Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
New Helix enhancements make the analyst experience even better for Security Operations
By Grant McDonald · October 29, 2025
Imagine using a new app on your phone that scrolls up and down but not from left to right. If that wasn’t irritating enough, imagine that it comes with no tutorial and presents the information you are looking for in five separate areas. Even worse, you have to take the same 15 steps every time you use it, and getting your job done relies on using this app!
The scenario is just a glimpse into how security operations (SecOps) teams feel about many of the tools they use on a daily basis. A poor analyst experience directly impacts SecOps teams’ ability to get their jobs done. At Trellix, we are constantly working to improve Trellix Helix to empower security analysts, significantly reduce alert fatigue, and accelerate incident response. In our latest release, we have added a few notable changes that streamline the investigation process, provide richer context, and automate crucial response actions, allowing your team to focus on the most critical threats.
In the newest release, Trellix Helix is adding capabilities to empower security analysts, significantly reduce alert fatigue, and accelerate incident response, including:
Faster threat context:
- Group alerts
- Enhanced alert details and timeline view
- More detailed event information
- Faster pivots with contextual actions
- Ability to pin and hide events
Easier access to historical data:
- Sortable, exportable timeline
- Table view
- Comprehensive asset and history tracking
Integrated threat intelligence
No-code automation:
- Automated response actions and workflow creation
Key new capabilities:
Faster threat context
Now faster than ever analysts can grasp the who, what, when, and how of an investigation with a single click, providing faster clarity and helping them decide quickly whether to dive deeper into an alert.
Group alerts
Helix now consolidates hundreds of discrete alerts from various sources into a single, correlated multi-vector alert. This crucial function helps analysts prioritize significant issues by cutting through the noise and presenting a unified view of related threats. This is even more impactful when you consider some of the new detection use cases our engineering teams have been creating, which take advantage of the broader Trellix Security platform.
Enhanced alert details and timeline view
Analysts need to know who, what, when, and how to start an investigation, but collecting the story across alerts isn’t always straightforward. To help provide faster clarity, Helix offers a high-level summary of alert details in just a single click from the alerts list page The new, resizable side panel provides an efficient way to review necessary information, helping you quickly decide whether to dive deeper or bypass an alert without losing context.
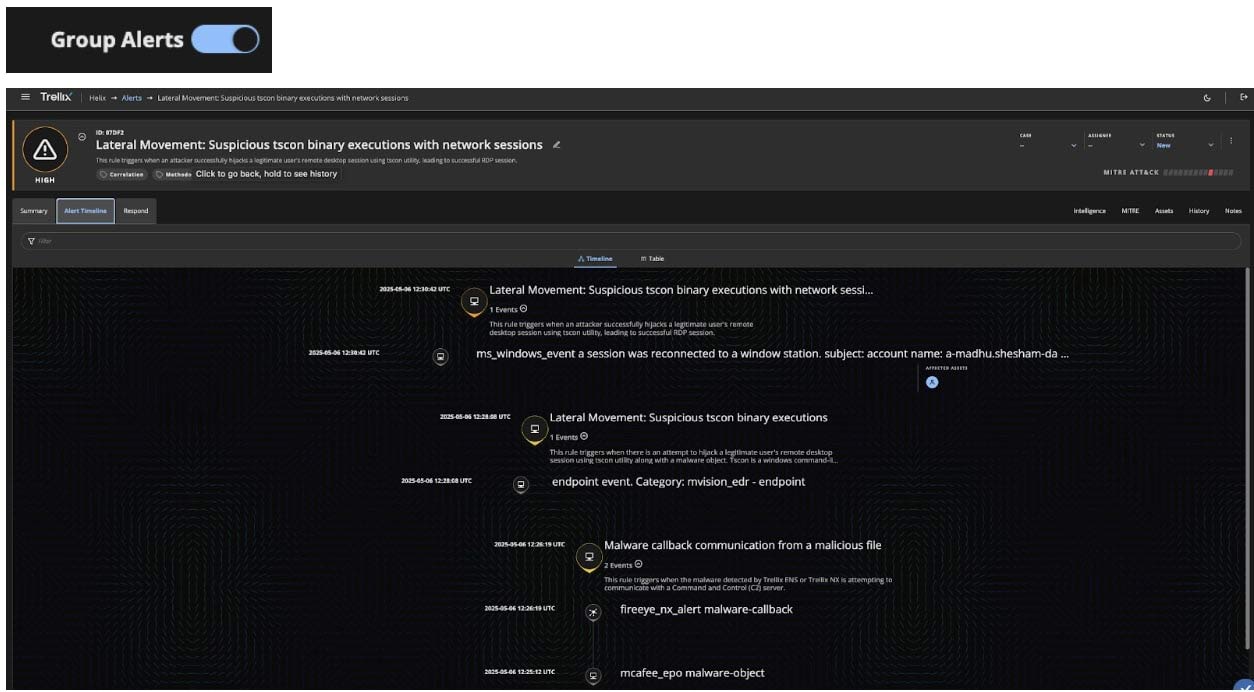
When you click into the alert details, the summary page shows you what triggered the alert, including the number of associated alerts, their first and last seen times, and critical "group by" values. These "group by" values are attributes that link related alerts across different vectors. For example, a file with a specific MD5 hash connecting an email alert to an endpoint alert indicates that the suspicious attachment from the email resulted in a malicious execution on the endpoint.
