Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Trellix NDR, the Next Evolution of Trellix Network Security (NX)
Expand network visibility and disrupt attacks faster with advanced AI
By Ravi Adireddi · October 10, 2025
As a Trellix Network Security (NX) customer, you've built a strong foundation for network threat detection. However, growing network complexity and maxed out security teams are making comprehensive protection against advanced threats increasingly difficult to achieve. But what if you could easily get insight into which assets are most at risk? And you could orchestrate your investigation and response using advanced AI, empowering your teams to disrupt attackers at every stage?
Trellix Network Detection and Response (NDR) enables you to do just that through risk-based intelligence, streamlined analyst workflows, and unified security operations. Even better—as an existing Trellix Network Security (NX) customer, you can seamlessly access this powerful new Trellix NDR technology while retaining all of your current NX capabilities.
Why the NDR evolution is inevitable
Enterprise networks have become significantly more complex, encompassing on-premises data centers, multicloud environments, remote endpoints, IoT devices, and third-party integrations, all forming intricate webs of interconnected systems.
This distributed infrastructure is experiencing a rapid proliferation of cyber assets, while the vulnerability landscape relentlessly expands, with each new connection point introducing potential attack vectors. As attack sophistication increases, organizations need to evolve their network security.
This explosive growth in both scale and complexity has fundamentally transformed the attack surface, leading to countless blind spots. It overwhelms traditional security approaches that were designed for simpler, more centralized network architectures.
In addition, the increased adoption of traffic encryption, while vital for privacy and compliance, has created an invisible network where sophisticated threats can operate undetected. Legacy security tools that rely only on deep packet inspection are less effective. This leaves organizations vulnerable to advanced attacks hiding within encrypted communications.
These conditions make it difficult—and expensive—for a modern-day SOC to rely on manual-only responses. So how does Trellix NDR address these issues? Let’s explore.
The Trellix NDR difference
Trellix has a strong heritage in network security. We’ve transformed our advanced threat detection appliances into a full NDR solution. A battle-tested veteran in enterprise environments, we are trusted by SOCs and incident response teams globally, with thousands of network security customers.
Over time, we’ve extended our capabilities from endpoint visibility to NDR through integration with the Trellix Security Platform. We’ve evolved our technology based on our security ops and development background, providing guided investigations through Trellix Wise, our advanced AI service.
Trellix NDR continuously monitors both north-south and east-west traffic across the perimeter and edge networks to detect and respond to threats, using machine learning and behavioral analytics to identify malicious and anomalous activities across cloud, hybrid, and on-premises environments. Such activities might be missed by traditional security tools such as next-generation firewalls, IPS, SSEs, and other systems.
By deploying advanced AI and orchestration, Trellix NDR empowers security teams to eliminate blind spots and risk, disrupt attackers at every stage, and accelerate investigation and response.
Here are three key areas in which Trellix NDR addresses today’s network security challenges with powerful capabilities.
Risk-based analyst workflows
Trellix NDR enhances threat investigation by streamlining and orchestrating workflows using Trellix’s risk aggregation framework to surface the most critical information and advanced AI to guide analyst response actions.
- The Detection Dashboard prioritizes alerts based on risk, showing assets most at risk, conversations, and alerts.
- Alert Workflows offer comprehensive context in one interface, enriching alerts with MITRE ATT&CK tactics, CVEs, and threat intelligence.
- Asset Workflows provide system risk visibility, combining vulnerability assessments, alert history, and network communications.
- Trellix Wise advanced AI capabilities automate threat analysis and provide contextual guidance, including alert summaries and remediation steps.
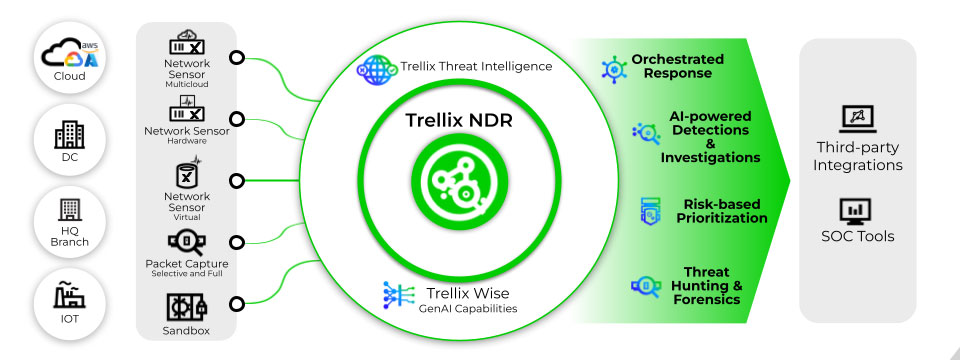
Figure 1: Trellix NDR provides advanced threat detection, investigation, hunting, and response capabilities.
Advanced detection and analytics powered by risk-based intelligence
Trellix NDR offers advanced detection capabilities against modern evasion techniques, providing comprehensive threat coverage and expanded visibility that other vendors can’t match.
- Asset risk prioritization uses AI and machine learning to correlate vulnerability data, allowing analysts to quickly identify and react to critical threats.
- Attack Path Discovery visualizes potential attack vectors by integrating vulnerability data with network topology. Machine learning–based detections identify subtle anomalies and unknown threats, including lateral movement and beaconing.
- Encrypted traffic analysis uncovers threats without decryption, using certificate reputation, SSL anomaly detection, and communication pattern analysis. Unlike other vendors, we provide this analysis inline, so you don’t need to bolt on another tool. Specialized detections cover credential harvesting, ICMP tunneling, DNS anomalies, domain controller anomalies, and data exfiltration.
Unified security operations
The Integration Hub unifies security operations by integrating with existing infrastructure.
- Trellix NDR enriches alerts and asset details with Tenable Security Center vulnerability findings, prioritizing high-risk assets.
- Integration with Trellix ePolicy Orchestrator On-premises provides endpoint context and enables direct containment actions.
- Splunk and other SIEM and EDR integrations offer enriched metadata forwarding and flexible integration options, while the Integration Hub provides centralized management and API-driven architecture for custom integrations. Third-party integrations with security tools, including vulnerability management tools, firewalls, proxies, and OT security platforms, are also available for complete network security visibility across IT and OT environments.
Easily go from Trellix NX to Trellix NDR
Trellix NDR seamlessly transitions Trellix NX users to its advanced capabilities. From Trellix NX to the enhanced Trellix NDR Sensor, customers retain all of their current NX capabilities. The transition preserves operational continuity while significantly expanding threat detection coverage and reducing false positive rates through intelligent correlation and risk-based scoring.
Trellix NDR is available with flexible deployment options. Existing Trellix NX users can make the move effortlessly, gaining advanced analytics and machine learning models, comprehensive threat coverage, intelligent risk prioritization, and unified security operations.
To learn more about transitioning from Trellix NX to Trellix NDR, contact your account manager to request a demo, or contact us to speak to an expert.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
