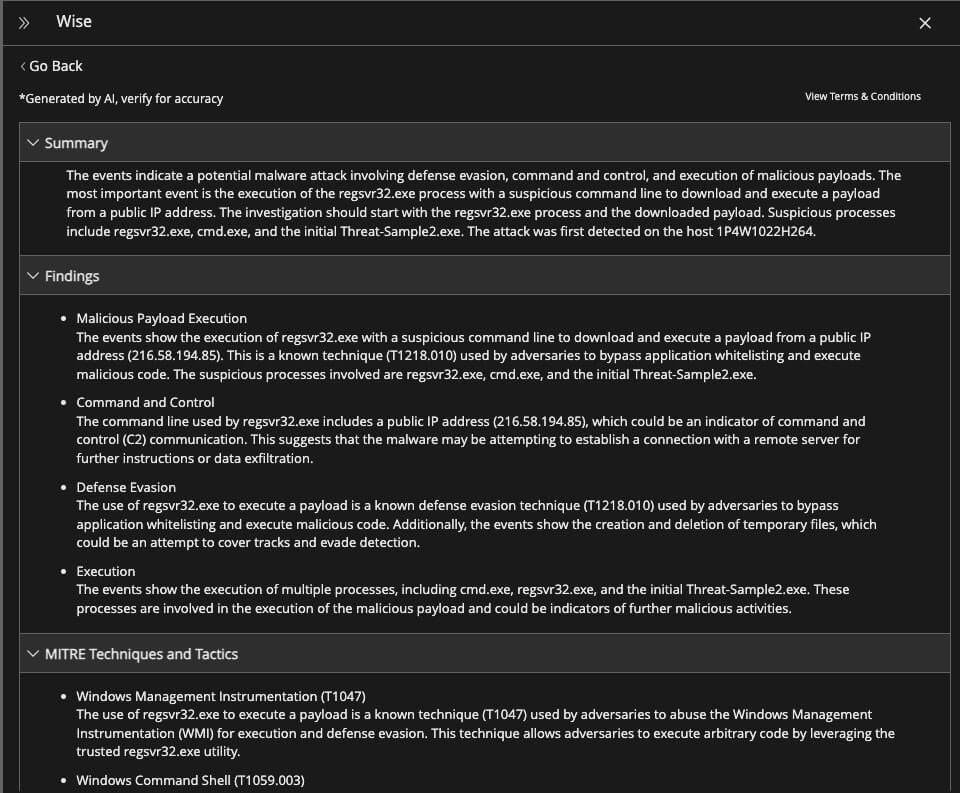
Conclusion
The integration of Trellix Wise into Trellix EDRF marks a significant advancement in how SOC analysts handle threat detection and response.
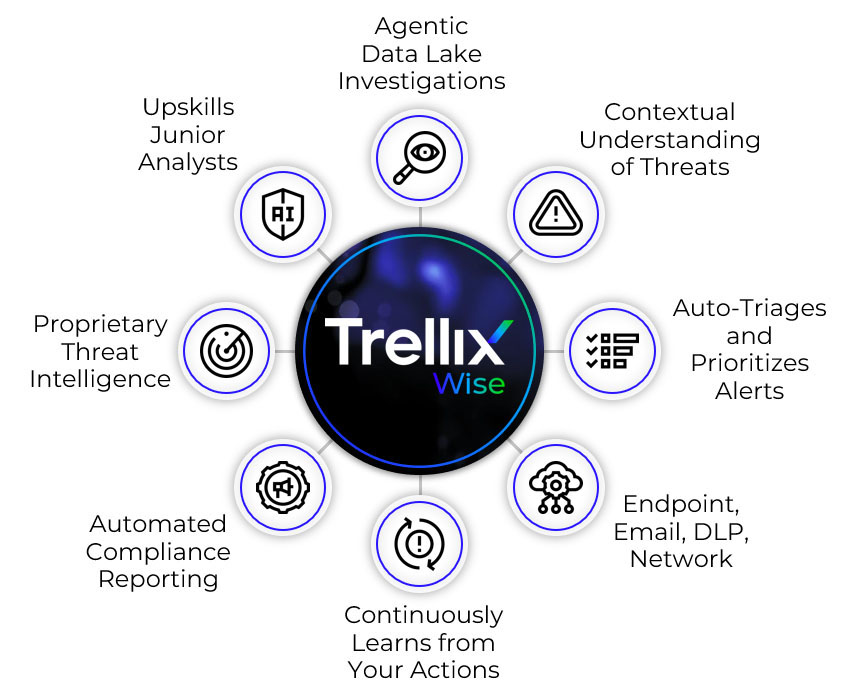
Trellix EDRF enhances the capabilities of our endpoint detection and response solutions. A highly performant modular agent that's built on a common sensor stack, it conforms to modern unified endpoint security agent architecture. Adding Trellix Wise’s powerful GenAI capabilities also simplifies the process of uncovering and investigating even the most deeply embedded and hidden threats, and ensures rapid and accurate remediation.
Trellix EDRF empowers resource-constrained security teams to cut through noise, accelerate threat hunting, and make more accurate decisions—boosting their effectiveness and confidence. To learn more, watch our webinar, “Beyond Detection: Rapid Response & Deep Forensics with EDRF.”
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