The new timeline view reconstructs the entire attack sequence for both single-staged and multi-staged alerts across relevant vectors. Analysts can then leverage filters to narrow down by severity or source, helping them focus on the most critical elements. Each card in the timeline displays the event/alert name along with description, associated rule, associated MITRE technique, and key artifacts essential for investigation.
More detailed event information
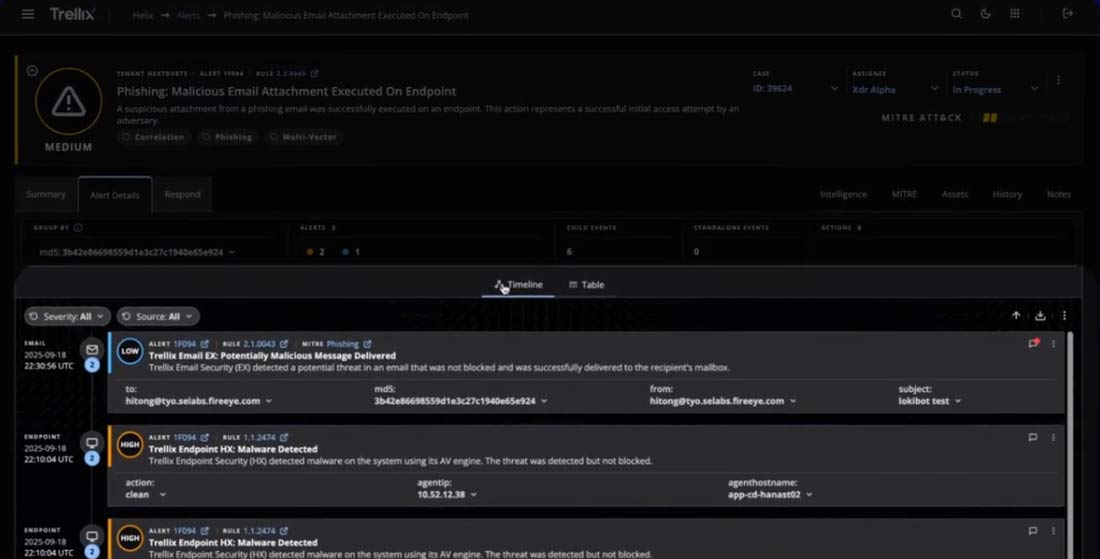
Drilling down into the timeline reveals associated events — access more information on associated events via the side panel. The new Event Details side panel provides all parsed fields for a selected event, with options to copy all fields or select individual ones. For deeper analysis, the raw log of the event is accessible and can be copied or exported. Analysts can also add formatted notes to specific events, marked by a red dot for easy identification.
Fast pivots with contextual actions
The Alert Details page now offers contextual actions for every field, including copying, grouping, adding to a new search, adding to an existing search, or excluding from a search. This enables fast pivots to new investigations without losing the current context. Selecting “add to search” on any field automatically populates the search bar and opens the Search results page in a new tab. This also helps analysts build queries in a single click, without needing to be fluent in any query language.
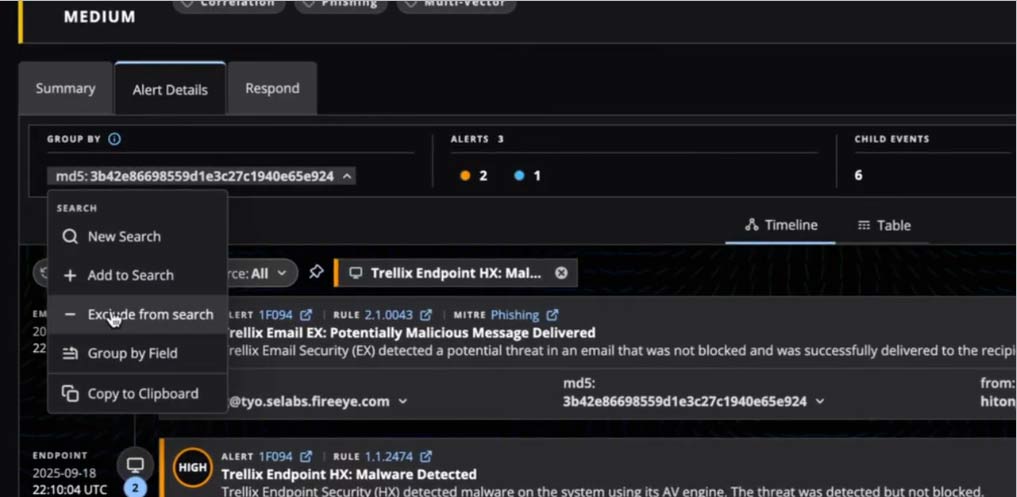
On the search results page, analysts can customize the default columns or save their own column set and view the details in the side panel for the specific event row. If the analyst wants to see all the parsed or raw data at once, they can toggle between the parsed and raw fields and view it on the same page.
The datetime field of a specific event, from either alert or search, offers a Time Wrinkle feature that lets analysts search for all the events that happened before or after that specific event occurred, allowing them to hunt for patterns. This seamless integration between alerts and search significantly reduces pivot time and enhances the investigation process.
Ability to pin and hide events
To combat long timelines, Helix introduces the ability to pin events and alerts of interest. This ensures that crucial information is readily available upon revisiting the page, eliminating the need to scroll through the entire timeline. You can hide unimportant events, and then unhide them with a simple click. The timeline further offers options to expand and collapse all nodes for improved navigation.
Easier access to historical data
Our new features empower analysts to quickly gain historical context combined with comprehensive asset and history tracking, ensuring better collaboration and auditable case management.
Sortable, exportable timeline
For reporting and further analysis, analysts can now export the timeline view, choosing between visible or all nodes. The timeline can also be sorted in ascending or descending order of event occurrence.
Table view
Complementing the timeline, the table view retains all interactions and filtering, providing a sortable grid for quicker data scanning.
Comprehensive asset and history tracking
The Assets tab offers a summary of all involved assets and their containment status, providing a quick overview of systems at risk. The History tab meticulously records every action taken on a specific alert, creating an auditable trail that supports collaboration and case management.
Threat intel
New features give analysts more context directly within the alert so they can make informed decisions quickly.
Integrated threat intelligence
The Notes section displays all notes related to an alert. The Intelligence tab provides critical threat intel from Trellix for specific artifacts, such as file hashes, IP addresses, domain reputation, etc. Clicking on intel reveals details such as overall severity, insights, associated campaigns, and a thorough description, along with recommended actions like searching for a hash on affected devices.
No-code automation
Trellix Hyperautomation allows analysts to rapidly configure and run automated response actions, empowering your team to focus on the most critical threats.
Automated response actions and workflow creation
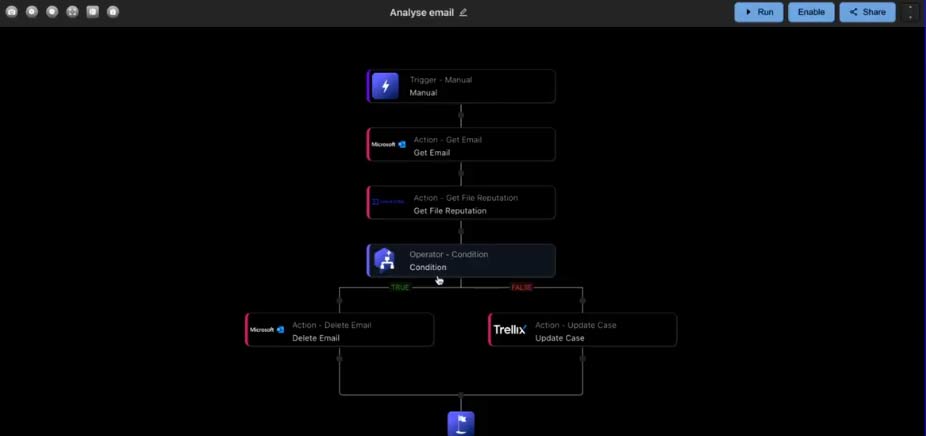
Trellix Hyperautomation is available with this release of Helix. It allows analysts with any level of expertise to create and perform automation. Workflows are created using a drag-and-drop workflow builder. Hyperautomation uses role-based access to help set the appropriate level of control over triggers and actions in your environment. Actions that require an administrator within the workflow won’t take place until the admin approves them.
Once they have sufficient context, they can navigate to the Respond tab to take action. If any workflows are configured, analysts will see them as recommended actions along with the workflow status and other details, and can run it directly. The new 'Add Actions' feature presents a list of all available actions and workflows, including who created and last updated them. Those actions can be configured, saved for later, or simultaneously saved and run for that particular alert. A notification confirms the successful execution of the workflow, and the summary page is updated with the latest action taken.
Analysts can also create custom workflows via the menu. Workflows are built by adding steps and conditions, configuring necessary parameters (e.g., email address and UID for retrieving an email), and defining output fields. Newly created workflows can be enabled and published, making them available in the alert section for specific alerts.
These enhancements are live for all current Helix customers, but we aren’t stopping there. We’re committed to continuously improving the analyst experience of Helix to make SecOps teams faster, more informed, and able to automate more of their incident response workflows. If you aren’t yet a Helix customer and want to see how it can boost the efficiency of your team, contact us, and one of our experts will be in touch to set up a personalized demonstration!
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
